Computer Virus
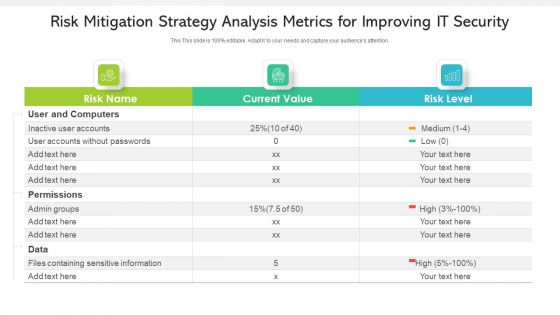
Risk Mitigation Strategy Analysis Metrics For Improving IT Security Ppt PowerPoint Presentation Gallery Gridlines PDF
Showcasing this set of slides titled risk mitigation strategy analysis metrics for improving it security ppt powerpoint presentation gallery gridlines pdf. The topics addressed in these templates are inactive user accounts, accounts without passwords, permissions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
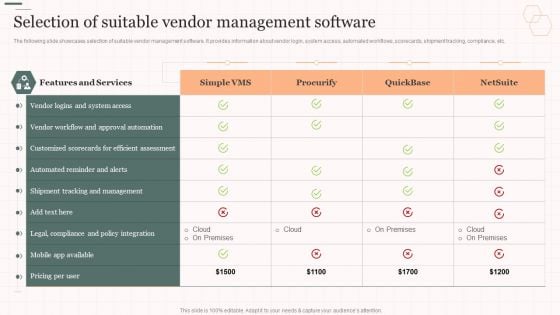
Selection Of Suitable Vendor Management Software Vendor Management Strategies Guidelines PDF
The following slide showcases selection of suitable vendor management software. It provides information about vendor login, system access, automated workflows, scorecards, shipment tracking, compliance, etc. Deliver an awe inspiring pitch with this creative Selection Of Suitable Vendor Management Software Vendor Management Strategies Guidelines PDF bundle. Topics like Approval Automation, Shipment Tracking, Legal Compliance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012
Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012-The euro is the currency used by the Institutions of the European Union and is the official currency of the Eurozone. This Template shows the currency Euro under the Umbrella which signifies the increasing rate of Euro from 2010 to 2012. Stable ideas are the building blocks of a successful structure. Lay down the fundamentals to build upon. Take it up to a higher level with your thoughts. -Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Currency protected by umbrella, security, business, money, shapes, metaphor Start accelerating revenue growth with our Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012. They will make you look good.

Cloud Security Threats Compliance Violations Demonstration PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state. This is a Cloud Security Threats Compliance Violations Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Businesses, Organizations, Authentication Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
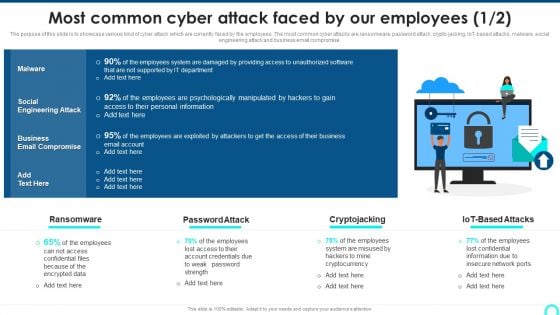
Most Common Cyber Attack Faced By Our Employees Clipart PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. This is a Most Common Cyber Attack Faced By Our Employees Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees Psychologically, Personal Information, Psychologically Manipulated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
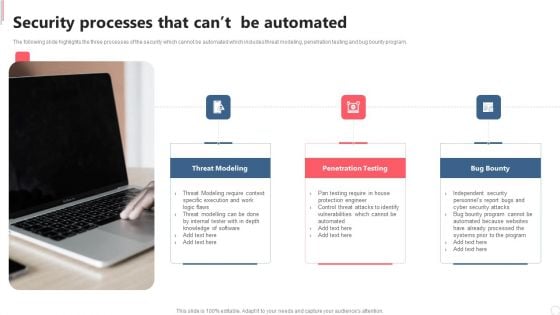
Cyber Security Automation Framework Security Processes That Cant Be Automated Topics PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Automation Framework Security Processes That Cant Be Automated Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
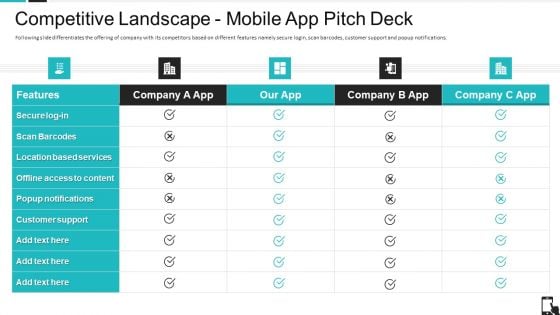
Competitive Landscape Mobile App Pitch Deck Ppt File Layout PDF
Following slide differentiates the offering of company with its competitors based on different features namely secure login, scan barcodes, customer support and popup notifications. Deliver an awe inspiring pitch with this creative competitive landscape mobile app pitch deck ppt file layout pdf bundle. Topics like secure login, scan barcodes, customer support, popup notifications, location based services, offline access to content can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
secure payment processing ppt powerpoint presentation styles visual aids cpb
Presenting this set of slides with name secure payment processing ppt powerpoint presentation styles visual aids cpb. This is an editable Powerpoint three stages graphic that deals with topics like secure payment processing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Information Security Risks Ppt PowerPoint Presentation Portfolio Aids Cpb
