Authentication

Identity Security PowerPoint Template 1110
Blue Earth globe and padlock isolated over white background Enhance your chances of asset creation. Diversify your base with our Identity Security PowerPoint Template 1110.

Improving The Balance Of Payments Ppt Slide
This is a improving the balance of payments ppt slide. This is a one stage process. The stages in this process are security, success, marketing, business.

Analyzing Customer Behavior Marketing More Effectively Ppt Slides
This is a analyzing customer behavior marketing more effectively ppt slides. This is a four stage process. The stages in this process are security, business, marketing.

Project Hierarchy Powerpoint Ideas
This is a project hierarchy powerpoint ideas. This is a five stage process. The stages in this process are technology, business, man, security, key.
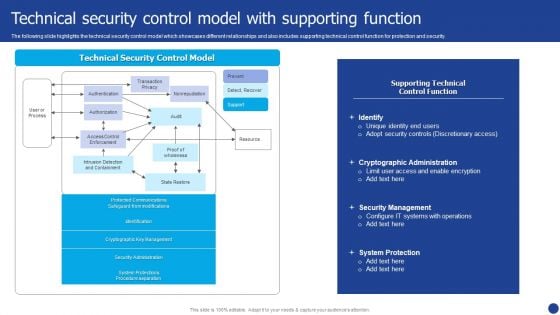
Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Secure Files PowerPoint Icon C
simple 3d illustration of a lock placed in front of an open file folder Our Secure Files PowerPoint Icon C are very falcon like. They keep a sharp eye on the target.
Secure Files PowerPoint Icon Cc
simple 3d illustration of a lock placed in front of an open file folder Enhance the belief of your congregation. Our Secure Files PowerPoint Icon Cc help add to their devotion.
Secure Files PowerPoint Icon S
simple 3d illustration of a lock placed in front of an open file folder Complement your thoughts with our Secure Files PowerPoint Icon S. They will give an admirable account.
Cybersecurity Tips Ppt PowerPoint Presentation Gallery Example File
This is a cybersecurity tips ppt powerpoint presentation gallery example file. This is a five stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Are you searching for a IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF from Slidegeeks today.

