Computer Virus
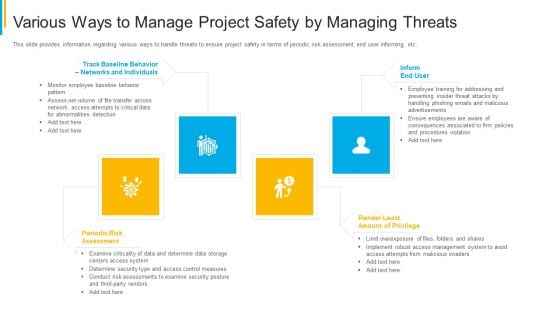
Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Project Security Administration IT Addressing Frequent Communication For Project Quality Management Icons PDF
This slide provides information regarding meetings that held in order to keep consistent quality entire project. These meetings are held on quarterly, annual basis. Presenting project security administration it addressing frequent communication for project quality management icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like executive, leaders, coordinators, initiation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Addressing Various Threats Affecting IT Project Safety Designs PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Presenting project security administration it addressing various threats affecting it project safety designs pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like general it threats, criminal it threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
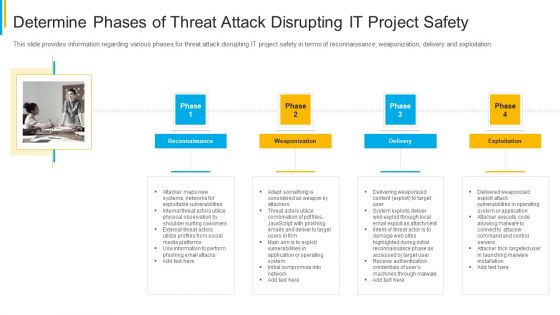
Project Security Administration IT Determine Phases Of Threat Attack Disrupting IT Project Safety Brochure PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. This is a project security administration it determine phases of threat attack disrupting it project safety brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Icons PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Presenting project security administration it determine phases of threat attack disrupting project safety contd icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Determine Staff Training Schedule For Skills Enhancement Formats PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting project security administration it determine staff training schedule for skills enhancement formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like determine staff training schedule for skills enhancement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
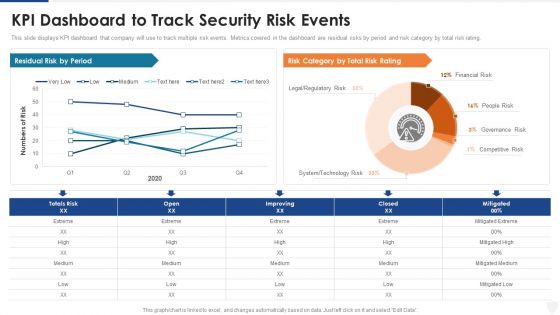
KPI Dashboard To Track Security Risk Events Ppt Pictures Deck PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this kpi dashboard to track security risk events ppt pictures deck pdf. Use them to share invaluable insights on technology risk, system, financial risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
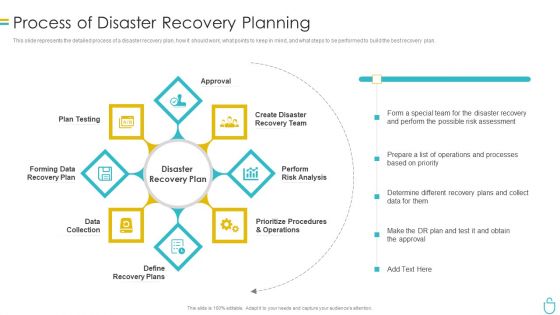
Information Security Process Of Disaster Recovery Planning Ppt Portfolio Backgrounds PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information security process of disaster recovery planning ppt portfolio backgrounds pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like recovery team, risk analysis, prioritize procedures, recovery plan, data collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
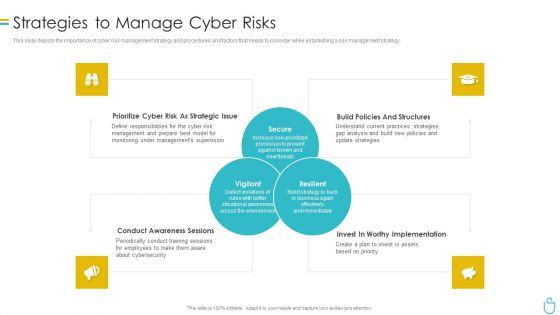