Presenting this set of slides with name information security risks ppt powerpoint presentation portfolio aids cpb. This is an editable Powerpoint seven stages graphic that deals with topics like information security risks to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Continuous Security Monitoring Ppt PowerPoint Presentation Professional Visual Aids Cpb
Presenting this set of slides with name continuous security monitoring ppt powerpoint presentation professional visual aids cpb. This is an editable Powerpoint six stages graphic that deals with topics like continuous security monitoring to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Internet Security Threats Management Framework Icons PDF
This slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Showcasing this set of slides titled internet security threats management framework icons pdf. The topics addressed in these templates are asset, control topic, evaluation questions, response, threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Safety Breach Response Playbook Checklist To Ensure Asset Protection From Internal Designs PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Are you searching for a Safety Breach Response Playbook Checklist To Ensure Asset Protection From Internal Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Safety Breach Response Playbook Checklist To Ensure Asset Protection From Internal Designs PDF from Slidegeeks today.

Digital Health Interventions Impact Of Digital Therapeutics On Data Protection Mockup PDF
This slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Retrieve professionally designed Digital Health Interventions Impact Of Digital Therapeutics On Data Protection Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
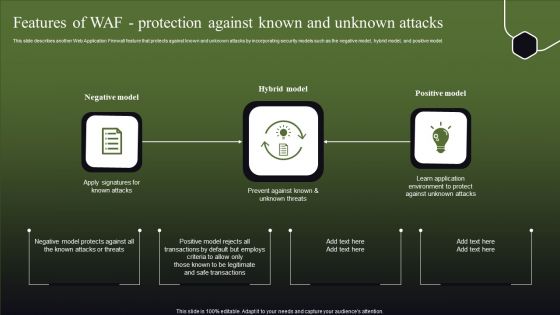
Features Of WAF Protection Against Known And Unknown Attacks Graphics PDF
This slide describes another Web Application Firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. This modern and well-arranged Features Of WAF Protection Against Known And Unknown Attacks Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
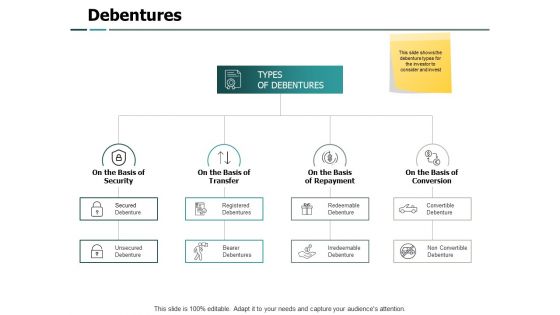
Debentures Security Conversion Ppt PowerPoint Presentation Show Aids
Presenting this set of slides with name debentures security conversion ppt powerpoint presentation show aids. This is a four stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Concept Of Secured Money America PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Concept Of Secured Money America PowerPoint Templates PPT Backgrounds For Slides 1212.Present our Security PowerPoint Templates because it Educates your team with your thoughts and logic. Download and present our Finance PowerPoint Templates because it shows to your group how they mesh together to drive the whole. Download our Success PowerPoint Templates because iT outlines the entire thought process for the benefit of others. Tell it to the world with your characteristic aplomb. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download our Money PowerPoint Templates because this is a wonderful graphics to see the smiles of happiness spread as your audience realizes the value of your words.Use these PowerPoint slides for presentations relating to Lock up & protect us dollar, money, finance, security, success, business. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Customers tell us our Concept Of Secured Money America PowerPoint Templates PPT Backgrounds For Slides 1212 are visually appealing. Presenters tell us our security PowerPoint templates and PPT Slides are Wonderful. Use our Concept Of Secured Money America PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. PowerPoint presentation experts tell us our us PowerPoint templates and PPT Slides are Nifty. Customers tell us our Concept Of Secured Money America PowerPoint Templates PPT Backgrounds For Slides 1212 are Classic. Presenters tell us our protect PowerPoint templates and PPT Slides are Magical. Keep them driven with our Concept Of Secured Money America PowerPoint Templates Ppt Backgrounds For Slides 1212. You will come out on top.
