Authentication
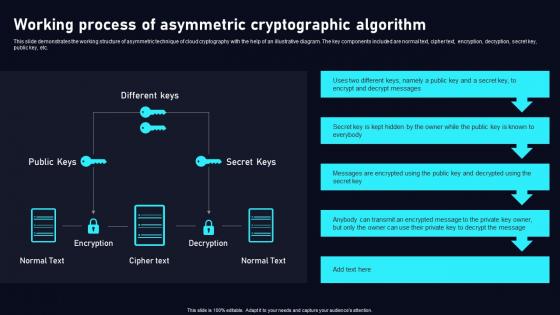
Working Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulateWorking Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.
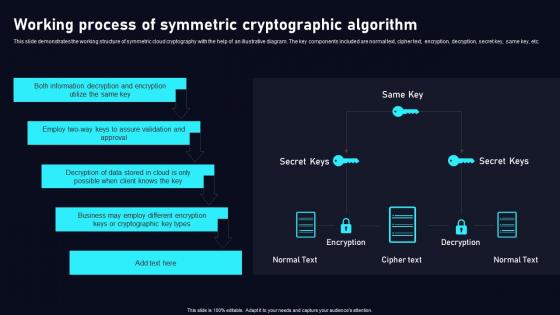
Working Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Want to ace your presentation in front of a live audience OurWorking Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.

About Us For Our Firewall Solutions Company Cloud Security Firewall Proposal
This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry-leading organizations, and history.Elevate your presentations with our intuitive About Us For Our Firewall Solutions Company Cloud Security Firewall Proposal template. Whether you are delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression. This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry-leading organizations, and history.

Business Model Canvas Security Service Provider Business Model BMC SS V
This slide provides the business model canvas of the company. It involves key partners, key activities, USP, customer relationships, customer segments, channels, revenue streams, channels, key resources, cost structure. Find a pre-designed and impeccable Business Model Canvas Security Service Provider Business Model BMC SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides the business model canvas of the company. It involves key partners, key activities, USP, customer relationships, customer segments, channels, revenue streams, channels, key resources, cost structure.

Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V
The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement.
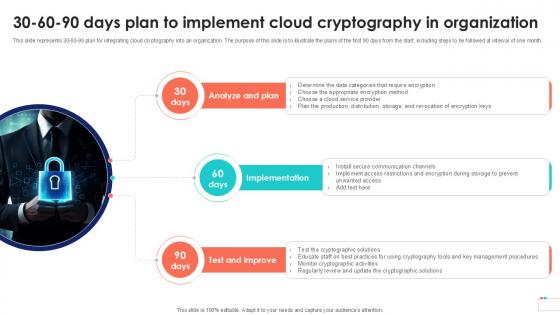
30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample
This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
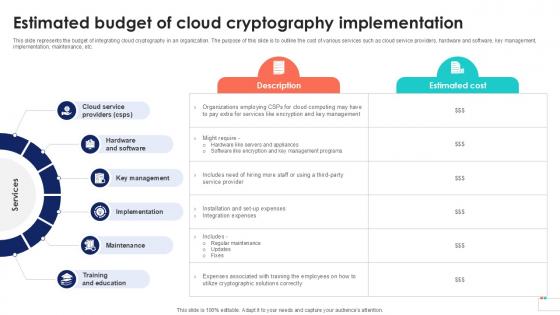
Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide from Slidegeeks and deliver a wonderful presentation. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
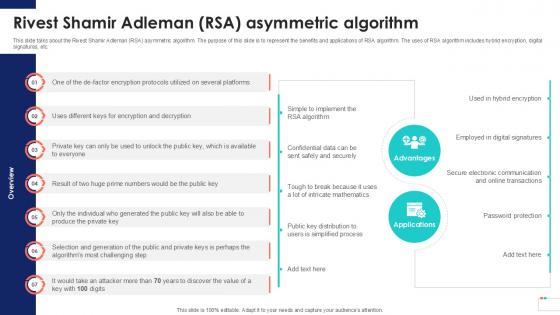
Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Want to ace your presentation in front of a live audience Our Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.
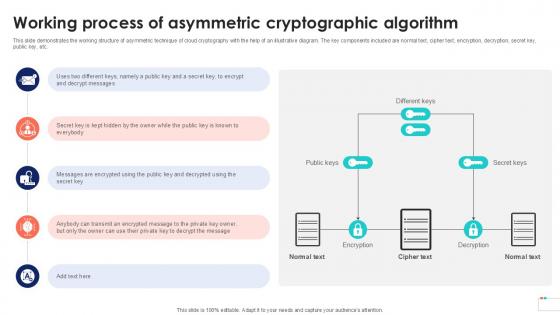
Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.

