Cloud Architecture
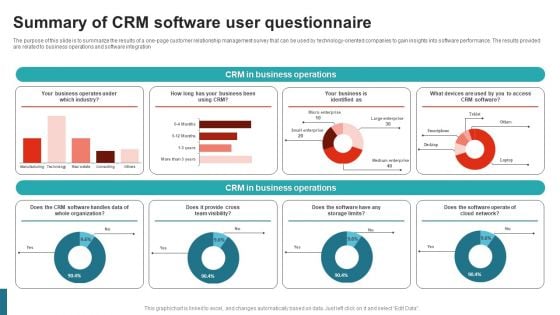
Summary Of CRM Software User Questionnaire Survey SS
The purpose of this slide is to summarize the results of a one-page customer relationship management survey that can be used by technology-oriented companies to gain insights into software performance. The results provided are related to business operations and software integration. Pitch your topic with ease and precision using this Summary Of CRM Software User Questionnaire Survey SS. This layout presents information on CRM In Business Operations, Industry, Cloud Network, Team Visibility. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
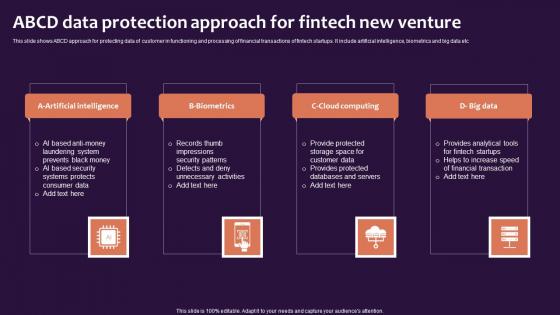
ABCD Data Protection Approach For Fintech New Venture Ideas Pdf
This slide shows ABCD approach for protecting data of customer in functioning and processing of financial transactions of fintech startups. It include artificial intelligence, biometrics and big data etc. Showcasing this set of slides titled ABCD Data Protection Approach For Fintech New Venture Ideas Pdf. The topics addressed in these templates are Biometrics, Cloud Computing, Big Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows ABCD approach for protecting data of customer in functioning and processing of financial transactions of fintech startups. It include artificial intelligence, biometrics and big data etc.
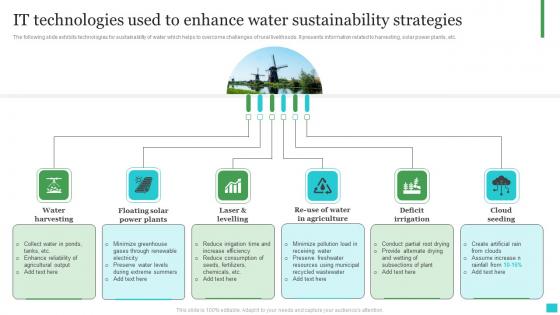
IT Technologies Used To Enhance Water Sustainability Strategies Topics Pdf
The following slide exhibits technologies for sustainability of water which helps to overcome challenges of rural livelihoods. It presents information related to harvesting, solar power plants, etc. Showcasing this set of slides titled IT Technologies Used To Enhance Water Sustainability Strategies Topics Pdf. The topics addressed in these templates are Water Harvesting, Cloud Seeding, Deficit Irrigation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide exhibits technologies for sustainability of water which helps to overcome challenges of rural livelihoods. It presents information related to harvesting, solar power plants, etc.

BYOD Policy Challenges And Mitigation Tips
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit BYOD Policy Challenges And Mitigation Tips and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide highlights challenges in implementing a Bring Your Own Device BYOD policy, including challenges like device loss, malicious apps, and insecure cloud storage. It also provides practical solutions to mitigate these risks and enhance security in the workplace.
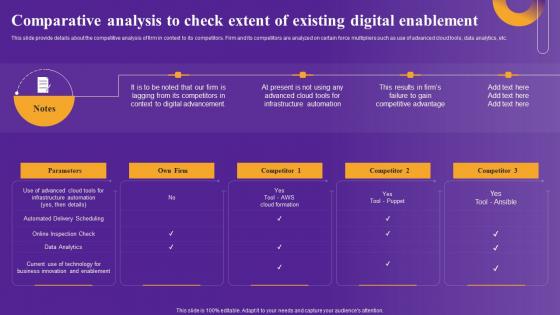
Comparative Analysis To Check Strategic Framework To Improve Digital Transformation Topics Pdf
This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis To Check Strategic Framework To Improve Digital Transformation Topics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis To Check Strategic Framework To Improve Digital Transformation Topics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc.
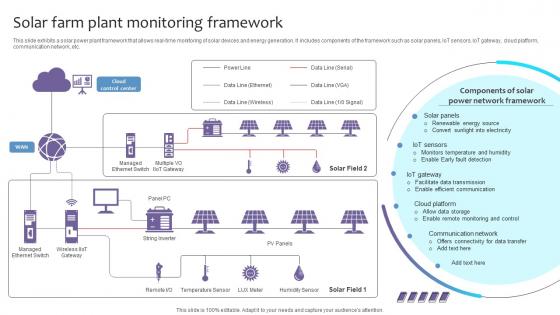
Empowering The Future Solar Farm Plant Monitoring Framework IoT SS V
This slide exhibits a solar power plant framework that allows real-time monitoring of solar devices and energy generation. It includes components of the framework such as solar panels, IoT sensors, IoT gateway, cloud platform, communication network, etc. Explore a selection of the finest Empowering The Future Solar Farm Plant Monitoring Framework IoT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Empowering The Future Solar Farm Plant Monitoring Framework IoT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide exhibits a solar power plant framework that allows real-time monitoring of solar devices and energy generation. It includes components of the framework such as solar panels, IoT sensors, IoT gateway, cloud platform, communication network, etc.
Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. This Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
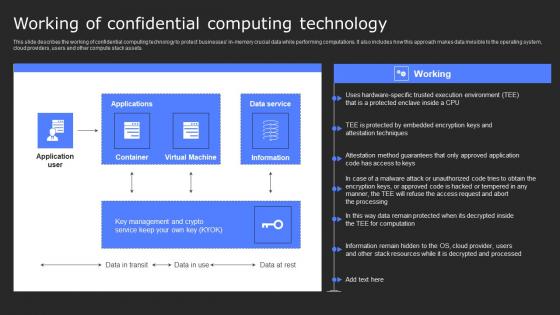
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
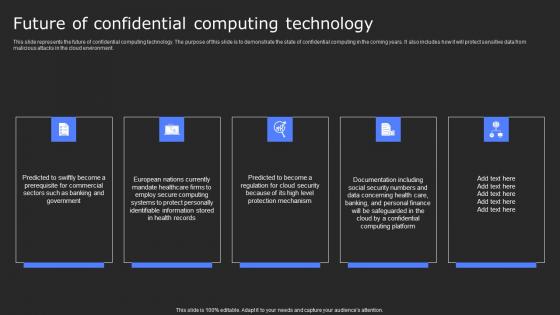
Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Presenting this PowerPoint presentation, titled Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.
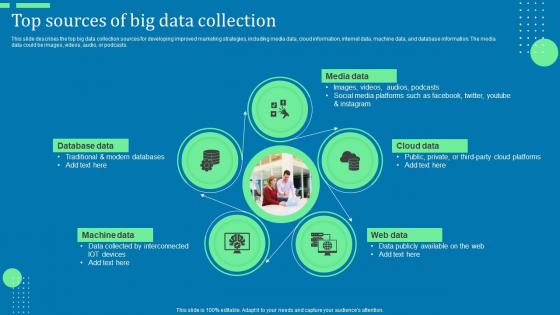
Top Sources Of Big Data Collection Advanced Tools For Hyperautomation Ppt File Background Designs Pdf
This slide describes the top big data collection sources for developing improved marketing strategies, including media data, cloud information, internet data, machine data, and database information. The media data could be images, videos, audio, or podcasts. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Top Sources Of Big Data Collection Advanced Tools For Hyperautomation Ppt File Background Designs Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Top Sources Of Big Data Collection Advanced Tools For Hyperautomation Ppt File Background Designs Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide describes the top big data collection sources for developing improved marketing strategies, including media data, cloud information, internet data, machine data, and database information. The media data could be images, videos, audio, or podcasts.
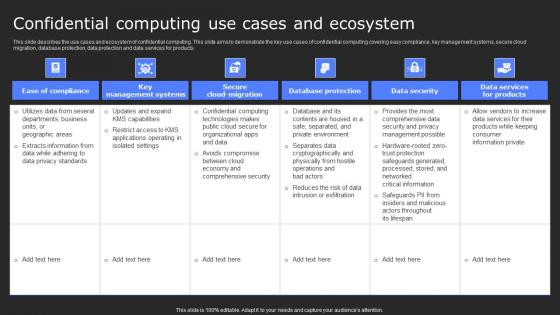
Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. The Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
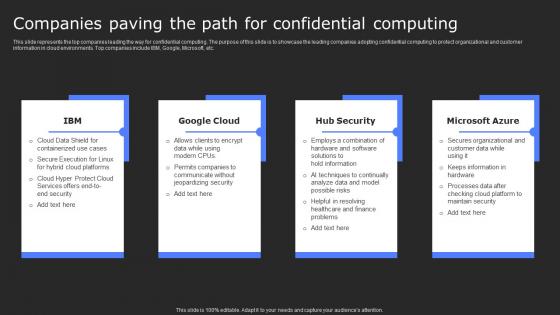
Companies Paving The Path For Confidential Secure Computing Framework Download Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Present like a pro with Companies Paving The Path For Confidential Secure Computing Framework Download Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
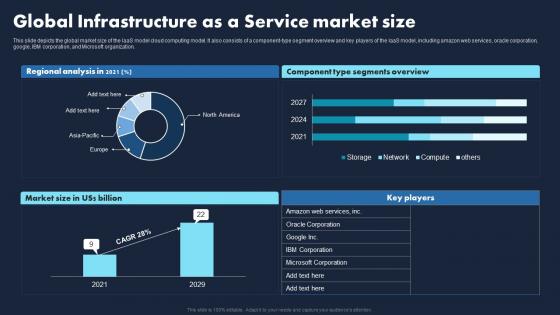
Global Infrastructure As A Service Market Size Transforming Business With IaaS Designs Pdf
This slide depicts the global market size of the IaaS model cloud computing model. It also consists of a component-type segment overview and key players of the laaS model, including amazon web services, oracle corporation, google, IBM corporation, and Microsoft organization. Create an editable Global Infrastructure As A Service Market Size Transforming Business With IaaS Designs Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Global Infrastructure As A Service Market Size Transforming Business With IaaS Designs Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide depicts the global market size of the IaaS model cloud computing model. It also consists of a component-type segment overview and key players of the laaS model, including amazon web services, oracle corporation, google, IBM corporation, and Microsoft organization.
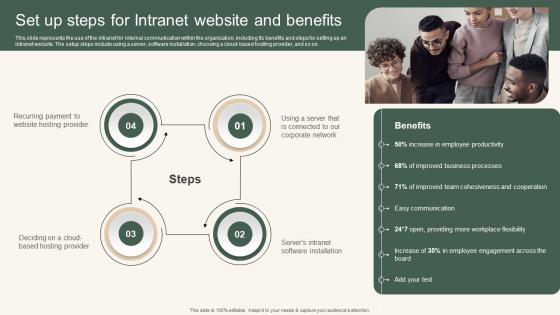
Set Up Steps For Intranet Instant Messenger For Internal Business Operations Designs Pdf
This slide represents the use of the intranet for internal communication within the organization, including its benefits and steps for setting up an intranet website. The setup steps include using a server, software installation, choosing a cloud based hosting provider, and so on. Present like a pro with Set Up Steps For Intranet Instant Messenger For Internal Business Operations Designs Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the use of the intranet for internal communication within the organization, including its benefits and steps for setting up an intranet website. The setup steps include using a server, software installation, choosing a cloud based hosting provider, and so on.

