Application Security
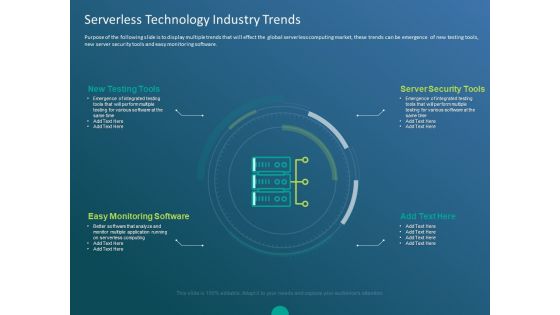
Functioning Of Serverless Computing Serverless Technology Industry Trends Ppt Portfolio Example Topics PDF
Purpose of the following slide is to display multiple trends that will effect the global serverless computing market, these trends can be emergence of new testing tools, new server security tools and easy monitoring software. This is a functioning of serverless computing serverless technology industry trends ppt portfolio example topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like new testing tools, server security tools, easy monitoring software, better software that analyze and monitor multiple application running, serverless computing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
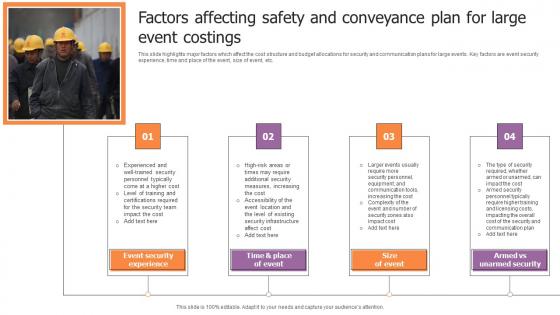
Factors Affecting Safety And Conveyance Plan For Large Event Costings Pictures Pdf
This slide highlights major factors which affect the cost structure and budget allocations for security and communication plans for large events. Key factors are event security experience, time and place of the event, size of event, etc. Pitch your topic with ease and precision using this Factors Affecting Safety And Conveyance Plan For Large Event Costings Pictures Pdf. This layout presents information on Event Security Experience, Size Of Event, Armed Vs Unarmed Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights major factors which affect the cost structure and budget allocations for security and communication plans for large events. Key factors are event security experience, time and place of the event, size of event, etc.
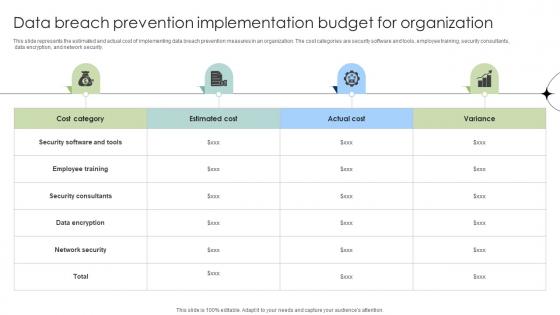
Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.
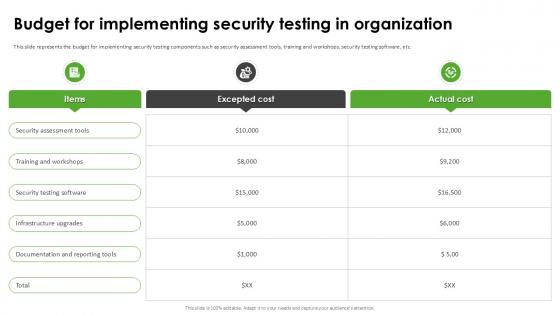
Budget For Implementing Harnessing The World Of Ethical Ppt Presentation
This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc. Get a simple yet stunning designed Budget For Implementing Harnessing The World Of Ethical Ppt Presentation It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget For Implementing Harnessing The World Of Ethical Ppt Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc.
