Collateral Management
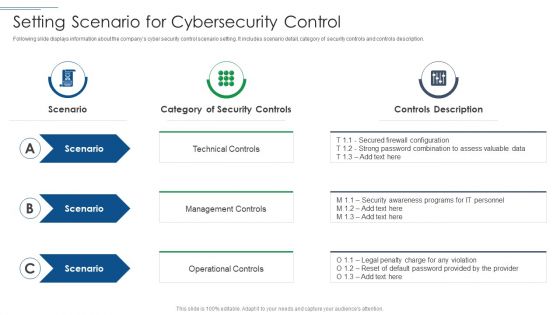
IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF
This is a IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technical Control, Management Controls, Operational Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF Use them to share invaluable insights on Assessing Information Security, Safeguarding Valuable, Vulnerability Intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enhanced Protection Corporate Event Administration Impact Of Effective Security Management Brochure PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration impact of effective security management brochure pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
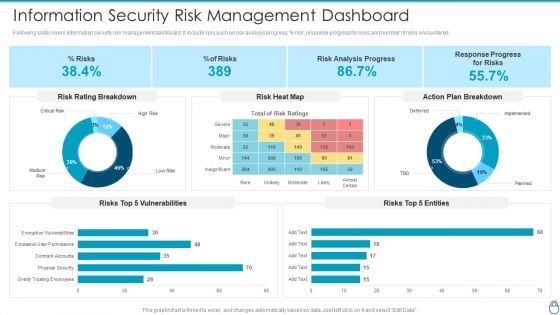
Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
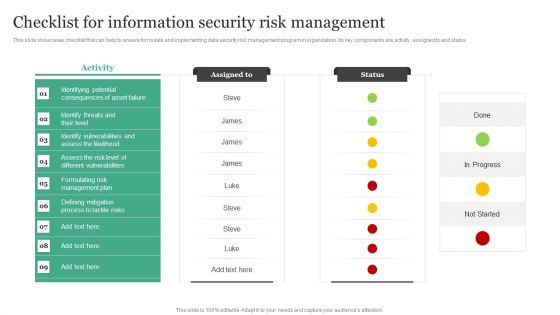
Checklist For Information Security Risk Management Information Security Risk Administration Portrait PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status.Take your projects to the next level with our ultimate collection of Checklist For Information Security Risk Management Information Security Risk Administration Portrait PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they all make your projects stand out from the rest.

Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Find highly impressive CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
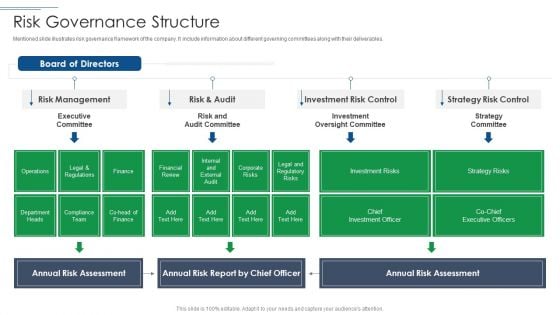
IT Security Risk Management Approach Introduction Risk Governance Structure Mockup PDF
Mentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Risk Governance Structure Mockup PDF. Use them to share invaluable insights on Risk Management, Investment Risk Control, Strategy Risk Control and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