Framework Of Information IT Security Action Program Slides PDF
This slide focuses on information security action program framework which covers governance plan, security standards, stakeholder engagement and operational management to manage risks, handling threat, data security management, etc.Showcasing this set of slides titled Framework Of Information IT Security Action Program Slides PDF The topics addressed in these templates are Security Standards, Data Protection, Response Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Business Diagram Correct Wrong And Security Icons For Antivirus Software Presentation Template
This business slide displays correct wrong and security icons. Download this slide to depict antivirus and software protection related concepts. It will make your presentation look professional and keep your audience mesmerized.
Causes Of Data Risk In Business With Poor Governance Ppt PowerPoint Presentation Infographics Icon PDF
Presenting causes of data risk in business with poor governance ppt powerpoint presentation infographics icon pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including poor data governance, data mismanagement, lacklustre data security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
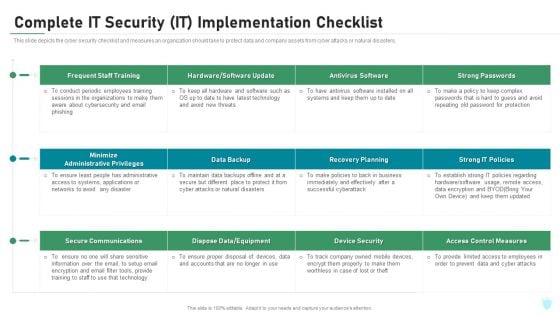
Complete IT Security IT Implementation Checklist Ppt Diagrams PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Deliver an awe inspiring pitch with this creative complete it security it implementation checklist ppt diagrams pdf bundle. Topics like training, antivirus software, secure communications, access control measures, device security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF. Use them to share invaluable insights on Effective Preventative, Information Systems, Security Consciousness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
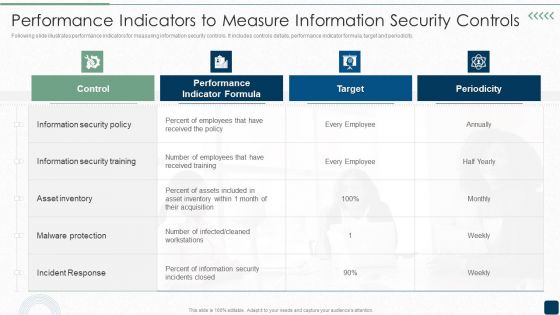
Performance Indicators To Measure Information Security Controls Brochure PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity.Deliver an awe inspiring pitch with this creative Performance Indicators To Measure Information Security Controls Brochure PDF bundle. Topics like Information Security, Security Training, Malware Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
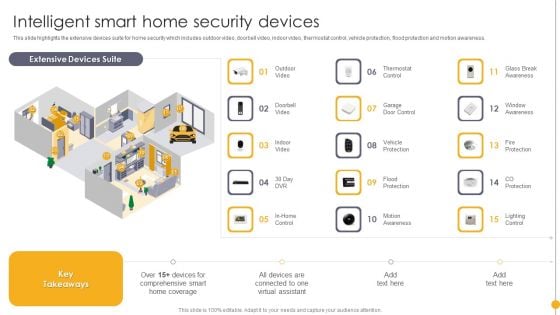
Portable Home Safety Systems Company Profile Intelligent Smart Home Security Devices Structure PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Portable Home Safety Systems Company Profile Intelligent Smart Home Security Devices Structure PDF bundle. Topics like Extensive Devices Suite, Comprehensive Smart, Virtual Assistant can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Current Security Infrastructure Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative effective it risk management process current security infrastructure clipart pdf bundle. Topics like asset management, data security, plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
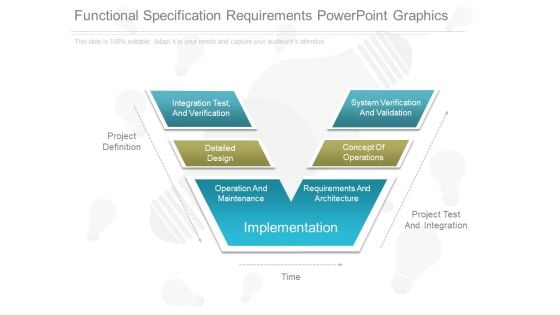
Functional Specification Requirements Powerpoint Graphics
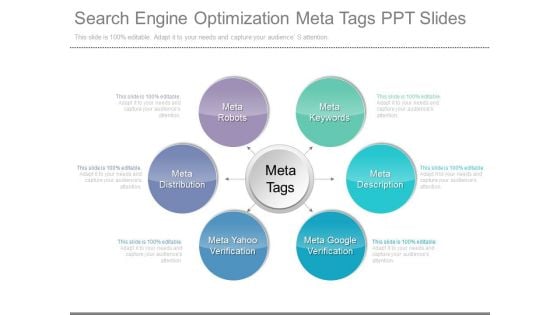
Search Engine Optimization Meta Tags Ppt Slides
This is a search engine optimization meta tags ppt slides. This is a six stage process. The stages in this process are meta robots, meta keywords, meta description, meta google verification, meta yahoo verification, meta distribution, meta tags.

