Business Security
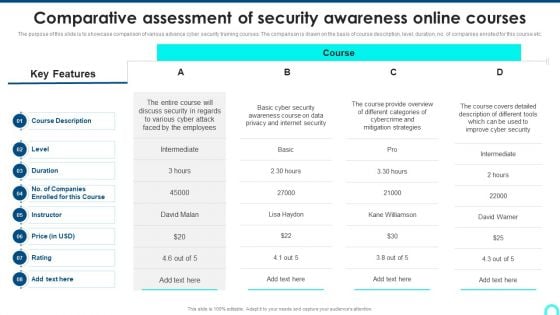
Comparative Assessment Of Security Awareness Online Courses Background PDF
Deliver an awe inspiring pitch with this creative Comparative Assessment Of Security Awareness Online Courses Background PDF bundle. Topics like Internet Security, Intermediate, Awareness Course can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Framework For Improving Critical Infra Cyber Security Icons PDF
The following slide exhibits framework for protection, resilience of infrastructure and other sectors important to national security. It presents information related to protection, responding, etc. Showcasing this set of slides titled Framework For Improving Critical Infra Cyber Security Icons PDF. The topics addressed in these templates are Identify, Protect, Detect. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
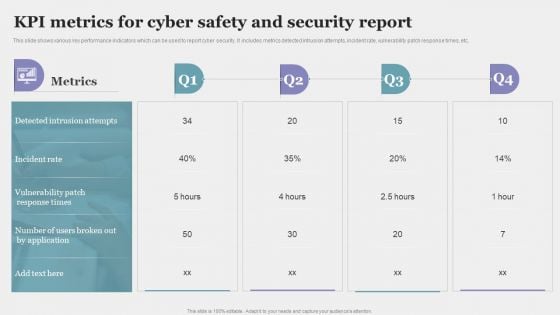
KPI Metrics For Cyber Safety And Security Report Elements PDF
This slide shows various key performance indicators which can be used to report cyber security. It includes metrics detected intrusion attempts, incident rate, vulnerability patch response times, etc. Showcasing this set of slides titled KPI Metrics For Cyber Safety And Security Report Elements PDF. The topics addressed in these templates are Incident Rate, Application, Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
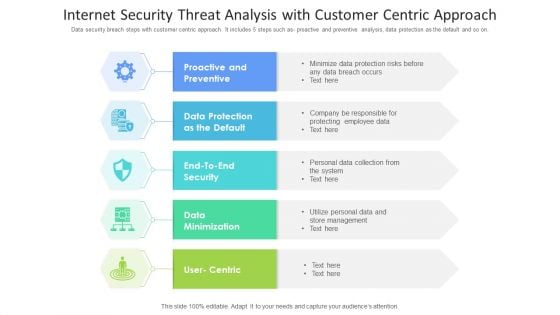
Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Private Security Organizational Structure Ppt PowerPoint Presentation Inspiration Pictures
This is a private security organizational structure ppt powerpoint presentation inspiration pictures. This is a five stage process. The stages in this process are private security organizational structure.
Information Security Tool Ppt PowerPoint Presentation Summary Portrait Cpb
This is a information security tool ppt powerpoint presentation summary portrait cpb. This is a three stage process. The stages in this process are information security tool.
Security Growth Ppt Powerpoint Presentation Show Infographic Template Cpb
This is a security growth ppt powerpoint presentation show infographic template cpb. This is a six stage process. The stages in this process are security growth.
Security Workforce Ppt PowerPoint Presentation Infographics Format Ideas Cpb
This is a security workforce ppt powerpoint presentation infographics format ideas cpb. This is a five stage process. The stages in this process are security workforce.
Cyber Security Solutions Ppt PowerPoint Presentation Layouts Icon Cpb
This is a cyber security solutions ppt powerpoint presentation layouts icon cpb. This is a six stage process. The stages in this process are cyber security solutions.
Types Data Security Ppt PowerPoint Presentation Styles Objects Cpb
This is a types data security ppt powerpoint presentation styles objects cpb. This is a ten stage process. The stages in this process are types data security.

Media Security Ppt PowerPoint Presentation Inspiration File Formats Cpb
This is a media security ppt powerpoint presentation inspiration file formats cpb. This is a three stage process. The stages in this process are media security.