Essential Steps For Effective Digital Service Management Public Sector Digital Solutions Infographics Pdf
This slide provides information regarding essential steps for effective digital service management in terms of determining firms cloud strategy, detecting vital services relevant for firm and managing KPIs for business. It helps executive stakeholders to progress in transformation strategy. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Essential Steps For Effective Digital Service Management Public Sector Digital Solutions Infographics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Essential Steps For Effective Digital Service Management Public Sector Digital Solutions Infographics Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide provides information regarding essential steps for effective digital service management in terms of determining firms cloud strategy, detecting vital services relevant for firm and managing KPIs for business. It helps executive stakeholders to progress in transformation strategy.

Future Of Confidential Computing Technology Secure Multi Party Rules Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Slidegeeks has constructed Future Of Confidential Computing Technology Secure Multi Party Rules Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.
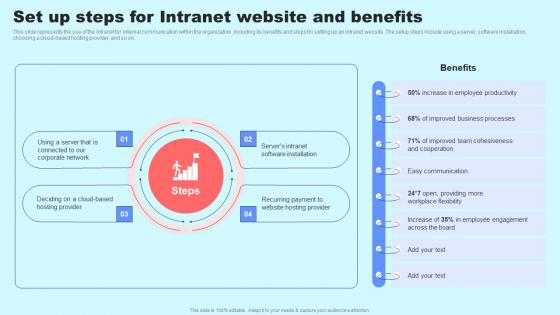
Social Media In Customer Support Set Up Steps For Intranet Website And Benefits Infographics Pdf
This slide represents the use of the intranet for internal communication within the organization, including its benefits and steps for setting up an intranet website. The setup steps include using a server, software installation, choosing a cloud based hosting provider, and so on. Slidegeeks has constructed Social Media In Customer Support Set Up Steps For Intranet Website And Benefits Infographics Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. This slide represents the use of the intranet for internal communication within the organization, including its benefits and steps for setting up an intranet website. The setup steps include using a server, software installation, choosing a cloud based hosting provider, and so on.
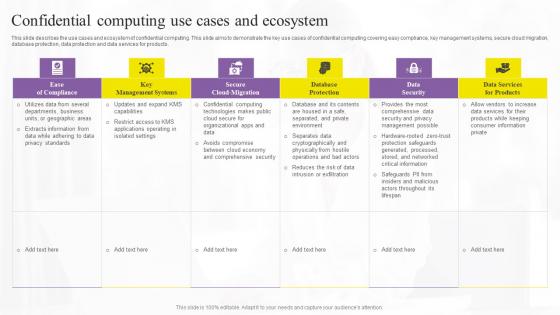
Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Slidegeeks has constructed Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
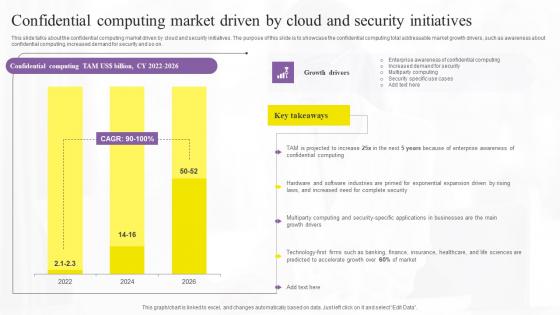
Confidential Computing Market Driven Confidential Computing Technologies Rules Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. This modern and well-arranged Confidential Computing Market Driven Confidential Computing Technologies Rules Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
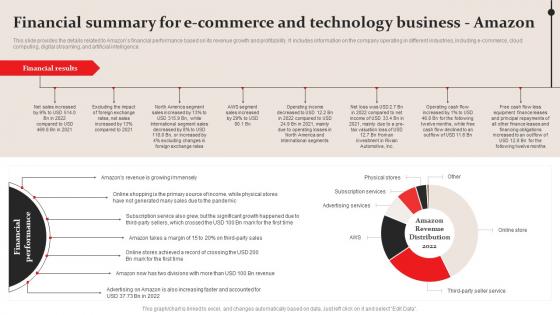
Financial Summary For E Commerce Amazon Business Plan Go To Market Strategy Template Pdf
This slide provides the details related to Amazons financial performance based on its revenue growth and profitability. It includes information on the company operating in different industries, including e commerce, cloud computing, digital streaming, and artificial intelligence. This modern and well arranged Financial Summary For E Commerce Amazon Business Plan Go To Market Strategy Template Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide provides the details related to Amazons financial performance based on its revenue growth and profitability. It includes information on the company operating in different industries, including e commerce, cloud computing, digital streaming, and artificial intelligence.
