Application Security

Portable Home Safety Systems Company Profile Security Company Strategic Partnerships Structure PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation. Deliver and pitch your topic in the best possible manner with this Portable Home Safety Systems Company Profile Security Company Strategic Partnerships Structure PDF. Use them to share invaluable insights on Services, Partnership Type, Year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
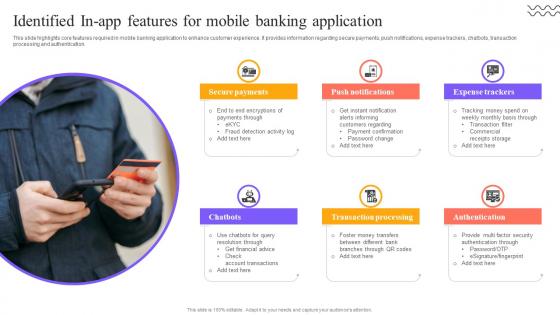
Digital Approach To Client Identified In App Features For Mobile Banking Application
This slide highlights core features required in mobile banking application to enhance customer experience. It provides information regarding secure payments, push notifications, expense trackers, chatbots, transaction processing and authentication. Are you searching for a Digital Approach To Client Identified In App Features For Mobile Banking Application that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Digital Approach To Client Identified In App Features For Mobile Banking Application from Slidegeeks today. This slide highlights core features required in mobile banking application to enhance customer experience. It provides information regarding secure payments, push notifications, expense trackers, chatbots, transaction processing and authentication.
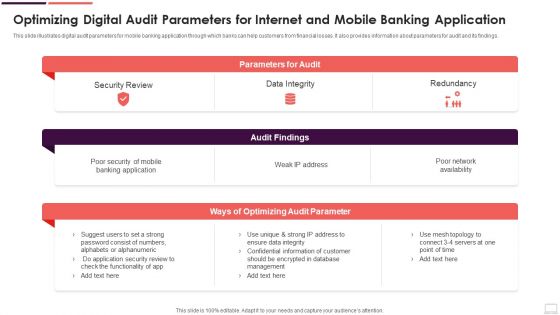
Optimizing Digital Audit Parameters For Internet And Mobile Banking Application Designs PDF
This slide illustrates digital audit parameters for mobile banking application through which banks can help customers from financial losses. It also provides information about parameters for audit and its findings. Pitch your topic with ease and precision using this Optimizing Digital Audit Parameters For Internet And Mobile Banking Application Designs PDF. This layout presents information on Security Review, Data Integrity, Redundancy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Security Controls To Be Addressed In The Program Ppt Professional Vector PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. This is a key security controls to be addressed in the program ppt professional vector pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like key security controls to be addressed in the program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
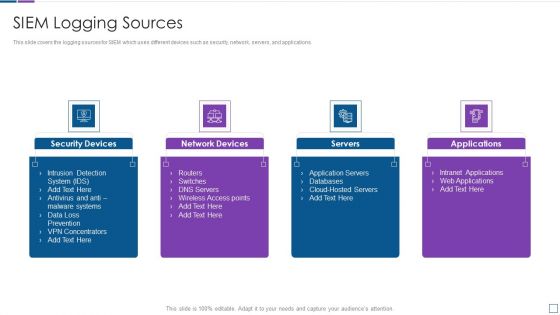
Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

API Management For Building Software Applications Present Application Programming Interface Issues Guidelines PDF
Presenting this set of slides with name api management for building software applications present application programming interface issues guidelines pdf. This is a four stage process. The stages in this process are technological complexity, security risks, high consumption time, expensive. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
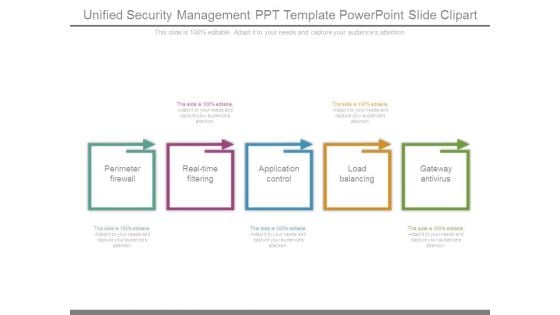
Unified Security Management Ppt Template Powerpoint Slide Clipart
This is a unified security management ppt template powerpoint slide clipart. This is a five stage process. The stages in this process are perimeter firewall, real time filtering, application control, load balancing, gateway antivirus.