Enhancing Cyber Safety With Vulnerability Administration What Sets Us Apart Microsoft PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. This is a enhancing cyber safety with vulnerability administration what sets us apart microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like productivity improvement for it, meet dynamic business , needs quickly unlock real value of security devices, attractive total cost ownership and roi. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
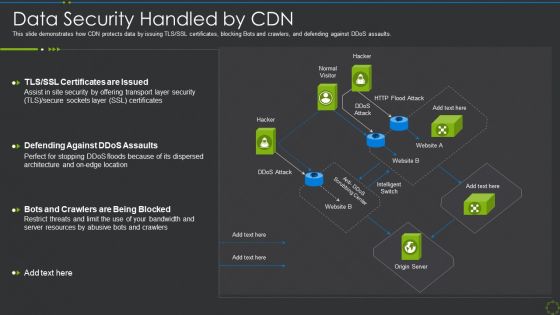
Data Security Handled By Cdn Ppt Show Clipart Images PDF
This slide demonstrates how CDN protects data by issuing TLS SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an awe inspiring pitch with this creative data security handled by cdn ppt show clipart images pdf bundle. Topics like data security handled by cdn can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
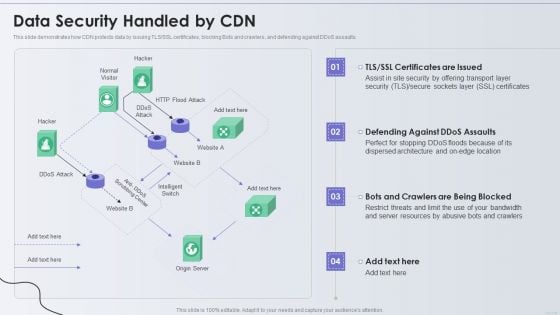
Distribution Network Data Security Handled By CDN Topics PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an awe inspiring pitch with this creative Distribution Network Data Security Handled By CDN Topics PDF bundle. Topics like Security, Resources, Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
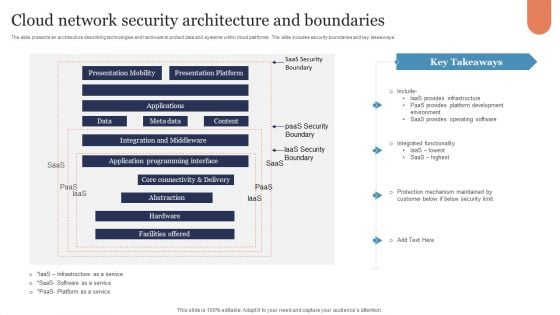
Cloud Network Security Architecture And Boundaries Graphics PDF
The slide presents an architecture describing technologies and hardware to protect data and systems within cloud platforms . The slide includes security boundaries and key takeaways. Showcasing this set of slides titled Cloud Network Security Architecture And Boundaries Graphics PDF. The topics addressed in these templates are Presentation Mobility, Presentation Platform, Applications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
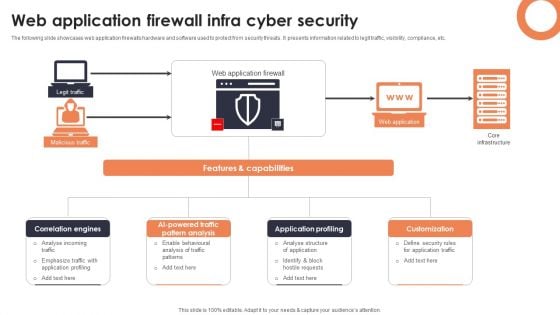
Web Application Firewall Infra Cyber Security Designs PDF
The following slide showcases web application firewalls hardware and software used to protect from security threats. It presents information related to legit traffic, visibility, compliance, etc. Showcasing this set of slides titled Web Application Firewall Infra Cyber Security Designs PDF. The topics addressed in these templates are Correlation Engines, AI Powered Traffic Pattern, Application Profiling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mobile Device Management For Ios Platform Mobile Device Security Management Mockup PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Deliver an awe inspiring pitch with this creative Mobile Device Management For Ios Platform Mobile Device Security Management Mockup PDF bundle. Topics like Device Enrollment, Theft Protection, Remote Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
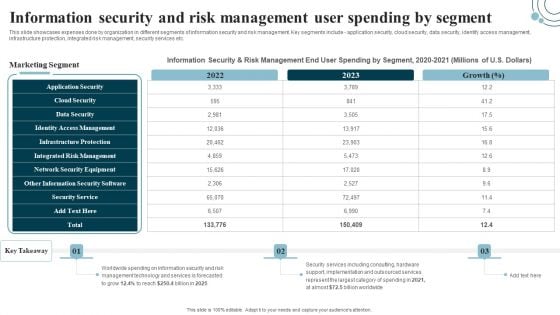
Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Present like a pro with Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Credit Card Security PowerPoint Template 1110
Security: Closeup of brass padlock on credit card. Lecture teams with our Credit Card Security PowerPoint Template 1110. Download without worries with our money back guaranteee.
Payment Card Industry Financial Regulatory Compliance Icons PDF
This slide showcases compliance of payment card industry. It includes conducting regular system tests, protecting cardholder data by encrypting and firewall, creating unique system password and maintaining security policy.Persuade your audience using this Payment Card Industry Financial Regulatory Compliance Icons PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Maintaining Security, Encrypting Cardholder, Assigning A Unique Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
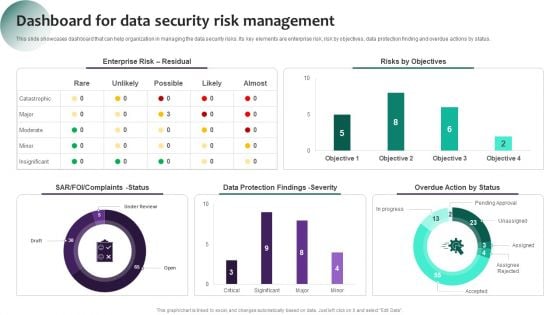
Information Systems Security And Risk Management Plan Dashboard For Data Security Risk Management Information PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. If you are looking for a format to display your unique thoughts, then the professionally designed Information Systems Security And Risk Management Plan Dashboard For Data Security Risk Management Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Systems Security And Risk Management Plan Dashboard For Data Security Risk Management Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Cyber Risk Intelligence Services For Enterprise Security Icons PDF
Persuade your audience using this cyber risk intelligence services for enterprise security icons pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including incident resolution, threat protection, it services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Exploitation IT Preventing Measures For Social Media Accounts Themes PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies. Presenting cyber exploitation it preventing measures for social media accounts themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like social media policies, anti malware software, social media login credentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
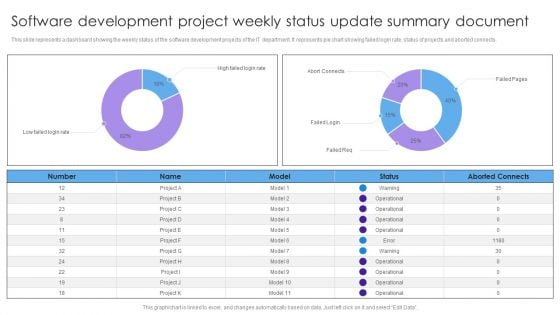
Software Development Project Weekly Status Update Summary Document Inspiration PDF
This slide represents a dashboard showing the weekly status of the software development projects of the IT department. It represents pie chart showing failed login rate, status of projects and aborted connects. Pitch your topic with ease and precision using this Software Development Project Weekly Status Update Summary Document Inspiration PDF. This layout presents information on High Failed, Login Rate, Abort Connects, Failed Login. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Conducting Vulnerability Comprehensive Guide To Blockchain Digital Security Mockup Pdf
The following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Conducting Vulnerability Comprehensive Guide To Blockchain Digital Security Mockup Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc.
Business Diagram Three Circles With Lock For Safety Presentation Template
Three air balloons with text boxes are used to craft this power point template slide. This PPT slide contains the concept of business text representation. This slide is usable for business and marketing related presentations.