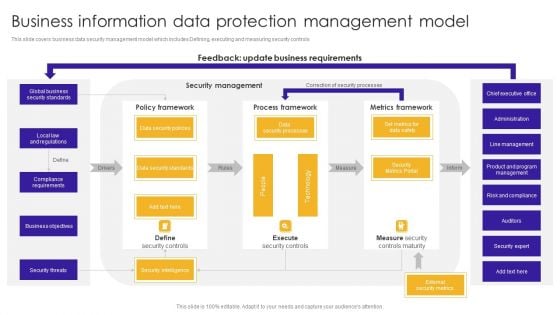
Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
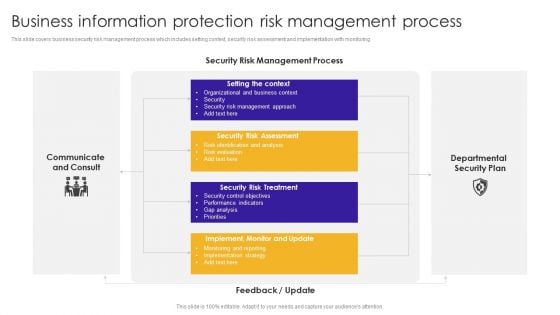
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
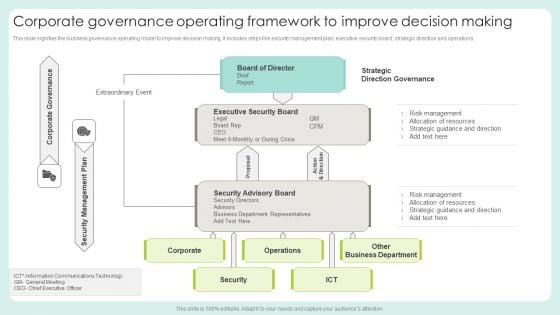
Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
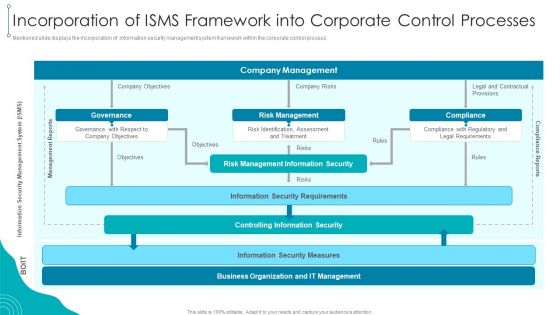
Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF. Use them to share invaluable insights on Management Information, Security Requirements, Information Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
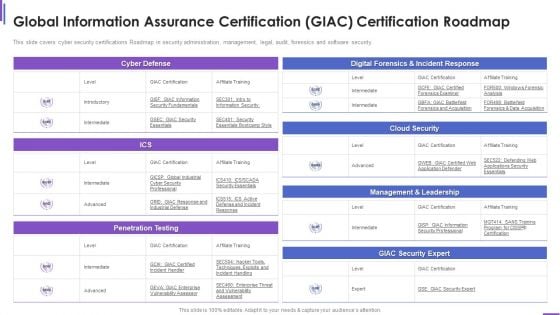
Collection Of Information Technology Certifications Global Information Assurance Designs PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this collection of information technology certifications global information assurance designs pdf. Use them to share invaluable insights on global information assurance certification giac certification roadmap and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Essential Roles And Responsibilities Involved In Secops Elements PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure.Deliver an awe inspiring pitch with this creative essential roles and responsibilities involved in secops elements pdf bundle. Topics like security incident responder, security alert investigator, security engineers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Main Advantages Of Software Harnessing The World Of Ethical Ppt Slide
This slide showcases the advantages of software security testing such as identifying weaknesses, enhancing security, ensuring compliance, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Main Advantages Of Software Harnessing The World Of Ethical Ppt Slide These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide showcases the advantages of software security testing such as identifying weaknesses, enhancing security, ensuring compliance, etc.
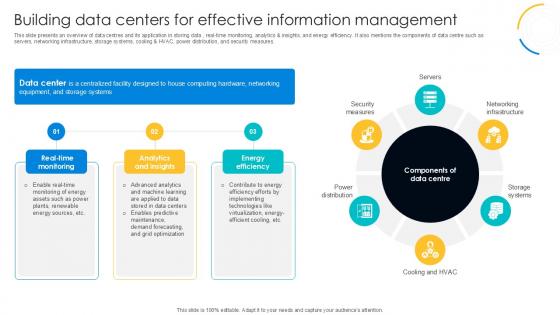
Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V
This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures. If you are looking for a format to display your unique thoughts, then the professionally designed Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures.
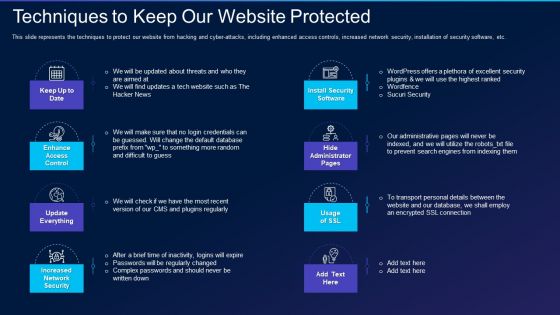
Cyber Exploitation IT Techniques To Keep Our Website Protected Brochure PDF
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective IT Risk Management Process Roles And Responsibilities For Managing Elements PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a effective it risk management process roles and responsibilities for managing elements pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, development, security, organizational, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF
The following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assessment Methodology, Risk QuestionsCyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
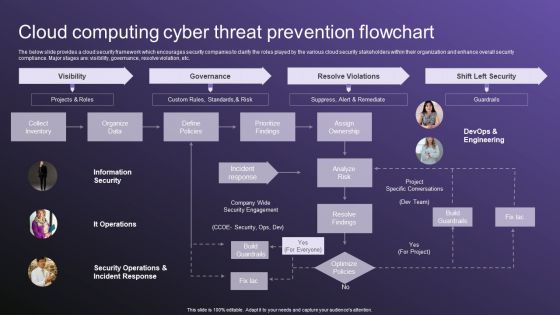
Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
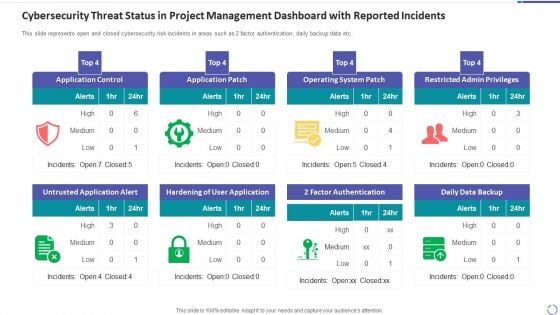
Cybersecurity Threat Status In Project Management Dashboard With Reported Incidents Introduction PDF
