Authentication

Weak Link Chain Security PowerPoint Template 0910
red man breaks the chain on white background Remove confusionswith our Weak Link Chain Security PowerPoint Template 0910. You'll deliver your best presentation yet.

Binary Internet Security PowerPoint Template 1110
Graphic depicting binary data escaping through a keyhole Make our Binary Internet Security PowerPoint Template 1110 the abode for your thoughts. They will exist in complete comfort.

Identity Theft Security PowerPoint Template 1110
Hand punching through the image grabbing documents Get people out of bed with our Identity Theft Security PowerPoint Template 1110. Just download, type and present.
Security Analysis Bar Graph Ppt Slides
This is a security analysis bar chart ppt slides. This is a one stage process. The stages in this process are business, finance, marketing.
Securities Trading Market Template Ppt Slides
This is a securities trading market template ppt slides. This is a five stage process. The stages in this process are investor, broker, exchange, clearing, depository.
Security Risk Assessment Sample Diagram Ppt Sample
This is a security risk assessment sample diagram ppt sample. This is a four stage process. The stages in this process are identify, document, decide, evaluate, review.
Security Challenges Domains On Web Sample Diagram
This is a security challenges domains on web sample diagram. This is a three stage process. The stages in this process are web, process, people, technology.

Security Patch Management Template Presentation Images
This is a security patch management template presentation images. This is a six stage process. The stages in this process are testing, architecture, quality assurance, analysis, design, synthesis.

