Building Icon
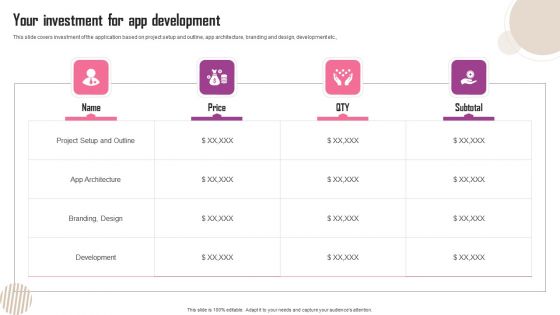
Your Investment For App Development Ppt File Infographic Template PDF
This slide covers investment of the application based on project setup and outline, app architecture, branding and design, development etc., From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Your Investment For App Development Ppt File Infographic Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
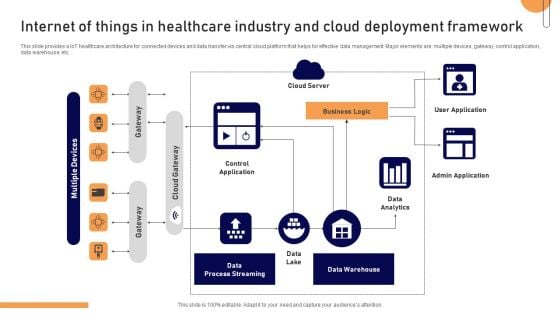
Internet Of Things In Healthcare Industry And Cloud Deployment Framework Topics PDF
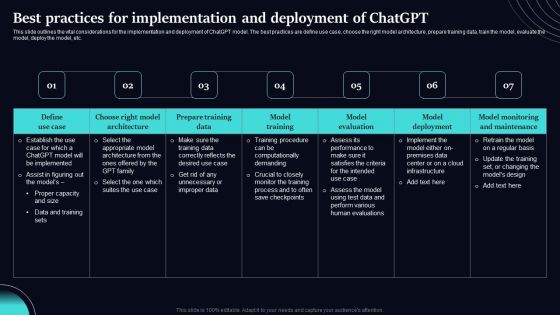
Regenerative Artificial Intelligence Systems Best Practices For Implementation And Deployment Of Chatgpt Guidelines PDF
This slide outlines the vital considerations for the implementation and deployment of ChatGPT model. The best practices are define use case, choose the right model architecture, prepare training data, train the model, evaluate the model, deploy the model, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Regenerative Artificial Intelligence Systems Best Practices For Implementation And Deployment Of Chatgpt Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Regenerative Artificial Intelligence Systems Training Of Chatgpt Large Language Model Microsoft PDF
This slide talks about the training of ChatGPT model using natural language processing. The purpose of this slide is to explain how large language models are incorporated into ChatGPT architecture. Two methods are next token prediction and masked language modelling. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Regenerative Artificial Intelligence Systems Training Of Chatgpt Large Language Model Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Enhancing Information Technology With Strategic Core Team Members Associated Information PDF
This slide provides information regarding core team members of IT functional areas un terms of VP for application, enterprise architecture, and creative. Other members include directors, etc. Create an editable Enhancing Information Technology With Strategic Core Team Members Associated Information PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Enhancing Information Technology With Strategic Core Team Members Associated Information PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
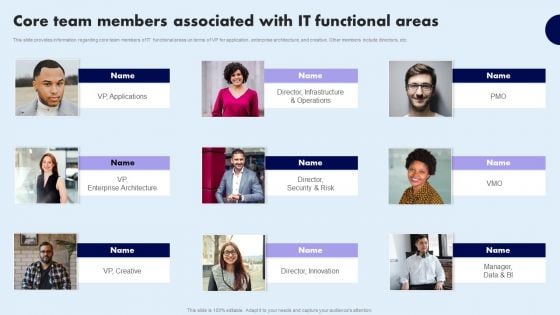
Core Team Members Associated With IT Functional Areas Topics PDF
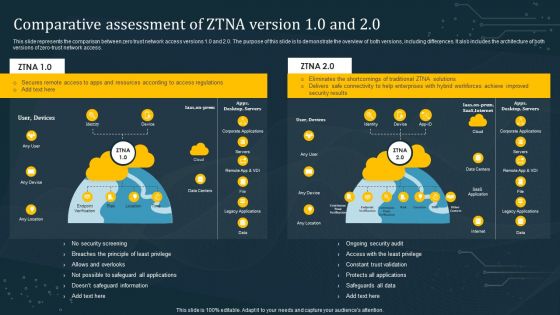
Comparative Assessment Of ZTNA Version 10 And 20 Template PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Comparative Assessment Of ZTNA Version 10 And 20 Template PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Future And Emerging Trends In ZTNA Model Summary PDF
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Future And Emerging Trends In ZTNA Model Summary PDF from Slidegeeks and deliver a wonderful presentation.
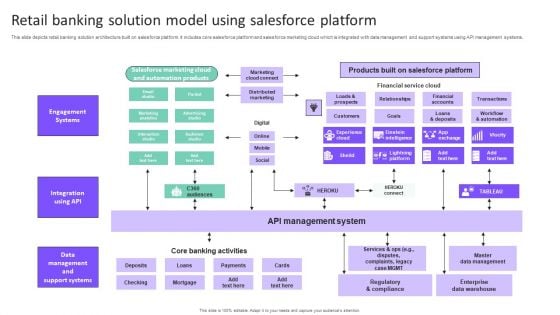
Retail Banking Solution Model Using Salesforce Platform Introduction PDF
This slide depicts retail banking solution architecture built on salesforce platform. It includes core salesforce platform and salesforce marketing cloud which is integrated with data management and support systems using API management systems. Present the topic in a bit more detail with this Retail Banking Solution Model Using Salesforce Platform Introduction PDF. Use it as a tool for discussion and navigation on Engagement Systems, Integration Using Api, Data Management. This template is free to edit as deemed fit for your organization. Therefore download it now.

