Computer Virus
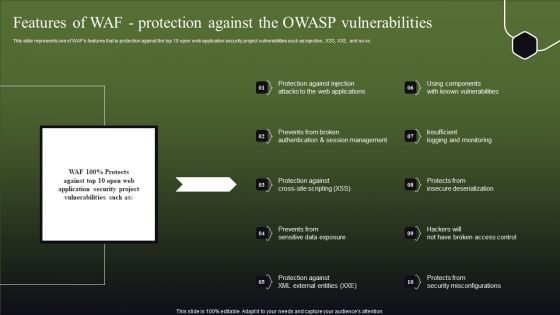
Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
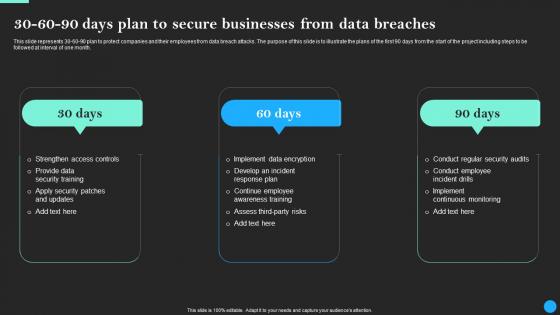
30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
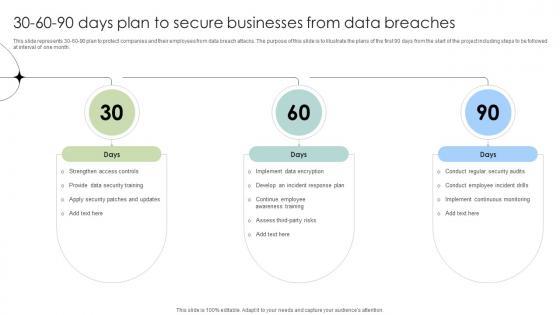
30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
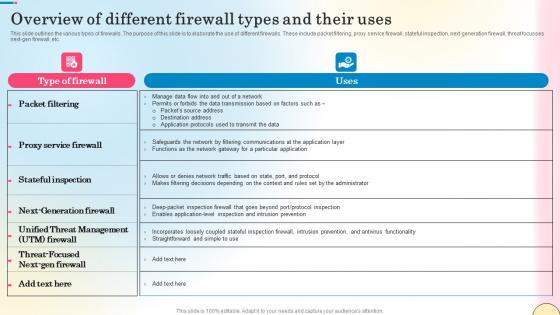
Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf
This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Find a pre-designed and impeccable Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc.
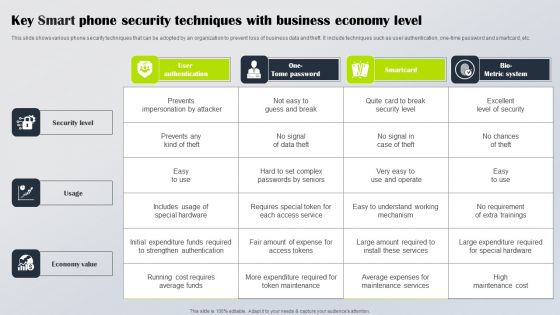
Key Smart Phone Security Techniques With Business Economy Level Brochure PDF
This slide shows various phone security techniques that can be adopted by an organization to prevent loss of business data and theft. It include techniques such as user authentication, one-time password and smartcard, etc. Showcasing this set of slides titled Key Smart Phone Security Techniques With Business Economy Level Brochure PDF. The topics addressed in these templates are Security Level, Usage, Economy Value. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
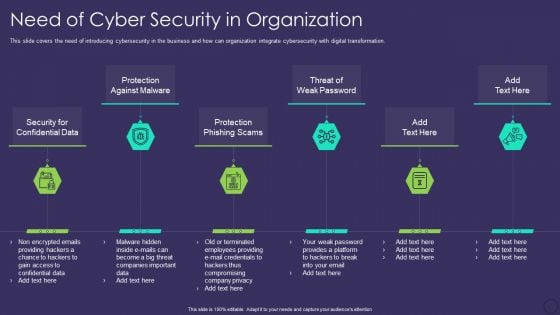
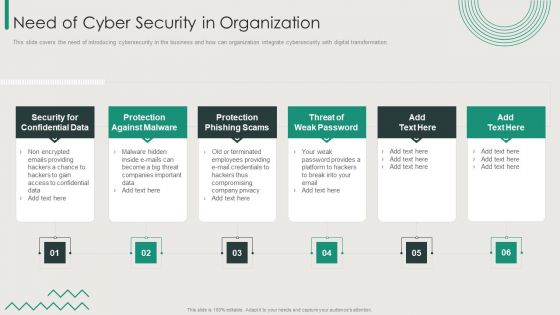
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
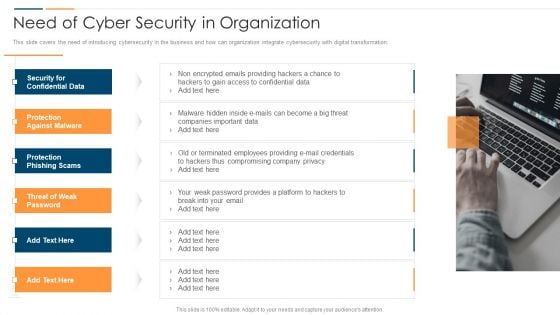
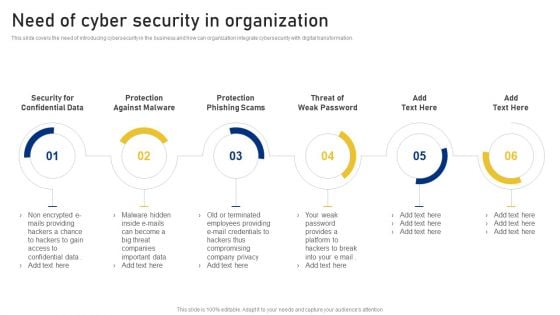
Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
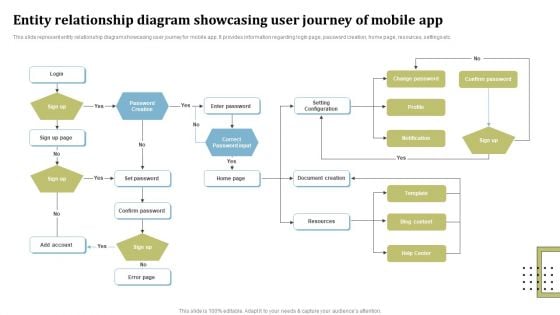
Entity Relationship Diagram Showcasing User Journey Of Mobile App Topics PDF
This slide represent entity relationship diagram showcasing user journey for mobile app. It provides information regarding login page, password creation, home page, resources, settings etc. Presenting Entity Relationship Diagram Showcasing User Journey Of Mobile App Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Password Creation, Correct Password Input, Setting Configuration, Document Creation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