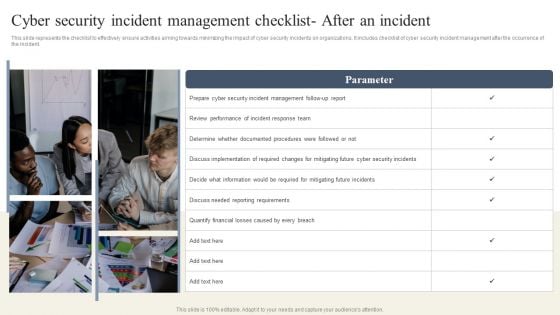
CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF can be your best option for delivering a presentation. Represent everything in detail using CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Present like a pro with Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
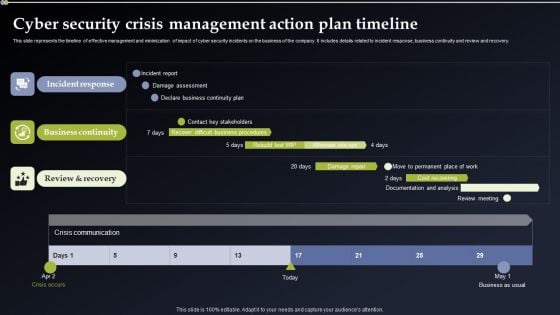
Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Developing IT Security Strategy Budget For Information Security Risk Management Information PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. This Developing IT Security Strategy Budget For Information Security Risk Management Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Budget For Information Security Risk Management Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Explore a selection of the finest Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
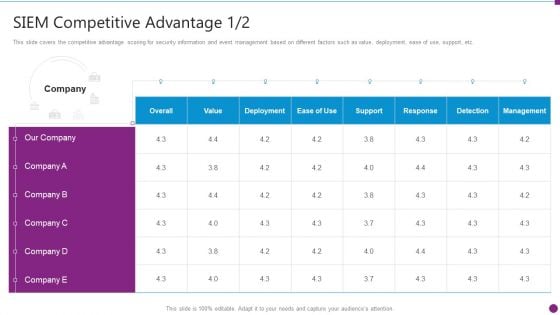
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Competitive Guidelines PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance siem competitive guidelines pdf. Use them to share invaluable insights on siem competitive advantage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
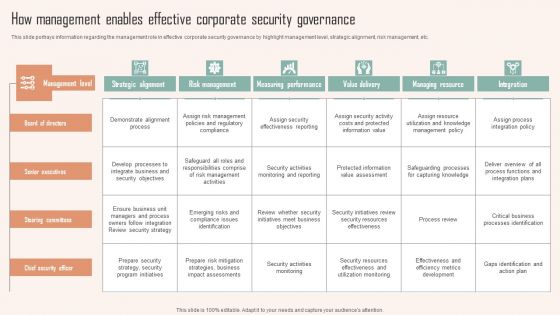
How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
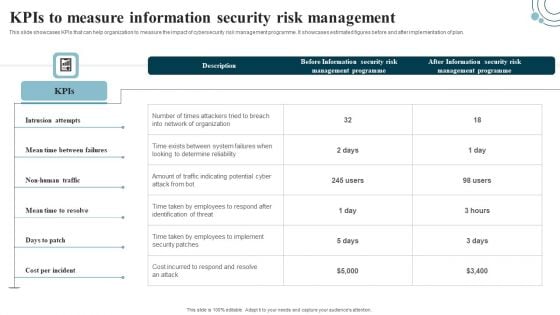
Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF today and make your presentation stand out from the rest.

Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
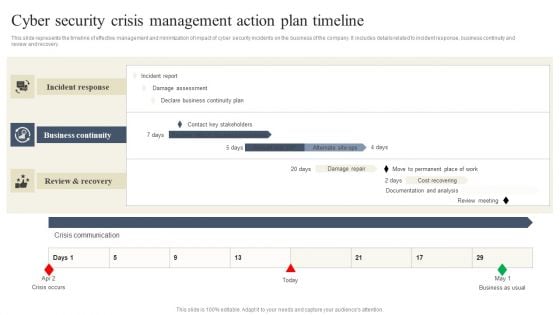
CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Get a simple yet stunning designed CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
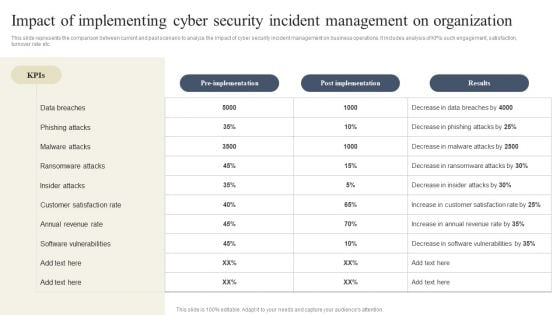
CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF.