Document Extraction Using SAP Intelligent Robotic Process Automation System Demonstration PDF
This slide provides an architectural overview of document extraction using SAP intelligent robotic process automation. It includes elements such as trigger, download invoices, save information, data extraction etc. Showcasing this set of slides titled Document Extraction Using SAP Intelligent Robotic Process Automation System Demonstration PDF. The topics addressed in these templates are Requesting Data Extraction, Information Extraction, Obtain Extraction Outcomes. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
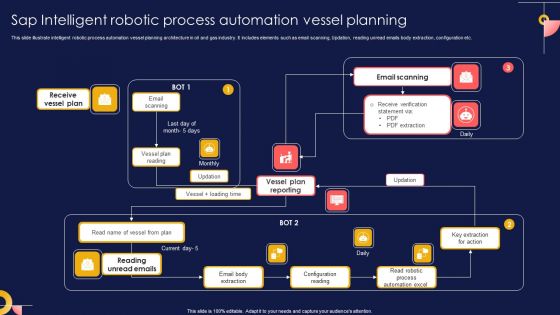
SAP Intelligent Robotic Process Automation Vessel Planning Pictures PDF
This slide illustrate intelligent robotic process automation vessel planning architecture in oil and gas industry. It includes elements such as email scanning, Updation, reading unread emails body extraction, configuration etc. Showcasing this set of slides titled SAP Intelligent Robotic Process Automation Vessel Planning Pictures PDF. The topics addressed in these templates are Vessel Plan Reading, Email Scanning, Receive Vessel Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
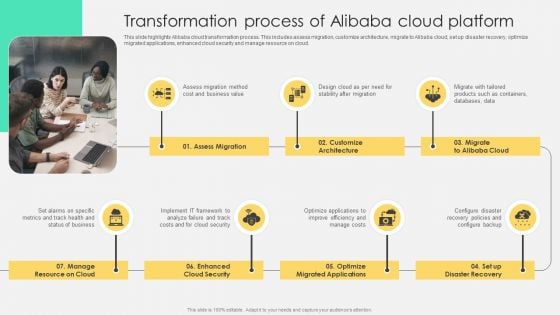
Transformation Process Of Alibaba Cloud Platform Introduction PDF
This slide highlights Alibaba cloud transformation process. This includes assess migration, customize architecture, migrate to Alibaba cloud, set up disaster recovery, optimize migrated applications, enhanced cloud security and manage resource on cloud. Find a pre-designed and impeccable Transformation Process Of Alibaba Cloud Platform Introduction PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cloud Deployment And Management Tools For Online Data Storage Clipart PDF
The following slide highlights tools for cloud management and implementation to manage, monitor an assess cloud architecture, services and infrastructure etc. It includes elements such as software, description, budget, free trial and user rating etc. Showcasing this set of slides titled Cloud Deployment And Management Tools For Online Data Storage Clipart PDF. The topics addressed in these templates are Description, Software, Budget. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
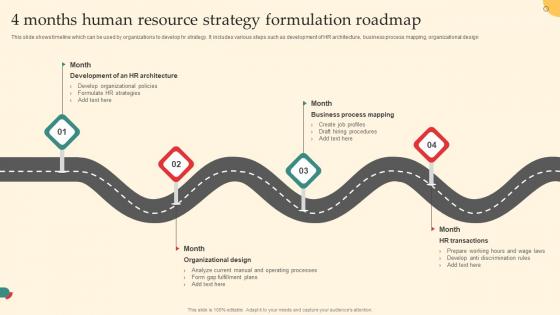
4 Months Human Resource Strategy Formulation Roadmap Microsoft Pdf
This slide shows timeline which can be used by organizations to develop hr strategy. It includes various steps such as development of HR architecture,business process mapping,organizational design Showcasing this set of slides titled 4 Months Human Resource Strategy Formulation Roadmap Microsoft Pdf. The topics addressed in these templates are Architecture,Organizational Design,Process Mapping. All the content presented in this PPT design is completely editable. Download it and make adjustments in color,background,font etc. as per your unique business setting. This slide shows timeline which can be used by organizations to develop hr strategy. It includes various steps such as development of HR architecture,business process mapping,organizational design
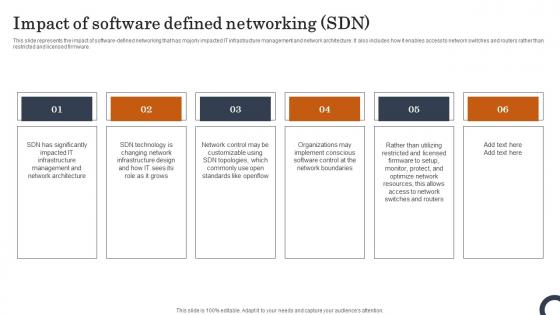
Impact Of Software Defined Networking SDN Evolution Of SDN Controllers Rules Pdf
