Collateral Management

Comparative Assessment Of Cloud And Traditional Project Management Microsoft PDF
The following slide showcases comparative analysis of cloud and traditional project management. It provides information about capital expenditure, scalability, efficiency, real time information, security, fixes, etc.There are so many reasons you need a Comparative Assessment Of Cloud And Traditional Project Management Microsoft PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Comparative Assessment Of Financial Management Software Brochure PDF
This slide showcases comparative analysis of top financial management software. It provides details Bonsai, Mint, Moneydance, Honeydue, accounting automation, financial reports, financial data security, etc. Find a pre-designed and impeccable Comparative Assessment Of Financial Management Software Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Key Challenges In Management Information Systems Portrait PDF
This slide presents key issues in management information and some appropriate solutions, that would help organisations to secure data and information in business processes. It includes digitizing information, automating processes, managing information growth and securing information. Presenting Key Challenges In Management Information Systems Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Digitizing Information, Automating Processes, Managing Information Growth. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
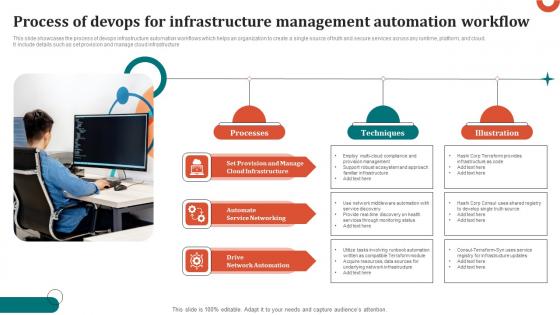
Process Of Devops For Infrastructure Management Automation Workflow Mockup Pdf
This slide showcases the process of devops infrastructure automation workflows which helps an organization to create a single source of truth and secure services across any runtime, platform, and cloud. It include details such as set provision and manage cloud infrastructure Pitch your topic with ease and precision using this Process Of Devops For Infrastructure Management Automation Workflow Mockup Pdf This layout presents information on Processes, Techniques, Illustration It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the process of devops infrastructure automation workflows which helps an organization to create a single source of truth and secure services across any runtime, platform, and cloud. It include details such as set provision and manage cloud infrastructure

Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices For Online Risk Management Graphics PDF
The purpose of this slide is to represent digital risk areas and solutions for effective risk management. It includes various risks such as mitigating cyber risk attack, managing third party, handling dynamic workforce, securing cloud migration etc. Presenting Best Practices For Online Risk Management Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigating Cyber Risk Attack, Managing Third Party, Handling Dynamic Workforce. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Adapting To Technological Change Technological Change Management Training Microsoft Pdf
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Adapting To Technological Change Technological Change Management Training Microsoft Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Adapting To Technological Change Technological Change Management Training Microsoft Pdf. This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc.
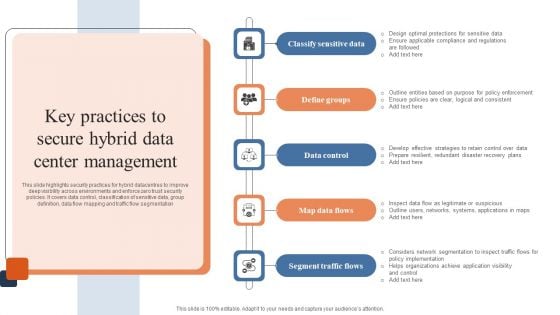
Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Additional Roles Pivotal For Successful Infrastructure Management Demonstration PDF