Major Cybersecurity Challenges With Required Actions Ppt Pictures Background Designs PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges This is a major cybersecurity challenges with required actions ppt pictures background designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, cybersecurity strategy, performing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
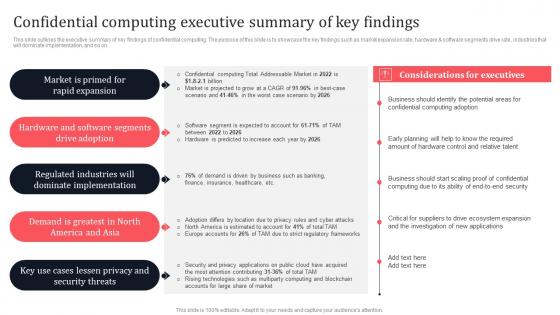
Confidential Computing Executive Summary Of Key Findings Secure Multi Party Topics Pdf
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Confidential Computing Executive Summary Of Key Findings Secure Multi Party Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on.
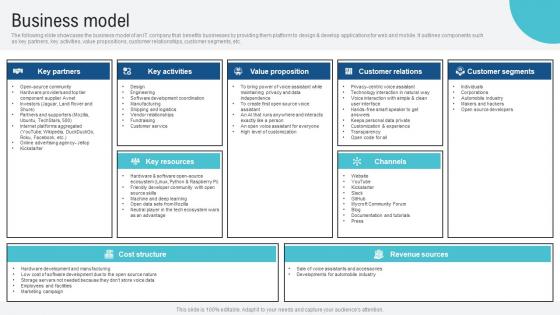
Business Model Voice Assistance Security Platform Investor Funding Presentation Guidelines Pdf
The following slide showcases the business model of an IT company that benefits businesses by providing them platform to design and develop applications for web and mobile. It outlines components such as key partners, key activities, value propositions, customer relationships, customer segments, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Business Model Voice Assistance Security Platform Investor Funding Presentation Guidelines Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide showcases the business model of an IT company that benefits businesses by providing them platform to design and develop applications for web and mobile. It outlines components such as key partners, key activities, value propositions, customer relationships, customer segments, etc.

Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V
The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry.
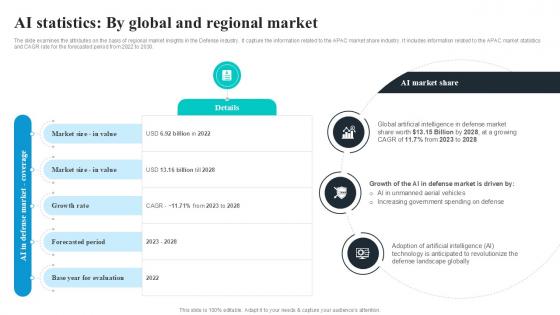
AI Statistics By Global And Regional Global Security Industry PPT Template IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. Boost your pitch with our creative AI Statistics By Global And Regional Global Security Industry PPT Template IR SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030.

Challenges For New Entrants In Global Security Industry PPT Example IR SS V
The slide showcases the barriers to entry in Defense industry. The main purpose of this slide is to recognize the variables that may impede or make it difficult for new entrants to enter the market successfully. By identifying these impediments, aspiring Defense companies can make educated judgements and establish appropriate strategies to overcome or manage them efficiently. Want to ace your presentation in front of a live audience Our Challenges For New Entrants In Global Security Industry PPT Example IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The slide showcases the barriers to entry in Defense industry. The main purpose of this slide is to recognize the variables that may impede or make it difficult for new entrants to enter the market successfully. By identifying these impediments, aspiring Defense companies can make educated judgements and establish appropriate strategies to overcome or manage them efficiently.

