Authentication
Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF
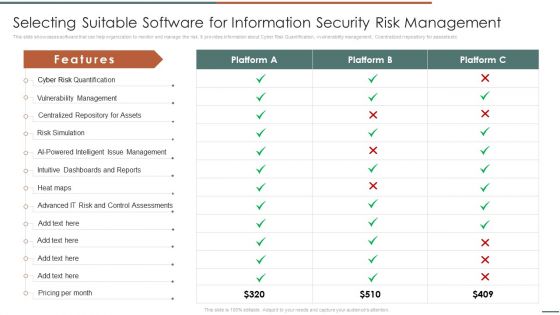
This slide showcases software that can help organization to monitor and manage the risk. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc .Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF. Use them to share invaluable insights on Vulnerability Management, Centralized Repository, Intelligent Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
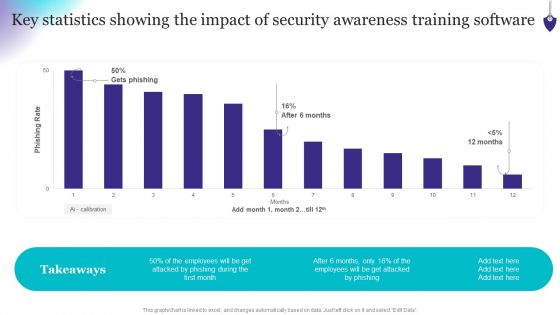
Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
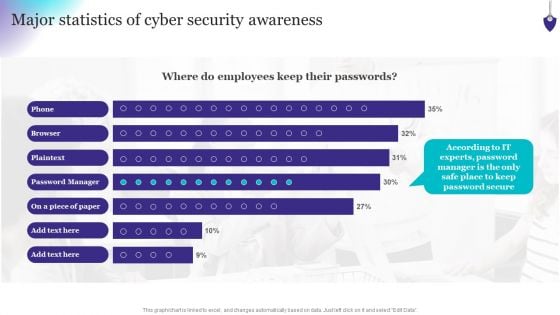
Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Welcome to our selection of the Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
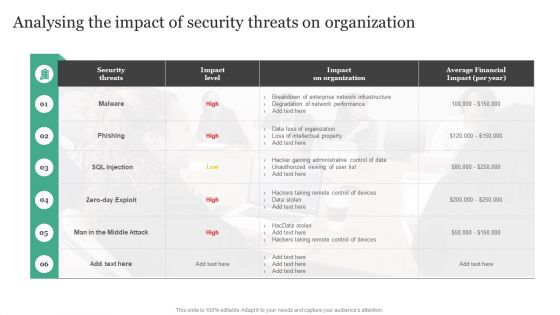
Analysing The Impact Of Security Threats On Organization Information Security Risk Administration Sample PDF
The Analysing The Impact Of Security Threats On Organization Information Security Risk Administration Sample PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
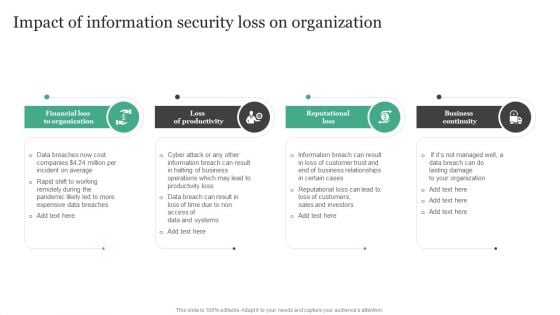
Impact Of Information Security Loss On Organization Information Security Risk Administration Infographics PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Impact Of Information Security Loss On Organization Information Security Risk Administration Infographics PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
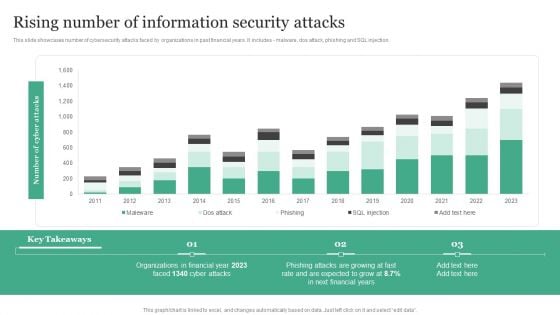
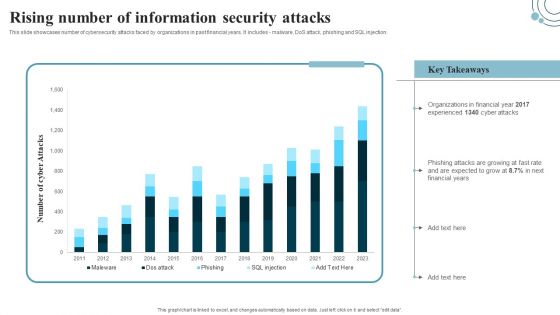
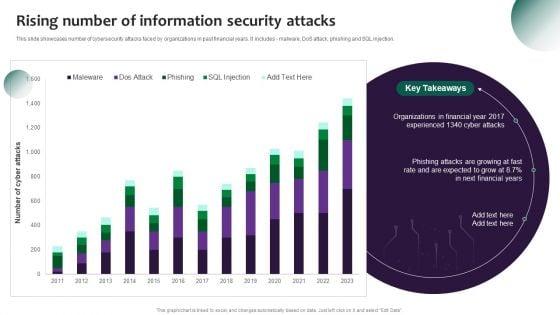
