Cloud Computing Security
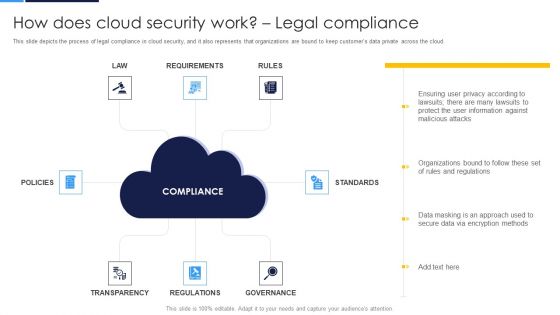
Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Deliver an awe inspiring pitch with this creative Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF bundle. Topics like Provide Limited, Personnel To Protect, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
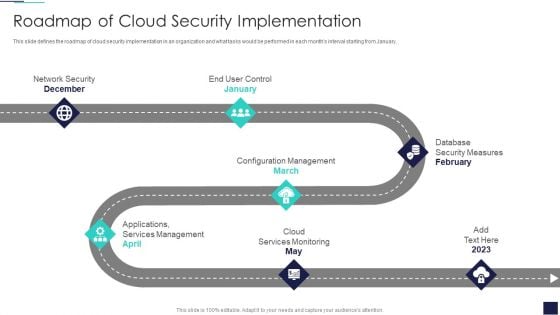
Cloud Information Security Roadmap Of Cloud Security Implementation Ppt Styles PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Cloud Information Security Roadmap Of Cloud Security Implementation Ppt Styles PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Network Security, Configuration Management, Cloud Services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Enterprise Cloud Security Solutions Ppt Ideas File Formats PDF
This slide describes the enterprise cloud security solutions, including multi-factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost-benefits of hybrid cloud. Presenting Cloud Information Security Enterprise Cloud Security Solutions Ppt Ideas File Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multi Factor Authentication, Cost Benefits, Hybrid Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. This is a Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Control Identity, Security Breaches, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Presenting Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Expanded Attack, Access Management, Complex Frameworks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
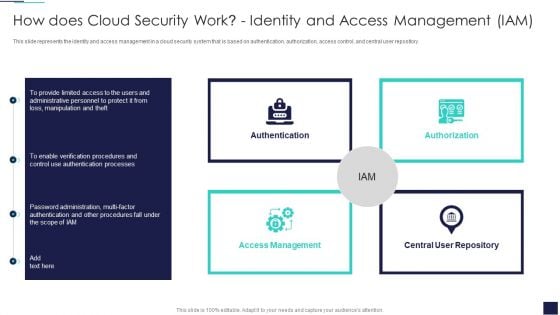
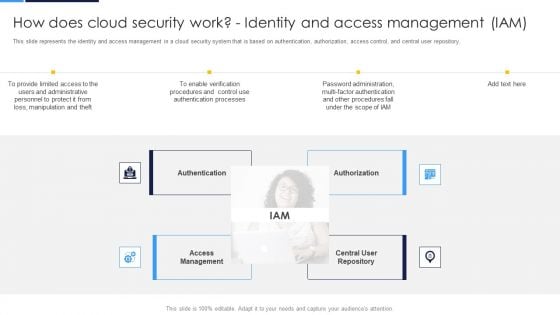
Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Central Repository, Access Management, Authorization Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
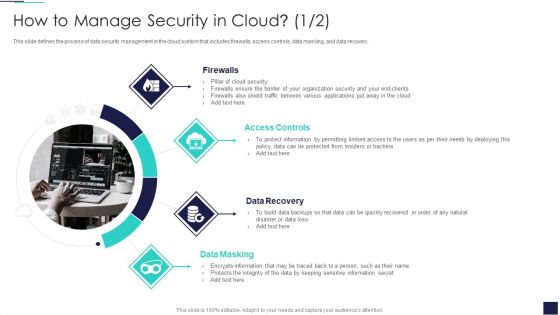
Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Controls, Data Recovery, Data Masking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
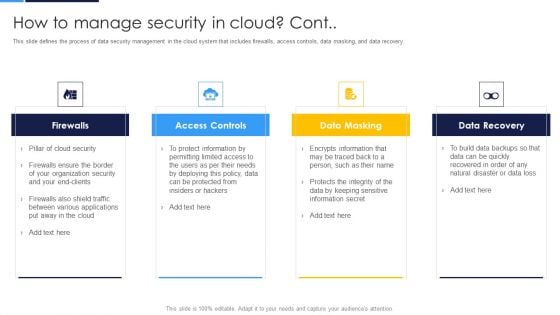
Cloud Security Assessment How To Manage Security In Cloud Cont Demonstration PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery.This is a Cloud Security Assessment How To Manage Security In Cloud Cont Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Firewalls, Access Controls, Data Masking You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Presenting Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Accessibility, Knowledge, Technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security How To Manage Cloud Security Ppt Model Graphics PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures. This is a four template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ensure Governance, Compliance Effective, Business Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
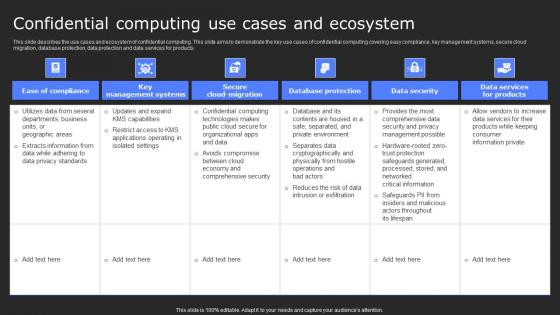
Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. The Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
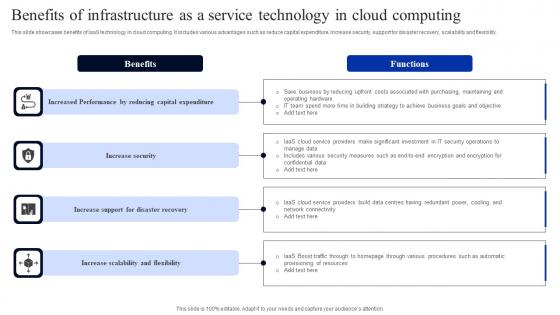
Benefits Of Infrastructure As A Service Technology In Cloud Computing Infographics Pdf
This slide showcases benefits of IaaS technology in cloud computing. It includes various advantages such as reduce capital expenditure, increase security, support for disaster recovery, scalability and flexibility. Pitch your topic with ease and precision using this Benefits Of Infrastructure As A Service Technology In Cloud Computing Infographics Pdf. This layout presents information on Capital Expenditure, Increase Security, Support Disaster Recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases benefits of IaaS technology in cloud computing. It includes various advantages such as reduce capital expenditure, increase security, support for disaster recovery, scalability and flexibility.