This slide represents the impact of software-defined networking that has majorly impacted IT infrastructure management and network architecture. It also includes how it enables access to network switches and routers rather than restricted and licensed firmware. This Impact Of Software Defined Networking SDN Evolution Of SDN Controllers Rules Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Impact Of Software Defined Networking SDN Evolution Of SDN Controllers Rules Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the impact of software-defined networking that has majorly impacted IT infrastructure management and network architecture. It also includes how it enables access to network switches and routers rather than restricted and licensed firmware.
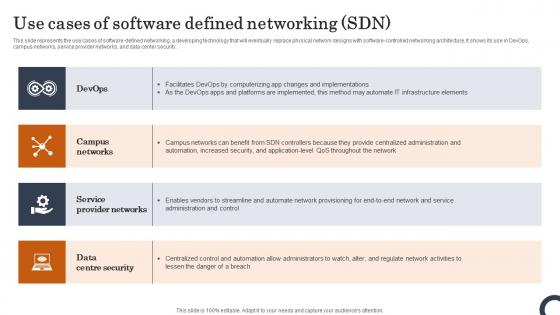
Use Cases Of Software Defined Networking SDN Evolution Of SDN Controllers Download Pdf
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Use Cases Of Software Defined Networking SDN Evolution Of SDN Controllers Download Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Use Cases Of Software Defined Networking SDN Evolution Of SDN Controllers Download Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security.
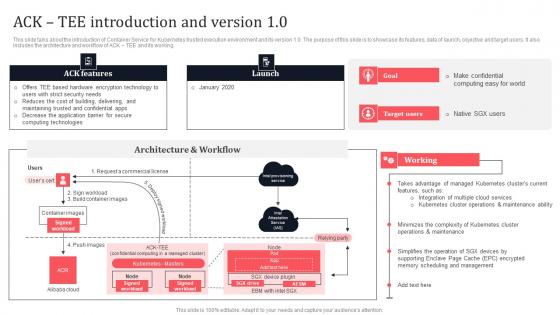
Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
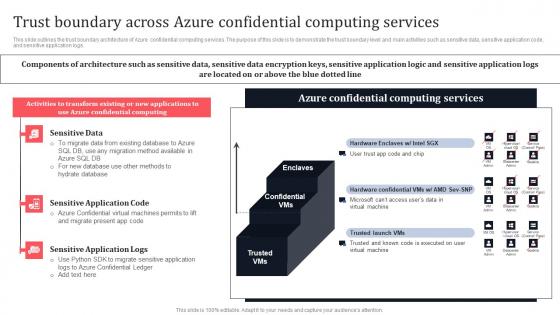
Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs.
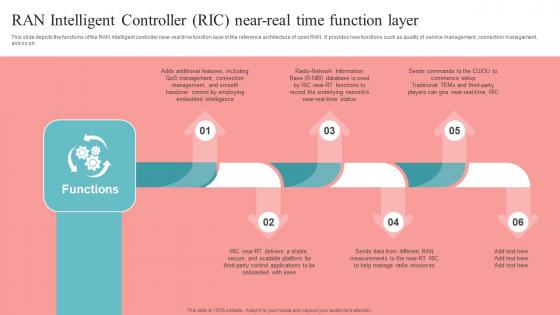
Ran Intelligent Controller RIC Near Real Time Unlocking The Potential Of Open RAN Brochure Pdf
This slide depicts the functions of the RAN intelligent controller near-real time function layer in the reference architecture of open RAN. It provides new functions such as quality of service management, connection management, and so on. This Ran Intelligent Controller RIC Near Real Time Unlocking The Potential Of Open RAN Brochure Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Ran Intelligent Controller RIC Near Real Time Unlocking The Potential Of Open RAN Brochure Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the functions of the RAN intelligent controller near-real time function layer in the reference architecture of open RAN. It provides new functions such as quality of service management, connection management, and so on.
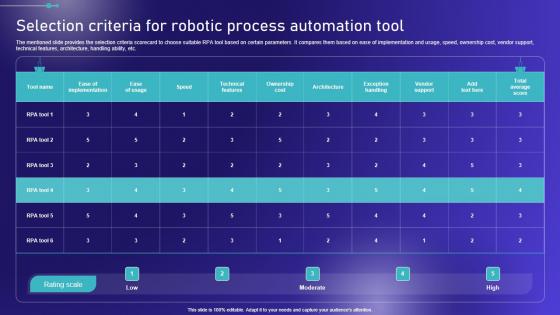
Selection Criteria For Robotic Process Automation Embracing Robotic Process Formats PDF
The mentioned slide provides the selection criteria scorecard to choose suitable RPA tool based on certain parameters. It compares them based on ease of implementation and usage, speed, ownership cost, vendor support, technical features, architecture, handling ability, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Selection Criteria For Robotic Process Automation Embracing Robotic Process Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Selection Criteria For Robotic Process Automation Embracing Robotic Process Formats PDF today and make your presentation stand out from the rest The mentioned slide provides the selection criteria scorecard to choose suitable RPA tool based on certain parameters. It compares them based on ease of implementation and usage, speed, ownership cost, vendor support, technical features, architecture, handling ability, etc.

