Computer Virus
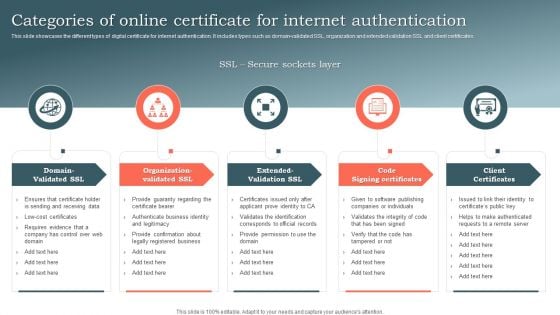
Categories Of Online Certificate For Internet Authentication Ppt Portfolio Samples PDF
This slide showcases the different types of digital certificate for internet authentication. It includes types such as domain-validated SSL, organization and extended validation SSL and client certificates. Presenting Categories Of Online Certificate For Internet Authentication Ppt Portfolio Samples PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Domain Validated SSL, Organization Validated SSL, Extended Validation SSL. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Image Of Key Chain Protection PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Image Of Key Chain Protection PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Download our Services PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Download and present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Use our Success PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Get noted for your awesome slides with our Image Of Key Chain Protection PowerPoint Templates Ppt Backgrounds For Slides 0113. You'll always stay ahead of the game.

Zero Trust Model Comparison Between ZTNA And Secure Access Service
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Model Comparison Between ZTNA And Secure Access Service and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V
This slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact.

IT Security Hacker Email Prevention Guidelines For Employees Information PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi factor authentication for email login credentials.This is a IT Security Hacker Email Prevention Guidelines For Employees Information PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Process, Pieces Of Information, Factor Authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Agribusiness Startup Addressing Plant Health Tracking And Protection Initiative Professional PDF
This slide caters details about plant health tracking and protection initiative developed by firm to detect and manage weed, pests, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Agribusiness Startup Addressing Plant Health Tracking And Protection Initiative Professional PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
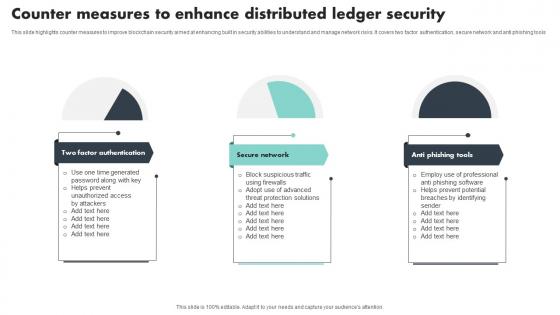
Counter Measures To Enhance Distributed Ledger Security Mockup Pdf
This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools Showcasing this set of slides titled Counter Measures To Enhance Distributed Ledger Security Mockup Pdf The topics addressed in these templates are Factor Authentication, Secure Network, Anti Phishing Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools
Cyber Terrorism Assault Use Of Strong Encrypted Password In The Company Icons PDF
This slide demonstrates the need to have encrypted passwords for various online accounts and indicates how almost every employee has the same password.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault use of strong encrypted password in the company icons pdf Use them to share invaluable insights on use of strong encrypted password in the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
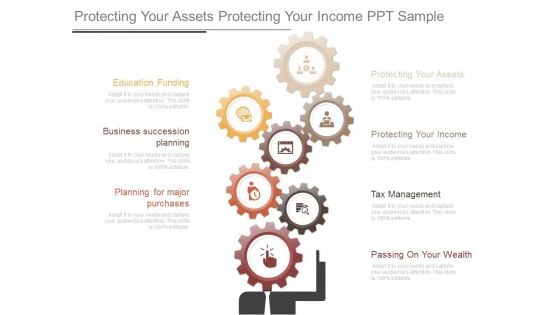
Protecting Your Assets Protecting Your Income Ppt Sample
This is a protecting your assets protecting your income ppt sample. This is a seven stage process. The stages in this process are protecting your assets, protecting your income, tax management, passing on your wealth, education funding, business succession planning, planning for major purchases.
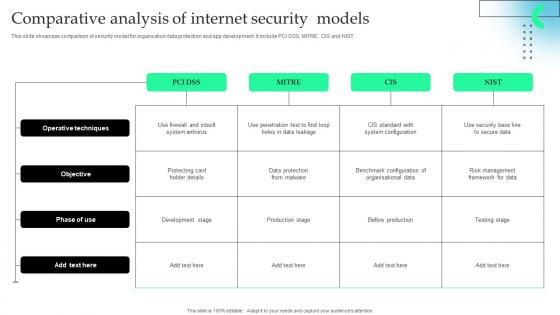
Comparative Analysis Of Internet Security Models Slides Pdf
This slide showcase comparison of security model for organsation data protection and app development. It include PCI DSS, MITRE, CIS and NIST Pitch your topic with ease and precision using this Comparative Analysis Of Internet Security Models Slides Pdf This layout presents information on Operative Techniques, Development Stage, Benchmark Configuration It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase comparison of security model for organsation data protection and app development. It include PCI DSS, MITRE, CIS and NIST

Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V
This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc.

Website Security Management Strategic Plan Step By Step Guide Slides PDF
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Website Security Management Strategic Plan Step By Step Guide Slides PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Website Security Management Strategic Plan Step By Step Guide Slides PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.
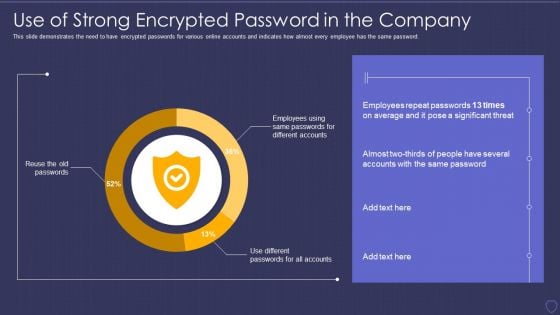
Global Cyber Terrorism Incidents On The Rise IT Use Of Strong Encrypted Password Download PDF
This slide demonstrates the need to have encrypted passwords for various online accounts and indicates how almost every employee has the same password. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it use of strong encrypted password download pdf. Use them to share invaluable insights on use of strong encrypted password in the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V
This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Slidegeeks is here to make your presentations a breeze with Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.
Username And Password For Web Portal Log In Ppt PowerPoint Presentation File Slides PDF
Presenting username and password for web portal log in ppt powerpoint presentation file slides pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including username and password for web portal log in. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Various Designs Of Main Door Lock System For Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various types of smart lock systems. Major types covered are sleek fingerprint scanner, doorknob lock with a password, phone-operated smart lock, video intercom and a combination of code and fingerprint sensor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Various Designs Of Main Door Lock System For Security Utilizing Smart Appliances IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides an overview of the various types of smart lock systems. Major types covered are sleek fingerprint scanner, doorknob lock with a password, phone-operated smart lock, video intercom and a combination of code and fingerprint sensor.
Access Control Management With User Id And Password Ppt PowerPoint Presentation Icon Introduction
This is a access control management with user id and password ppt powerpoint presentation icon introduction. This is a three stage process. The stages in this process are access rights, access management, business.
Password For Mobile Access Vector Icon Ppt PowerPoint Presentation Gallery Layout Ideas PDF
Persuade your audience using this password for mobile access vector icon ppt powerpoint presentation gallery layout ideas pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including password for mobile access vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Protect Your Idea Presentation Powerpoint
This is a protect your idea presentation powerpoint. This is a four stage process. The stages in this process are protect your idea, market evaluation, waste discharge, prototype evaluation.