Security Website Template Powerpoint Slide Background
This is a security website template powerpoint slide background. This is a six stage process. The stages in this process are deep scan, uncover and retire, inventory.
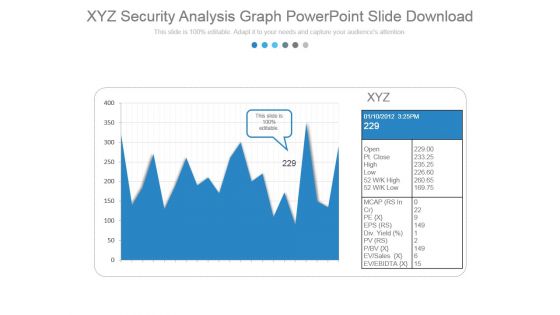
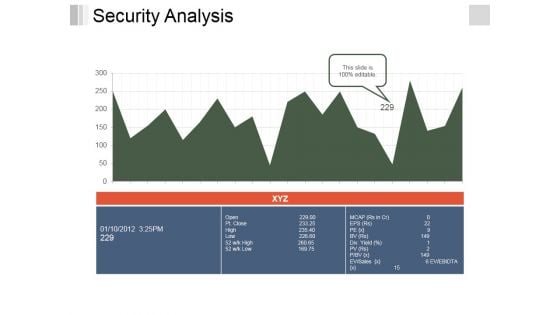
Xyz Security Analysis Graph Powerpoint Slide Download
This is a xyz security analysis graph powerpoint slide download. This is a two stage process. The stages in this process are business, marketing, growth, graph.
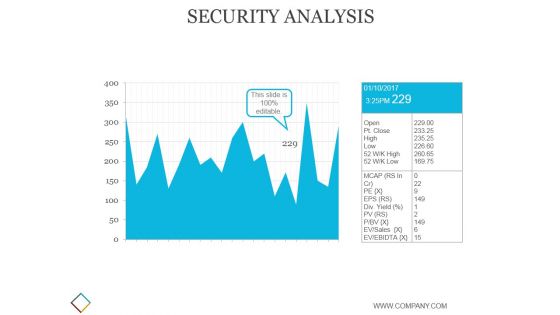
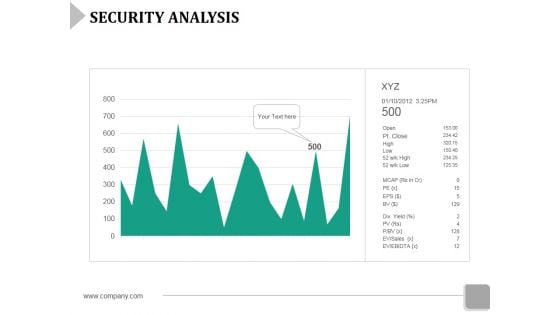
Security Analysis Ppt PowerPoint Presentation Slides
This is a security analysis ppt powerpoint presentation slides. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, growth.
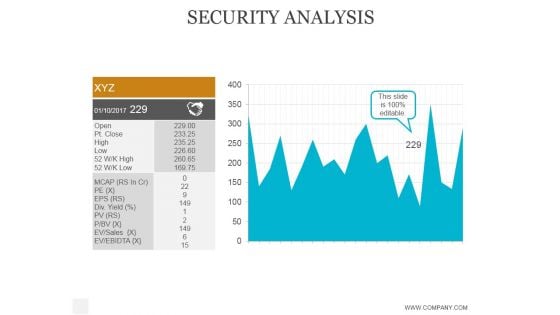
Security Analysis Ppt PowerPoint Presentation Layout
This is a security analysis ppt powerpoint presentation layout. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, success.
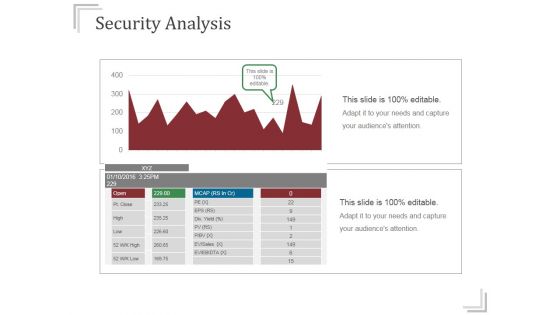
Security Analysis Ppt PowerPoint Presentation Infographics
This is a security analysis ppt powerpoint presentation infographics. This is a two stage process. The stages in this process are business, finance, growth, analysis, success.
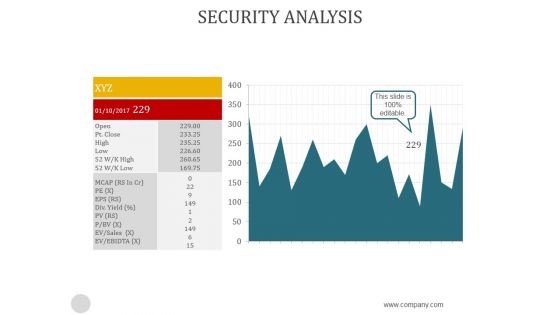
Security Analysis Ppt PowerPoint Presentation Background Image
This is a security analysis ppt powerpoint presentation background image. This is a two stage process. The stages in this process are business, analysis, strategic, finance, management.
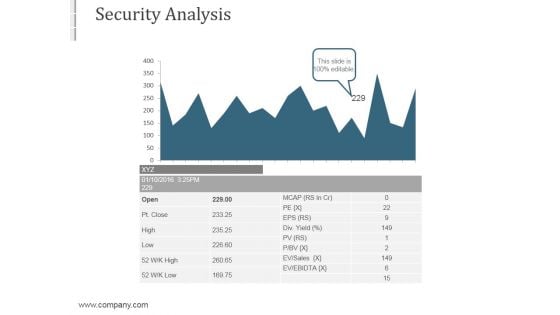
Security Analysis Ppt PowerPoint Presentation Guidelines
This is a security analysis ppt powerpoint presentation guidelines. This is a one stage process. The stages in this process are high risk, low risk.
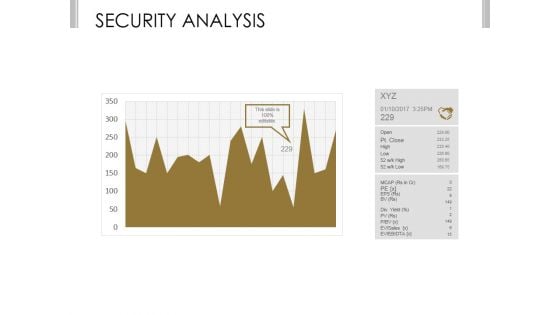
Security Analysis Ppt PowerPoint Presentation Deck
This is a security analysis ppt powerpoint presentation deck. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, growth.
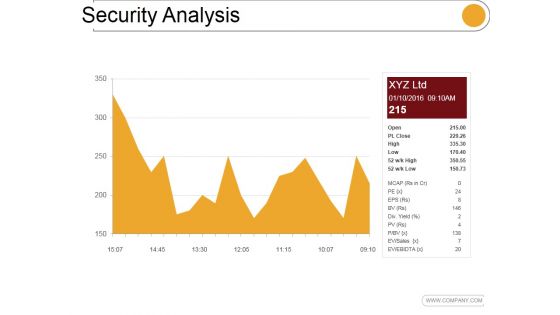
Security Analysis Ppt PowerPoint Presentation Show
This is a security analysis ppt powerpoint presentation show. This is a one stage process. The stages in this process are open, high, low, business, marketing.
Security Analysis Ppt PowerPoint Presentation File Inspiration
This is a security analysis ppt powerpoint presentation file inspiration. This is a two stage process. The stages in this process are business, growth, analysis, strategy, management.
Security Analysis Ppt Powerpoint Presentation File Tips
This is a security analysis ppt powerpoint presentation file tips. This is a one stage process. The stages in this process are graph, marketing, business, growth, finance.
Cyber Security Ppt PowerPoint Presentation Layouts Brochure
This is a cyber security ppt powerpoint presentation layouts brochure. This is a three stage process. The stages in this process are business, management, planning, strategy, marketing.

