Authentication
Cloud Computing Infra Cyber Security Icon Sample PDF
Presenting Cloud Computing Infra Cyber Security Icon Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Infra Cyber, Security Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Infra Cyber Security Icon For Eliminating Cyber Threats Designs PDF
Presenting Infra Cyber Security Icon For Eliminating Cyber Threats Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infra Cyber Security Icon, Eliminating Cyber Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Icon For Cyber Threat Prevention Information PDF
Presenting Cyber Security Icon For Cyber Threat Prevention Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cyber Security, Icon Cyber Threat, Prevention. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Critical Importance Of HR Security At Workplace Demonstration PDF
Showcasing this set of slides titled Critical Importance Of HR Security At Workplace Demonstration PDF. The topics addressed in these templates are Critical Importance, HR Security Workplace. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Evaluation Of HR Security Policy And Procedure Diagrams PDF
Persuade your audience using this Evaluation Of HR Security Policy And Procedure Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluation HR Security, Policy Procedure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Hazards Management Program Icon Slides PDF
Persuade your audience using this Cyber Security Hazards Management Program Icon Slides PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Management Program. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Change Analysis And Evaluation Icon Ideas PDF
Presenting Security Change Analysis And Evaluation Icon Ideas PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Change, Analysis And Evaluation Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Security Attack Incident Communication Plan Icon Professional PDF
Showcasing this set of slides titled IT Security Attack Incident Communication Plan Icon Professional PDF. The topics addressed in these templates are IT Security Attack, Incident Communication, Plan Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Communication Plan Development Icon Portrait PDF
Presenting IT Security Communication Plan Development Icon Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including IT Security Communication, Plan Development Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Security Communication Plan Development Strategy Icon Professional PDF
Showcasing this set of slides titled IT Security Communication Plan Development Strategy Icon Professional PDF. The topics addressed in these templates are IT Security Communication, Plan Development Strategy Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cloud Computing Safety And Security Architecture Icon Download PDF
Presenting Cloud Computing Safety And Security Architecture Icon Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing Safety, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Motion Smart Sensor Technology For Security Improvement Icon Mockup PDF
Presenting Motion Smart Sensor Technology For Security Improvement Icon Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Motion Smart, Sensor Technology, Security Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Virtual Coinage Icon For Secured Payment System Professional PDF