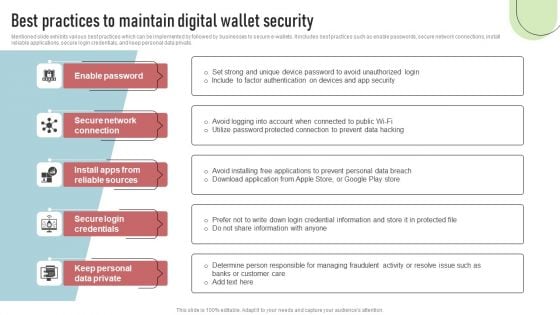
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
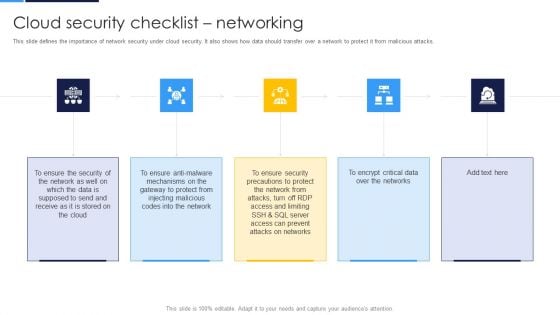
Cloud Security Assessment Cloud Security Checklist Networking Formats PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks.This is a Cloud Security Assessment Cloud Security Checklist Networking Formats PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Gateway To Protect, Injecting Malicious, Precautions To Protect You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
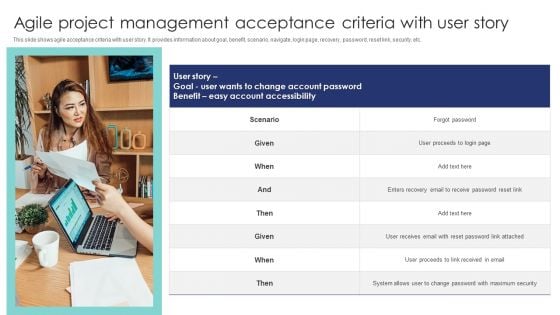
Agile Project Management Acceptance Criteria With User Story Ideas PDF
This slide shows agile acceptance criteria with user story. It provides information about goal, benefit, scenario, navigate, login page, recovery, password, reset link, security, etc. Presenting Agile Project Management Acceptance Criteria With User Story Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Proceeds, Benefit, Goal. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
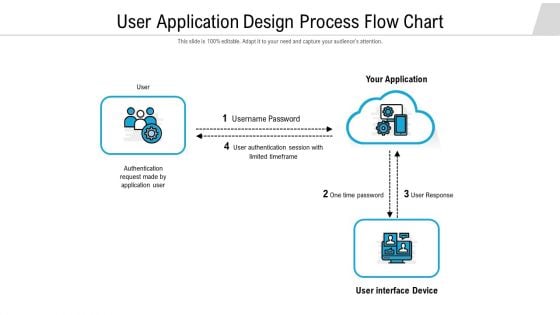
User Application Design Process Flow Chart Demonstration PDF
Presenting user application design process flow chart demonstration pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including authentication request made by application user, username password, authentication session with limited timeframe. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
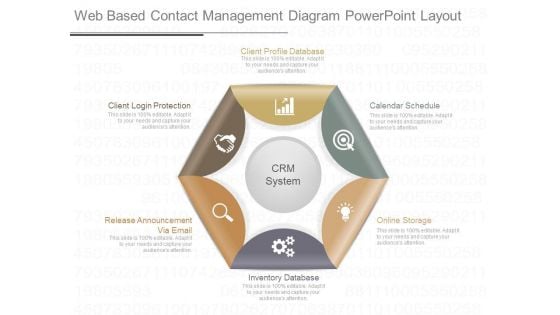
Web Based Contact Management Diagram Powerpoint Layout
This is a web based contact management diagram powerpoint layout. This is a six stage process. The stages in this process are client profile database, client login protection, release announcement via email, inventory database, calendar schedule, online storage.

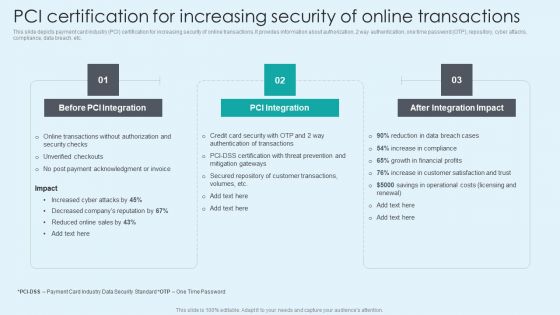
PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Colorful Illustration Using Arrows Flow Chart Business Plan PowerPoint Templates
