Botnets
Botnet Hacking Network Attack Icon Demonstration PDF
Persuade your audience using this Botnet Hacking Network Attack Icon Demonstration PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Botnet Hacking, Network Attack Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Coordinated Criminal Botnet Attack Icon Structure PDF
Showcasing this set of slides titled Coordinated Criminal Botnet Attack Icon Structure PDF. The topics addressed in these templates are Coordinated Criminal, Botnet Attack Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
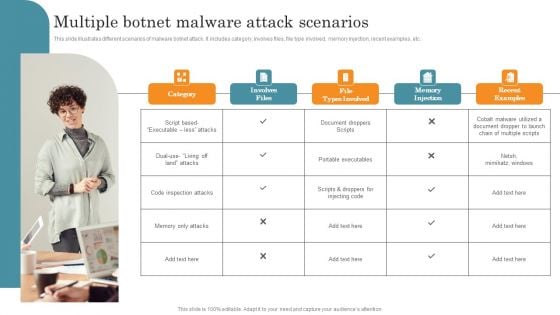
Multiple Botnet Malware Attack Scenarios Microsoft PDF
This slide illustrates different scenarios of malware botnet attack. It includes category, involves files, file type involved, memory injection, recent examples, etc. Presenting Multiple Botnet Malware Attack Scenarios Microsoft PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Involves Files, File Types Involved, Memory Injection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
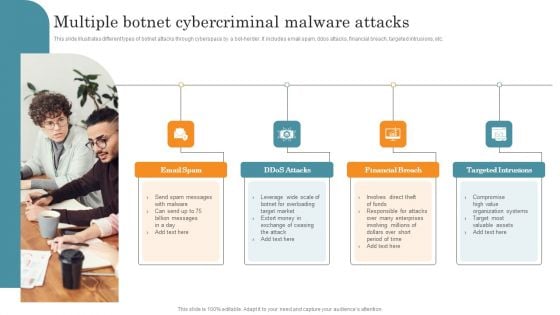
Multiple Botnet Cybercriminal Malware Attacks Elements PDF
This slide illustrates different types of botnet attacks through cyberspace by a bot-herder. It includes email spam, ddos attacks, financial breach, targeted intrusions, etc. Persuade your audience using this Multiple Botnet Cybercriminal Malware Attacks Elements PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Email Spam, Financial Breach, Targeted Intrusions. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
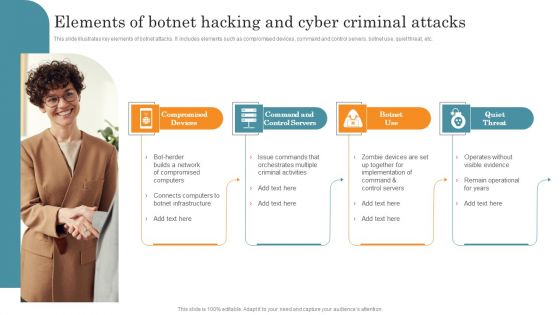
Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF
This slide illustrates key elements of botnet attacks. It includes elements such as compromised devices, command and control servers, botnet use, quiet threat, etc. Persuade your audience using this Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Compromised Devices, Command Control Servers, Botnet Use, Quiet Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Botnet Attack Cyber Criminal Activity Icon Ideas PDF
Showcasing this set of slides titled Botnet Attack Cyber Criminal Activity Icon Ideas PDF. The topics addressed in these templates are Botnet Attack Cyber, Criminal Activity Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
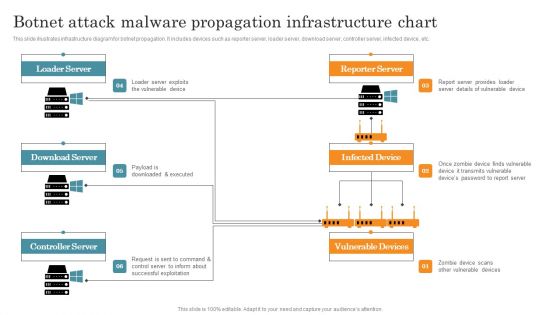
Botnet Attack Malware Propagation Infrastructure Chart Graphics PDF