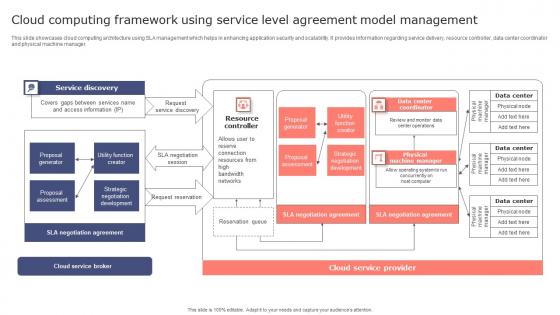
Cloud Computing Framework Using Service Level Agreement Model Management Topics Pdf
This slide showcases cloud computing architecture using SLA management which helps in enhancing application security and scalability. It provides information regarding service delivery, resource controller, data center coordinator and physical machine manager. Showcasing this set of slides titled Cloud Computing Framework Using Service Level Agreement Model Management Topics Pdf. The topics addressed in these templates are Service Discovery, Resource Controller. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases cloud computing architecture using SLA management which helps in enhancing application security and scalability. It provides information regarding service delivery, resource controller, data center coordinator and physical machine manager.
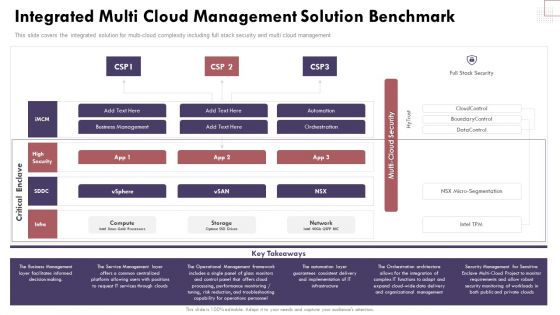
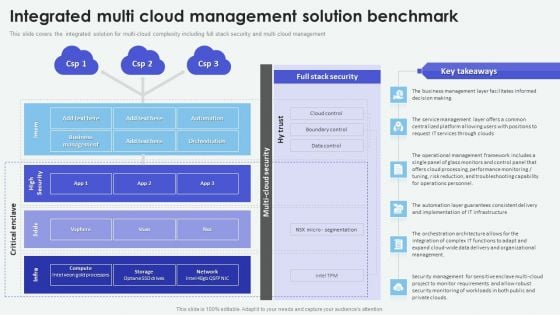
Integrated Multi Cloud Management Solution Benchmark Cloud Computing Complexities And Solutions Graphics PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management.Find a pre-designed and impeccable Integrated Multi Cloud Management Solution Benchmark Cloud Computing Complexities And Solutions Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
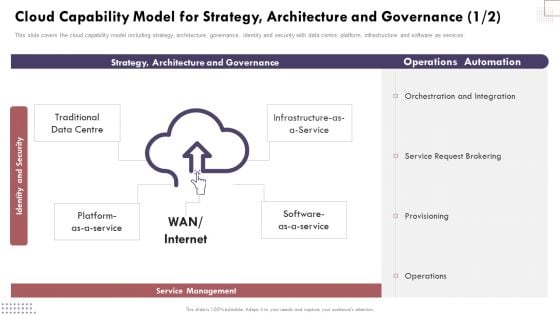
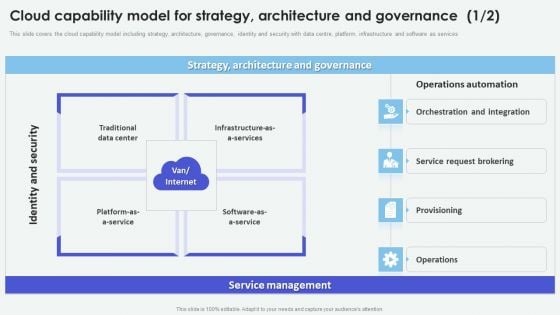
Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. Explore a selection of the finest Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
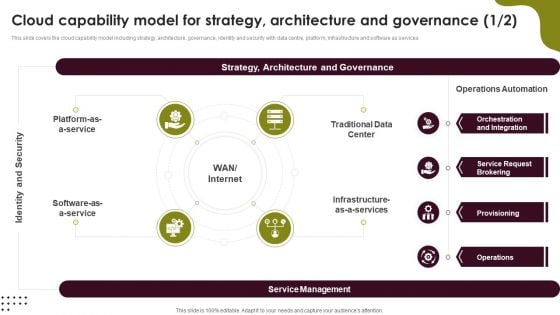
Cloud Computing Scalability Cloud Capability Model For Strategy Architecture Template PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. There are so many reasons you need a Cloud Computing Scalability Cloud Capability Model For Strategy Architecture Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Cloud Based Computing Analysis Integrated Multi Cloud Management Solution Inspiration PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Based Computing Analysis Integrated Multi Cloud Management Solution Inspiration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Cloud Computing Scalability Integrated Multi Cloud Management Solution Benchmark Icons PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Computing Scalability Integrated Multi Cloud Management Solution Benchmark Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Computing Scalability Integrated Multi Cloud Management Solution Benchmark Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
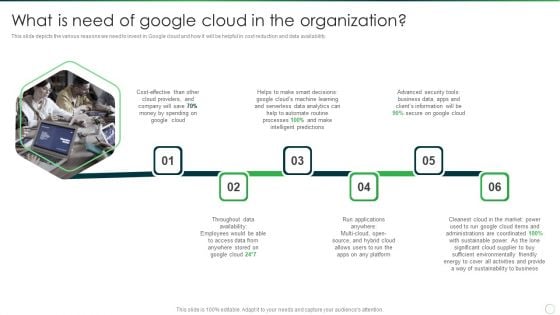
Google Cloud Computing System What Is Need Of Google Cloud In The Organization Guidelines PDF
This slide depicts the various reasons we need to invest in Google cloud and how it will be helpful in cost reduction and data availability. Presenting Google Cloud Computing System What Is Need Of Google Cloud In The Organization Guidelines PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Serverless Data Analytics, Business Data, Advanced Security Tools. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Based Computing Analysis Cloud Capability Model For Strategy Architecture Mockup PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. Want to ace your presentation in front of a live audience Our Cloud Based Computing Analysis Cloud Capability Model For Strategy Architecture Mockup PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
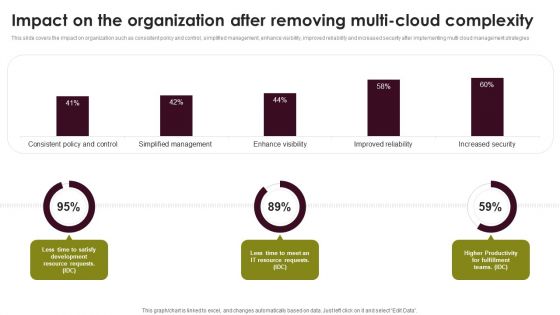