We present our colorful illustration using arrows flow chart business plan PowerPoint templates.Use our Arrows PowerPoint Templates because,You are the Champion of your team shall anoint. Use our Shapes PowerPoint Templates because, This will helps you to explore the minutest detail of each concept and follow the trail to its conclusion. Use our Signs PowerPoint Templates because,You can take it along a sure fire road to good profit. Use our Business PowerPoint Templates because, Spell out your advertising plans to increase market share. The feedback has been positive and productive Use our Process and Flows PowerPoint Templates because,They will Amplify your basic corporate concept and forefront the benefits of overlapping processes to arrive at common goals.Use these PowerPoint slides for presentations relating to 3d, background, colorful, communication, computing, concept, connection, data, database, design, development, digital, download, glossy, graphic, illustration, information, internet, isolated, network, networking, online, orange, plastic, security, segment, server, store, symbol, system, technology, upload, website,. The prominent colors used in the PowerPoint template are Green, Red, Black. People tell us our colorful illustration using arrows flow chart business plan PowerPoint templates are Spiffy. The feedback we get is that our data PowerPoint templates and PPT Slides are Versatile. People tell us our colorful illustration using arrows flow chart business plan PowerPoint templates are designed by a team of presentation professionals. Presenters tell us our concept PowerPoint templates and PPT Slides are Appealing. The feedback we get is that our colorful illustration using arrows flow chart business plan PowerPoint templates are Tranquil. Professionals tell us our concept PowerPoint templates and PPT Slides are Gorgeous. Burn away doubts with our Colorful Illustration Using Arrows Flow Chart Business Plan PowerPoint Templates. You will come out on top.