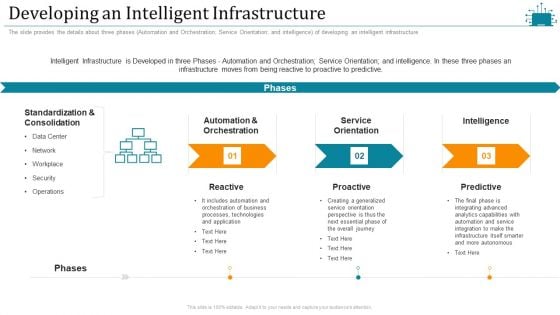
Cloud Intelligence Framework For Application Consumption Developing An Intelligent Infrastructure Diagrams PDF
The slide provides the details about three phases Automation and Orchestration Service Orientation and intelligence of developing an intelligent infrastructure. Presenting cloud intelligence framework for application consumption developing an intelligent infrastructure diagrams pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, business processes, technologies and application, service orientation, automation orchestration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
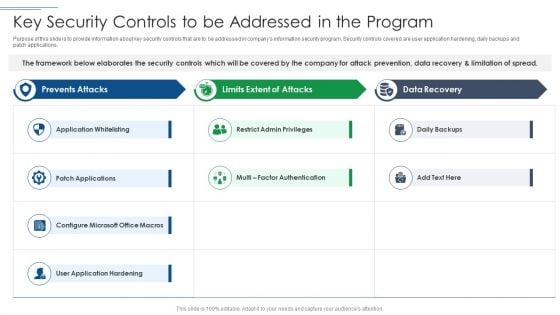
IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF. Use them to share invaluable insights on Application Whitelisting, Patch Applications, User Application Hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
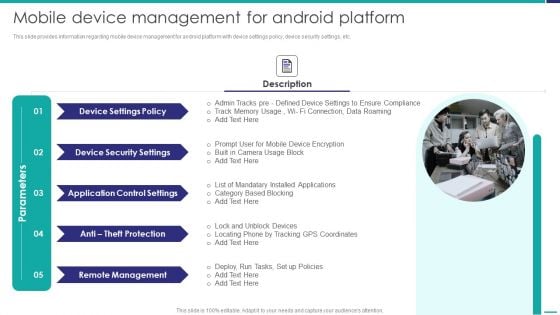
Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Presenting Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Device Security, Application Control, Remote Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
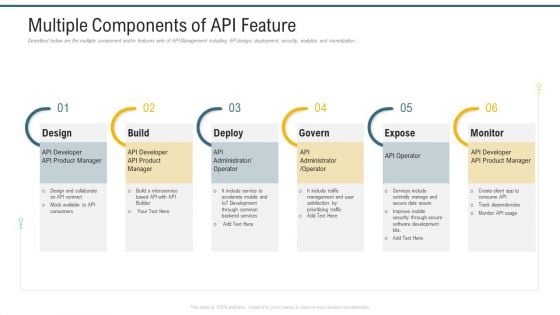
Application Programming Interface Marketplace Multiple Components Of API Feature Introduction PDF
Described below are the multiple component and or features sets of API Management including API design, deployment, security, analytics and monetization. Presenting application programming interface marketplace multiple components of api feature introduction pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like design, build, deploy, monitor. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Operating Designs PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard operating designs pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Unlocking Potential IoTs Application Emerging Trends And Future Applications Of IoT SS V
This slide presents the emerging trends and future applications of IoT. It incorporates edge computing in IoT, AI, and ML in IoT data analysis, IoT in smart cities, and Blockchain technology for security and privacy. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Unlocking Potential IoTs Application Emerging Trends And Future Applications Of IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Unlocking Potential IoTs Application Emerging Trends And Future Applications Of IoT SS V. This slide presents the emerging trends and future applications of IoT. It incorporates edge computing in IoT, AI, and ML in IoT data analysis, IoT in smart cities, and Blockchain technology for security and privacy.