Information Security Strategies To Manage Cyber Risks Ppt Layouts Gridlines PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information security strategies to manage cyber risks ppt layouts gridlines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk, management, strategies, analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Types Of Disaster Recovery Plan Ppt Ideas Example PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud based disaster recovery plans, etc. Presenting information security types of disaster recovery plan ppt ideas example pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like locations, technology, infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information security define access control measures for employees ppt icon pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Dispose Data And Equipment Properly Ppt Infographics Styles PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting information security dispose data and equipment properly ppt infographics styles pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Minimize Administrative And Staff Privileges Ppt Slides Pictures PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. This is a information security minimize administrative and staff privileges ppt slides pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimize administrative and staff privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
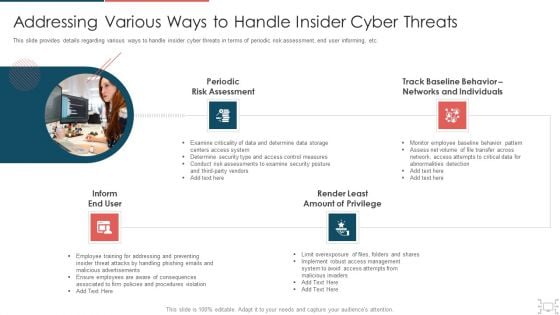
Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Various Types Of Workplace Violence And Threats Inspiration PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber security administration in organization various types of workplace violence and threats inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical, threatening, behavior, stalking, harassment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Workplace Employee Assistance Program Professional PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting cyber security administration in organization workplace employee assistance program professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical, services, employer, management, consultations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Workplace Incident Summary Report Brochure PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a cyber security administration in organization workplace incident summary report brochure pdf template with various stages. Focus and dispense information on eigt stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident, employees, location, emergency, assistance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
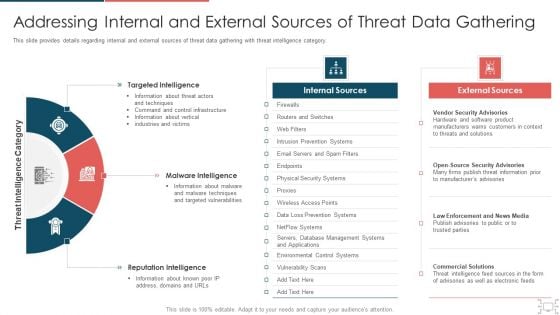
cyber security administration in organization addressing internal and external sources of gathering structure pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a cyber security administration in organization addressing internal and external sources of gathering structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, sources, internal, intelligence, reputation . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
