Cloud Computing Security

Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Get a simple yet stunning designed Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.

Different Types Of Cryptographic Data Security In Cloud Computing Ppt Example
This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric-key cryptography, asymmetric-key cryptography, hash functions, steganography, etc. This Different Types Of Cryptographic Data Security In Cloud Computing Ppt Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Different Types Of Cryptographic Data Security In Cloud Computing Ppt Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric-key cryptography, asymmetric-key cryptography, hash functions, steganography, etc.
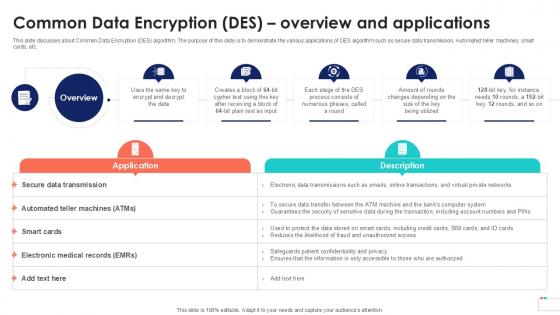
Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc.
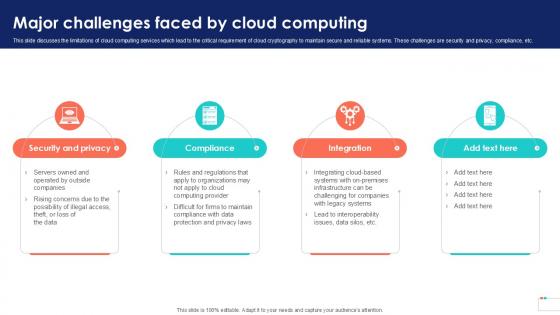
Major Challenges Faced By Data Security In Cloud Computing Ppt Sample
This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc. Do you know about Slidesgeeks Major Challenges Faced By Data Security In Cloud Computing Ppt Sample These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc.

Types Of Attacks Prevented By Data Security In Cloud Computing Ppt Template
This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man-in-the-middle MitM attacks, data breaches, insider attacks, etc. Find highly impressive Types Of Attacks Prevented By Data Security In Cloud Computing Ppt Template on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Types Of Attacks Prevented By Data Security In Cloud Computing Ppt Template for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man-in-the-middle MitM attacks, data breaches, insider attacks, etc.
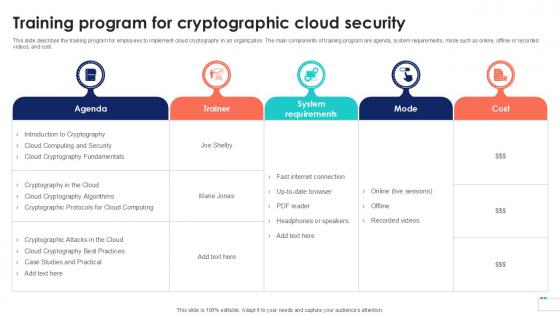
Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.
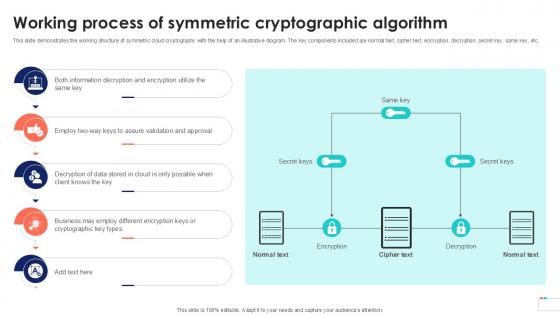
Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Process Of Symmetric Data Security In Cloud Computing Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Process Of Symmetric Data Security In Cloud Computing Ppt Template This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.

What Are Benefits Of Using Data Security In Cloud Computing Ppt Template
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit What Are Benefits Of Using Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.

Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Take your projects to the next level with our ultimate collection of Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc.

Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.
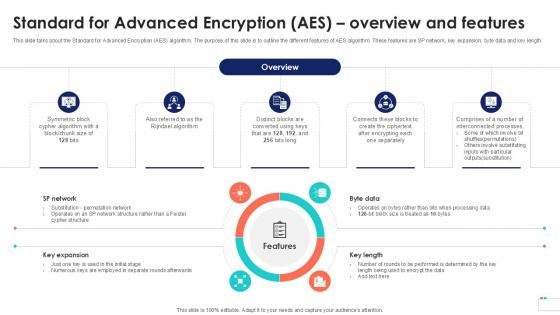
Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample a try. Our experts have put a lot of knowledge and effort into creating this impeccable Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.

About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.