Distributed Unit Du And Remote Radio Revolutionizing Mobile Networks Sample PDF
This slide represents the functions of the distributed unit and remote radio unit in the reference architecture of open RAN, including the tasks performed by both, such as real-time L2 functions, base processing, radio frequency processing, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Distributed Unit Du And Remote Radio Revolutionizing Mobile Networks Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Distributed Unit Du And Remote Radio Revolutionizing Mobile Networks Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the functions of the distributed unit and remote radio unit in the reference architecture of open RAN, including the tasks performed by both, such as real-time L2 functions, base processing, radio frequency processing, etc.
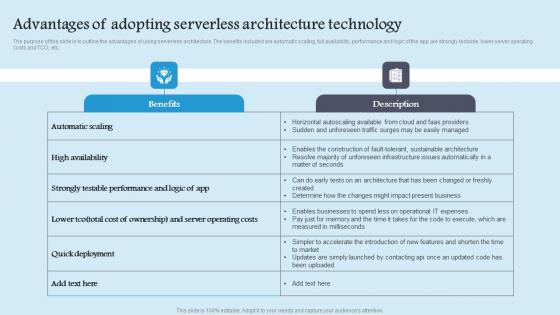
Advantages Adopting Serverless Role Serverless Computing Modern Technology Rules Pdf
The purpose of this slide is to outline the advantages of using serverless architecture. The benefits included are automatic scaling, full availability, performance and logic of the app are strongly testable, lower server operating costs and TCO, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Advantages Adopting Serverless Role Serverless Computing Modern Technology Rules Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Advantages Adopting Serverless Role Serverless Computing Modern Technology Rules Pdf today and make your presentation stand out from the rest The purpose of this slide is to outline the advantages of using serverless architecture. The benefits included are automatic scaling, full availability, performance and logic of the app are strongly testable, lower server operating costs and TCO, etc.
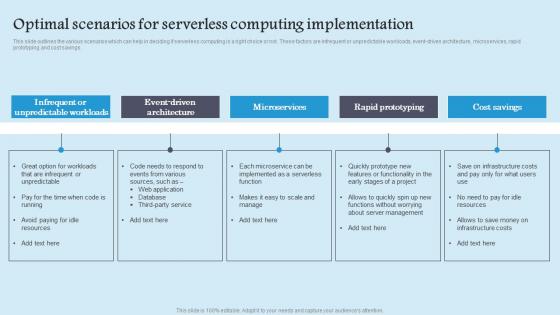
Optimal Scenarios Serverless Role Serverless Computing Modern Technology Demonstration Pdf
This slide outlines the various scenarios which can help in deciding if serverless computing is a right choice or not. These factors are infrequent or unpredictable workloads, event driven architecture, microservices, rapid prototyping and cost savings. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Optimal Scenarios Serverless Role Serverless Computing Modern Technology Demonstration Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Optimal Scenarios Serverless Role Serverless Computing Modern Technology Demonstration Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the various scenarios which can help in deciding if serverless computing is a right choice or not. These factors are infrequent or unpredictable workloads, event driven architecture, microservices, rapid prototyping and cost savings.
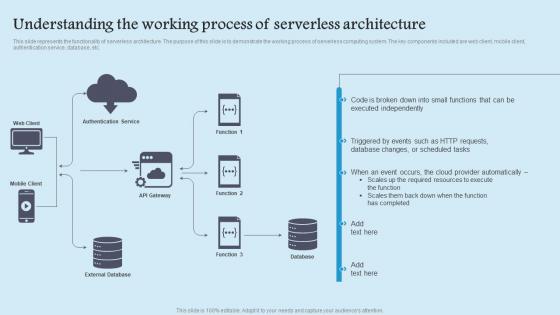
Understanding Working Process Role Serverless Computing Modern Technology Ideas Pdf
This slide represents the functionality of serverless architecture. The purpose of this slide is to demonstrate the working process of serverless computing system. The key components included are web client, mobile client, authentication service, database, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Understanding Working Process Role Serverless Computing Modern Technology Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Understanding Working Process Role Serverless Computing Modern Technology Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the functionality of serverless architecture. The purpose of this slide is to demonstrate the working process of serverless computing system. The key components included are web client, mobile client, authentication service, database, etc.
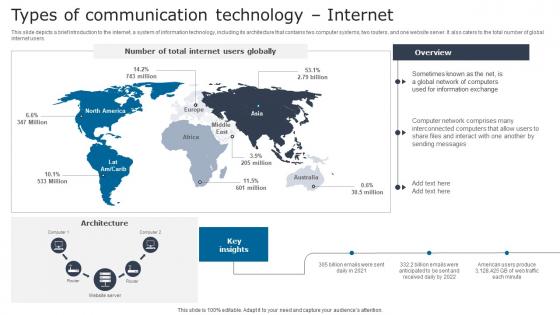
Types Of Communication Digital Signage In Internal Communication Channels Brochure Pdf
This slide depicts a brief introduction to the internet, a system of information technology, including its architecture that contains two computer systems, two routers, and one website server. It also caters to the total number of global internet users. This Types Of Communication Digital Signage In Internal Communication Channels Brochure Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Types Of Communication Digital Signage In Internal Communication Channels Brochure Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts a brief introduction to the internet, a system of information technology, including its architecture that contains two computer systems, two routers, and one website server. It also caters to the total number of global internet users.

