Business Security
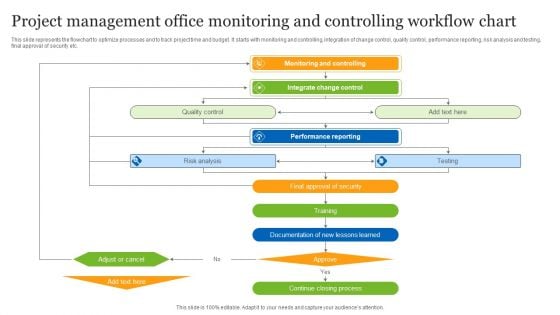
Project Management Office Monitoring And Controlling Workflow Chart Ppt Slides Mockup PDF
This slide represents the flowchart to optimize processes and to track project time and budget. It starts with monitoring and controlling, integration of change control, quality control, performance reporting, risk analysis and testing, final approval of security etc. Presenting Project Management Office Monitoring And Controlling Workflow Chart Ppt Slides Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Monitoring And Controlling, Integrate Change Control, Performance Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organizational Data Accuracy Issues With Solutions Elements PDF
The slide highlights various data integrity challenges and solutions to overcome such issues. Various problems included are lack of data integration, manual data collection, data security issues and dependence on legacy systems.Persuade your audience using this Organizational Data Accuracy Issues With Solutions Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Integration, Manual Data Collection, Dependence Legacy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
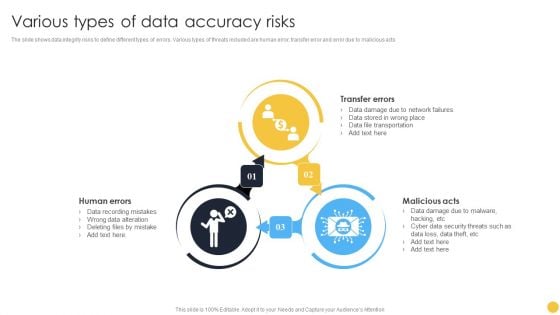
Various Types Of Data Accuracy Risks Guidelines PDF
The slide shows data integrity risks to define different types of errors. Various types of threats included are human error, transfer error and error due to malicious acts.Persuade your audience using this Various Types Of Data Accuracy Risks Guidelines PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Recording Mistakes, File Transportation, Security Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
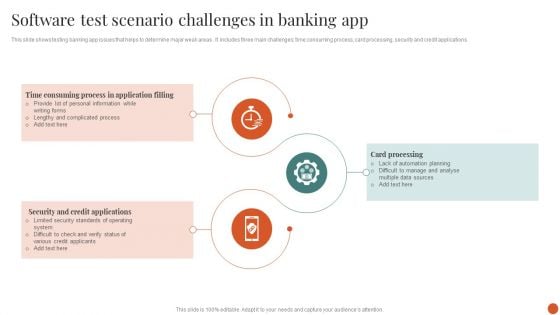
Software Test Scenario Challenges In Banking App Structure PDF
This slide shows testing banking app issues that helps to determine major weak areas . It includes three main challenges time consuming process, card processing, security and credit applications.Persuade your audience using this Software Test Scenario Challenges In Banking App Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Software Test, Scenario Checklist Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
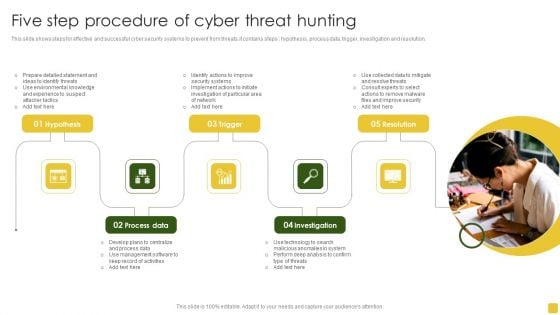
Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Project Tracking Risk Tracker Matrix Themes PDF