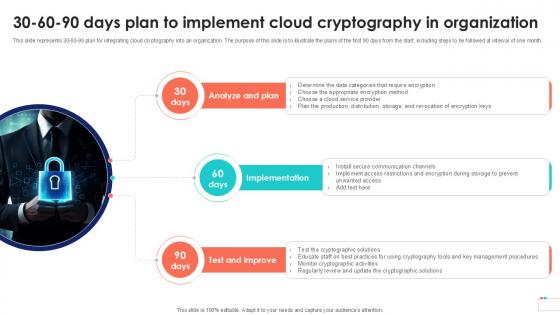
30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample
This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
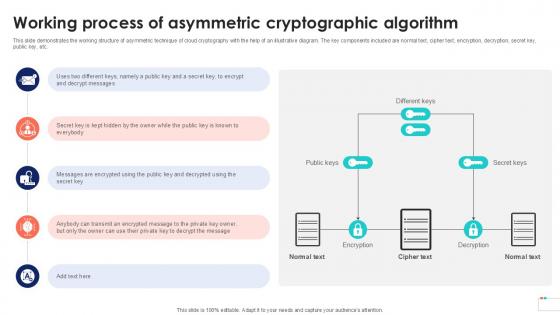
Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.

Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template
This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Welcome to our selection of the Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc.
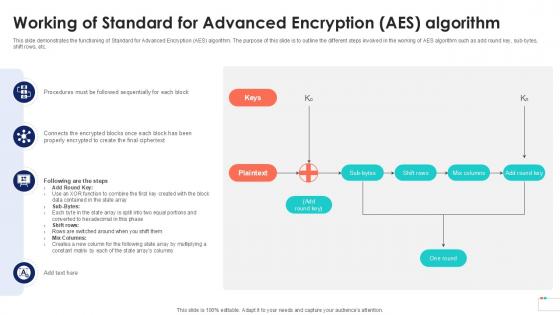
Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc.
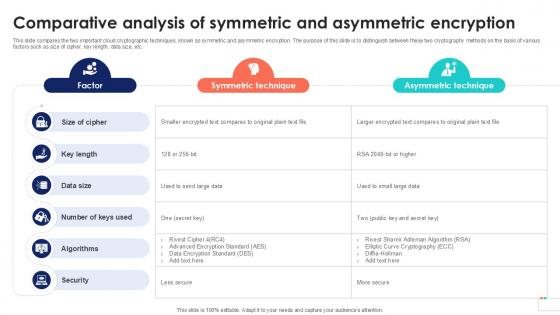
Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
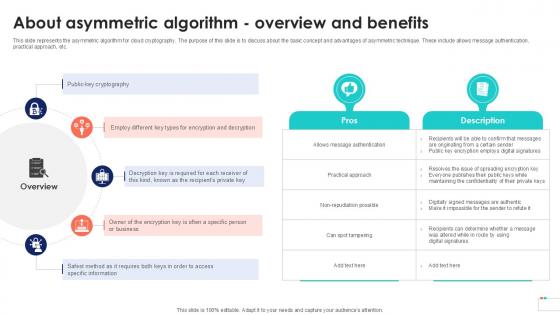
About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Boost your pitch with our creative About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.

About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Want to ace your presentation in front of a live audience Our About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.
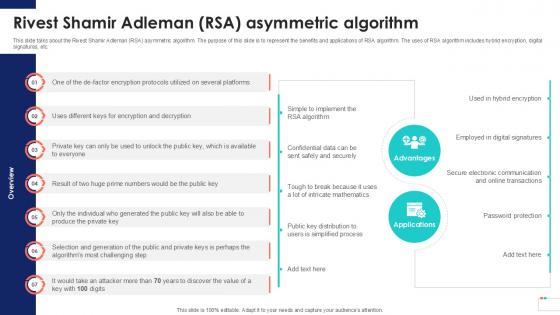
Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Want to ace your presentation in front of a live audience Our Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.
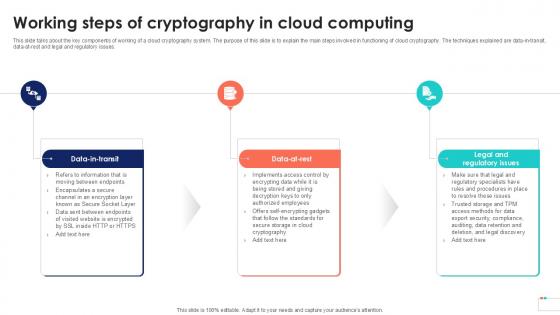
Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues.

Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. Slidegeeks is here to make your presentations a breeze with Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc.
