Collateral Management
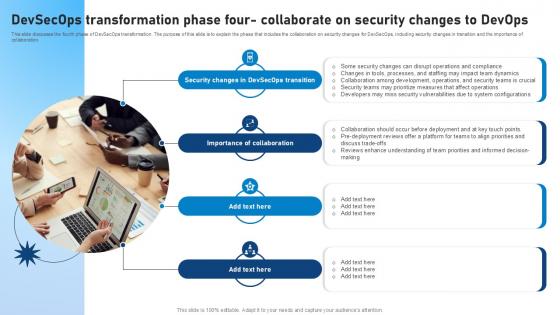
Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide
This slide discusses the fourth phase of DevSecOps transformation. The purpose of this slide is to explain the phase that includes the collaboration on security changes for DevSecOps, including security changes in transition and the importance of collaboration. This Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the fourth phase of DevSecOps transformation. The purpose of this slide is to explain the phase that includes the collaboration on security changes for DevSecOps, including security changes in transition and the importance of collaboration.
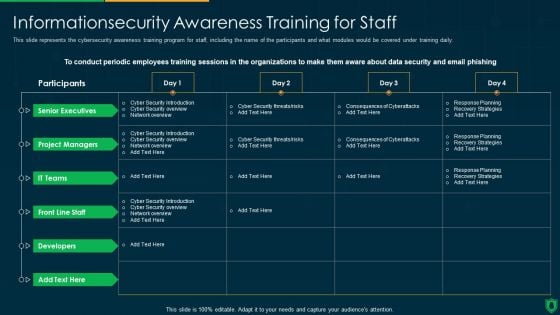
Info Security Information security Awareness Training For Staff Ppt PowerPoint Presentation Gallery Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this info security information security awareness training for staff ppt powerpoint presentation gallery template pdf. Use them to share invaluable insights on senior executives, project managers, it teams, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.

Cloud Information Security Measures And Controls In Cloud Security Ppt Slides Graphic Images PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. This is a Cloud Information Security Measures And Controls In Cloud Security Ppt Slides Graphic Images PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Detective Control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
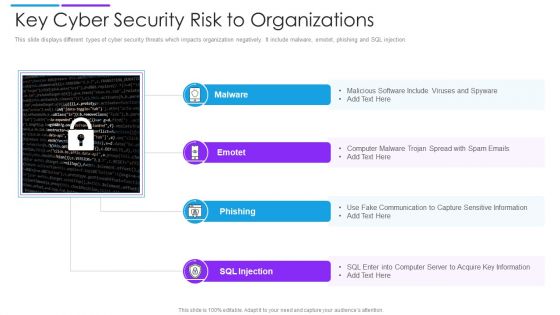
Key Cyber Security Risk To Organizations Structure PDF
This slide displays different types of cyber security threats which impacts organization negatively. It include malware, emotet, phishing and SQL injection. Presenting key cyber security risk to organizations structure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including malware, phishing, sql injection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Channels Security Service Provider Business Model BMC SS V
This slide showcases key channels of the multinational company to connect with the customers. The channels covered in the slide are website, technical assistance center, social media and customer service. Boost your pitch with our creative Channels Security Service Provider Business Model BMC SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases key channels of the multinational company to connect with the customers. The channels covered in the slide are website, technical assistance center, social media and customer service.
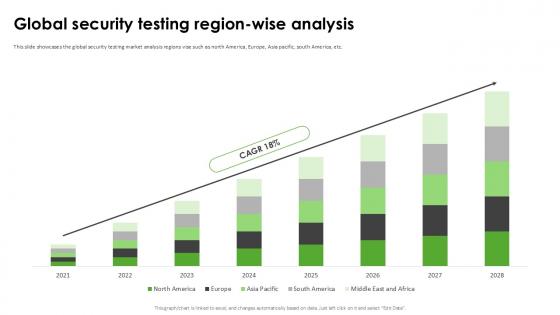
Global Security Testing Region Harnessing The World Of Ethical Ppt Example
This slide showcases the global security testing market analysis regions vise such as north America, Europe, Asia pacific, south America, etc. Find highly impressive Global Security Testing Region Harnessing The World Of Ethical Ppt Example on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Global Security Testing Region Harnessing The World Of Ethical Ppt Example for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the global security testing market analysis regions vise such as north America, Europe, Asia pacific, south America, etc.

Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Our Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Administrator Updating Information System Security Infographics PDF
Presenting administrator updating information system security infographics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including administrator updating information system security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Top Rated Outdoor Security Lights that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
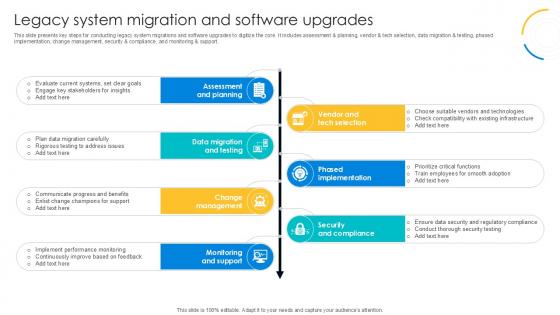
Legacy System Migration And Software Digital Transformation Journey PPT PowerPoint DT SS V
This slide presents key steps for conducting legacy system migrations and software upgrades to digitize the core. It includes assessment and planning, vendor and tech selection, data migration and testing, phased implementation, change management, security and compliance, and monitoring and support. Do you know about Slidesgeeks Vendor And Tech Selection, Phased Implementation, Security And Compliance These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide presents key steps for conducting legacy system migrations and software upgrades to digitize the core. It includes assessment and planning, vendor and tech selection, data migration and testing, phased implementation, change management, security and compliance, and monitoring and support.
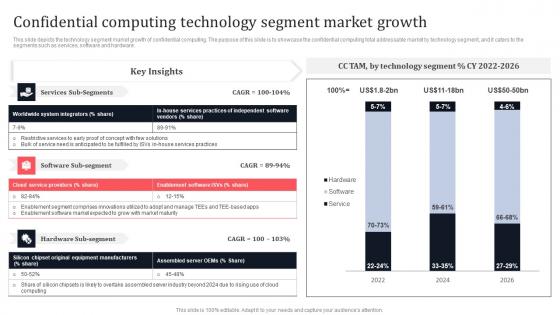
Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. This Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.

Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V
The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects. This Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects.

Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V
The slide determines the attributes on the basis of major trends in the Defense market. The purpose of this slide is to aware about the different areas where Defense is reshaping the market. It capture the information related to upcoming trends offered in the industry. This Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide determines the attributes on the basis of major trends in the Defense market. The purpose of this slide is to aware about the different areas where Defense is reshaping the market. It capture the information related to upcoming trends offered in the industry..

Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf
Find highly impressive Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. Our Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents Security Service Provider Business Model BMC SS V
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Security Service Provider Business Model BMC SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Security Service Provider Business Model BMC SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Table Of Contents Security Service Provider Business Model BMC SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Global Market Analysis Of Secure Web Gateway Web Threat Protection System
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. If you are looking for a format to display your unique thoughts, then the professionally designed Global Market Analysis Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Market Analysis Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.
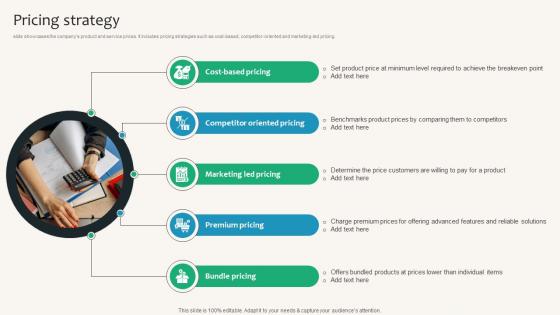
Pricing Strategy Security Service Provider Business Model BMC SS V
slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Pricing Strategy Security Service Provider Business Model BMC SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Pricing Strategy Security Service Provider Business Model BMC SS V today and make your presentation stand out from the rest slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing.
Credit Rating For Investors Sample Ppt Powerpoint Templates
This is a credit rating for investors sample ppt powerpoint templates. This is a four stage process. The stages in this process are pool their money with, fund manager, invest in, investors, securities, passed back to, returns, securities, generates.
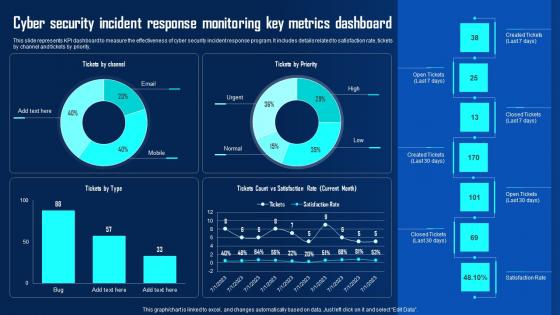
Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority.