Security Identity Management Ppt Powerpoint Presentation Pictures Portrait Cpb
This is a security identity management ppt powerpoint presentation pictures portrait cpb. This is a eight stage process. The stages in this process are security identity management.
Cyber Security Technology Ppt PowerPoint Presentation File Template Cpb
This is a cyber security technology ppt powerpoint presentation file template cpb. This is a six stage process. The stages in this process are cyber security technology.

Cyber Security Relationship Ppt PowerPoint Presentation Layouts Designs Download Cpb
This is a cyber security relationship ppt powerpoint presentation layouts designs download cpb. This is a four stage process. The stages in this process are cyber security relationship.
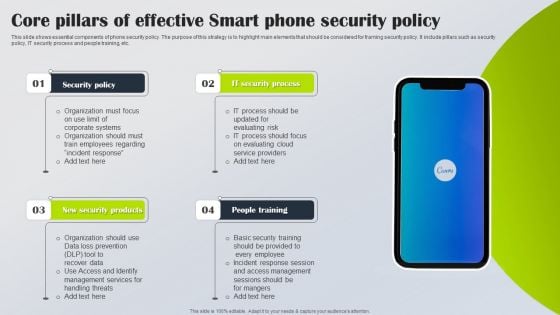
Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
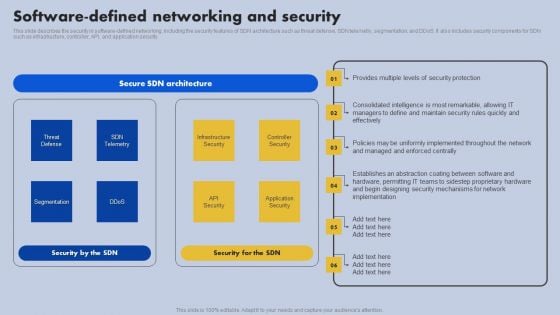
Software Defined Networking And Security Ppt Styles Slides PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is here to make your presentations a breeze with Software Defined Networking And Security Ppt Styles Slides PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
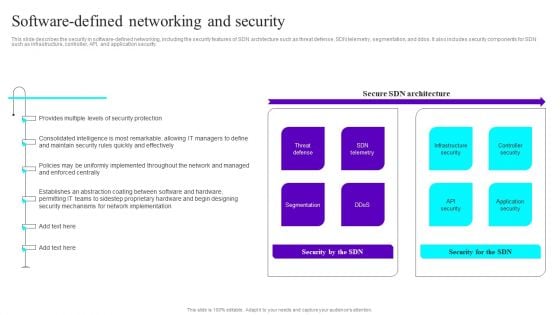
Software Defined Networking And Security Ppt Slides File Formats PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is here to make your presentations a breeze with Software Defined Networking And Security Ppt Slides File Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
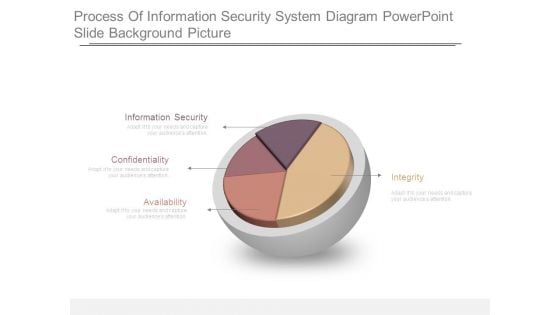
Process Of Information Security System Diagram Powerpoint Slide Background Picture
This is a process of information security system diagram powerpoint slide background picture. This is a four stage process. The stages in this process are information security, confidentiality, availability, integrity.
Architect Trade Cyber Security Data Ppt PowerPoint Presentation Gallery Layouts
This is a architect trade cyber security data ppt powerpoint presentation gallery layouts. This is a four stage process. The stages in this process are architect trade, cyber security data.
