Cloud Comparison
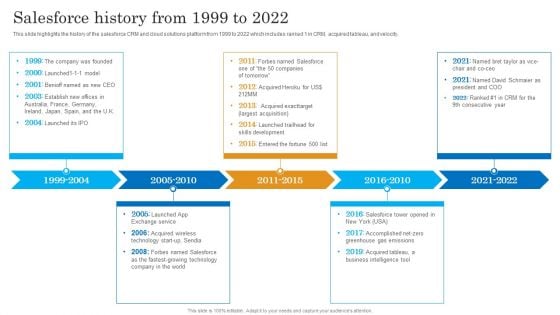
Salesforce History From 1999 To 2022 Salesforce Business Profile Brochure PDF
This slide highlights the history of the salesforce CRM and cloud solutions platform from 1999 to 2022 which includes ranked 1 in CRM, acquired tableau, and velocity. This is a Salesforce History From 1999 To 2022 Salesforce Business Profile Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Exchange Service, Acquired Wireless, Technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
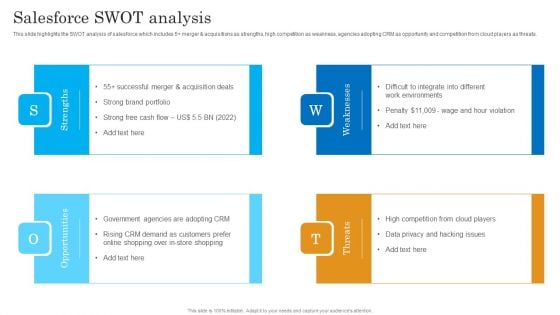
Salesforce SWOT Analysis Salesforce Business Profile Guidelines PDF
This slide highlights the SWOT analysis of salesforce which includes 5 merger and acquisitions as strengths, high competition as weakness, agencies adopting CRM as opportunity and competition from cloud players as threats. This is a Salesforce SWOT Analysis Salesforce Business Profile Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Opportunities, Threats, Weaknesses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Estate Company Details Case Study Ppt PowerPoint Presentation File Ideas PDF
This slide shows the case study which includes challenge faced by client to gain real time project visibility, evaluate temperature differentials, etc. that our company considered and offered cloud based analytics software to reduce monitoring expenses.This is a Real Estate Company Details Case Study Ppt PowerPoint Presentation File Ideas PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Key Challenge, Solution, Cellular Connectivity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
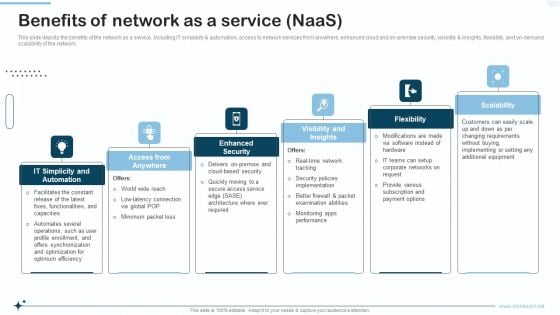
Naas Integrated Solution IT Benefits Of Network As A Service Naas Themes PDF
This slide depicts the benefits of the network as a service, including IT simplicity and automation, access to network services from anywhere, enhanced cloud and on premise security, visibility and insights, flexibility, and on-demand scalability of the network. This is a olution IT Benefits Of Network As A Service Naas Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Flexibility Scalability, Visibility And Insights. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
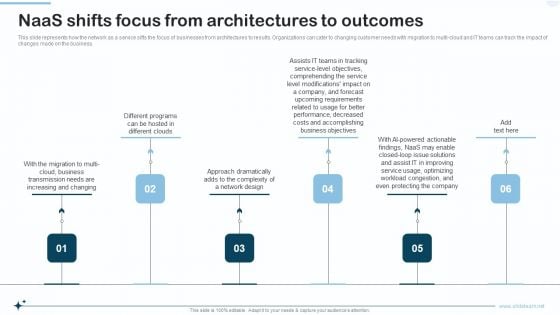
Naas Integrated Solution IT Naas Shifts Focus From Architectures To Outcomes Background PDF
This slide represents how the network as a service sifts the focus of businesses from architectures to results. Organizations can cater to changing customer needs with migration to multi cloud and IT teams can track the impact of changes made on the business. This is a Naas Integrated Solution IT Naas Shifts Focus From Architectures To Outcomes Background PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirements, Business Objectives, Costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
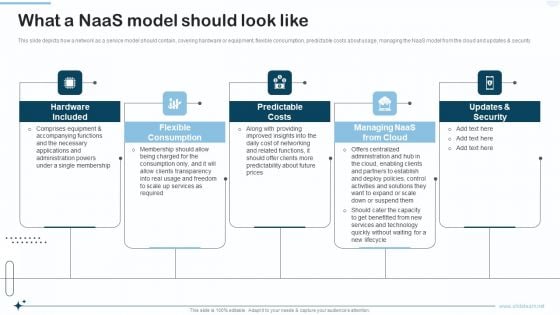
Naas Integrated Solution IT What A Naas Model Should Look Like Brochure PDF
This slide depicts how a network as a service model should contain, covering hardware or equipment, flexible consumption, predictable costs about usage, managing the NaaS model from the cloud and updates and security. This is a Naas Integrated Solution IT What A Naas Model Should Look Like Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Flexible Consumption, Predictable Costs, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Change Drivers Why Converge Managing Organizational Transformation Template PDF
This slide covers the change drivers which are driving the IT OT convergence growth such as new edge to cloud architectures and new industrial connectivity protocols. This is a Change Drivers Why Converge Managing Organizational Transformation Template PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Change Drivers, Connectivity Protocols, Industrial Assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
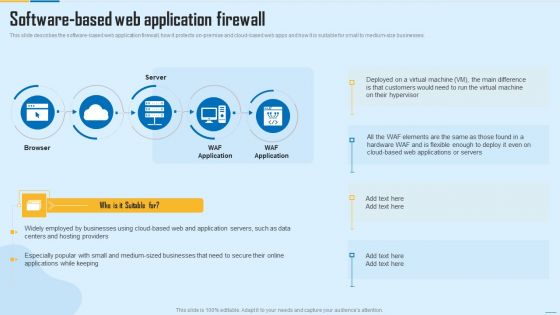
Software Based Web Application Firewall WAF Platform Demonstration PDF