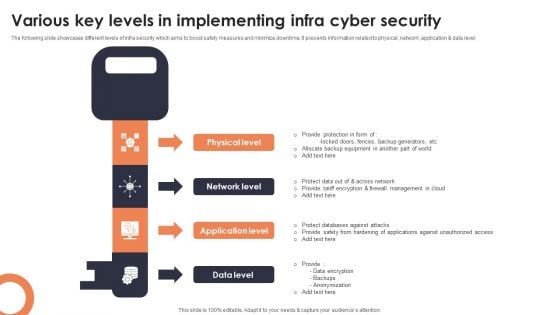
Various Key Levels In Implementing Infra Cyber Security Mockup PDF
The following slide showcases different levels of infra security which aims to boost safety measures and minimize downtime. It presents information related to physical, network, application and data level. Presenting Various Key Levels In Implementing Infra Cyber Security Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Physical Level, Network Level, Application Level. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
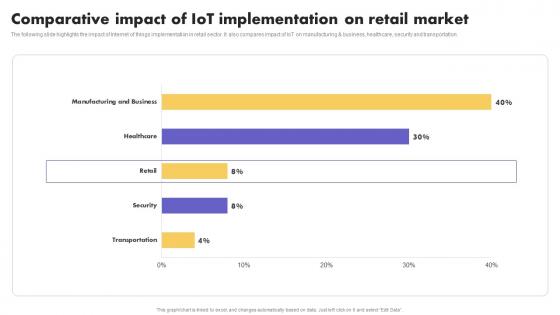
IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation. Create an editable IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation
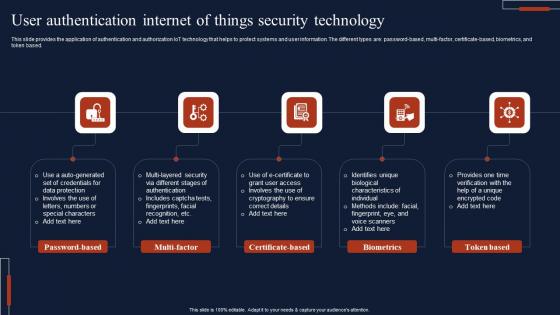
User Authentication Internet Of Things Security Technology Microsoft Pdf
This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based. Pitch your topic with ease and precision using this User Authentication Internet Of Things Security Technology Microsoft Pdf This layout presents information on Password Based, Multi Factor, Certificate Based It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based.
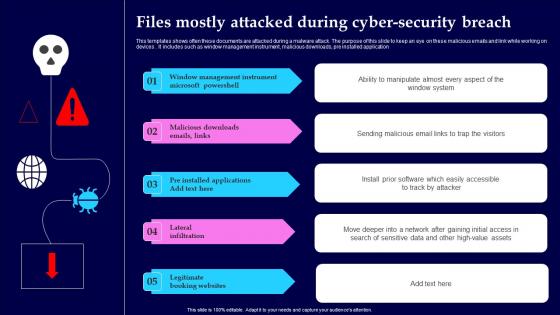
Files Mostly Attacked During Cyber Security Breach Structure Pdf
This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application Showcasing this set of slides titled Files Mostly Attacked During Cyber Security Breach Structure Pdf The topics addressed in these templates are Window Management, Instrument Microsoft, Lateral Infiltration All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application
Safety And Security App Mapping Icon Slides PDF
This slide showcases comparative analysis various tools used for application mapping to help organization identify best available option. It further includes details about price, free trail and characteristics. Showcasing this set of slides titled Safety And Security App Mapping Icon Slides PDF. The topics addressed in these templates are Safety And Security, App Mapping Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Key Security Considerations For 5G For Threat Handling Icons PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling Icons PDF. Use them to share invaluable insights on Denial Of Service, Information Interception, Application Plane Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
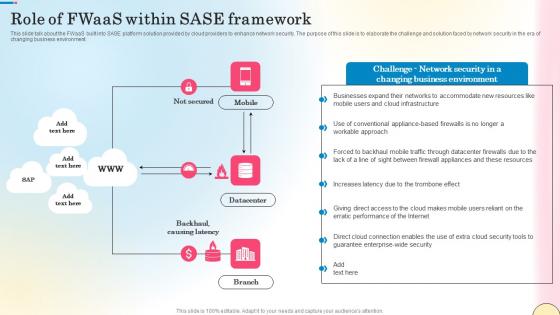
Role Of Fwaas Within Sase Framework Network Security Elements Pdf
This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment. Want to ace your presentation in front of a live audience Our Role Of Fwaas Within Sase Framework Network Security Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment.

WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF
This slide represents the steps to be considered by organizations to maximize the benefits of WAF. The purpose of this slide is to showcase the best practices businesses can consider for successful web application firewall implementation, such as support for app security goals, evaluation and testing, and resource listing. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
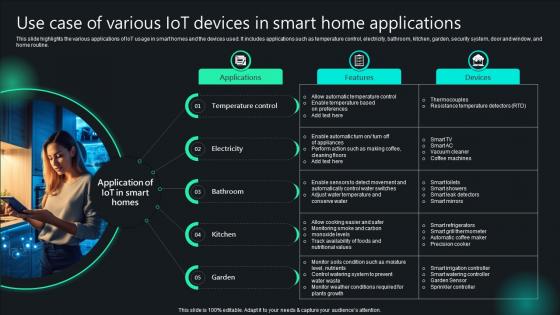
Unlocking Potential IoTs Application Use Case Of Various IoT Devices In Smart Home Applications IoT SS V
This slide highlights the various applications of IoT usage in smart homes and the devices used. It includes applications such as temperature control, electricity, bathroom, kitchen, garden, security system, door and window, and home routine. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Unlocking Potential IoTs Application Use Case Of Various IoT Devices In Smart Home Applications IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights the various applications of IoT usage in smart homes and the devices used. It includes applications such as temperature control, electricity, bathroom, kitchen, garden, security system, door and window, and home routine.
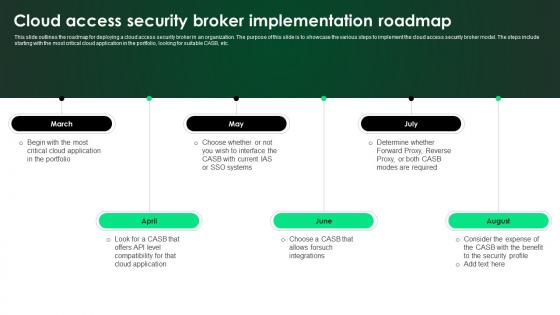
CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Welcome to our selection of the CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc.
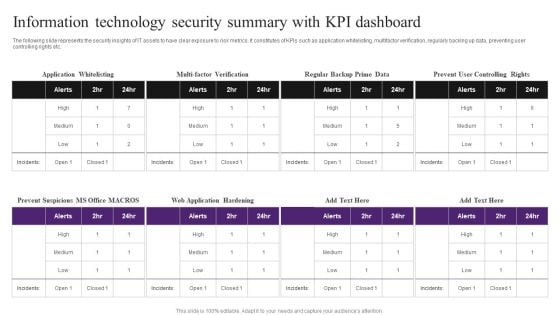
Information Technology Security Summary With KPI Dashboard Inspiration PDF
The following slide represents the security insights of IT assets to have clear exposure to risk metrics. It constitutes of KPIs such as application whitelisting, multifactor verification, regularly backing up data, preventing user controlling rights etc. Pitch your topic with ease and precision using this Information Technology Security Summary With KPI Dashboard Inspiration PDF. This layout presents information on Information Technology Security, Summary With KPI Dashboard. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Scan Principle For Smart Phone Security Model Clipart PDF
This slide shows SCAN framework for securing phone against possible threats to prevent loss of business data. It include components such as system, configuration, application and network, etc. Persuade your audience using this Scan Principle For Smart Phone Security Model Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including System, Configuration, App. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
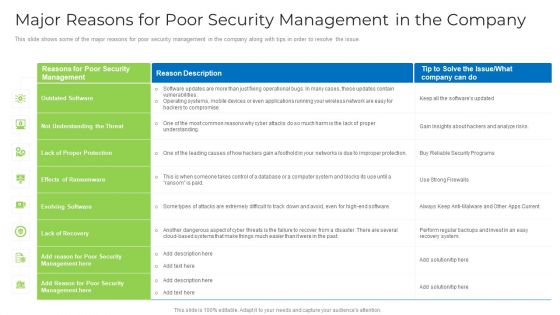
Major Reasons For Poor Security Management In The Company Download PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company download pdf bundle. Topics like applications, operating systems, network, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

SDN Security Architecture Infrastructure Layer And Apis Professional PDF
This slide represents the infrastructure layer and Application programming interfaces of SDN architecture. The layer contains the physical switches and other devices that help redirect the network traffic, and APIs are used to interact between the three layers of the SDN architecture. Slidegeeks has constructed SDN Security Architecture Infrastructure Layer And Apis Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Security Background PowerPoint Templates And PowerPoint Backgrounds 0911
Microsoft PowerPoint Template and Background with security online software as blue abstract art Carve out a name for yourself with our Security Background PowerPoint Templates And PowerPoint Backgrounds 0911. The audience will award you with accolades.