The following slide depicts the risk assessment matrix of project tracking to manage uncertain activities and improve decision making. It includes activities such as assessment, configuration, advancement, security check and dispose etc. Persuade your audience using this Project Tracking Risk Tracker Matrix Themes PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Project Tracking Risk, Tracker Matrix. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
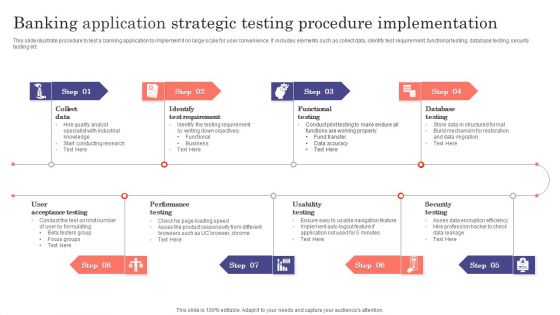
Banking Application Strategic Testing Procedure Implementation Ppt Slides Infographics PDF
This slide illustrate procedure to test a banking application to implement it on large scale for user convenience. It includes elements such as collect data, identify test requirement, functional testing, database testing, security testing etc. Presenting Banking Application Strategic Testing Procedure Implementation Ppt Slides Infographics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Collect Data, Identify Test Requirement, Functional Testing, Database Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Storage Software Freemium Pricing Generation Model Background PDF
This slide covers multiple offerings under both free and premium models for a cloud storage software. It includes offerings such as unlimited bases, attachments, automatic table syncing, dedicated success managers, etc.Presenting Cloud Storage Software Freemium Pricing Generation Model Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Space Requirements, Attachments Base, Security Requirements. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
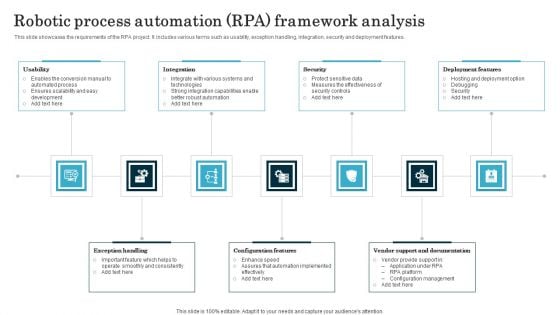
Robotic Process Automation RPA Framework Analysis Inspiration PDF
This slide showcases the requirements of the RPA project. It includes various terms such as usability, exception handling, integration, security and deployment features. Persuade your audience using this Robotic Process Automation RPA Framework Analysis Inspiration PDF. This PPT design covers Seven stages, thus making it a great tool to use. It also caters to a variety of topics including Usability, Exception Handling, Configuration Features. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
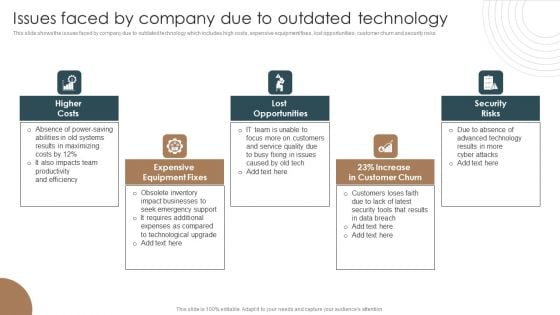
Issues Faced By Company Due To Outdated Technology Integrating Technology To Transform Change Pictures PDF
This slide shows the issues faced by company due to outdated technology which includes high costs, expensive equipment fixes, lost opportunities, customer churn and security risks.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Issues Faced By Company Due To Outdated Technology Integrating Technology To Transform Change Pictures PDF from Slidegeeks and deliver a wonderful presentation.