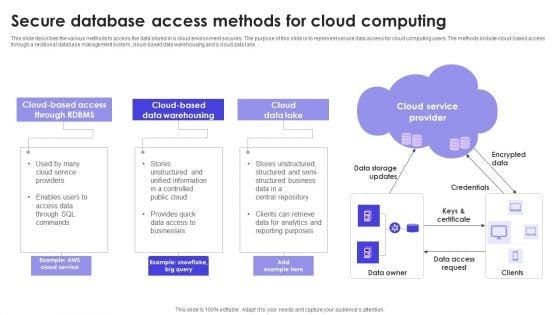
Secure Database Access Methods For Cloud Computing Formats PDF
This slide describes the various methods to access the data stored in a cloud environment securely. The purpose of this slide is to represent secure data access for cloud computing users. The methods include cloud-based access through a relational database management system, cloud-based data warehousing and a cloud data lake. Persuade your audience using this Secure Database Access Methods For Cloud Computing Formats PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Data Lake, Data Warehousing, Cloud Service Provider. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
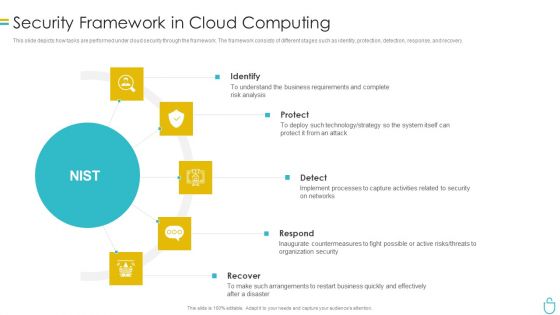
Information Security Security Framework In Cloud Computing Ppt Summary Designs PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Presenting information security security framework in cloud computing ppt summary designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like identify, protect, detect, respond, recover. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
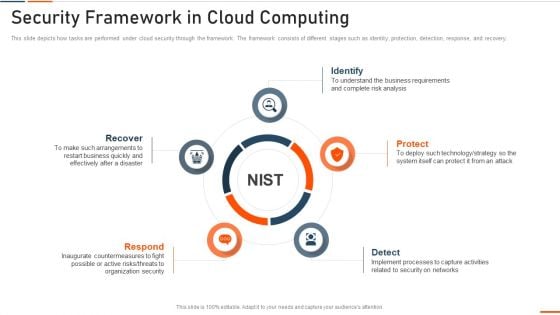
Information Technology Security Security Framework In Cloud Computing Ppt Outline Graphics Design PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a information technology security security framework in cloud computing ppt outline graphics design pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recover, respond, identify, protect . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
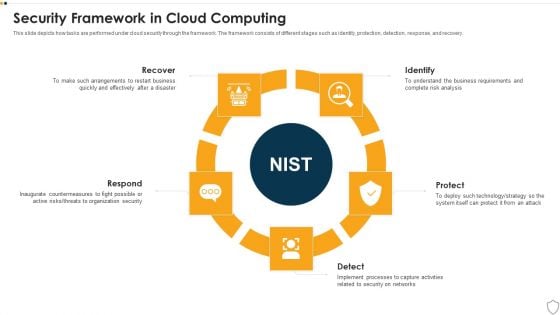
IT Security Security Framework In Cloud Computing Ppt Model Sample PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a it security security framework in cloud computing ppt model sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recover, respond, identify, protect, detect. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
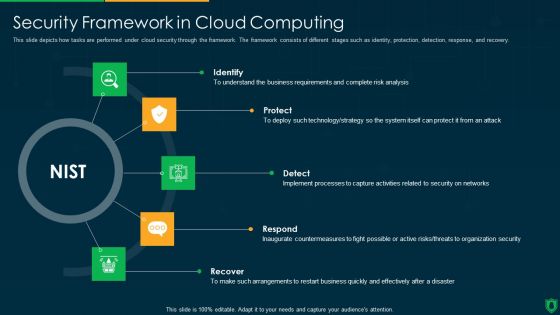
Info Security Security Framework In Cloud Computing Ppt PowerPoint Presentation Gallery Images PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a info security security framework in cloud computing ppt powerpoint presentation gallery images pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identify, protect, detect, respond, recover. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
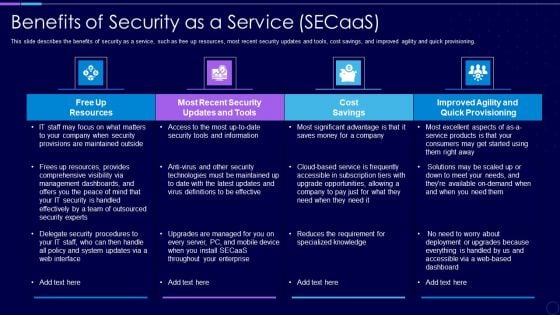
Everything As A Service Xaas For Cloud Computing IT Benefits Of Security As A Service Clipart PDF
This slide describes the benefits of security as a service, such as free up resources, most recent security updates and tools, cost savings, and improved agility and quick provisioning. Deliver an awe inspiring pitch with this creative everything as a service xaas for cloud computing it benefits of security as a service clipart pdf bundle. Topics like cost savings, security, resources, dashboards can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
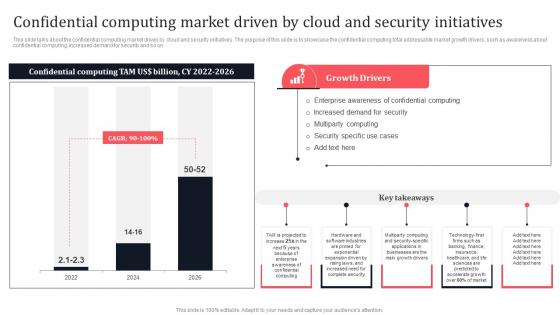
Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
Security Testing Tools Cloud Computing Ppt PowerPoint Presentation Model Example File Cpb Pdf