Cloud Computing Scalability Impact On The Organization After Removing Multi Cloud Diagrams PDF
This slide covers the impact on organization such as consistent policy and control, simplified management, enhance visibility, improved reliability and increased security after implementing multi cloud management strategies. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Computing Scalability Impact On The Organization After Removing Multi Cloud Diagrams PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Public Cloud Platforms In Cloud Computing Vector Icon Ppt PowerPoint Presentation File Professional PDF
Persuade your audience using this public cloud platforms in cloud computing vector icon ppt powerpoint presentation file professional pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including public cloud platforms in cloud computing vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Google Cloud Computing System What Are Google Cloud Services Designs PDF
This slide describes the google clouds primary services, including compute, storage and database, big data, developer tools, identity and security, internet of things, cloud AI, management tools, and data transfer. This is a Google Cloud Computing System What Are Google Cloud Services Designs PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Networking, Management Tools, Data Transfer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
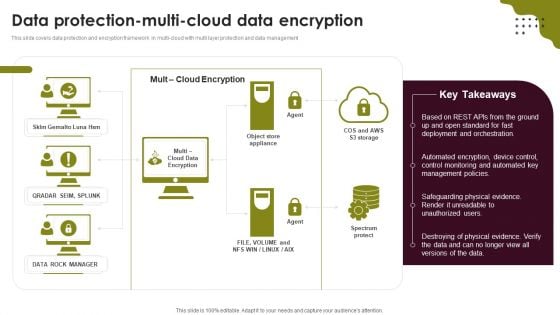
Cloud Computing Scalability Data Protection Multi Cloud Data Encryption Information PDF
This slide covers data protection and encryption framework in multi-cloud with multi layer protection and data management. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Computing Scalability Data Protection Multi Cloud Data Encryption Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
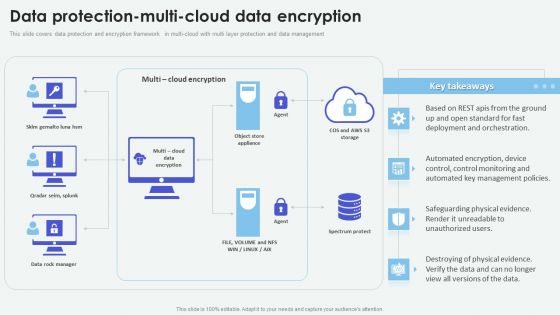
Cloud Based Computing Analysis Data Protection Multi Cloud Data Encryption Background PDF
This slide covers data protection and encryption framework in multi-cloud with multi layer protection and data management. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Based Computing Analysis Data Protection Multi Cloud Data Encryption Background PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Based Computing Analysis Data Protection Multi Cloud Data Encryption Background PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cloud Distribution Service Models Cloud Computing In Finance Industry Microsoft PDF
This slide represents the usage of cloud computing in the finance industry, and it provides many tools for the finance industry such as blockchain, elastic compute cloud auto-scaling, etc. This is a Cloud Distribution Service Models Cloud Computing In Finance Industry Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Developing Investment, Capital Markets, Financial Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
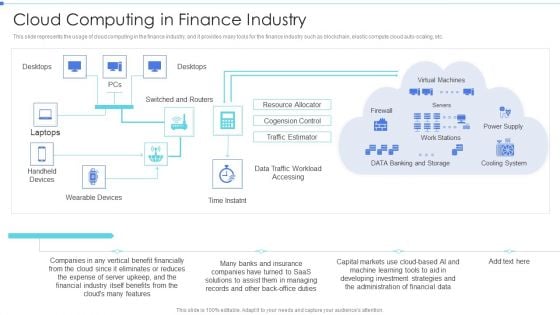
Cloud Based Service Models Cloud Computing In Finance Industry Slides PDF
This slide represents the usage of cloud computing in the finance industry, and it provides many tools for the finance industry such as blockchain, elastic compute cloud auto scaling, etc.Presenting Cloud Based Service Models Cloud Computing In Finance Industry Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Resource Allocator, Cogension Control, Traffic Estimator. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
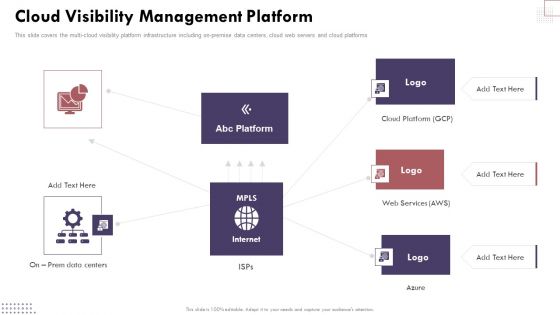