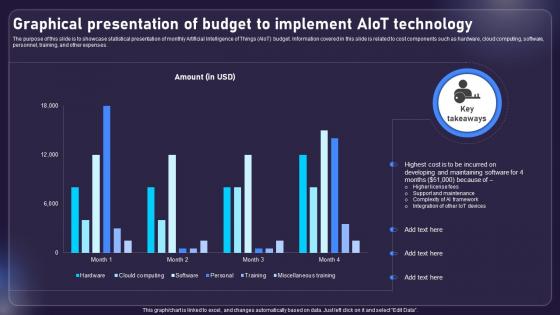
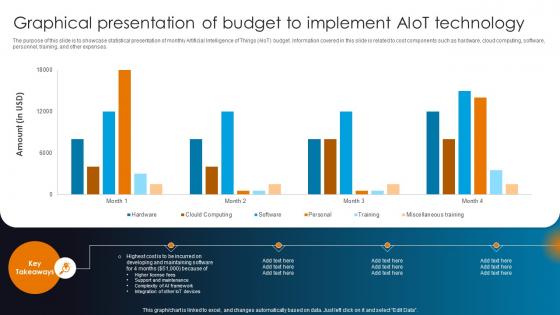
Graphical Presentation Of Budget To Implement AIOT AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase statistical presentation of monthly Artificial Intelligence of Things AIoT budget. Information covered in this slide is related to cost components such as hardware, cloud computing, software, personnel, training, and other expenses. This modern and well-arranged Graphical Presentation Of Budget To Implement AIOT AIOT Applications For Various Industries IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The purpose of this slide is to showcase statistical presentation of monthly Artificial Intelligence of Things AIoT budget. Information covered in this slide is related to cost components such as hardware, cloud computing, software, personnel, training, and other expenses.

Introduction To Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. This modern and well-arranged Introduction To Next Generation Secure Web Gateway Web Threat Protection System provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.
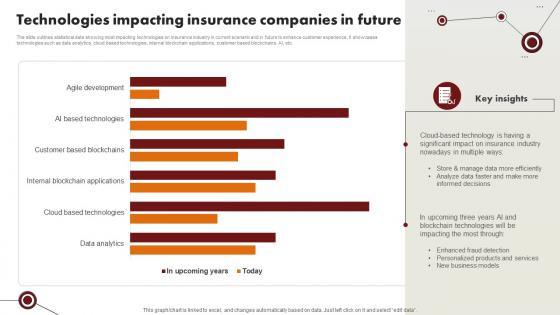
Technology Trends In Online Insurance Technologies Impacting Insurance Companies In Future
The slide outlines statistical data showing most impacting technologies on insurance industry in current scenario and in future to enhance customer experience, It showcases technologies such as data analytics, cloud based technologies, internal blockchain applications, customer based blockchains, AI, etc. This modern and well-arranged Technology Trends In Online Insurance Technologies Impacting Insurance Companies In Future provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide outlines statistical data showing most impacting technologies on insurance industry in current scenario and in future to enhance customer experience, It showcases technologies such as data analytics, cloud based technologies, internal blockchain applications, customer based blockchains, AI, etc.
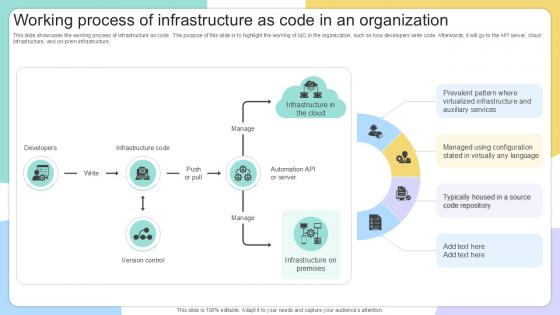
Working Process Of Infrastructure IAC Tools For Performance Analysis PPT PowerPoint
This slide showcases the working process of infrastructure as code. The purpose of this slide is to highlight the working of IaC in the organization, such as how developers write code. Afterwards, it will go to the API server, cloud infrastructure, and on-prem infrastructure. This modern and well-arranged Working Process Of Infrastructure IAC Tools For Performance Analysis PPT PowerPoint provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcases the working process of infrastructure as code. The purpose of this slide is to highlight the working of IaC in the organization, such as how developers write code. Afterwards, it will go to the API server, cloud infrastructure, and on-prem infrastructure.
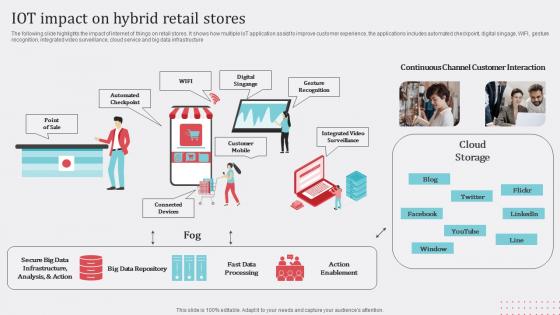
IoT Impact On Hybrid How Industrial IoT Is Changing Worldwide Themes Pdf
The following slide highlights the impact of internet of things on retail stores. It shows how multiple IoT application assist to improve customer experience, the applications includes automated checkpoint, digital singage, WIFI, gesture recognition, integrated video surveillance, cloud service and big data infrastructure. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IoT Impact On Hybrid How Industrial IoT Is Changing Worldwide Themes Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IoT Impact On Hybrid How Industrial IoT Is Changing Worldwide Themes Pdf The following slide highlights the impact of internet of things on retail stores. It shows how multiple IoT application assist to improve customer experience, the applications includes automated checkpoint, digital singage, WIFI, gesture recognition, integrated video surveillance, cloud service and big data infrastructure
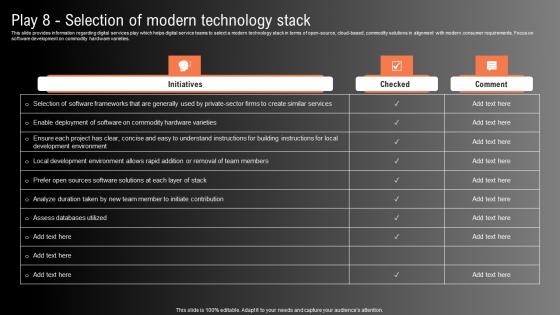
Play 8 Selection Of Modern Technology Stack Technological Innovation Playbook Graphics Pdf
This slide provides information regarding digital services play which helps digital service teams to select a modern technology stack in terms of open source, cloud based, commodity solutions in alignment with modern consumer requirements. Focus on software development on commodity hardware varieties. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Play 8 Selection Of Modern Technology Stack Technological Innovation Playbook Graphics Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Play 8 Selection Of Modern Technology Stack Technological Innovation Playbook Graphics Pdf This slide provides information regarding digital services play which helps digital service teams to select a modern technology stack in terms of open source, cloud based, commodity solutions in alignment with modern consumer requirements. Focus on software development on commodity hardware varieties.

Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck
This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches.
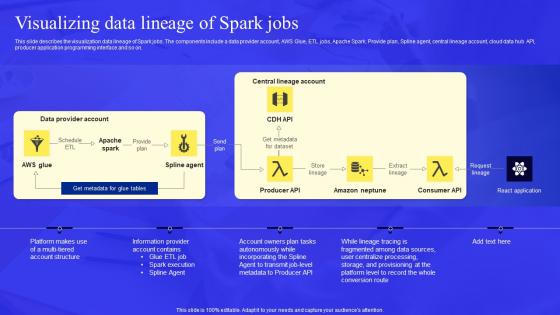
Business Process Data Lineage Visualizing Data Lineage Of Spark Jobs Ideas Pdf
This slide describes the visualization data lineage of Spark jobs. The components include a data provider account, AWS Glue, ETL jobs, Apache Spark, Provide plan, Spline agent, central lineage account, cloud data hub API, producer application programming interface and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Business Process Data Lineage Visualizing Data Lineage Of Spark Jobs Ideas Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the visualization data lineage of Spark jobs. The components include a data provider account, AWS Glue, ETL jobs, Apache Spark, Provide plan, Spline agent, central lineage account, cloud data hub API, producer application programming interface and so on.
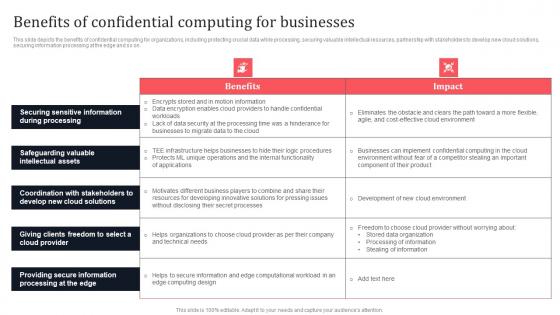
Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Do you know about Slidesgeeks Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.
Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
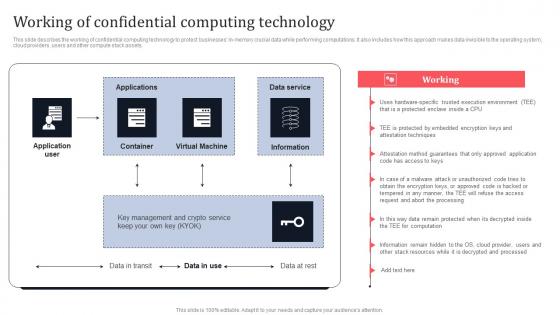
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
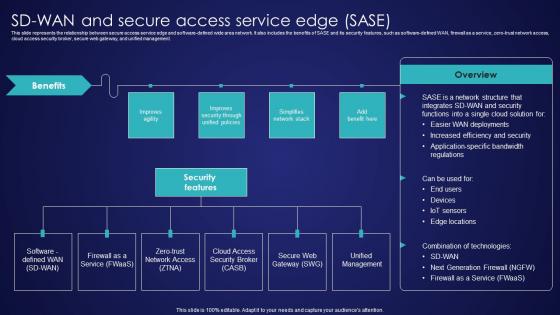
SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Welcome to our selection of the SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management.
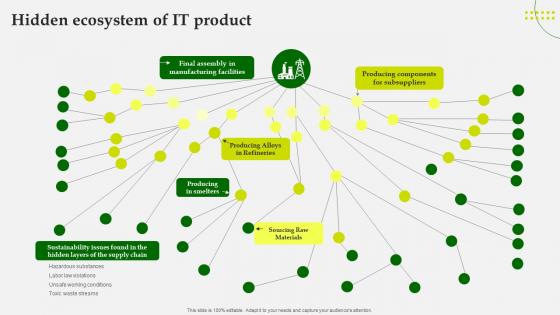
Green Computing Hidden Ecosystem Of It Product
This slide represents thepositive effect of green cloud computing on the environment. The purpose of this slide is to showcase how green IT is providing a more sustainable environment through fewer carbon footprints, less paper usage, less power consumption, providing reliable infrastructure, and so on. Welcome to our selection of the Green Computing Hidden Ecosystem Of It Product These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents thepositive effect of green cloud computing on the environment. The purpose of this slide is to showcase how green IT is providing a more sustainable environment through fewer carbon footprints, less paper usage, less power consumption, providing reliable infrastructure, and so on.
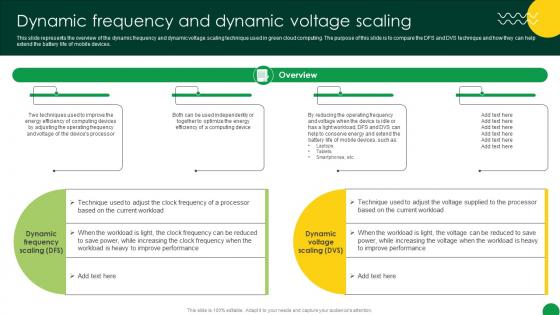
Sustainable Dynamic Frequency And Dynamic Voltage Scaling
This slide represents the overview of the dynamic frequency and dynamic voltage scaling technique used in green cloud computing. The purpose of this slide is to compare the DFS and DVS technique and how they can help extend the battery life of mobile devices. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Sustainable Dynamic Frequency And Dynamic Voltage Scaling to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the overview of the dynamic frequency and dynamic voltage scaling technique used in green cloud computing. The purpose of this slide is to compare the DFS and DVS technique and how they can help extend the battery life of mobile devices.