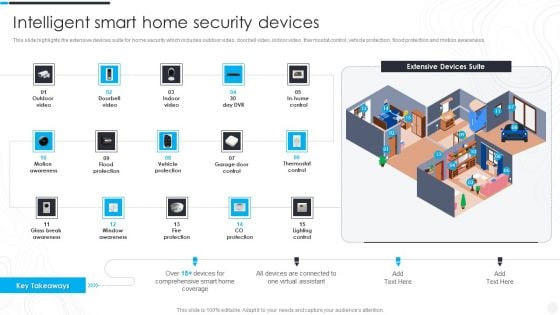
Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF bundle. Topics like Flood Protection, Motion Awareness, Vehicle Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
PCI Certification For Increasing Security Of Online Transactions Background PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Explore a selection of the finest PCI Certification For Increasing Security Of Online Transactions Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PCI Certification For Increasing Security Of Online Transactions Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
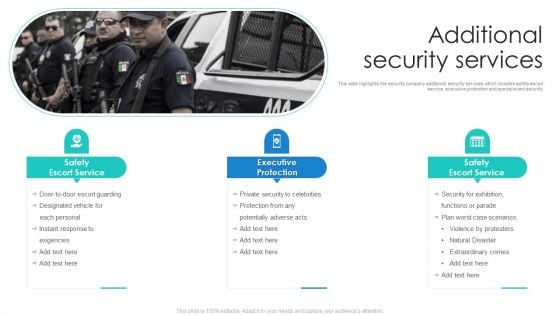
Manpower Corporate Security Business Profile Additional Security Services Formats PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Additional Security Services Formats PDF bundle. Topics like Safety Escort Service, Executive Protection, Safety Escort Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
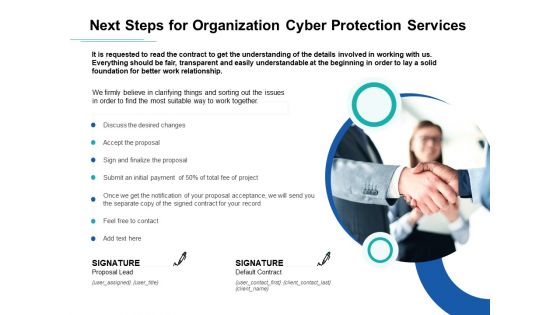
Develop Corporate Cyber Security Risk Mitigation Plan Next Steps For Organization Cyber Protection Services Topics PDF Themes PDF
Presenting develop corporate cyber security risk mitigation plan next steps for organization cyber protection services topics pdf themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like desired changes, initial payment, organization, cyber protection services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
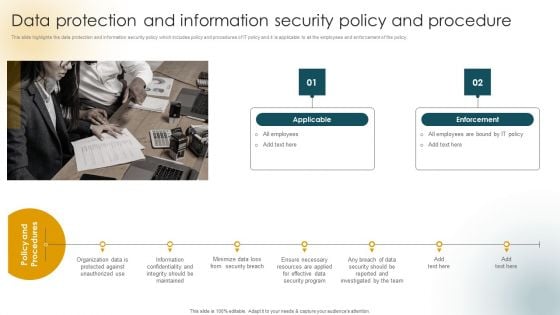
Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cloud Security Assessment Enterprise Cloud Security Solutions Introduction PDF
This slide describes the enterprise cloud security solutions, including multi-factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost-benefits of hybrid cloud.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Enterprise Cloud Security Solutions Introduction PDF. Use them to share invaluable insights on Manage Accounts, Services Proactively, Processes Fingerprints and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