Security Background PowerPoint Themes And PowerPoint Slides 0911
Microsoft PowerPoint Theme and Slide with security online software as blue abstract art Exhibit global market dominance with our Security Background PowerPoint Themes And PowerPoint Slides 0911. They will make you look good.
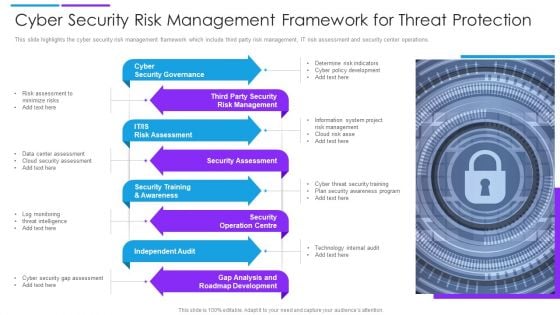
Cyber Security Risk Management Framework For Threat Protection Demonstration PDF
This slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting cyber security risk management framework for threat protection demonstration pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including cyber security governance, security assessment, independent audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

API Management For Building Software Applications Features Of Our Application Programming Interface Ideas PDF
Presenting this set of slides with name api management for building software applications features of our application programming interface ideas pdf. This is a six stage process. The stages in this process are high performance, load balancing, security, rate limiting, authentication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
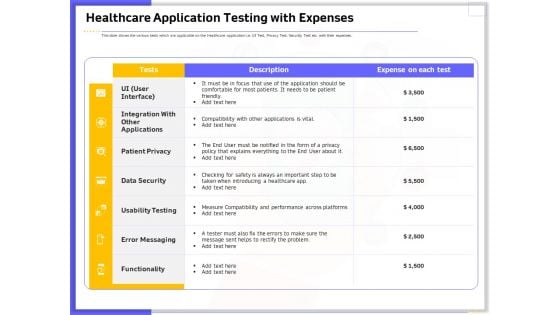
Developing Deploying Android Applications Healthcare Application Testing With Expenses Microsoft PDF
Presenting this set of slides with name developing deploying android applications healthcare application testing with expenses microsoft pdf. The topics discussed in these slides are data security, functionality, usability testing, patient privacy, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
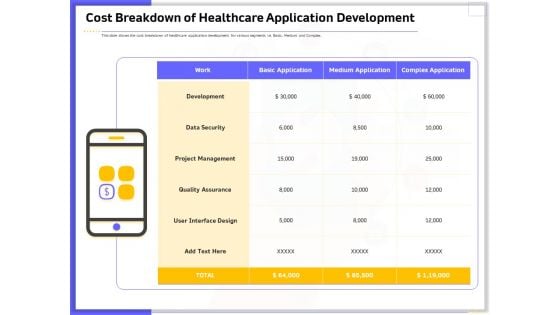
Developing Deploying Android Applications Cost Breakdown Of Healthcare Application Development Formats PDF
Presenting this set of slides with name developing deploying android applications cost breakdown of healthcare application development formats pdf. This is a one stage process. The stages in this process are development, data security, project management, quality assurance, interface design. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
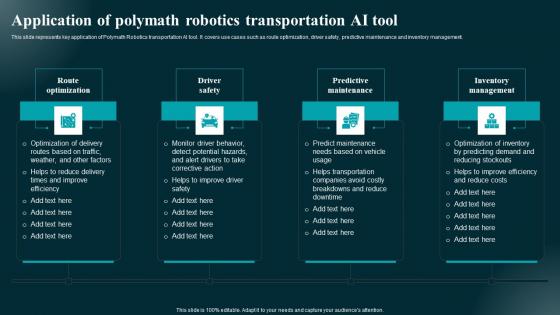
Application Of Polymath Robotics Transportation AI Tool Applications And Impact Demonstration Pdf
This slide represents key application of Polymath Robotics transportation AI tool. It covers use cases such as route optimization, driver safety, predictive maintenance and inventory management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Application Of Polymath Robotics Transportation AI Tool Applications And Impact Demonstration Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents key application of Polymath Robotics transportation AI tool. It covers use cases such as route optimization, driver safety, predictive maintenance and inventory management.