This slide describes the software based web application firewall, how it protects on premise and cloud based web apps and how it is suitable for small to medium size businesses. This is a Software Based Web Application Firewall WAF Platform Demonstration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like WAF Application, Application Servers, Businesses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
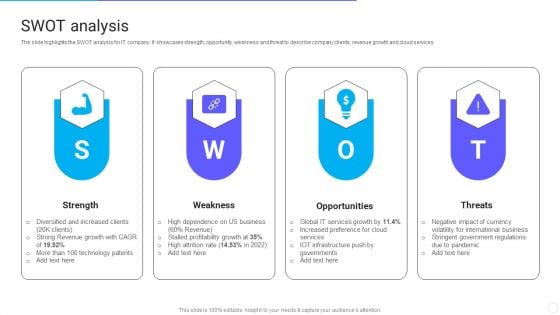
IT Application Services Company Outline SWOT Analysis Portrait PDF
The slide highlights the SWOT analysis for IT company. It showcases strength, opportunity, weakness and threat to describe company clients, revenue growth and cloud services. This is a IT Application Services Company Outline SWOT Analysis Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strength, Weakness, Opportunities, Threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
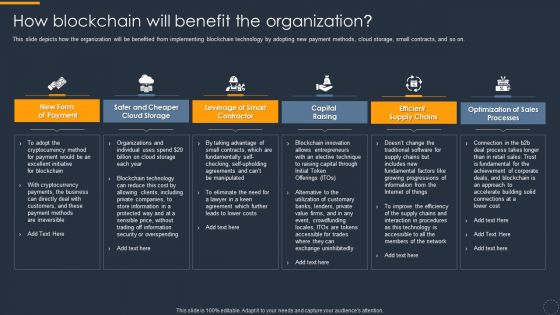
Cryptocurrency Ledger How Blockchain Will Benefit The Organization Brochure PDF
This slide depicts how the organization will be benefited from implementing blockchain technology by adopting new payment methods, cloud storage, small contracts, and so on. This is a Cryptocurrency Ledger How Blockchain Will Benefit The Organization Brochure PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Capital Raising, Efficient Supply Chains, Optimization Of Sales Processes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
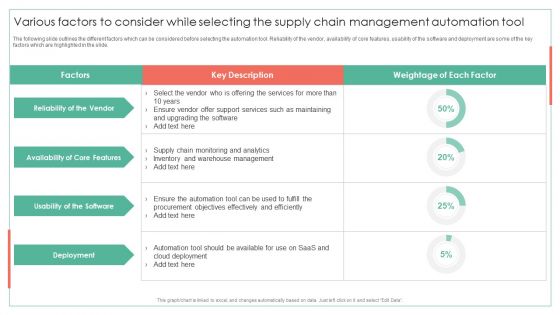
Various Factors To Consider While Selecting The Supply Chain Achieving Operational Efficiency Template PDF
The following slide outlines the different factors which can be considered before selecting the automation tool. Reliability of the vendor, availability of core features, usability of the software and deployment are some of the key factors which are highlighted in the slide.Deliver an awe inspiring pitch with this creative Various Factors To Consider While Selecting The Supply Chain Achieving Operational Efficiency Template PDF bundle. Topics like Reliability Vendor, Cloud Deployment, Objectives Effectively can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Deployment Of Smart Factory Solutions Budget Plan For Smart Manufacturing Implementation Topics PDF
This slide represents budget plan for smart manufacturing implementation. It includes cloud computing, augmented reality, sustainable manufacturing, equipment sensors etc. This is a Deployment Of Smart Factory Solutions Budget Plan For Smart Manufacturing Implementation Topics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Augmented Reality, Sensors Of Equipment, Sustainable Manufacturing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Visibility And Management Challenges Demonstration PDF
This slide covers the challenges faced by the organization in visibility management of the multi cloud such as difficulty in performance management, difficulty in troubleshooting performance and many more. This is a Visibility And Management Challenges Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Applications, Network, Systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
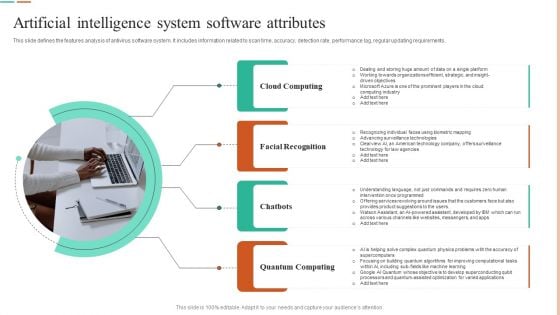
Artificial Intelligence System Software Attributes Formats PDF
This slide defines the features analysis of antivirus software system. It includes information related to scan time, accuracy, detection rate, performance lag, regular updating requirements. Persuade your audience using this Artificial Intelligence System Software Attributes Formats PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Computing, Facial Recognition, Quantum Computing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
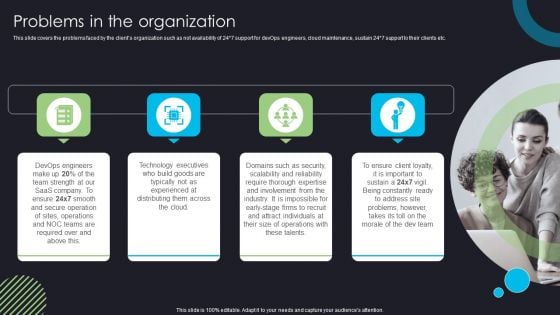
Devops Deployment And Transformation Services Advisory Problems In The Organization Microsoft PDF
This slide covers the problems faced by the clients organization such as not availability of 24 7 support for devOps engineers, cloud maintenance, sustain 24 7 support to their clients etc. Elevate your presentations with our intuitive Devops Deployment And Transformation Services Advisory Problems In The Organization Microsoft PDF template. Whether youre delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression.