Secure Web Gateway For Remote And On Site Workers Web Threat Protection System
This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Do you know about Slidesgeeks Secure Web Gateway For Remote And On Site Workers Web Threat Protection System These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees.
Integrating AI With IoT Graphical Presentation Of Budget To Implement AIoT Technology IoT SS V
The purpose of this slide is to showcase statistical presentation of monthly Artificial Intelligence of Things AIoT budget. Information covered in this slide is related to cost components such as hardware, cloud computing, software, personnel, training, and other expenses. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integrating AI With IoT Graphical Presentation Of Budget To Implement AIoT Technology IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The purpose of this slide is to showcase statistical presentation of monthly Artificial Intelligence of Things AIoT budget. Information covered in this slide is related to cost components such as hardware, cloud computing, software, personnel, training, and other expenses.
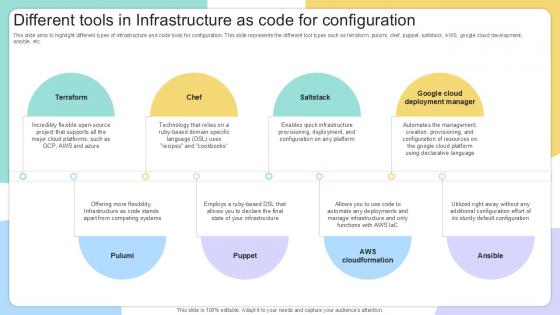
Different Tools In Infrastructure As Code IAC Tools For Performance Analysis PPT Example
This slide aims to highlight different types of infrastructure and code tools for configuration. This slide represents the different tool types such as terraform, pulumi, chef, puppet, saltstack, AWS, google cloud development, ansible, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Different Tools In Infrastructure As Code IAC Tools For Performance Analysis PPT Example to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide aims to highlight different types of infrastructure and code tools for configuration. This slide represents the different tool types such as terraform, pulumi, chef, puppet, saltstack, AWS, google cloud development, ansible, etc.
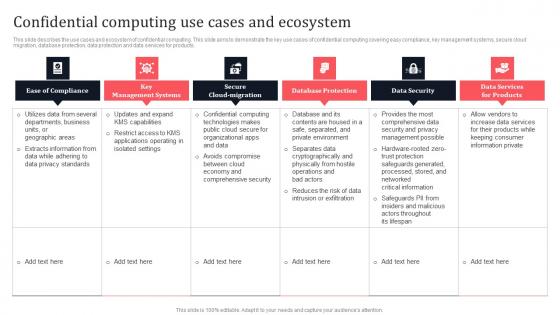
Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Explore a selection of the finest Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
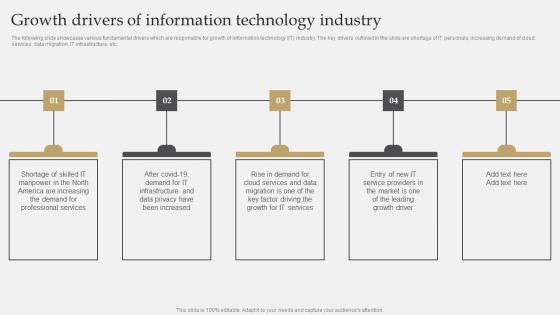
IT Industry Market Research Growth Drivers Of Information Technology Industry Infographics Pdf
The following slide showcases various fundamental drivers which are responsible for growth of information technology IT industry. The key drivers outlined in the slide are shortage of IT personals, increasing demand of cloud services, data migration, IT infrastructure, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than IT Industry Market Research Growth Drivers Of Information Technology Industry Infographics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab IT Industry Market Research Growth Drivers Of Information Technology Industry Infographics Pdf today and make your presentation stand out from the rest. The following slide showcases various fundamental drivers which are responsible for growth of information technology IT industry. The key drivers outlined in the slide are shortage of IT personals, increasing demand of cloud services, data migration, IT infrastructure, etc.
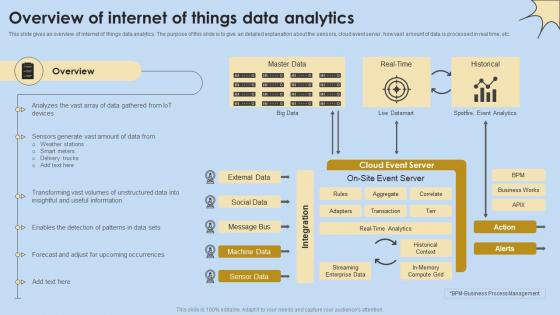
Overview Of Internet Of Things Data Analytics Internet Of Things Analysis Clipart Pdf
This slide gives an overview of internet of things data analytics. The purpose of this slide is to give an detailed explanation about the sensors, cloud event server, how vast amount of data is processed in real time, etc. Retrieve professionally designed Overview Of Internet Of Things Data Analytics Internet Of Things Analysis Clipart Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide gives an overview of internet of things data analytics. The purpose of this slide is to give an detailed explanation about the sensors, cloud event server, how vast amount of data is processed in real time, etc.

Essential Requirements Hiring Enhancing Customer Service Operations Using CRM Technology Graphics Pdf
Following slide provides glimpse of hiring development to assure successful development of billing system. It includes benefits and requirements such as knowledge of cloud computing, machine learning, soft skills etc. If you are looking for a format to display your unique thoughts, then the professionally designed Essential Requirements Hiring Enhancing Customer Service Operations Using CRM Technology Graphics Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Essential Requirements Hiring Enhancing Customer Service Operations Using CRM Technology Graphics Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Following slide provides glimpse of hiring development to assure successful development of billing system. It includes benefits and requirements such as knowledge of cloud computing, machine learning, soft skills etc.