Application Development Top Benefits Of Ios App Development For Business Introduction PDF
This slide depicts the top benefits of iOS app development for business, including high security, upgraded user experience, increased return on investment, etc.Presenting Application Development Top Benefits Of Ios App Development For Business Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like High Security, Upgraded User Experience, Increased Return On Investment In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Stop Piracy Security PowerPoint Templates And PowerPoint Backgrounds 0111
Microsoft PowerPoint Template and Background with a chainlock and cd showing software piracy & copyright Many feel defeated by what has befallen them. Brush up their courage with our Stop Piracy Security PowerPoint Templates And PowerPoint Backgrounds 0111.
Email Security Vector Icon Ppt PowerPoint Presentation Model Example Topics
Presenting this set of slides with name email security vector icon ppt powerpoint presentation model example topics. This is a four stage process. The stages in this process are email security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Encrypted Business Data Cyber Security Assessment Icon Professional PDF
Presenting Encrypted Business Data Cyber Security Assessment Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
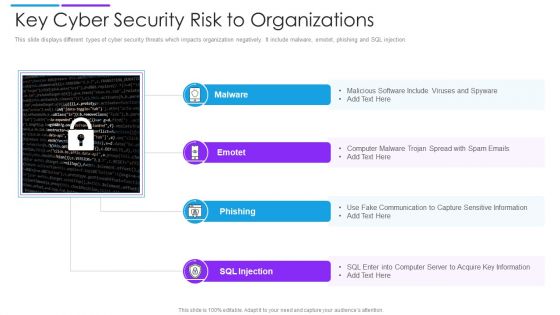
Key Cyber Security Risk To Organizations Structure PDF
This slide displays different types of cyber security threats which impacts organization negatively. It include malware, emotet, phishing and SQL injection. Presenting key cyber security risk to organizations structure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including malware, phishing, sql injection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Of Cloud Computing Ppt PowerPoint Presentation Inspiration Microsoft
This is a security of cloud computing ppt powerpoint presentation inspiration microsoft. This is a four stage process. The stages in this process are computer software, operating system, open source.
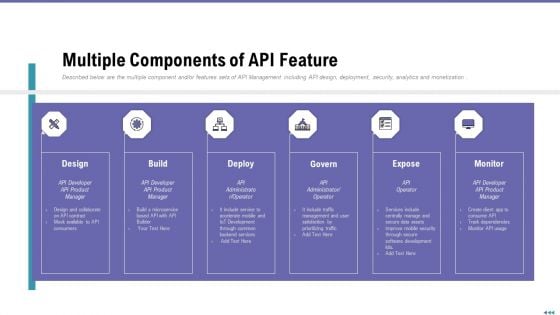
Market Viewpoint Application Programming Interface Governance Multiple Components Of API Feature Topics PDF
Described below are the multiple component and or features sets of API Management including API design, deployment, security, analytics and monetization. This is a market viewpoint application programming interface governance multiple components of api feature topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like design, build, deploy, govern, expose. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
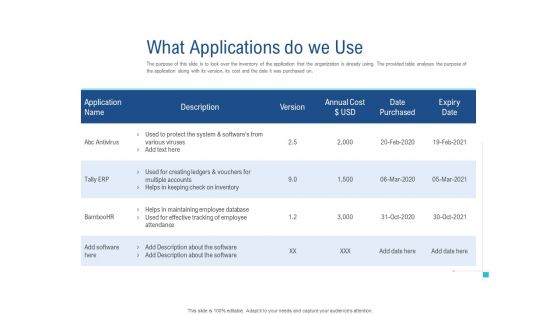
Enhance Enterprise Application Performance What Applications Do We Use Clipart PDF
Deliver an awe-inspiring pitch with this creative enhance enterprise application performance what applications do we use clipart pdf bundle. Topics like annual cost, protect system, tally ERP, effective tracking, application can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

House With Key Security PowerPoint Templates And PowerPoint Themes 1112
House With Key Security PowerPoint Templates And PowerPoint Themes 1112-Develop competitive advantage with our above template which contains a diagram of greenhouse connected with keys. This image represents the concept of security. It portrays the concept of building, chain, development, investment, mortgage, residential etc. Our PPT images are so ideally designed that it reveals the very basis of our PPT template are an effective tool to make your clients understand. The structure of our templates allows you to effectively highlight the key issues concerning the growth of your business.-House With Key Security PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-House with key, Security, Design, Business, Abstract, Metaphor The audience will always evince interest. Our House With Key Security PowerPoint Templates And PowerPoint Themes 1112 will make them apply their minds.
