Computer Security
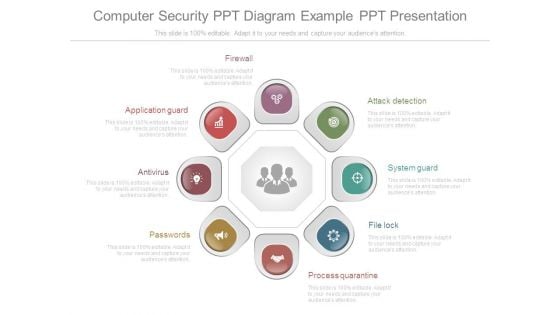
Computer Security Ppt Diagram Example Ppt Presentation
This is a computer security ppt diagram example ppt presentation. This is a eight stage process. The stages in this process are application guard, antivirus, passwords, firewall, attack detection, system guard, file lock, process quarantine.
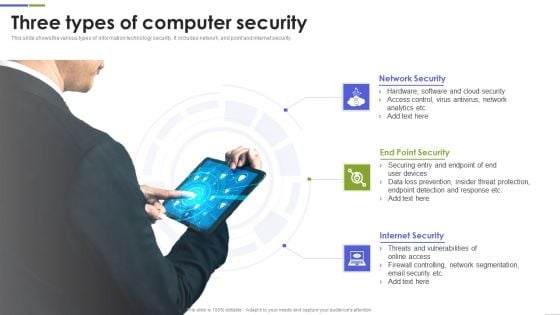
Three Types Of Computer Security Designs PDF
This slide shows the various types of information technology security. It includes network, end point and internet security. Presenting Three Types Of Computer Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Network Security, Point Security, Internet Security This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
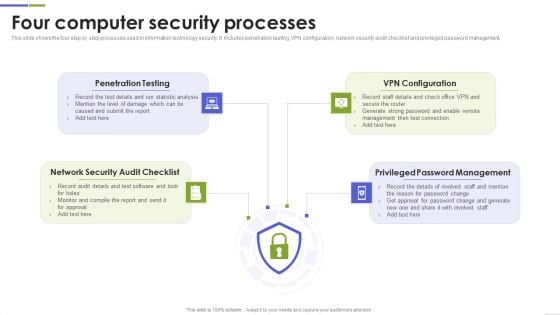
Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
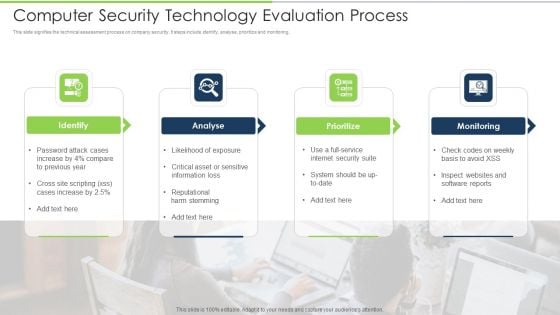
Computer Security Technology Evaluation Process Download PDF
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Security Ppt PowerPoint Presentation Complete Deck
Improve your presentation delivery using this Computer Security Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
Cloud Computing Security Architecture Icon Slides PDF
Presenting Cloud Computing Security Architecture Icon Slides PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
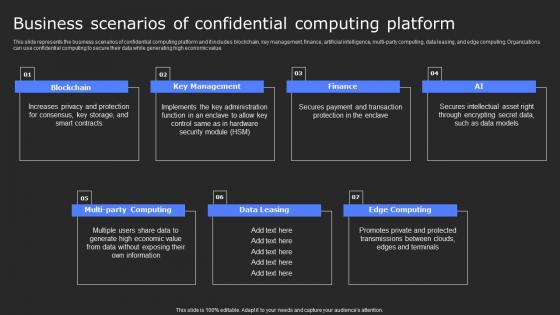
Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
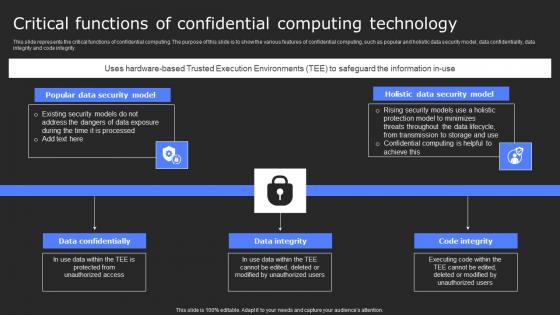
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
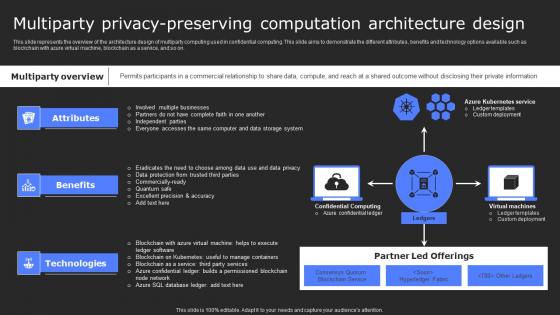
Multiparty Privacy Preserving Computation Secure Computing Framework Topics Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with azure virtual machine, blockchain as a service, and so on. Want to ace your presentation in front of a live audience Our Multiparty Privacy Preserving Computation Secure Computing Framework Topics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with azure virtual machine, blockchain as a service, and so on.