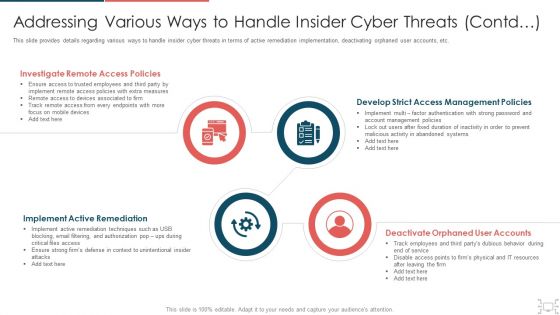
cyber security administration in organization addressing various ways to handle insider cyber active template pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting cyber security administration in organization addressing various ways to handle insider cyber active template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like investigate, access, policies, remediation, implement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
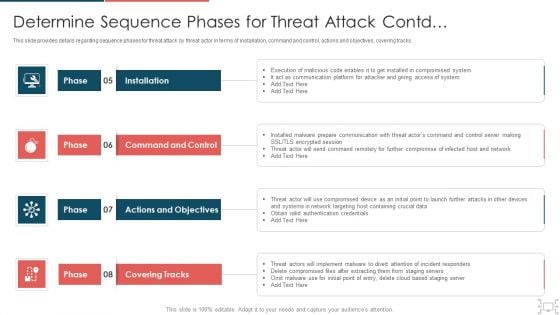
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
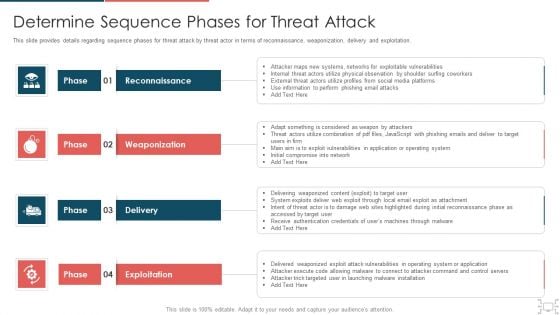
cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
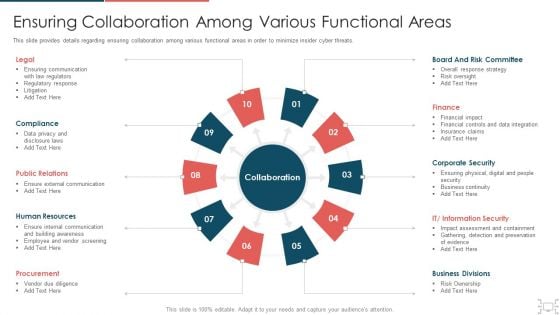
cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
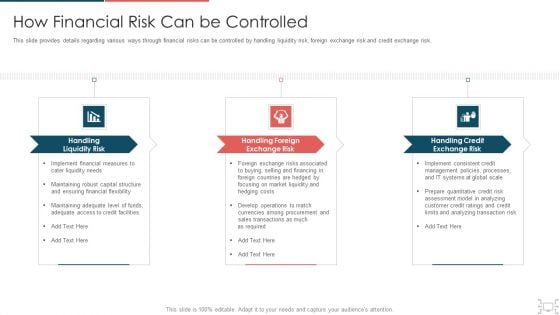
cyber security administration in organization how financial risk can be controlled inspiration pdf
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. This is a cyber security administration in organization how financial risk can be controlled inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like handling, liquidity, financial, flexibility, structure . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
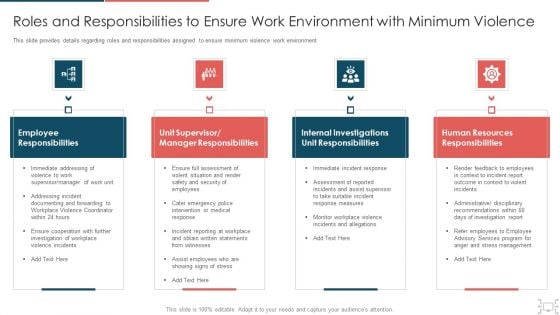
cyber security administration in organization roles and responsibilities to ensure work environment slides pdf
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a cyber security administration in organization roles and responsibilities to ensure work environment slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsibilities, manager, assessment, manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

cyber security administration in organization threat management action plan introduction pdf
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber security administration in organization threat management action plan introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like responsibilities, manager, assessment, manager . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
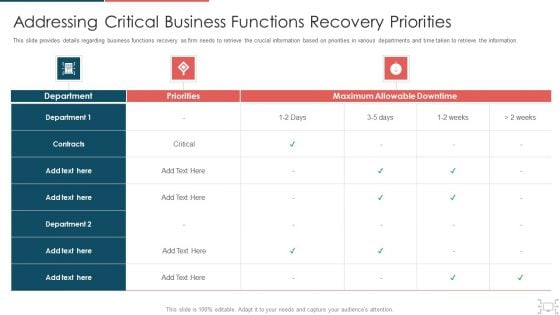
Cyber Security Administration In Organization Addressing Critical Business Functions Recovery Download PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing critical business functions recovery download pdf. Use them to share invaluable insights on addressing critical business functions recovery priorities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
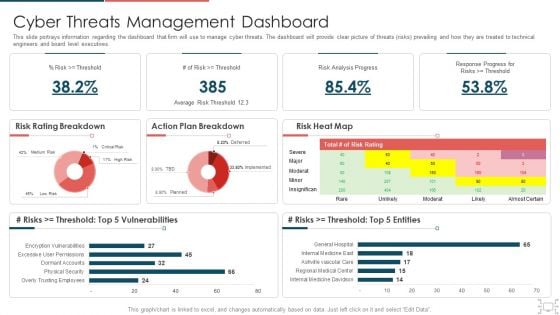
Cyber Security Administration In Organization Cyber Threats Management Dashboard Formats PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an awe inspiring pitch with this creative cyber security administration in organization cyber threats management dashboard formats pdf bundle. Topics like cyber threats management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Determine Several Threat Actors Profile Sample PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization determine several threat actors profile sample pdf. Use them to share invaluable insights on determine several threat actors profile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