Presenting Virtual Coinage Icon For Secured Payment System Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Virtual Coinage Icon, Secured Payment System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Best Data Security Software 30 60 90 Days Plan For Company Online Database Security Proposal Sample PDF
Presenting this set of slides with name best data security software 30 60 90 days plan for company online database security proposal sample pdf. This is a three stage process. The stages in this process are 30 60 90 days plan, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Malicious Icons PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with malicious icons pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
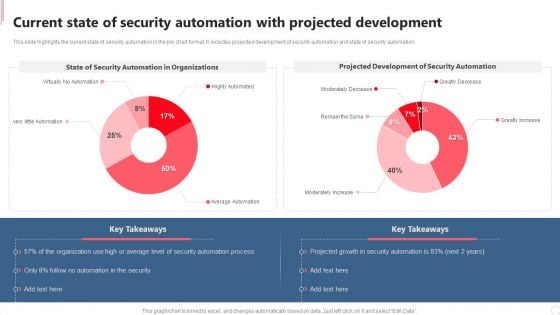
Current State Of Security Automation With Projected Development Rules PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed Current State Of Security Automation With Projected Development Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Current State Of Security Automation With Projected Development Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
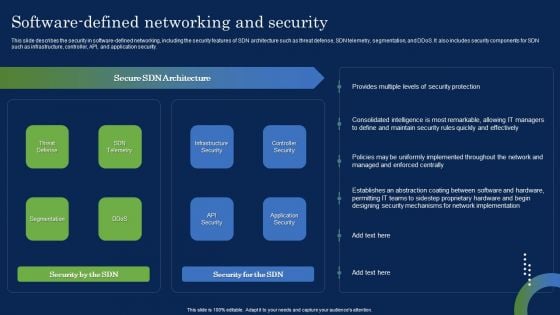
Deploying SDN System Software Defined Networking And Security Mockup PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Deploying SDN System Software Defined Networking And Security Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
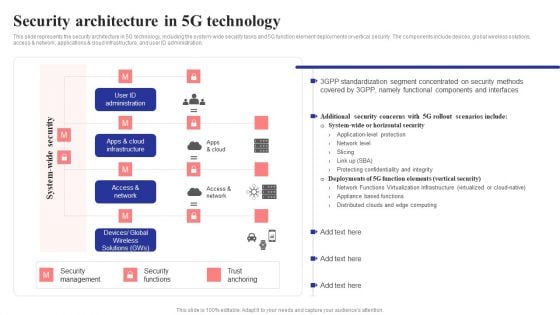
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
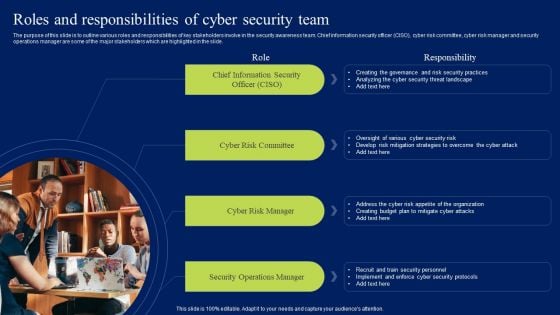
Roles And Responsibilities Of Cyber Security Team Ppt Portfolio
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roles And Responsibilities Of Cyber Security Team Ppt Portfolio can be your best option for delivering a presentation. Represent everything in detail using Roles And Responsibilities Of Cyber Security Team Ppt Portfolio and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
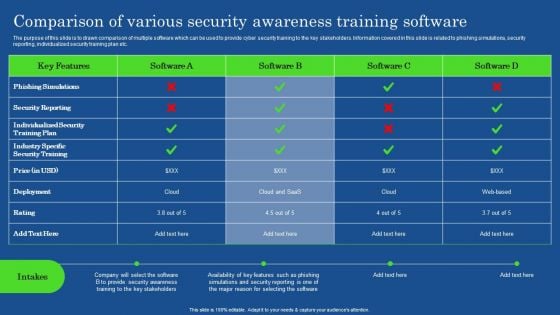
Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
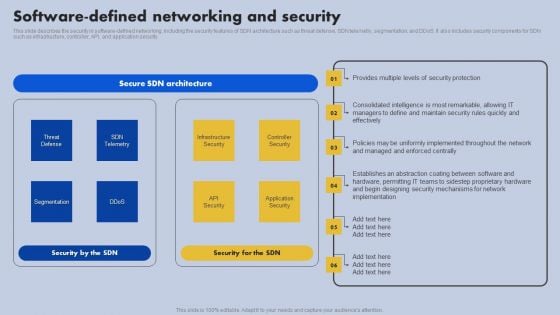
Software Defined Networking And Security Ppt Styles Slides PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is here to make your presentations a breeze with Software Defined Networking And Security Ppt Styles Slides PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
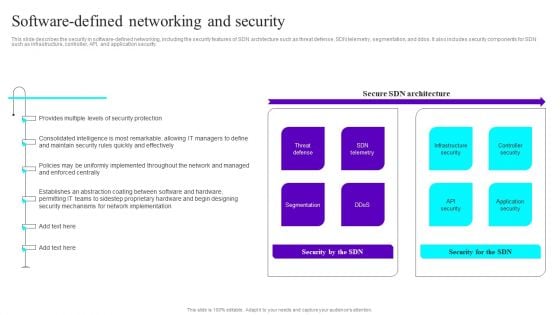
Software Defined Networking And Security Ppt Slides File Formats PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is here to make your presentations a breeze with Software Defined Networking And Security Ppt Slides File Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF
This slide depicts the main tasks of the command security operations center. The purpose of this slide is to highlight the main responsibilities, responsible team members, and task status. The main tasks include monitoring and analyzing security events, coordinating incident response, managing security operations, etc. Get a simple yet stunning designed Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
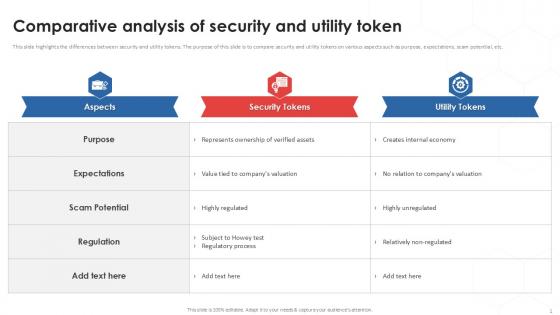
Comparative Analysis Of Tokenization Strategies For Data Security PPT Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Find a pre-designed and impeccable Comparative Analysis Of Tokenization Strategies For Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc.