Devops Deployment And Transformation Services Advisory Solutions For Devops Transformation Mockup PDF
This slide covers the DevOps transformation services such as tools optimization, performance testing, defining TOM, cloud readiness and migration etc. Elevate your presentations with our intuitive Devops Deployment And Transformation Services Advisory Solutions For Devops Transformation Mockup PDF template. Whether youre delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression.
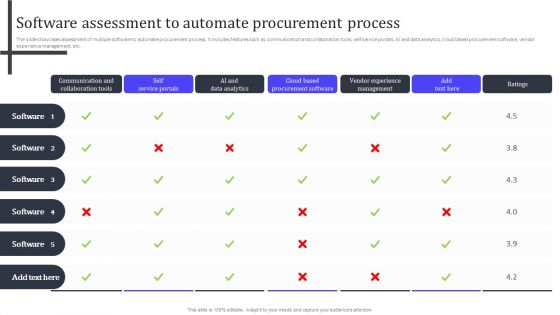
Software Assessment To Automate Procurement Process Ppt PowerPoint Presentation File Files PDF
The slide showcases assessment of multiple software to automate procurement process. It includes features such as communication and collaboration tools, self service portals, AI and data analytics, cloud based procurement software, vendor experience management, etc. There are so many reasons you need a Software Assessment To Automate Procurement Process Ppt PowerPoint Presentation File Files PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
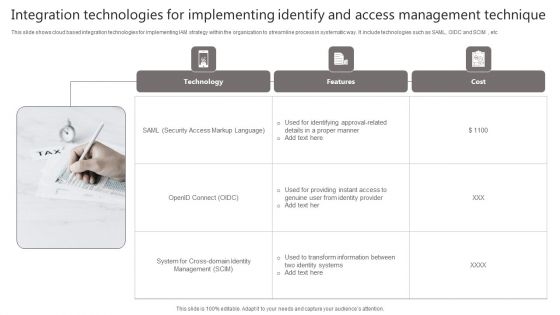
Integration Technologies For Implementing Identify And Access Management Technique Portrait PDF
This slide shows cloud based integration technologies for implementing IAM strategy within the organization to streamline process in systematic way. It include technologies such as SAML, OIDC and SCIM , etc Presenting Integration Technologies For Implementing Identify And Access Management Technique Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Technology, Features, Cost. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
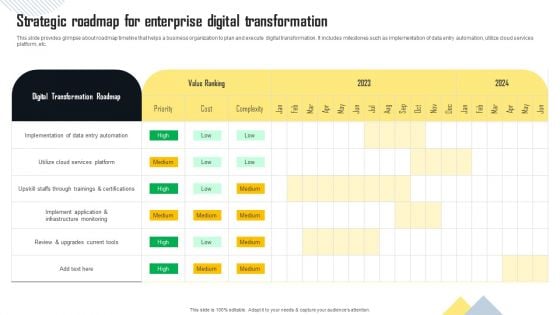
Strategic Roadmap For Enterprise Digital Transformation Demonstration PDF
This slide provides glimpse about roadmap timeline that helps a business organization to plan and execute digital transformation. It includes milestones such as implementation of data entry automation, utilize cloud services platform, etc. This Strategic Roadmap For Enterprise Digital Transformation Demonstration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
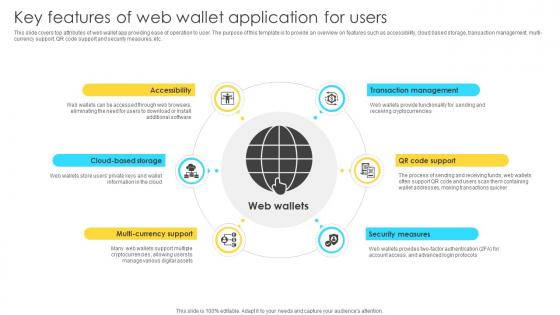
Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V
This slide covers top attributes of web wallet app providing ease of operation to user. The purpose of this template is to provide an overview on features such as accessibility, cloud based storage, transaction management, multi-currency support, QR code support and security measures, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers top attributes of web wallet app providing ease of operation to user. The purpose of this template is to provide an overview on features such as accessibility, cloud based storage, transaction management, multi-currency support, QR code support and security measures, etc.
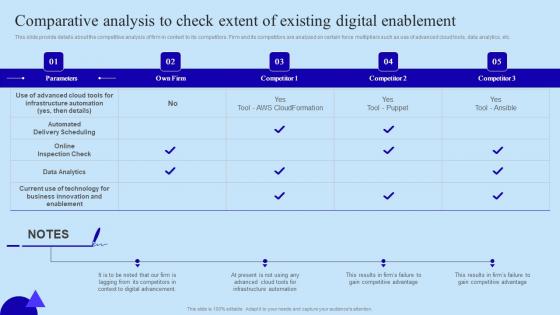
Comparative Analysis To Check Extent Organisational Digital Innovation Microsoft PDF
This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis To Check Extent Organisational Digital Innovation Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis To Check Extent Organisational Digital Innovation Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc.