This slide provides information regarding the additional roles considered as pivotal for successful infrastructure management in terms of release manager, automation architect integration specialist, software tester developer and security engineer.This is a Additional Roles Pivotal For Successful Infrastructure Management Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Release Manager, Automation Architect, Integration Specialist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
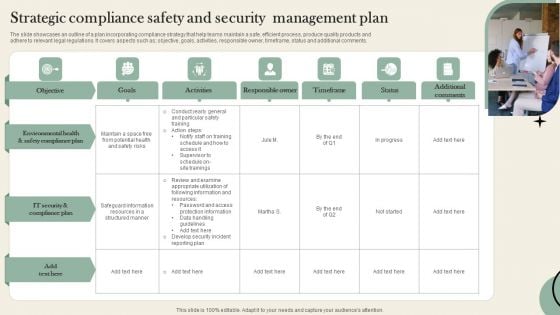
Strategic Compliance Safety And Security Management Plan Microsoft PDF
The slide showcases an outline of a plan incorporating compliance strategy that help teams maintain a safe, efficient process, produce quality products and adhere to relevant legal regulations. It covers aspects such as objective, goals, activities, responsible owner, timeframe, status and additional comments. Persuade your audience using this Strategic Compliance Safety And Security Management Plan Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Compliance Plan, It Security, Potential. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
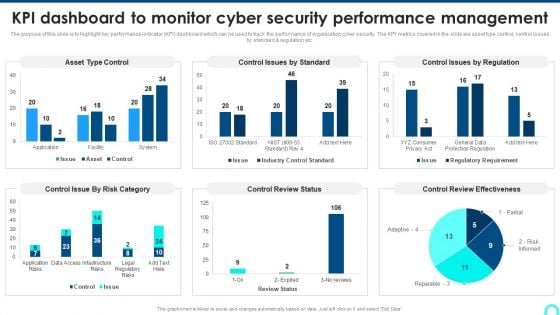
KPI Dashboard To Monitor Cyber Security Performance Management Background PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc.Deliver and pitch your topic in the best possible manner with this KPI Dashboard To Monitor Cyber Security Performance Management Background PDF. Use them to share invaluable insights on Control Issue, Control Review, Review Effectiveness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Threat Management Strategy With Strategies Ideas PDF
This slide focuses on the security risk mitigation plan which covers security components, vulnerabilities and mitigation strategies such as administrative, physical, technical and organizational safeguards with conducting workforce training, installing alarm systems, etc. Showcasing this set of slides titled Security Threat Management Strategy With Strategies Ideas PDF. The topics addressed in these templates are Security Component, Examples Of Vulnerabilities, Security Mitigation Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
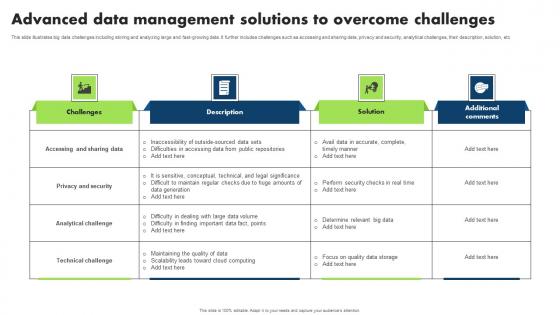
Advanced Data Management Solutions To Overcome Challenges Microsoft Pdf
This slide illustrates big data challenges including storing and analyzing large and fast growing data. It further includes challenges such as accessing and sharing data, privacy and security, analytical challenges, their description, solution, etc Pitch your topic with ease and precision using this Advanced Data Management Solutions To Overcome Challenges Microsoft Pdf. This layout presents information on Accessing Sharing Data, Privacy Security, Analytical Challenge. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates big data challenges including storing and analyzing large and fast growing data. It further includes challenges such as accessing and sharing data, privacy and security, analytical challenges, their description, solution, etc
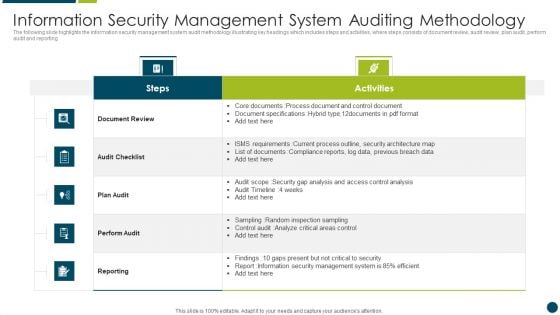
Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Data Encryption Security Management Technology Ideas PDF
This slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting Business Data Encryption Security Management Technology Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Authentication, Privacy, Regulatory Compliance, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IOT Technology Trends In Cybersecurity Management Inspiration Pdf
This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection. Pitch your topic with ease and precision using this IOT Technology Trends In Cybersecurity Management Inspiration Pdf This layout presents information on Cybersecurity Mesh, Security At Manufacturing, Network Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection.