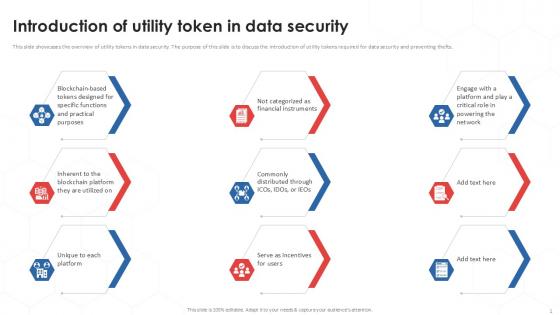
Introduction Of Utility Tokenization Strategies For Data Security PPT Presentation
This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Boost your pitch with our creative Introduction Of Utility Tokenization Strategies For Data Security PPT Presentation. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts.
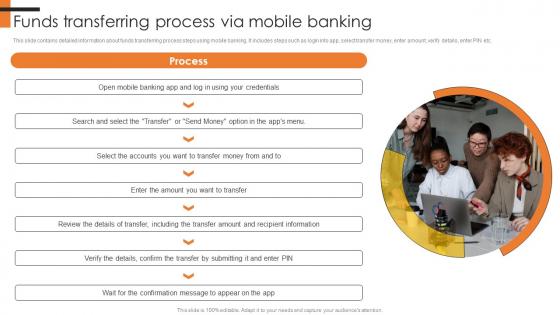
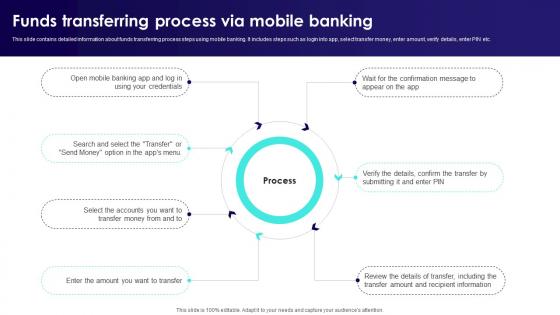
Funds Transferring Process Via Mobile Banking Comprehensive Smartphone Banking Structure Pdf
This slide contains detailed information about funds transferring process steps using mobile banking. It includes steps such as login into app, select transfer money, enter amount, verify details, enter PIN etc.This modern and well-arranged Funds Transferring Process Via Mobile Banking Comprehensive Smartphone Banking Structure Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide contains detailed information about funds transferring process steps using mobile banking. It includes steps such as login into app, select transfer money, enter amount, verify details, enter PIN etc.
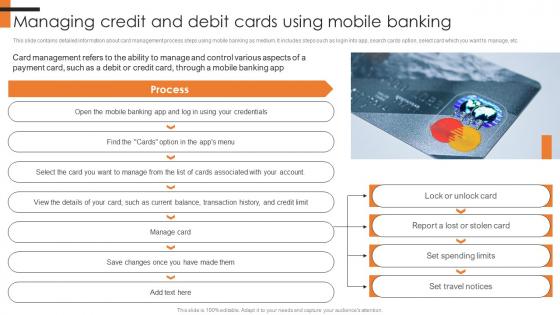
Managing Credit And Debit Cards Using Mobile Comprehensive Smartphone Banking Slides Pdf
This slide contains detailed information about card management process steps using mobile banking as medium. It includes steps such as login into app, search cards option, select card which you want to manage, etc. Boost your pitch with our creative Managing Credit And Debit Cards Using Mobile Comprehensive Smartphone Banking Slides Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide contains detailed information about card management process steps using mobile banking as medium. It includes steps such as login into app, search cards option, select card which you want to manage, etc.
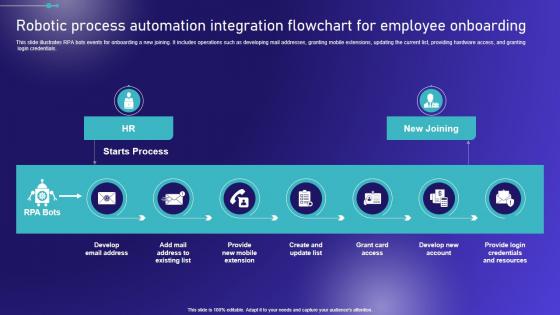
Robotic Process Automation Integration Embracing Robotic Process Sample PDF
This slide illustrates RPA bots events for onboarding a new joining. It includes operations such as developing mail addresses, granting mobile extensions, updating the current list, providing hardware access, and granting login credentials. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Robotic Process Automation Integration Embracing Robotic Process Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide illustrates RPA bots events for onboarding a new joining. It includes operations such as developing mail addresses, granting mobile extensions, updating the current list, providing hardware access, and granting login credentials.