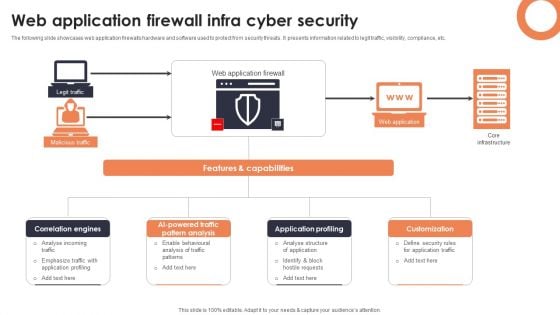
Web Application Firewall Infra Cyber Security Designs PDF
The following slide showcases web application firewalls hardware and software used to protect from security threats. It presents information related to legit traffic, visibility, compliance, etc. Showcasing this set of slides titled Web Application Firewall Infra Cyber Security Designs PDF. The topics addressed in these templates are Correlation Engines, AI Powered Traffic Pattern, Application Profiling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Customer Employee Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name cyber security customer employee ppt powerpoint presentation complete deck. The topics discussed in these slides are computer security, shield, organization, customer, employee. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Biometrics For Identity Security Ppt PowerPoint Presentation Summary Background Designs
Presenting this set of slides with name biometrics for identity security ppt powerpoint presentation summary background designs. The topics discussed in these slides are fingerprints, biometrics for identity security, fingerprint recognition. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Biometrics For Security Ppt PowerPoint Presentation Layouts Design Ideas
Presenting this set of slides with name biometrics for security ppt powerpoint presentation layouts design ideas. The topics discussed in these slides are fingerprints, biometrics for identity security, fingerprint recognition. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
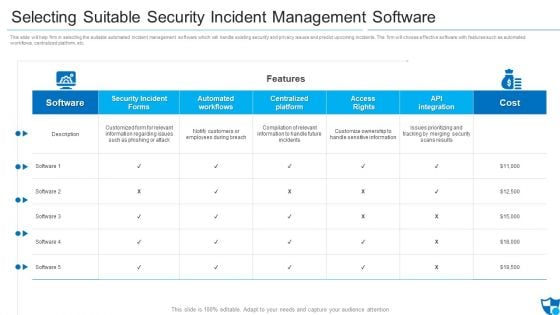
Selecting Suitable Security Incident Management Software Formats PDF
Deliver and pitch your topic in the best possible manner with this selecting suitable security incident management software formats pdf. Use them to share invaluable insights on security incident forms, automated workflows, automated workflows and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Differentiating 2 Items Graphic For Free Internet Security Guidelines PDF
Deliver an awe inspiring pitch with this creative differentiating 2 items graphic for free internet security guidelines pdf bundle. Topics like differentiating 2 items graphic for free internet security reviews can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Plan Icon Showcasing Electronic Alert Ideas PDF
Pitch your topic with ease and precision using this IT Security Plan Icon Showcasing Electronic Alert Ideas PDF. This layout presents information on IT Security Plan Icon, Showcasing Electronic Alert. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Risk Security Impact Mitigation Icon With Shield Themes PDF
Pitch your topic with ease and precision using this Risk Security Impact Mitigation Icon With Shield Themes PDF. This layout presents information on Icon With Shield, Risk Security Impact Mitigation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Big Data Security Analytics Icon With Shield Symbol Background PDF
Pitch your topic with ease and precision using this Big Data Security Analytics Icon With Shield Symbol Background PDF. This layout presents information on Big Data Security Analytics, Icon With Shield Symbol. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
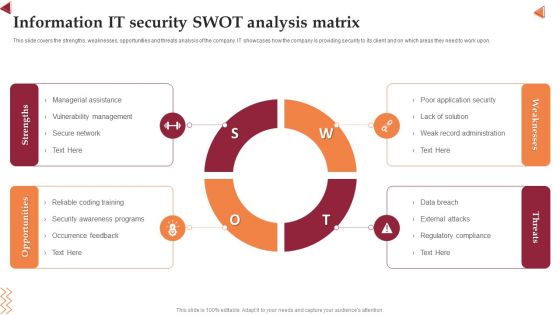
Information IT Security Swot Analysis Matrix Clipart PDF