This slide represents open and closed cybersecurity risk incidents in areas such as 2 factor authentication, daily backup data etc. Showcasing this set of slides titled cybersecurity threat status in project management dashboard with reported incidents introduction pdf. The topics addressed in these templates are application control, application patch, operating system patch, restricted admin privileges, untrusted application alert. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
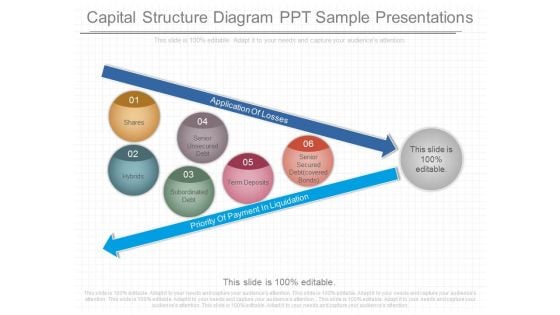
Capital Structure Diagram Ppt Sample Presentations
This is a capital structure diagram ppt sample presentations. This is a six stage process. The stages in this process are application of losses, shares, hybrids, senior unsecured debt, subordinated debt, term deposits, senior secured debt covered bonds, priority of payment in liquidation.

Fiber Optics Overview Advantages And Working Fibers IT
This slide gives an overview of optical fiber technology, including its working and benefits. The purpose of this slide is to showcase fiber optics, their pros, application areas, and the working process. The application areas include computer networking and broadcasting, internet and cable television, etc. Want to ace your presentation in front of a live audience Our Fiber Optics Overview Advantages And Working Fibers IT can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide gives an overview of optical fiber technology, including its working and benefits. The purpose of this slide is to showcase fiber optics, their pros, application areas, and the working process. The application areas include computer networking and broadcasting, internet and cable television, etc.

Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF
Presenting Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Information System Categorization, Security Control Selection, Security Control Implementation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
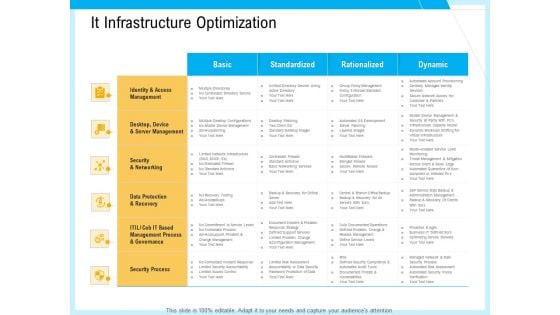
IT And Cloud Facilities Management It Infrastructure Optimization Ppt Model Slide PDF
Deliver an awe-inspiring pitch with this creative it and cloud facilities management it infrastructure optimization ppt model slide pdf bundle. Topics like standardized, rationalized, dynamic, identity and access management, security and networking, security process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
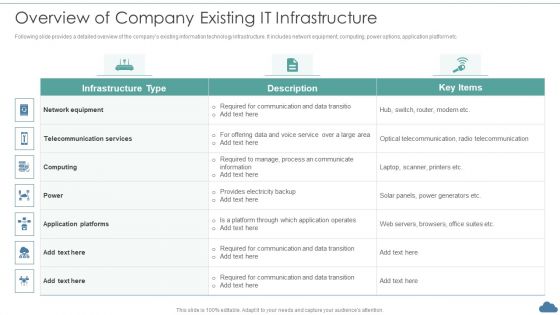
Cloud Optimization Infrastructure Model Overview Of Company Existing IT Infrastructure Topics PDF
Following slide provides a detailed overview of the companys existing information technology infrastructure. It includes network equipment, computing, power options, application platform etc.Deliver and pitch your topic in the best possible manner with this Cloud Optimization Infrastructure Model Overview Of Company Existing IT Infrastructure Topics PDF Use them to share invaluable insights on Telecommunication Services, Application Platforms, Required For Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

On Premises Data Center To Cloud Warm Recovery Background PDF