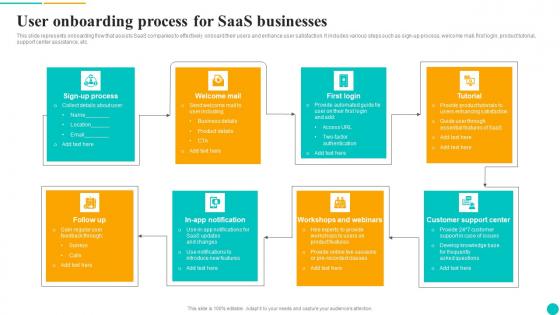
User Onboarding Process For Saas Businesses Mockup Pdf
This slide represents onboarding flow that assists SaaS companies to effectively onboard their users and enhance user satisfaction. It includes various steps such as sign-up process, welcome mail, first login, product tutorial, support center assistance, etc. Showcasing this set of slides titled User Onboarding Process For Saas Businesses Mockup Pdf. The topics addressed in these templates are Welcome Mail, Follow Up, Workshops And Webinars. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents onboarding flow that assists SaaS companies to effectively onboard their users and enhance user satisfaction. It includes various steps such as sign-up process, welcome mail, first login, product tutorial, support center assistance, etc.
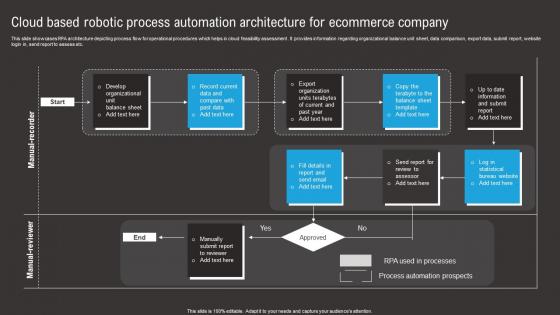
Cloud Based Robotic Process Automation Architecture For Ecommerce Company Mockup Pdf
This slide showcases RPA architecture depicting process flow for operational procedures which helps in cloud feasibility assessment . It provides information regarding organizational balance unit sheet, data comparison, export data, submit report, website login in, send report to assess etc. Showcasing this set of slides titled Cloud Based Robotic Process Automation Architecture For Ecommerce Company Mockup Pdf. The topics addressed in these templates are Balance Sheet, Past Data, Export Organization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases RPA architecture depicting process flow for operational procedures which helps in cloud feasibility assessment . It provides information regarding organizational balance unit sheet, data comparison, export data, submit report, website login in, send report to assess etc.
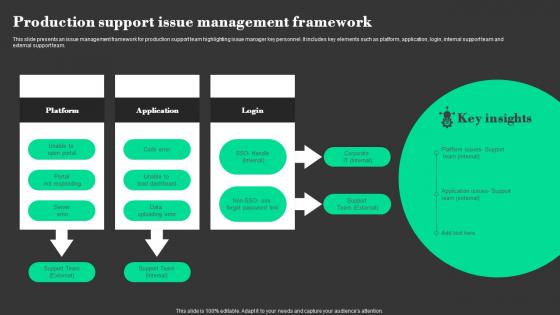
Production Support Issue Management Framework Guidelines Pdf
This slide presents an issue management framework for production support team highlighting issue manager key personnel. It includes key elements such as platform, application, login, internal support team and external support team. Pitch your topic with ease and precision using this Production Support Issue Management Framework Guidelines Pdf This layout presents information on Platform, Application, Server Error, Load Dashboard It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents an issue management framework for production support team highlighting issue manager key personnel. It includes key elements such as platform, application, login, internal support team and external support team.
Wireless Banking To Improve Funds Transferring Process Via Mobile Banking Fin SS V
This slide contains detailed information about funds transferring process steps using mobile banking. It includes steps such as login into app, select transfer money, enter amount, verify details, enter PIN etc. Are you searching for a Wireless Banking To Improve Funds Transferring Process Via Mobile Banking Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wireless Banking To Improve Funds Transferring Process Via Mobile Banking Fin SS V from Slidegeeks today. This slide contains detailed information about funds transferring process steps using mobile banking. It includes steps such as login into app, select transfer money, enter amount, verify details, enter PIN etc.