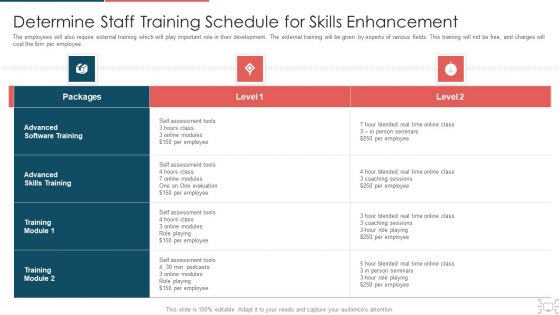
Cyber Security Administration In Organization Determine Staff Training Schedule For Skills Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine staff training schedule for skills diagrams pdf bundle. Topics like determine staff training schedule for skills enhancement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
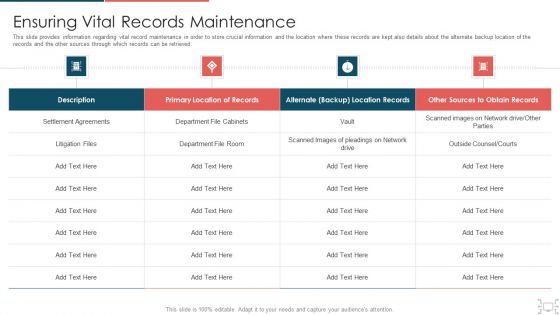
Cyber Security Administration In Organization Ensuring Vital Records Maintenance Topics PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization ensuring vital records maintenance topics pdf. Use them to share invaluable insights on ensuring vital records maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
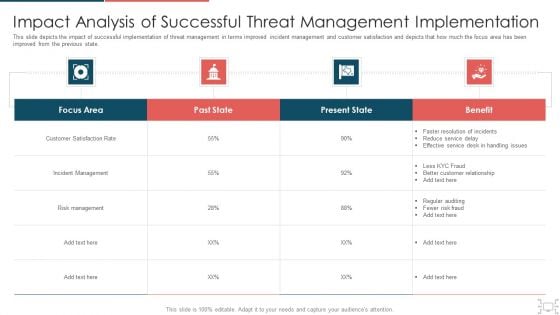
Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
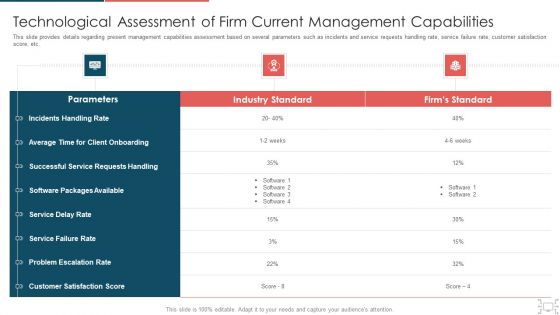
Cyber Security Administration In Organization Technological Assessment Of Firm Current Management Elements PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization technological assessment of firm current management elements pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Threat Management Action Plan Level Information PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative cyber security administration in organization threat management action plan level information pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Global Cyber Terrorism Incidents On The Rise IT Roadmap To Implement Cyber Security Icons PDF
This slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. This is a global cyber terrorism incidents on the rise it roadmap to implement cyber security icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like keep the hardware and software updated, awareness training for employees, creating personal accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cybersecurity Types Of Latest Threats In Electronic Information Security Ppt Portfolio Icon PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a cybersecurity types of latest threats in electronic information security ppt portfolio icon pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Desktop Security Management Define Access Control Measures For Employees Icons PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a desktop security management define access control measures for employees icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
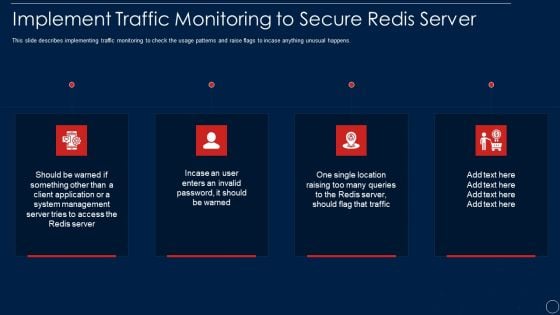
Redis Cache Data Structure IT Implement Traffic Monitoring To Secure Redis Server Ideas PDF