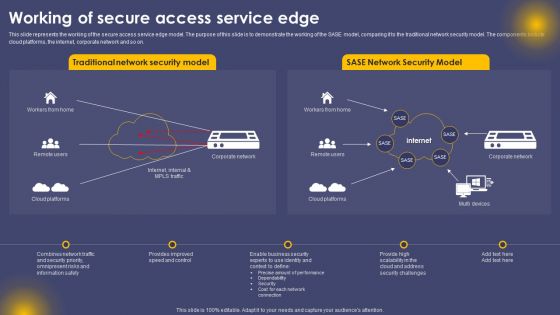
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Develop Corporate Cyber Security Risk Mitigation Plan Case Study For Organization Cyber Protection Services Themes PDF Sample PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan case study for organization cyber protection services themes pdf sample pdf bundle. Topics like problem, results, our solution, low cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
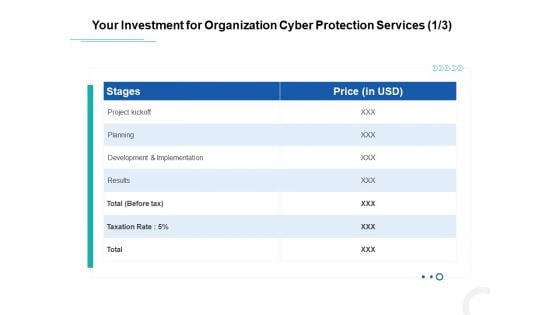
Develop Corporate Cyber Security Risk Mitigation Plan Your Investment For Organization Cyber Protection Services Planning Rules PDF
Deliver and pitch your topic in the best possible manner with this develop corporate cyber security risk mitigation plan your investment for organization cyber protection services planning rules pdf. Use them to share invaluable insights on project kickoff, planning, development and implementation, results and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
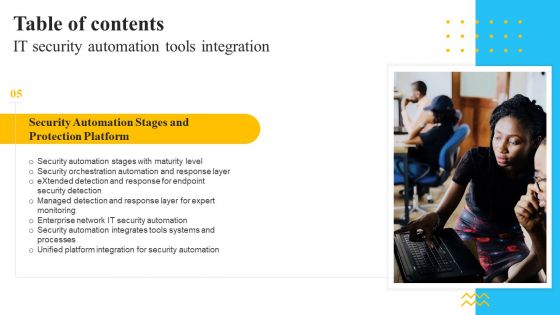
Table Of Contents IT Security Automation Tools Integration Ppt Gallery Aids PDF
Presenting Table Of Contents IT Security Automation Tools Integration Ppt Gallery Aids PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Automation Stages, Protection Platform, Security Orchestration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
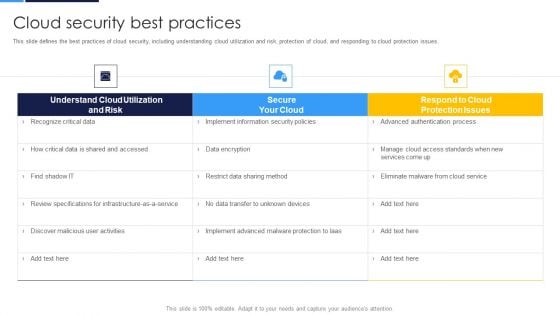
Cloud Security Assessment Cloud Security Best Practices Infographics PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Cloud Security Best Practices Infographics PDF Use them to share invaluable insights on Understand Cloud, Review Specifications, Discover Malicious and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today. This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security.

Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.