Cloud Visibility Management Platform Cloud Computing Complexities And Solutions Mockup PDF
This slide covers the multi-cloud visibility platform infrastructure including on-premise data centers, cloud web servers and cloud platforms. Retrieve professionally designed Cloud Visibility Management Platform Cloud Computing Complexities And Solutions Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Cloud Distribution Service Models Disadvantages Of Paas Cloud Computing Layer Icons PDF
This slide depicts the disadvantages of the PaaS cloud Computing layer, including vendor lock-in, data privacy, and integration with the rest of the system applications. Presenting Cloud Distribution Service Models Disadvantages Of Paas Cloud Computing Layer Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Data Privacy, System Applications, Vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
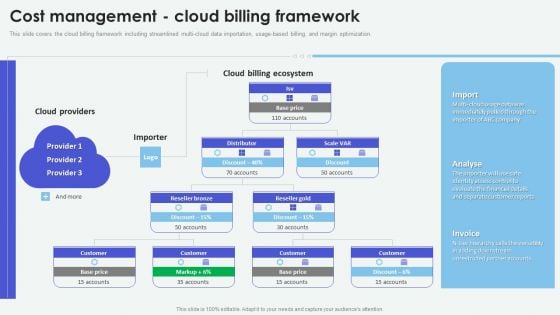
Cloud Based Computing Analysis Cost Management Cloud Billing Framework Portrait PDF
This slide covers the cloud billing framework including streamlined multi-cloud data importation, usage-based billing, and margin optimization. Present like a pro with Cloud Based Computing Analysis Cost Management Cloud Billing Framework Portrait PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
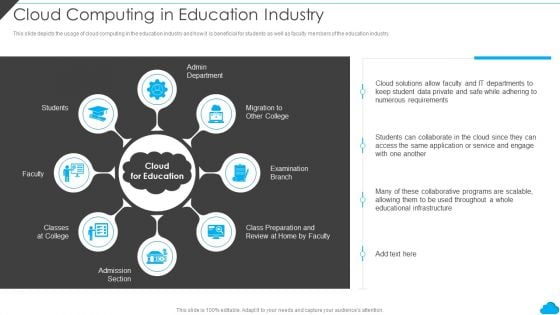
Cloud Distribution Service Models Cloud Computing In Education Industry Themes PDF
This slide depicts the usage of cloud computing in the education industry and how it is beneficial for students as well as faculty members of the education industry. Presenting Cloud Distribution Service Models Cloud Computing In Education Industry Themes PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Numerous Requirements, Service, Application. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Distribution Service Models Real Business Advantage Of Cloud Computing Microsoft PDF
This slide depicts the real business advantages of cloud computing and it includes off-site data storage, assistance in disasters, availability, productivity, etc. This is a Cloud Distribution Service Models Real Business Advantage Of Cloud Computing Microsoft PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Anywhere Productivity, Data Storage, Ownership Costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
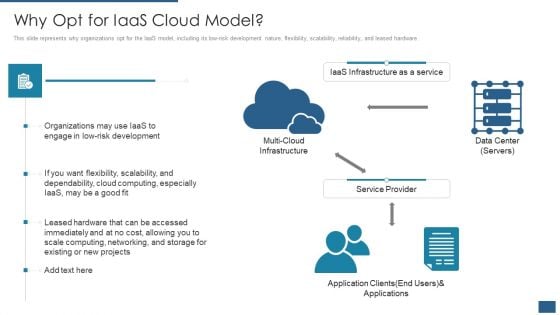
Cloud Computing Service Models IT Why Opt For Iaas Cloud Model Slides PDF
This slide represents why organizations opt for the IaaS model, including its low-risk development nature, flexibility, scalability, reliability, and leased hardware. Presenting cloud computing service models it why opt for iaas cloud model slides pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like multi cloud infrastructure, service provider, iaas infrastructure as a service, data center, application clients. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
1 Cloud Computing Concept With Mobile Wireless Email Device Connected To The Cloud Ppt Slides
This image slide displays cloud computing concept with mobile wireless email devices connected to the cloud. This image slide has been crafted with graphic of cloud and various icons representing communication on blue color background. This image slide depicts cloud computing on wireless devices. Use this image slide, in your presentations to explain concepts like cloud computing, technology and business. This image slide will enhance the quality of your presentations.