Rising Number Of Information Security Attacks Information Security Risk Administration Information PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes - malware, dos attack, phishing and SQL injection.Find a pre-designed and impeccable Rising Number Of Information Security Attacks Information Security Risk Administration Information PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
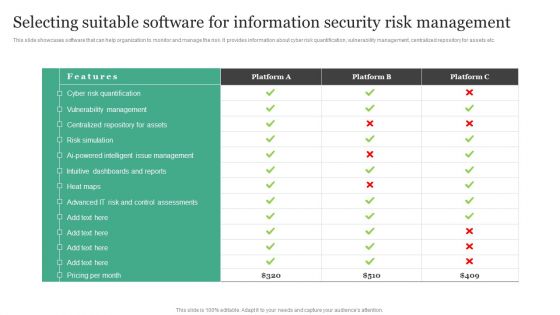
Selecting Suitable Software For Information Security Risk Management Information Security Risk Administration Sample PDF
This slide showcases software that can help organization to monitor and manage the risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. Want to ace your presentation in front of a live audience Our Selecting Suitable Software For Information Security Risk Management Information Security Risk Administration Sample PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
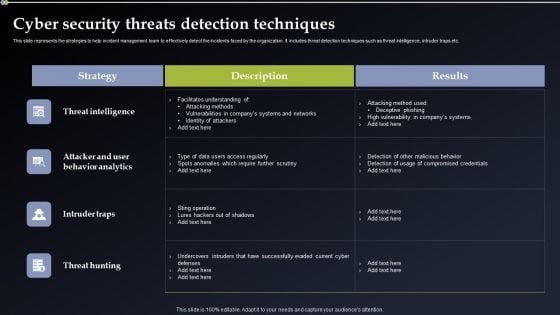
Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Want to ace your presentation in front of a live audience Our Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
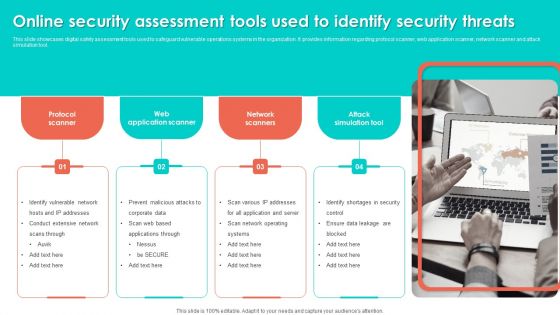
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
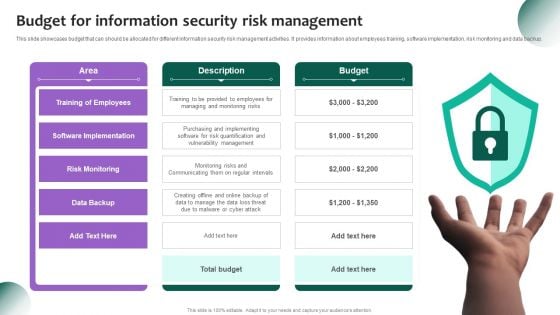
Information Systems Security And Risk Management Plan Budget For Information Security Risk Management Guidelines PDF
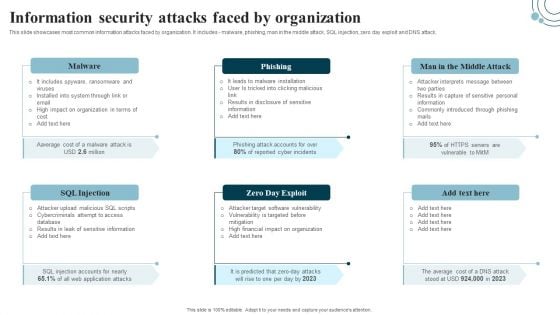
This slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Systems Security And Risk Management Plan Budget For Information Security Risk Management Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