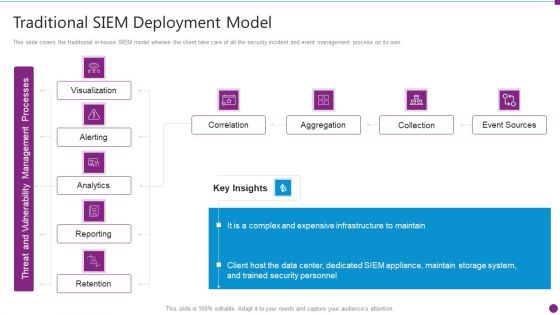
Security Information And Event Management Strategies For Financial Audit And Compliance Traditional SIEM Deployment Guidelines PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance traditional siem deployment guidelines pdf bundle. Topics like correlation, aggregation, collection, event sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Configuration Management Compliance Ppt PowerPoint Presentation Gallery Graphics Cpb Pdf
Presenting this set of slides with name security configuration management compliance ppt powerpoint presentation gallery graphics cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like security configuration management compliance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Agenda Of Security Information And Event Management Strategies For Financial Audit And Compliance Infographics PDF
This is a agenda of security information and event management strategies for financial audit and compliance infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like customers, security intelligence, log management and compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Governance Risk Management Ppt PowerPoint Presentation Gallery Graphics Pictures Cpb Pdf
Presenting this set of slides with name information security governance risk management ppt powerpoint presentation gallery graphics pictures cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like information security governance risk management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
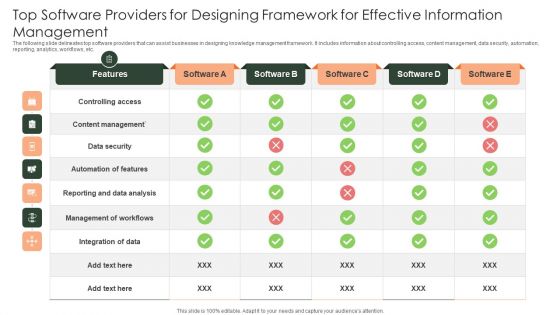
Top Software Providers For Designing Framework For Effective Information Management Slides PDF
The following slide delineates top software providers that can assist businesses in designing knowledge management framework. It includes information about controlling access, content management, data security, automation, reporting, analytics, workflows, etc. Showcasing this set of slides titled Top Software Providers For Designing Framework For Effective Information Management Slides PDF. The topics addressed in these templates are Content Management, Data Security, Controlling Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
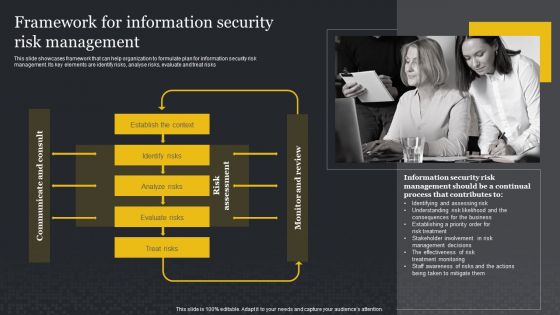
Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks. Presenting this PowerPoint presentation, titled Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. Explore a selection of the finest Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
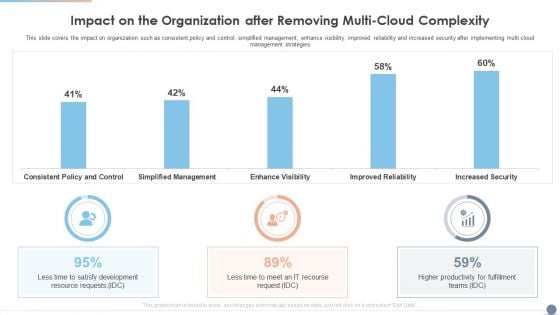
Multi Cloud Complexity Management Impact On The Organization After Removing Multi Cloud Complexity Information PDF