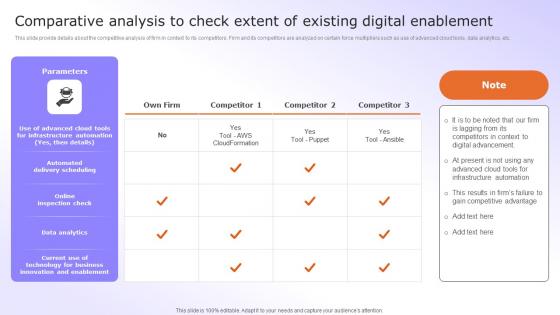
Digital Advancement Checklist Comparative Analysis To Check Extent Of Existing Digital Brochure Pdf
This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Digital Advancement Checklist Comparative Analysis To Check Extent Of Existing Digital Brochure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Digital Advancement Checklist Comparative Analysis To Check Extent Of Existing Digital Brochure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc.

Complete Beginners Guide Comparative Analysis Of Bitcoin Mining Techniques Fin SS V
This slide shows details about methods of bitcoin mining that can help organization assess different process on the basis of investment cost recovers and average setup cost. Its four methods are cloud mining, CPU mining, GPU mining and ASIC mining. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Complete Beginners Guide Comparative Analysis Of Bitcoin Mining Techniques Fin SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Complete Beginners Guide Comparative Analysis Of Bitcoin Mining Techniques Fin SS V today and make your presentation stand out from the rest This slide shows details about methods of bitcoin mining that can help organization assess different process on the basis of investment cost recovers and average setup cost. Its four methods are cloud mining, CPU mining, GPU mining and ASIC mining.

Comparative Analysis Of Bitcoin Everything About Bitcoin PPT Slide Fin SS V
This slide shows details about methods of bitcoin mining that can help organization assess different process on the basis of investment cost recovers and average setup cost. Its four methods are cloud mining, CPU mining, GPU mining and ASIC mining. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Analysis Of Bitcoin Everything About Bitcoin PPT Slide Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Comparative Analysis Of Bitcoin Everything About Bitcoin PPT Slide Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows details about methods of bitcoin mining that can help organization assess different process on the basis of investment cost recovers and average setup cost. Its four methods are cloud mining, CPU mining, GPU mining and ASIC mining.

Comparative Analysis To Check Extent E Sales Generation Checklist Infographics PDF
This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis To Check Extent E Sales Generation Checklist Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis To Check Extent E Sales Generation Checklist Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc.
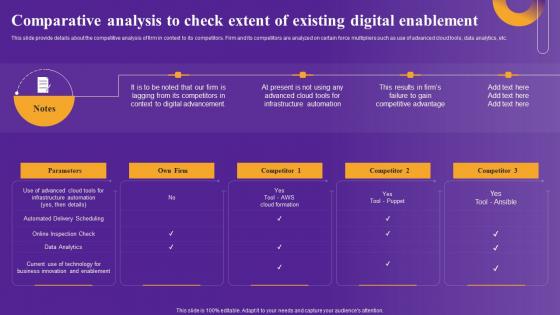
Comparative Analysis To Check Strategic Framework To Improve Digital Transformation Topics Pdf
This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis To Check Strategic Framework To Improve Digital Transformation Topics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis To Check Strategic Framework To Improve Digital Transformation Topics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provide details about the competitive analysis of firm in context to its competitors. Firm and its competitors are analyzed on certain force multipliers such as use of advanced cloud tools, data analytics, etc.
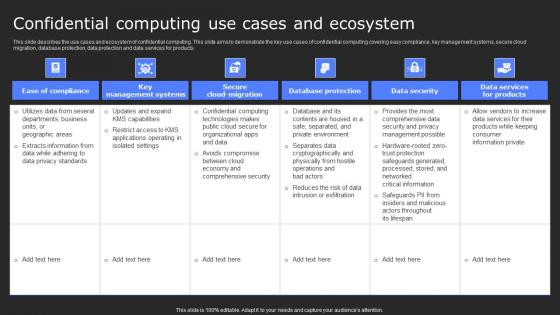
Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. The Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
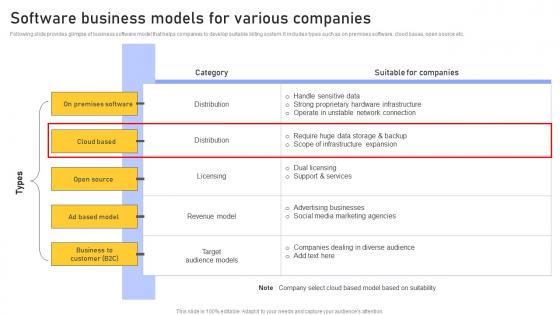
Software Business Models Enhancing Customer Service Operations Using CRM Technology Template Pdf
Following slide provides glimpse of business software model that helps companies to develop suitable billing system. It includes types such as on premises software, cloud bases, open source etc. Presenting this PowerPoint presentation, titled Software Business Models Enhancing Customer Service Operations Using CRM Technology Template Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Software Business Models Enhancing Customer Service Operations Using CRM Technology Template Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Software Business Models Enhancing Customer Service Operations Using CRM Technology Template Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. Following slide provides glimpse of business software model that helps companies to develop suitable billing system. It includes types such as on premises software, cloud bases, open source etc.