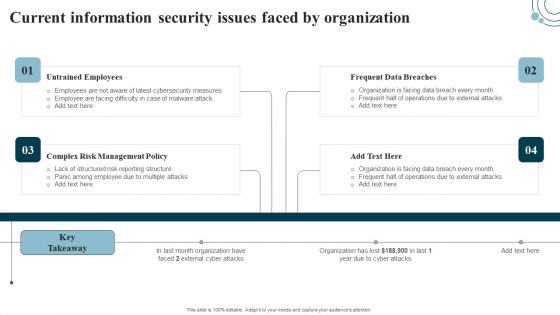
Information Systems Security And Risk Management Plan Current Information Security Issues Faced By Organization Rules PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Information Systems Security And Risk Management Plan Current Information Security Issues Faced By Organization Rules PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information Systems Security And Risk Management Plan Mitigation Strategies To Tackle Information Security Threats Information PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Systems Security And Risk Management Plan Mitigation Strategies To Tackle Information Security Threats Information PDF from Slidegeeks and deliver a wonderful presentation.
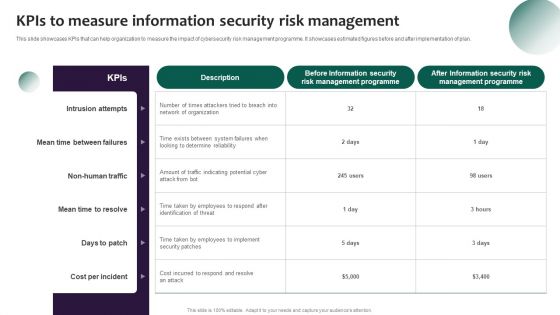
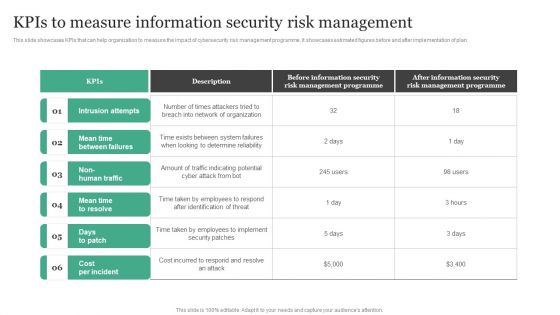
Information Systems Security And Risk Management Plan Kpis To Measure Information Security Risk Management Template PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Want to ace your presentation in front of a live audience Our Information Systems Security And Risk Management Plan Kpis To Measure Information Security Risk Management Template PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
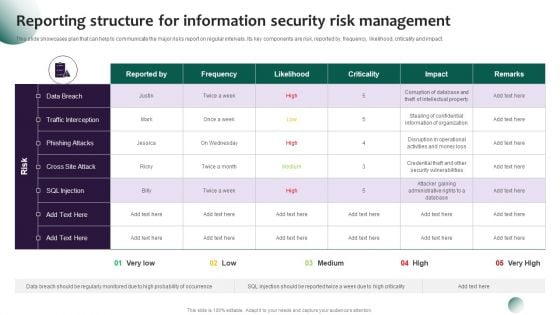
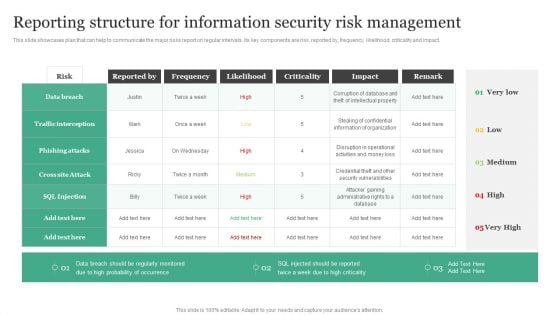
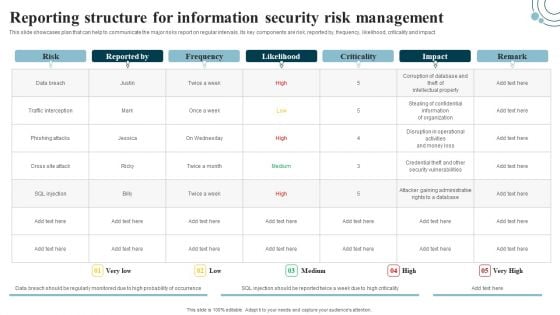
Information Systems Security And Risk Management Plan Reporting Structure For Information Security Risk Management Demonstration PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. This Information Systems Security And Risk Management Plan Reporting Structure For Information Security Risk Management Demonstration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Developing IT Security Strategy Current Information Security Issues Faced By Organization Pictures PDF
The Developing IT Security Strategy Current Information Security Issues Faced By Organization Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Developing IT Security Strategy Rising Number Of Information Security Attacks Graphics PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes - malware, DoS attack, phishing and SQL injection. This modern and well-arranged Developing IT Security Strategy Rising Number Of Information Security Attacks Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
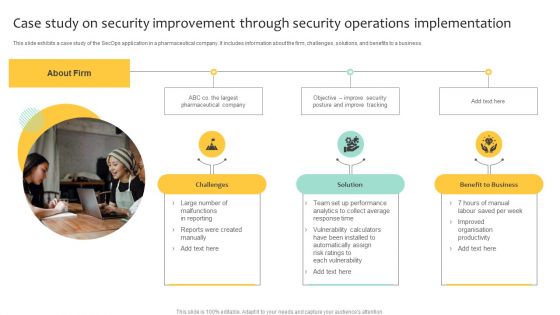
Case Study On Security Improvement Through Security Operations Implementation Mockup PDF