Serverless Computing Security Role Serverless Computing Modern Technology Ideas Pdf
The purpose of this slide is to outline the security challenges and risks of serverless computing. These problems are vulnerable configuration, permissions for too powerful functions, infusion of event data, insufficient function recording and monitoring, etc. This modern and well arranged Serverless Computing Security Role Serverless Computing Modern Technology Ideas Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The purpose of this slide is to outline the security challenges and risks of serverless computing. These problems are vulnerable configuration, permissions for too powerful functions, infusion of event data, insufficient function recording and monitoring, etc.
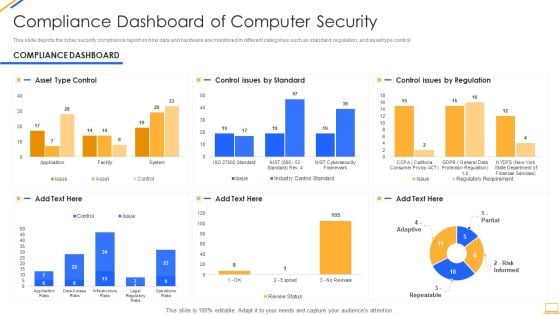
Desktop Security Management Compliance Dashboard Of Computer Security Graphics PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative desktop security management compliance dashboard of computer security graphics pdf bundle. Topics like compliance dashboard of computer security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Roadmap For Computer Security Training Graphics PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting desktop security management roadmap for computer security training graphics pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Key Elements Of Computer Security Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a desktop security management key elements of computer security download pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, information security, application security, network security, cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Complete Computer Security Implementation Checklist Demonstration PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting desktop security management complete computer security implementation checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, organizations, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Latest Threats In Computer Security Inspiration PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting desktop security management latest threats in computer security inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financial, information, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Computer Security PowerPoint Templates And PowerPoint Themes 1012
Computer Security PowerPoint Templates And PowerPoint Themes 1012-With the move to high speed internet connection comes the greater possibility of your business being the target of an attack. One use of the term computer security refers to technology to implement a secure operating system. The Above Template will help you and your partners to understand the importance of Computer Security. Deliver amazing presentations to mesmerize your audience with our Security Template.-Computer Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Protect your computer, security, communication, computer, technology, background Bolster the excitement with our Computer Security PowerPoint Templates And PowerPoint Themes 1012. They will not let the enthusiasm fade.

Computer Security Ppt PowerPoint Presentation Complete Deck With Slides
This is a computer security ppt powerpoint presentation complete deck with slides. This is a one stage process. The stages in this process are computer security, business, planning, strategy, marketing.
Computer Security Vector Icon Ppt PowerPoint Presentation File Outline PDF
Presenting this set of slides with name computer security vector icon ppt powerpoint presentation file outline pdf. This is a three stage process. The stages in this process are computer security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Thank You Computer Security Ppt PowerPoint Presentation Outline Guidelines
This is a thank you computer security ppt powerpoint presentation outline guidelines. This is a one stage process. The stages in this process are thank you.