Market Restraints Impacting The Global Security Industry PPT Template IR SS V
The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry. This modern and well-arranged Market Restraints Impacting The Global Security Industry PPT Template IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc.
Cyber Security Ppt PowerPoint Presentation Styles Inspiration
This is a cyber security ppt powerpoint presentation styles inspiration. This is a three stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
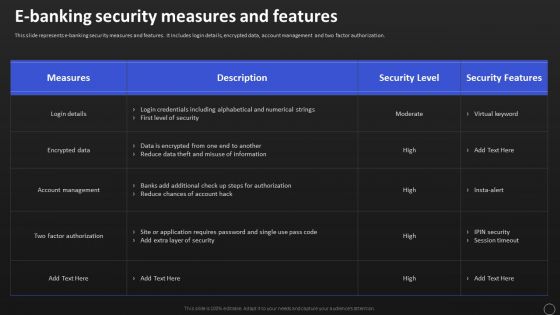
Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF
This slide represents e banking security measures and features. It includes login details, encrypted data, account management and two factor authorization. This Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

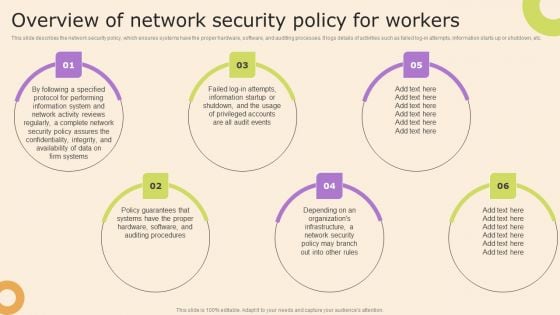
Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF from Slidegeeks and deliver a wonderful presentation.
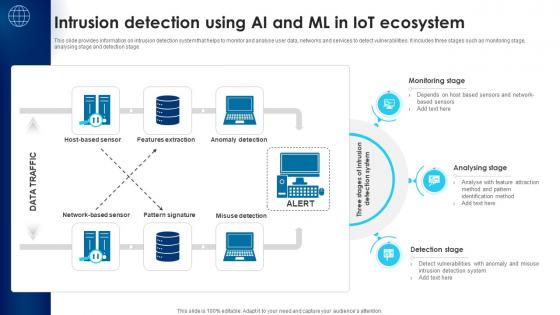
Building Trust With IoT Security Intrusion Detection Using AI And ML In IoT Ecosystem IoT SS V
This slide provides information on intrusion detection system that helps to monitor and analyse user data, networks and services to detect vulnerabilities. It includes three stages such as monitoring stage, analysing stage and detection stage. This Building Trust With IoT Security Intrusion Detection Using AI And ML In IoT Ecosystem IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Building Trust With IoT Security Intrusion Detection Using AI And ML In IoT Ecosystem IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information on intrusion detection system that helps to monitor and analyse user data, networks and services to detect vulnerabilities. It includes three stages such as monitoring stage, analysing stage and detection stage.
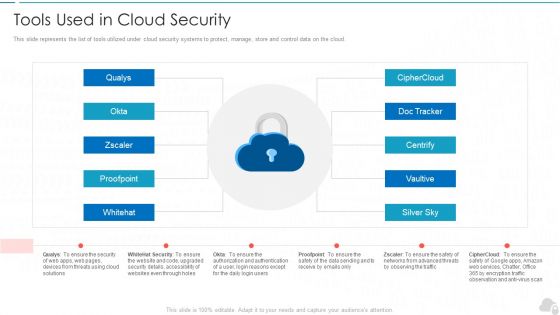
Tools Used In Cloud Security Cloud Computing Security IT Ppt Background Images PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a tools used in cloud security cloud computing security it ppt background images pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like silver sky, centrify, doc tracker, proofpoint, whitehat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
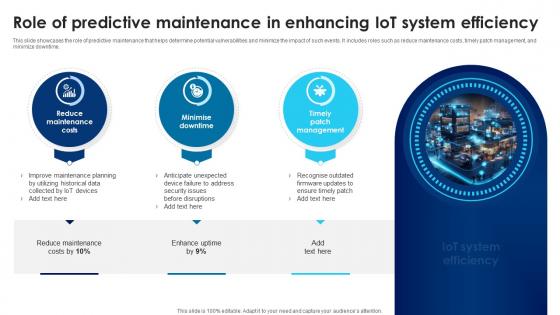
Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V
This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime.
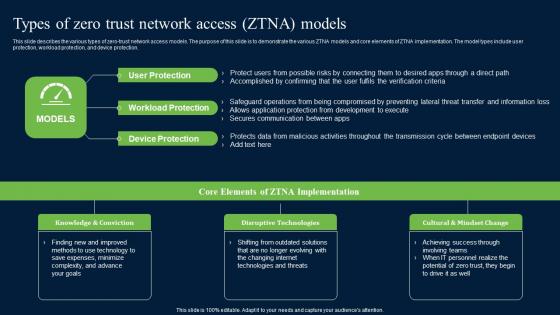
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.