Use Case 2 Box And Oc Public Works Ultimate Guide To Adopt Box Infographics PDF
This slide showcases case study of box cloud implementation on OC public works. It further includes company name, industry, company size, year founded, objective, challenges faced, solutions and results, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Use Case 2 Box And Oc Public Works Ultimate Guide To Adopt Box Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Use Case 2 Box And Oc Public Works Ultimate Guide To Adopt Box Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases case study of box cloud implementation on OC public works. It further includes company name, industry, company size, year founded, objective, challenges faced, solutions and results, etc.
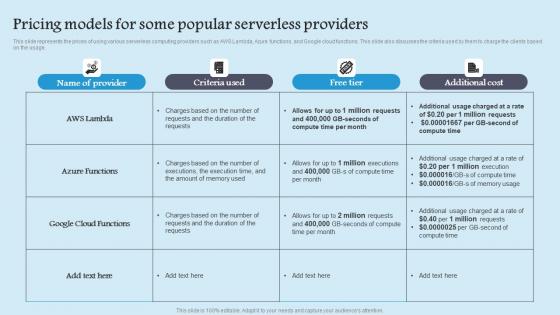
Pricing Models For Some Role Serverless Computing Modern Technology Themes Pdf
This slide represents the prices of using various serverless computing providers such as AWS Lambda, Azure functions, and Google cloud functions. This slide also discusses the criteria used by them to charge the clients based on the usage. Get a simple yet stunning designed Pricing Models For Some Role Serverless Computing Modern Technology Themes Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Pricing Models For Some Role Serverless Computing Modern Technology Themes Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the prices of using various serverless computing providers such as AWS Lambda, Azure functions, and Google cloud functions. This slide also discusses the criteria used by them to charge the clients based on the usage.
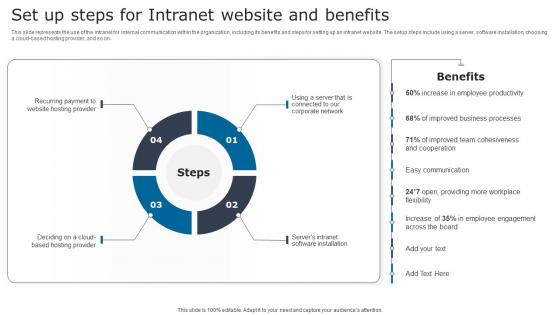
Set Up Steps For Intranet Digital Signage In Internal Communication Channels Guidelines Pdf
This slide represents the use of the intranet for internal communication within the organization, including its benefits and steps for setting up an intranet website. The setup steps include using a server, software installation, choosing a cloud based hosting provider, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Set Up Steps For Intranet Digital Signage In Internal Communication Channels Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Set Up Steps For Intranet Digital Signage In Internal Communication Channels Guidelines Pdf today and make your presentation stand out from the rest This slide represents the use of the intranet for internal communication within the organization, including its benefits and steps for setting up an intranet website. The setup steps include using a server, software installation, choosing a cloud based hosting provider, and so on.
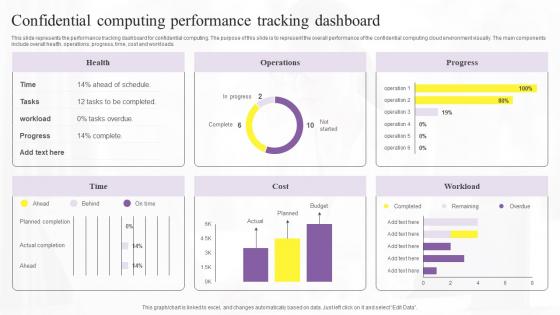
Confidential Computing Performance Confidential Computing Technologies Brochure Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. This Confidential Computing Performance Confidential Computing Technologies Brochure Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Performance Confidential Computing Technologies Brochure Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
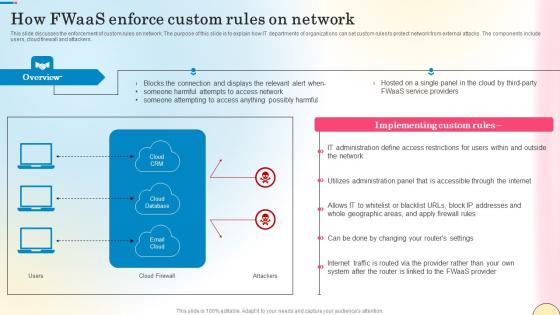
How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf
This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers. This How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers.
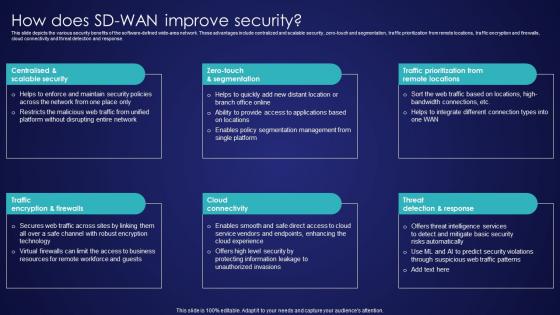
How Does SD Wan Improve Security Wide Area Network Services Structure Pdf
This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than How Does SD Wan Improve Security Wide Area Network Services Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab How Does SD Wan Improve Security Wide Area Network Services Structure Pdf today and make your presentation stand out from the rest. This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response.
Major Milestones Achieved Nubity Capital Funding Pitch Deck Icons Pdf
This slide covers major milestone achieved by cloud managing and monitoring platform. It involves awards such as rising star partner of the year and innovation partner of the year. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Nubity Capital Funding Pitch Deck Icons Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Nubity Capital Funding Pitch Deck Icons Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers major milestone achieved by cloud managing and monitoring platform. It involves awards such as rising star partner of the year and innovation partner of the year.