Fact Based Planning Foundational Competencies Ppt Example
This is a fact based planning foundational competencies ppt example. This is a four stage process. The stages in this process are fact based planning, foundational competencies, developing potential, business planning.

Developing Self And Other Powerpoint Slide Presentation Tips
This is a developing self and other powerpoint slide presentation tips. This is a one stage process. The stages in this process are achieving results, developing self and other, working self and other.

Finding Innovative Solutions Embracing Change Ppt Slides
This is a finding innovative solutions embracing change ppt slides. This is a four stage process. The stages in this process are providing direction, finding innovative solutions, using resources, embracing change.\n\n
Affirmative Action Plan Applicant Tracking Ppt Example
This is a affirmative action plan applicant tracking ppt example. This is a five stage process. The stages in this process are affirmative action plan, union negotiation costing, availability analysis, workforce utilization, applicant tracking.
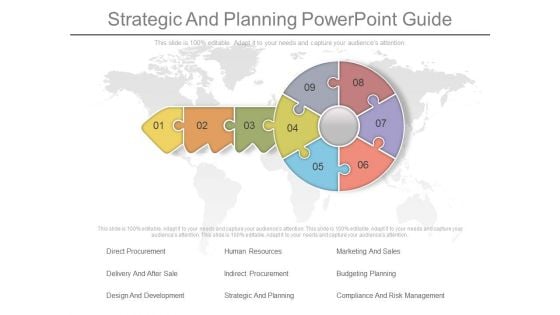
Strategic And Planning Powerpoint Guide
This is a strategic and planning powerpoint guide. This is a nine stage process. The stages in this process are direct procurement, human resources, marketing and sales, delivery and after sale, indirect procurement, budgeting planning, design and development, strategic and planning, compliance and risk management.

