Architect
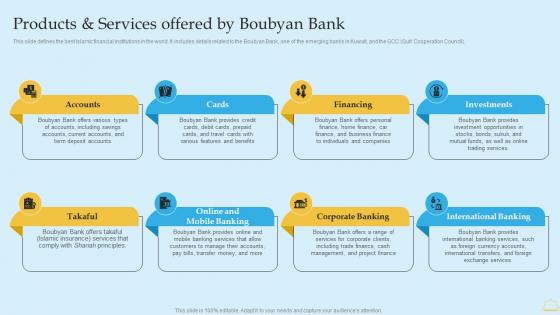
In Depth Analysis Of Islamic Banking Products And Services Offered By Boubyan Bank Rules PDF
This slide defines the best Islamic financial institutions in the world. It includes details related to the Boubyan Bank, one of the emerging banks in Kuwait, and the GCC Gulf Cooperation Council. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than In Depth Analysis Of Islamic Banking Products And Services Offered By Boubyan Bank Rules PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab In Depth Analysis Of Islamic Banking Products And Services Offered By Boubyan Bank Rules PDF today and make your presentation stand out from the rest. This slide defines the best Islamic financial institutions in the world. It includes details related to the Boubyan Bank, one of the emerging banks in Kuwait, and the GCC Gulf Cooperation Council.

Client Testimonials Investor Funding Pitch Deck For Pinterests Expansion Diagrams Pdf
This slide caters to the details related to the clients feedback based on their experiences. It consists of information about the image-sharing and social media services created to enable the saving and discovery of information on the internet using images, animated GIFs, and videos. Create an editable Client Testimonials Investor Funding Pitch Deck For Pinterests Expansion Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Client Testimonials Investor Funding Pitch Deck For Pinterests Expansion Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide caters to the details related to the clients feedback based on their experiences. It consists of information about the image-sharing and social media services created to enable the saving and discovery of information on the internet using images, animated GIFs, and videos.

Funding History Investor Funding Pitch Deck For Pinterests Expansion Portrait Pdf
This slide caters to the details related to the funding round announced by the company offering a visual bookmarking tool for saving and discovering creative ideas. It consists of information about IPO initial public offering, venture rounds, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Funding History Investor Funding Pitch Deck For Pinterests Expansion Portrait Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Funding History Investor Funding Pitch Deck For Pinterests Expansion Portrait Pdf today and make your presentation stand out from the rest. This slide caters to the details related to the funding round announced by the company offering a visual bookmarking tool for saving and discovering creative ideas. It consists of information about IPO initial public offering, venture rounds, etc.

Value Proposition Investor Funding Pitch Deck For Pinterests Expansion Infographics Pdf
This slide caters to the USP Unique Selling Proposition of the company offering image-sharing and social media services created to enable the saving and discovery of information on the internet using images, animated GIFs, and videos. Explore a selection of the finest Value Proposition Investor Funding Pitch Deck For Pinterests Expansion Infographics Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Value Proposition Investor Funding Pitch Deck For Pinterests Expansion Infographics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide caters to the USP Unique Selling Proposition of the company offering image-sharing and social media services created to enable the saving and discovery of information on the internet using images, animated GIFs, and videos.