Confidential Computing For Total Confidential Computing Technologies Background Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing For Total Confidential Computing Technologies Background Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing For Total Confidential Computing Technologies Background Pdf This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
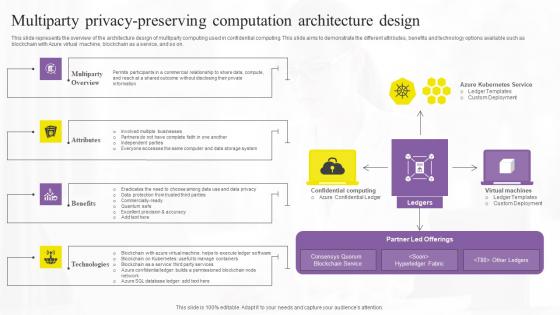
Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on.
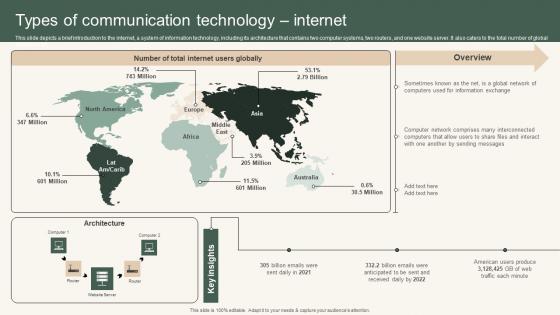
Types Of Communication Instant Messenger For Internal Business Operations Elements Pdf
This slide depicts a brief introduction to the internet, a system of information technology, including its architecture that contains two computer systems, two routers, and one website server. It also caters to the total number of global internet users. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Types Of Communication Instant Messenger For Internal Business Operations Elements Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide depicts a brief introduction to the internet, a system of information technology, including its architecture that contains two computer systems, two routers, and one website server. It also caters to the total number of global internet users.
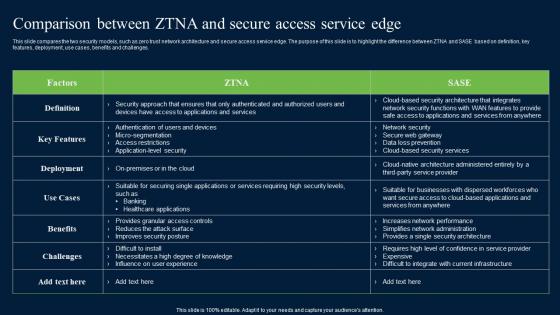
Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
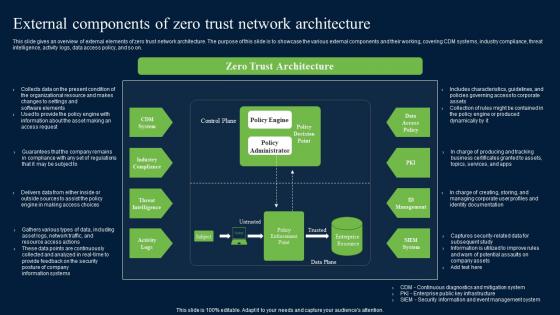
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
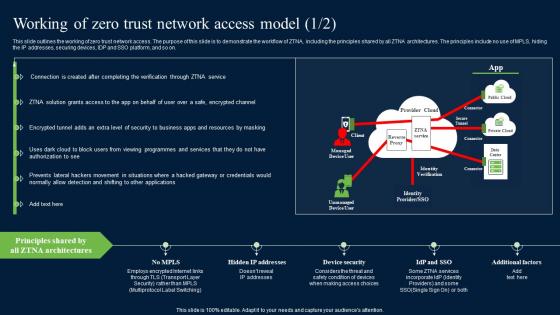
Working Of Zero Trust Network Access Model Security Pictures Pdf
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Working Of Zero Trust Network Access Model Security Pictures Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.
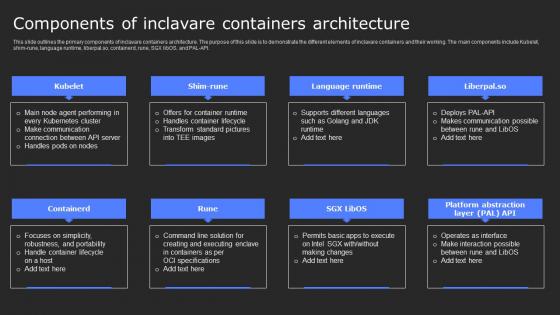
Components Of Inclavare Containers Secure Computing Framework Professional Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Slidegeeks is here to make your presentations a breeze with Components Of Inclavare Containers Secure Computing Framework Professional Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
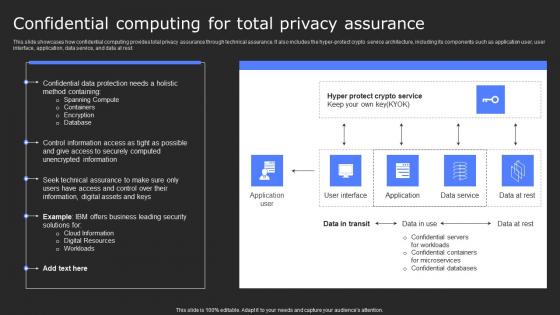
Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
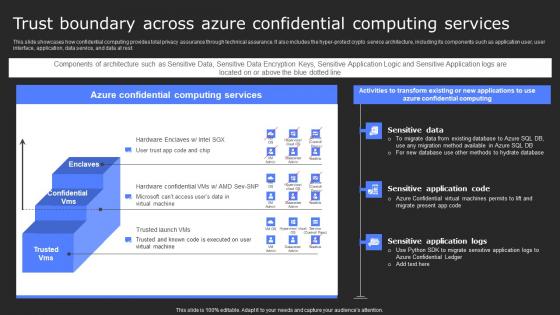
Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
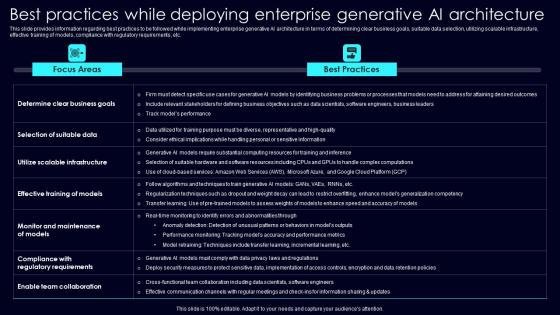
Best Practices While Deploying Exploring Rise Of Generative AI In Artificial Intelligence Microsoft Pdf
This slide provides information regarding best practices to be followed while implementing enterprise generative AI architecture in terms of determining clear business goals, suitable data selection, utilizing scalable infrastructure, effective training of models, compliance with regulatory requirements, etc. Slidegeeks is here to make your presentations a breeze with Best Practices While Deploying Exploring Rise Of Generative AI In Artificial Intelligence Microsoft Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides information regarding best practices to be followed while implementing enterprise generative AI architecture in terms of determining clear business goals, suitable data selection, utilizing scalable infrastructure, effective training of models, compliance with regulatory requirements, etc.