Cyber Security Compliance Framework With Individual Rights Ppt PowerPoint Presentation Infographics Graphics Pictures
Presenting this set of slides with name cyber security compliance framework with individual rights ppt powerpoint presentation infographics graphics pictures. This is a twelve stage process. The stages in this process are raise awareness, information held, communicating privacy, individual rights, subject access requests, legalities of processing personal data, consent, protecting childrens data, data breaches, data protection by design, data protection officers, international work. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Real Time Assessment Of Security Threats Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of sixty five slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.
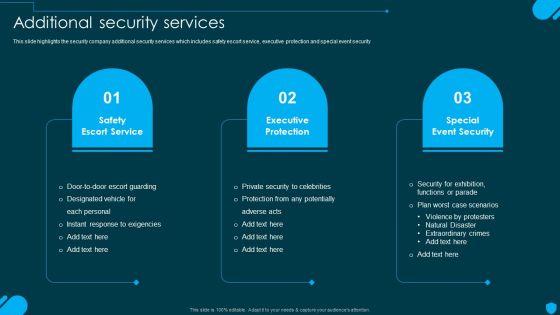
Security And Human Resource Services Business Profile Additional Security Services Rules PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Find a pre-designed and impeccable Security And Human Resource Services Business Profile Additional Security Services Rules PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Information Privacy IT Gdpr Law Governing Data Privacy Ideas PDF
This slide explains the General Data Protection Regulation it is the most extensive data protection law applied to each member of the EU. Presenting information privacy it gdpr law governing data privacy ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like gdpr law governing data privacy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Corporate Security And Risk Management Icons PDF
This is a corporate security and risk management corporate security and risk management icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate security and risk management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
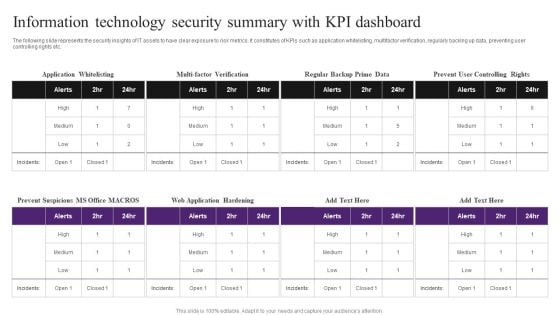
Information Technology Security Summary With KPI Dashboard Inspiration PDF
The following slide represents the security insights of IT assets to have clear exposure to risk metrics. It constitutes of KPIs such as application whitelisting, multifactor verification, regularly backing up data, preventing user controlling rights etc. Pitch your topic with ease and precision using this Information Technology Security Summary With KPI Dashboard Inspiration PDF. This layout presents information on Information Technology Security, Summary With KPI Dashboard. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
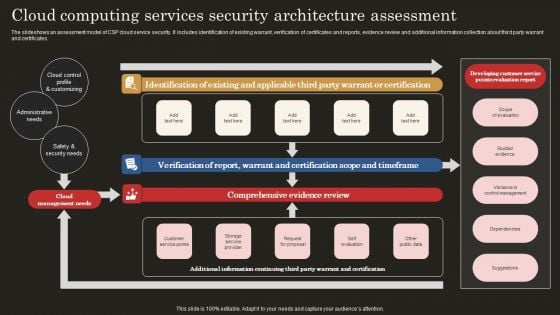
Cloud Computing Services Security Architecture Assessment Infographics PDF
The slideshows an assessment model of CSP cloud service security. It includes identification of existing warrant, verification of certificates and reports, evidence review and additional information collection about third party warrant and certificates. Showcasing this set of slides titled Cloud Computing Services Security Architecture Assessment Infographics PDF. The topics addressed in these templates are Cloud Control Profile, Administrative Need, Safety Security Needs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Diagram Warning Sign For Eye Protection With Yellow Sign Presentation Template
Display the sign of eye protection in your presentation with this exclusive diagram. This diagram slide contains the eye protection warning sign on yellow board. Use this diagram to make exclusive presentation on safety measures.
Employee Performance Review Brand Protection Ppt PowerPoint Presentation Infographic Template Format
This is a employee performance review brand protection ppt powerpoint presentation infographic template format. This is a three stage process. The stages in this process are employee performance review, brand protection.
Marketing Communications Brand Protection Ppt PowerPoint Presentation Infographic Template Graphics Tutorials
This is a marketing communications brand protection ppt powerpoint presentation infographic template graphics tutorials. This is a seven stage process. The stages in this process are marketing, communications, brand, protection.
Brand Protection Capital Structure Components Ppt PowerPoint Presentation Infographic Template Visual Aids
This is a brand protection capital structure components ppt powerpoint presentation infographic template visual aids. This is a four stage process. The stages in this process are brand, protection, capital, structure, components.
Quality Brand Protection Marketing Analysis Ppt PowerPoint Presentation Inspiration Slide Portrait
This is a quality brand protection marketing analysis ppt powerpoint presentation inspiration slide portrait. This is a seven stage process. The stages in this process are quality brand protection, marketing analysis.
Innovation Entrepreneurship Value Management Process Data Protection Directive Ppt PowerPoint Presentation Professional Layout
This is a innovation entrepreneurship value management process data protection directive ppt powerpoint presentation professional layout. This is a three stage process. The stages in this process are innovation entrepreneurship, value management process, data protection directive.