This slide covers the strengths, weaknesses, opportunities and threats analysis of the company. IT showcases how the company is providing security to its client and on which areas they need to work upon. Persuade your audience using this Information IT Security Swot Analysis Matrix Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Opportunities, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Crisis Program Presentation Risk Management Action Plan Security Inspiration PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Deliver an awe-inspiring pitch with this creative crisis program presentation risk management action plan security inspiration pdf bundle. Topics like potential risk, communication, confidential information security, required resources, data backup team plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
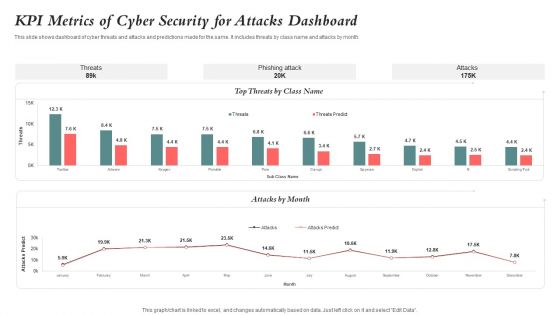
KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF
This slide shows dashboard of cyber threats and attacks and predictions made for the same. It includes threats by class name and attacks by month. Showcasing this set of slides titled KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF. The topics addressed in these templates are Kpi Metrics, Cyber Security, Attacks Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
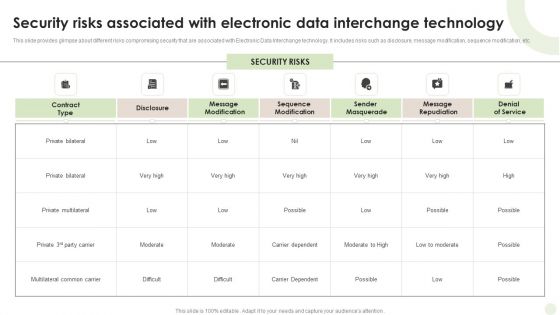
Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF
This slide provides glimpse about different risks compromising security that are associated with Electronic Data Interchange technology. It includes risks such as disclosure, message modification, sequence modification, etc.Showcasing this set of slides titled Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF. The topics addressed in these templates are Private Multilateral, Multilateral Common, Carrier Dependent. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
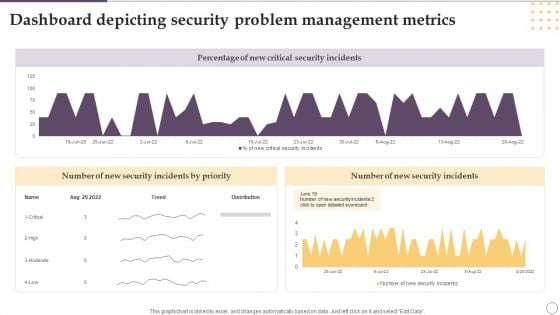
Dashboard Depicting Security Problem Management Metrics Ppt Gallery Designs PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Showcasing this set of slides titled Dashboard Depicting Security Problem Management Metrics Ppt Gallery Designs PDF. The topics addressed in these templates are Percentage, New Critical, Security Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Measuring The Impact Of Security Awareness Training Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. There are so many reasons you need a Measuring The Impact Of Security Awareness Training Icons PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
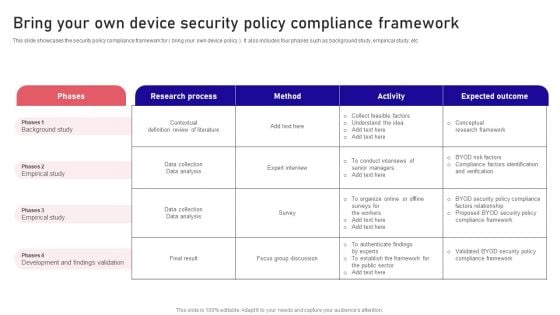
Bring Your Own Device Security Policy Compliance Framework Ideas PDF
This slide showcases the security policy compliance framework for bring your own device policy. It also includes four phases such as background study, empirical study, etc. Showcasing this set of slides titled Bring Your Own Device Security Policy Compliance Framework Ideas PDF. The topics addressed in these templates are Phases, Background Study, Empirical Study . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
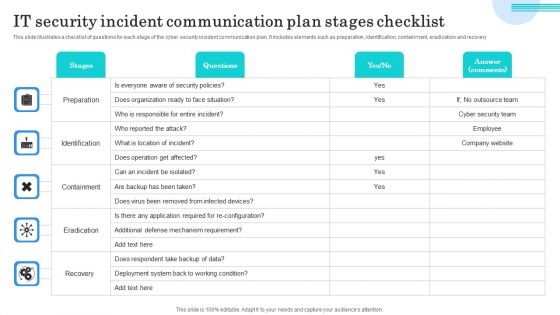
IT Security Incident Communication Plan Stages Checklist Topics PDF
This slide illustrates a checklist of questions for each stage of the cyber security incident communication plan. It includes elements such as preparation, identification, containment, eradication and recovery. Showcasing this set of slides titled IT Security Incident Communication Plan Stages Checklist Topics PDF. The topics addressed in these templates are Preparation, Identification, Containment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
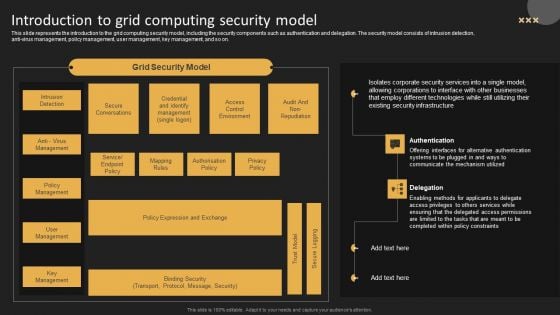
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Complete Guide To Launch Best Practices For Website Security Management
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Get a simple yet stunning designed Complete Guide To Launch Best Practices For Website Security Management. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Guide To Launch Best Practices For Website Security Management can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.