Strategies To Build Meaningful Business Skills Training For Managers To Improve Team Template PDF
The slide showcases skill training requirements for managers in organizations that results in instilling efficient team working . it contains point such as coaching skills enhancement , people management skills , personal resilience , cross cultural training etc. Along with description, format opted, batch. Create an editable Strategies To Build Meaningful Business Skills Training For Managers To Improve Team Template PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Strategies To Build Meaningful Business Skills Training For Managers To Improve Team Template PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The slide showcases skill training requirements for managers in organizations that results in instilling efficient team working . it contains point such as coaching skills enhancement , people management skills , personal resilience , cross cultural training etc. Along with description, format opted, batch.
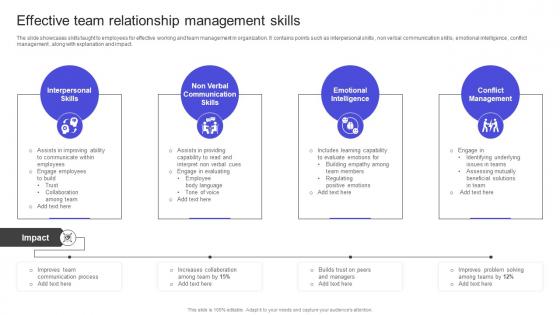
Strategies To Build Meaningful Effective Team Relationship Management Skills Template PDF
The slide showcases skills taught to employees for effective working and team management in organization. It contains points such as interpersonal skills , non verbal communication skills , emotional intelligence , conflict management , along with explanation and impact. Get a simple yet stunning designed Strategies To Build Meaningful Effective Team Relationship Management Skills Template PDF It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Strategies To Build Meaningful Effective Team Relationship Management Skills Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide showcases skills taught to employees for effective working and team management in organization. It contains points such as interpersonal skills , non verbal communication skills , emotional intelligence , conflict management , along with explanation and impact.
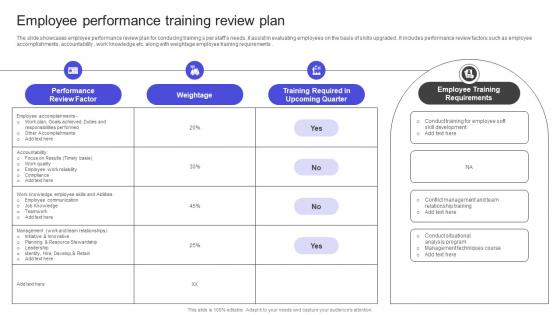
Strategies To Build Meaningful Employee Performance Training Review Plan Portrait PDF
The slide showcases employee performance review plan for conducing training s per staffs needs, it assist in evaluating employees on the basis of skills upgraded . It includes performance review factors such as employee accomplishments, accountability , work knowledge etc. along with weightage employee training requirements . Slidegeeks is here to make your presentations a breeze with Strategies To Build Meaningful Employee Performance Training Review Plan Portrait PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide showcases employee performance review plan for conducing training s per staffs needs, it assist in evaluating employees on the basis of skills upgraded . It includes performance review factors such as employee accomplishments, accountability , work knowledge etc. along with weightage employee training requirements .
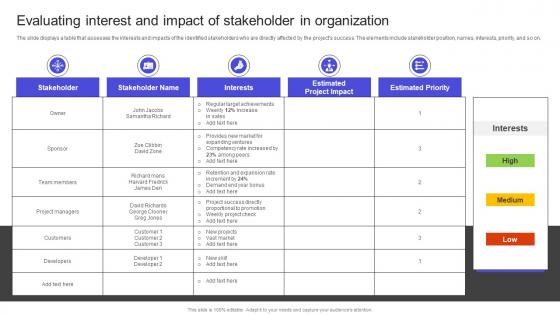
Strategies To Build Meaningful Evaluating Interest And Impact Of Stakeholder In Clipart PDF
The slide displays a table that assesses the interests and impacts of the identified stakeholders who are directly affected by the projects success. The elements include stakeholder position, names, interests, priority, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Strategies To Build Meaningful Evaluating Interest And Impact Of Stakeholder In Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Strategies To Build Meaningful Evaluating Interest And Impact Of Stakeholder In Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The slide displays a table that assesses the interests and impacts of the identified stakeholders who are directly affected by the projects success. The elements include stakeholder position, names, interests, priority, and so on.
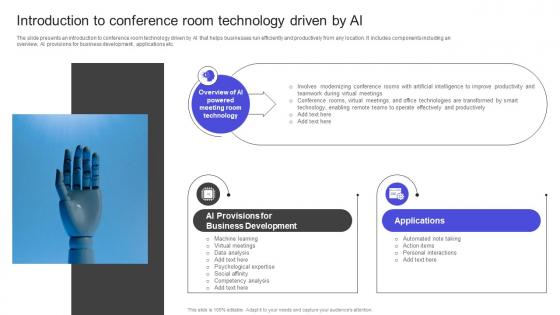
Strategies To Build Meaningful Introduction To Conference Room Technology Driven By Ai Pictures PDF
The slide presents an introduction to conference room technology driven by AI that helps businesses run efficiently and productively from any location. It includes components including an overview, AI provisions for business development , applications etc. This Strategies To Build Meaningful Introduction To Conference Room Technology Driven By Ai Pictures PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Strategies To Build Meaningful Introduction To Conference Room Technology Driven By Ai Pictures PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide presents an introduction to conference room technology driven by AI that helps businesses run efficiently and productively from any location. It includes components including an overview, AI provisions for business development , applications etc.
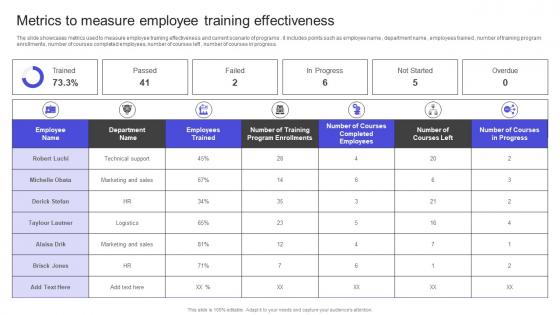
Strategies To Build Meaningful Metrics To Measure Employee Training Effectiveness Sample PDF
The slide showcases metrics used to measure employee training effectiveness and current scenario of programs . it includes points such as employee name , department name , employees trained , number of training program enrollments , number of courses completed employees, number of courses left , number of courses in progress. Explore a selection of the finest Strategies To Build Meaningful Metrics To Measure Employee Training Effectiveness Sample PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Strategies To Build Meaningful Metrics To Measure Employee Training Effectiveness Sample PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The slide showcases metrics used to measure employee training effectiveness and current scenario of programs . it includes points such as employee name , department name , employees trained , number of training program enrollments , number of courses completed employees, number of courses left , number of courses in progress.