This slide covers the impact on organization such as consistent policy and control, simplified management, enhance visibility, improved reliability and increased security after implementing multi cloud management strategies. Deliver an awe inspiring pitch with this creative Multi Cloud Complexity Management Impact On The Organization After Removing Multi Cloud Complexity Information PDF bundle. Topics like Satisfy Development, Resource Requests, Fulfillment Teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
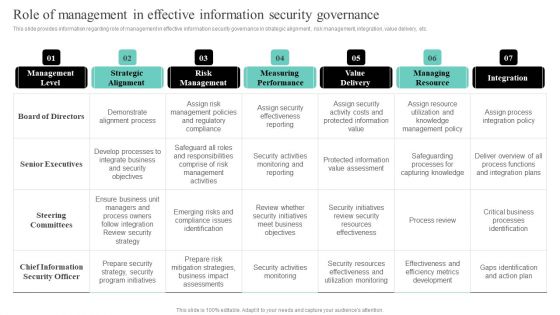
IT Cost Reduction Strategiesrole Of Management In Effective Information Security Clipart PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT Cost Reduction Strategiesrole Of Management In Effective Information Security Clipart PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT Cost Reduction Strategiesrole Of Management In Effective Information Security Clipart PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
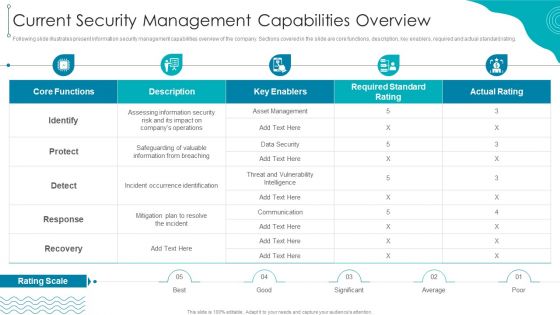
ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF bundle. Topics like Occurrence Identification, Communication, Required Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Implementing An Effective Ecommerce Management Framework Importance Of Secure Ecommerce Payment Systems Designs PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. It includes benefits of order management system such as fast delivery, less mistakes etc. It includes benefits of order management system such as fast delivery, less mistakes etc. This Implementing An Effective Ecommerce Management Framework Importance Of Secure Ecommerce Payment Systems Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing An Effective Ecommerce Management Framework Importance Of Secure Ecommerce Payment Systems Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today

ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver and pitch your topic in the best possible manner with this ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF. Use them to share invaluable insights on Assessing Information, Occurrence Identification, Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
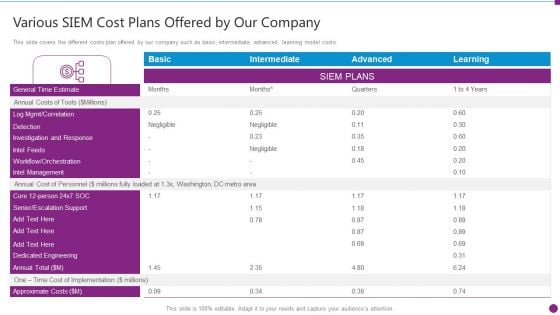
Security Information And Event Management Strategies For Financial Audit And Compliance Various SIEM Cost Clipart PDF
This slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance various siem cost clipart pdf. Use them to share invaluable insights on intel management, general time, annual costs of tools and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
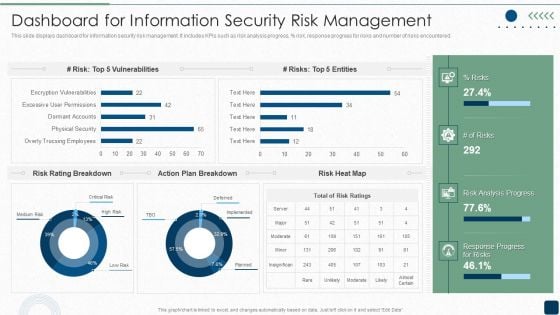
ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF bundle. Topics like Vulnerabilities, Rating Breakdown, Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf
This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc. This Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc.