1 Cloud Computing Technology Icons Coming Out Of A Cloud Image Ppt Slides
This image slide displays cloud computing technology icons coming out of a cloud image. This image slide has been crafted with graphic of clouds and various icons representing communication. This image slide depicts cloud computing. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like cloud computing, technology and business. This image slide will help you achieve your goal of making professional presentations.
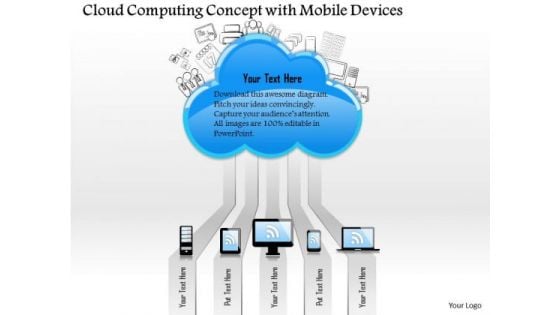
1 Cloud Computing Concept With Mobile Devices Connected To Public Cloud Ppt Slides
This image slide displays cloud computing concept with mobile devices connected to public. This image slide has been crafted with graphic of cloud and various technology devices like mobile, tablet, laptop, computer. Graphic of various business icons has also been used in this image slide. This image slide depicts cloud computing. Use this image slide, in your presentations to explain concepts like cloud computing, technology and business. This image slide will impart professional appearance to your presentations.
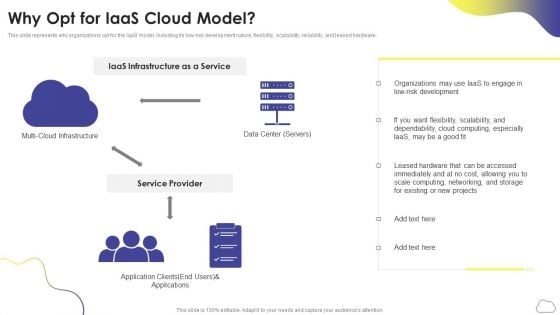
Cloud Computing Services Why Opt For Iaas Cloud Model Ppt PowerPoint Presentation File Images PDF
This slide represents why organizations opt for the IaaS model, including its low-risk development nature, flexibility, scalability, reliability, and leased hardware. This is a Cloud Computing Services Why Opt For Iaas Cloud Model Ppt PowerPoint Presentation File Images PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Provider, Data Center Servers, Multi Cloud Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
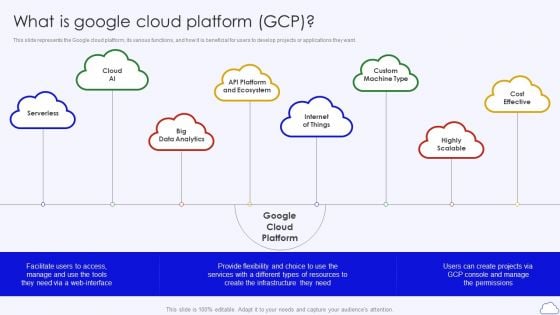
What Is Google Cloud Platform GCP Google Cloud Computing System Inspiration PDF
This slide represents the Google cloud platform, its various functions, and how it is beneficial for users to develop projects or applications they want.This is a What Is Google Cloud Platform GCP Google Cloud Computing System Inspiration PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Provide Flexibility, Services Different, Create Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
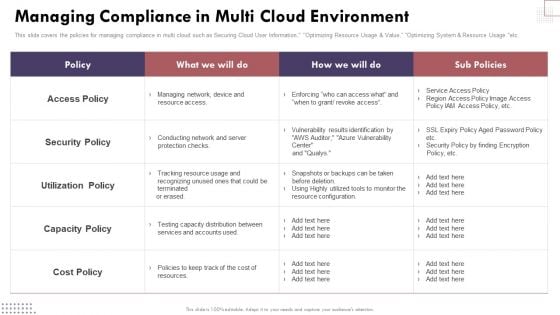
Managing Compliance In Multi Cloud Environment Cloud Computing Complexities And Solutions Diagrams PDF
This slide covers the policies for managing compliance in multi cloud such as Securing Cloud User Information, Optimizing Resource Usage Value, Optimizing System Resource Usage etc.Boost your pitch with our creative Managing Compliance In Multi Cloud Environment Cloud Computing Complexities And Solutions Diagrams PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cloud Computing Scalability Managing Compliance In Multi Cloud Environment Graphics PDF
This slide covers the policies for managing compliance in multi cloud such as Securing Cloud User Information, Optimizing Resource Usage and Value,Optimizing System and Resource Usage etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Computing Scalability Managing Compliance In Multi Cloud Environment Graphics PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cloud Based Computing Analysis Multi Cloud Services Fail To Deliver On Expectations Summary PDF
This modern and well-arranged Cloud Based Computing Analysis Multi Cloud Services Fail To Deliver On Expectations Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Based Computing Analysis Managing Compliance In Multi Cloud Environment Summary PDF
This slide covers the policies for managing compliance in multi cloud such as securing cloud user information, optimizing resource usage and value, optimizing system and resource usage etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Based Computing Analysis Managing Compliance In Multi Cloud Environment Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Based Computing Analysis Managing Compliance In Multi Cloud Environment Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cloud Computing Assessment Objectives To Conclude Evidences Ppt Portfolio Pictures PDF