Presenting this set of slides with name security testing tools cloud computing ppt powerpoint presentation model example file cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like security testing tools cloud computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
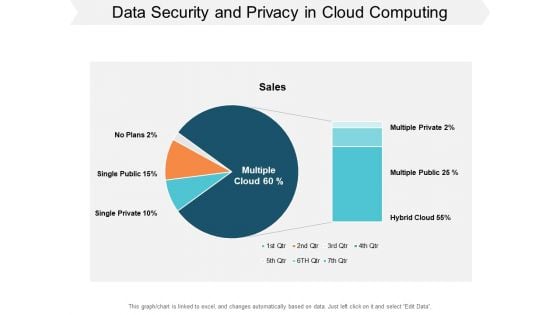
Data Security And Privacy In Cloud Computing Ppt PowerPoint Presentation Slides Graphic Tips
This is a data security and privacy in cloud computing ppt powerpoint presentation slides graphic tips. This is a two stage process. The stages in this process are cloud strategy, cloud planning, cloud management.
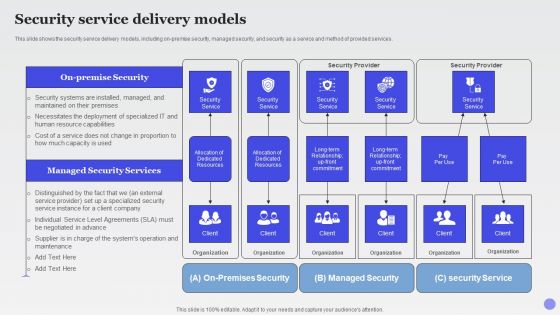
Security Service Delivery Models Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Graphics PDF
This slide shows the security service delivery models, including on premise security, managed security, and security as a service and method of provided services.Deliver an awe inspiring pitch with this creative Security Service Delivery Models Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Graphics PDF bundle. Topics like Dedicated Resources, Security Service, Managed Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Securing Data Over Google Cloud Google Cloud Computing System Professional PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock.Presenting Securing Data Over Google Cloud Google Cloud Computing System Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Protect Information, Compute Engine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Computer System Interface Icon With Cloud Storage Ppt File Backgrounds PDF
Persuade your audience using this Security Computer System Interface Icon With Cloud Storage Ppt File Backgrounds PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Security Computer System, Interface Icon, Cloud Storage. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
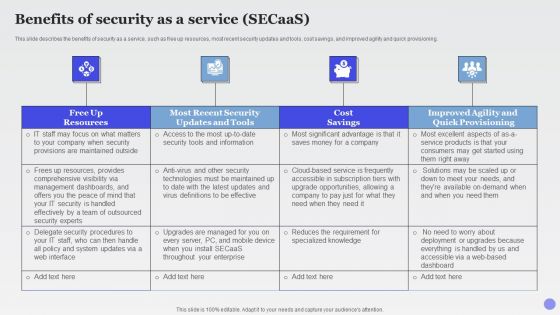
Benefits Of Security As A Service Secaas Xaas Cloud Computing Models Ppt PowerPoint Presentation Show Slide Portrait PDF
This slide describes the benefits of security as a service, such as free up resources, most recent security updates and tools, cost savings, and improved agility and quick provisioning.This is a Benefits Of Security As A Service Secaas Xaas Cloud Computing Models Ppt PowerPoint Presentation Show Slide Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Dashboards, Security Handled, Effectively Outsourced. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
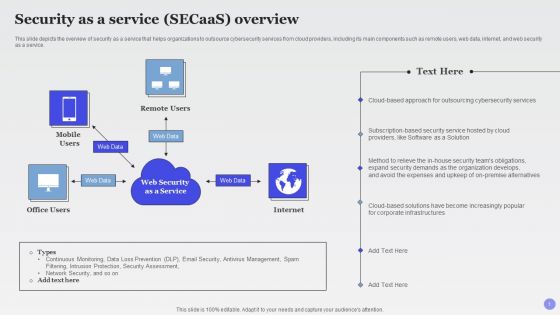
Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service.Deliver and pitch your topic in the best possible manner with this Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF. Use them to share invaluable insights on Outsourcing Cybersecurity, Software Solution, Expenses Upkeep and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
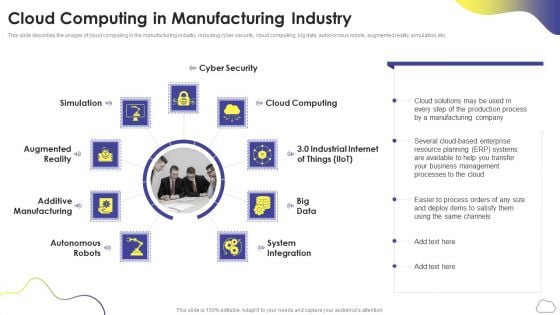
Cloud Computing Services Cloud Computing In Manufacturing Industry Inspiration PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. Presenting Cloud Computing Services Cloud Computing In Manufacturing Industry Inspiration PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cyber Security, Cloud Computing, System Integration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