Internal Audit Control Mechanism Implementation Risks And Mitigation Strategies Icons PDF
This slide mentions implementation risks and solutions of internal audit control system. The parameters include audit system design, management and governance, internal security controls and reporting and analytics. Persuade your audience using this Internal Audit Control Mechanism Implementation Risks And Mitigation Strategies Icons PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Parameters, Risks, Mitigation Strategies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Decentralized Applications Benefits Of Tron Blockchain Infographics PDF
This slide highlights the advantages of Tron blockchain, including equivalent profits, data ownership, strong security confirmation, scalability, and high effectiveness. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Decentralized Applications Benefits Of Tron Blockchain Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Decentralized Applications Benefits Of Tron Blockchain Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
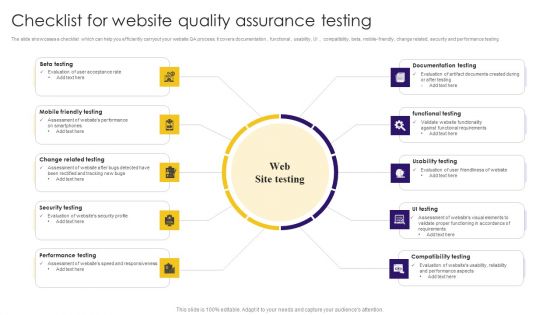
Checklist For Website Quality Assurance Testing Ppt Layouts Background Images PDF
The slide showcases a checklist which can help you efficiently carryout your website qa process. it covers documentation, functional, usability, ui, compatibility, beta, mobile-friendly, change related, security and performance testing. Presenting Checklist For Website Quality Assurance Testing Ppt Layouts Background Images PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Beta Testing, Mobile Friendly Testing, Change Related Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Strategies Of Private Wealth Administration System Professional PDF
The following slide showcases strategies that help to achieve financial security and growth in wealth. It presents information related to debt management, insurance policies, budgeting, etc. Persuade your audience using this Strategies Of Private Wealth Administration System Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Budgeting, Debt Management, Insurance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
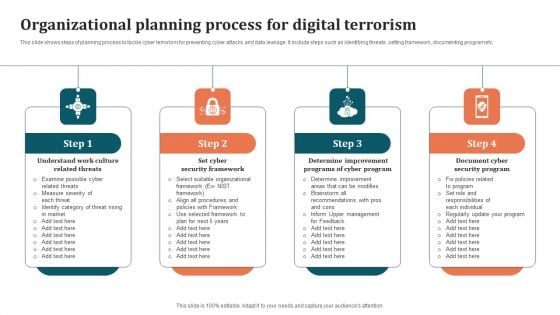
Organizational Planning Process For Digital Terrorism Graphics PDF
This slide shows steps of planning process to tackle cyber terrorism for preventing cyber attacks and data leakage. It include steps such as identifying threats, setting framework, documenting program etc. Presenting Organizational Planning Process For Digital Terrorism Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cyber Program, Determine Improvement Programs, Document Cyber Security Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
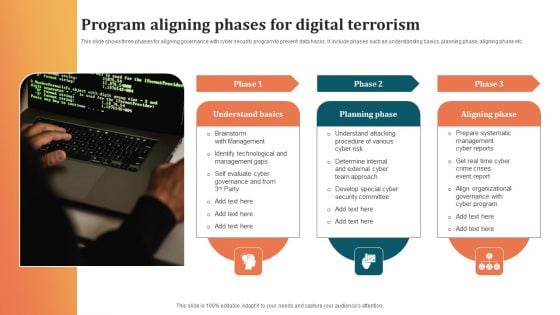
Program Aligning Phases For Digital Terrorism Infographics PDF
This slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc. Persuade your audience using this Program Aligning Phases For Digital Terrorism Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Planning Phase, Aligning Phase, Understand Basics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
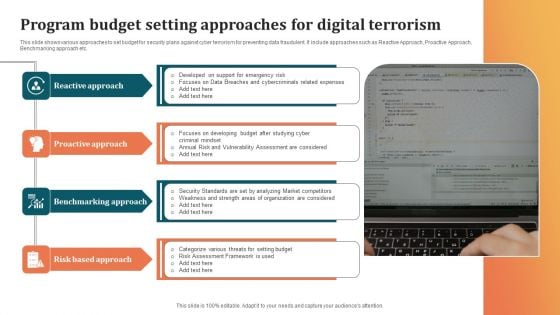
Program Budget Setting Approaches For Digital Terrorism Background PDF
This slide shows various approaches to set budget for security plans against cyber terrorism for preventing data fraudulent. It include approaches such as Reactive Approach, Proactive Approach, Benchmarking approach etc. Presenting Program Budget Setting Approaches For Digital Terrorism Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benchmarking Approach, Risk Based Approach, Proactive Approach. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Steps Of NIST Cybersecurity Risk Management Framework Mockup PDF