Security Information And Event Management Services Mockup PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting security information and event management services mockup pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
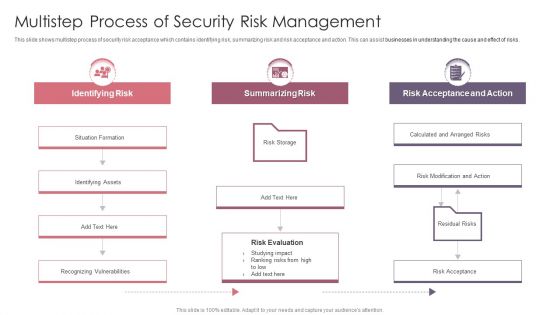
Multistep Process Of Security Risk Management Slides PDF
This slide shows multistep process of security risk acceptance which contains identifying risk, summarizing risk and risk acceptance and action. This can assist businesses in understanding the cause and effect of risks. Persuade your audience using this Multistep Process Of Security Risk Management Slides PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Identifying Risk, Summarizing Risk, Risk Acceptance And Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
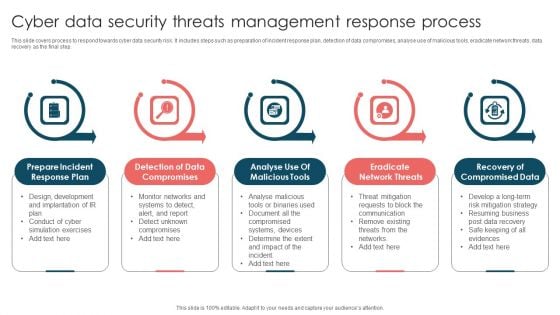
Cyber Data Security Threats Management Response Process Infographics PDF
This slide covers process to respond towards cyber data security risk. It includes steps such as preparation of incident response plan, detection of data compromises, analyse use of malicious tools, eradicate network threats, data recovery as the final step. Presenting Cyber Data Security Threats Management Response Process Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prepare Incident, Response Plan, Detection Data Compromises, Eradicate Network Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
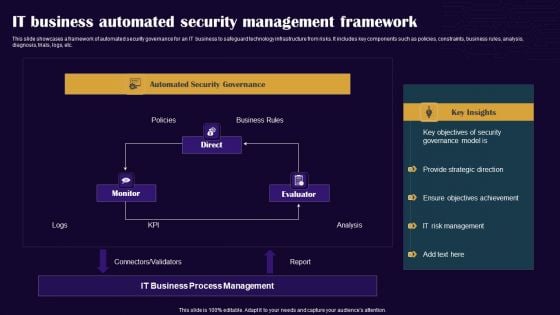
IT Business Automated Security Management Framework Professional PDF
This slide showcases a framework of automated security governance for an IT business to safeguard technology infrastructure from risks. It includes key components such as policies, constraints, business rules, analysis, diagnosis, trials, logs, etc. Showcasing this set of slides titled IT Business Automated Security Management Framework Professional PDF. The topics addressed in these templates are Monitor, Direct, Evaluator. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
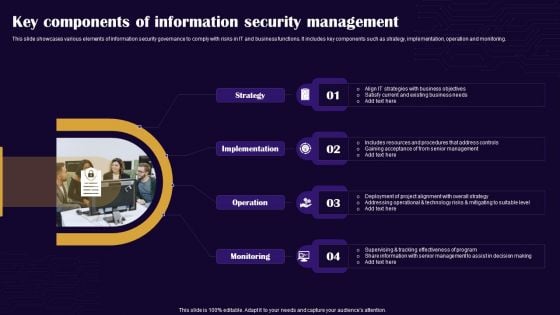
Key Components Of Information Security Management Graphics PDF
This slide showcases various elements of information security governance to comply with risks in IT and business functions. It includes key components such as strategy, implementation, operation and monitoring. Persuade your audience using this Key Components Of Information Security Management Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strategy, Implementation, Operation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
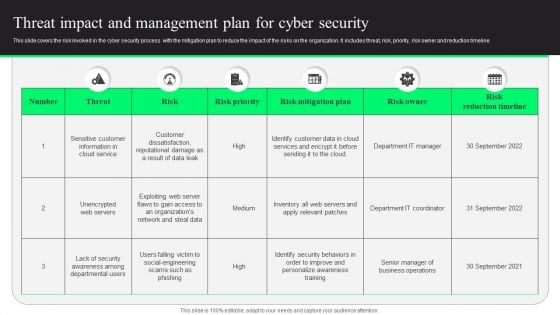
Threat Impact And Management Plan For Cyber Security Designs PDF
This slide covers the risk involved in the cyber security process with the mitigation plan to reduce the impact of the risks on the organization. It includes threat, risk, priority, risk owner and reduction timeline. Showcasing this set of slides titled Threat Impact And Management Plan For Cyber Security Designs PDF. The topics addressed in these templates are Risk Mitigation Plan, Risk Reduction Timeline, Customer Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Digital Banking Security Management Technology Trends Introduction PDF