Application Security Testing Ppt Powerpoint Presentation Complete Deck With Slides

Global Security Industry Report Ppt Presentation IR CD V

Tokenization Strategies For Data Security Powerpoint Presentation Slides
This Tokenization Strategies For Data Security Powerpoint Presentation Slides is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This eighty three slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now. Our Tokenization Strategies For Data Security Powerpoint Presentation Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
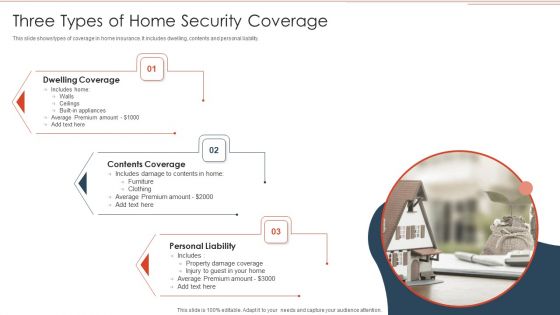
Three Types Of Home Security Coverage Demonstration PDF
This slide shows types of coverage in home insurance. It includes dwelling, contents and personal liability. Showcasing this set of slides titled Three Types Of Home Security Coverage Demonstration PDF. The topics addressed in these templates are Contents Coverage, Dwelling Coverage, Personal Liability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Cloud Security Assessment Cont Background PDF
This is a Table Of Contents For Cloud Security Assessment Cont Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Security Responsibilities, Security Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Cloud Security Assessment Ideas PDF
Presenting Table Of Contents For Cloud Security Assessment Ideas PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Cloud Security, Security Different, Security Is Important. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
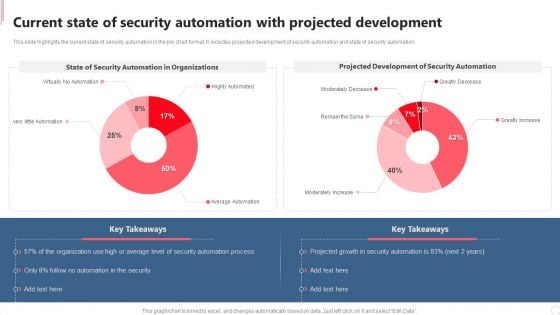
Current State Of Security Automation With Projected Development Rules PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed Current State Of Security Automation With Projected Development Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Current State Of Security Automation With Projected Development Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
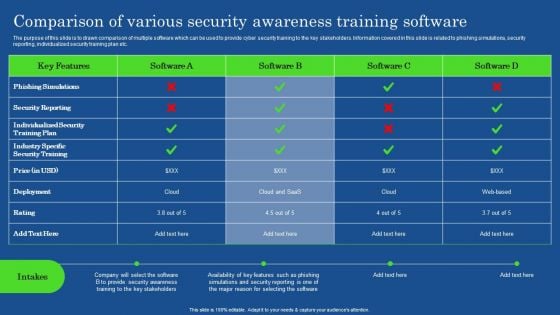
Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF
This slide depicts the main tasks of the command security operations center. The purpose of this slide is to highlight the main responsibilities, responsible team members, and task status. The main tasks include monitoring and analyzing security events, coordinating incident response, managing security operations, etc. Get a simple yet stunning designed Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Best Practices For Implementing Big Data Security Monitoring Sample pdf
This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc. Showcasing this set of slides titled Best Practices For Implementing Big Data Security Monitoring Sample pdf. The topics addressed in these templates are Preserve Data Privacy, Big Data Cryptography, Granular Access Control. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc.