Strategies To Build Meaningful Positive Impact Of Rewards And Recognition Framework Download PDF
The slide presents impact initiated on employees and work efficiency after implying rewards and recognition programs in organizations. It contains elements such as pay and reward , benefits , learning and development , work environment along with overall impact . This Strategies To Build Meaningful Positive Impact Of Rewards And Recognition Framework Download PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The slide presents impact initiated on employees and work efficiency after implying rewards and recognition programs in organizations. It contains elements such as pay and reward , benefits , learning and development , work environment along with overall impact .
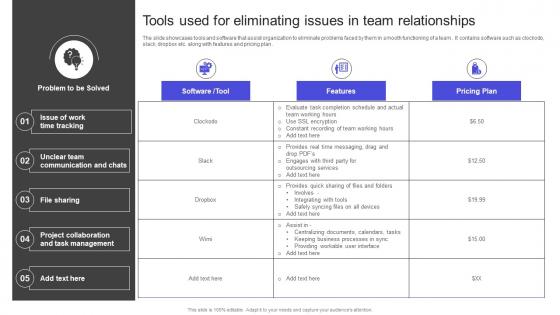
Strategies To Build Meaningful Tools Used For Eliminating Issues In Team Relationships Introduction PDF
The slide showcases tools and software that assist organization to eliminate problems faced by them in smooth functioning of a team . It contains software such as clockodo, slack, dropbox etc. along with features and pricing plan . Get a simple yet stunning designed Strategies To Build Meaningful Tools Used For Eliminating Issues In Team Relationships Introduction PDF It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Strategies To Build Meaningful Tools Used For Eliminating Issues In Team Relationships Introduction PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide showcases tools and software that assist organization to eliminate problems faced by them in smooth functioning of a team . It contains software such as clockodo, slack, dropbox etc. along with features and pricing plan .
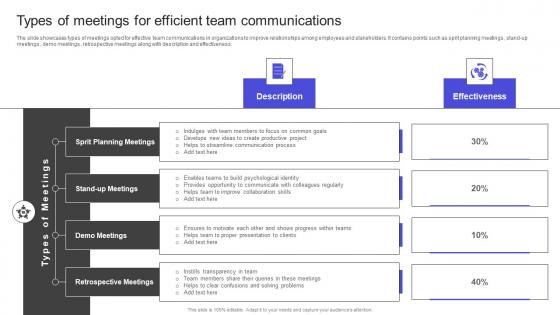
Strategies To Build Meaningful Types Of Meetings For Efficient Team Communications Graphics PDF
The slide showcases types of meetings opted for effective team communications in organizations to improve relationships among employees and stakeholders. It contains points such as sprit planning meetings , stand-up meetings , demo meetings , retrospective meetings along with description and effectiveness. Slidegeeks is here to make your presentations a breeze with Strategies To Build Meaningful Types Of Meetings For Efficient Team Communications Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide showcases types of meetings opted for effective team communications in organizations to improve relationships among employees and stakeholders. It contains points such as sprit planning meetings , stand-up meetings , demo meetings , retrospective meetings along with description and effectiveness.
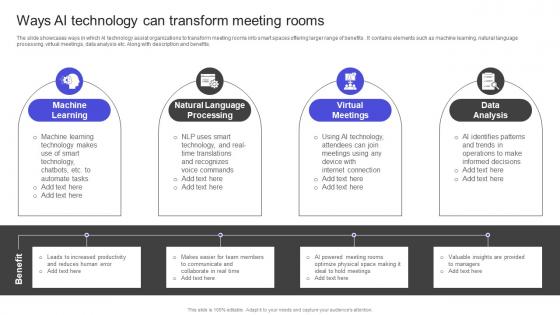
Strategies To Build Meaningful Ways Ai Technology Can Transform Meeting Rooms Summary PDF
The slide showcases ways in which AI technology assist organizations to transform meeting rooms into smart spaces offering larger range of benefits . It contains elements such as machine learning, natural language processing, virtual meetings, data analysis etc. Along with description and benefits. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Strategies To Build Meaningful Ways Ai Technology Can Transform Meeting Rooms Summary PDF With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Strategies To Build Meaningful Ways Ai Technology Can Transform Meeting Rooms Summary PDF today and make your presentation stand out from the rest The slide showcases ways in which AI technology assist organizations to transform meeting rooms into smart spaces offering larger range of benefits . It contains elements such as machine learning, natural language processing, virtual meetings, data analysis etc. Along with description and benefits.
Strategies To Build Meaningful Dashboard And Kpi For Evaluating Overall Employee Icons Pdf
The slide showcases dashboard and KPI evaluating employees overall performance and how employee working is going on in an organization . It contains KPIs such as employee absenteeism , employee overtime hours, employee training costs, overall employee effectiveness . Create an editable Strategies To Build Meaningful Dashboard And Kpi For Evaluating Overall Employee Icons Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Strategies To Build Meaningful Dashboard And Kpi For Evaluating Overall Employee Icons Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The slide showcases dashboard and KPI evaluating employees overall performance and how employee working is going on in an organization . It contains KPIs such as employee absenteeism , employee overtime hours, employee training costs, overall employee effectiveness .