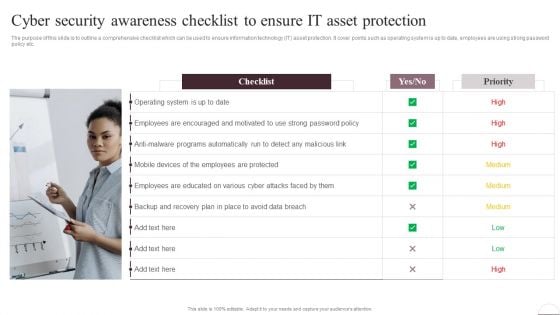
Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Get a simple yet stunning designed Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
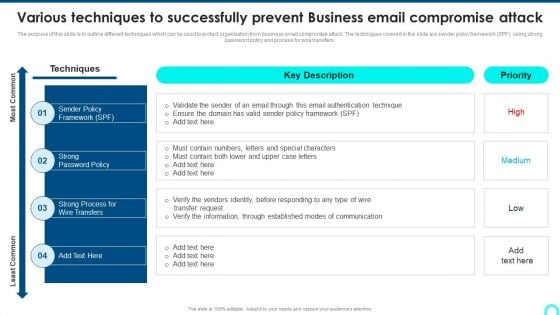
Various Techniques To Successfully Prevent Business Email Compromise Attack Sample PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Deliver and pitch your topic in the best possible manner with this Various Techniques To Successfully Prevent Business Email Compromise Attack Sample PDF. Use them to share invaluable insights on Through Established, Authentication Technique, Through Established and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf today and make your presentation stand out from the rest The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc.
Key On Human Hand Vector Icon Ppt PowerPoint Presentation Visual Aids Outline
Presenting this set of slides with name key on human hand vector icon ppt powerpoint presentation visual aids outline. This is a one stage process. The stages in this process are formation, business, corporate. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Process Improvement With Measure And Analyze Ppt PowerPoint Presentation Summary Visual Aids PDF
Presenting this set of slides with name business process improvement with measure and analyze ppt powerpoint presentation summary visual aids pdf. This is a one stage process. The stages in this process are control, improve, define, measure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Analyst Diagrams Man Suffering From Disaster PowerPoint Theme Slides
We present our business analyst diagrams man suffering from disaster powerpoint theme Slides.Present our Security PowerPoint Templates because you should once Tap the ingenuity of our PowerPoint Templates and Slides. They are programmed to succeed. Use our Symbol PowerPoint Templates because Our PowerPoint Templates and Slides have the Brilliant backdrops. Guaranteed to illuminate the minds of your audience. Present our Business PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Download our People PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team.Use these PowerPoint slides for presentations relating to Accident, Activity, Assistance, Background, Belt, Buoy, Business, Businessman, Care, Circle, Concept, Crash, Danger, Despair, Disaster, Emergency, Emotional, Equipment, Hand, Help, Hopelessness, Human, Illustration, Insurance, Isolated, Life, Lifebuoy, Life Preserver, Loss, Lost, People, Person, Protection, Rescue, Ring, Risk, Rubber, Safe, Safety, Salvage, Security, Shipwreck, Single, Stress, Survival, Symbol, Warning, White. The prominent colors used in the PowerPoint template are Red, Gray, White. PowerPoint presentation experts tell us our business analyst diagrams man suffering from disaster powerpoint theme Slides are designed by a team of presentation professionals. Use our Assistance PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. You can be sure our business analyst diagrams man suffering from disaster powerpoint theme Slides will help them to explain complicated concepts. Presenters tell us our Care PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. You can be sure our business analyst diagrams man suffering from disaster powerpoint theme Slides have awesome images to get your point across. Professionals tell us our Belt PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Assist the fallen with our Business Analyst Diagrams Man Suffering From Disaster PowerPoint Theme Slides. Give them hope to rise again.