Consumer Protection Business Intelligence Career Development Business Plan Ppt PowerPoint Presentation Inspiration Graphics Example
This is a consumer protection business intelligence career development business plan ppt powerpoint presentation inspiration graphics example. This is a three stage process. The stages in this process are consumer protection, business intelligence, career development, business plan.
Professional Development Data Protection Seeing Dogs Market Research Ppt PowerPoint Presentation Icon Graphics Template
This is a professional development data protection seeing dogs market research ppt powerpoint presentation icon graphics template. This is a five stage process. The stages in this process are professional development, data protection, seeing dogs, market research.

Market Attractiveness Analysis Qualitative Data Analysis Data Protection Ppt PowerPoint Presentation Layouts Example
This is a market attractiveness analysis qualitative data analysis data protection ppt powerpoint presentation layouts example. This is a two stage process. The stages in this process are market attractiveness analysis, qualitative data analysis, data protection.
Successful Business Models Web Business Intelligence Brand Protection Ppt PowerPoint Presentation Show Summary
This is a successful business models web business intelligence brand protection ppt powerpoint presentation show summary. This is a seven stage process. The stages in this process are successful business models, web business intelligence, brand protection.
Building Client Relationships Onboarding Process Customers Asset Protection Ppt PowerPoint Presentation Ideas Graphics Example
This is a building client relationships onboarding process customers asset protection ppt powerpoint presentation ideas graphics example. This is a six stage process. The stages in this process are building client relationships, onboarding process customers, asset protection.
Business Assets Protection Personal Business Statement Business Funding Ppt PowerPoint Presentation Pictures Portfolio
This is a business assets protection personal business statement business funding ppt powerpoint presentation pictures portfolio. This is a four stage process. The stages in this process are business assets protection, personal business statement, business funding.
Performance Bond Insurance Protecting Your Assets Work Outsourcing Ppt PowerPoint Presentation Slides Images
This is a performance bond insurance protecting your assets work outsourcing ppt powerpoint presentation slides images. This is a five stage process. The stages in this process are performance bond insurance, protecting your assets, work outsourcing.