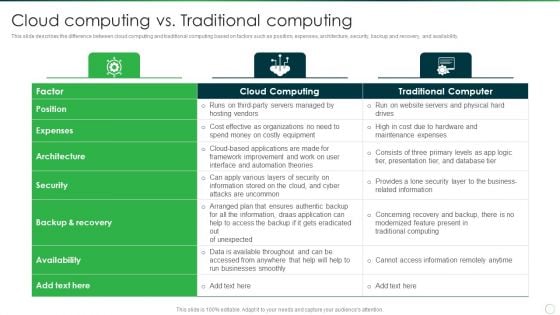
Google Cloud Computing System Cloud Computing Vs Traditional Computing Mockup PDF
This slide describes the difference between cloud computing and traditional computing based on factors such as position, expenses, architecture, security, backup and recovery, and availability. Deliver and pitch your topic in the best possible manner with this Google Cloud Computing System Cloud Computing Vs Traditional Computing Mockup PDF. Use them to share invaluable insights on Cloud Computing, Traditional Computer, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
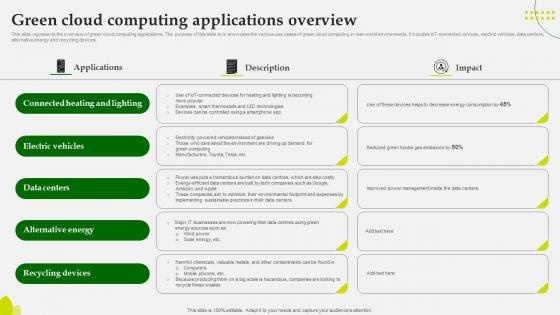
Green Computing Green Cloud Computing Applications Overview
This slide represents the overview of green cloud computing applications. The purpose of this slide is to showcase the various use cases of green cloud computing in real-world environments. It includes IoT-connected devices, electric vehicles, data centers, alternative energy and recycling devices. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Green Computing Green Cloud Computing Applications Overview and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the overview of green cloud computing applications. The purpose of this slide is to showcase the various use cases of green cloud computing in real-world environments. It includes IoT-connected devices, electric vehicles, data centers, alternative energy and recycling devices.

Green Computing Green Cloud Computing Adoption Challenges
This slide outlines the various challenges that come while implementing green cloud computing measures. The purpose of this slide is to showcase the various issues that organizations face while adopting green cloud computing, including corporate objectives, frictions with competing properties, and unfunded mandates. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Green Computing Green Cloud Computing Adoption Challenges can be your best option for delivering a presentation. Represent everything in detail using Green Computing Green Cloud Computing Adoption Challenges and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the various challenges that come while implementing green cloud computing measures. The purpose of this slide is to showcase the various issues that organizations face while adopting green cloud computing, including corporate objectives, frictions with competing properties, and unfunded mandates.

Green Computing Green Cloud Computing Strategy Components
This slide represents the components of a green cloud computing strategy. The purpose of this slide is to showcasethe different components of green computing strategy, including remote work, smart technology, upgrading and rearranging data centers, power down, strategic scheduling, display selection, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Green Computing Green Cloud Computing Strategy Components and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the components of a green cloud computing strategy. The purpose of this slide is to showcasethe different components of green computing strategy, including remote work, smart technology, upgrading and rearranging data centers, power down, strategic scheduling, display selection, and so on.