Desktop Security Management What Are The Benefits Of Computer Security Icons PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting desktop security management what are the benefits of computer security icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, environment, potential, devices, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
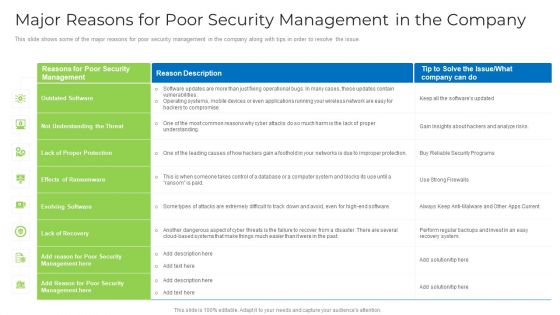
Major Reasons For Poor Security Management In The Company Download PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company download pdf bundle. Topics like applications, operating systems, network, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
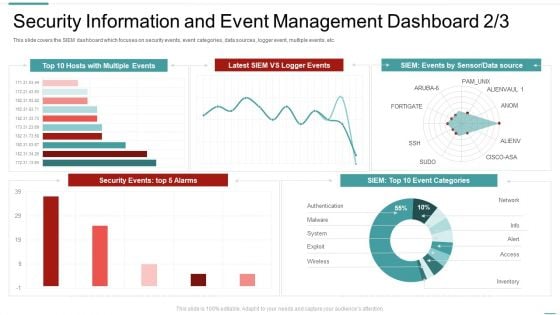
SIEM Services Security Information And Event Management Ppt File Objects PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative siem services security information and event management ppt file objects pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
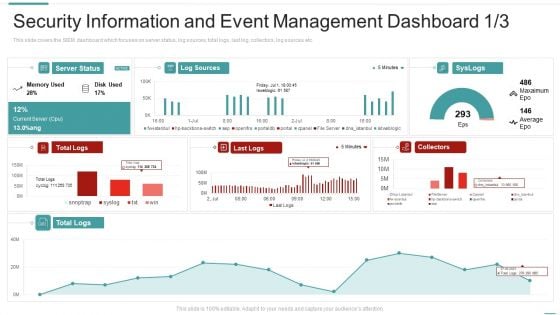
Risk Recognition Automation Security Information And Event Management Dashboard Ppt Model Elements PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard ppt model elements pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
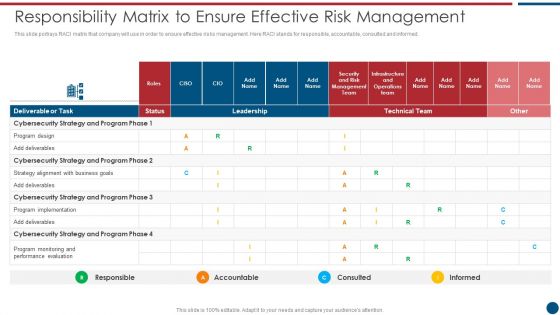
Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF
This slide signifies increasing cyber security and IT through problem management process. It includes stages like detection, define, investigate, identify resolutions, implement and follow up. Presenting Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Problem Detection, Define, Investigate, Identify Resolutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
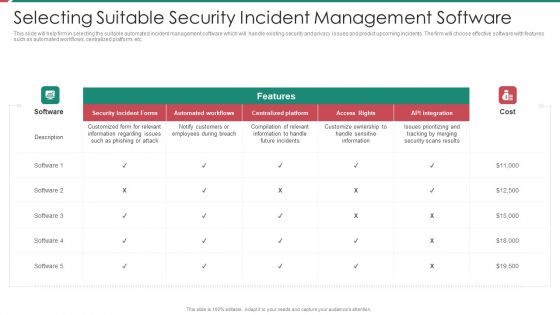
Security And Process Integration Selecting Suitable Security Incident Management Software Brochure PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative security and process integration selecting suitable security incident management software brochure pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Risk Assessment And Analysis Template PDF
This is a security management plan steps in detail risk assessment and analysis template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential consequence, security risks or liabilities, management to educate You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
5 Stage Framework Security Policy Management Slide Ppt PowerPoint Presentation Outline Examples PDF
Persuade your audience using this 5 stage framework security policy management slide ppt powerpoint presentation outline examples pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 5 stage framework security policy management slide. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
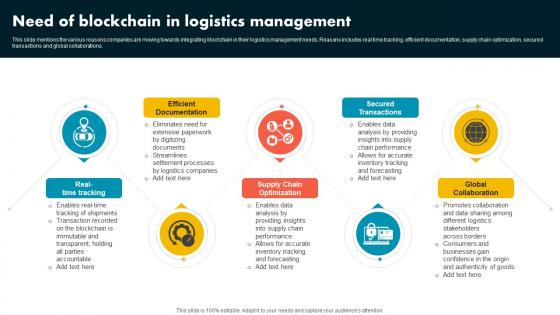