The slide highlights various objectives of cloud computing audit to ensure effective assessment and mitigation of IT risks. Various objectives included are manage IT risks, ensure compliance and identify security controls Persuade your audience using this Cloud Computing Assessment Objectives To Conclude Evidences Ppt Portfolio Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Manage IT Risks, Ensure Compliance, Identify Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
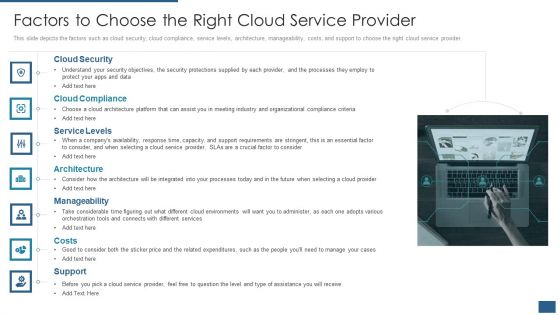
Cloud Computing Service Models IT Factors To Choose The Right Cloud Service Provider Topics PDF
This slide depicts the factors such as cloud security, cloud compliance, service levels, architecture, manageability, costs, and support to choose the right cloud service provider. This is a cloud computing service models it factors to choose the right cloud service provider topics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cloud security, cloud compliance, service levels, architecture, manageability, costs, support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Services Factors To Choose The Right Cloud Service Provider Slides PDF
This slide depicts the factors such as cloud security, cloud compliance, service levels, architecture, manageability, costs, and support to choose the right cloud service provider. Presenting Cloud Computing Services Factors To Choose The Right Cloud Service Provider Slides PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Cloud Security, Cloud Compliance, Service Levels, Architecture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
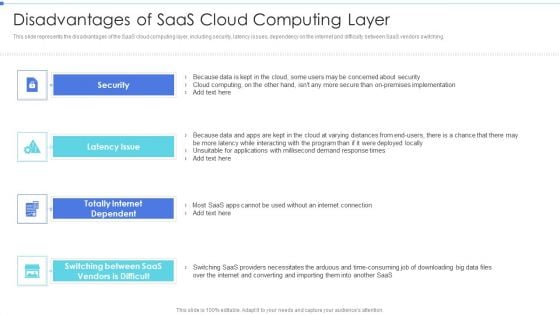
Cloud Based Service Models Disadvantages Of Saas Cloud Computing Layer Designs PDF
This slide depicts the factors such as cloud security, cloud compliance, service levels, architecture, manageability, costs, and support to choose the right cloud service provider.Presenting Cloud Based Service Models Disadvantages Of Saas Cloud Computing Layer Designs PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Cloud Security, Manageability, Architecture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
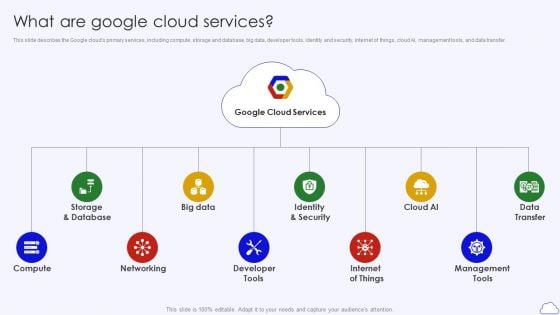
What Are Google Cloud Services Google Cloud Computing System Topics PDF
This slide describes the Google clouds primary services, including compute, storage and database, big data, developer tools, identity and security, internet of things, cloud AI, management tools, and data transfer. This is a What Are Google Cloud Services Google Cloud Computing System Topics PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Storage Database, Identity Security, Internet Things. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Factors To Choose The Right Cloud Service Platform Application Areas Of Mobile Cloud Computing
This slide depicts the factors needed to select the right cloud service provider for the mobile app. It includes factors such as cloud security, cloud compliance, service levels, architecture, manageability, costs, and support. Find highly impressive Factors To Choose The Right Cloud Service Platform Application Areas Of Mobile Cloud Computing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Factors To Choose The Right Cloud Service Platform Application Areas Of Mobile Cloud Computing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide depicts the factors needed to select the right cloud service provider for the mobile app. It includes factors such as cloud security, cloud compliance, service levels, architecture, manageability, costs, and support
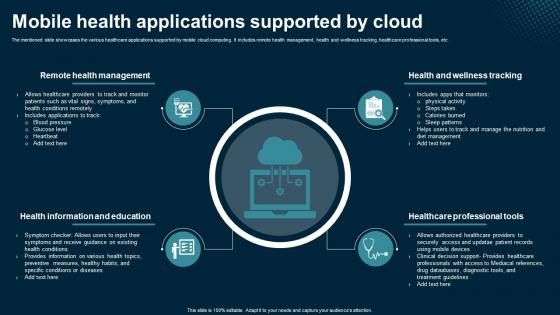
Mobile Health Applications Supported By Cloud Application Areas Of Mobile Cloud Computing
The mentioned slide showcases the various healthcare applications supported by mobile cloud computing. It includes remote health management, health and wellness tracking, healthcare professional tools, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Mobile Health Applications Supported By Cloud Application Areas Of Mobile Cloud Computing from Slidegeeks and deliver a wonderful presentation. The mentioned slide showcases the various healthcare applications supported by mobile cloud computing. It includes remote health management, health and wellness tracking, healthcare professional tools, etc.