Demand Management In Supply Chain Ppt Ideas
This is a demand management in supply chain ppt ideas. This is a four stage process. The stages in this process are marketing, customer relationship management, demand planning, sales forecasting.

Configurable Business Rules Example Of Ppt Presentation
This is a configurable business rules example of ppt presentation. This is a five stage process. The stages in this process are configurable business rules, real time insights collection, restaurants and hotels, flexible integration, best practices implemented.
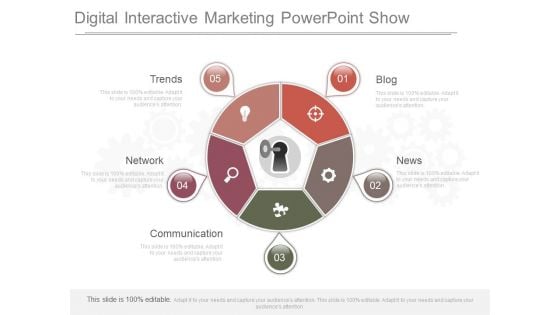
Digital Interactive Marketing Powerpoint Show
This is a digital interactive marketing powerpoint show. This is a five stage process. The stages in this process are blog, news, communication, network, trends.

Implementation Governance Ppt Sample File
This is a implementation governance ppt sample file. This is a two stage process. The stages in this process are implementation governance, requirements management.

Recognize Good Business Opportunities Template Ppt Slide
This is a recognize good business opportunities template ppt slide. This is a five stage process. The stages in this process are Analyze And Collaborate, Connect And Interact, Incorporate And Repeat, Find And Engage, Inspire And Advocate.
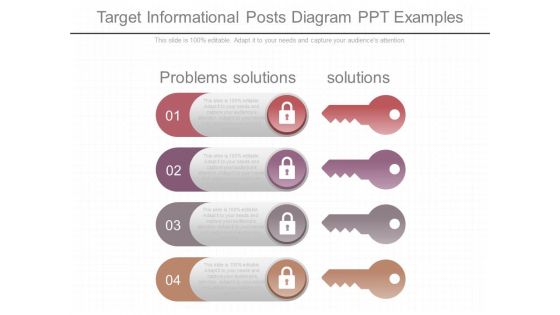
Target Informational Posts Diagram Ppt Examples
This is a target informational posts diagram ppt examples. This is a four stage process. The stages in this process are problems solutions , solutions.
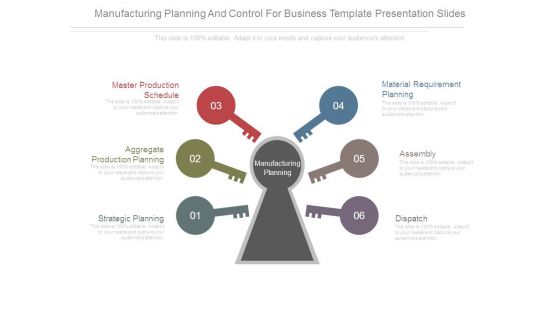
Manufacturing Planning And Control For Business Template Presentation Slides
This is a Manufacturing Planning And Control For Business Template Presentation Slides. This is a six stage process. The stages in this process are master production schedule, aggregate production planning, strategic planning, material requirement planning, assembly, dispatch.
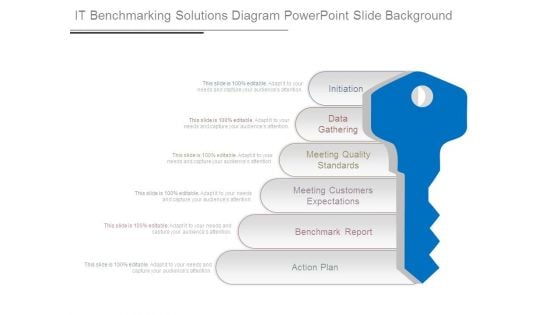
It Benchmarking Solutions Diagram Powerpoint Slide Background
This is a it benchmarking solutions diagram powerpoint slide background. This is a six stage process. The stages in this process are initiation, data gathering, meeting quality standards, meeting customers expectations, benchmark report, action plan.
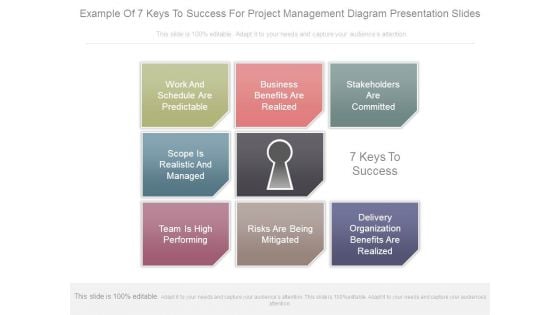
Example Of 7 Keys To Success For Project Management Diagram Presentation Slides
This is a example of 7 keys to success for project management diagram presentation slides. This is a eight stage process. The stages in this process are work and schedule are predictable, business benefits are realized, stakeholders are committed, scope is realistic and managed, 7 keys to success, team is high performing, risks are being mitigated, delivery organization benefits are realized.
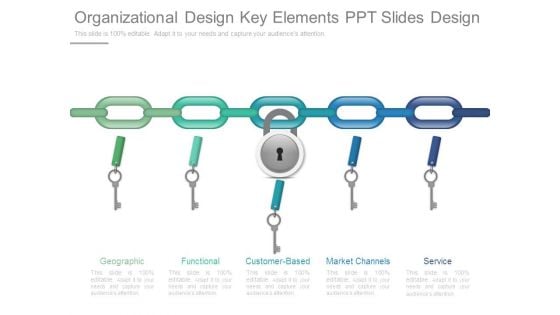
Organizational Design Key Elements Ppt Slides Design
This is a organizational design key elements ppt slides design. This is a five stage process. The stages in this process are geographic, functional, customer based, market channels, service.
Real Estate Template 1 Ppt PowerPoint Presentation Background Images
This is a real estate template 1 ppt powerpoint presentation background images. This is a one stage process. The stages in this process are real estate, planning, management, marketing, strategy.