The following slide provides the integration of security technology with banking which helps to provide improved and enhanced customer experience. Key components are login protection, artificial intelligence and cloud computing. Presenting Digital Banking Security Management Technology Trends Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Login Protection, Ai, Cloud Computing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
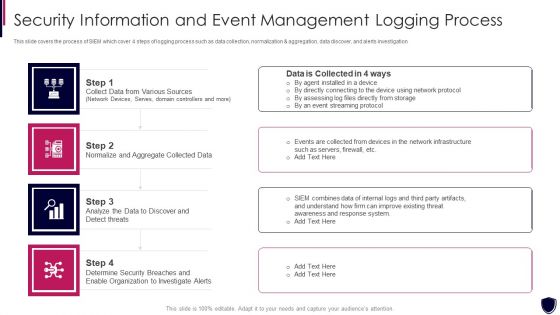
Security Information And Event Management Logging Process Diagrams PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collect data from various sources, normalize and aggregate collected data, organization to investigate alerts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
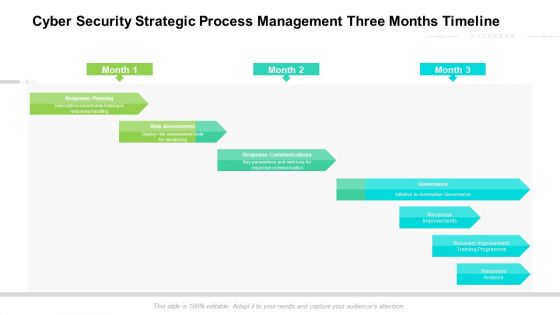
Cyber Security Strategic Process Management Three Months Timeline Introduction
Presenting the cyber security strategic process management three months timeline introduction. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
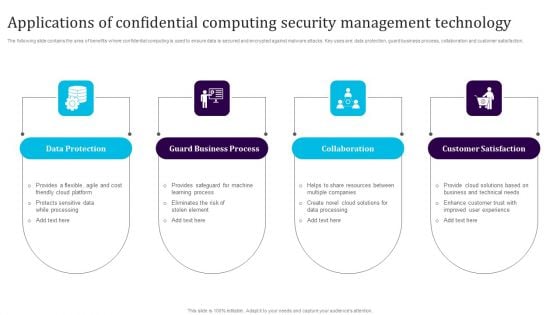
Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Systems Security And Risk Management Plan Roadmap Clipart PDF
Present like a pro with Information Systems Security And Risk Management Plan Roadmap Clipart PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
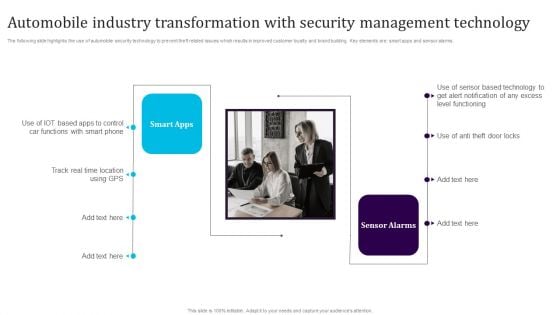
Automobile Industry Transformation With Security Management Technology Microsoft PDF
The following slide highlights the use of automobile security technology to prevent theft related issues which results in improved customer loyalty and brand building. Key elements are smart apps and sensor alarms. Presenting Automobile Industry Transformation With Security Management Technology Microsoft PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Smart Apps, Sensor Alarms. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Iot Smart Home Security Management Technology Demonstration PDF
This slide provides the use of smart security technology to get real time monitoring of home and obtain authenticity. Key features mentioned are smart cameras, biometric locks, smart cameras, connected switches and fire sensor. Persuade your audience using this Iot Smart Home Security Management Technology Demonstration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Smart Cameras, Biometric Locks, Smart Cameras, Connected Switches, Fire Sensor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
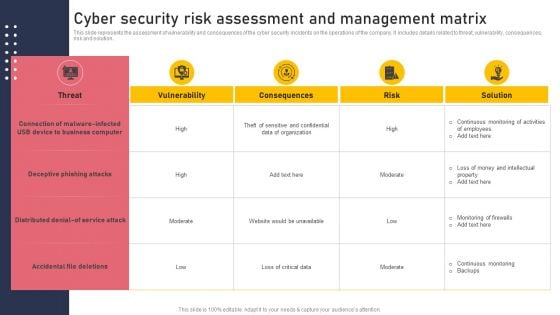
Cyber Security Risk Assessment And Management Matrix Inspiration PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Find a pre designed and impeccable Cyber Security Risk Assessment And Management Matrix Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
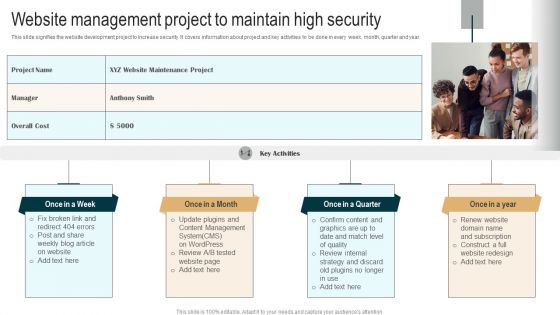
Website Management Project To Maintain High Security Demonstration PDF
This slide signifies the website development project to increase security. It covers information about project and key activities to be done in every week, month, quarter and year. Presenting Website Management Project To Maintain High Security Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fix broken link, Update plugins, Confirm content. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Desktop Security Management Prepare A Disaster Recovery Plan Demonstration PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a desktop security management prepare a disaster recovery plan demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, location, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