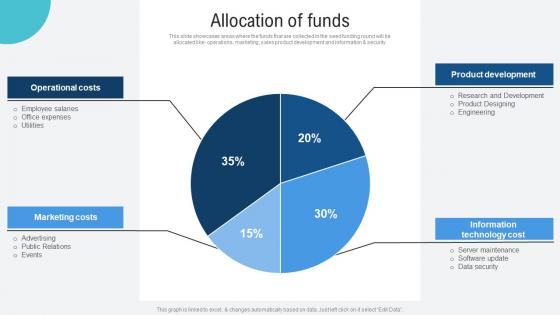
Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security. If you are looking for a format to display your unique thoughts, then the professionally designed Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security.

Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.
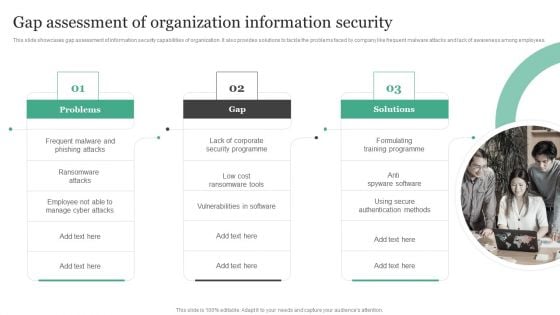
Gap Assessment Of Organization Information Security Information Security Risk Administration Summary PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employees.Find highly impressive Gap Assessment Of Organization Information Security Information Security Risk Administration Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Gap Assessment Of Organization Information Security Information Security Risk Administration Summary PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
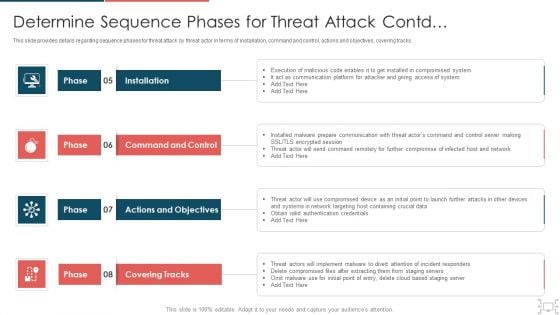
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
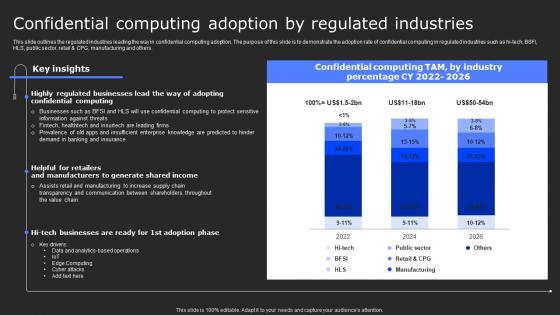
Confidential Computing Adoption By Secure Computing Framework Mockup Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Adoption By Secure Computing Framework Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Adoption By Secure Computing Framework Mockup Pdf today and make your presentation stand out from the rest This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
Identifying Information Security Threats And Impact On Organization Information Security Risk Administration Icons PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization.If you are looking for a format to display your unique thoughts, then the professionally designed Identifying Information Security Threats And Impact On Organization Information Security Risk Administration Icons PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Identifying Information Security Threats And Impact On Organization Information Security Risk Administration Icons PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
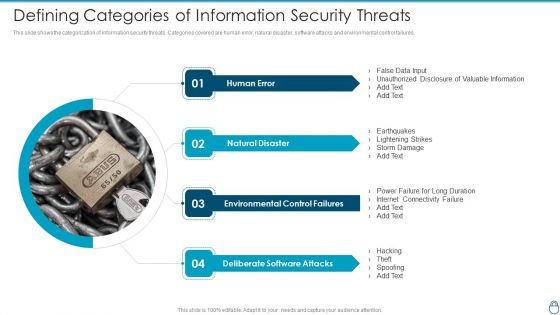
Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.This is a Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disaster, Environmental Control Failures, Deliberate Software Attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CASB 2 0 IT Cloud Access Security Broker And User Authentication
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CASB 2 0 IT Cloud Access Security Broker And User Authentication to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0.