Major Components Of ChatGpt Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf
This slide provides information regarding key elements of ChatGPT architecture which is based on a neural network, including input layer, embedding layer and transformer blocks. Each transformer block caters multi head attention mechanism and feed forward neural network. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Major Components Of ChatGpt Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Major Components Of ChatGpt Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provides information regarding key elements of ChatGPT architecture which is based on a neural network, including input layer, embedding layer and transformer blocks. Each transformer block caters multi head attention mechanism and feed forward neural network.

Wireless Banking To Improve Three Layer Technological Framework Of Neobanks Fin SS V
This slide shows details about technological model used by neobanks for running banking operations smoothly. It includes three layers which are hosting infrastructure, open source core platform architecture and front end apps for users. Explore a selection of the finest Wireless Banking To Improve Three Layer Technological Framework Of Neobanks Fin SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Wireless Banking To Improve Three Layer Technological Framework Of Neobanks Fin SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide shows details about technological model used by neobanks for running banking operations smoothly. It includes three layers which are hosting infrastructure, open source core platform architecture and front end apps for users.

Zero Trust Model Future And Emerging Trends In ZTNA Model
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. This Zero Trust Model Future And Emerging Trends In ZTNA Model is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Future And Emerging Trends In ZTNA Model features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.

Zero Trust Model Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model Working Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Sustainable Checklist To Implement Green Cloud Computing
This slide describes the checklist to implementing green cloud computing in a company. The purpose of this slide is to showcase the different strategies to implement green IT, including knowing when to use the cloud, offsetting carbon emissions, green cloud architecture, and choosing the right cloud service. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Sustainable Checklist To Implement Green Cloud Computing and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the checklist to implementing green cloud computing in a company. The purpose of this slide is to showcase the different strategies to implement green IT, including knowing when to use the cloud, offsetting carbon emissions, green cloud architecture, and choosing the right cloud service.
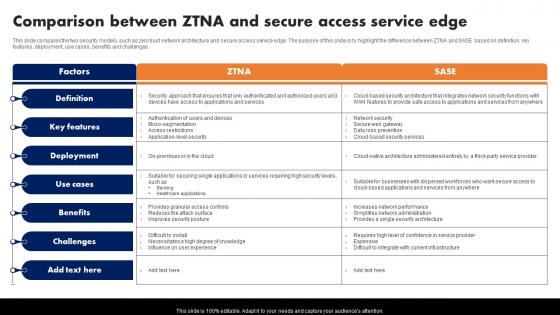
Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
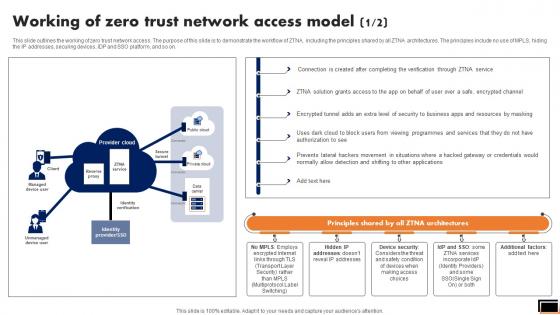
Working Of Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Zero Trust Network Access Model Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

IoT Based Satellite Platform For Maritime Transport Services IoT In Orbit Unleashing The Power IoT SS V
This slide exhibits IoT satellite system architecture that helps to establish efficient communication infrastructure for maritime operations. It includes key elements such as IoT devices, smart IoT gateway, 5G cellular network, Teleport, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than IoT Based Satellite Platform For Maritime Transport Services IoT In Orbit Unleashing The Power IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab IoT Based Satellite Platform For Maritime Transport Services IoT In Orbit Unleashing The Power IoT SS V today and make your presentation stand out from the rest This slide exhibits IoT satellite system architecture that helps to establish efficient communication infrastructure for maritime operations. It includes key elements such as IoT devices, smart IoT gateway, 5G cellular network, Teleport, etc.