This slide exhibits a case study of the SecOps application in a pharmaceutical company. It includes information about the firm, challenges, solutions, and benefits to a business. Persuade your audience using this Case Study On Security Improvement Through Security Operations Implementation Mockup PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Benefit To Business, Organisation Productivity, Average. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Series Of Cyber Security Attacks Against Ukraine 2022 Hybrid Warfare Cyber Rapid Response Team CRRT Themes PDF
This slide talks about the cyber rapid response team deployed to protect ukraine from russian cyber attacks, including experts from lithuania, croatia, poland, estonia, romania, and the netherlands. Want to ace your presentation in front of a live audience Our Series Of Cyber Security Attacks Against Ukraine 2022 Hybrid Warfare Cyber Rapid Response Team CRRT Themes PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Safety Lock Cyber Security Global Security Ppt PowerPoint Presentation Complete Deck
Boost your confidence and team morale with this well-structured safety lock cyber security global security ppt powerpoint presentation complete deck. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of fourteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
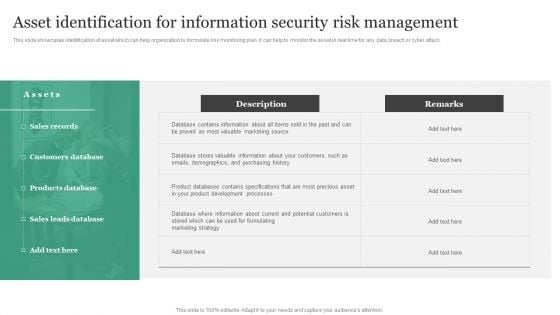
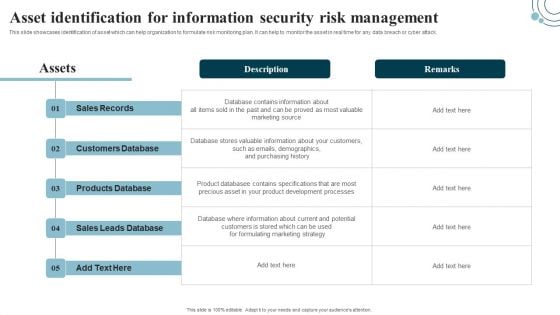
Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Slidegeeks has constructed Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.This modern and well-arranged Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Reporting Structure For Information Security Risk Management Information Security Risk Administration Elements PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Do you know about Slidesgeeks Reporting Structure For Information Security Risk Management Information Security Risk Administration Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
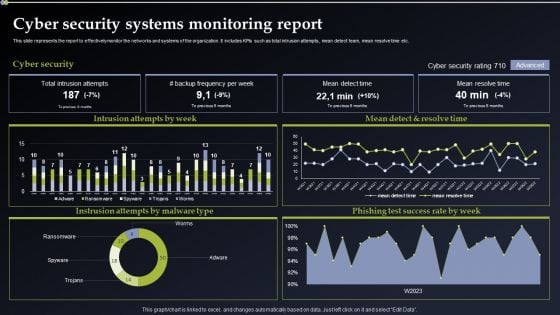
Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Slidegeeks is here to make your presentations a breeze with Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. Take your projects to the next level with our ultimate collection of Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
Information Systems Security And Risk Management Plan Rising Number Of Information Security Attacks Information PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes - malware, DoS attack, phishing and SQL injection. Welcome to our selection of the Information Systems Security And Risk Management Plan Rising Number Of Information Security Attacks Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Developing IT Security Strategy Information Security Attacks Faced By Organization Rules PDF
This slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Slidegeeks is here to make your presentations a breeze with Developing IT Security Strategy Information Security Attacks Faced By Organization Rules PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Developing IT Security Strategy Reporting Structure For Information Security Risk Sample PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Reporting Structure For Information Security Risk Sample PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present like a pro with Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
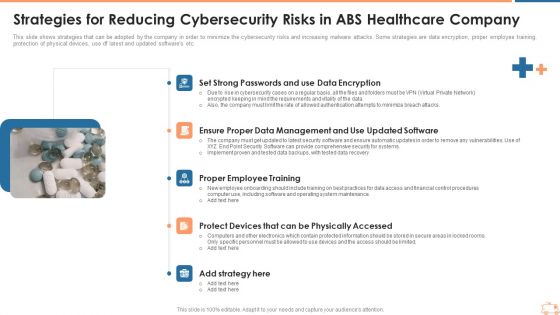
Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Rules PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Presenting strategies for reducing cybersecurity risks in abs healthcare company rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like set strong passwords and use data encryption, proper employee training, protect devices that can be physically accessed, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Ppt Gallery Background Images PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Deliver an awe inspiring pitch with this creative strategies for reducing cybersecurity risks in abs healthcare company ppt gallery background images pdf bundle. Topics like set strong passwords and use data encryption, ensure proper data management and use updated software, proper employee training, protect devices that can be physically accessed, strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Administration Strategy Security Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this security administration strategy security ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Payroll Automation Benefits In Organization Industry Ppt Layouts Graphics Download PDF
The following slide highlights application of payroll automation in business industry for quick report preparation and reduce verification time to enhance employee morale. It includes components such as timekeeping, overtime compensation approvals, employment verification, commissions and payroll taxes etc. Presenting Payroll Automation Benefits In Organization Industry Ppt Layouts Graphics Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Timekeeping, Employment Verification, Commissions . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