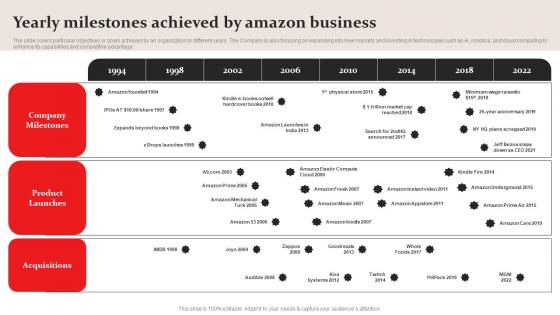
Yearly Milestones Achieved By Amazon Business Plan Go To Market Strategy Download Pdf
The slide covers particular objectives or goals achieved by an organization in different years. The Company is also focusing on expanding into new markets and investing in technologies such as AI, robotics, and cloud computing to enhance its capabilities and competitive advantage. Get a simple yet stunning designed Yearly Milestones Achieved By Amazon Business Plan Go To Market Strategy Download Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Yearly Milestones Achieved By Amazon Business Plan Go To Market Strategy Download Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide covers particular objectives or goals achieved by an organization in different years. The Company is also focusing on expanding into new markets and investing in technologies such as AI, robotics, and cloud computing to enhance its capabilities and competitive advantage.

Case Study How Phillips Improves Employee Comfort AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase comprehensive case study of how Phillips enhanced employees comfort with Google Cloud Internet of Things IoT services. Information covered in this slide is related to issues faced, solutions offered, and result. Slidegeeks is here to make your presentations a breeze with Case Study How Phillips Improves Employee Comfort AIOT Applications For Various Industries IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The purpose of this slide is to showcase comprehensive case study of how Phillips enhanced employees comfort with Google Cloud Internet of Things IoT services. Information covered in this slide is related to issues faced, solutions offered, and result.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Green Computing Nano Data Center Overview And Advantages
This slide describes the role of nano data centers in green cloud computing, including their benefits. The purpose of this slide is to showcase the various advantages of nano data centers, including energy efficiency, reduced costs, scalability, improved performance, flexibility, and resilience. This Green Computing Nano Data Center Overview And Advantages from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide describes the role of nano data centers in green cloud computing, including their benefits. The purpose of this slide is to showcase the various advantages of nano data centers, including energy efficiency, reduced costs, scalability, improved performance, flexibility, and resilience.

Sustainable Types Of Green Data Centers Energy Efficient
This slide outlines the overview of energy efficient types of green data centers. The purpose of this slide is to showcase the different energy efficiency methods, including cooling systems, green cloud technology and community heating and cooling. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Sustainable Types Of Green Data Centers Energy Efficient. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Sustainable Types Of Green Data Centers Energy Efficient today and make your presentation stand out from the rest This slide outlines the overview of energy efficient types of green data centers. The purpose of this slide is to showcase the different energy efficiency methods, including cooling systems, green cloud technology and community heating and cooling.
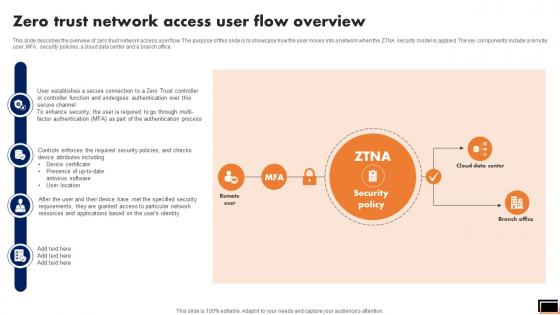
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Key Erp Trends Optimizing Manufacturing Operations Erp And Digital Transformation For Maximizing DT SS V
This slide analysis key trends in manufacturing enterprise resource planning that help innovate for companies to capture benefits across their value chain. It mentions trends such as devices and industrial internet of things IIoT with ERP, Cloud ERP, supply chain information and collaboration, remote access, anywhere, anytime, and role of artificial intelligence AI and ERP.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Key Erp Trends Optimizing Manufacturing Operations Erp And Digital Transformation For Maximizing DT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide analysis key trends in manufacturing enterprise resource planning that help innovate for companies to capture benefits across their value chain. It mentions trends such as devices and industrial internet of things IIoT with ERP, Cloud ERP, supply chain information and collaboration, remote access, anywhere, anytime, and role of artificial intelligence AI and ERP.

Current Trends Enhancing Performance Of Secure Web Gateway Web Threat Protection System
This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc. Slidegeeks is here to make your presentations a breeze with Current Trends Enhancing Performance Of Secure Web Gateway Web Threat Protection System With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc.
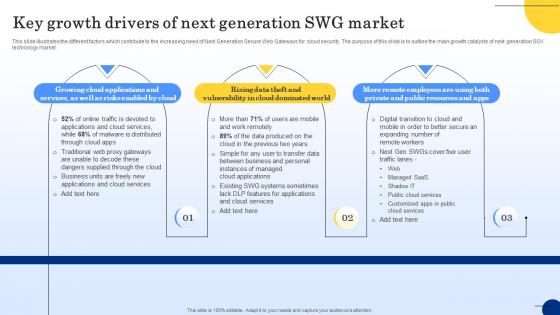
Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Explore a selection of the finest Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.

Generative AI Tool Competent In Solving Anything ChatGPT How Generative AI Tools Work AI SS V
This slide provides information regarding the insights about ChatGPT platform , an AI-based language model that is developed on deep learning methodology which uses an artificial neural network for generating humanoid text. It includes details related to its owner, userbase, cloud infrastructure, purpose of ChatGPT, etc. Retrieve professionally designed Generative AI Tool Competent In Solving Anything ChatGPT How Generative AI Tools Work AI SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide provides information regarding the insights about ChatGPT platform , an AI-based language model that is developed on deep learning methodology which uses an artificial neural network for generating humanoid text. It includes details related to its owner, userbase, cloud infrastructure, purpose of ChatGPT, etc.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.


 Continue with Email
Continue with Email

 Home
Home


