Computer Security Business Ppt PowerPoint Presentation Layouts Background Cpb
Presenting this set of slides with name computer security business ppt powerpoint presentation layouts background cpb. This is an editable Powerpoint five stages graphic that deals with topics like computer security business to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Computer Security Ppt PowerPoint Presentation Layouts Format Ideas Cpb
Presenting this set of slides with name computer security ppt powerpoint presentation layouts format ideas cpb. This is an editable Powerpoint three stages graphic that deals with topics like computer security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Computer Security Plan Ppt PowerPoint Presentation Visual Aids Show Cpb
Presenting this set of slides with name computer security plan ppt powerpoint presentation visual aids show cpb. This is an editable Powerpoint four stages graphic that deals with topics like computer security plan to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Types Computer Security Ppt PowerPoint Presentation File Templates Cpb
Presenting this set of slides with name types computer security ppt powerpoint presentation file templates cpb. This is an editable Powerpoint four stages graphic that deals with topics like types computer security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Business Computer Security Ppt PowerPoint Presentation Slide Cpb
Presenting this set of slides with name business computer security ppt powerpoint presentation slide cpb. This is an editable Powerpoint five stages graphic that deals with topics like business computer security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Computer Security Attack Ppt PowerPoint Presentation File Templates Cpb Pdf
Presenting this set of slides with name computer security attack ppt powerpoint presentation file templates cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like computer security attack to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Computer Security Incident Handling Optimizing Cybersecurity Framework Roadmap Designs PDF
Presenting this set of slides with name computer security incident handling optimizing cybersecurity framework roadmap designs pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
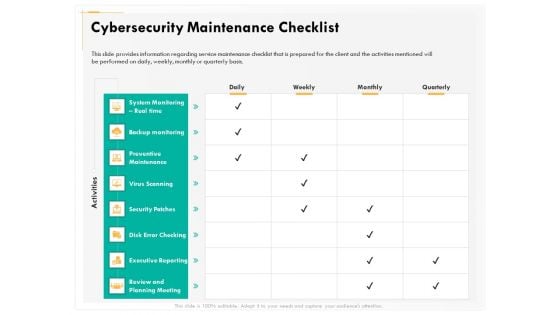
Computer Security Incident Handling Cybersecurity Maintenance Checklist Background PDF
Presenting this set of slides with name computer security incident handling cybersecurity maintenance checklist background pdf. The topics discussed in these slides are system monitoring real time, backup monitoring, preventive maintenance, virus scanning, security patches, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
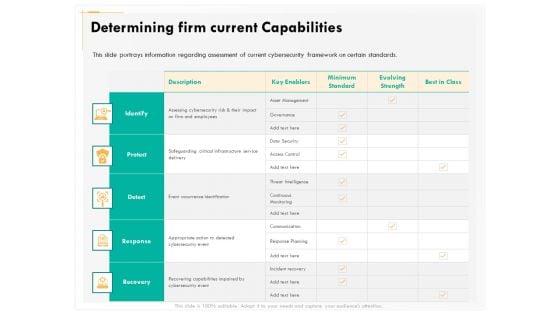
Computer Security Incident Handling Determining Firm Current Capabilities Inspiration PDF
Presenting this set of slides with name computer security incident handling determining firm current capabilities inspiration pdf. The topics discussed in these slides are identify, protect, detect, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Management Action Plan Graphics PDF