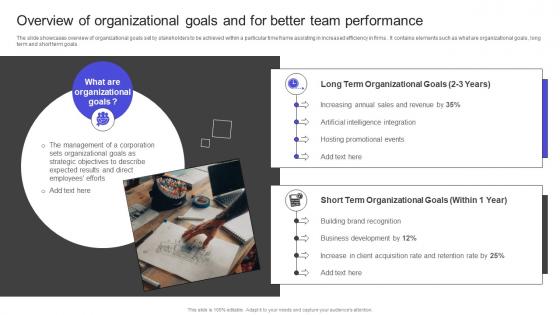
Strategies To Build Meaningful Overview Of Organizational Goals And For Better Team Guidelines Pdf
The slide showcases overview of organizational goals set by stakeholders to be achieved within a particular time frame assisting in increased efficiency in firms . It contains elements such as what are organizational goals , long term and short term goals . Get a simple yet stunning designed Strategies To Build Meaningful Overview Of Organizational Goals And For Better Team Guidelines Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Strategies To Build Meaningful Overview Of Organizational Goals And For Better Team Guidelines Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide showcases overview of organizational goals set by stakeholders to be achieved within a particular time frame assisting in increased efficiency in firms . It contains elements such as what are organizational goals , long term and short term goals .
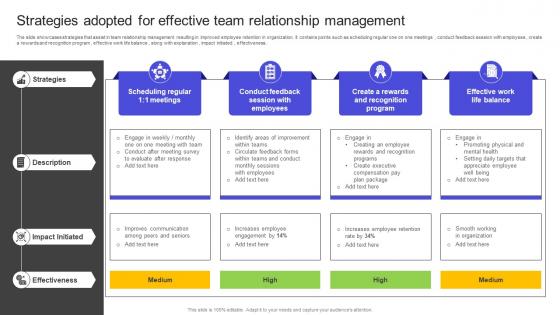
Strategies To Build Meaningful Strategies Adopted For Effective Team Relationship Management Pictures Pdf
The slide showcases strategies that assist in team relationship management resulting in improved employee retention in organization. It contains points such as scheduling regular one on one meetings , conduct feedback session with employees , create a rewards and recognition program , effective work life balance , along with explanation , impact initiated , effectiveness. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Strategies To Build Meaningful Strategies Adopted For Effective Team Relationship Management Pictures Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Strategies To Build Meaningful Strategies Adopted For Effective Team Relationship Management Pictures Pdf today and make your presentation stand out from the rest The slide showcases strategies that assist in team relationship management resulting in improved employee retention in organization. It contains points such as scheduling regular one on one meetings , conduct feedback session with employees , create a rewards and recognition program , effective work life balance , along with explanation , impact initiated , effectiveness.
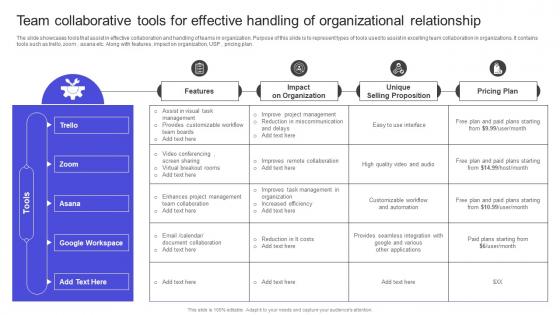
Strategies To Build Meaningful Team Collaborative Tools For Effective Handling Structure Pdf
The slide showcases tools that assist in effective collaboration and handling of teams in organization. Purpose of this slide is to represent types of tools used to assist in excelling team collaboration in organizations. It contains tools such as trello, zoom , asana etc. Along with features, impact on organization, USP , pricing plan . If you are looking for a format to display your unique thoughts, then the professionally designed Strategies To Build Meaningful Team Collaborative Tools For Effective Handling Structure Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Strategies To Build Meaningful Team Collaborative Tools For Effective Handling Structure Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The slide showcases tools that assist in effective collaboration and handling of teams in organization. Purpose of this slide is to represent types of tools used to assist in excelling team collaboration in organizations. It contains tools such as trello, zoom , asana etc. Along with features, impact on organization, USP , pricing plan .
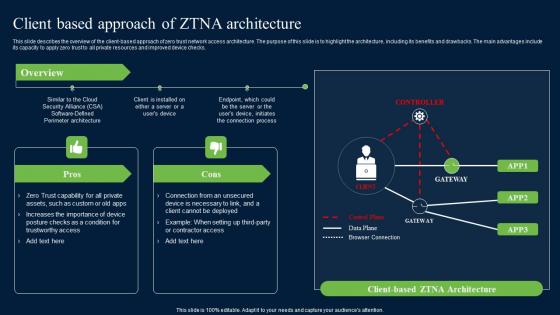
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
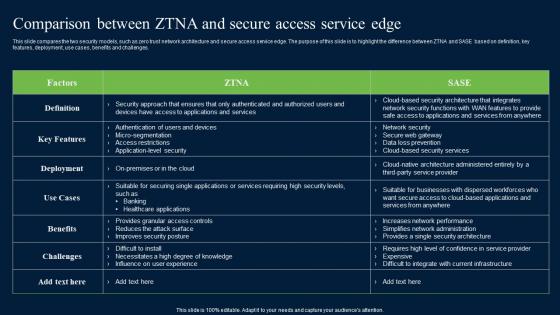
Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Critical Principles Of Zero Trust Network Access Security Formats Pdf
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Critical Principles Of Zero Trust Network Access Security Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Critical Principles Of Zero Trust Network Access Security Formats Pdf today and make your presentation stand out from the rest This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.
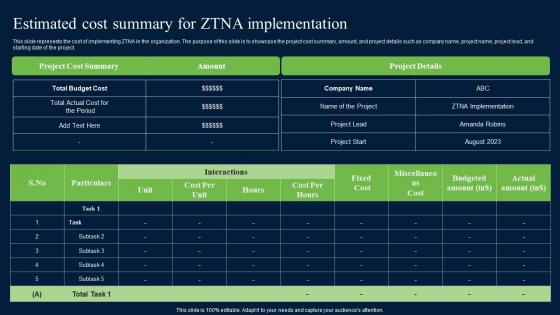
Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.
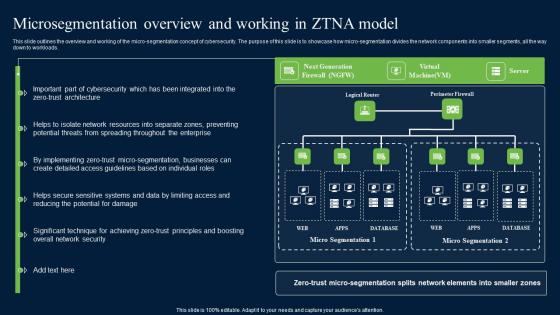
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.