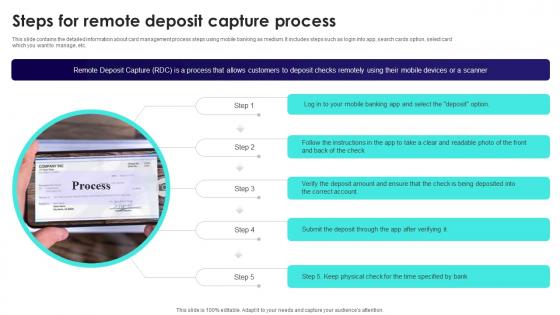
Wireless Banking To Improve Steps For Remote Deposit Capture Process Fin SS V
This slide contains the detailed information about card management process steps using mobile banking as medium. It includes steps such as login into app, search cards option, select card which you want to manage, etc. This modern and well-arranged Wireless Banking To Improve Steps For Remote Deposit Capture Process Fin SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide contains the detailed information about card management process steps using mobile banking as medium. It includes steps such as login into app, search cards option, select card which you want to manage, etc.

Decoding Data Utilized From Instagram Account Everything To Know About Instagram Threads AI SS V
This slide provides information regarding types of data utilized from the Instagram account over Threads such as the users login information, followers, profile information, accounts the user follows, account status, etc. Create an editable Decoding Data Utilized From Instagram Account Everything To Know About Instagram Threads AI SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Decoding Data Utilized From Instagram Account Everything To Know About Instagram Threads AI SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding types of data utilized from the Instagram account over Threads such as the users login information, followers, profile information, accounts the user follows, account status, etc.

Topics That Fall Under The Umbrella Of Cloud Security Cloud Computing Security IT Ppt Model Example Introduction PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. Presenting topics that fall under the umbrella of cloud security cloud computing security it ppt model example introduction pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data centre security, threat prevention, access control, threat detection, threat mitigation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
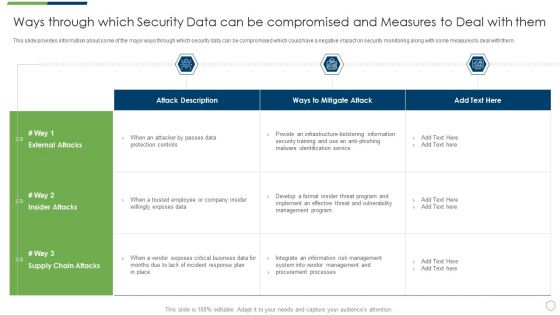
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ways Through Which Security Data Themes PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach ways through which security data themes pdf bundle. Topics like ways through which security data can be compromised and measures to deal with them can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
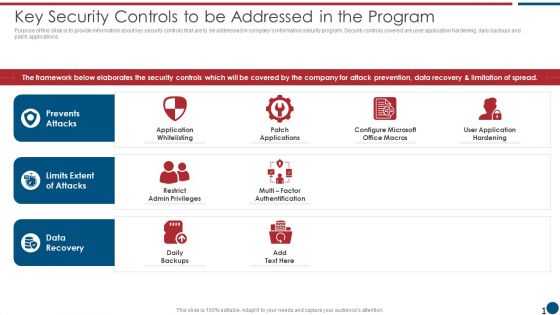
Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF bundle. Topics like Prevents Attacks, Limits Extent, Data Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