The slide showcases various steps of Nist RMF process which instructs in monitoring, selecting and implementing security controls. It covers identify, select, implement, assess, authorize and monitor. Persuade your audience using this Steps Of NIST Cybersecurity Risk Management Framework Mockup PDF.zip. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Overcome Payment Card Processing Errors Information PDF
This slide outline the how to overcome credit card processing errors. It includes various credit card issues such as credit card verification error, transaction not permitted, insufficient funds, incorrect security code and exceeded credit limit. Presenting Overcome Payment Card Processing Errors Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Credit Card Verification Error, Insufficient Funds, Exceeded Credit Limit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Remitbee Venture Capital Elevator Pitch Deck Problem Statement Icons PDF
This slide caters to details about several problems in the market faced by prospects. These pain points are international money transfer expenses, low speed, and security concerns. Present like a pro with Remitbee Venture Capital Elevator Pitch Deck Problem Statement Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Major Challenges Neobanks Are Facing Currently Ppt Portfolio Master Slide PDF
This slide shows information about various problems and issues which are faced by neobanks in the market. These challenge includes security issues, regulatory challenges, technological risks and no physical existence. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Major Challenges Neobanks Are Facing Currently Ppt Portfolio Master Slide PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
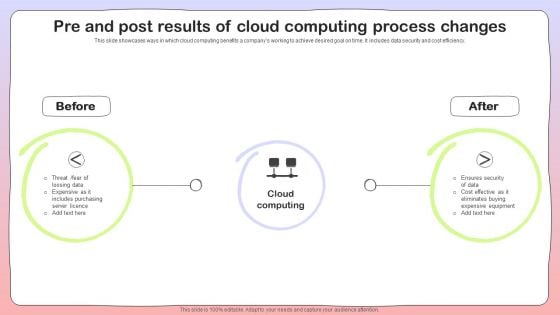
Pre And Post Results Of Cloud Computing Process Changes Graphics PDF
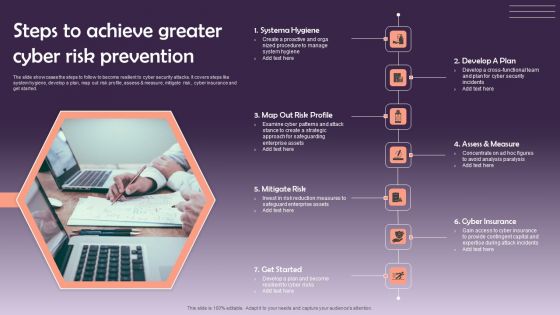
Steps To Achieve Greater Cyber Risk Prevention Infographics PDF
The slide showcases the steps to follow to become resilient to cyber security attacks. It covers steps like system hygiene, develop a plan, map out risk profile, assess and measure, mitigate risk, cyber insurance and get started. Presenting Steps To Achieve Greater Cyber Risk Prevention Infographics PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Systema Hygiene, Develop A Plan, Mitigate Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
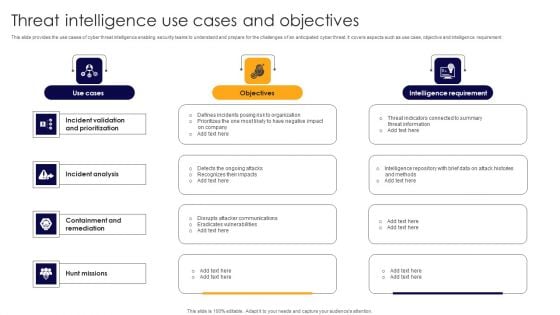
Threat Intelligence Use Cases And Objectives Demonstration PDF
This slide provides the use cases of cyber threat intelligence enabling security teams to understand and prepare for the challenges of an anticipated cyber threat. It covers aspects such as use case, objective and intelligence requirement. Presenting Threat Intelligence Use Cases And Objectives Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Analysis, Containment Remediation, Hunt Missions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Project Risk Optimization Strategic Approaches Formats PDF
This slide comprises different ways to assess portfolio risk in order to make asset allocation and security selection decisions. Some of the best practices include portfolio standard deviation, shortfall risk, tracking error, Sharpe ratio, and beta. Persuade your audience using this Project Risk Optimization Strategic Approaches Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Portfolio Standard Deviation, Shortfall Risk, Tracking Error. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