The Big Idea Ppt PowerPoint Presentation Show
This is a the big idea ppt powerpoint presentation show. This is a one stage process. The stages in this process are safety, key, business, marketing.
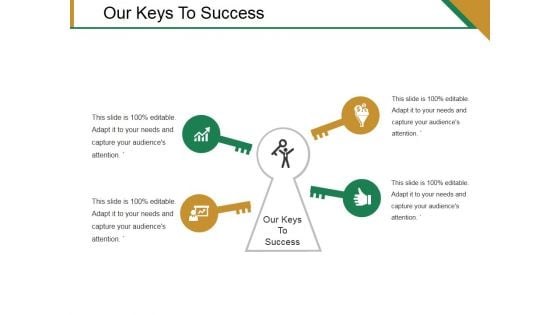
Our Keys To Success Template 1 Ppt PowerPoint Presentation Professional Elements
This is a our keys to success template 1 ppt powerpoint presentation professional elements. This is a four stage process. The stages in this process are our keys to success.
Checklist Icon With Four Text Boxes Ppt PowerPoint Presentation Show Model
This is a checklist icon with four text boxes ppt powerpoint presentation show model. This is a one stage process. The stages in this process are risk management icon, governance icon, compliance icon.
Pci Regulatory Icon Ppt PowerPoint Presentation File Display
This is a pci regulatory icon ppt powerpoint presentation file display. This is a one stage process. The stages in this process are risk management icon, governance icon, compliance icon.
Privacy Ppt PowerPoint Presentation Outline Slides
This is a privacy ppt powerpoint presentation outline slides. This is a four stage process. The stages in this process are privacy, business, management, planning, strategy.
Open Access Computer Screen With Unlock Icon Ppt PowerPoint Presentation Layouts Slides
This is a open access computer screen with unlock icon ppt powerpoint presentation layouts slides. This is a three stage process. The stages in this process are computer software, operating system, open source.


 Continue with Email
Continue with Email

 Home
Home


