Petals Diagram With 3 Stages For Business Process Ppt Copy Of Plan PowerPoint Slides
We present our petals diagram with 3 stages for business process ppt copy of plan PowerPoint Slides.Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides have the Brilliant backdrops. Guaranteed to illuminate the minds of your audience. Use our Signs PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey.Use these PowerPoint slides for presentations relating to project, business, diagram, swot, opportunity, model, framework, plan, concept, vector, success, symbol, threat, template, process, analysis, marketing, theory, label, abstract, management, manage, illustration, chart, weakness, strength, company, organization, commerce, conceptual, manager. The prominent colors used in the PowerPoint template are Gray, Green, Black. Get noted for your awesome slides with our Petals Diagram With 3 Stages For Business Process Ppt Copy Of Plan PowerPoint Slides. You'll always stay ahead of the game.

British Police Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with british police in front of union jack Our British Police Security PowerPoint Backgrounds And Templates 1210 are a great feeder line. They keep the energy coming to you.
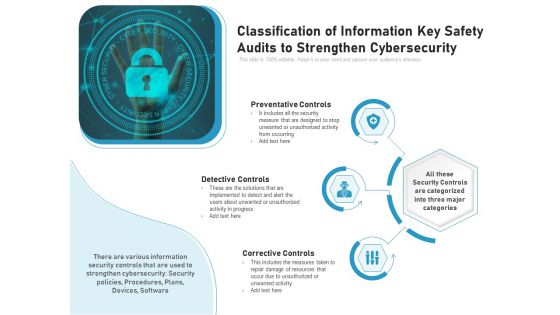
Classification Of Information Key Safety Audits To Strengthen Cybersecurity Ppt PowerPoint Presentation File Formats PDF
Presenting classification of information key safety audits to strengthen cybersecurity ppt powerpoint presentation file formats pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including preventative controls, detective controls, corrective controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
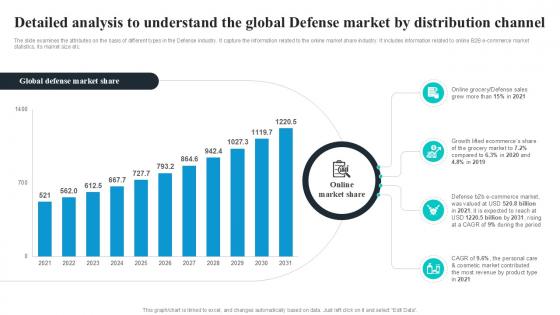
Detailed Analysis To Understand The Global Security Industry PPT Slide IR SS V
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to the online market share industry. It includes information related to online B2B e-commerce market statistics, its market size etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Detailed Analysis To Understand The Global Security Industry PPT Slide IR SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Detailed Analysis To Understand The Global Security Industry PPT Slide IR SS V today and make your presentation stand out from the rest The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to the online market share industry. It includes information related to online B2B e-commerce market statistics, its market size etc.
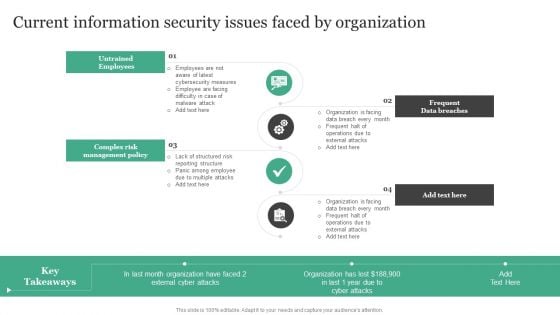
Current Information Security Issues Faced By Organization Information Security Risk Administration Summary PDF
Find a pre-designed and impeccable Current Information Security Issues Faced By Organization Information Security Risk Administration Summary PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Table Of Contents Cyber Security Administration In Organization Security Sample PDF
This is a table of contents cyber security administration in organization security sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring, financial, assets, security, workforce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
3 Stages For Business Process Ppt Construction Plan Template PowerPoint Slides
We present our 3 stages for business process ppt construction plan template PowerPoint Slides.Download and present our Success PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Use our Marketing PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Download and present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides have the Brilliant backdrops. Guaranteed to illuminate the minds of your audience. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime. Use our Signs PowerPoint Templates because you should Experience excellence with our PowerPoint Templates and Slides. They will take your breath away.Use these PowerPoint slides for presentations relating to project, business, diagram, swot, opportunity, model, framework, plan, concept, vector, success, symbol, threat, template, process, analysis, marketing, theory, label, abstract, management, manage, illustration, chart, weakness, strength, company, organization, commerce, conceptual, manager. The prominent colors used in the PowerPoint template are Yellow, White, Gray. Be the architect of your own destiny. Design it with our 3 Stages For Business Process Ppt Construction Plan Template PowerPoint Slides.