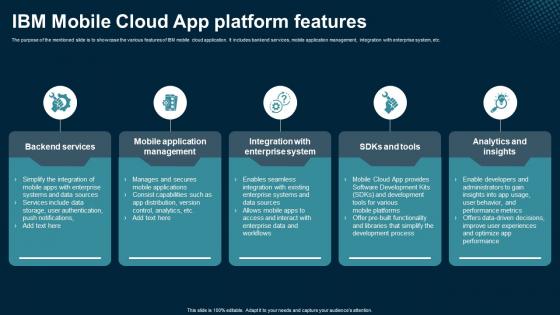
IBM Mobile Cloud App Platform Features Application Areas Of Mobile Cloud Computing
The purpose of the mentioned slide is to showcase the various features of IBM mobile cloud application. It includes bankend services, mobile application management, integration with enterprise system, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IBM Mobile Cloud App Platform Features Application Areas Of Mobile Cloud Computing template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IBM Mobile Cloud App Platform Features Application Areas Of Mobile Cloud Computing that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of the mentioned slide is to showcase the various features of IBM mobile cloud application. It includes bankend services, mobile application management, integration with enterprise system, etc.
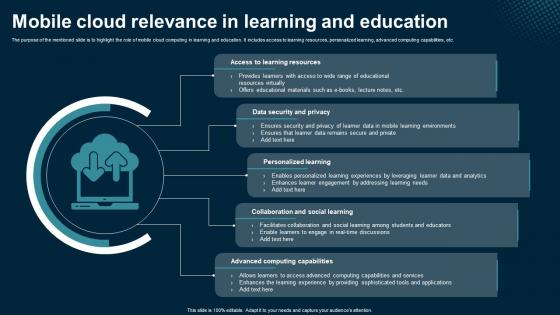
Mobile Cloud Relevance In Learning And Education Application Areas Of Mobile Cloud Computing
Explore a selection of the finest Mobile Cloud Relevance In Learning And Education Application Areas Of Mobile Cloud Computing here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Mobile Cloud Relevance In Learning And Education Application Areas Of Mobile Cloud Computing to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The purpose of the mentioned slide is to highlight the role of mobile cloud computing in learning and education. It includes access to learning resources, personalized learning, advanced computing capabilities, etc.
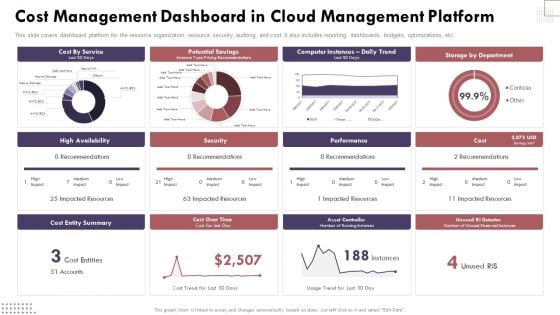
Cost Management Dashboard In Cloud Management Platform Cloud Computing Complexities And Solutions Ideas PDF
This slide covers dashboard platform for the resource organization, resource security, auditing, and cost. It also includes reporting, dashboards, budgets, optimizations, etc. Presenting this PowerPoint presentation, titled Cost Management Dashboard In Cloud Management Platform Cloud Computing Complexities And Solutions Ideas PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cost Management Dashboard In Cloud Management Platform Cloud Computing Complexities And Solutions Ideas PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cost Management Dashboard In Cloud Management Platform Cloud Computing Complexities And Solutions Ideas PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
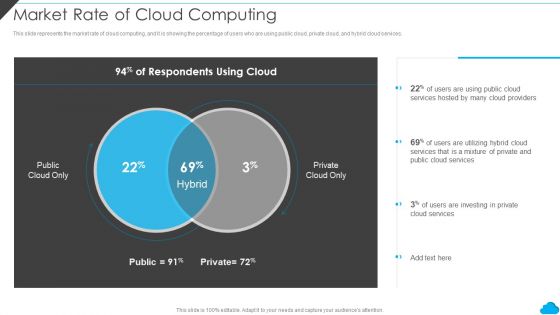
Cloud Distribution Service Models Market Rate Of Cloud Computing Introduction PDF
This slide represents the market rate of cloud computing, and it is showing the percentage of users who are using public cloud, private cloud, and hybrid cloud services. This is a Cloud Distribution Service Models Market Rate Of Cloud Computing Introduction PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Market Rate, Cloud Computing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Assessment Of Cloud And Traditional Integrating Cloud Computing To Enhance Projects Effectiveness Mockup PDF
The following slide showcases comparative analysis of cloud and traditional project management. It provides information about capital expenditure, scalability, efficiency, real time information, security, fixes, etc. There are so many reasons you need a Comparative Assessment Of Cloud And Traditional Integrating Cloud Computing To Enhance Projects Effectiveness Mockup PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