Computer Enhanced Security System Ppt PowerPoint Presentation Show Structure
This is a computer enhanced security system ppt powerpoint presentation show structure. This is a three stage process. The stages in this process are access rights, access management, business.

Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012
Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012-The euro is the currency used by the Institutions of the European Union and is the official currency of the Eurozone. This Template shows the currency Euro under the Umbrella which signifies the increasing rate of Euro from 2010 to 2012. Stable ideas are the building blocks of a successful structure. Lay down the fundamentals to build upon. Take it up to a higher level with your thoughts. -Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Currency protected by umbrella, security, business, money, shapes, metaphor Start accelerating revenue growth with our Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012. They will make you look good.

Grid Computing Applications Application Of Grid Computing In Life Science Ideas PDF
This slide represents the application of grid computing in life science for efficient access, collection, and critical information mining. Grid computing is adopted by various life science disciplines such as computational biology, bioinformatics, genomics, neurology, and so on. Boost your pitch with our creative Grid Computing Applications Application Of Grid Computing In Life Science Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
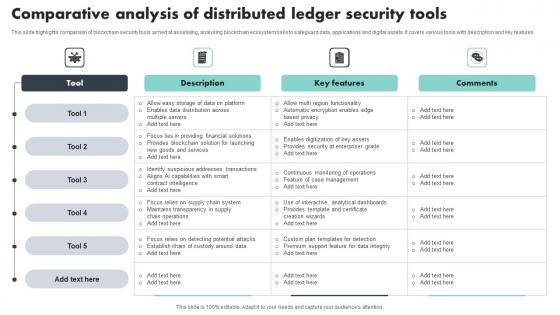
Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf
This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features Showcasing this set of slides titled Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf The topics addressed in these templates are Key Features, Comparative Analysis, Security Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features
System Security Vector Icon Ppt PowerPoint Presentation Model Templates
Presenting this set of slides with name system security vector icon ppt powerpoint presentation model templates. This is a four stage process. The stages in this process are system security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Context Diagram 3d Man With Chain Security PowerPoint Slides
We present our business context diagram 3d man with chain security PowerPoint Slides.Download our Security PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will effectively help you save your valuable time. They are readymade to fit into any presentation structure. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Use our Process and Flows PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time.Use these PowerPoint slides for presentations relating to 3d, Business, Chain, Connect, Connection, Heavy, Industrial, Industry, Isolated, Link, Linked, Man, Metal, Power, Powerful, Protection, Secure, Steel, Strength, Support, Symbol, Teamwork, Weak, White. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. The feedback we get is that our Industry PowerPoint templates and PPT Slides are designed to make your presentations professional. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Connection PowerPoint templates and PPT Slides are designed by professionals PowerPoint presentation experts tell us our business context diagram 3d man with chain security PowerPoint Slides look good visually. You can be sure our Industry PowerPoint templates and PPT Slides will make you look like a winner. You've found a treasure for presentations. Get goingwith our Business Context Diagram 3d Man With Chain Security PowerPoint Slides. You'll deliver your best presentation yet.