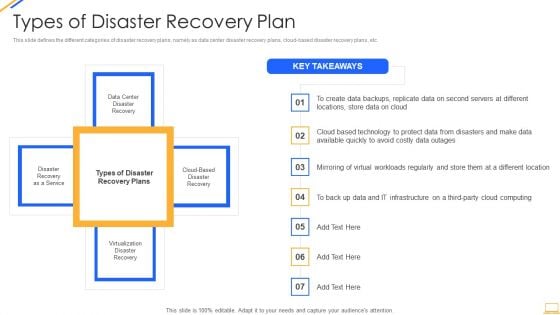
Desktop Security Management Types Of Disaster Recovery Plan Topics PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a desktop security management types of disaster recovery plan topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, locations, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
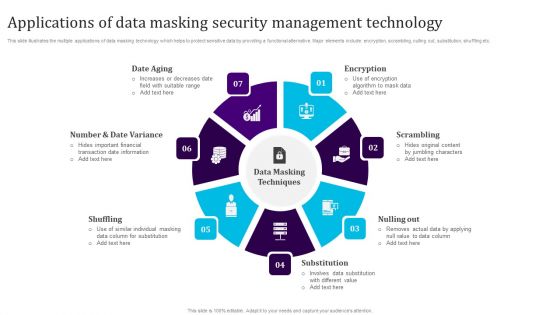
Applications Of Data Masking Security Management Technology Sample PDF
This slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Persuade your audience using this Applications Of Data Masking Security Management Technology Sample PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Date Aging, Shuffling, Substitution, Nulling Out, Scrambling, Encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Asset Identification For Information Security Risk Management Topics PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack This is a Asset Identification For Information Security Risk Management Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers Database, Products Database, Sales Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
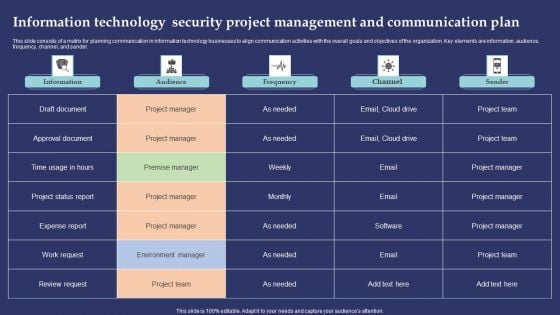
Information Technology Security Project Management And Communication Plan Designs PDF
This slide consists of a matrix for planning communication in information technology businesses to align communication activities with the overall goals and objectives of the organization. Key elements are information, audience, frequency, channel, and sender. Showcasing this set of slides titled Information Technology Security Project Management And Communication Plan Designs PDF. The topics addressed in these templates are Draft Document, Audience, Frequency. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
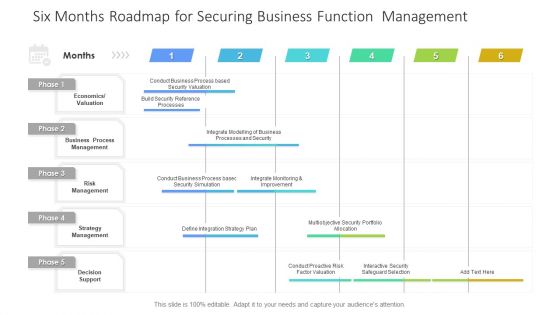
Six Months Roadmap For Securing Business Function Management Topics PDF
Presenting the six months roadmap for securing business function management topics pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
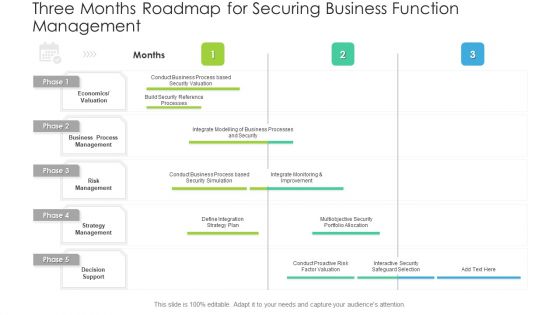
Three Months Roadmap For Securing Business Function Management Inspiration PDF
Presenting the three months roadmap for securing business function management inspiration pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
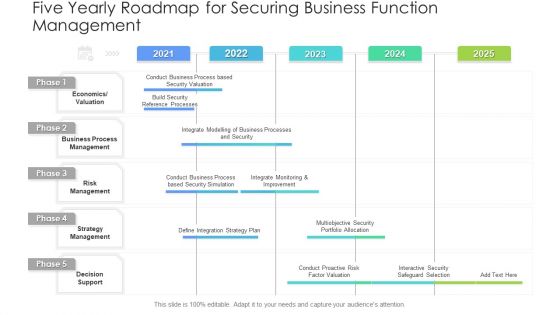
Five Yearly Roadmap For Securing Business Function Management Graphics PDF
Presenting the five yearly roadmap for securing business function management graphics pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
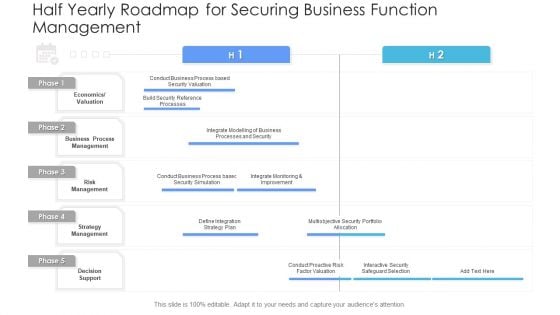
Half Yearly Roadmap For Securing Business Function Management Guidelines PDF
Presenting the half yearly roadmap for securing business function management guidelines pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
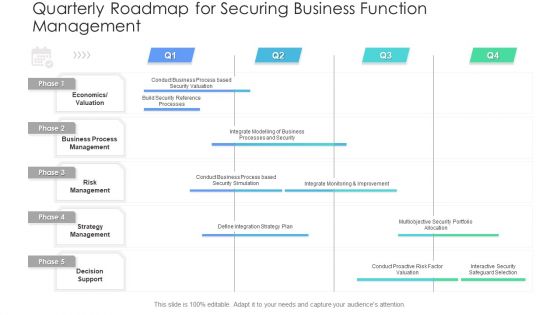
Quarterly Roadmap For Securing Business Function Management Clipart PDF