This slide describes implementing traffic monitoring to check the usage patterns and raise flags to incase anything unusual happens. Presenting redis cache data structure it implement traffic monitoring to secure redis server ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management, system, location. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Secured Video Hosting Platform Investor Capital Funding Pitch Deck Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This secured video hosting platform investor capital funding pitch deck ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of thirty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
Secured Video Hosting Platform Investor Capital Funding Addressing Purpose Defining Brand And Culture Graphics PDF
This slide caters details about purpose that act as a driving force in enabling firm in defining its brand and culture and it caters details about the three mantras that reflect its purpose in market. Presenting secured video hosting platform investor capital funding addressing purpose defining brand and culture graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like upload content, browse content, share content. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Secured Video Hosting Platform Investor Capital Funding Addressing Various Problems Limiting User Experience Topics PDF
This slide caters details about several problems that existing in market which are faced by prospects. These pain points are harnessing overall user experience due to large video size, no standardization, etc. This is a secured video hosting platform investor capital funding addressing various problems limiting user experience topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like addressing various problems limiting user experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Secured Video Hosting Platform Investor Capital Funding Determine Video Hosting Platform Product Development Process Portrait PDF
This slide caters details about present state of product, features existing in pipeline and future scenario for product scaling. Presenting secured video hosting platform investor capital funding determine video hosting platform product development process portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like community, architecture, determine features presently in development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Secured Video Hosting Platform Investor Capital Funding Future Initiatives By Online Video Hosting Platform Sample PDF
This slide caters details about future initiatives by online video hosting platform that will focus on leveraging relationships with members or clients or subscribers across globe. This is a secured video hosting platform investor capital funding future initiatives by online video hosting platform sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like future initiatives by online video hosting platform. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
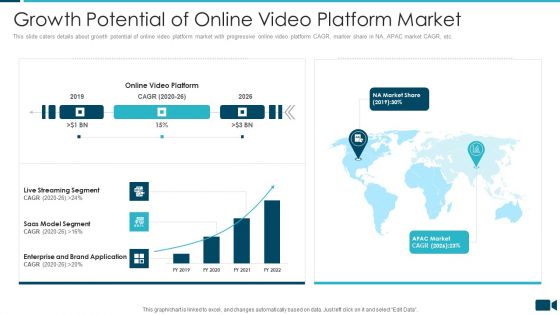