This slide describes the on premises data center to cloud warm recovery architecture and covers its elements such as application environment, building resources, and customer web requests. Deliver and pitch your topic in the best possible manner with this On Premises Data Center To Cloud Warm Recovery Background PDF. Use them to share invaluable insights on Application Environment, Build Resources, Network Endpoint and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Important Attributes Of Mobile Operating With Webview Ppt PowerPoint Presentation Inspiration Icon PDF
Persuade your audience using this important attributes of mobile operating with webview ppt powerpoint presentation inspiration icon pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including application planning, application backup, authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
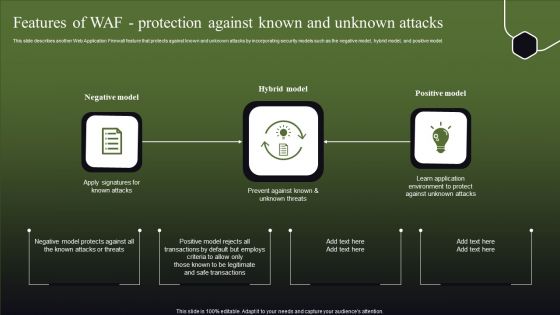
Features Of WAF Protection Against Known And Unknown Attacks Graphics PDF
This slide describes another Web Application Firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. This modern and well-arranged Features Of WAF Protection Against Known And Unknown Attacks Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
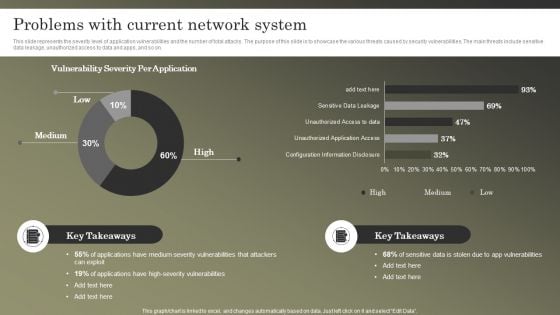
Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
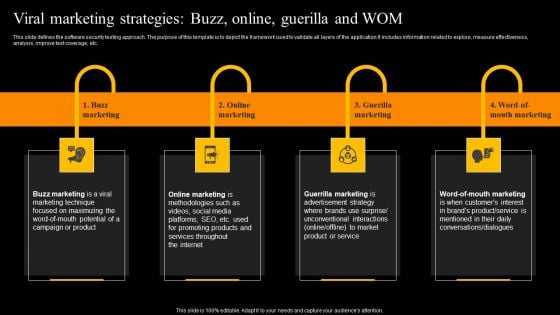
Viral Marketing Strategies Buzz Online Guerilla And WOM Diagrams PDF
This slide defines the software security testing approach. The purpose of this template is to depict the framework used to validate all layers of the application It includes information related to explore, measure effectiveness, analysis, improve test coverage, etc. Explore a selection of the finest Viral Marketing Strategies Buzz Online Guerilla And WOM Diagrams PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Viral Marketing Strategies Buzz Online Guerilla And WOM Diagrams PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add-ons, using a customized web application firewall etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF today and make your presentation stand out from the rest.
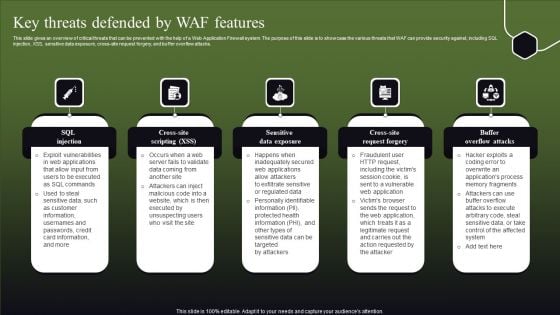
Key Threats Defended By WAF Features Ppt Pictures Elements PDF
This slide gives an overview of critical threats that can be prevented with the help of a Web Application Firewall system. The purpose of this slide is to showcase the various threats that WAF can provide security against, including SQL injection, XSS, sensitive data exposure, cross-site request forgery, and buffer overflow attacks. Explore a selection of the finest Key Threats Defended By WAF Features Ppt Pictures Elements PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Threats Defended By WAF Features Ppt Pictures Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
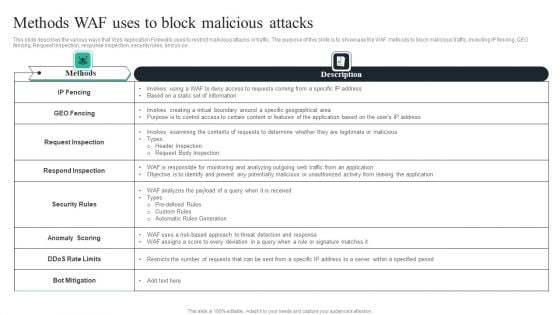
WAF Introduction Methods WAF Uses To Block Malicious Attacks Graphics PDF