Technology Protection Ppt Infographic Template
This is a technology protection ppt infographic template. This is a five stage process. The stages in this process are technology protection, current brand strength, oligopolistic or pure competition, financial strength, buyer power.
Yellow Lock Icon For Security And Protection Ppt PowerPoint Presentation Infographics Tips PDF
Presenting this set of slides with name yellow lock icon for security and protection ppt powerpoint presentation infographics tips pdf. This is a three stage process. The stages in this process are yellow lock icon for security and protection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Data Protection With Cyber Security Vector Icon Ppt PowerPoint Presentation Gallery Smartart PDF
Presenting data protection with cyber security vector icon ppt powerpoint presentation gallery smartart pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data protection with cyber security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Security Data Protection Vector Icon Ppt PowerPoint Presentation Gallery Show PDF
Presenting it security data protection vector icon ppt powerpoint presentation gallery show pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including it security data protection vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Protection Shield Icon For Information Security Ppt PowerPoint Presentation File Background PDF
Presenting protection shield icon for information security ppt powerpoint presentation file background pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including protection shield icon for information security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
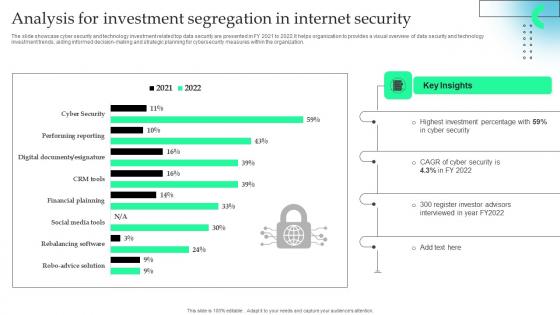
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.

Developing Firm Security Strategy Plan Elevating Brand Protection Strategy Mockup PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. This is a developing firm security strategy plan elevating brand protection strategy mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like overt security features, covert security features, serialization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
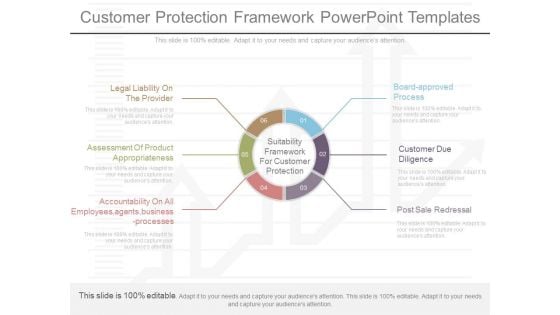
Customer Protection Framework Powerpoint Templates
This is a customer protection framework powerpoint templates. This is a six stage process. The stages in this process are legal liability on the provider, assessment of product appropriateness, accountability on all employees,agents,business processes, board approved process, customer due diligence, post sale redressal, suitability framework for customer protection.
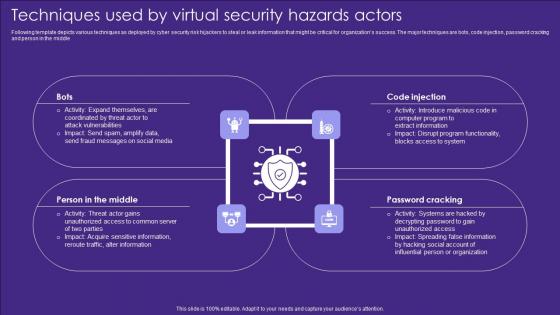
Techniques Used By Virtual Security Hazards Actors Professional Pdf