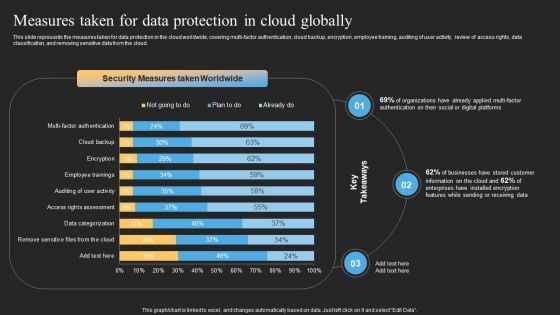
Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF
This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. This Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
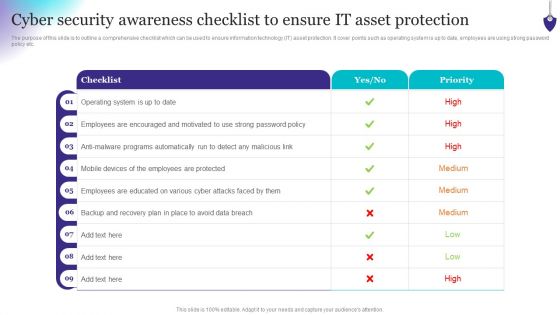
Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Develop Corporate Cyber Security Risk Mitigation 30 60 90 Days Plan For Organization Cyber Protection Proposal Mockup PDF
This is a develop corporate cyber security risk mitigation 30 60 90 days plan for organization cyber protection proposal mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
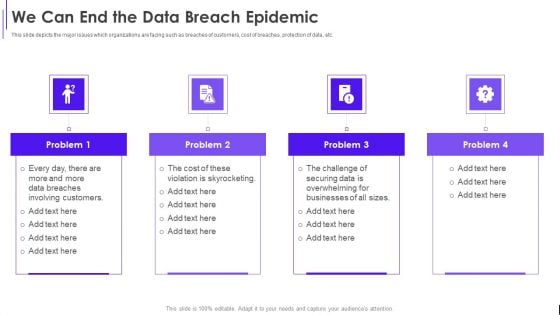
Fundraising Pitch Deck For Evervault We Can End The Data Breach Epidemic Ppt Infographics Graphics Example PDF
This slide depicts the major issues which organizations are facing such as breaches of customers, cost of breaches, protection of data, etc. This is a Fundraising Pitch Deck For Evervault We Can End The Data Breach Epidemic Ppt Infographics Graphics Example PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Breaches, Involving Customers, Violation Skyrocketing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Big Data Use For Market Optimization Icon Ppt Gallery Ideas pdf
Pitch your topic with ease and precision using this Big Data Use For Market Optimization Icon Ppt Gallery Ideas pdf. This layout presents information on Big Data Use, Market Optimization Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Big Data Use For Market Optimization Icon Ppt Gallery Ideas pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Effective Use Of Big Data Icon Ppt Portfolio Layouts pdf
Showcasing this set of slides titled Effective Use Of Big Data Icon Ppt Portfolio Layouts pdf. The topics addressed in these templates are Effective Use, Big Data Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Effective Use Of Big Data Icon Ppt Portfolio Layouts pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Based Robotic Process Automation Architecture Icon For Business Automation Process Diagrams Pdf
Pitch your topic with ease and precision using this Cloud Based Robotic Process Automation Architecture Icon For Business Automation Process Diagrams Pdf. This layout presents information on Cloud Based Robotic, Process Automation Architecture. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cloud Based Robotic Process Automation Architecture Icon For Business Automation Process Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Data Integration With Based Robotic Process Automation Icon Rules Pdf
Showcasing this set of slides titled Cloud Data Integration With Based Robotic Process Automation Icon Rules Pdf. The topics addressed in these templates are Cloud Data Integration, Based Robotic Process Automation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cloud Data Integration With Based Robotic Process Automation Icon Rules Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Migration Readiness Assessment Icon Ppt Layouts Pictures Pdf
Pitch your topic with ease and precision using this Cloud Migration Readiness Assessment Icon Ppt Layouts Pictures Pdf. This layout presents information on Cloud Migration, Readiness Assessment, Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cloud Migration Readiness Assessment Icon Ppt Layouts Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Readiness Assessment Checklist Icon Ppt Guidelines Pdf
Showcasing this set of slides titled Cloud Readiness Assessment Checklist Icon Ppt Guidelines Pdf. The topics addressed in these templates are Cloud Readiness, Assessment Checklist, Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cloud Readiness Assessment Checklist Icon Ppt Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Enterprise Cloud Readiness Assessment And Management Icon Ppt Professional Example Pdf
Pitch your topic with ease and precision using this Enterprise Cloud Readiness Assessment And Management Icon Ppt Professional Example Pdf. This layout presents information on Enterprise Cloud, Readiness Assessment, Management Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Enterprise Cloud Readiness Assessment And Management Icon Ppt Professional Example Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
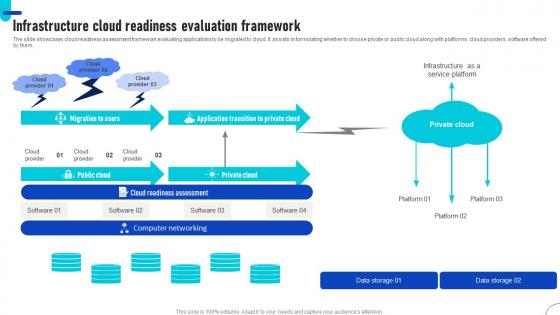
Infrastructure Cloud Readiness Evaluation Framework Ppt File Skills Pdf
The slide showcases cloud readiness assessment framework evaluating applications to be migrated to cloud. It assists in formulating whether to choose private or public cloud along with platforms, cloud providers, software offered by them. Showcasing this set of slides titled Infrastructure Cloud Readiness Evaluation Framework Ppt File Skills Pdf. The topics addressed in these templates are Cloud Provider, Public Cloud, Private Cloud. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases cloud readiness assessment framework evaluating applications to be migrated to cloud. It assists in formulating whether to choose private or public cloud along with platforms, cloud providers, software offered by them.