On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
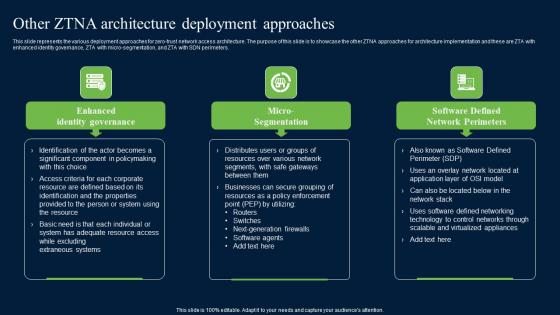
Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.
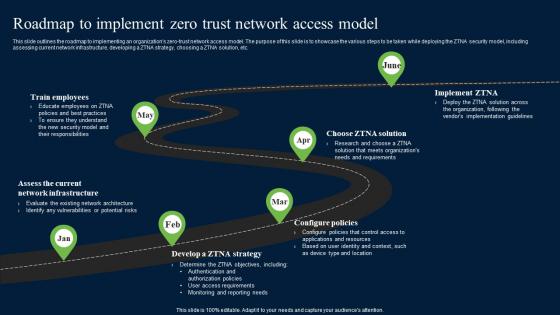
Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf
This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Create an editable Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members.
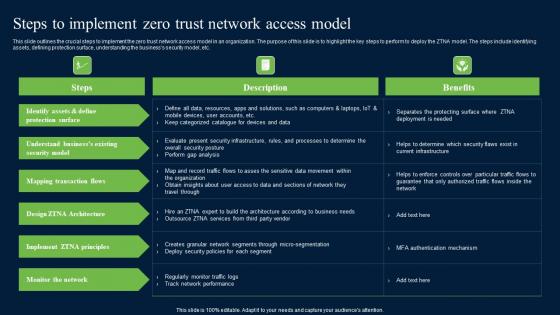
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
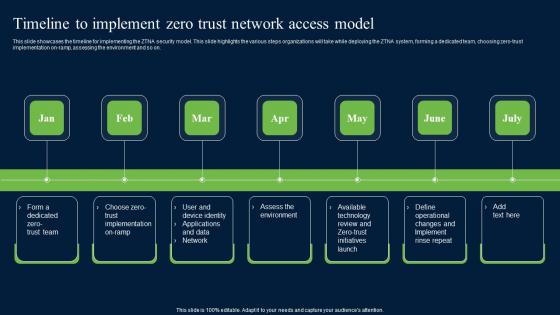
Timeline To Implement Zero Trust Network Security Themes Pdf
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Zero Trust Network Security Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
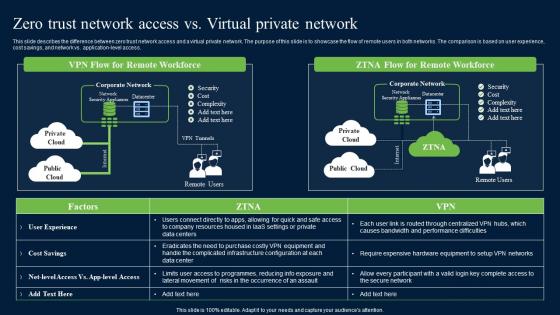
Zero Trust Network Access Vs Virtual Private Network Mockup Pdf
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Network Access Vs Virtual Private Network Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Network Access Vs Virtual Private Network Mockup Pdf today and make your presentation stand out from the rest This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access.
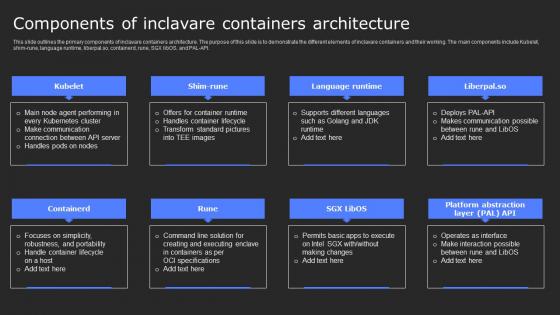
Components Of Inclavare Containers Secure Computing Framework Professional Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Slidegeeks is here to make your presentations a breeze with Components Of Inclavare Containers Secure Computing Framework Professional Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
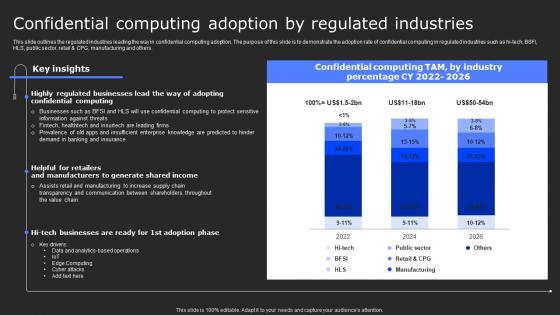
Confidential Computing Adoption By Secure Computing Framework Mockup Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Adoption By Secure Computing Framework Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Adoption By Secure Computing Framework Mockup Pdf today and make your presentation stand out from the rest This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
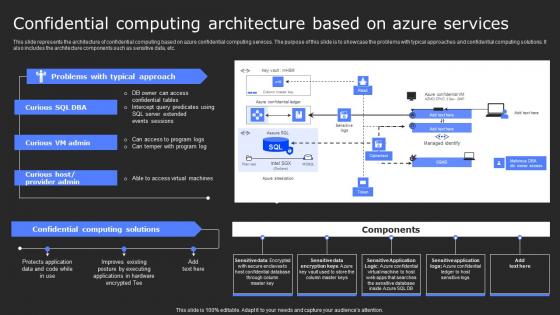
Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf
This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc.
Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. This Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
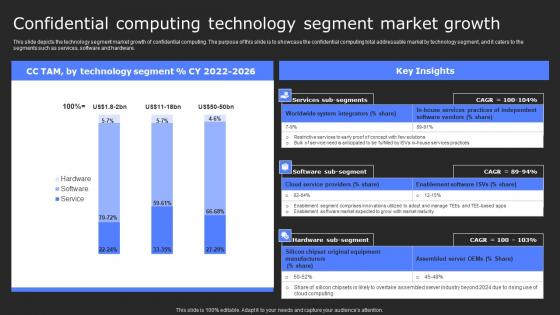
Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Explore a selection of the finest Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.
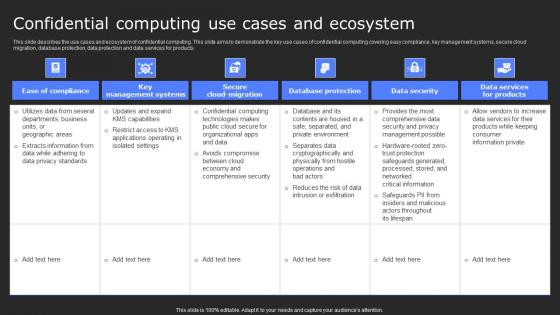
Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. The Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
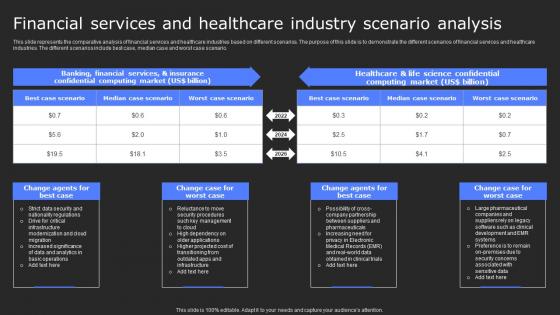
Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. Retrieve professionally designed Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario.
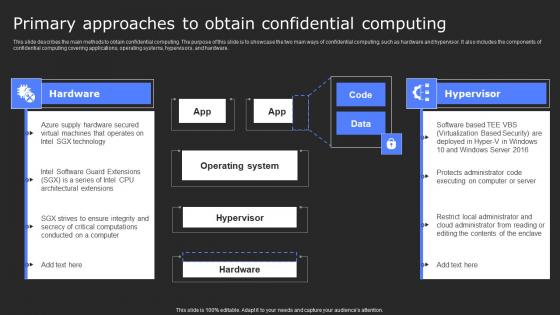
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.

Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf
This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf today and make your presentation stand out from the rest This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
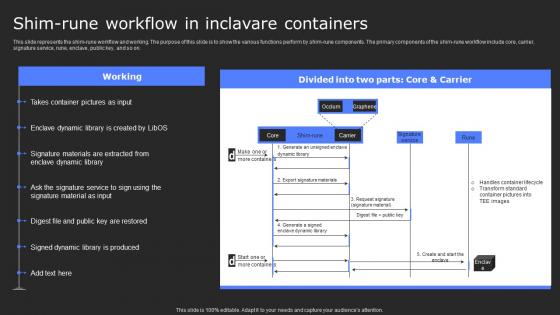
Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Create an editable Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.
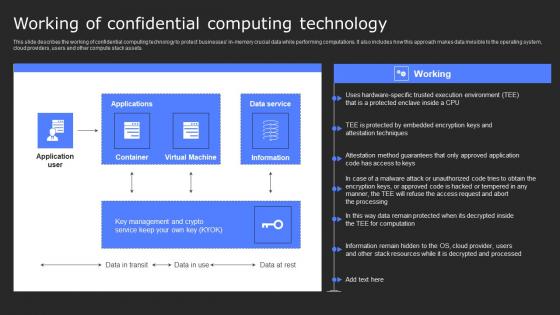
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
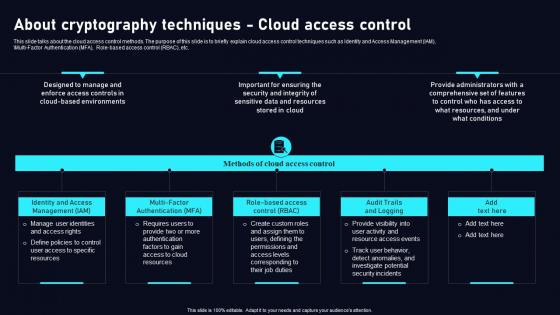
About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf
This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf today and make your presentation stand out from the rest This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc.

Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.
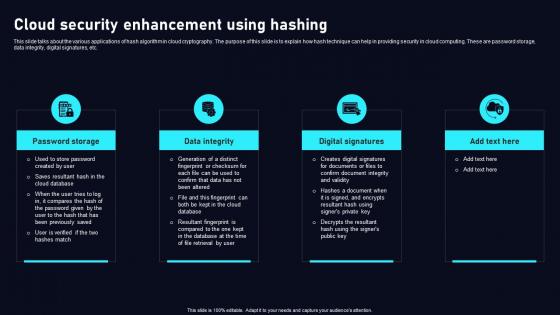
Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. This Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.
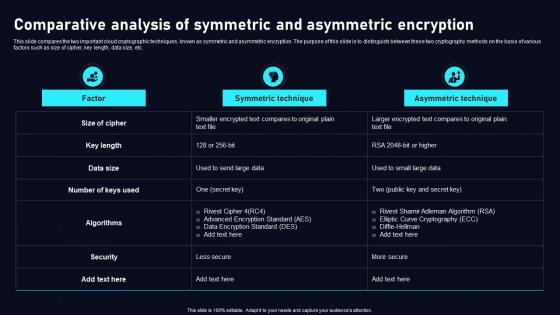
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.

Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. The Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.
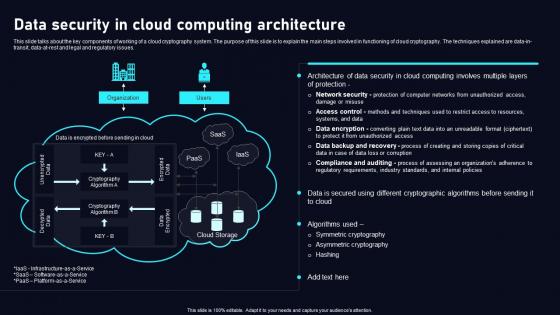
Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. Retrieve professionally designed Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues.
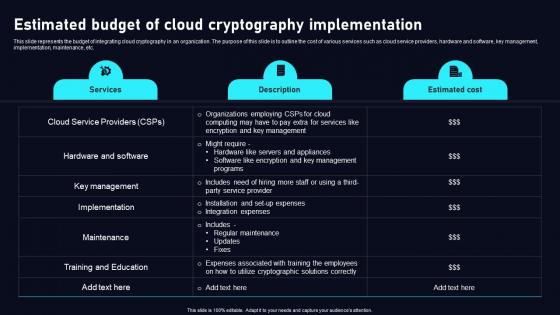
Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. This Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
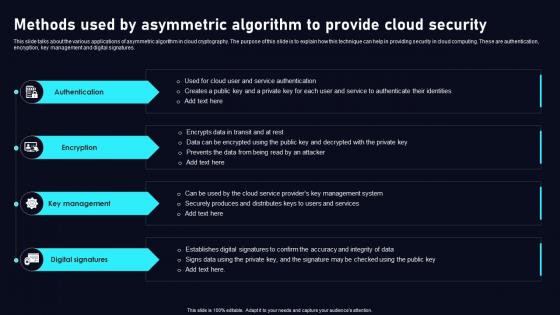
Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
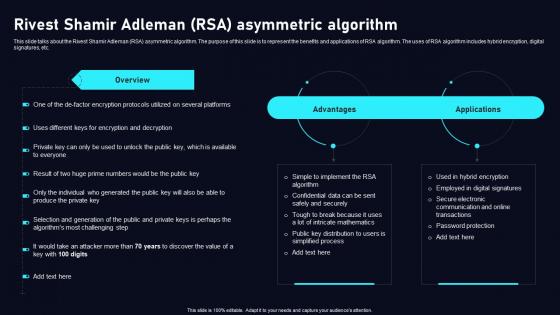
Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Slidegeeks is here to make your presentations a breeze with Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.
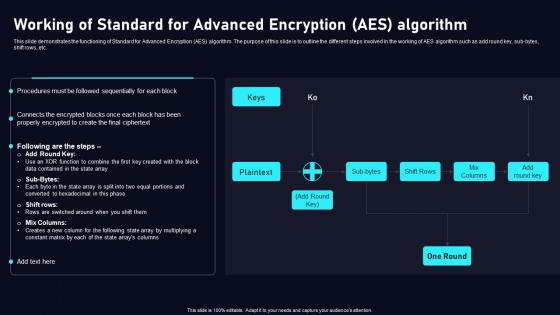
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc.