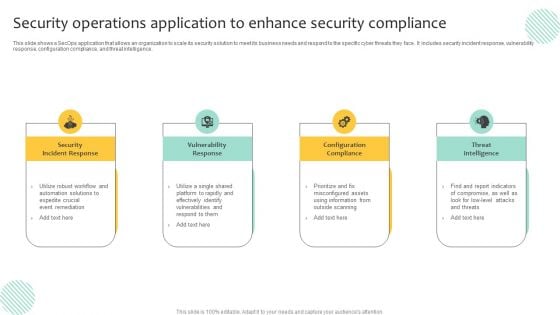
Security Operations Application To Enhance Security Compliance Rules PDF
This slide shows a SecOps application that allows an organization to scale its security solution to meet its business needs and respond to the specific cyber threats they face. It includes security incident response, vulnerability response, configuration compliance, and threat intelligence. Persuade your audience using this Security Operations Application To Enhance Security Compliance Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Configuration Compliance, Threat Intelligence, Vulnerability Response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
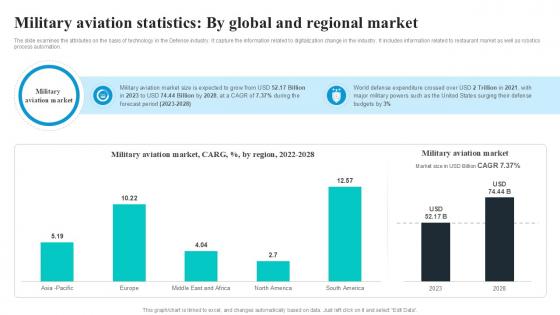
Military Aviation Statistics By Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to restaurant market as well as robotics process automation. Welcome to our selection of the Military Aviation Statistics By Global Security Industry PPT PowerPoint IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to restaurant market as well as robotics process automation.
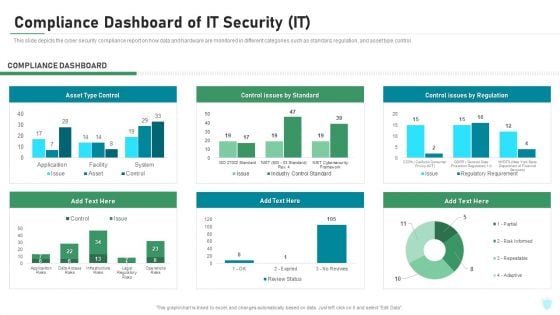
Compliance Dashboard Of IT Security IT Ppt Layouts Ideas PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative compliance dashboard of it security it ppt layouts ideas pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
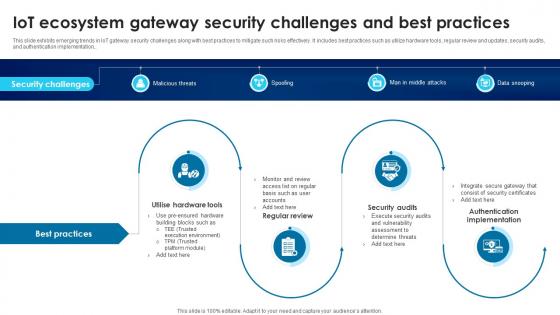
Building Trust With IoT Security IoT Ecosystem Gateway Security Challenges And Best Practices IoT SS V
This slide exhibits emerging trends in IoT gateway security challenges along with best practices to mitigate such risks effectively. It includes best practices such as utilize hardware tools, regular review and updates, security audits, and authentication implementation. Slidegeeks has constructed Building Trust With IoT Security IoT Ecosystem Gateway Security Challenges And Best Practices IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide exhibits emerging trends in IoT gateway security challenges along with best practices to mitigate such risks effectively. It includes best practices such as utilize hardware tools, regular review and updates, security audits, and authentication implementation.