Following template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle Pitch your topic with ease and precision using this Techniques Used By Virtual Security Hazards Actors Professional Pdf. This layout presents information on Code Injection, Password Cracking, Middle. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle
Information Security Data Protection Vector Icon Ppt PowerPoint Presentation Gallery Clipart PDF
Persuade your audience using this information security data protection vector icon ppt powerpoint presentation gallery clipart pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including information security data protection vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Agriculture Business Elevator Pitch Deck Addressing Plant Health Tracking And Protection Initiative Guidelines PDF
This slide caters details about plant health tracking and protection initiative developed by firm to detect and manage weed, pests, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Agriculture Business Elevator Pitch Deck Addressing Plant Health Tracking And Protection Initiative Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Agriculture Business Elevator Pitch Deck Addressing Plant Health Tracking And Protection Initiative Guidelines PDF
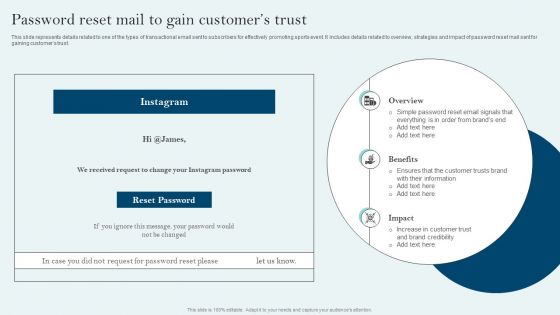
Comprehensive Sports Event Marketing Plan Password Reset Mail To Gain Customers Trust Sample PDF
This slide represents details related to one of the types of transactional email sent to subscribers for effectively promoting sports event. It includes details related to overview, strategies and impact of password reset mail sent for gaining customers trust. Take your projects to the next level with our ultimate collection of Comprehensive Sports Event Marketing Plan Password Reset Mail To Gain Customers Trust Sample PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
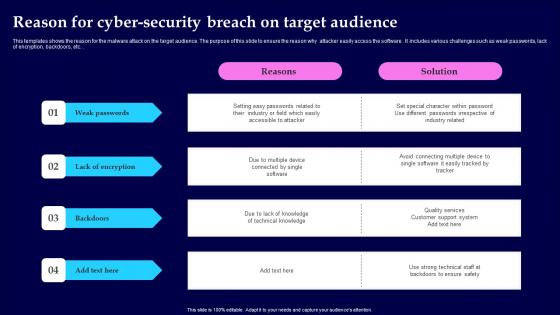
Reason For Cyber Security Breach On Target Audience Microsoft Pdf
This templates shows the reason for the malware attack on the target audience. The purpose of this slide to ensure the reason why attacker easily access the software . It includes various challenges such as weak passwords, lack of encryption, backdoors, etc. Showcasing this set of slides titled Reason For Cyber Security Breach On Target Audience Microsoft Pdf The topics addressed in these templates are Weak Passwords, Lack Of Encryption, Backdoors All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the reason for the malware attack on the target audience. The purpose of this slide to ensure the reason why attacker easily access the software . It includes various challenges such as weak passwords, lack of encryption, backdoors, etc.

Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication.
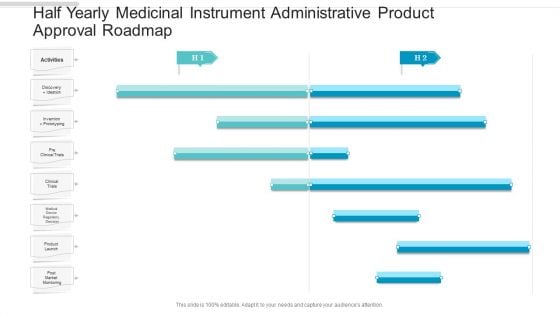
Half Yearly Medicinal Instrument Administrative Product Approval Roadmap Graphics
We present our half yearly medicinal instrument administrative product approval roadmap graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly medicinal instrument administrative product approval roadmap graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
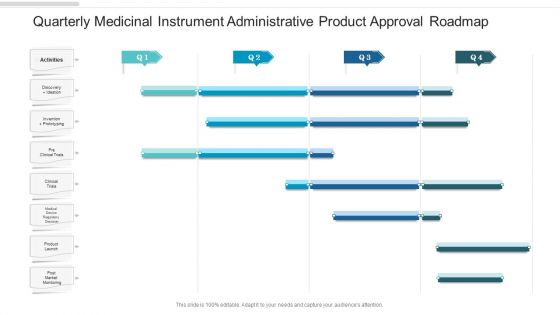
Quarterly Medicinal Instrument Administrative Product Approval Roadmap Template
We present our quarterly medicinal instrument administrative product approval roadmap template. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly medicinal instrument administrative product approval roadmap template in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
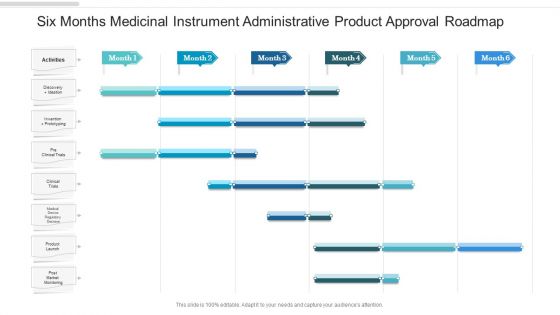
Six Months Medicinal Instrument Administrative Product Approval Roadmap Clipart
We present our six months medicinal instrument administrative product approval roadmap clipart. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months medicinal instrument administrative product approval roadmap clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
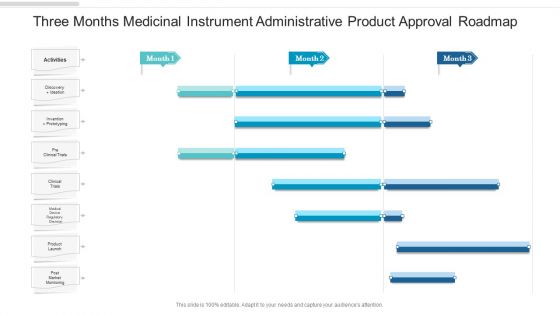
Three Months Medicinal Instrument Administrative Product Approval Roadmap Background
We present our three months medicinal instrument administrative product approval roadmap background. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months medicinal instrument administrative product approval roadmap background in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Protected World Environment Security PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Protected World Environment Security PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Environment PowerPoint Templates because Our PowerPoint Templates and Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Download our Umbrellas PowerPoint Templates because Our PowerPoint Templates and Slides will provide you the cutting edge. Slice through the doubts in the minds of your listeners. Download our Security PowerPoint Templates because Your audience will believe you are the cats whiskers. Download and present our Future PowerPoint Templates because Our PowerPoint Templates and Slides are a sure bet. Gauranteed to win against all odds. Present our Success PowerPoint Templates because Your audience will believe you are the cats whiskers.Use these PowerPoint slides for presentations relating to Protection of an environment, security, environment, umbrellas, success, future. The prominent colors used in the PowerPoint template are Green, Gray, White. Research problems with our Protected World Environment Security PowerPoint Templates Ppt Backgrounds For Slides 0313. Download without worries with our money back guaranteee.