This slide illustrates infrastructure diagram for botnet propagation. It includes devices such as reporter server, loader server, download server, controller server, infected device, etc. Pitch your topic with ease and precision using this Botnet Attack Malware Propagation Infrastructure Chart Graphics PDF. This layout presents information on Loader Server, Download Server, Controller Server. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
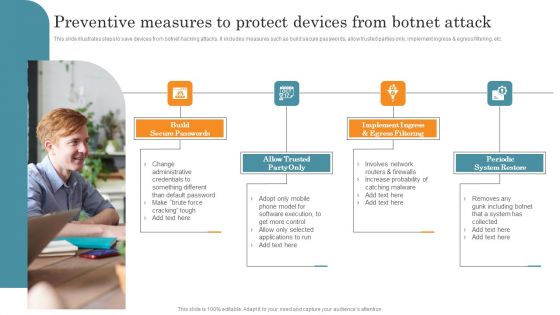
Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF
This slide illustrates steps to save devices from botnet hacking attacks. It includes measures such as build secure passwords, allow trusted parties only, implement ingress and egress filtering, etc. Presenting Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Build Secure Passwords, Allow Trusted Party Only, Implement Ingress. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Process Flow Of Botnet Malware Attack Icons PDF
This slide illustrates flowchart of attack through botnet malware hacking. It includes transmitting specific string to C and C, C and C authorizes bot connection, etc. Persuade your audience using this Process Flow Of Botnet Malware Attack Icons PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware In Victim, Hacker Launches, Malware Reads. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
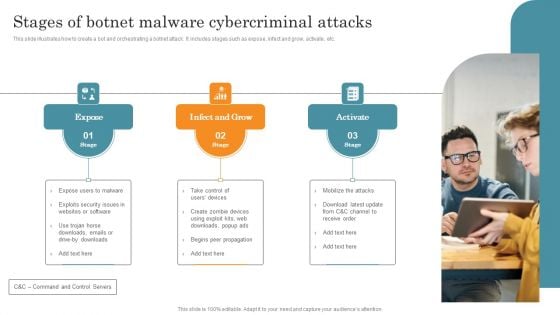
Stages Of Botnet Malware Cybercriminal Attacks Themes PDF
This slide illustrates how to create a bot and orchestrating a botnet attack. It includes stages such as expose, infect and grow, activate, etc. Persuade your audience using this Stages Of Botnet Malware Cybercriminal Attacks Themes PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Expose, Infect And Grow, Activate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Botnet Attack Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Botnet Attack Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising this Twelve professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
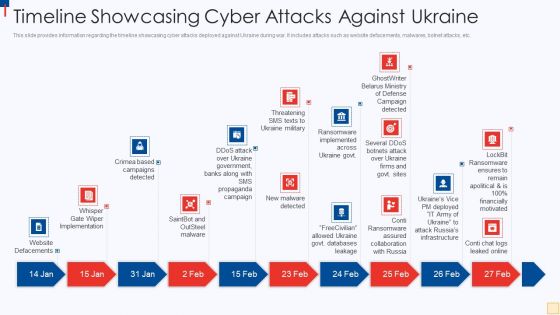
Ukraine Vs Russia Examining Timeline Showcasing Cyber Attacks Against Ukraine Ideas PDF
This slide provides information regarding the timeline showcasing cyber attacks deployed against Ukraine during war. It includes attacks such as website defacements, malwares, botnet attacks, etc. Presenting Ukraine Vs Russia Examining Timeline Showcasing Cyber Attacks Against Ukraine Ideas PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Website Defacements, Saintbot And Outsteel Malware, New Malware Detected, Threatening SMS Texts To Ukraine Military. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