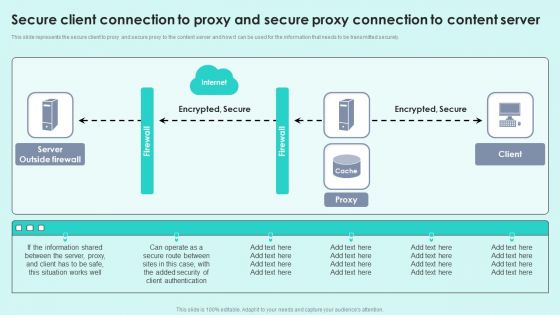
Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely.Deliver and pitch your topic in the best possible manner with this Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF. Use them to share invaluable insights on Server Outside, Between Server, Situation Works and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
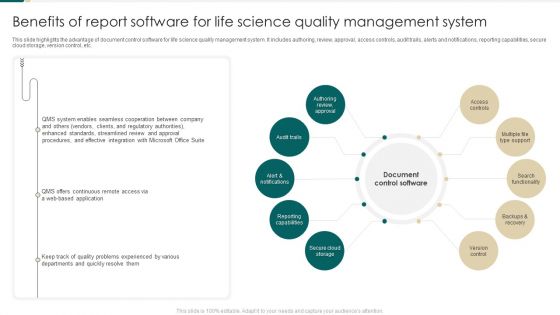
Benefits Of Report Software For Life Science Quality Management System Summary PDF
This slide highlights the advantage of document control software for life science quality management system. It includes authoring, review, approval, access controls, audit trails, alerts and notifications, reporting capabilities, secure cloud storage, version control, etc. Presenting Benefits Of Report Software For Life Science Quality Management System Summary PDF to dispense important information. This template comprises Ten stages. It also presents valuable insights into the topics including Reporting Capabilities, Secure Cloud Storage, Version Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
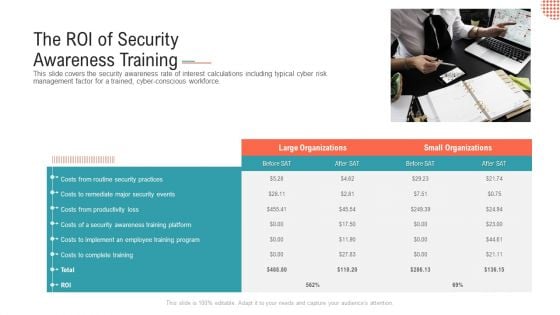
The ROI Of Security Awareness Training Ppt Slides Background PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyberconscious workforce.This is a the roi of security awareness training ppt slides background pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs from routine security practices, costs from productivity loss. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
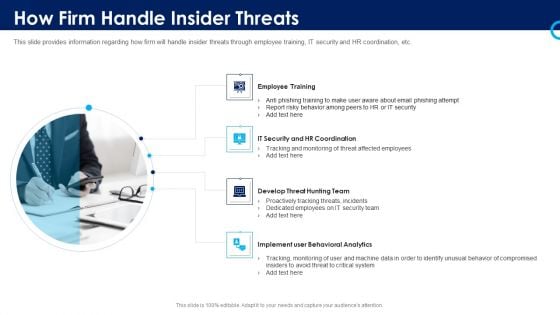
Organizational Security Solutions How Firm Handle Insider Threats Introduction PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a organizational security solutions how firm handle insider threats introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How Security Concerns Affect Firm In Present Times Pictures PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative how security concerns affect firm in present times pictures pdf bundle. Topics like reported financial losses due to increase security threats, data breaches and records exposed, security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
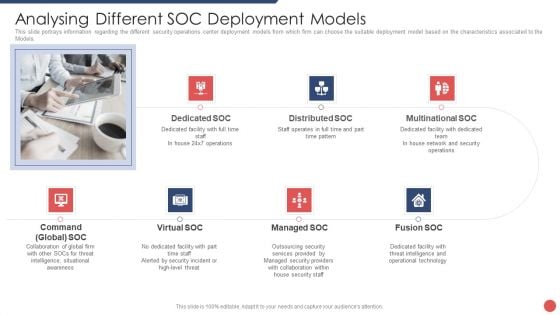
Security Functioning Centre Analysing Different SOC Deployment Models Template PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the Models. This is a security functioning centre analysing different soc deployment models template pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like distributed, network, security operations, operational technology, threat intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