This slide describes the various ways that Web Application Firewalls uses to restrict malicious attacks or traffic. The purpose of this slide is to showcase the WAF methods to block malicious traffic, including IP fencing, GEO fencing, Request Inspection, response inspection, security rules, and so on. Welcome to our selection of the WAF Introduction Methods WAF Uses To Block Malicious Attacks Graphics PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Data Safety Initiatives Overview Of New IT Policy Framework Pictures PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. This is a data safety initiatives overview of new it policy framework pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it policy framework, it security and usage policies, data policies, it security policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
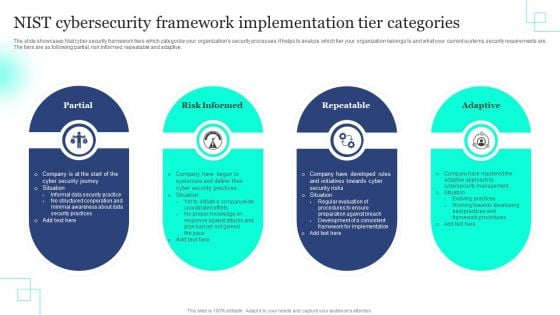
NIST Cybersecurity Framework Implementation Tier Categories Rules PDF
The slide showcases Nist cyber security framework tiers which categorize your organizations security processes, it helps to analyze which tier your organization belongs to and what your current systems security requirements are. The tiers are as following partial, risk informed, repeatable and adaptive. Persuade your audience using this NIST Cybersecurity Framework Implementation Tier Categories Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Partial, Risk Informed, Repeatable . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
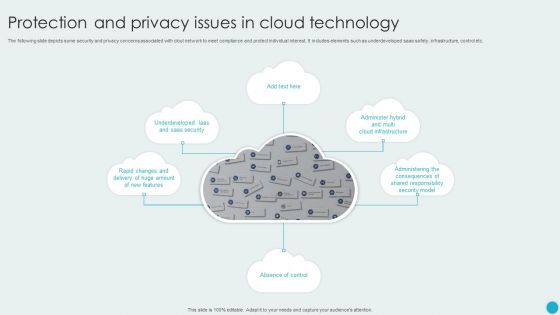
Protection And Privacy Issues In Cloud Technology Rules PDF
The following slide depicts some security and privacy concerns associated with clout network to meet compliance and protect individual interest. It includes elements such as underdeveloped saas safety, infrastructure, control etc. Persuade your audience using this Protection And Privacy Issues In Cloud Technology Rules PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Absence Of Control, Saas Security, Security Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
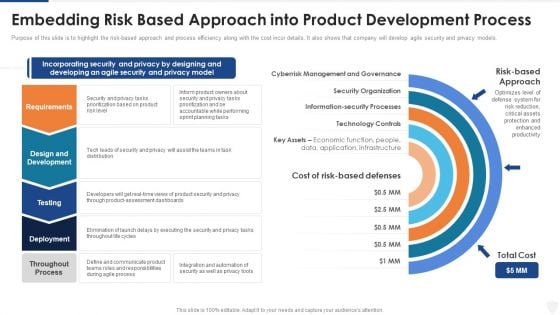
Embedding Risk Based Approach Into Product Development Process Ppt Model Files PDF
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Presenting embedding risk based approach into product development process ppt model files pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like technology controls, information security processes, security organization, economic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
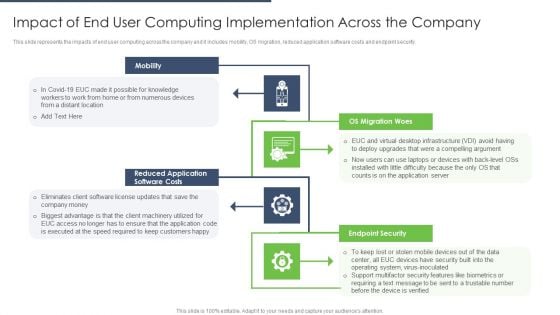
End User Computing Impact Of End User Computing Implementation Across The Company Download PDF
This slide represents the impacts of end user computing across the company and it includes mobility, OS migration, reduced application software costs and endpoint security.This is a End User Computing Impact Of End User Computing Implementation Across The Company Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Distant Location, Reduced Application, Eliminates Client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
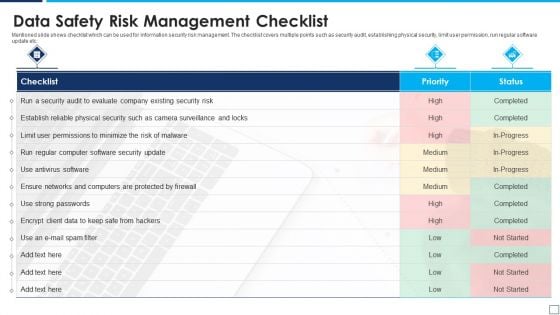
Data Safety Risk Management Checklist Information PDF
Mentioned slide shows checklist which can be used for information security risk management. The checklist covers multiple points such as security audit, establishing physical security, limit user permission, run regular software update etc. Presenting data safety risk management checklist information pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including data safety risk management checklist. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