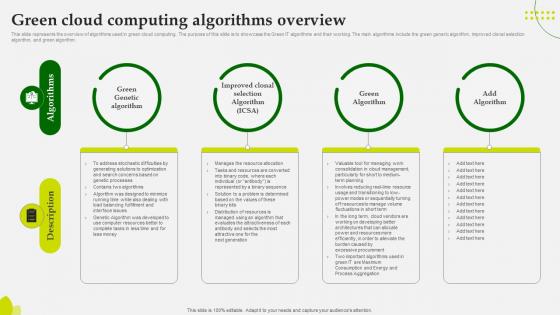
Green Computing Green Cloud Computing Algorithms Overview
This slide represents the overview of algorithms used in green cloud computing. The purpose of this slide is to showcase the Green IT algorithms and their working. The main algorithms include the green generic algorithm, improved clonal selection algorithm, andgreen algorithm. Find highly impressive Green Computing Green Cloud Computing Algorithms Overview on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Green Computing Green Cloud Computing Algorithms Overview for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of algorithms used in green cloud computing. The purpose of this slide is to showcase the Green IT algorithms and their working. The main algorithms include the green generic algorithm, improved clonal selection algorithm, andgreen algorithm.
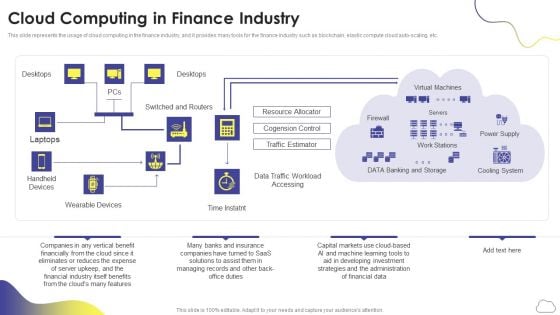
Cloud Computing Services Cloud Computing In Finance Industry Brochure PDF
This slide represents the usage of cloud computing in the finance industry, and it provides many tools for the finance industry such as blockchain, elastic compute cloud auto-scaling, etc. Presenting Cloud Computing Services Cloud Computing In Finance Industry Brochure PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Resource Allocator, Cogension Control, Traffic Estimator. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
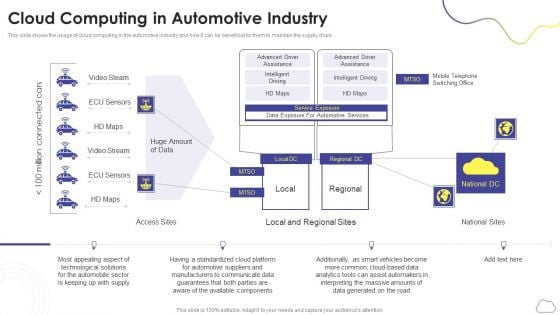
Cloud Computing Services Cloud Computing In Automotive Industry Download PDF
This slide shows the usage of cloud computing in the automotive industry and how it can be beneficial for them to maintain the supply chain. This is a Cloud Computing Services Cloud Computing In Automotive Industry Download PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like National Sites, Access Sites, Mobile Telephone, Switching Office. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Service Models IT Cloud Computing In Manufacturing Industry Inspiration PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. This is a cloud computing service models it cloud computing in manufacturing industry inspiration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like simulation, cyber security, cloud computing, system integration, autonomous robots. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
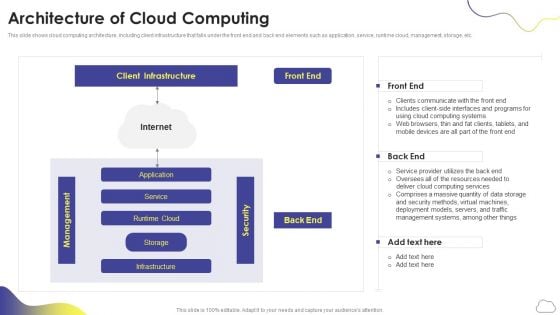
Cloud Computing Services Architecture Of Cloud Computing Slides PDF
This slide shows cloud computing architecture, including client infrastructure that falls under the front end and back end elements such as application, service, runtime cloud, management, storage, etc. Deliver and pitch your topic in the best possible manner with this Cloud Computing Services Architecture Of Cloud Computing Slides PDF. Use them to share invaluable insights on Client Infrastructure, Front End, Application, Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
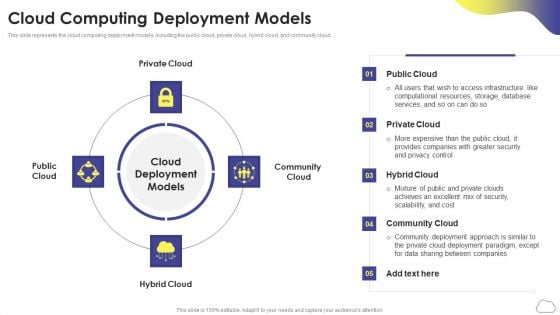
Cloud Computing Services Cloud Computing Deployment Models Diagrams PDF