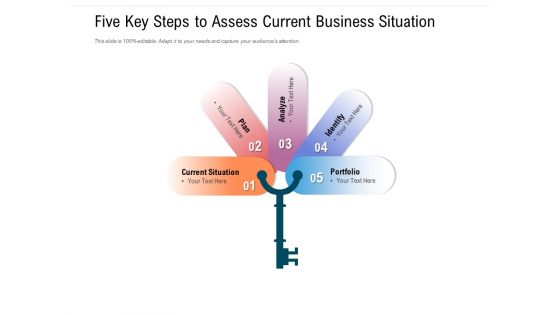
Five Key Steps To Assess Current Business Situation Ppt PowerPoint Presentation Visual Aids Styles PDF
Persuade your audience using this five key steps to assess current business situation ppt powerpoint presentation visual aids styles pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including current situation, plan, analyze, identify, portfolio. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
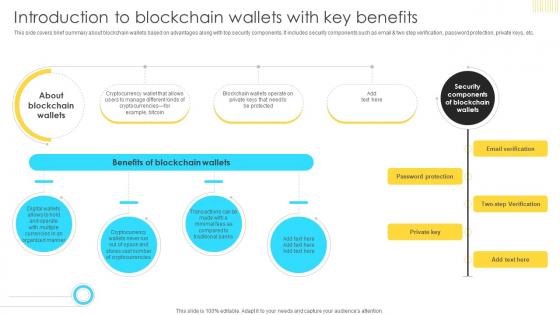
Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V
This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc Do you know about Slidesgeeks Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc

Security Testing Types Code Review Application Security Testing
This slide outlines the introduction of secure code review in application security for efficient working of an application. This Security Testing Types Code Review Application Security Testing from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the introduction of secure code review in application security for efficient working of an application.

Tools For Vulnerability Scanning In Security Testing Application Security Testing
This slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc. Retrieve professionally designed Tools For Vulnerability Scanning In Security Testing Application Security Testing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc.
Developing Firm Security Strategy Plan Addressing Different Security Priorities At Organization Business Formats PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of people security, intellectual property, brand protection, crisis management, corporate governance and information security. Presenting developing firm security strategy plan addressing different security priorities at organization business formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security of people, corporate governance, intellectual property, information security, brand protection, crisis management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
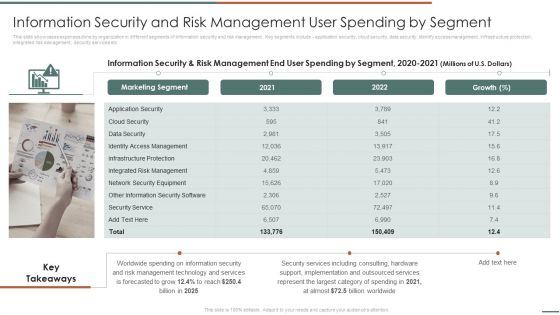
Information Security Risk Evaluation Information Security And Risk Management User Spending By Segment Demonstration PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc.This is a Information Security Risk Evaluation Information Security And Risk Management User Spending By Segment Demonstration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Management, Infrastructure Protection, Security Equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
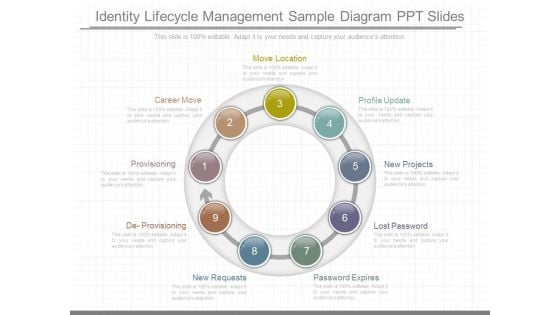
Identity Lifecycle Management Sample Diagram Ppt Slides
This is a identity lifecycle management sample diagram ppt slides. This is a nine stage process. The stages in this process are move location, profile update, new projects, lost password, password expires, new requests, de provisioning, provisioning, career move.