Data Breach Prevention Strategies For Users Data Breach Prevention Sample Pdf
This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Breach Prevention Strategies For Users Data Breach Prevention Sample Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc.
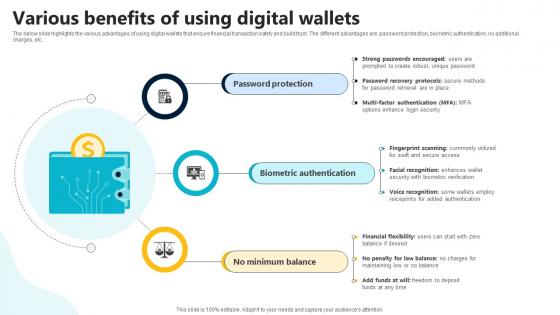
Various Benefits Of Using Digital Wallets In Depth Guide To Digital Wallets Fin SS V
The below slide highlights the various advantages of using digital wallets that ensure financial transaction safety and build trust. The different advantages are password protection, biometric authentication, no additional charges, etc. The Various Benefits Of Using Digital Wallets In Depth Guide To Digital Wallets Fin SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The below slide highlights the various advantages of using digital wallets that ensure financial transaction safety and build trust. The different advantages are password protection, biometric authentication, no additional charges, etc.

Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V
This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection. Are you searching for a Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V from Slidegeeks today. This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection.

Key Takeaways And Strategic Insights Global Security Industry PPT Sample IR SS V
This slide highlights the global Defense insights which are responsible for the growth. The purpose of this slide is to provide a brief insights related to the Defense market and its growth. It covers opportunity protection, macro and geopolitical insights related to the insurers, and demand for cyber security defense analysis. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Takeaways And Strategic Insights Global Security Industry PPT Sample IR SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights the global Defense insights which are responsible for the growth. The purpose of this slide is to provide a brief insights related to the Defense market and its growth. It covers opportunity protection, macro and geopolitical insights related to the insurers, and demand for cyber security defense analysis.

Find The Right Way Of Investment PowerPoint Templates Ppt Backgrounds For Slides 0413
Knock on the door to success with our Find The Right Way Of Investment PowerPoint Templates PPT Backgrounds For Slides 0413. Be assured of gaining entry. Give them a dose of your ability. It will go down well with our Find The Right Way Of Investment PowerPoint Templates PPT Backgrounds For Slides 0413. Try our Find The Right Way Of Investment PowerPoint Templates Ppt Backgrounds For Slides 0413 and get bitten by the bug. You will cease to consider anything else.
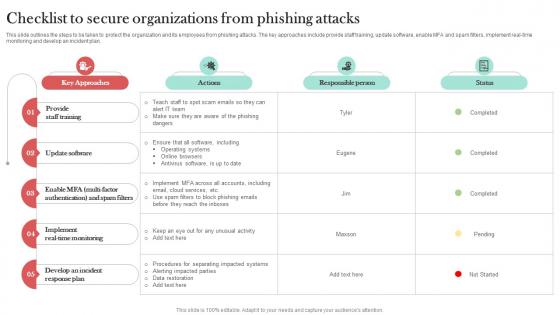
Checklist To Secure Organizations From Man In The Middle Phishing IT
This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Checklist To Secure Organizations From Man In The Middle Phishing IT template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Checklist To Secure Organizations From Man In The Middle Phishing IT that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan.