This slide represents the cloud computing deployment models, including the public cloud, private cloud, hybrid cloud, and community cloud. This is a Cloud Computing Services Cloud Computing Deployment Models Diagrams PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Private Cloud, Community Cloud, Public Cloud, Hybrid Cloud. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Services Cloud Computing In Healthcare Industry Professional PDF
This slide represents the usage of cloud computing in the healthcare industry including health education, better practice management, population health management, etc. This is a Cloud Computing Services Cloud Computing In Healthcare Industry Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Population Health Management, Health Education, Biological Softwares. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Services Cloud Computing In Education Industry Mockup PDF
This slide depicts the usage of cloud computing in the education industry and how it is beneficial for students as well as faculty members of the education industry. This is a Cloud Computing Services Cloud Computing In Education Industry Mockup PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Admin Department, Examination Branch, Admission Section. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
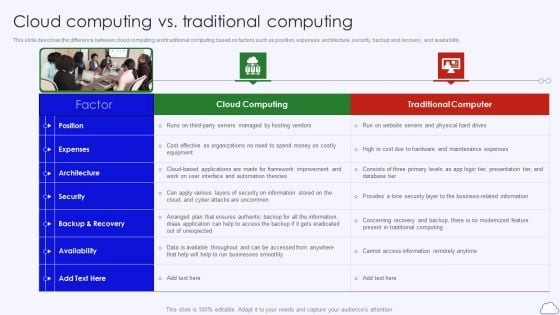
Cloud Computing Vs Traditional Computing Google Cloud Computing System Slides PDF
This slide describes the difference between cloud computing and traditional computing based on factors such as position, expenses, architecture, security, backup and recovery, and availability.This is a Cloud Computing Vs Traditional Computing Google Cloud Computing System Slides PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Traditional Computer, Architecture, Availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
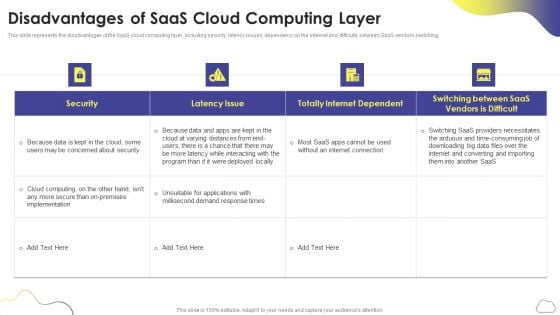
Cloud Computing Services Disadvantages Of Saas Cloud Computing Layer Slides PDF
This slide represents the disadvantages of the SaaS cloud computing layer, including security, latency issues, dependency on the internet and difficulty between SaaS vendors switching. Deliver and pitch your topic in the best possible manner with this Cloud Computing Services Disadvantages Of Saas Cloud Computing Layer Slides PDF. Use them to share invaluable insights on Security, Latency Issue, Totally Internet Dependent and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
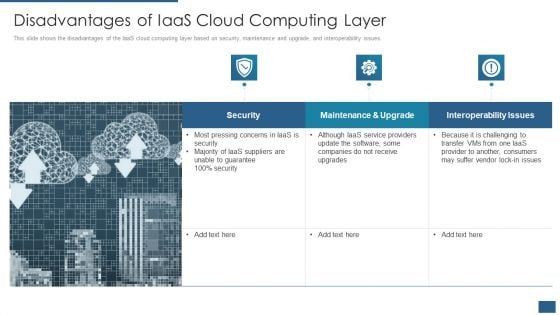
Cloud Computing Service Models IT Disadvantages Of Iaas Cloud Computing Layer Rules PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. Deliver an awe inspiring pitch with this creative cloud computing service models it disadvantages of iaas cloud computing layer rules pdf bundle. Topics like security, maintenance and upgrade, interoperability issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
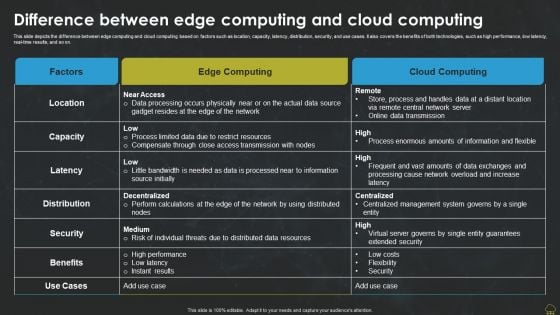
Difference Between Edge Computing And Cloud Computing Professional PDF