1 Cloud Computing Cloud With Mobile Devices Around It Showing Global Connectivity Ppt Slide
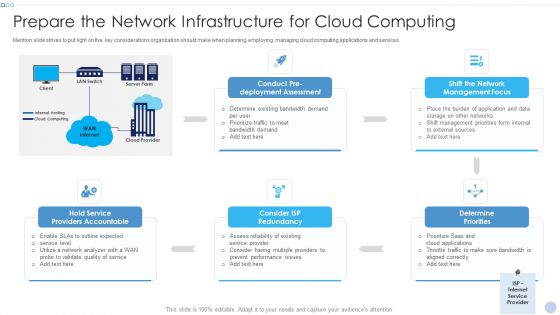
Techniques To Implement Cloud Infrastructure Prepare The Network Infrastructure For Cloud Computing Structure PDF
Mention slide strives to put light on five key considerations organization should make when planning, employing, managing cloud computing applications and services.Deliver and pitch your topic in the best possible manner with this Techniques To Implement Cloud Infrastructure Prepare The Network Infrastructure For Cloud Computing Structure PDF. Use them to share invaluable insights on Providers Accountable, Deployment Assessment, Management Focus and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
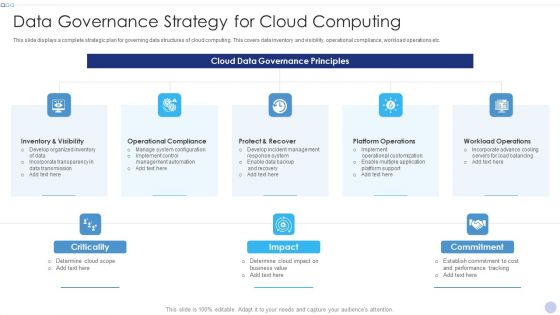
Techniques To Implement Cloud Infrastructure Data Governance Strategy For Cloud Computing Background PDF
This slide displays a complete strategic plan for governing data structures of cloud computing. This covers data inventory and visibility, operational compliance, workload operations etc. Deliver and pitch your topic in the best possible manner with this Techniques To Implement Cloud Infrastructure Data Governance Strategy For Cloud Computing Background PDF. Use them to share invaluable insights on Operational Compliance, Platform Operations, Workload Operations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
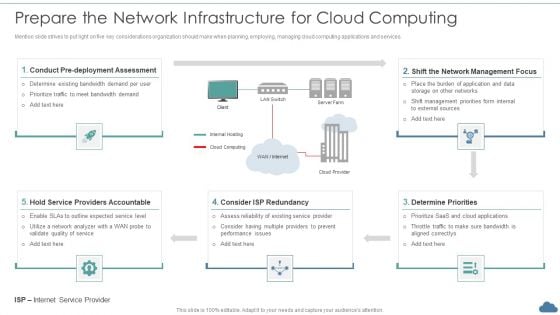
Cloud Optimization Infrastructure Model Prepare The Network Infrastructure For Cloud Computing Inspiration PDF
Mention slide strives to put light on five key considerations organization should make when planning, employing, managing cloud computing applications and services.Deliver an awe inspiring pitch with this creative Cloud Optimization Infrastructure Model Prepare The Network Infrastructure For Cloud Computing Inspiration PDF bundle. Topics like Providers Accountable, Determine Priorities, Consider Redundancy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
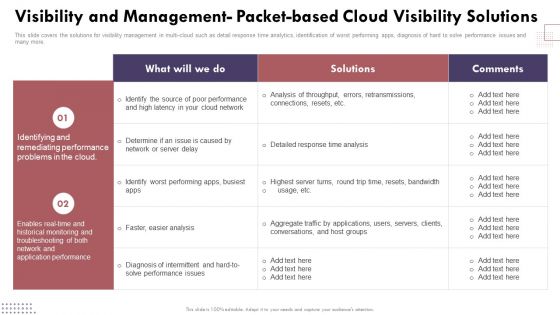
Visibility And Management Packetbased Cloud Visibility Cloud Computing Complexities And Solutions Rules PDF
This slide covers the number of cloud providers are being used which are increasing complexity and their importance in managing companys cloud capabilities.Get a simple yet stunning designed Visibility And Management Packetbased Cloud Visibility Cloud Computing Complexities And Solutions Rules PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Visibility And Management Packetbased Cloud Visibility Cloud Computing Complexities And Solutions Rules PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
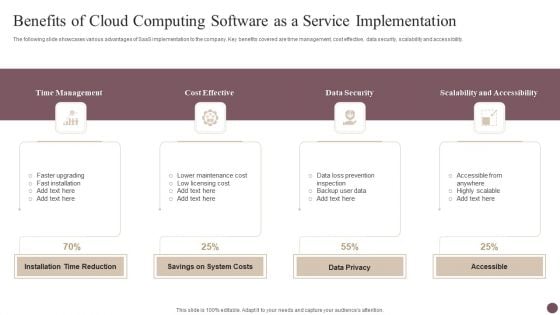
Benefits Of Cloud Computing Software As A Service Implementation Slides PDF
The following slide showcases various advantages of SaaS implementation to the company. Key benefits covered are time management, cost effective, data security, scalability and accessibility. Presenting Benefits Of Cloud Computing Software As A Service Implementation Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Time Management, Cost Effective, Data Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