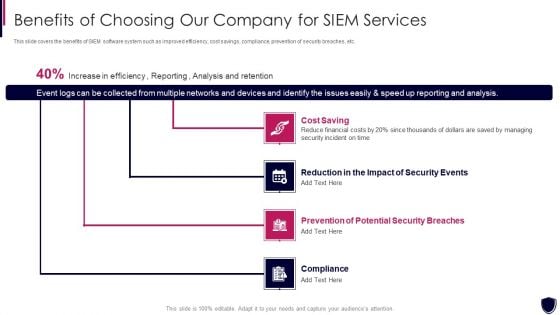
Enhancing Cyber Safety With Vulnerability Administration Benefits Of Choosing Our Company Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting enhancing cyber safety with vulnerability administration benefits of choosing our company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Influencer Marketing 4 Months Project Status Update Icon Slides PDF
This slide covers the four months project status update of software implementation project undertaken by the IT team. It includes various activities to be performed under IT help desk, web server, network and global security.Showcasing this set of slides titled Influencer Marketing 4 Months Project Status Update Icon Slides PDF. The topics addressed in these templates are Global Security, Network Speed, Security Plan . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SIEM Benefits Of Choosing Our Company For SIEM Services Ppt File Outfit PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting siem benefits of choosing our company for siem services ppt file outfit pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
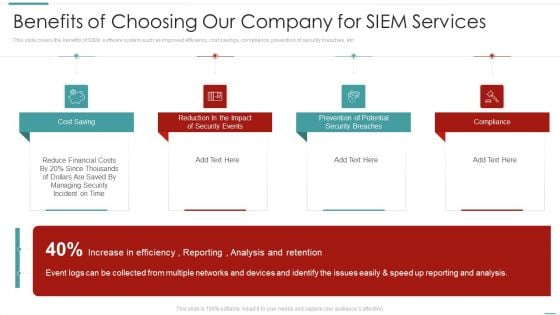
Risk Recognition Automation Benefits Of Choosing Our Company For Siem Services Ppt Gallery Design Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a risk recognition automation benefits of choosing our company for siem services ppt gallery design inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, prevention of potential security breaches, compliance, reduction in the impact of security events. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
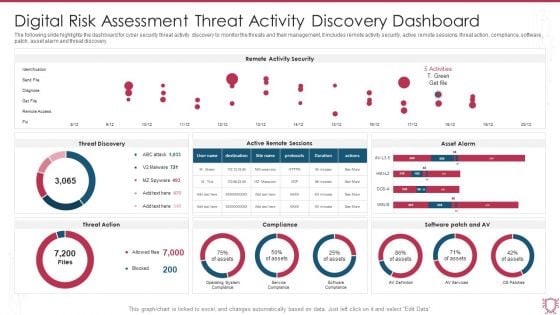
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
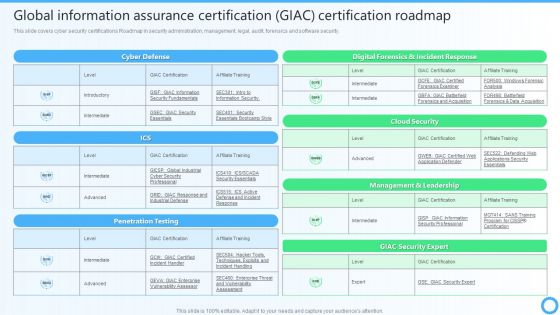
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
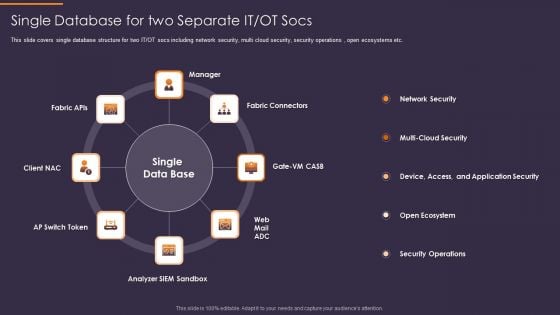
Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Fabric Connectors, Analyzer SIEM Sandbox, AP Switch Token, Client NAC, Fabric APIs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
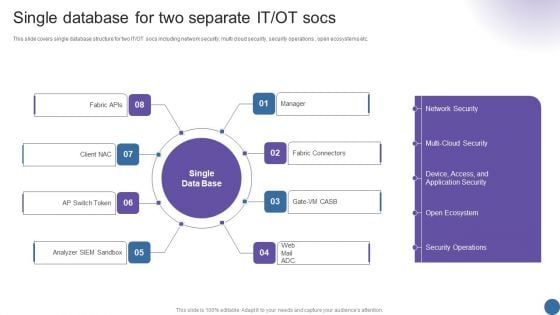
Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF
This slide covers single database structure for two IT OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Single Database, Two Separate, Fabric Connectors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
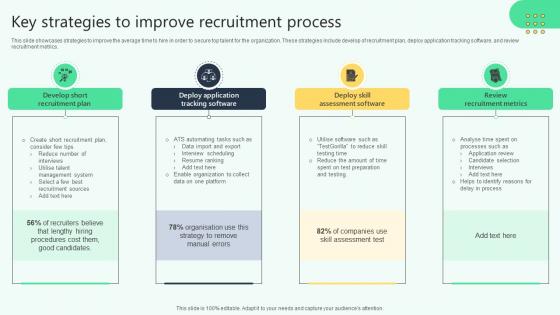
Key Strategies To Improve Recruitment Process Analysing Hr Data For Effective Decision Making
This slide showcases strategies to improve the average time to hire in order to secure top talent for the organization. These strategies include develop of recruitment plan, deploy application tracking software, and review recruitment metrics. Find a pre-designed and impeccable Key Strategies To Improve Recruitment Process Analysing Hr Data For Effective Decision Making. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases strategies to improve the average time to hire in order to secure top talent for the organization. These strategies include develop of recruitment plan, deploy application tracking software, and review recruitment metrics.