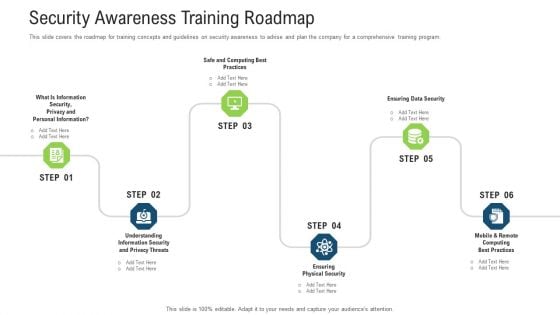
Security Awareness Training Roadmap Ppt Portfolio Demonstration PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a Security Awareness Training Roadmap Ppt Portfolio Demonstration Pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
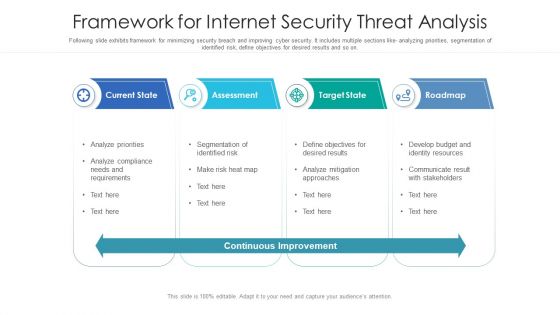
Framework For Internet Security Threat Analysis Structure PDF
Following slide exhibits framework for minimizing security breach and improving cyber security. It includes multiple sections like- analyzing priorities, segmentation of identified risk, define objectives for desired results and so on. Showcasing this set of slides titled framework for internet security threat analysis structure pdf. The topics addressed in these templates are current state, assessment, target state, roadmap. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
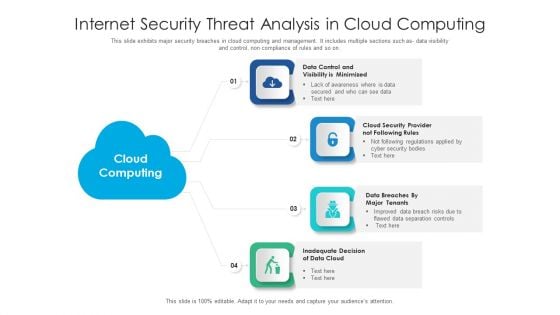
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
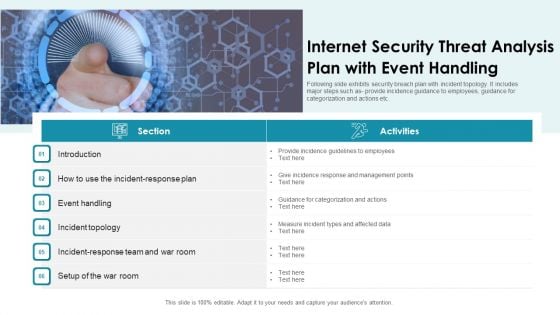
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
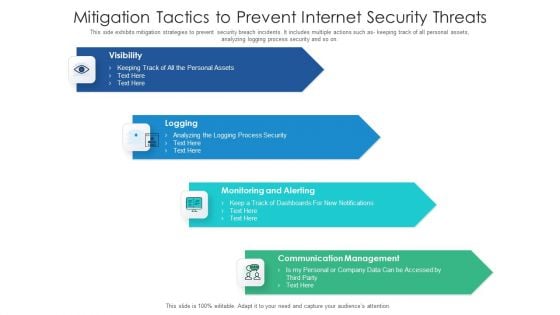
Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
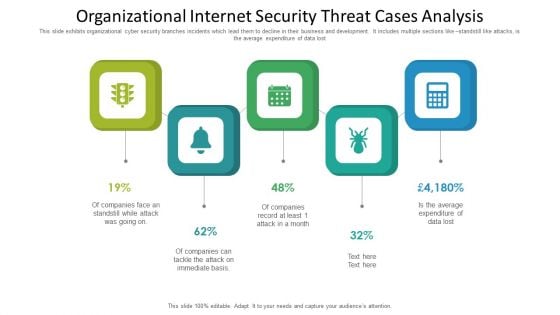
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Video Meeting Internet Security Threat Analysis Measures Brochure PDF
Following slide showcase video meeting security breach control tasks and actions. It includes multiple actions such as- run the recent version of application, utilizing corporate mails to send meeting links and so on. Persuade your audience using this video meeting internet security threat analysis measures brochure pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including video meeting internet security threat analysis measures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
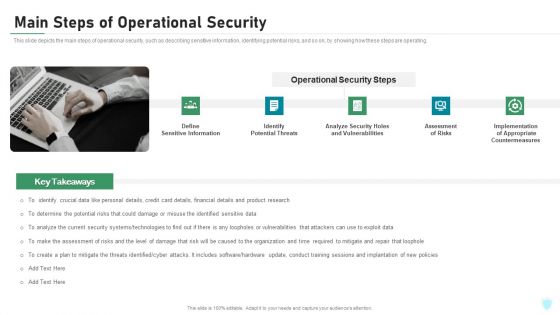
Main Steps Of Operational Security Ppt Ideas Summary PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a main steps of operational security ppt ideas summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential threats, analyze security holes and vulnerabilities, assessment of risks, implementation of appropriate countermeasures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
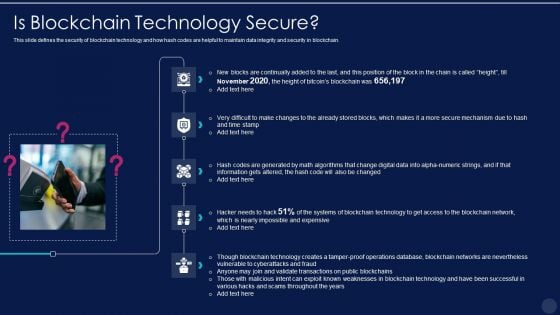
Blockchain Technology Framework IT Is Blockchain Technology Secure Demonstration PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a blockchain technology framework it is blockchain technology secure demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like expensive, systems, blockchain network, operations database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