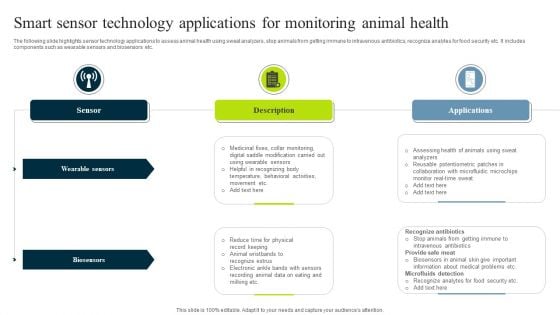
Smart Sensor Technology Applications For Monitoring Animal Health Clipart PDF
The following slide highlights sensor technology applications to assess animal health using sweat analyzers, stop animals from getting immune to intravenous antibiotics, recognize analytes for food security etc. It includes components such as wearable sensors and biosensors etc. Persuade your audience using this Smart Sensor Technology Applications For Monitoring Animal Health Clipart PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Wearable Sensors, Biosensors, Description. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
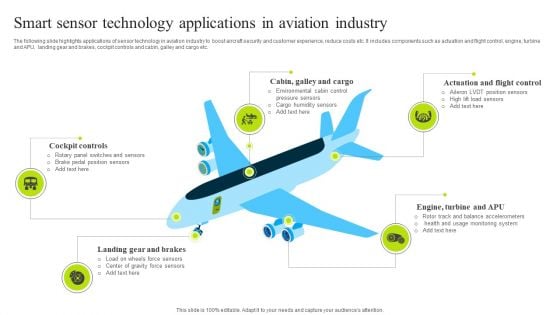
Smart Sensor Technology Applications In Aviation Industry Introduction PDF
The following slide highlights applications of sensor technology in aviation industry to boost aircraft security and customer experience, reduce costs etc. It includes components such as actuation and flight control, engine, turbine and APU, landing gear and brakes, cockpit controls and cabin, galley and cargo etc. Presenting Smart Sensor Technology Applications In Aviation Industry Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Cockpit Controls, Brakes, Industry. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
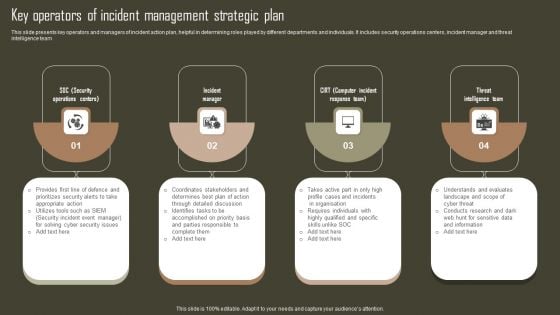
Key Operators Of Incident Management Strategic Plan Professional PDF
This slide presents key operators and managers of incident action plan, helpful in determining roles played by different departments and individuals. It includes security operations centers, incident manager and threat intelligence team. Presenting Key Operators Of Incident Management Strategic Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Manager, Threat Intelligence Team, Sensitive Data And Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Strategies To Optimize Data Center Management Technology Operations Icons PDF
This slide highlights strategies to optimize datacentre with the purpose of improving infrastructural efficiency to make datacentre central hub for all technologies. It covers hiring data security officer, utilizing cloud computing, upgrading hardware, virtualization, management transparency and automation. Presenting Strategies To Optimize Data Center Management Technology Operations Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Utilize Cloud Computing, Upgrade Hardware, Virtualization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Major Roles And Responsibilities Of Financial Mitigating Corporate Scams And Robberies Topics Pdf
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Major Roles And Responsibilities Of Financial Mitigating Corporate Scams And Robberies Topics Pdf from Slidegeeks and deliver a wonderful presentation. The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
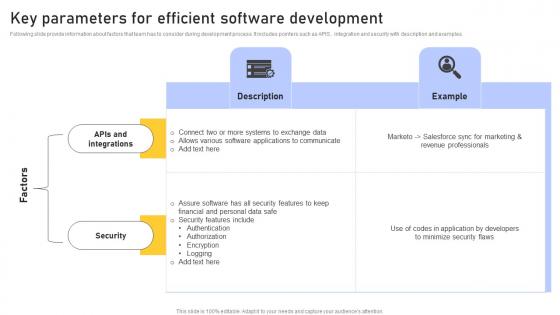
Key Parameters Efficient Enhancing Customer Service Operations Using CRM Technology Topics Pdf
Following slide provide information about factors that team has to consider during development process. It includes pointers such as APIS , integration and security with description and examples. This Key Parameters Efficient Enhancing Customer Service Operations Using CRM Technology Topics Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Key Parameters Efficient Enhancing Customer Service Operations Using CRM Technology Topics Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today Following slide provide information about factors that team has to consider during development process. It includes pointers such as APIS , integration and security with description and examples.