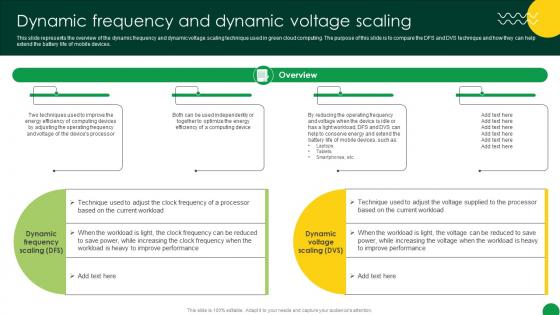
Sustainable Dynamic Frequency And Dynamic Voltage Scaling
This slide represents the overview of the dynamic frequency and dynamic voltage scaling technique used in green cloud computing. The purpose of this slide is to compare the DFS and DVS technique and how they can help extend the battery life of mobile devices. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Sustainable Dynamic Frequency And Dynamic Voltage Scaling to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the overview of the dynamic frequency and dynamic voltage scaling technique used in green cloud computing. The purpose of this slide is to compare the DFS and DVS technique and how they can help extend the battery life of mobile devices.

IoT Powered Energy Management Architecture Internet Of Things Solutions To Enhance Energy IoT SS V
This slide showcases IoT based energy management architecture with edge computing highlighting key components and their roles useful in optimising energy utilisation. It includes key components such as energy cloud servers, energy edge servers, and energy devices. This IoT Powered Energy Management Architecture Internet Of Things Solutions To Enhance Energy IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The IoT Powered Energy Management Architecture Internet Of Things Solutions To Enhance Energy IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide showcases IoT based energy management architecture with edge computing highlighting key components and their roles useful in optimising energy utilisation. It includes key components such as energy cloud servers, energy edge servers, and energy devices.
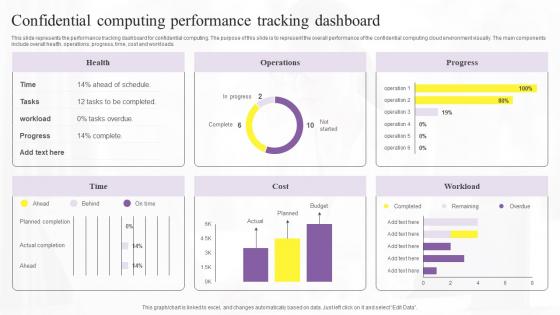
Confidential Computing Performance Confidential Computing Technologies Brochure Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. This Confidential Computing Performance Confidential Computing Technologies Brochure Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Performance Confidential Computing Technologies Brochure Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. This Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
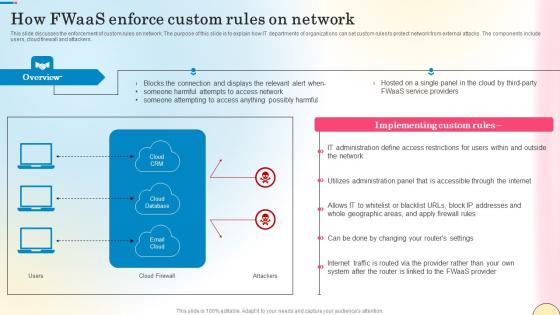
How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf
This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers. This How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers.
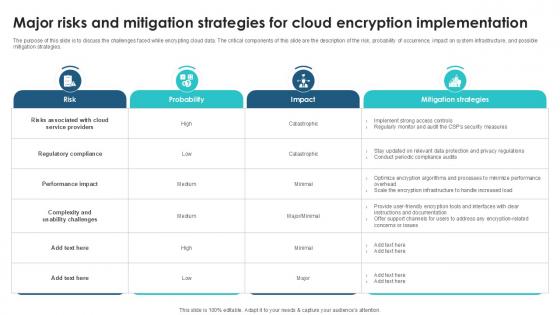
Major Risks And Mitigation Strategies Client Side Encryption PPT Template
The purpose of this slide is to discuss the challenges faced while encrypting cloud data. The critical components of this slide are the description of the risk, probability of occurrence, impact on system infrastructure, and possible mitigation strategies. This Major Risks And Mitigation Strategies Client Side Encryption PPT Template is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Major Risks And Mitigation Strategies Client Side Encryption PPT Template features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The purpose of this slide is to discuss the challenges faced while encrypting cloud data. The critical components of this slide are the description of the risk, probability of occurrence, impact on system infrastructure, and possible mitigation strategies.
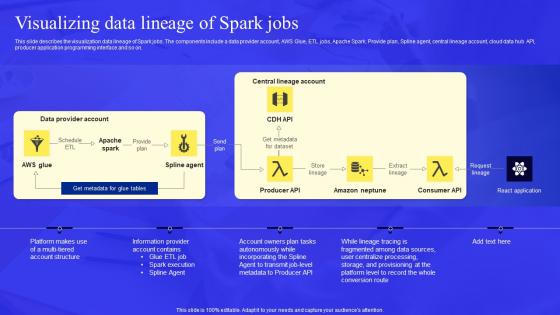
Business Process Data Lineage Visualizing Data Lineage Of Spark Jobs Ideas Pdf
This slide describes the visualization data lineage of Spark jobs. The components include a data provider account, AWS Glue, ETL jobs, Apache Spark, Provide plan, Spline agent, central lineage account, cloud data hub API, producer application programming interface and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Business Process Data Lineage Visualizing Data Lineage Of Spark Jobs Ideas Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the visualization data lineage of Spark jobs. The components include a data provider account, AWS Glue, ETL jobs, Apache Spark, Provide plan, Spline agent, central lineage account, cloud data hub API, producer application programming interface and so on.
Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
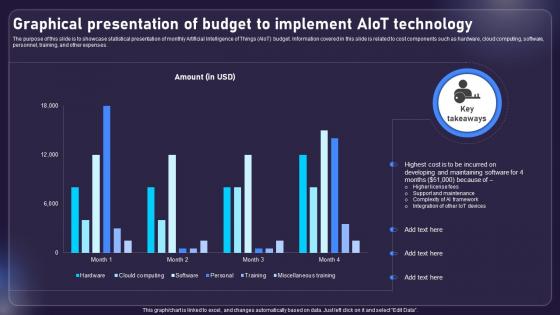
Graphical Presentation Of Budget To Implement AIOT AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase statistical presentation of monthly Artificial Intelligence of Things AIoT budget. Information covered in this slide is related to cost components such as hardware, cloud computing, software, personnel, training, and other expenses. This modern and well-arranged Graphical Presentation Of Budget To Implement AIOT AIOT Applications For Various Industries IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The purpose of this slide is to showcase statistical presentation of monthly Artificial Intelligence of Things AIoT budget. Information covered in this slide is related to cost components such as hardware, cloud computing, software, personnel, training, and other expenses.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
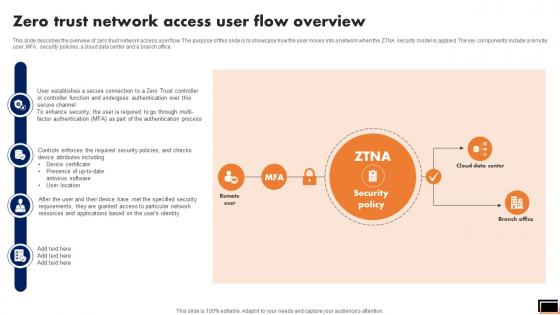
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
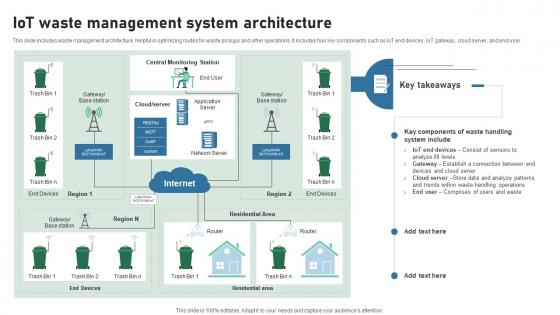
IOT Waste Management System Architecture IOT Applications In Smart Waste IoT SS V
This slide includes waste management architecture, helpful in optimizing routes for waste pickups and other operations. It includes four key components such as IoT end devices, IoT gateway, cloud server, and end user. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download IOT Waste Management System Architecture IOT Applications In Smart Waste IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the IOT Waste Management System Architecture IOT Applications In Smart Waste IoT SS V. This slide includes waste management architecture, helpful in optimizing routes for waste pickups and other operations. It includes four key components such as IoT end devices, IoT gateway, cloud server, and end user.

Integration Of SWG Inside SASE Architecture Web Threat Protection System
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integration Of SWG Inside SASE Architecture Web Threat Protection System to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
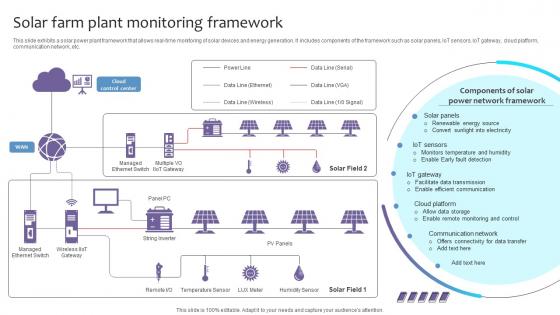
Empowering The Future Solar Farm Plant Monitoring Framework IoT SS V
This slide exhibits a solar power plant framework that allows real-time monitoring of solar devices and energy generation. It includes components of the framework such as solar panels, IoT sensors, IoT gateway, cloud platform, communication network, etc. Explore a selection of the finest Empowering The Future Solar Farm Plant Monitoring Framework IoT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Empowering The Future Solar Farm Plant Monitoring Framework IoT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide exhibits a solar power plant framework that allows real-time monitoring of solar devices and energy generation. It includes components of the framework such as solar panels, IoT sensors, IoT gateway, cloud platform, communication network, etc.

Web Access Control Solution Integration Of Swg Inside Sase Architecture
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. The Web Access Control Solution Integration Of Swg Inside Sase Architecture is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc.
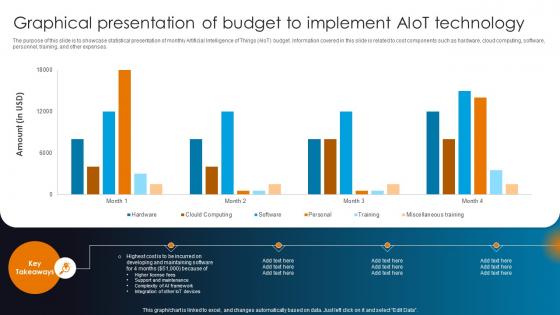
Integrating AI With IoT Graphical Presentation Of Budget To Implement AIoT Technology IoT SS V
The purpose of this slide is to showcase statistical presentation of monthly Artificial Intelligence of Things AIoT budget. Information covered in this slide is related to cost components such as hardware, cloud computing, software, personnel, training, and other expenses. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integrating AI With IoT Graphical Presentation Of Budget To Implement AIoT Technology IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The purpose of this slide is to showcase statistical presentation of monthly Artificial Intelligence of Things AIoT budget. Information covered in this slide is related to cost components such as hardware, cloud computing, software, personnel, training, and other expenses.
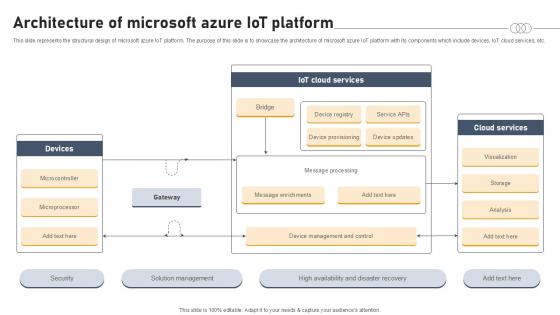
Architecture Of Microsoft Azure IOT Platform Aws IOT Platform Ppt Template
This slide represents the structural design of microsoft azure IoT platform. The purpose of this slide is to showcase the architecture of microsoft azure IoT platform with its components which include devices, IoT cloud services, etc. Explore a selection of the finest Architecture Of Microsoft Azure IOT Platform Aws IOT Platform Ppt Template here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Architecture Of Microsoft Azure IOT Platform Aws IOT Platform Ppt Template to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the structural design of microsoft azure IoT platform. The purpose of this slide is to showcase the architecture of microsoft azure IoT platform with its components which include devices, IoT cloud services, etc.