Rescue Real Estate PowerPoint Templates And PowerPoint Themes 1012
Emphatically define your message with our above template which contains a graphic of lifesaver and a 3d house. This image depicts rescue of real estate concept. It is a useful captivating tool concieved to enable you to define your message in your Real estate PPT presentations on protection, security, assistance and private property. Go ahead and add charm to your presentations with our unique template. Complete your presentation with our Rescue Real Estate PowerPoint Templates And PowerPoint Themes 1012. Just download, type and present.

Internet Security PowerPoint Template 0910
Blue Earth globe and padlock isolated over white background Embrace changes with our Internet Security PowerPoint Template 0910. Develop the correct attitude for it.

Stock Photo Two Piggy Banks With Yellow Umbrellas PowerPoint Slide
This image slide displays two blue piggy banks with yellow color umbrella. This image slide may be used in your presentations to express views on finance, savings, protection and accounting business finance. Create wonderful presentations using this image slide.

Stock Photo Earth Globe Covered Chain And Lock Image Graphics For PowerPoint Slide
This image slide has been designed with graphic of blue colored globe locked with chains. This image displays the concept of earth safety and protection. Create eye-catching presentations using this image.

Stock Photo Globe And Chain For Safety Image Graphics For PowerPoint Slide
This image slide has been designed with graphic of blue colored globe locked with chains. This image displays the concept of earth safety and protection. Create eye-catching presentations using this image.
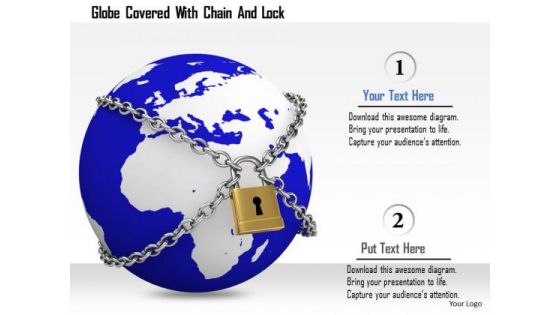
Stock Photo Globe Covered With Chain And Lock Image Graphics For PowerPoint Slide
This image slide has been designed with graphic of blue colored globe locked with chains. This image displays the concept of earth safety and protection. Create eye-catching presentations using this image.
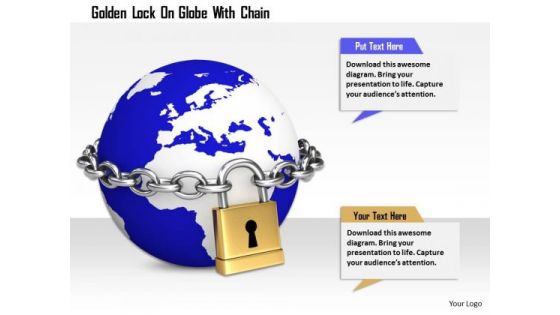
Stock Photo Golden Lock On Globe With Chian Image Graphics For PowerPoint Slide
This image slide has been designed with graphic of blue colored globe locked with chains. This image displays the concept of earth safety and protection. Create eye-catching presentations using this image.
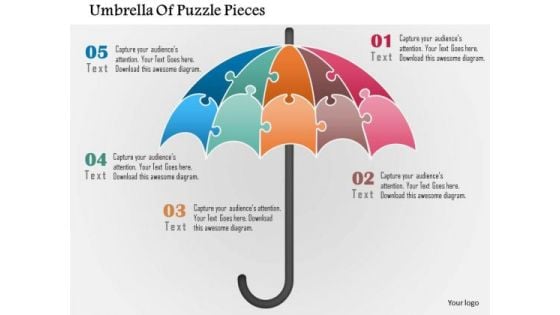
Business Diagram Umbrella Of Puzzle Pieces Presentation Template
Colorful umbrella graphics has been used to design this power point template. This business diagram contains the concept of safety and protection. Use this template to illustrate what you say.