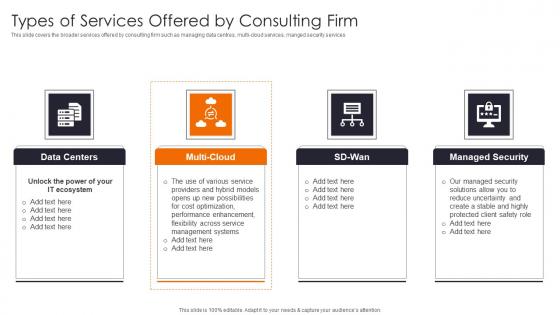
Types Of Services Offered Enhancing Workload Efficiency Through Cloud Architecture Introduction Pdf
This slide covers the broader services offered by consulting firm such as managing data centres, multi cloud services, manged security services If you are looking for a format to display your unique thoughts, then the professionally designed Types Of Services Offered Enhancing Workload Efficiency Through Cloud Architecture Introduction Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Types Of Services Offered Enhancing Workload Efficiency Through Cloud Architecture Introduction Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers the broader services offered by consulting firm such as managing data centres, multi cloud services, manged security services

A47 Roadmap To Implement Zero Trust Network Access Model
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Find a pre-designed and impeccable A47 Roadmap To Implement Zero Trust Network Access Model. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

A51 Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Want to ace your presentation in front of a live audience Our A51 Zero Trust Network Access Implementation Challenges can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on

Zero Trust Network Access Implementation Challenges Mockup Pdf
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Get a simple yet stunning designed Zero Trust Network Access Implementation Challenges Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Network Access Implementation Challenges Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Zero Trust Model Roadmap To Implement Zero Trust Network Access Model
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Find a pre-designed and impeccable Zero Trust Model Roadmap To Implement Zero Trust Network Access Model. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Zero Trust Model Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Model Zero Trust Network Access Implementation Challenges from Slidegeeks and deliver a wonderful presentation. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Zero Trust Network Access Implementation Challenges Software Defined Perimeter SDP
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Network Access Implementation Challenges Software Defined Perimeter SDP from Slidegeeks and deliver a wonderful presentation. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT Ss V
This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc.
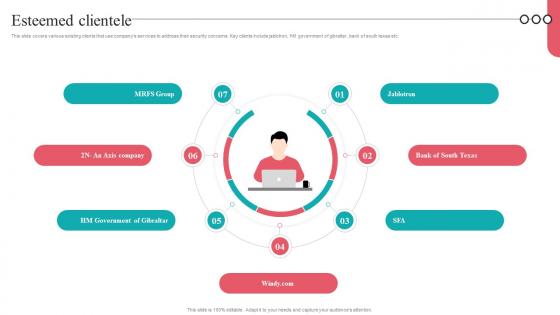
Esteemed Clientele Camera Management Platform Investor Funding Elevator Pitch Deck
This slide covers various existing clients that use companys services to address their security concerns. Key clients include jablotron, HM government of gibraltar, bank of south texas etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Esteemed Clientele Camera Management Platform Investor Funding Elevator Pitch Deck a try. Our experts have put a lot of knowledge and effort into creating this impeccable Esteemed Clientele Camera Management Platform Investor Funding Elevator Pitch Deck. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers various existing clients that use companys services to address their security concerns. Key clients include jablotron, HM government of gibraltar, bank of south texas etc.

Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V
This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals This Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals
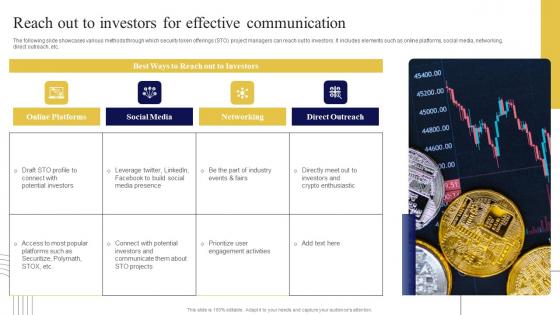
Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf
The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc. Slidegeeks is here to make your presentations a breeze with Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc.
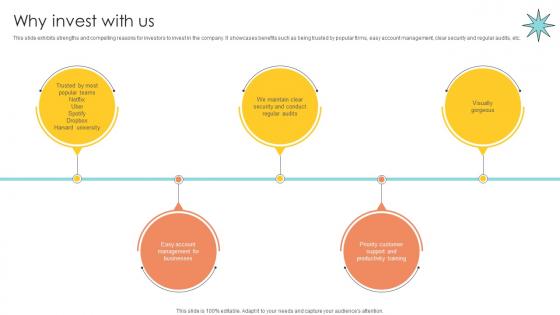
Why Invest With Us Email Management Technology Pitch Deck
This slide exhibits strengths and compelling reasons for investors to invest in the company. It showcases benefits such as being trusted by popular firms, easy account management, clear security and regular audits, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Why Invest With Us Email Management Technology Pitch Deck from Slidegeeks and deliver a wonderful presentation. This slide exhibits strengths and compelling reasons for investors to invest in the company. It showcases benefits such as being trusted by popular firms, easy account management, clear security and regular audits, etc.