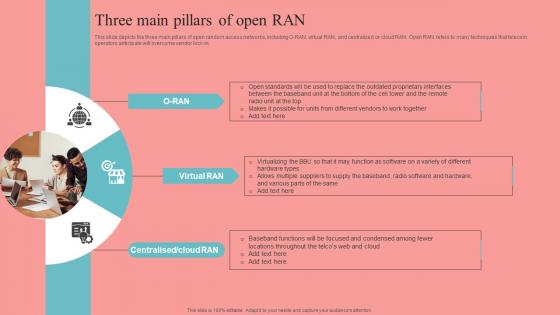
Three Main Pillars Of Open RAN Unlocking The Potential Of Open RAN Diagrams Pdf
This slide depicts the three main pillars of open random access networks, including O-RAN, virtual RAN, and centralized or cloud RAN. Open RAN refers to many techniques that telecom operators anticipate will overcome vendor lock-in. Presenting this PowerPoint presentation, titled Three Main Pillars Of Open RAN Unlocking The Potential Of Open RAN Diagrams Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Three Main Pillars Of Open RAN Unlocking The Potential Of Open RAN Diagrams Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Three Main Pillars Of Open RAN Unlocking The Potential Of Open RAN Diagrams Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide depicts the three main pillars of open random access networks, including O-RAN, virtual RAN, and centralized or cloud RAN. Open RAN refers to many techniques that telecom operators anticipate will overcome vendor lock-in.
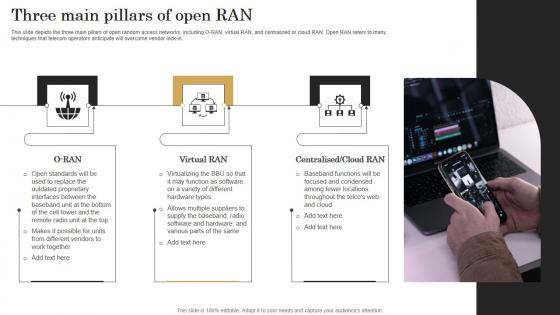
Three Main Pillars Of Open Ran Revolutionizing Mobile Networks Elements PDF
This slide depicts the three main pillars of open random access networks, including O-RAN, virtual RAN, and centralized or cloud RAN. Open RAN refers to many techniques that telecom operators anticipate will overcome vendor lock-in. Presenting this PowerPoint presentation, titled Three Main Pillars Of Open Ran Revolutionizing Mobile Networks Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Three Main Pillars Of Open Ran Revolutionizing Mobile Networks Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Three Main Pillars Of Open Ran Revolutionizing Mobile Networks Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide depicts the three main pillars of open random access networks, including O-RAN, virtual RAN, and centralized or cloud RAN. Open RAN refers to many techniques that telecom operators anticipate will overcome vendor lock-in.
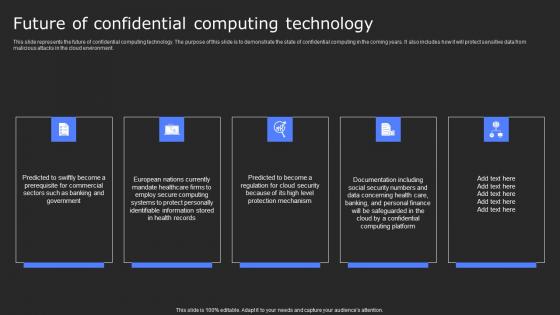
Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Presenting this PowerPoint presentation, titled Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.

Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf
This slide describes the overview of SD-WAN architectural layers, including orchestration and analytics, virtual service delivery, and secure cloud network. The purpose of this slide is to highlight the main features and functions of SD-WAN layers. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf This slide describes the overview of SD-WAN architectural layers, including orchestration and analytics, virtual service delivery, and secure cloud network. The purpose of this slide is to highlight the main features and functions of SD-WAN layers.
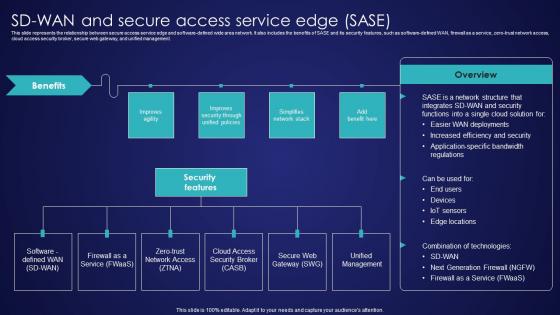
SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Welcome to our selection of the SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management.
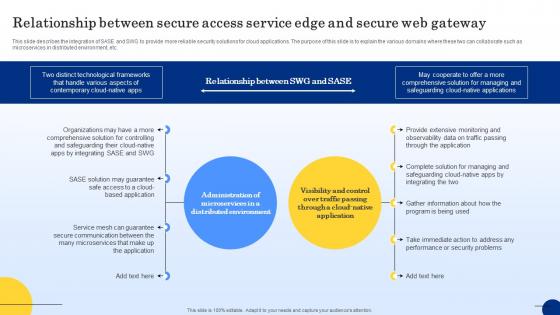
Relationship Between Secure Access Service Edge Web Threat Protection System
This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Presenting this PowerPoint presentation, titled Relationship Between Secure Access Service Edge Web Threat Protection System, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Relationship Between Secure Access Service Edge Web Threat Protection System. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Relationship Between Secure Access Service Edge Web Threat Protection System that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc.

CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration.

Future Opportunities And Technologies In Using Data Mining Tools To Optimize Processes AI SS V
This slide showcases future opportunities relating to data mining which can help associated players to improvise their current offerings. It provides details machine learning, AI, internet of things, cloud tools, etc. Presenting this PowerPoint presentation, titled Future Opportunities And Technologies In Using Data Mining Tools To Optimize Processes AI SS V, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Future Opportunities And Technologies In Using Data Mining Tools To Optimize Processes AI SS V. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Future Opportunities And Technologies In Using Data Mining Tools To Optimize Processes AI SS V that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide showcases future opportunities relating to data mining which can help associated players to improvise their current offerings. It provides details machine learning, AI, internet of things, cloud tools, etc.
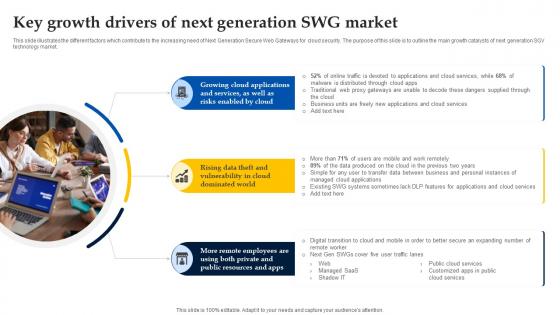
Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Presenting this PowerPoint presentation, titled Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.
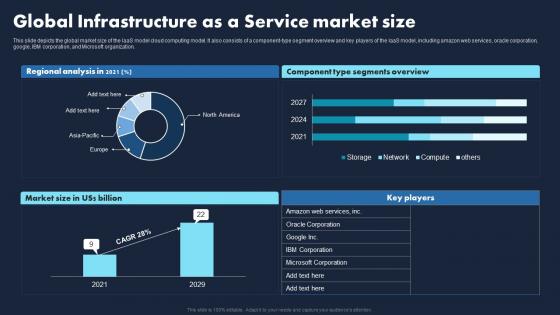
Global Infrastructure As A Service Market Size Transforming Business With IaaS Designs Pdf
This slide depicts the global market size of the IaaS model cloud computing model. It also consists of a component-type segment overview and key players of the laaS model, including amazon web services, oracle corporation, google, IBM corporation, and Microsoft organization. Create an editable Global Infrastructure As A Service Market Size Transforming Business With IaaS Designs Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Global Infrastructure As A Service Market Size Transforming Business With IaaS Designs Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide depicts the global market size of the IaaS model cloud computing model. It also consists of a component-type segment overview and key players of the laaS model, including amazon web services, oracle corporation, google, IBM corporation, and Microsoft organization.

Green Computing Nano Data Center Overview And Advantages
This slide describes the role of nano data centers in green cloud computing, including their benefits. The purpose of this slide is to showcase the various advantages of nano data centers, including energy efficiency, reduced costs, scalability, improved performance, flexibility, and resilience. This Green Computing Nano Data Center Overview And Advantages from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide describes the role of nano data centers in green cloud computing, including their benefits. The purpose of this slide is to showcase the various advantages of nano data centers, including energy efficiency, reduced costs, scalability, improved performance, flexibility, and resilience.
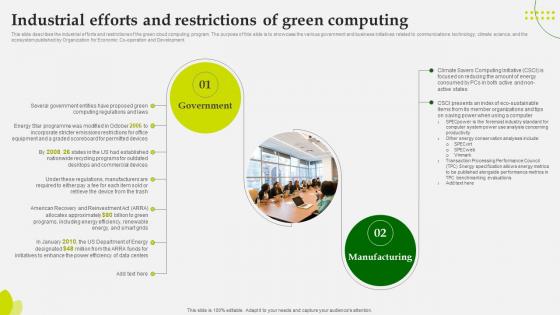
Green Computing Industrial Efforts And Restrictions Of Green Computing
This slide describes the industrial efforts and restrictions of the green cloud computing program. The purpose of this slide is to showcase the various government and business initiativesrelated to communications technology, climate science, and the ecosystem published by Organization for Economic Co-operation and Development. Are you searching for a Green Computing Industrial Efforts And Restrictions Of Green Computing that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Green Computing Industrial Efforts And Restrictions Of Green Computing from Slidegeeks today. This slide describes the industrial efforts and restrictions of the green cloud computing program. The purpose of this slide is to showcase the various government and business initiativesrelated to communications technology, climate science, and the ecosystem published by Organization for Economic Co-operation and Development.
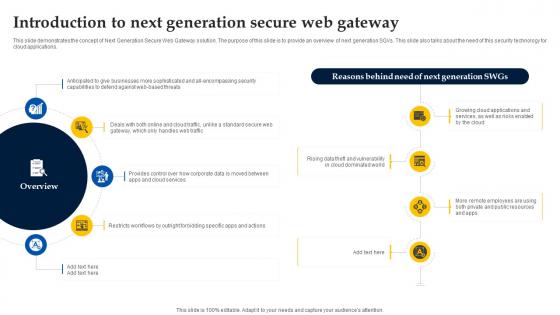
Web Access Control Solution Introduction To Next Generation Secure Web Gateway
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Are you searching for a Web Access Control Solution Introduction To Next Generation Secure Web Gateway that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Web Access Control Solution Introduction To Next Generation Secure Web Gateway from Slidegeeks today. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.


 Continue with Email
Continue with Email

 Home
Home


