Secured Video Hosting Platform Investor Capital Funding Growth Potential Of Online Video Platform Market Formats PDF
This slide caters details about growth potential of online video platform market with progressive online video platform CAGR, marker share in NA, APAC market CAGR, etc. Deliver an awe inspiring pitch with this creative secured video hosting platform investor capital funding growth potential of online video platform market formats pdf bundle. Topics like saas model segment, enterprise and brand application, live streaming segment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
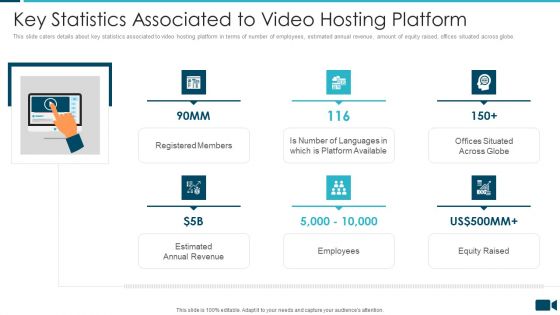
Secured Video Hosting Platform Investor Capital Funding Key Statistics Associated To Video Hosting Platform Rules PDF
This slide caters details about key statistics associated to video hosting platform in terms of number of employees, estimated annual revenue, amount of equity raised, offices situated across globe. Presenting secured video hosting platform investor capital funding key statistics associated to video hosting platform rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like registered members, employees, equity raised, estimated annual revenue. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
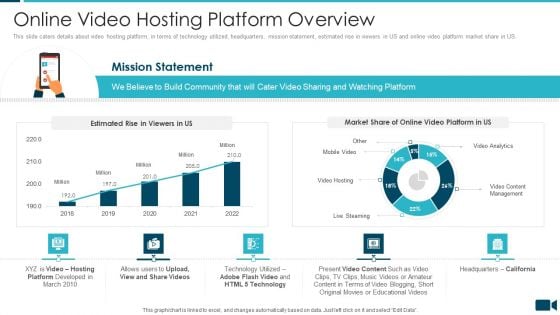
Secured Video Hosting Platform Investor Capital Funding Online Video Hosting Platform Overview Sample PDF
This slide caters details about video hosting platform, in terms of technology utilized, headquarters, mission statement, estimated rise in viewers in US and online video platform market share in US. Deliver and pitch your topic in the best possible manner with this secured video hosting platform investor capital funding online video hosting platform overview sample pdf. Use them to share invaluable insights on online video hosting platform overview and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
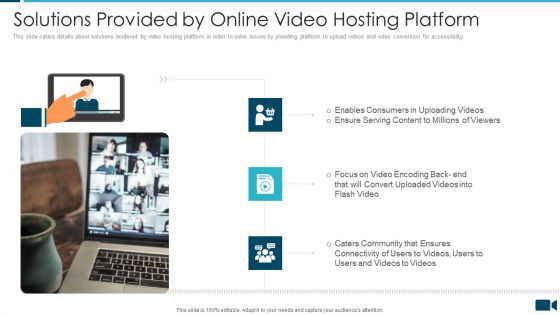
Secured Video Hosting Platform Investor Capital Funding Solutions Provided By Online Video Hosting Platform Introduction PDF
This slide caters details about solutions rendered by video hosting platform in order to solve issues by providing platform to upload videos and video conversion for accessibility. Presenting secured video hosting platform investor capital funding solutions provided by online video hosting platform introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like solutions provided by online video hosting platform. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
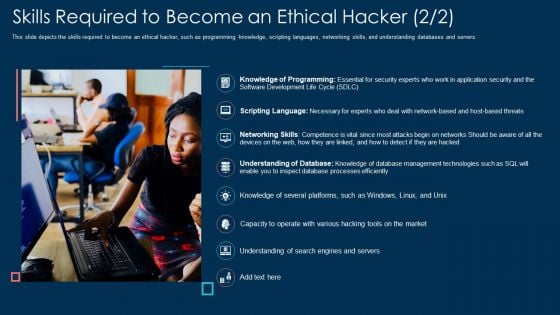
Skills Required To Become An Ethical Hacker Security Ppt Layouts Guide PDF