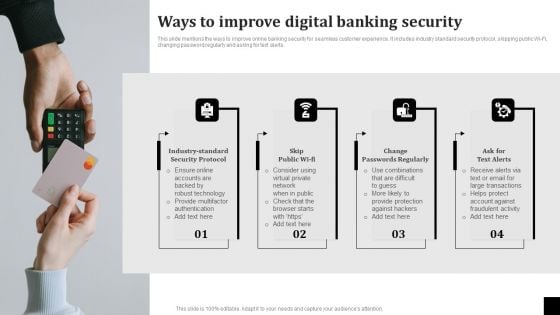
Ways To Improve Digital Banking Security Elements PDF
This slide mentions the ways to improve online banking security for seamless customer experience. It includes industry standard security protocol, skipping public Wi-Fi, changing password regularly and asking for text alerts. Presenting Ways To Improve Digital Banking Security Elements PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Industry Standard Security Protocol, Skip Public Wifi, Change Passwords Regularly. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V
The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness. This Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness.
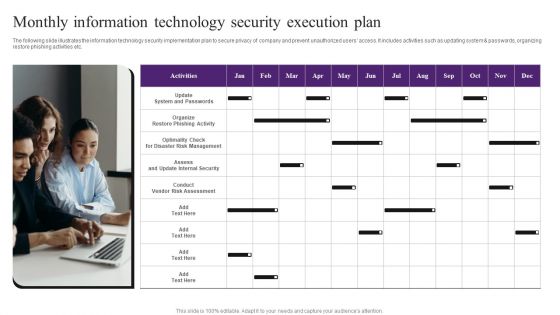
Monthly Information Technology Security Execution Plan Template PDF
The following slide illustrates the information technology security implementation plan to secure privacy of company and prevent unauthorized users access. It includes activities such as updating system and passwords, organizing restore phishing activities etc. Presenting Monthly Information Technology Security Execution Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Update System And Passwords, Conduct Vendor Risk Assessment, Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
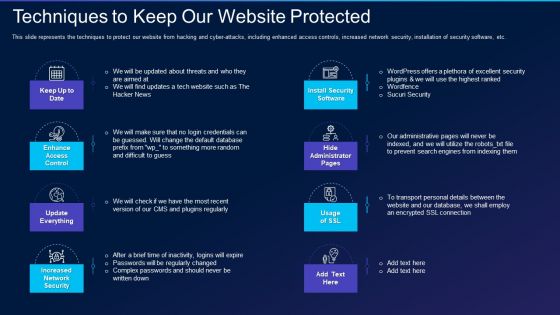
Cyber Exploitation IT Techniques To Keep Our Website Protected Brochure PDF
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Application Security Performance Monitoring Application Security Testing
This slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Want to ace your presentation in front of a live audience Our Application Security Performance Monitoring Application Security Testing can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the performance tracking dashboard for application security to analyze and monitor security of application.
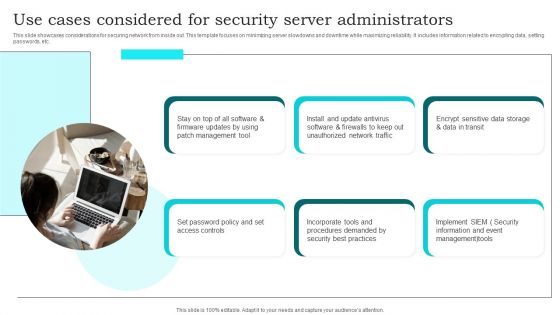
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security In 5G Technology Architecture 5G Functional Architecture Formats PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.This is a Security In 5G Technology Architecture 5G Functional Architecture Formats PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Previous Generations, Distinguish Authentication, Transactions Adaptable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Protect Earth Environment PowerPoint Templates And PowerPoint Themes 0812
Protect Earth Environment PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with protective earth With our Protect Earth Environment PowerPoint Templates And PowerPoint Themes 0812 you will feel up to it. Derive the confidence to go for it.
Curriculum Development Brand Protection Ppt PowerPoint Presentation Ideas
This is a curriculum development brand protection ppt powerpoint presentation ideas. This is a seven stage process. The stages in this process are curriculum, development, brand, protection.
Business Asset Protection Ppt Powerpoint Presentation Model Mockup Cpb
This is a business asset protection ppt powerpoint presentation model mockup cpb. This is a three stage process. The stages in this process are business asset protection.
Asset Protection Ppt PowerPoint Presentation File Icon Cpb
This is a asset protection ppt powerpoint presentation file icon cpb. This is a five stage process. The stages in this process are asset protection.


 Continue with Email
Continue with Email

 Home
Home


