What Makes Cloud Security Different Diagrams PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi tenant storage system. This is a What Makes Cloud Security Different Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Developing, Essential Strategy, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Management Form Guidelines PDF
This slide shows information security risk acceptance form which contains accountable person details, risk acceptance summary, acceptance advantages, justification, advice, etc. This can benefit cyber security department in careful review prior to the acceptance of major risks involved. Pitch your topic with ease and precision using this Information Security Risk Management Form Guidelines PDF. This layout presents information on Risk Modification, Risk Acceptance, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
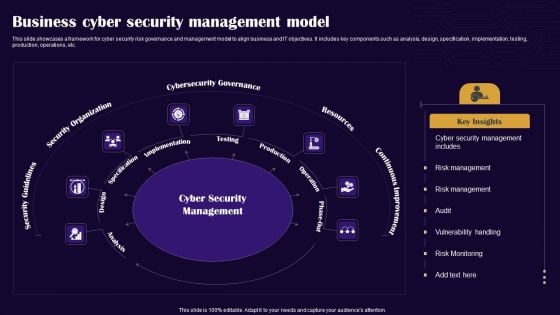
Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
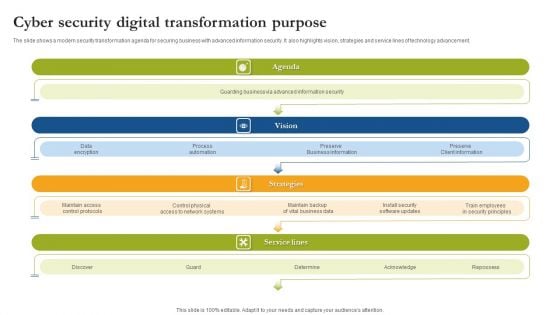
Cyber Security Digital Transformation Purpose Sample PDF
The slide shows a modern security transformation agenda for securing business with advanced information security. It also highlights vision, strategies and service lines of technology advancement. Persuade your audience using this Cyber Security Digital Transformation Purpose Sample PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Agenda, Vision, Strategies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
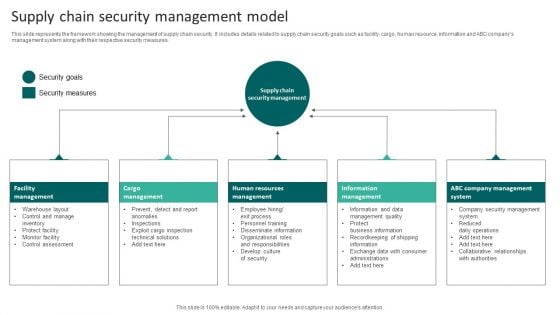
Supply Chain Security Management Model Infographics PDF
This slide represents the framework showing the management of supply chain security. It includes details related to supply chain security goals such as facility, cargo, human resource, information and ABC companys management system along with their respective security measures. Presenting Supply Chain Security Management Model Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Human Resources Management, Cargo Management, Facility Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
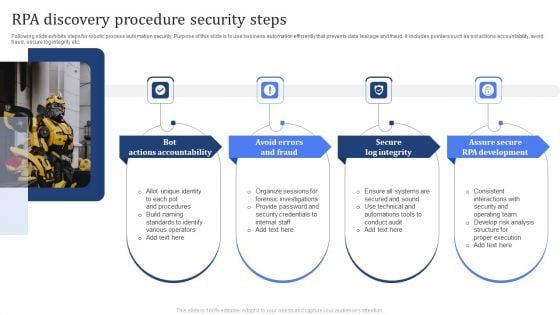
RPA Discovery Procedure Security Steps Brochure PDF
Following slide exhibits steps for robotic process automation security. Purpose of this slide is to use business automation efficiently that prevents data leakage and fraud. It includes pointers such as bot actions accountability, avoid fraud, secure log integrity etc. Presenting RPA Discovery Procedure Security Steps Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Bot Actions Accountability, Avoid Errors And Fraud, Secure Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
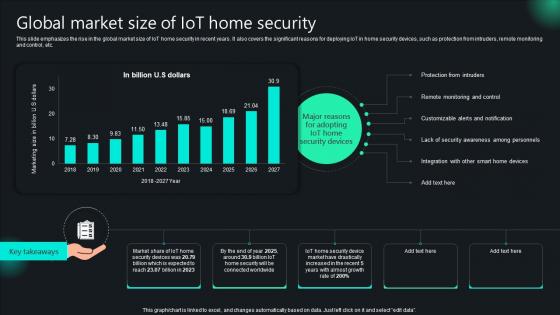
Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V
This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc. The Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc.