This slide depicts the skills required to become an ethical hacker, such as programming knowledge, scripting languages, networking skills, and understanding databases and servers. Presenting skills required to become an ethical hacker security ppt layouts guide pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like networking, technologies, management, database. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SIEM Services Security Information And Event Management Logging Process Ppt Model Example Topics PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Presenting siem services security information and event management logging process ppt model example topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine, breaches, organization, investigate, aggregate. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Critical Business Functions Recovery Priorities Guidelines PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. This is a corporate security and risk management addressing critical business functions recovery priorities guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like addressing critical business functions recovery priorities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
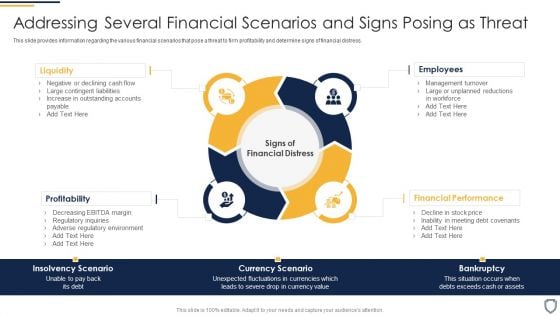
Corporate Security And Risk Management Addressing Several Financial Scenarios And Signs Posing As Threat Pictures PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting corporate security and risk management addressing several financial scenarios and signs posing as threat pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like profitability, liquidity, employees, financial performance . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
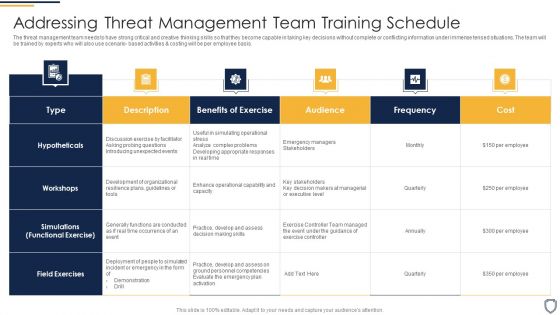
Corporate Security And Risk Management Addressing Threat Management Team Training Schedule Clipart PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative corporate security and risk management addressing threat management team training schedule clipart pdf bundle. Topics like benefits of exercise, audience, frequency, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Contd Guidelines PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting corporate security and risk management addressing various ways to handle insider cyber threats contd guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
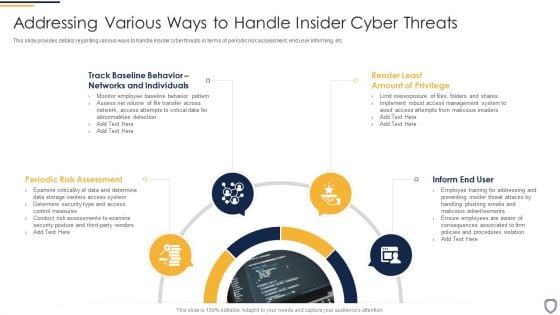
Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Infographics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a corporate security and risk management addressing various ways to handle insider cyber threats infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, inform end user, render least amount of privilege, track baseline behavior networks and individuals . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Budget For Effective Threat Management At Workplace Portrait PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative corporate security and risk management budget for effective threat management at workplace portrait pdf bundle. Topics like incident management, risk management, client onboarding process, document management, information management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