Challenges And Considerations In Cloud Erp Integration Erp And Digital Transformation For Maximizing DT SS V
This slide addresses the key challenges faced while Integrating an ERP system with the cloud. It includes change management, security, access, permissions and productivity, optimum architectural and licensing models, and user onboarding and training.Slidegeeks is here to make your presentations a breeze with Challenges And Considerations In Cloud Erp Integration Erp And Digital Transformation For Maximizing DT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide addresses the key challenges faced while Integrating an ERP system with the cloud. It includes change management, security, access, permissions and productivity, optimum architectural and licensing models, and user onboarding and training.
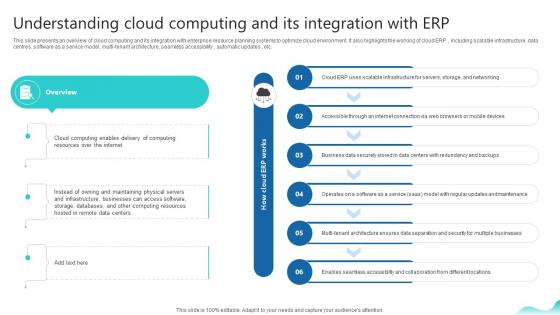
Understanding Cloud Computing And Its Integration Erp And Digital Transformation For Maximizing DT SS V
This slide presents an overview of cloud computing and its integration with enterprise resource planning systems to optimize cloud environment. It also highlights the working of cloud ERP , including scalable infrastructure, data centres, software as a service model, multi-tenant architecture, seamless accessibility , automatic updates , etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Understanding Cloud Computing And Its Integration Erp And Digital Transformation For Maximizing DT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Understanding Cloud Computing And Its Integration Erp And Digital Transformation For Maximizing DT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide presents an overview of cloud computing and its integration with enterprise resource planning systems to optimize cloud environment. It also highlights the working of cloud ERP , including scalable infrastructure, data centres, software as a service model, multi-tenant architecture, seamless accessibility , automatic updates , etc.
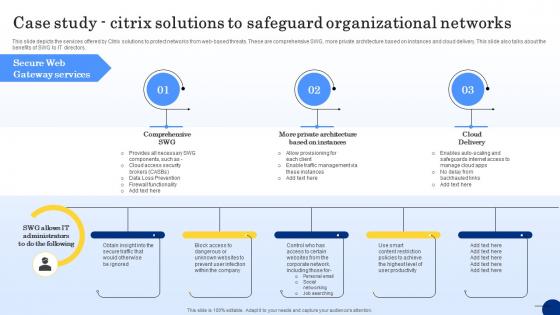
Case Study Citrix Solutions To Safeguard Organizational Networks Web Threat Protection System
This slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Citrix Solutions To Safeguard Organizational Networks Web Threat Protection System a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Citrix Solutions To Safeguard Organizational Networks Web Threat Protection System. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors.

Steps To Select Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Slidegeeks is here to make your presentations a breeze with Steps To Select Next Generation Secure Web Gateway Web Threat Protection System With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc.

Best Practices While Deploying Enterprise How Generative AI Tools Work AI SS V
This slide provides information regarding best practices to be followed while implementing enterprise generative AI architecture in terms of determining clear business goals, suitable data selection, utilizing scalable infrastructure, effective training of models, compliance with regulatory requirements, etc. Create an editable Best Practices While Deploying Enterprise How Generative AI Tools Work AI SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Best Practices While Deploying Enterprise How Generative AI Tools Work AI SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding best practices to be followed while implementing enterprise generative AI architecture in terms of determining clear business goals, suitable data selection, utilizing scalable infrastructure, effective training of models, compliance with regulatory requirements, etc.
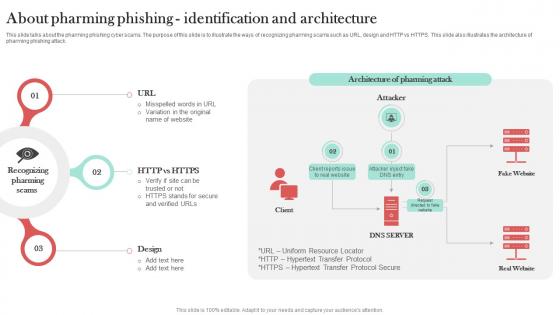
About Pharming Phishing Identification Man In The Middle Phishing IT
This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give About Pharming Phishing Identification Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable About Pharming Phishing Identification Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack.

Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Get a simple yet stunning designed Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Zero Trust Network Access Comparative Assessment Of ZTNA Version 1 0 And 2 0
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. This Zero Trust Network Access Comparative Assessment Of ZTNA Version 1 0 And 2 0 is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Comparative Assessment Of ZTNA Version 1 0 And 2 0 features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.

Zero Trust Network Access Future And Emerging Trends In ZTNA Model
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Future And Emerging Trends In ZTNA Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Future And Emerging Trends In ZTNA Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Future And Emerging Trends In ZTNA Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.

Zero Trust Network Access Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Working Of Zero Trust Network Access Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Working Of Zero Trust Network Access Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Working Of Zero Trust Network Access Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

CASB 2 0 IT API Scanning CASB Deployment Model
This slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Want to ace your presentation in front of a live audience Our CASB 2 0 IT API Scanning CASB Deployment Model can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs.