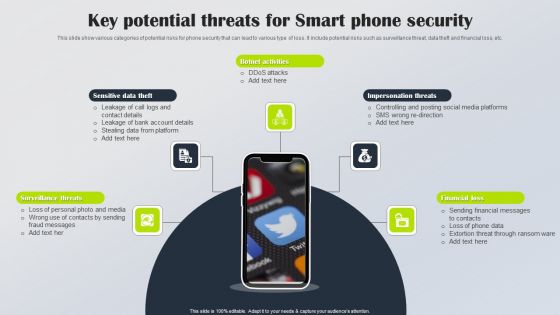
Key Potential Threats For Smart Phone Security Summary PDF
This slide show various categories of potential risks for phone security that can lead to various type of loss. It include potential risks such as surveillance threat, data theft and financial loss, etc. Persuade your audience using this Key Potential Threats For Smart Phone Security Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Botnet Activities, Impersonation Threats, Financial Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Threats Affecting Infra Cyber Security In Market Icons PDF
The following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Presenting Threats Affecting Infra Cyber Security In Market Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Phishing, Ransomware, Botnets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
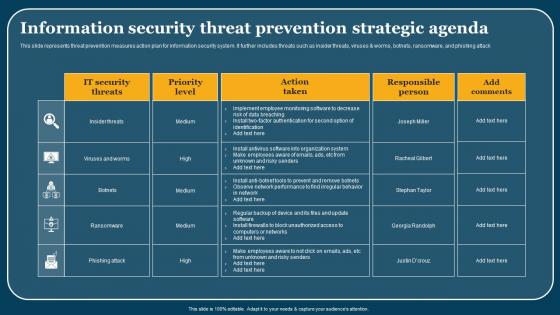
Information Security Threat Prevention Strategic Agenda Introduction Pdf
This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack. Pitch your topic with ease and precision using this Information Security Threat Prevention Strategic Agenda Introduction Pdf. This layout presents information on Security Threats, Priority Level, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack.
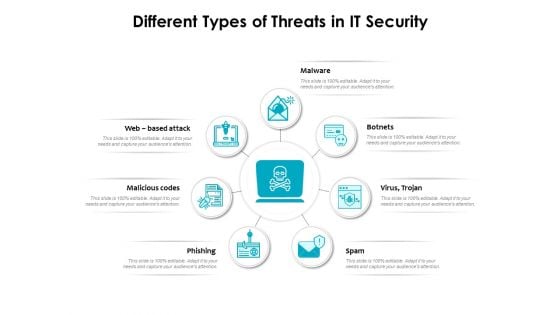
Different Types Of Threats In IT Security Ppt PowerPoint Presentation Portfolio Model PDF
Persuade your audience using this different types of threats in it security ppt powerpoint presentation portfolio model pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including malware, botnets, virus, trojan, spam, phishing, malicious codes, web based attack. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
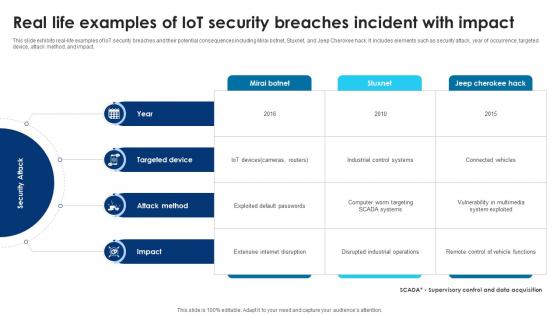
Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V
This slide exhibits real-life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack. It includes elements such as security attack, year of occurrence, targeted device, attack method, and impact. Get a simple yet stunning designed Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide exhibits real-life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack. It includes elements such as security attack, year of occurrence, targeted device, attack method, and impact.


 Continue with Email
Continue with Email

 Home
Home


