Agenda Of Security Risk Management Graphics PDF
This is a agenda of security risk management graphics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vulnerabilities, organizational, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Administrator Updating Information System Security Infographics PDF
Presenting administrator updating information system security infographics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including administrator updating information system security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Functional Technology Security Elements PDF
Presenting icon for functional technology security elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including icon for functional technology security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Computer Safety And Security Icon Infographics PDF
Persuade your audience using this Computer Safety And Security Icon Infographics PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Computer Safety, Security Icon Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
KPI Dashboard Metrics Security Icon Download PDF
Persuade your audience using this KPI Dashboard Metrics Security Icon Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Kpi Dashboard, Metrics Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
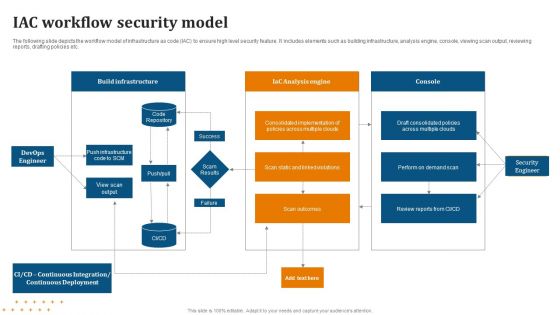
IAC Workflow Security Model Diagrams PDF
Showcasing this set of slides titled IAC Workflow Security Model Diagrams PDF. The topics addressed in these templates are Workflow, Security Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
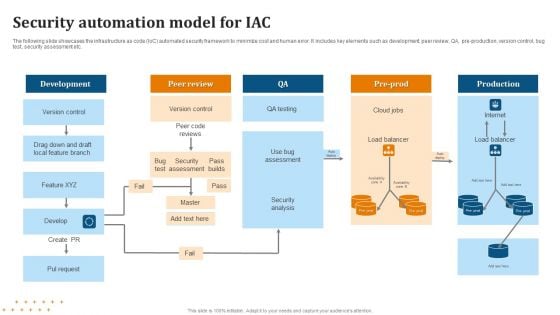
Security Automation Model For IAC Summary PDF
Pitch your topic with ease and precision using this Security Automation Model For IAC Summary PDF. This layout presents information on Security Automation, Model For IAC . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Data Storage Security Management Icon Professional PDF
Presenting Data Storage Security Management Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Storage, Security, Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Secure Computer Database Access Icon Slides PDF
Presenting Secure Computer Database Access Icon Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Secure, Computer, Database Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Payment Card Security Processing Icon Portrait PDF
Presenting Payment Card Security Processing Icon Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Payment Card Security, Processing Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Computing Security Architecture Icon Slides PDF
Presenting Cloud Computing Security Architecture Icon Slides PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Employee Training Record With Participant Record Ppt PowerPoint Presentation Pictures Background PDF
Presenting this set of slides with name employee training record with participant record ppt powerpoint presentation pictures background pdf. The topics discussed in these slides are department, designation, verification training effectiveness, verification criteria, satisfactory. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
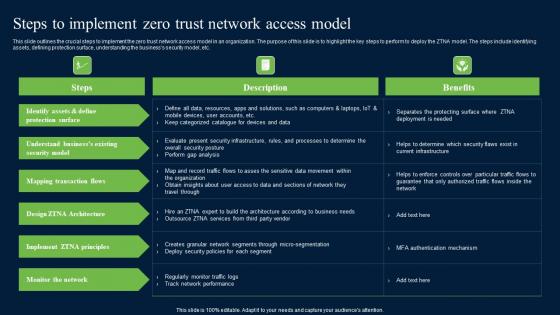
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.
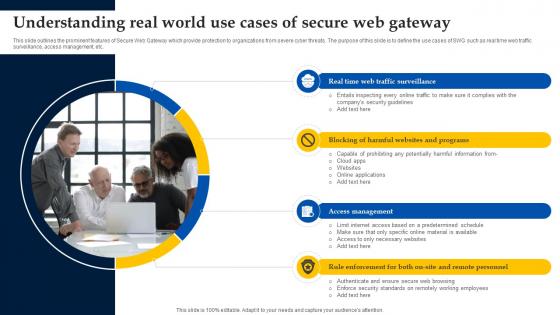
Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.
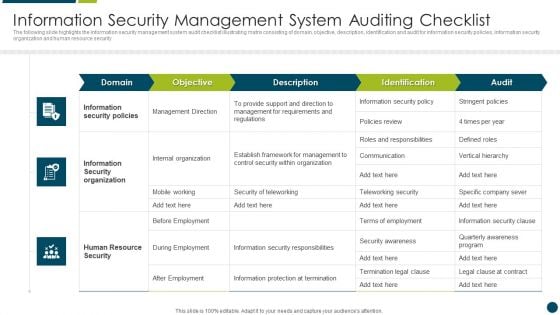
Information Security Management System Auditing Brochure PDF
The following slide highlights the information security management system audit process illustrating information security system details, information collection, statement o applicability review, audit scope, risk management analysis, gap analysis, business continuity and contingency plan review, mitigation strategy and compliance audit activities PresentingInformation Security Management System Auditing Brochure PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Risk Management Analysis, Information Collection, Mitigation Strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully
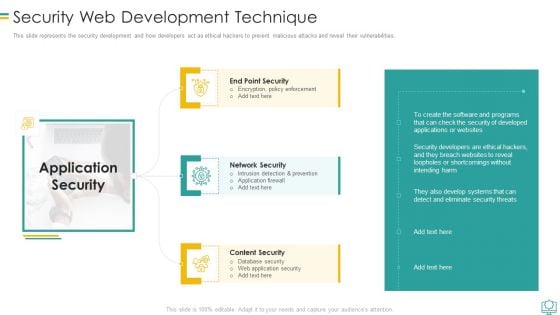
Security Web Development Technique Mockup PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Security Web Development Technique Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection And Prevention, Encryption Policy Enforcement, Database Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Access Control Rules PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Presenting Cloud Security Checklist Access Control Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Systems, Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Segmentation Of Cloud Security Responsibilities Icons PDF
This slide shows cloud security responsibilities based on service type, namely Software as a Service SaaS, Platform as a service PaaS, Infrastructure as a Service IaaS. Presenting Segmentation Of Cloud Security Responsibilities Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cloud Security Responsibilities, Segmentation, Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Does Cloud Security Work Download PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. This is a How Does Cloud Security Work Download PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organizations, Encryption Methods, Secure Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
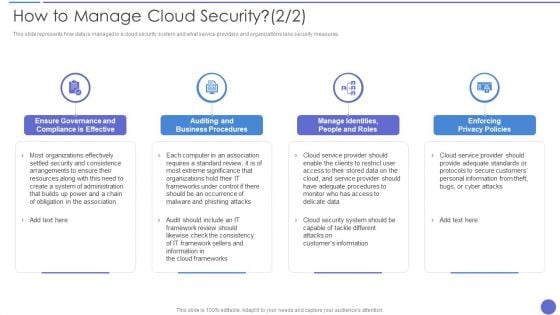
How To Manage Cloud Security Topics PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures. This is a How To Manage Cloud Security Topics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enforcing Privacy Policies, Auditing And Business Procedures, Organizations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
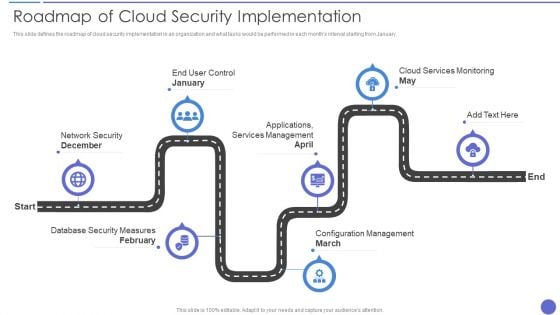
Roadmap Of Cloud Security Implementation Infographics PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Roadmap Of Cloud Security Implementation Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Applications Services Management, Cloud Services Monitoring, Network Security December. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Risk Mitigation Framework Demonstration PDF
The following slide showcases the risk mitigation framework to plan preventive and reactive actions. It includes elements such as categorize, select, implement, assess, authorize and monitor etc. Persuade your audience using this Cyber Security Risk Mitigation Framework Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Categorize System, Select Security Controls, Implement Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
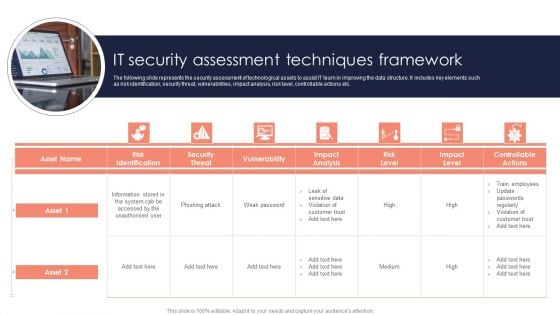
It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
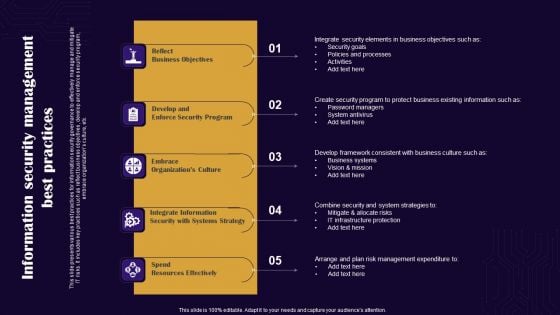
Information Security Management Best Practices Themes PDF
This slide presents various best practices for information security governance to effectively manage and mitigate IT risks. It includes key practices such as reflect business objectives, develop and enforce security program, embrace organizations culture, etc. Presenting Information Security Management Best Practices Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Reflect Business Objectives, Spend Resources Effectively, Embrace Organizations Culture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Process Success PowerPoint Templates And PowerPoint Themes 0512
Security Process Success PowerPoint Templates And PowerPoint Themes PPT designs-Microsoft Powerpoint Templates and Background with security process Encourage your community to take action. Get them to back the cause you champion.