Need Of Blockchain In Logistics Management Supply Chain Evolution Harnessing The Power BCT SS V
This slide mentions the various reasons companies are moving towards integrating blockchain in their logistics management needs. Reasons includes real time tracking, efficient documentation, supply chain optimization, secured transactions and global collaborations. Make sure to capture your audiences attention in your business displays with our gratis customizable Need Of Blockchain In Logistics Management Supply Chain Evolution Harnessing The Power BCT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide mentions the various reasons companies are moving towards integrating blockchain in their logistics management needs. Reasons includes real time tracking, efficient documentation, supply chain optimization, secured transactions and global collaborations.

CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist During An Incident Sample PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist During An Incident Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Benefits Of Content Management Role Web Designing User Engagement Clipart PDF
This slide represents the benefits of using a Content Management System in the organization, and it provides features such as on-page SEO, teams collaboration, template making, security, and analytics. Want to ace your presentation in front of a live audience Our Benefits Of Content Management Role Web Designing User Engagement Clipart PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the benefits of using a Content Management System in the organization, and it provides features such as on-page SEO, teams collaboration, template making, security, and analytics.
Identity Based Security Access Management Ppt PowerPoint Presentation Gallery Background Cpb
Presenting this set of slides with name identity based security access management ppt powerpoint presentation gallery background cpb. This is an editable Powerpoint five stages graphic that deals with topics like identity based security access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Network Monitoring Management Security Ppt PowerPoint Presentation Summary Clipart Images Cpb
Presenting this set of slides with name network monitoring management security ppt powerpoint presentation summary clipart images cpb. This is an editable Powerpoint five stages graphic that deals with topics like network monitoring management security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
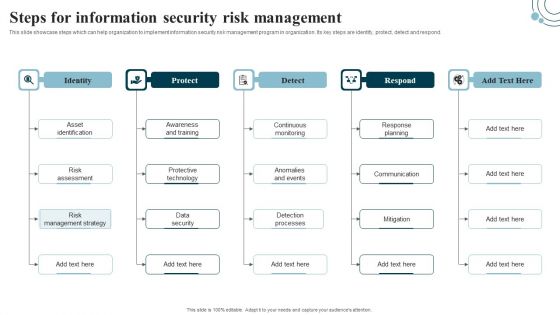
Developing IT Security Strategy Steps For Information Security Risk Management Slides PDF
This slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Developing IT Security Strategy Steps For Information Security Risk Management Slides PDF from Slidegeeks and deliver a wonderful presentation.