Vendor Data Security Checklist For Market Research Company Sample Pdf
The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc. Pitch your topic with ease and precision using this Vendor Data Security Checklist For Market Research Company Sample Pdf. This layout presents information on Vendor Data Security, Market Research. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc.
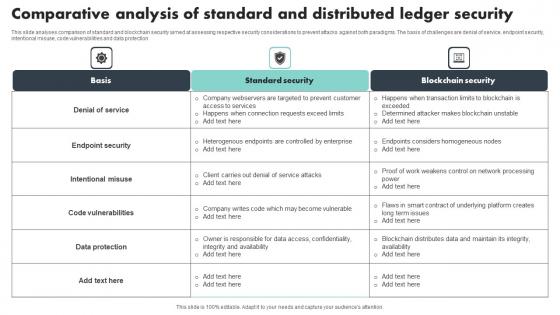
Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf
This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection Pitch your topic with ease and precision using this Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf This layout presents information on Denial Of Service, Endpoint Security, Code Vulnerabilities It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection

Web Access Control Solution Integration Of Swg Inside Sase Architecture
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. The Web Access Control Solution Integration Of Swg Inside Sase Architecture is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc.
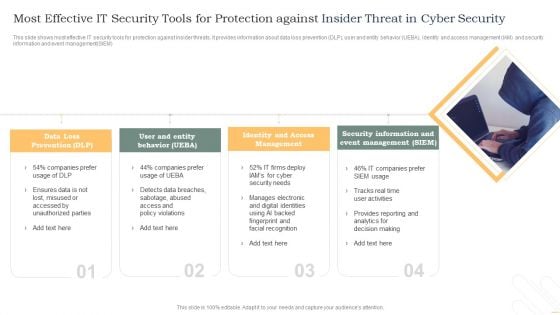
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Protection Piggy Bank PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Security Protection Piggy Bank PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject. Download our Services PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Download and present our Curves and Lines PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Present our Finance PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune.Use these PowerPoint slides for presentations relating to Piggy bank secured with padlock and chain, security, business, services, curves and lines, finance. The prominent colors used in the PowerPoint template are Blue, Yellow, White. Make the break with our Security Protection Piggy Bank PowerPoint Templates Ppt Backgrounds For Slides 0213. Your thoughts will create a breakthrough.
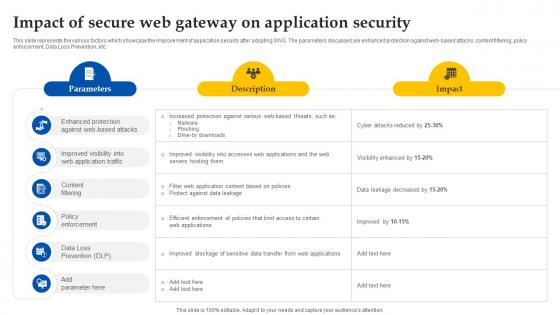
Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
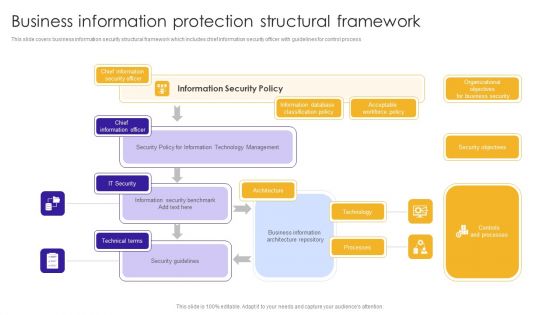
Business Information Protection Structural Framework Summary PDF
This slide covers business information security structural framework which includes chief information security officer with guidelines for control process.Showcasing this set of slides titled Business Information Protection Structural Framework Summary PDF. The topics addressed in these templates are Information Database, Classification Policy, Architecture Repository. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Dos And Donts Of Cyber Security Awareness Professional PDF
The purpose of this slide is to highlight the major dos and donts of cyber security awareness. The dos covered in the slide are using multi-factor authentication, password manager, frequently changing the password, etc. The donts are using the same password, simple and short passwords, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Dos And Donts Of Cyber Security Awareness Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Dollar Under Protection Financial Security PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Dollar Under Protection Financial Security PowerPoint Templates PPT Backgrounds For Slides 0313.Download and present our Money PowerPoint Templates because It can Bubble and burst with your ideas. Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will definately Enhance the stature of your presentation. Adorn the beauty of your thoughts with their colourful backgrounds. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Download and present our Signs PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market. Present our Umbrellas PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues.Use these PowerPoint slides for presentations relating to Dollar under the umbrella, money, signs, business, umbrellas, security . The prominent colors used in the PowerPoint template are Blue, Red, Black. Take your thoughts that extra mile. Express your dream with our Dollar Under Protection Financial Security PowerPoint Templates Ppt Backgrounds For Slides 0313.