Presenting this set of slides with name computer security incident handling cybersecurity management action plan graphics pdf. The topics discussed in these slides are risk identification, risk treatment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Risk Management Worksheet Ideas PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management worksheet ideas pdf. The topics discussed in these slides are identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
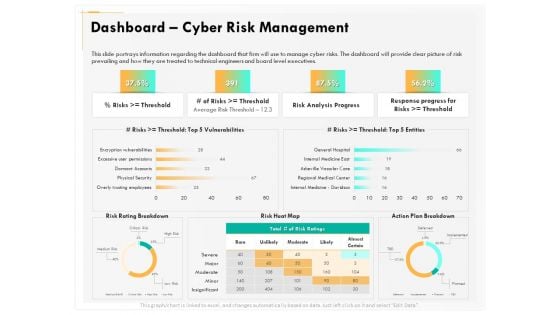
Computer Security Incident Handling Dashboard Cyber Risk Management Download PDF
Presenting this set of slides with name computer security incident handling dashboard cyber risk management download pdf. The topics discussed in these slides are risk rating breakdown, risk heat map, action plan breakdown, risk analysis progress, response progress for risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
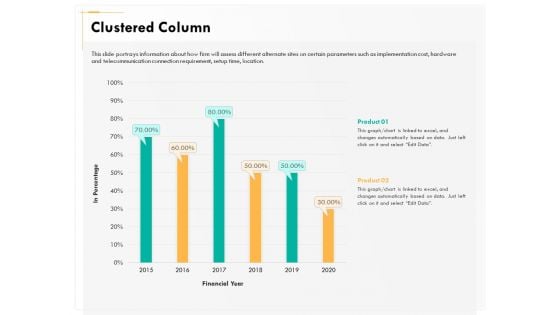
Computer Security Incident Handling Clustered Column Ppt Show Styles PDF
Presenting this set of slides with name computer security incident handling clustered column ppt show styles pdf. The topics discussed in these slides are product 1, product 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
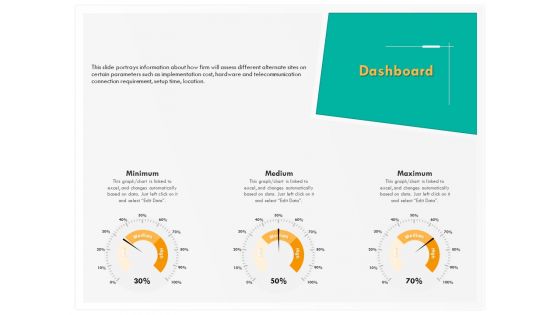
Computer Security Incident Handling Dashboard Ppt Model Introduction PDF
Presenting this set of slides with name computer security incident handling dashboard ppt model introduction pdf. This is a three stage process. The stages in this process are minimum, medium, maximum. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Financial Ppt Portfolio Pictures PDF
Presenting this set of slides with name computer security incident handling financial ppt portfolio pictures pdf. This is a three stage process. The stages in this process are revenue, deposits, net income. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Our Mission Ppt Styles Slides PDF
Presenting this set of slides with name computer security incident handling our mission ppt styles slides pdf. This is a three stage process. The stages in this process are vision, mission, goal. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Computer Security Incident Handling Our Team Ppt Model Files PDF
Presenting this set of slides with name computer security incident handling our team ppt model files pdf. This is a four stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Computer Security Incident Handling Thank You Ppt Summary Designs PDF
Presenting this set of slides with name computer security incident handling thank you ppt summary designs pdf. This is a one stage process. The stages in this process are thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Essential Contingency Plan Strategies Ideas PDF
Presenting this set of slides with name computer security incident handling essential contingency plan strategies ideas pdf. The topics discussed in these slides are contingency considerations, contingency solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Present Concerns Impeding Cybersecurity Formats PDF