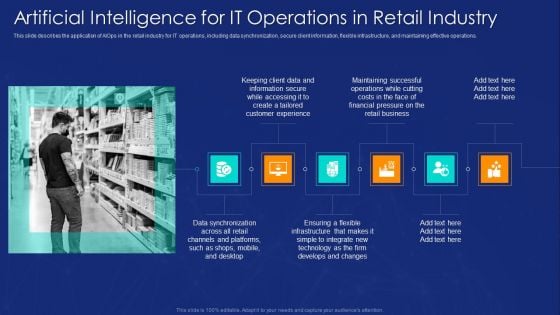
AIOPS Implementation Artificial Intelligence For IT Operations In Retail Industry Background PDF
This slide describes the application of AIOps in the retail industry for IT operations, including data synchronization, secure client information, flexible infrastructure, and maintaining effective operations. Deliver an awe inspiring pitch with this creative AIOPS Implementation Artificial Intelligence For IT Operations In Retail Industry Background PDF bundle. Topics like Customer Experience, Retail Business, New Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Technology Domain Layout Powerpoint Slide Ideas
This is a internet technology domain layout powerpoint slide ideas. This is a fourteen stage process. The stages in this process are product management, security, erp, crm, wcdma, it infrastructure, rdbms, system software, embedded technology, technical trainer, semiconductor, application software, web technology, mainframe.
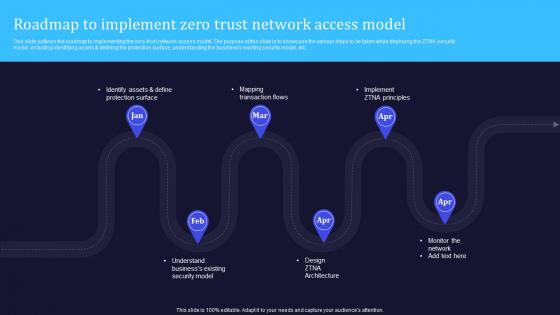
A20 Zero Trust Model Roadmap To Implement Zero Trust Network Access
This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the businesss existing security model, etc. Find a pre-designed and impeccable A20 Zero Trust Model Roadmap To Implement Zero Trust Network Access. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the businesss existing security model, etc.
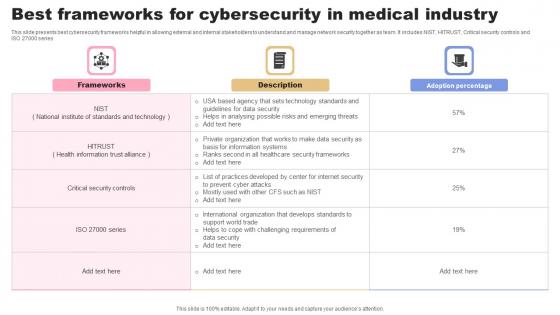
Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf
This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series Showcasing this set of slides titled Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf. The topics addressed in these templates are Frameworks, Description, Adoption Percentage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series
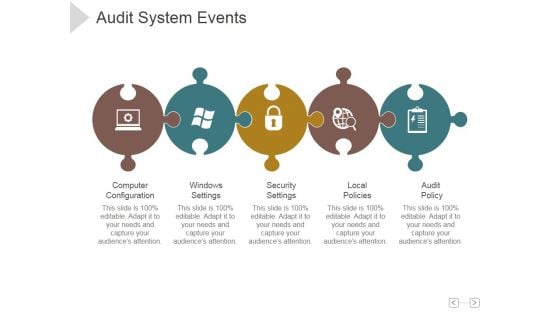
Audit System Events Ppt PowerPoint Presentation Model
This is a audit system events ppt powerpoint presentation model. This is a five stage process. The stages in this process are computer configuration, windows settings , security settings , local policies, audit policy.
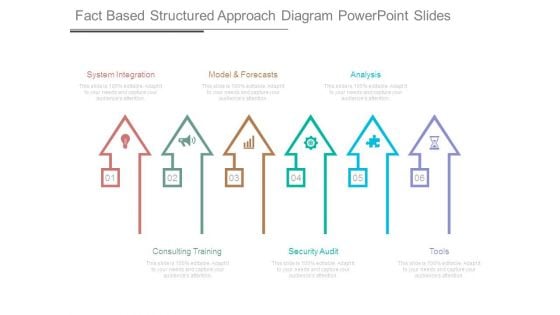
Fact Based Structured Approach Diagram Powerpoint Slides
This is a fact based structured approach diagram powerpoint slides. This is a six stage process. The stages in this process are system integration, model and forecasts, analysis, consulting training, security audit, tools.