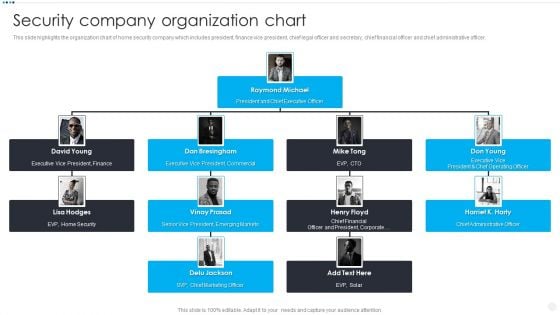
Smart Home Security Solutions Company Profile Security Company Organization Chart Diagrams PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. Presenting Smart Home Security Solutions Company Profile Security Company Organization Chart Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Executive Vice President, EVP Home Security, Chief Marketing Officer, Chief Administrative Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
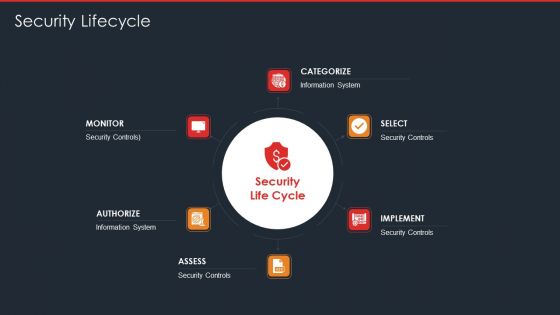
Data Safety Initiatives For Effective IT Security Threats Administration Security Lifecycle Template PDF
This is a data safety initiatives for effective it security threats administration security lifecycle template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information system, security controls, monitor, assess, implement, authorize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Data Encryption Performance Tracking Client Side Encryption PPT Presentation
This slide represents the dashboard which can be utilized by organization to monitor cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Data Encryption Performance Tracking Client Side Encryption PPT Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Encryption Performance Tracking Client Side Encryption PPT Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the dashboard which can be utilized by organization to monitor cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc.
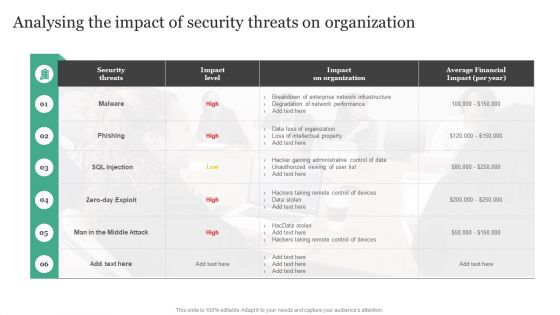
Analysing The Impact Of Security Threats On Organization Information Security Risk Administration Sample PDF
The Analysing The Impact Of Security Threats On Organization Information Security Risk Administration Sample PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
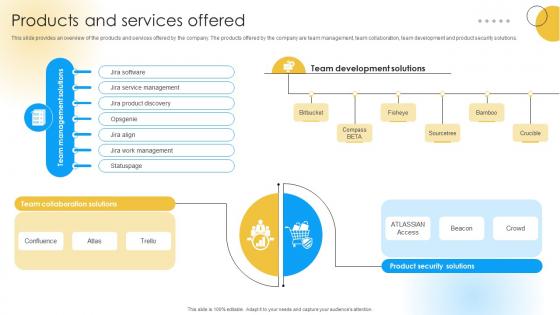
Products And Services Offered Software Development Company Funding Elevator Pitch Deck
This slide provides an overview of the products and services offered by the company. The products offered by the company are team management, team collaboration, team development and product security solutions. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Products And Services Offered Software Development Company Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Products And Services Offered Software Development Company Funding Elevator Pitch Deck. This slide provides an overview of the products and services offered by the company. The products offered by the company are team management, team collaboration, team development and product security solutions.

Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf
This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc.