Presenting this set of slides with name computer security incident handling present concerns impeding cybersecurity formats pdf. The topics discussed in these slides are reported financial losses due to increase in cybercrimes, data branches and records exposed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Recovery Task List Maintenance Background PDF
Presenting this set of slides with name computer security incident handling recovery task list maintenance background pdf. The topics discussed in these slides are task no., task description, estimated time, actual time, assigned to, comments. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Timeframe For Incident Management Infographics PDF
Presenting this set of slides with name computer security incident handling timeframe for incident management infographics pdf. The topics discussed in these slides are incident logging, ticket creation, incident categorization, incident prioritization, incident resolution, incident closure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Computer Security Incident Handling Vital Records Maintenance Register Icons PDF
Presenting this set of slides with name computer security incident handling vital records maintenance register icons pdf. The topics discussed in these slides are primary location of records, alternate location of records, other sources to obtain records. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
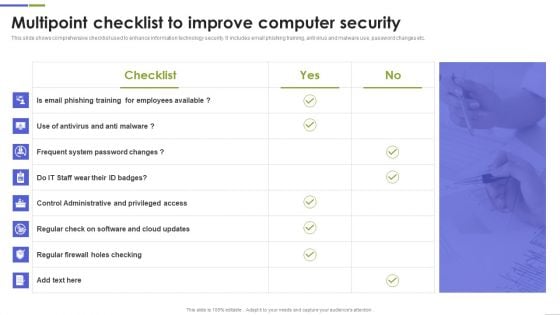
Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
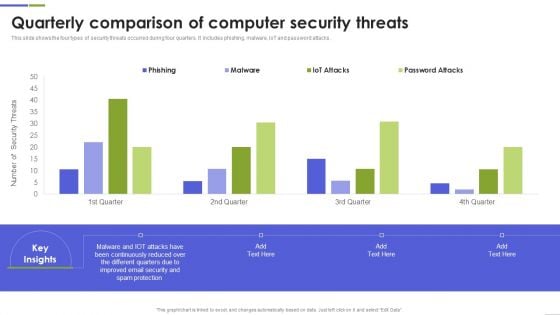
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Security Incident Handling Agenda For Cybersecurity Management Slides PDF
Presenting this set of slides with name computer security incident handling agenda for cybersecurity management slides pdf. The topics discussed in these slides are determining roles and responsibilities of senior management and executives who are responsible in risk management, presenting optimize cybersecurity risk framework to senior management and executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Various Kpis To Measure Computer Security System Portrait PDF
This slide shows the different KPIs used to measure IT security system. These are level of preparedness, intrusion attempts, days to patch, incidents reported etc. Persuade your audience using this Various Kpis To Measure Computer Security System Portrait PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Performance Indicators, Excepted Results, Actual Results Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
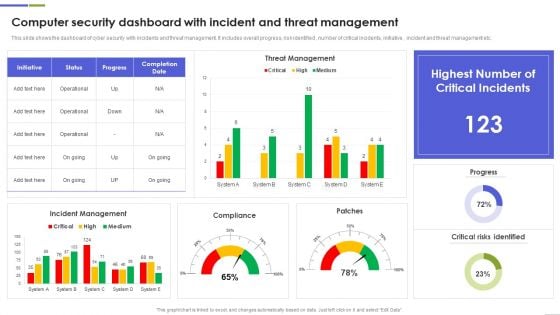
Computer Security Dashboard With Incident And Threat Management Rules PDF
This slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc.Showcasing this set of slides titled Computer Security Dashboard With Incident And Threat Management Rules PDF The topics addressed in these templates are Critical Incidents, Risks Identified, Compliance All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
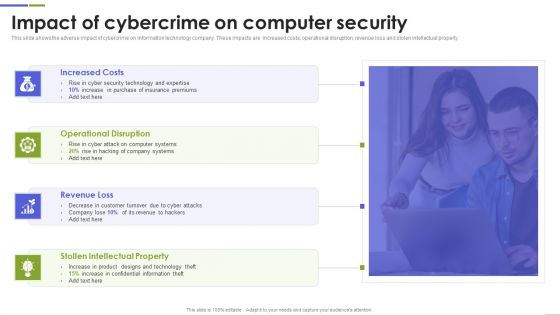
Impact Of Cybercrime On Computer Security Formats PDF