This slide depicts the difference between edge computing and cloud computing based on factors such as location, capacity, latency, distribution, security, and use cases. It also covers the benefits of both technologies, such as high performance, low latency, real-time results, and so on. Find a pre designed and impeccable Difference Between Edge Computing And Cloud Computing Professional PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
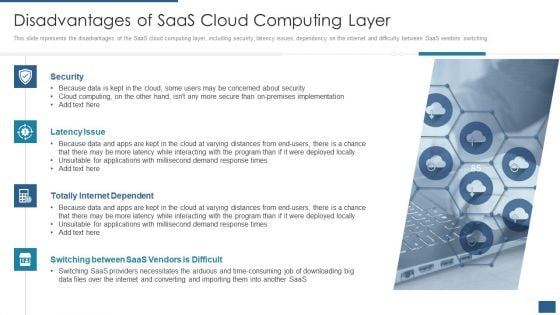
Cloud Computing Service Models IT Disadvantages Of Saas Cloud Computing Layer Elements PDF
This slide represents the disadvantages of the SaaS cloud computing layer, including security, latency issues, dependency on the internet and difficulty between SaaS vendors switching. Presenting cloud computing service models it disadvantages of saas cloud computing layer elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, latency issue, totally internet dependent, switching between saas vendors is difficult. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
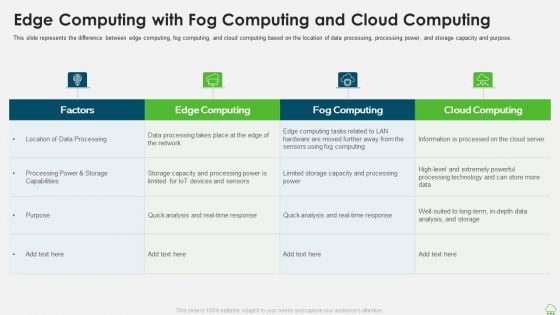
Distributed Computing IT Edge Computing With Fog Computing And Cloud Computing Sample PDF
This slide represents the difference between edge computing, fog computing, and cloud computing based on the location of data processing, processing power, and storage capacity and purpose. Deliver and pitch your topic in the best possible manner with this distributed computing it edge computing with fog computing and cloud computing sample pdf. Use them to share invaluable insights on data processing, analysis, capacity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
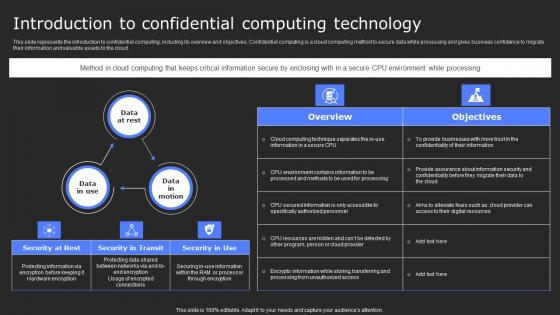
Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
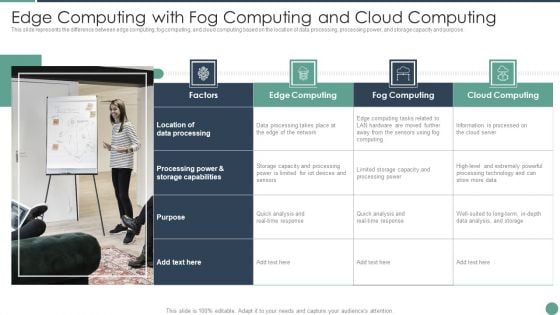
Distributed Computing Edge Computing With Fog Computing And Cloud Computing Designs PDF
This slide represents the difference between edge computing, fog computing, and cloud computing based on the location of data processing, processing power, and storage capacity and purpose.Presenting Distributed Computing Edge Computing With Fog Computing And Cloud Computing Designs PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Processing Power, Storage Capabilities, Data Processing In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. This is a Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Maintenance And Upgrade, Security, Interoperability Issues. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Distributed Computing Compare Edge Cloud Cloud Computing And Edge Computing Clipart PDF
This slide defines a comparison between edge cloud, edge computing, and cloud computing based on latency, processing power, storage capacity, and bandwidth.Presenting Distributed Computing Compare Edge Cloud Cloud Computing And Edge Computing Clipart PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Artificial Intelligence, Storage Capacity, Processing And Compute In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