HML Analysis For Inventory Management Tactical Guide Stock Administration Inspiration Pdf
This slide showcases HML analysis method that can help organization in inventory management. It categorized inventory into high, medium and low priced items which can help to determine the verification frequency of different type of stock categories. This slide showcases HML analysis method that can help organization in inventory management. It categorized inventory into high, medium and low priced items which can help to determine the verification frequency of different type of stock categories. This slide showcases HML analysis method that can help organization in inventory management. It categorized inventory into high, medium and low priced items which can help to determine the verification frequency of different type of stock categories.

Food Adulteration Defense Prevention Strategy Template Pdf
This slide provides information about bulk liquor receiving fraud mitigation plan. It includes element such as mitigation strategy, food defense monitoring, food defense action and record verification Showcasing this set of slides titled Food Adulteration Defense Prevention Strategy Template Pdf. The topics addressed in these templates are Mitigation Strategy, Defense Monitoring, Record Verification. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provides information about bulk liquor receiving fraud mitigation plan. It includes element such as mitigation strategy, food defense monitoring, food defense action and record verification

Stock Photo Graphics Of Padlock With Us Dollar Pwerpoint Slide
This business image has been designed with graphic of padlock with US dollar. This image contains the concept of finance and security. Make a quality presentation for financial security.

Stock Photo Textured Lock With Us Dollar Pwerpoint Slide
This business image has been designed with graphic of textured lock with US dollar. This image contains the concept of finance and security. Make a quality presentation for financial security.

Stock Photo Us Dollar Lock With Golden Keys Pwerpoint Slide
This business image has been crafted with graphic of US dollar lock and golden keys. This image contains the concept of finance and security related presentation. Build a strong presentation for wealth management and security.

Stock Photo Dollar Covered With Chain Financial Safety PowerPoint Slide
This Power Point image template has been crafted with graphic of dollar. Dollar is covered with chain which shows the concept of security. Use this image template financial security related presentations.
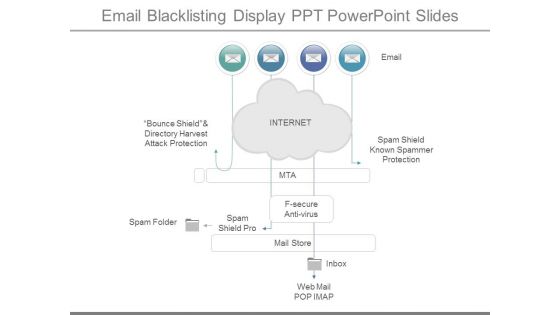
Email Blacklisting Display Ppt Powerpoint Slides
This is a email blacklisting display ppt powerpoint slides. This is a one stage process. The stages in this process are email, spam shield known spammer protection, internet, bounce shield and directory harvest attack protection, mta, spam folder, spam shield pro, f secure anti virus, mail store, inbox, web mail pop imap.

Process Of Enterprise Mobility Solutions Ppt Powerpoint Slide Themes
This is a process of enterprise mobility solutions ppt powerpoint slide themes. This is a eight stage process. The stages in this process are user and app access, app and data protection, device management, threat protection, secure file sharing, cost and resources, augment income, easy access to confidential data.
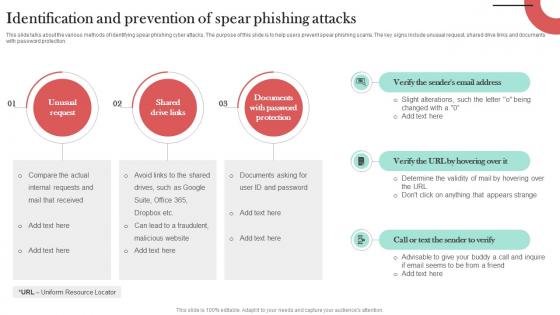
Identification And Prevention Of Spear Man In The Middle Phishing IT
This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Presenting this PowerPoint presentation, titled Identification And Prevention Of Spear Man In The Middle Phishing IT, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Identification And Prevention Of Spear Man In The Middle Phishing IT. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Identification And Prevention Of Spear Man In The Middle Phishing IT that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection.

Uniformed Security Proposal For Security Guard Services Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of twenty three slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

The Problem Challenges Tools Ppt Slides
This is a the problem challenges tools ppt slides. This is a four stage process. The stages in this process are business, industrial, security, success.
Vertical Chart For Solution Powerpoint Slide Designs
This is a vertical chart for solution powerpoint slide designs. This is a six stage process. The stages in this process are business, success, management, strategy, security.
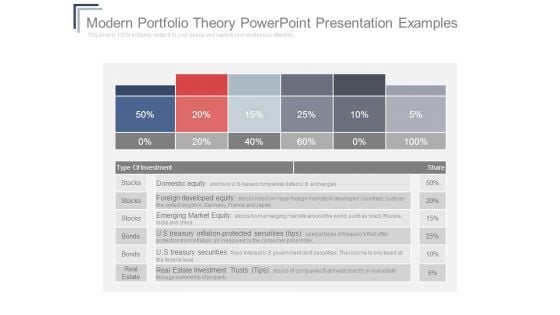
Modern Portfolio Theory Powerpoint Presentation Examples
This is a modern portfolio theory powerpoint presentation examples. This is a six stage process. The stages in this process are u s treasury securities, domestic equity, foreign developed equity, emerging market equity, u s treasury inflation protected securities tips, u s treasury securities, real estate investment trusts tips, type of investment, stocks, bonds, real estate.