Presenting the quarterly roadmap for securing business function management clipart pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
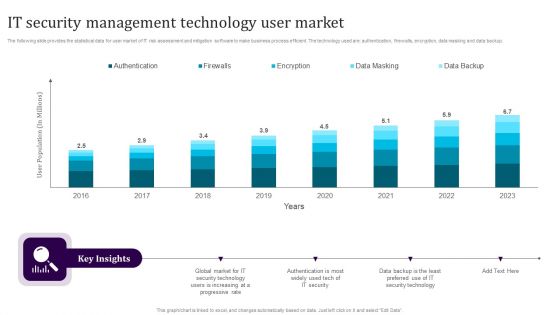
IT Security Management Technology User Market Guidelines PDF
The following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Showcasing this set of slides titled IT Security Management Technology User Market Guidelines PDF. The topics addressed in these templates are Authentication, Firewalls, Encryption, Data Masking, Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Information Systems Security And Risk Management Plan Timeline Professional PDF
Slidegeeks has constructed Information Systems Security And Risk Management Plan Timeline Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

User Authentication And Authorization Security Management Technology Summary PDF
This slide provides the use of multiple authentication and authorization technology which are used to protect systems and user information. Key categories are password based, multi factor, certificate based, biometrics and token based. Persuade your audience using this User Authentication And Authorization Security Management Technology Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Based, Multi Factor, Certificate Based, Biometrics, Token Based. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
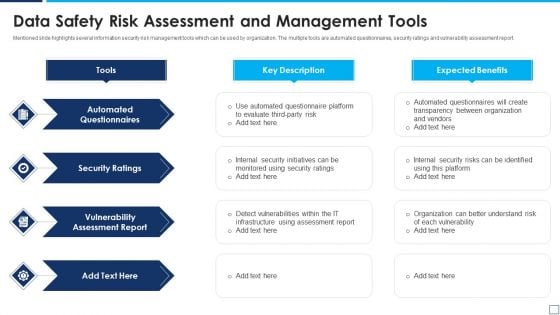
Data Safety Risk Assessment And Management Tools Demonstration PDF
Mentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Presenting data safety risk assessment and management tools demonstration pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including automated questionnaires, security ratings, vulnerability assessment report. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF
The following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Presenting Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Asset Inventory, Synchronization, Response, Security Gaps. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

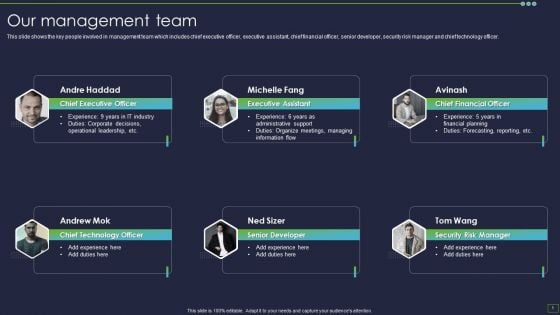
Information Technology Solutions Business Profile Our Management Team Introduction PDF
This slide shows the key people involved in management team which includes chief executive officer, executive assistant, chief financial officer, senior developer, security risk manager and chief technology officer.Presenting Information Technology Solutions Business Profile Our Management Team Introduction PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Executive Officer, Executive Assistant, Financial Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
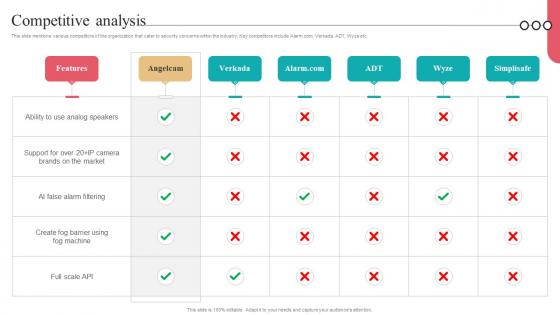
Competitive Analysis Camera Management Platform Investor Funding Elevator Pitch Deck
This slide mentions various competitors of the organization that cater to security concerns within the industry. Key competitors include Alarm.com, Verkada, ADT, Wyze etc. Want to ace your presentation in front of a live audience Our Competitive Analysis Camera Management Platform Investor Funding Elevator Pitch Deck can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide mentions various competitors of the organization that cater to security concerns within the industry. Key competitors include Alarm.com, Verkada, ADT, Wyze etc.