Business Framework Entry Barrier 1 PowerPoint Presentation
This business framework PPT diagram has been designed with graphic of traffic cones and barrier. This PPT diagram contains the concept of security and construction. Use this PPT diagram for your road safety and traffic rules related presentations.

Methods Of Software Risk Assessment Ppt Powerpoint Guide
This is a methods of software risk assessment ppt powerpoint guide. This is a seven stage process. The stages in this process are risk management, risk assessment, risk identification, risk periodization, security requirements, external review, penetration testing.

Our Services Ppt PowerPoint Presentation Gallery Model
This is a our services ppt powerpoint presentation gallery model. This is a four stage process. The stages in this process are marketing and analytics, digital advertising, security maintenance, digital care package.
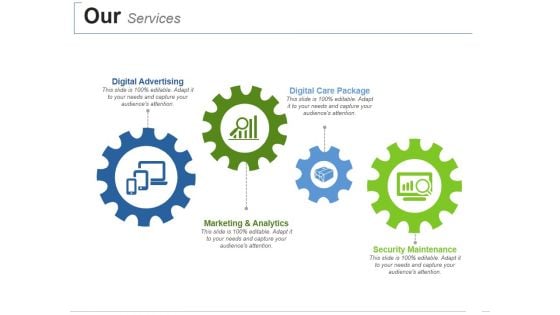
Our Services Ppt PowerPoint Presentation Model Grid
This is a our services ppt powerpoint presentation model grid. This is a four stage process. The stages in this process are digital advertising, digital care package, marketing and analytics , security maintenance.
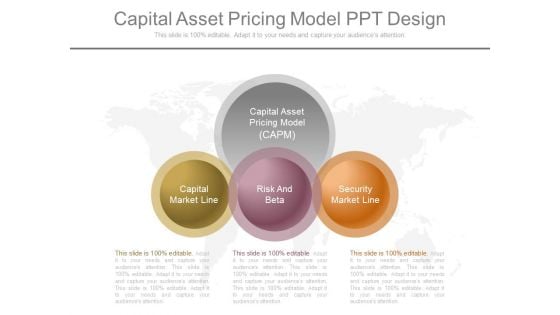
Capital Asset Pricing Model Ppt Design
This is a capital asset pricing model ppt design. This is a three stage process. The stages in this process are capital market line, risk and beta, security market line, capital asset pricing model.
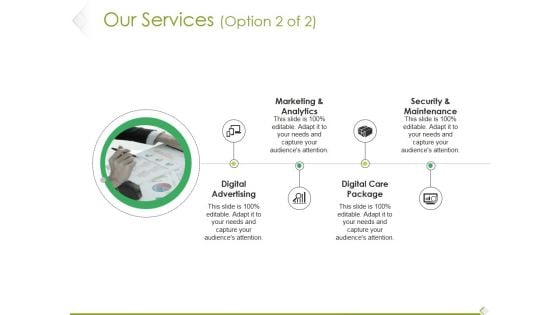
Our Services Template 2 Ppt PowerPoint Presentation Model Background Images
This is a our services template 2 ppt powerpoint presentation model background images. This is a four stage process. The stages in this process are digital advertising, digital care package, marketing and analytics, security and maintenance.

Our Services Template 1 Ppt PowerPoint Presentation Model Picture
This is a our services template 1 ppt powerpoint presentation model picture. This is a four stage process. The stages in this process are digital advertising, marketing and analytics, digital care package, security and maintenance.
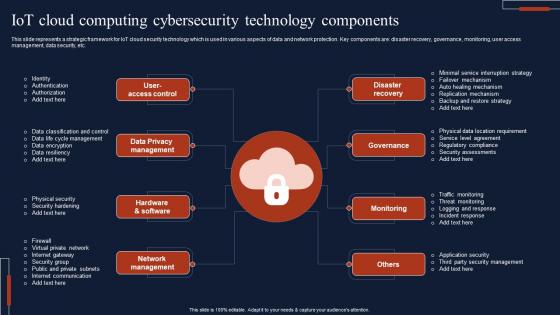
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc.
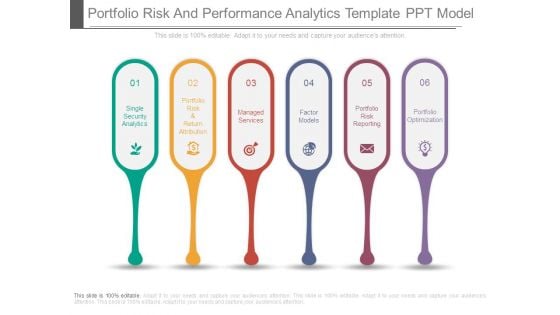
Portfolio Risk And Performance Analytics Template Ppt Model
This is a portfolio risk and performance analytics template ppt model. This is a six stage process. The stages in this process are single security analytics, portfolio risk and return attribution, managed services, factor models, portfolio risk reporting, portfolio optimization.


 Continue with Email
Continue with Email

 Home
Home


