Org Structure Business Communication Improvement Platform Investor Sample Pdf
This slide showcases the team members and co founders of Aircall. It includes co founder , chief people officer, chief technology officer, chief customer officer, SVP product, Senior associate project manager, business value consultant. If you are looking for a format to display your unique thoughts, then the professionally designed Org Structure Business Communication Improvement Platform Investor Sample Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download org structure business communication improvement platform investor sample pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases the team members and co founders of Aircall. It includes co founder , chief people officer, chief technology officer, chief customer officer, SVP product, Senior associate project manager, business value consultant.

How Sound Sensory Marketing Strategy Helps Brand Driven Digital Marketing Brochure Pdf
This slide represents key reasons of why marketers should use sound to attract and build connections with customers. It includes seamless user experience, customer behavior etc. If you are looking for a format to display your unique thoughts, then the professionally designed How Sound Sensory Marketing Strategy Helps Brand Driven Digital Marketing Brochure Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download How Sound Sensory Marketing Strategy Helps Brand Driven Digital Marketing Brochure Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents key reasons of why marketers should use sound to attract and build connections with customers. It includes seamless user experience, customer behavior etc.

Esteemed Clientele Carelulu Shareholders Fund Raising Pitch Deck Inspiration Pdf
The following slide showcases customer categories that uses products and services offered by company which provides an online marketplace that helps parents to find and compare childcare services nearby. Its customers segments consists of parents, childcare services and businesses. Get a simple yet stunning designed Esteemed Clientele Carelulu Shareholders Fund Raising Pitch Deck Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Esteemed Clientele Carelulu Shareholders Fund Raising Pitch Deck Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases customer categories that uses products and services offered by company which provides an online marketplace that helps parents to find and compare childcare services nearby. Its customers segments consists of parents, childcare services and businesses.
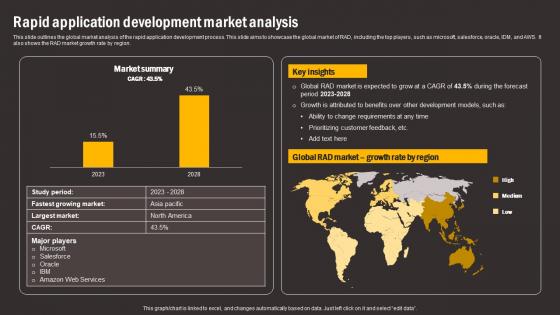
Rapid Application Development Market Comparing RAD And Other Software Template Pdf
This slide outlines the global market analysis of the rapid application development process. This slide aims to showcase the global market of RAD, including the top players, such as microsoft, salesforce, oracle, IDM, and AWS. It also shows the RAD market growth rate by region. Slidegeeks is here to make your presentations a breeze with Rapid Application Development Market Comparing RAD And Other Software Template Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the global market analysis of the rapid application development process. This slide aims to showcase the global market of RAD, including the top players, such as microsoft, salesforce, oracle, IDM, and AWS. It also shows the RAD market growth rate by region.

About Identity Theft Overview And Techniques Data Breach Prevention Download Pdf
This slide talks about the major crime committed by phishers, named as identity theft. The purpose of this slide is to outline the ways of stealing information, such as robbery, computer fraud, social networking sites, mail theft, and dumpster diving. Create an editable About Identity Theft Overview And Techniques Data Breach Prevention Download Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Identity Theft Overview And Techniques Data Breach Prevention Download Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the major crime committed by phishers, named as identity theft. The purpose of this slide is to outline the ways of stealing information, such as robbery, computer fraud, social networking sites, mail theft, and dumpster diving.
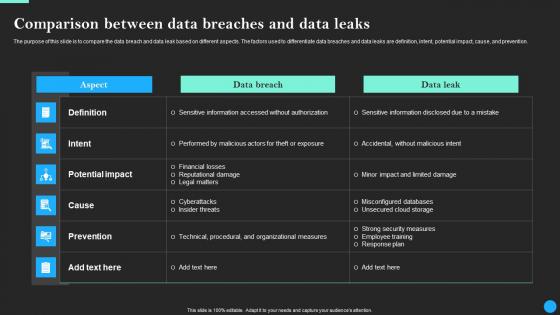
Comparison Between Data Breaches And Data Leaks Data Breach Prevention Download Pdf
The purpose of this slide is to compare the data breach and data leak based on different aspects. The factors used to differentiate data breaches and data leaks are definition, intent, potential impact, cause, and prevention. Slidegeeks is here to make your presentations a breeze with Comparison Between Data Breaches And Data Leaks Data Breach Prevention Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The purpose of this slide is to compare the data breach and data leak based on different aspects. The factors used to differentiate data breaches and data leaks are definition, intent, potential impact, cause, and prevention.

Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.
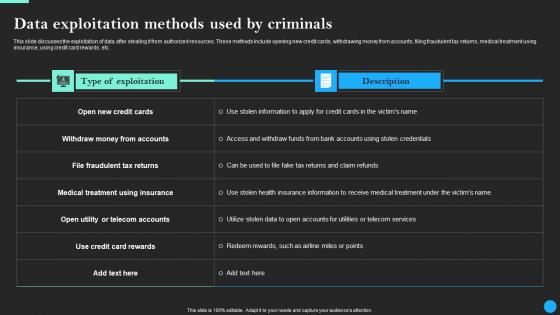
Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf
This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc. Explore a selection of the finest Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc.


 Continue with Email
Continue with Email

 Home
Home


