IoT Based Energy Management System Multi Internet Of Things Solutions To Enhance Energy IoT SS V
This slide exhibits four layers energy management system architecture utilising IoT technology. It includes four layers such as applications layer, cognition layer, network layer, and sensing layer. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IoT Based Energy Management System Multi Internet Of Things Solutions To Enhance Energy IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IoT Based Energy Management System Multi Internet Of Things Solutions To Enhance Energy IoT SS V This slide exhibits four layers energy management system architecture utilising IoT technology. It includes four layers such as applications layer, cognition layer, network layer, and sensing layer.

Solar Computing IT Checklist To Implement Green Cloud Computing
This slide describes the checklist to implementing green cloud computing in a company. The purpose of this slide is to showcase the different strategies to implement green IT, including knowing when to use the cloud, offsetting carbon emissions, green cloud architecture, and choosing the right cloud service. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Solar Computing IT Checklist To Implement Green Cloud Computing a try. Our experts have put a lot of knowledge and effort into creating this impeccable Solar Computing IT Checklist To Implement Green Cloud Computing. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide describes the checklist to implementing green cloud computing in a company. The purpose of this slide is to showcase the different strategies to implement green IT, including knowing when to use the cloud, offsetting carbon emissions, green cloud architecture, and choosing the right cloud service.

Factors To Choose The Right Cloud Service Platform Application Areas Of Mobile Cloud Computing
This slide depicts the factors needed to select the right cloud service provider for the mobile app. It includes factors such as cloud security, cloud compliance, service levels, architecture, manageability, costs, and support. Find highly impressive Factors To Choose The Right Cloud Service Platform Application Areas Of Mobile Cloud Computing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Factors To Choose The Right Cloud Service Platform Application Areas Of Mobile Cloud Computing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide depicts the factors needed to select the right cloud service provider for the mobile app. It includes factors such as cloud security, cloud compliance, service levels, architecture, manageability, costs, and support
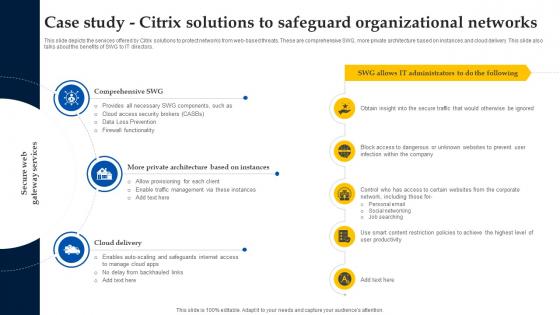
Web Access Control Solution Case Study Citrix Solutions To Safeguard Organizational Networks
This slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors. Find highly impressive Web Access Control Solution Case Study Citrix Solutions To Safeguard Organizational Networks on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Web Access Control Solution Case Study Citrix Solutions To Safeguard Organizational Networks for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors.
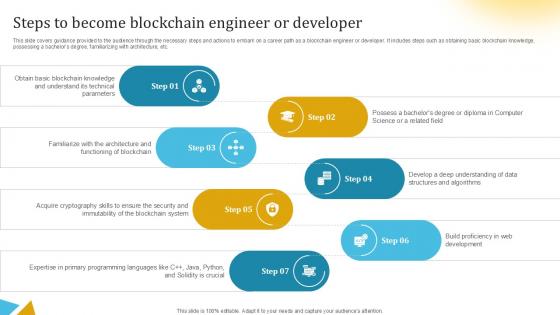
Steps To Become Blockchain Engineer Or Developer Ppt Example BCT SS V
This slide covers guidance provided to the audience through the necessary steps and actions to embark on a career path as a blockchain engineer or developer. It includes steps such as obtaining basic blockchain knowledge, possessing a bachelors degree, familiarizing with architecture, etc. Present like a pro with Steps To Become Blockchain Engineer Or Developer PPT Example BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers guidance provided to the audience through the necessary steps and actions to embark on a career path as a blockchain engineer or developer. It includes steps such as obtaining basic blockchain knowledge, possessing a bachelors degree, familiarizing with architecture, etc.
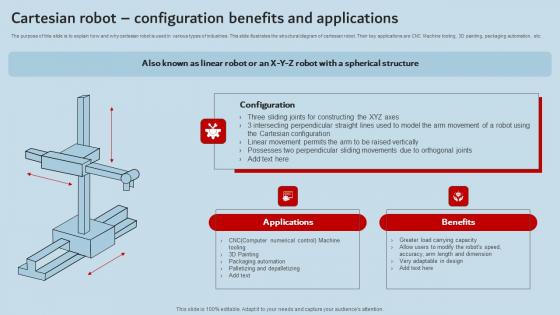
Cartesian Robot Configuration Benefits And Applications Industrial Robots Guidelines Pdf
The purpose of this slide is to explain how and why cartesian robot is used in various types of industries. This slide illustrates the structural diagram of cartesian robot. Their key applications are CNC Machine tooling, 3D painting, packaging automation, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cartesian Robot Configuration Benefits And Applications Industrial Robots Guidelines Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cartesian Robot Configuration Benefits And Applications Industrial Robots Guidelines Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. The purpose of this slide is to explain how and why cartesian robot is used in various types of industries. This slide illustrates the structural diagram of cartesian robot. Their key applications are CNC Machine tooling, 3D painting, packaging automation, etc.


 Continue with Email
Continue with Email

 Home
Home


