Stock Photo Business Strategy Innovation Make Secure Folder Images
Our stock photo business strategy innovation make secure folder stock photo images Powerpoint Templates Heighten Concentration. Your Audience Will Be On The Edge. Get An Edge With Our Security Powerpoint Templates. They Give You Advantage Plus.

Stock Photo 3d Dollars Stack Unlocked Security Concept PowerPoint Slide
Graphic of dollar bundle is inside the lock is used in this power point image template. We have displayed concept of financial security in this image. Use this image for security or finance related topics.
Information Security Outsourcing Ppt PowerPoint Presentation Styles Outfit Cpb
This is a information security outsourcing ppt powerpoint presentation styles outfit cpb. This is a four stage process. The stages in this process are information security outsourcing, planning, business, management, marketing.

Digital Files Security PowerPoint Template 1110
3d illustration of transparent binary and html data revolving around an open file folder Examine every deatail with our Digital Files Security PowerPoint Template 1110. Put each element to the test.

Data Is Secure Internet PowerPoint Template 1110
3d illustration of a lock sitting in front of a computer display showing a file folder Approve plans with our Data Is Secure Internet PowerPoint Template 1110. You will come out on top.

Laptop Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with rendered illustration of a laptop with chains and lock around screen Challenge old thoughts with our Laptop Security PowerPoint Backgrounds And Templates 1210. You will come out on top.

Flag American Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with flag american with gun creative actual for designer Distill your thoughts with our Flag American Security PowerPoint Presentation Slides C. They will draw outthe essence of it all.


 Continue with Email
Continue with Email

 Home
Home


