This slide shows the adverse impact of cybercrime on information technology company. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Persuade your audience using this Impact Of Cybercrime On Computer Security Formats PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Increased Costs, Operational Disruption, Revenue Loss Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
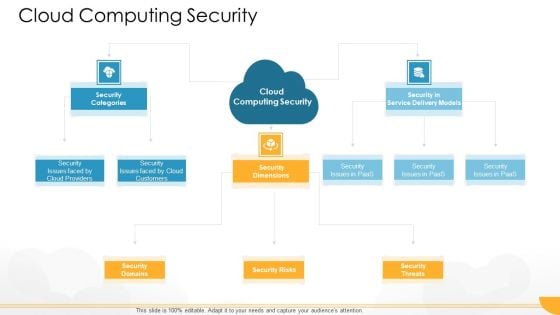
Technology Guide For Serverless Computing Cloud Computing Security Designs PDF
Presenting technology guide for serverless computing cloud computing security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security categories, security domains, security risks, security threats, security dimensions. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
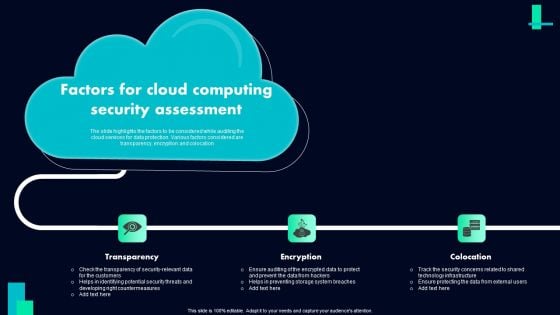
Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF
Presenting Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Factors For, Cloud Computing, Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Computing Security Management Ppt PowerPoint Presentation Outline Icons Cpb
Presenting this set of slides with name cloud computing security management ppt powerpoint presentation outline icons cpb. This is an editable Powerpoint four stages graphic that deals with topics like cloud computing security management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
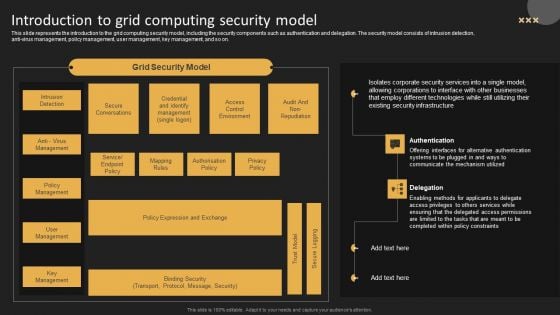
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
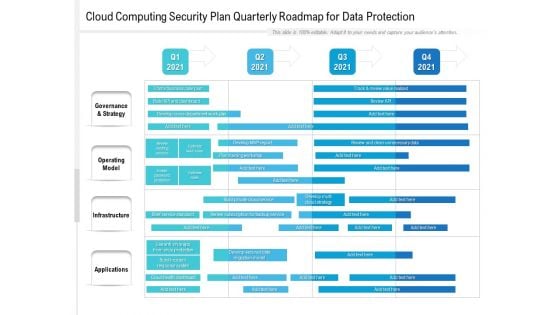
Cloud Computing Security Plan Quarterly Roadmap For Data Protection Brochure
We present our cloud computing security plan quarterly roadmap for data protection brochure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security plan quarterly roadmap for data protection brochure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cloud Computing Security Five Years Roadmap With Deployment Plan Designs
We present our cloud computing security five years roadmap with deployment plan designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security five years roadmap with deployment plan designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
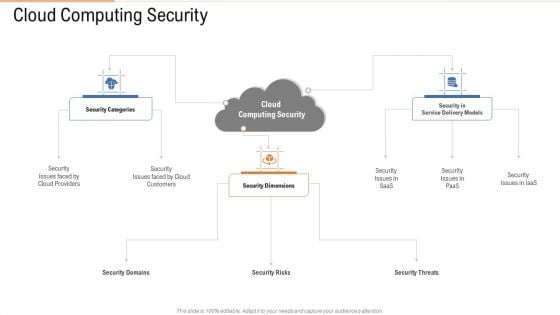
Cloud Computing Security Ppt Portfolio Background Images PDF
Presenting cloud computing security ppt portfolio background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security dimensions, customers, security categories. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Computing Security IT Icons Slide Ppt Inspiration Guidelines PDF
Introducing our well designed cloud computing security it icons slide ppt inspiration guidelines pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
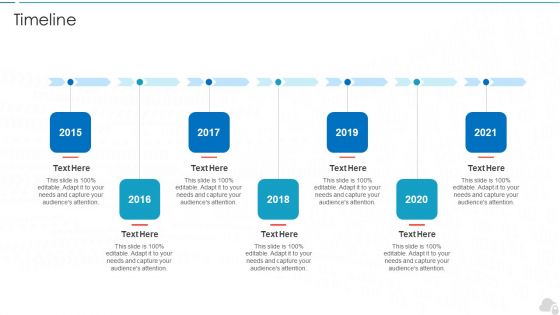
Timeline Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
Presenting timeline cloud computing security it ppt layouts slide portrait pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like timeline, 2015 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
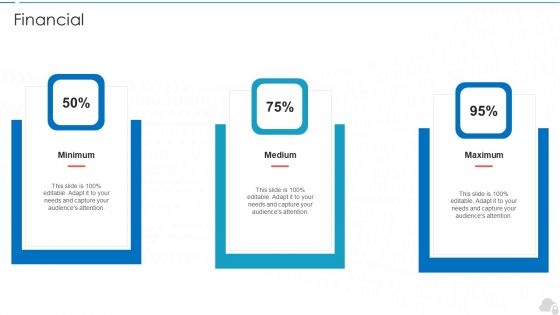
Financial Cloud Computing Security IT Ppt Slides Grid PDF
This is a financial cloud computing security it ppt slides grid pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimum, medium, maximum. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