Major Target Areas Of Virtual Security Hazards Summary Pdf
The following slide consists of major target points of cyber security attacks aimed at accessing, changing, or destroying sensitive information extorting money from users or interrupting normal business processes. The major targets are electronic devices, critical information, financial resources and public opinion Pitch your topic with ease and precision using this Major Target Areas Of Virtual Security Hazards Summary Pdf. This layout presents information on Financial Resources, Public Opinion, Electronic Devices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide consists of major target points of cyber security attacks aimed at accessing, changing, or destroying sensitive information extorting money from users or interrupting normal business processes. The major targets are electronic devices, critical information, financial resources and public opinion
Employee Benefits Concept Social Security Ppt PowerPoint Presentation Outline Show
Presenting this set of slides with name employee benefits concept social security ppt powerpoint presentation outline show. The topics discussed in these slides are business, planning, strategy, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Home Security Network Icon Ppt PowerPoint Presentation Portfolio Ideas
Presenting this set of slides with name home security network icon ppt powerpoint presentation portfolio ideas. The topics discussed in these slides are communication, teamwork, build network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today. This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security.

Effective Security Operations Tools To Prevent Cyber Threats Formats PDF
This slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Pitch your topic with ease and precision using this Effective Security Operations Tools To Prevent Cyber Threats Formats PDF. This layout presents information on Develops, Organization Security, Compliance Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
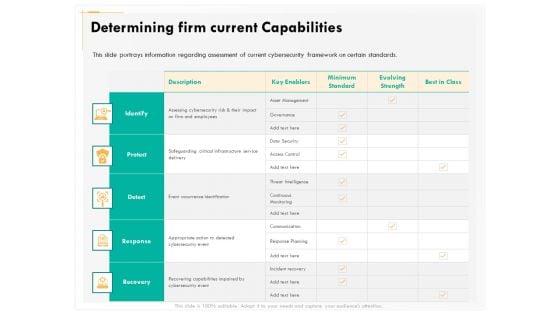
Computer Security Incident Handling Determining Firm Current Capabilities Inspiration PDF
Presenting this set of slides with name computer security incident handling determining firm current capabilities inspiration pdf. The topics discussed in these slides are identify, protect, detect, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Infrastructure Building Administration 4 Dimensions Of Infrastructure Security Designs PDF
Deliver and pitch your topic in the best possible manner with this infrastructure building administration 4 dimensions of infrastructure security designs pdf. Use them to share invaluable insights on systems applications, structured, unstructured, employees, outsources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
icons slide for cyber security administration in organization summary pdf
Presenting our innovatively structured icons slide for cyber security administration in organization summary pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.

Email Security Market Research Report Deployment Ppt Professional Tips PDF
Presenting this set of slides with name email security market research report deployment ppt professional tips pdf. The topics discussed in these slides are deployment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
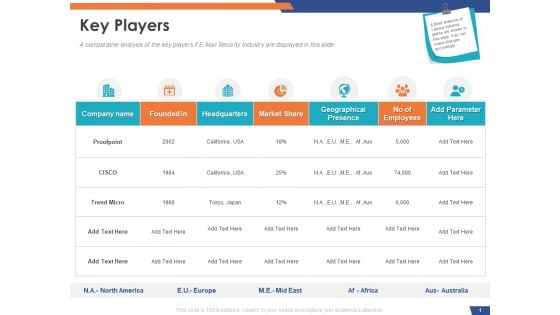
Email Security Market Research Report Key Players Ppt Model PDF
Presenting this set of slides with name email security market research report key players ppt model pdf. The topics discussed in these slides are company name, founded in, headquarters, market share, geographical presence, no of employees. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Thesis Process Research Introduction Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name security thesis process research introduction ppt powerpoint presentation complete deck. The topics discussed in these slides are process, research, introduction, interests, conclusions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Facility Operations Contol 4 Dimensions Of Infrastructure Security Brochure PDF
Presenting this set of slides with name facility operations contol 4 dimensions of infrastructure security brochure pdf. The topics discussed in these slides are people, data, applications, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