Stock Photo Business Intelligence Strategy Theme Of Key To Success Pictures Images
Extract Admiration From The Audience. Create A Forceful Impact With Our stock photo business intelligence strategy theme of key to success pictures images. Force Doors Open With Our security. The Audience Will Decide To Let Your Thoughts Enter.
Stock Photo Business Model Strategy Keys For Terms Best
Actualize The Dreams Of Your Forefathers. Bring Them To The Forefront With Our stock photo business model strategy keys for terms best. Put Your Ideas In The Forefront. Our security Will Back Your Call.
Stock Photo Basic Marketing Concepts Illustration Of Key Innovation Business Pictures Images
Get The Doers Into Action. Activate Them With Our stock photo basic marketing concepts illustration of key innovation business pictures images Powerpoint Templates. Put Your Money On Our Security Powerpoint Templates. Your Ideas Will Rake In The Dollars.
Stock Photo Basic Marketing Concepts Illustration Of Key To Success Business Pictures Images
Put In A Dollop Of Our stock photo basic marketing concepts illustration of key to success business pictures images Powerpoint Templates. Give Your Thoughts A Distinctive Flavor. Create Your Domain With Our Security Powerpoint Templates. Rule Minds With Your Thoughts.
Stock Photo Business And Strategy Find The Key Of Solution Clipart Images
Connect The Dots With Our stock photo business and strategy find the key of solution clipart images Powerpoint Templates. Watch The Whole Picture Clearly Emerge. Dot Your Thoughts With Our Security Powerpoint Templates. Give Your Demeanor That Propel Look.
Stock Photo Business Development Strategy Illustration Of Key Solution Clipart Images
Land The Idea With Our stock photo business development strategy illustration of key solution clipart images Powerpoint Templates. Help It Grow With Your Thoughts. Cover The Compass With Our Security Powerpoint Templates. Your Ideas Will Be Acceptable To All.

Stock Photo Business Expansion Strategy Key Of Strategies Pictures
Draft It Out On Our stock photo business expansion strategy key of strategies pictures Powerpoint Templates. Give The Final Touches With Your Ideas. Get A Bakers Dozen With Our Security Powerpoint Templates. Receive That Little Bit More Than Expected.

Stock Photo Business Strategy Execution Keys Of Success And Growth Clipart
Delight Them With Our Stock Photo Business Strategy Execution Keys Of Success And Growth Clipart Powerpoint Templates. Your Audience Will Be Ecstatic. Our Security Powerpoint Templates Are Created Cost Effective. They Understand The Need For Economy.

Business Diagram Lock With Puzzle Strategy Concept Presentation Template
This business diagram template has been crafted with graphic of puzzle. This diagram contains the concept of strategy building and safety. Use this diagram for your business and security related presentations.

Stock Photo Pile Of Dollars Chained And Locked PowerPoint Slide
This image displays dollar bundles locked in chains. Use this image slide, in your PowerPoint presentations to express views on financial security and monetary savings. This image will enhance the quality of your presentations.
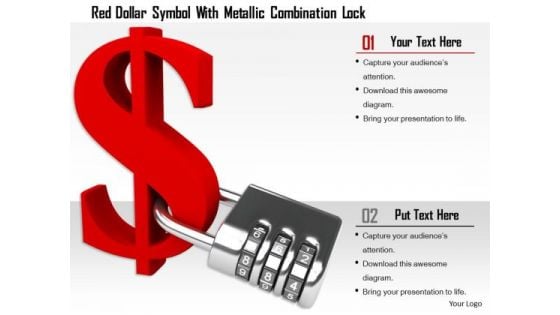
Stock Photo Red Dollar Symbol With Metallic Combination Lock PowerPoint Slide
This image slide displays red color dollar symbol with combination lock. Use this image, in your PowerPoint presentations to express views on financial security and monetary savings. This image slide will enhance the quality of your presentations.


 Continue with Email
Continue with Email

 Home
Home


