Real Time Assessment Of Security Threats Security Information And Event Management Logging Process Demonstration PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a real time assessment of security threats security information and event management logging process demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Security Operations Management Ppt PowerPoint Presentation Show Format Cpb Pdf
Presenting this set of slides with name cyber security operations management ppt powerpoint presentation show format cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber security operations management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Software Security Management Ppt PowerPoint Presentation Gallery Designs Download Cpb Pdf
Presenting this set of slides with name software security management ppt powerpoint presentation gallery designs download cpb pdf. This is an editable Powerpoint one stages graphic that deals with topics like software security management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Claims Management Security Contract Vector Icon Ppt PowerPoint Presentation Ideas Graphics Example PDF
Persuade your audience using this claims management security contract vector icon ppt powerpoint presentation ideas graphics example pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including claims management security contract vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cloud Data Security Management Vector Icon Ppt PowerPoint Presentation Gallery Vector PDF
Persuade your audience using this cloud data security management vector icon ppt powerpoint presentation gallery vector pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cloud data security management vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Data Management And Security With Contract File Vector Icon Ppt PowerPoint Presentation Gallery Display PDF
Persuade your audience using this data management and security with contract file vector icon ppt powerpoint presentation gallery display pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including data management and security with contract file vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
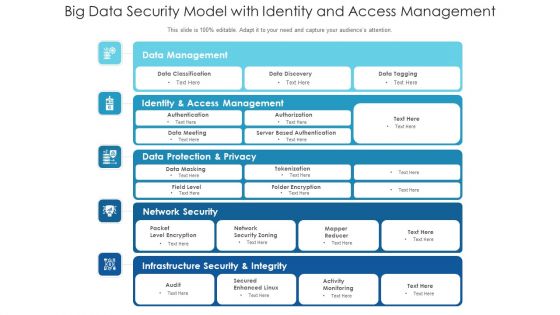
Big Data Security Model With Identity And Access Management Ppt PowerPoint Presentation Inspiration Good PDF
Pitch your topic with ease and precision using this big data security model with identity and access management ppt powerpoint presentation inspiration good pdf. This layout presents information on identity and access management, data protection and privacy, infrastructure security and integrity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Agenda For Implementing Security Management Strategy To Mitigate Risk Topics PDF
This is a agenda for implementing security management strategy to mitigate risk topics pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for implementing security management strategy to mitigate risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
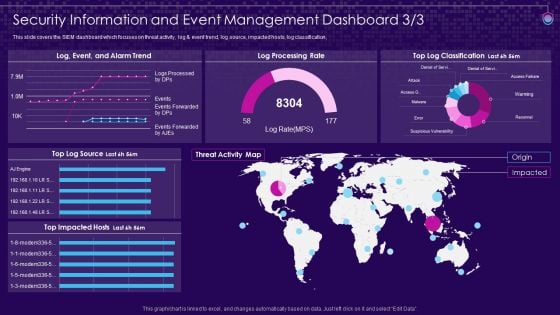
SIEM Services Security Information And Event Management Dashboard Source Ppt Outline Design Inspiration PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative siem services security information and event management dashboard source ppt outline design inspiration pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
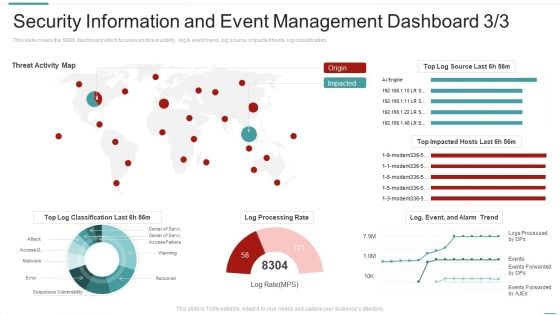
Risk Recognition Automation Security Information And Event Management Dashboard Activity Ppt Styles Influencers PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard activity ppt styles influencers pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
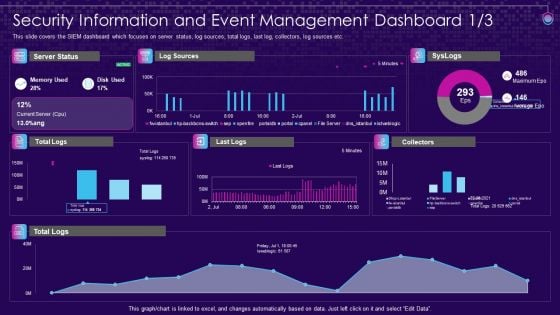
Risk Recognition Automation Security Information And Event Management Dashboard Source Ppt Professional Display PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this risk recognition automation security information and event management dashboard source ppt professional display pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