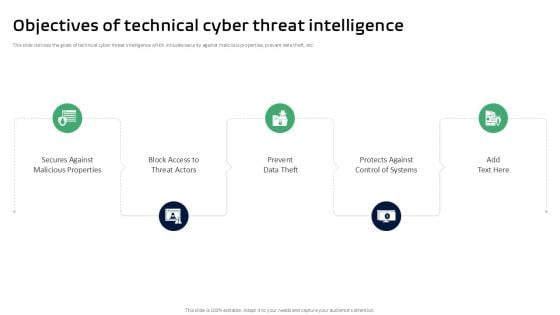
Objectives Of Technical Cyber Threat Intelligence Ppt Slides
This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc. This Objectives Of Technical Cyber Threat Intelligence Ppt Slides is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Objectives Of Technical Cyber Threat Intelligence Ppt Slides features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc.
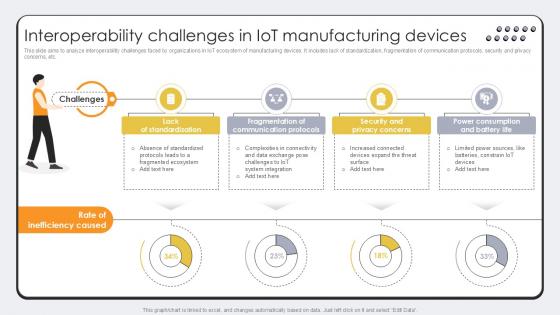
Interoperability Challenges In Revolutionizing Production IoT Ppt Sample
This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc. Slidegeeks has constructed Interoperability Challenges In Revolutionizing Production IoT Ppt Sample after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc.
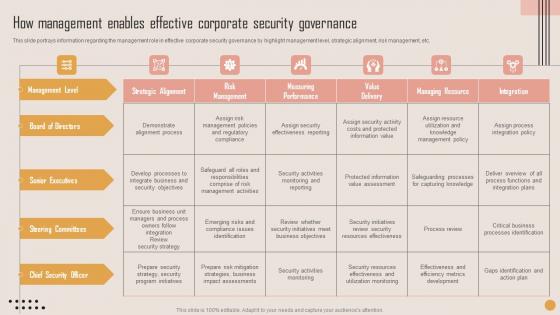
How Management Enables Effective Playbook For Strategic Actions To Improve IT Performance Topics Pdf
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created How Management Enables Effective Playbook For Strategic Actions To Improve IT Performance Topics Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc.
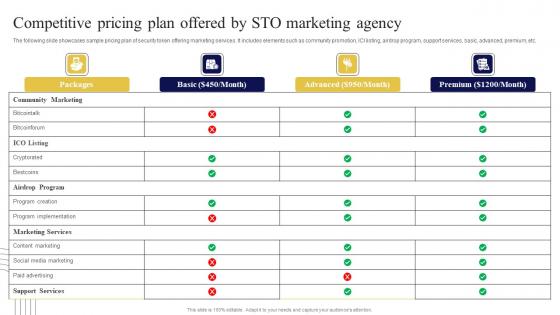
Competitive Pricing Plan Offered Exploring Investment Opportunities Elements Pdf
The following slide showcases sample pricing plan of security token offering marketing services. It includes elements such as community promotion, ICI listing, airdrop program, support services, basic, advanced, premium, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Competitive Pricing Plan Offered Exploring Investment Opportunities Elements Pdf can be your best option for delivering a presentation. Represent everything in detail using Competitive Pricing Plan Offered Exploring Investment Opportunities Elements Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide showcases sample pricing plan of security token offering marketing services. It includes elements such as community promotion, ICI listing, airdrop program, support services, basic, advanced, premium, etc.

CASB 2 0 IT 30 60 90 Days Plan To Deploy CASB Model
This slide represents the 30-0-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days. Boost your pitch with our creative CASB 2 0 IT 30 60 90 Days Plan To Deploy CASB Model. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the 30-0-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days.
Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
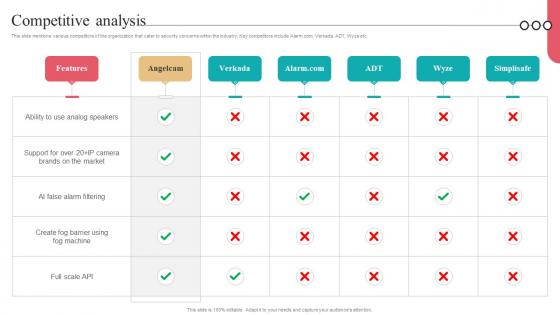
Competitive Analysis Camera Management Platform Investor Funding Elevator Pitch Deck
This slide mentions various competitors of the organization that cater to security concerns within the industry. Key competitors include Alarm.com, Verkada, ADT, Wyze etc. Want to ace your presentation in front of a live audience Our Competitive Analysis Camera Management Platform Investor Funding Elevator Pitch Deck can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide mentions various competitors of the organization that cater to security concerns within the industry. Key competitors include Alarm.com, Verkada, ADT, Wyze etc.

CASB 2 0 IT Primary Types Of Reverse Proxy Server Deployment
This slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations. Present like a pro with CASB 2 0 IT Primary Types Of Reverse Proxy Server Deployment. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations.
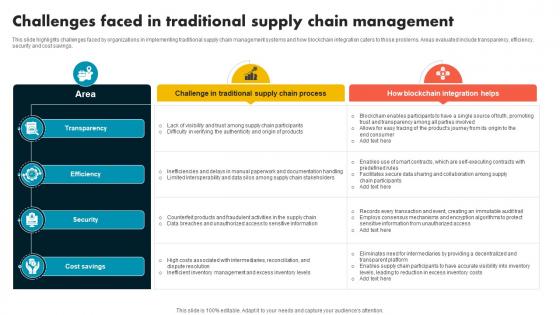
Challenges Faced In Traditional Supply Chain Evolution Harnessing The Power BCT SS V
This slide highlights challenges faced by organizations in implementing traditional supply chain management systems and how blockchain integration caters to those problems. Areas evaluated include transparency, efficiency, security and cost savings. This modern and well-arranged Challenges Faced In Traditional Supply Chain Evolution Harnessing The Power BCT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide highlights challenges faced by organizations in implementing traditional supply chain management systems and how blockchain integration caters to those problems. Areas evaluated include transparency, efficiency, security and cost savings.
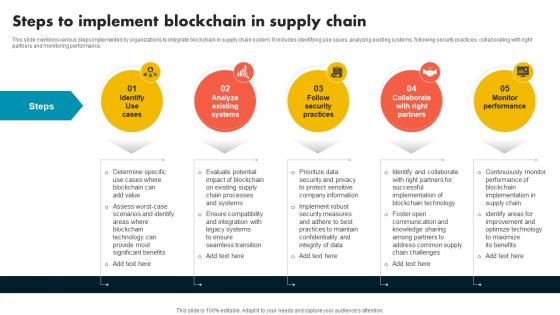
Steps To Implement Blockchain In Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V
This slide mentions various steps implemented by organizations to integrate blockchain in supply chain system. It includes identifying use cases, analyzing existing systems, following security practices, collaborating with right partners and monitoring performance. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Steps To Implement Blockchain In Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V from Slidegeeks and deliver a wonderful presentation. This slide mentions various steps implemented by organizations to integrate blockchain in supply chain system. It includes identifying use cases, analyzing existing systems, following security practices, collaborating with right partners and monitoring performance.
Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.

Performance Analysis Of Corrective Regression Testing Ppt Sample
The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Performance Analysis Of Corrective Regression Testing Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions.

Performance Analysis Of Current Automated Regression Testing And Achieving PPT Slide
The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Find highly impressive Performance Analysis Of Current Automated Regression Testing And Achieving PPT Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Performance Analysis Of Current Automated Regression Testing And Achieving PPT Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions.

Performance Analysis Of Partial Regression Testing For A Best PPT Sample
The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Find highly impressive Performance Analysis Of Partial Regression Testing For A Best PPT Sample on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Performance Analysis Of Partial Regression Testing For A Best PPT Sample for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions.


 Continue with Email
Continue with Email

 Home
Home


