Personal Data Protection Policy Ppt Powerpoint Presentation Infographics Graphic Tips Cpb
This is a personal data protection policy ppt powerpoint presentation infographics graphic tips cpb. This is a three stage process. The stages in this process are personal data protection policy.
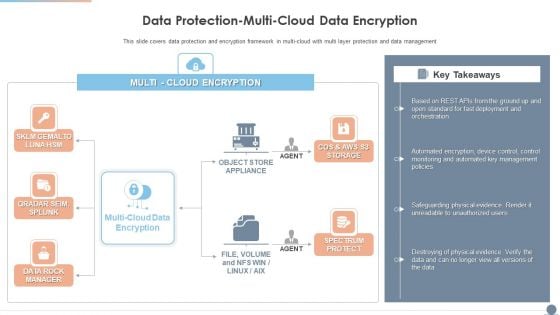
Multi Cloud Complexity Management Data Protection Multi Cloud Data Encryption Themes PDF
This slide covers data protection and encryption framework in multi cloud with multi layer protection and data management. Deliver an awe inspiring pitch with this creative Multi Cloud Complexity Management Data Protection Multi Cloud Data Encryption Themes PDF bundle. Topics like Automated Key Management, Spectrum Protect, Cloud Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
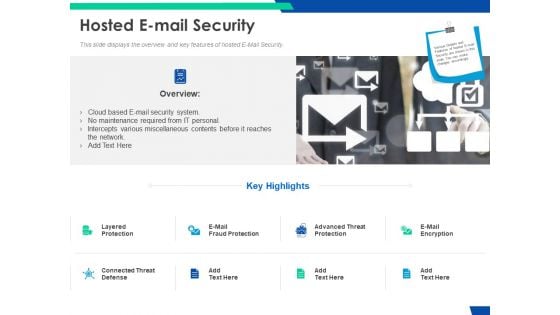
Cloud Based Email Security Market Report Hosted E Mail Security Ppt Ideas Rules PDF
This slide displays the overview and key features of hosted E Mail Security. This is a cloud based email security market report hosted e mail security ppt ideas rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like maintenance, security, miscellaneous, protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
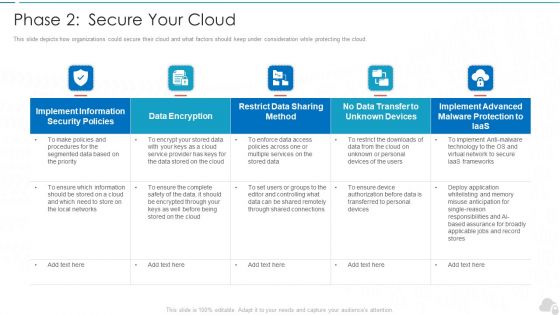
Phase 2 Secure Your Cloud Cloud Computing Security IT Ppt Slides Skills PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative phase 2 secure your cloud cloud computing security it ppt slides skills pdf bundle. Topics like implement, security policies, data encryption, services, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Risk Management Plan Current Security Infrastructure Performance Analysis Icons PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative cyber security risk management plan current security infrastructure performance analysis icons pdf bundle. Topics like technology, target, plan, vulnerability intelligence, security infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
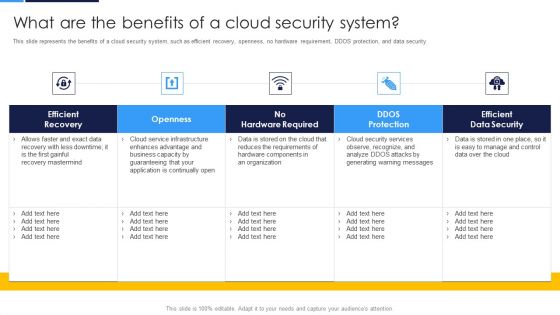
Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF. Use them to share invaluable insights on Efficient Recovery, Hardware Required, Efficient Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Security Cloud Data Ppt PowerPoint Presentation Summary Graphics Download
This is a cyber security cloud data ppt powerpoint presentation summary graphics download. This is a five stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
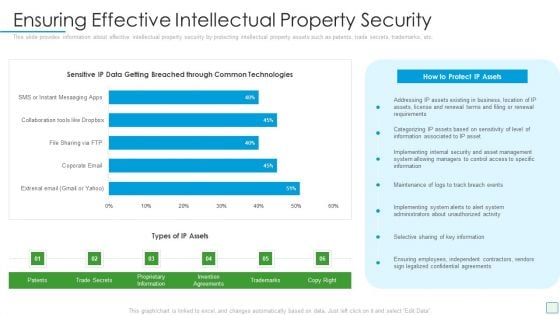
Developing Firm Security Strategy Plan Ensuring Effective Intellectual Property Security Download PDF
This slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan ensuring effective intellectual property security download pdf. Use them to share invaluable insights on business, management, implementing, maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
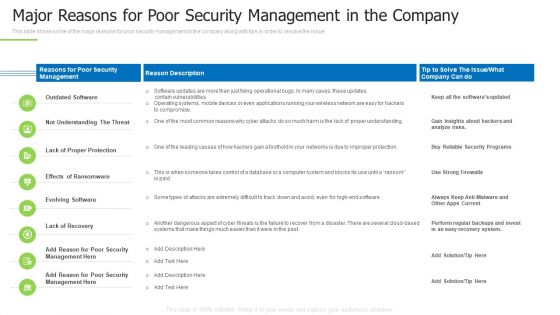
Techniques And Strategies To Reduce Security Management Risks Major Reasons For Poor Security Guidelines PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks major reasons for poor security guidelines pdf bundle. Topics like outdated software, lack of proper protection, another dangerous aspect can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
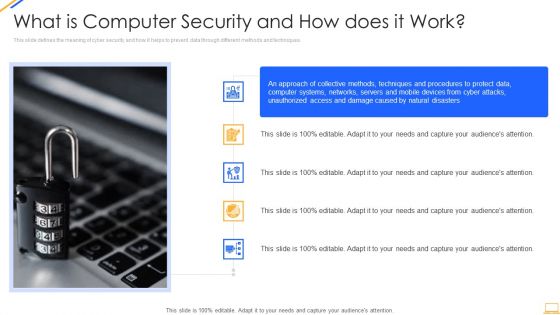
Desktop Security Management What Is Computer Security And How Does It Work Template PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Deliver an awe inspiring pitch with this creative desktop security management what is computer security and how does it work template pdf bundle. Topics like networks, systems, protect data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
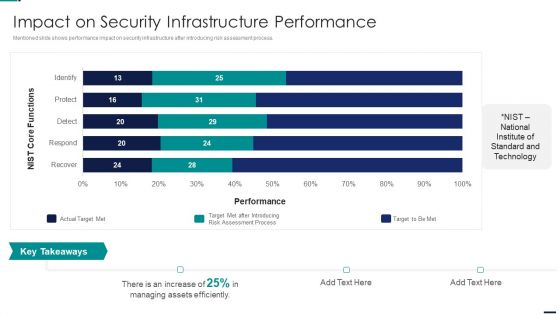
Risk Management Model For Data Security Impact On Security Infrastructure Performance Elements PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Impact On Security Infrastructure Performance Elements PDF. Use them to share invaluable insights on Identify, Protect, Detect, Respond, Recover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF bundle. Topics like Identify, Protect, Detect, Response, Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF bundle. Topics like Implement Information, Data Encryption, Implement Advanced can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
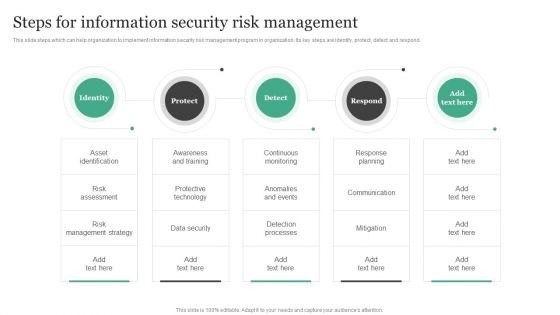
Steps For Information Security Risk Management Information Security Risk Administration Template PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond.There are so many reasons you need a Steps For Information Security Risk Management Information Security Risk Administration Template PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

American Intelligence And Security PowerPoint Templates Ppt Backgrounds For Slides 0813
Put yourself in a dominant position. Our American Intelligence And Security PowerPoint Templates PPT Backgrounds For Slides will confirm your superiority. Dominate proceedings with your ideas. Our Americana PowerPoint Templates will empower your thoughts. Our Medical PowerPoint Templates have a domino effect. Your ideas will generate one after another.


 Continue with Email
Continue with Email

 Home
Home


