Key Parameters To Prepare Security Strategic Agenda Summary Pdf
This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion. Pitch your topic with ease and precision using this Key Parameters To Prepare Security Strategic Agenda Summary Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion.
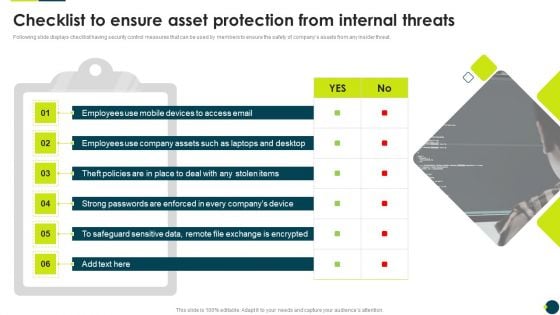
IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF bundle. Topics like Safeguard Sensitive, Strong Passwords, Exchange Encrypted can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhanced Protection Corporate Event Administration Role Of Security Operations Centre In Security Operations Brochure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting enhanced protection corporate event administration role of security operations centre in security operations brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Complete Guide To Launch Best Practices For Website Security Management
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Get a simple yet stunning designed Complete Guide To Launch Best Practices For Website Security Management. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Guide To Launch Best Practices For Website Security Management can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.
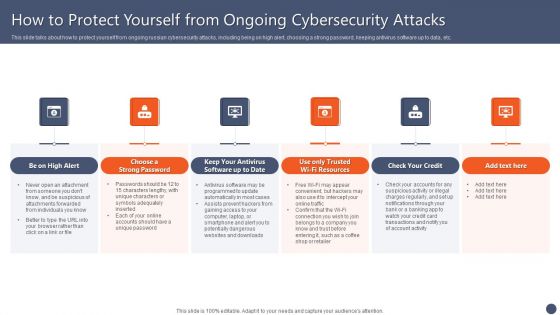
Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF
This slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
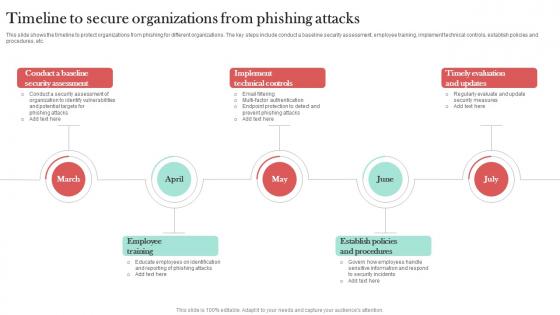
Timeline To Secure Organizations From Man In The Middle Phishing IT
This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. This Timeline To Secure Organizations From Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Timeline To Secure Organizations From Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Stock Photo Internet Symbol With Lock PowerPoint Slide
This image slide displays internet symbol with lock. This conceptual image slide has been designed with graphic of blue color at the rate symbol and lock. This image slide depicts online security. Use this PowerPoint template, in your presentations to express views on e-mail, internet, security, safeguard, password and privacy. This image may also be used to exhibit technology protection. This wonderful image is sure to help you achieve your goal of making professional presentations.
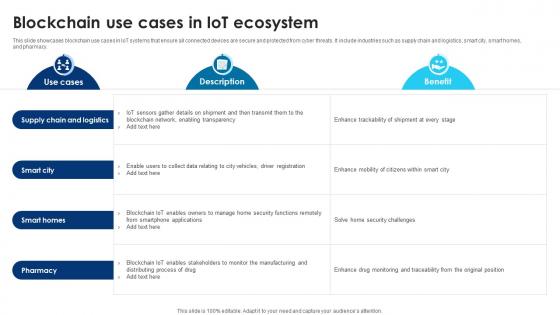
Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V
This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy.

Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V
This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc. Retrieve professionally designed Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
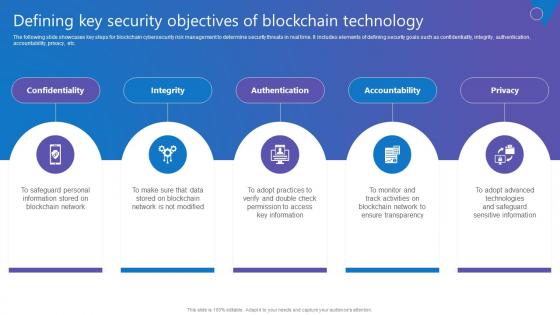
Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf
The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Want to ace your presentation in front of a live audience Our Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc.

Stock Photo Globe With Shield For Protection Image Graphics For PowerPoint Slide
This image slide has been designed with graphic of blue colored globe with security shield. This image displays the concept of earth safety and protection. Create eye-catching presentations using this image.

Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V
The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory.


 Continue with Email
Continue with Email

 Home
Home


