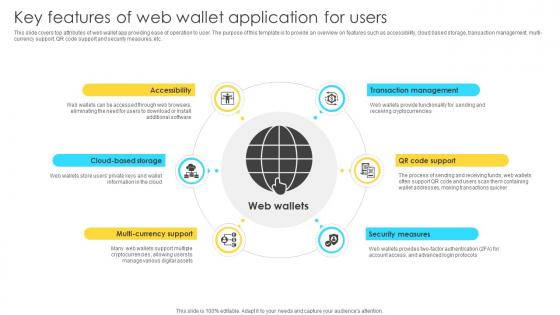
Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V
This slide covers top attributes of web wallet app providing ease of operation to user. The purpose of this template is to provide an overview on features such as accessibility, cloud based storage, transaction management, multi-currency support, QR code support and security measures, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers top attributes of web wallet app providing ease of operation to user. The purpose of this template is to provide an overview on features such as accessibility, cloud based storage, transaction management, multi-currency support, QR code support and security measures, etc.
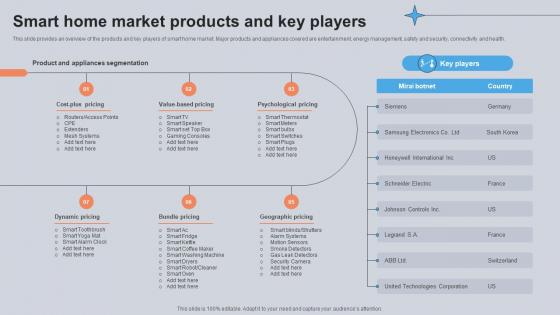
Smart Home Market Products And Key Players Utilizing Smart Appliances IoT SS V
This slide provides an overview of the products and key players of smart home market. Major products and appliances covered are entertainment, energy management, safety and security, connectivity and health. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Smart Home Market Products And Key Players Utilizing Smart Appliances IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Smart Home Market Products And Key Players Utilizing Smart Appliances IoT SS V. This slide provides an overview of the products and key players of smart home market. Major products and appliances covered are entertainment, energy management, safety and security, connectivity and health.

On Ramp Option 3 The Network Zero Trust Network Access
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than On Ramp Option 3 The Network Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab On Ramp Option 3 The Network Zero Trust Network Access today and make your presentation stand out from the rest This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Zero Trust Model On Ramp Option 3 The Network
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Presenting this PowerPoint presentation, titled Zero Trust Model On Ramp Option 3 The Network, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Model On Ramp Option 3 The Network. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Model On Ramp Option 3 The Network that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
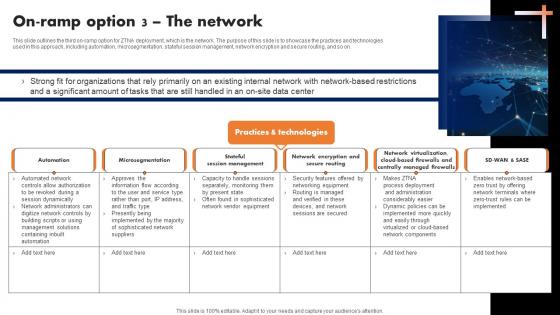
On Ramp Option 3 The Network Software Defined Perimeter SDP
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Software Defined Perimeter SDP from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
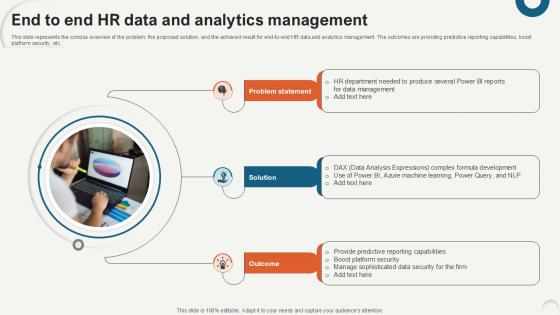
End To End HR Data And Analytics Data Analytics For Informed Decision Ppt Sample
This slide represents the concise overview of the problem, the proposed solution, and the achieved result for end-to-end HR data and analytics management. The outcomes are providing predictive reporting capabilities, boost platform security, etc. If you are looking for a format to display your unique thoughts, then the professionally designed End To End HR Data And Analytics Data Analytics For Informed Decision Ppt Sample is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download End To End HR Data And Analytics Data Analytics For Informed Decision Ppt Sample and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the concise overview of the problem, the proposed solution, and the achieved result for end-to-end HR data and analytics management. The outcomes are providing predictive reporting capabilities, boost platform security, etc.