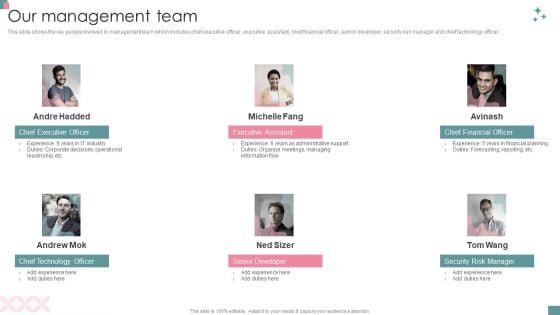
IT Consultancy Services Company Profile Our Management Team Topics PDF
This slide shows the key people involved in management team which includes chief executive officer, executive assistant, chief financial officer, senior developer, security risk manager and chief technology officer.Presenting IT Consultancy Services Company Profile Our Management Team Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Operational Leadership, Corporate Decisions, Organize Meetings. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Small Business Venture Company Profile Our Management Team Formats PDF
This slide shows the key people involved in management team which includes chief executive officer, executive assistant, chief financial officer, senior developer, security risk manager and chief technology officer.Presenting Small Business Venture Company Profile Our Management Team Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Chief Executive, Executive Assistant, Chief Financial. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Facts Data Management Company Investor Funding Pitch Deck
The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of rightsizing savings, reverted deploys, effective cost per resource, production incidents by application or team and number of security lapses. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Key Facts Data Management Company Investor Funding Pitch Deck and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of rightsizing savings, reverted deploys, effective cost per resource, production incidents by application or team and number of security lapses.
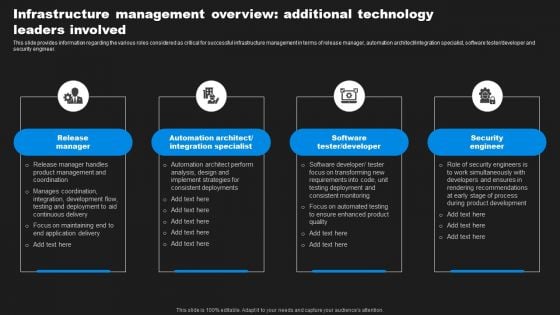
Enhancing Information Technology With Strategic Infrastructure Management Technology Guidelines PDF
This slide provides information regarding the various roles considered as critical for successful infrastructure management in terms of release manager, automation architect integration specialist, software tester developer and security engineer. Make sure to capture your audiences attention in your business displays with our gratis customizable Enhancing Information Technology With Strategic Infrastructure Management Technology Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
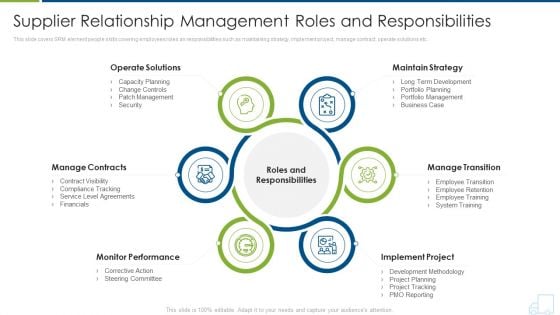
Distributor Strategy Supplier Relationship Management Roles And Responsibilities Structure PDF
This slide covers SRM element people skills covering employees roles an responsibilities such as maintaining strategy, implement project, manage contract, operate solutions etc. Presenting distributor strategy supplier relationship management roles and responsibilities structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like management, security, service, financials, performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
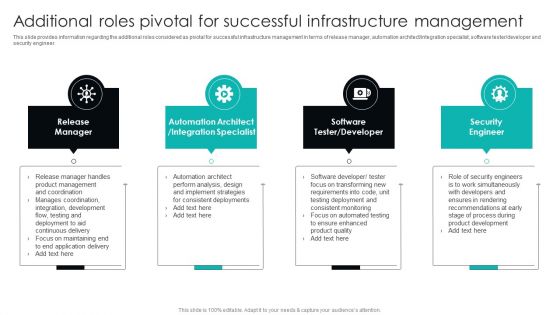
Additional Roles Pivotal For Successful Infrastructure Management Summary PDF
This slide provides information regarding the additional roles considered as pivotal for successful infrastructure management in terms of release manager, automation architect integration specialist, software tester developer and security engineer. Find a pre designed and impeccable Additional Roles Pivotal For Successful Infrastructure Management Summary PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Resolving Virtual Virtual Team Management Challenges Rules PDF