Framework Administration Interdependence Resiliency And Security Ppt Ideas PDF
Presenting framework administration interdependence resiliency and security ppt ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like lifecycle adaptive components of resilience framework, infrastructure resilience wheel. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
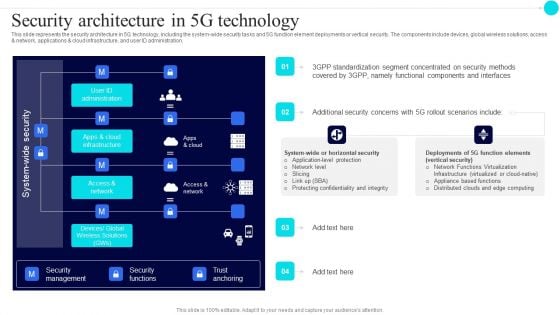
Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
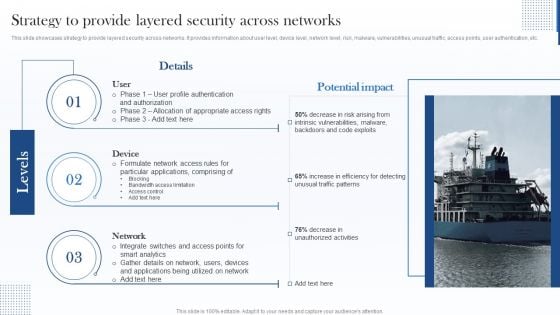
Strategy To Provide Layered Security Across Networks Microsoft PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver an awe inspiring pitch with this creative Strategy To Provide Layered Security Across Networks Microsoft PDF bundle. Topics like Device, Network, Applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
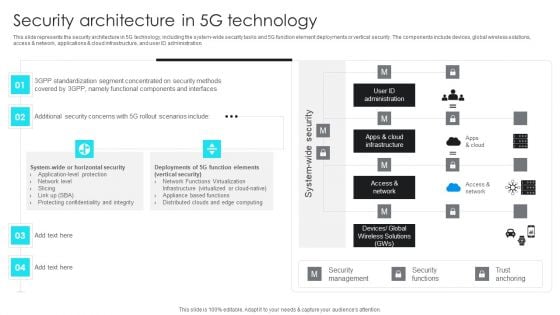
5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
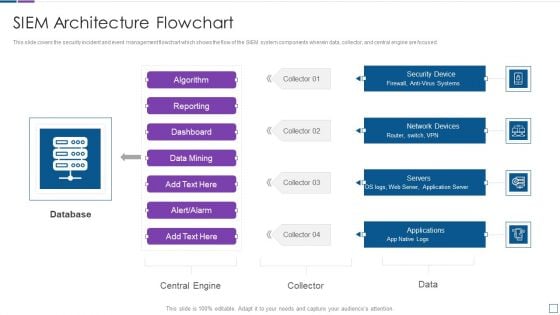
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
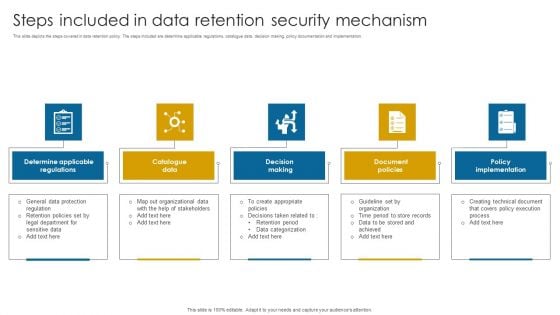
Steps Included In Data Retention Security Mechanism Introduction PDF
This slide depicts the steps covered in data retention policy. The steps included are determine applicable regulations, catalogue data, decision making, policy documentation and implementation.Persuade your audience using this Steps Included In Data Retention Security Mechanism Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Catalogue Data, Decision Making, Document Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Application Patient Satisfaction Tactics Enhance Clinical Results Strategies To Decrease Wait Brochure PDF
This slide shows the strategies that can be used by the medical facility institution in order to decrease the patient waiting time such as avoid overbooking, speed up patient intake process, use a mobile queue system, use secure messaging offer multiple scheduling options etc. Presenting application patient satisfaction tactics enhance clinical results strategies to decrease wait brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like avoid overbooking, use secure messaging, conduct a survey, scheduling options. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Protection And Information Security Policy And Procedure Guidelines PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Protection And Information Security Policy And Procedure Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Protection And Information Security Policy And Procedure Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Key Aspects Of 5G Network Security Topics Pdf
This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications. Pitch your topic with ease and precision using this Key Aspects Of 5G Network Security Topics Pdf. This layout presents information on Security Domains, Description, Importance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications.
Web Acceleration Security Software Shopping Carts Ppt Example
This is a web acceleration security software shopping carts ppt example. This is a eight stage process. The stages in this process are web acceleration, security software, shopping carts, data services, portals and intranets, domain name services, hosted application, cloud computing.

4 Steps For Building Internet Security Strategy Clipart Pdf
This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.Showcasing this set of slides titled 4 Steps For Building Internet Security Strategy Clipart Pdf The topics addressed in these templates are Cyber Security Maturity, Cyber Security Program, Document Cybersecurity Strategy All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.


 Continue with Email
Continue with Email

 Home
Home


