Info Security Compliance Dashboard Of Information Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative info security compliance dashboard of information security ppt powerpoint presentation file graphics download pdf bundle. Topics like compliance dashboard, asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Zero Trust Model Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. This Zero Trust Model Overview Of Zero Trust Solution Categories from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Challenges And Considerations In Cloud Erp Integration Erp And Digital Transformation For Maximizing DT SS V
This slide addresses the key challenges faced while Integrating an ERP system with the cloud. It includes change management, security, access, permissions and productivity, optimum architectural and licensing models, and user onboarding and training.Slidegeeks is here to make your presentations a breeze with Challenges And Considerations In Cloud Erp Integration Erp And Digital Transformation For Maximizing DT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide addresses the key challenges faced while Integrating an ERP system with the cloud. It includes change management, security, access, permissions and productivity, optimum architectural and licensing models, and user onboarding and training.
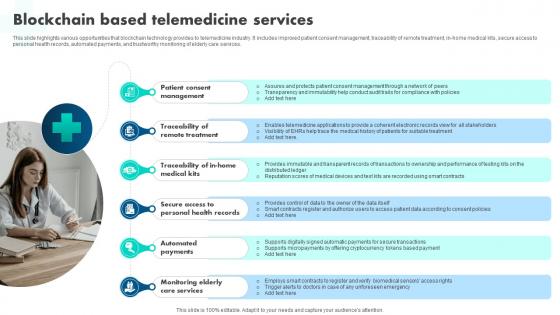
A55 How Blockchain Is Reshaping Blockchain Based Telemedicine Services BCT SS V
This slide highlights various opportunities that blockchain technology provides to telemedicine industry. It includes improved patient consent management, traceability of remote treatment, in-home medical kits, secure access to personal health records, automated payments, and trustworthy monitoring of elderly care services. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A55 How Blockchain Is Reshaping Blockchain Based Telemedicine Services BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights various opportunities that blockchain technology provides to telemedicine industry. It includes improved patient consent management, traceability of remote treatment, in-home medical kits, secure access to personal health records, automated payments, and trustworthy monitoring of elderly care services.
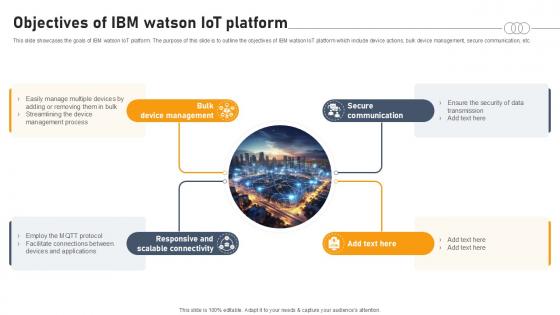
Objectives Of Ibm Watson IOT Platform Aws IOT Platform Ppt Slide
This slide showcases the goals of IBM watson IoT platform. The purpose of this slide is to outline the objectives of IBM watson IoT platform which include device actions, bulk device management, secure communication, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Objectives Of Ibm Watson IOT Platform Aws IOT Platform Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases the goals of IBM watson IoT platform. The purpose of this slide is to outline the objectives of IBM watson IoT platform which include device actions, bulk device management, secure communication, etc.
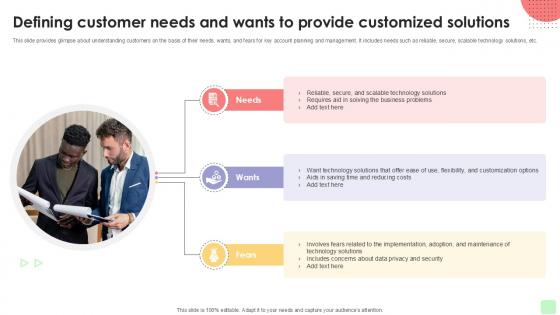
Defining Customer Needs And Wants Detailed Business Account PPT Presentation Strategy SS V
This slide provides glimpse about understanding customers on the basis of their needs, wants, and fears for key account planning and management. It includes needs such as reliable, secure, scalable technology solutions, etc. While your presentation may contain top-notch content, if it lacks visual appeal, youre not fully engaging your audience. Introducing our Defining Customer Needs And Wants Detailed Business Account PPT Presentation Strategy SS V deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, its downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck. This slide provides glimpse about understanding customers on the basis of their needs, wants, and fears for key account planning and management. It includes needs such as reliable, secure, scalable technology solutions, etc.


 Continue with Email
Continue with Email

 Home
Home


