Following slide demonstrates ways to manage remote team challenges which organizations employ to eliminate potential threats and enhance productivity. This slide provides data regarding challenges, description, solutions and overall impact. Pitch your topic with ease and precision using this Resolving Virtual Virtual Team Management Challenges Rules PDF. This layout presents information on Communication, Project Collaborations, Performance Management, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Additional Roles Pivotal For Successful Infrastructure Management Pictures PDF
This slide provides information regarding the additional roles considered as pivotal for successful infrastructure management in terms of release manager, automation architect or integration specialist, software tester or developer and security engineer.This is a Additional Roles Pivotal For Successful Infrastructure Management Pictures PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automation Architect, Integration Specialist, Software Tester. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
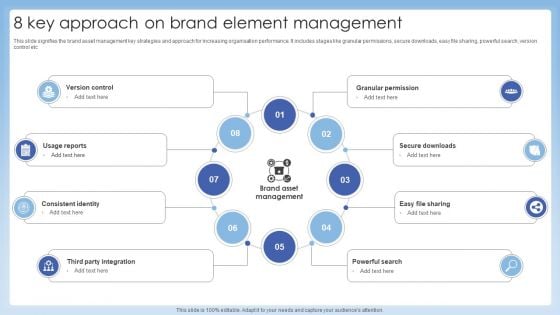
8 Key Approach On Brand Element Management Rules PDF
This slide signifies the brand asset management key strategies and approach for increasing organisation performance. It includes stages like granular permissions, secure downloads, easy file sharing, powerful search, version control etc. Presenting 8 Key Approach On Brand Element Management Rules PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Version Control, Granular Permission, Secure Downloads. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
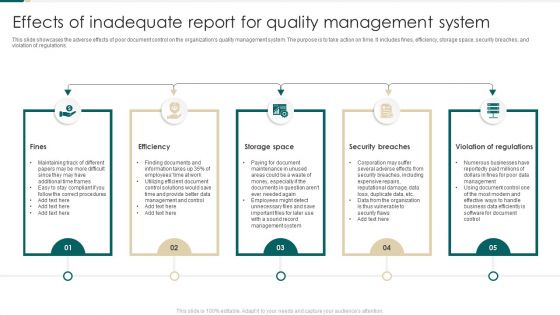
Effects Of Inadequate Report For Quality Management System Clipart PDF
This slide showcases the adverse effects of poor document control on the organizations quality management system. The purpose is to take action on time. It includes fines, efficiency, storage space, security breaches, and violation of regulations. Persuade your audience using this Effects Of Inadequate Report For Quality Management System Clipart PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Storage Space, Security Breaches, Violation Of Regulations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
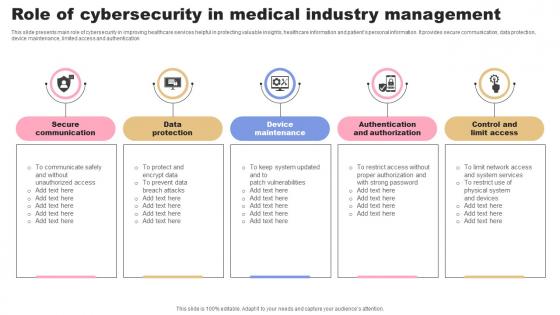
Role Of Cybersecurity In Medical Industry Management Rules Pdf
This slide presents main role of cybersecurity in improving healthcare services helpful in protecting valuable insights, healthcare information and patients personal information. It provides secure communication, data protection, device maintenance, limited access and authentication Pitch your topic with ease and precision using this Role Of Cybersecurity In Medical Industry Management Rules Pdf. This layout presents information on Secure Communication, Data Protection, Maintenance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents main role of cybersecurity in improving healthcare services helpful in protecting valuable insights, healthcare information and patients personal information. It provides secure communication, data protection, device maintenance, limited access and authentication


 Continue with Email
Continue with Email

 Home
Home


