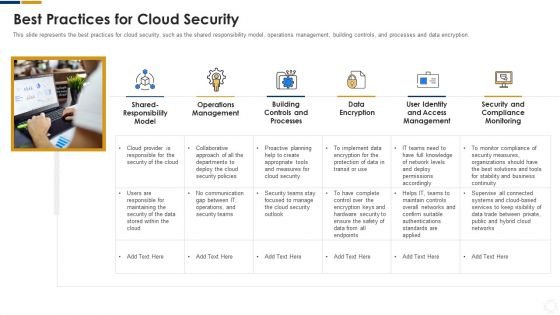
Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
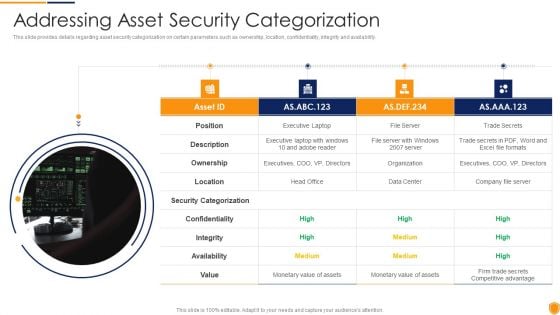
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Asset Security Elements PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. This is a mitigating cybersecurity threats and vulnerabilities addressing asset security elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ownership, location, integrity, security categorization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
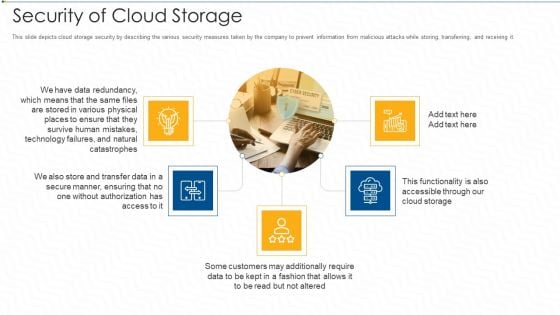
Security Of Cloud Storage Ppt Pictures Gridlines PDF
This slide depicts cloud storage security by describing the various security measures taken by the company to prevent information from malicious attacks while storing, transferring, and receiving it. This is a security of cloud storage ppt pictures gridlines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, customers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Information And Event Management Services Mockup PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting security information and event management services mockup pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
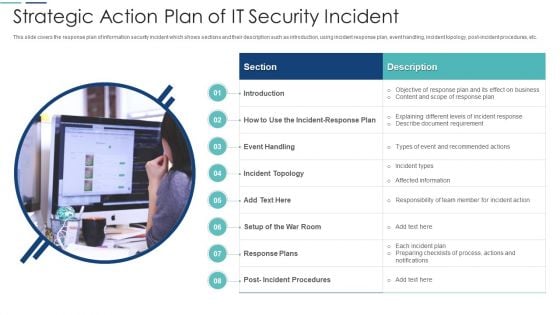
Strategic Action Plan Of It Security Incident Ideas PDF
This slide covers the response plan of information security incident which shows sections and their description such as introduction, using incident response plan, event handling, incident topology, post-incident procedures, etc. Persuade your audience using this strategic action plan of it security incident ideas pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including strategic action plan of it security incident. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
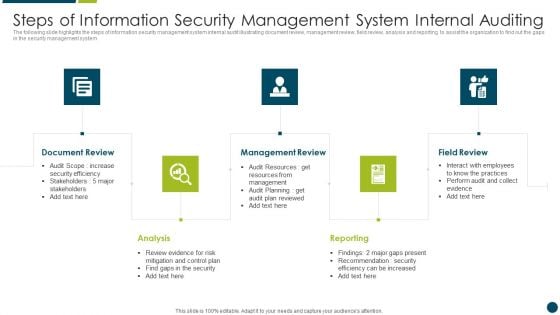
Steps Of Information Security Management System Internal Auditing Structure PDF
The following slide highlights the steps of information security management system internal audit illustrating document review, management review, field review, analysis and reporting to assist the organization to find out the gaps in the security management system Presenting Steps Of Information Security Management System Internal Auditing Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Management Review, Reporting, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully


 Continue with Email
Continue with Email

 Home
Home


