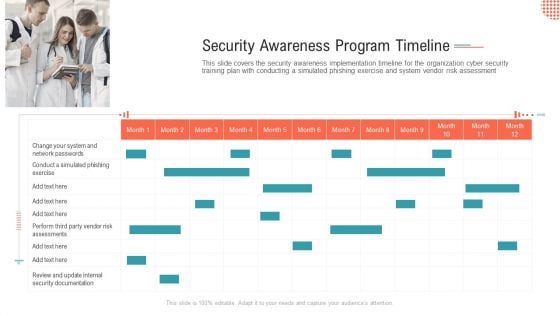
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Process To Manage Firms Sensitive Data Mockup PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Boost your pitch with our creative Information Security Process To Manage Firms Sensitive Data Mockup PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
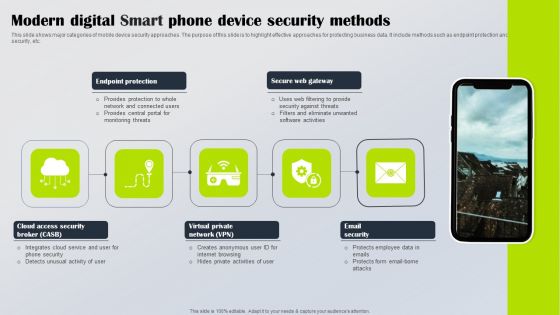
Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
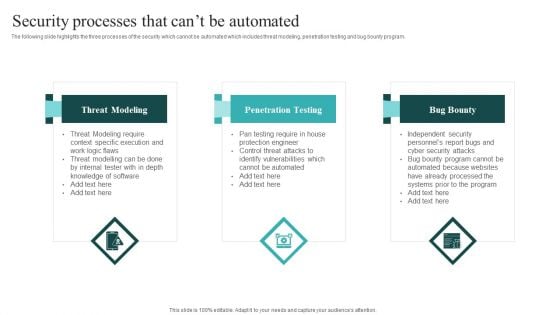
IT Security Automation Systems Guide Security Processes That Cant Be Automated Portrait PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Find highly impressive IT Security Automation Systems Guide Security Processes That Cant Be Automated Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IT Security Automation Systems Guide Security Processes That Cant Be Automated Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
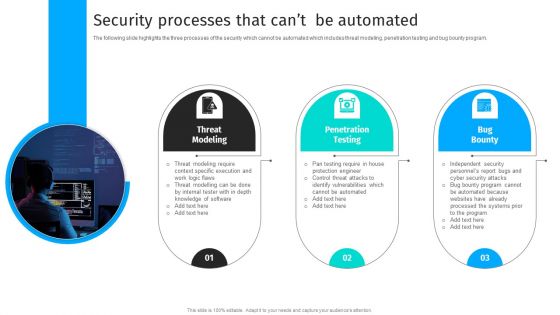
Security Automation To Analyze And Mitigate Cyberthreats Security Processes That Cant Clipart PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program.Explore a selection of the finest Security Automation To Analyze And Mitigate Cyberthreats Security Processes That Cant Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Automation To Analyze And Mitigate Cyberthreats Security Processes That Cant Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, iot-based attack, malware etc. Do you know about Slidesgeeks Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

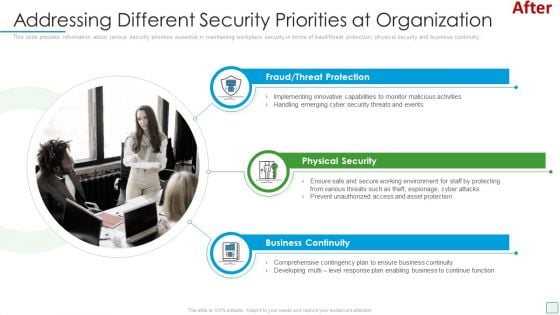
Developing Firm Security Strategy Plan Addressing Different Security Priorities At Organization Background PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of fraud or threat protection, physical security and business continuity. This is a developing firm security strategy plan addressing different security priorities at organization background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fraud or threat protection, physical security, business continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
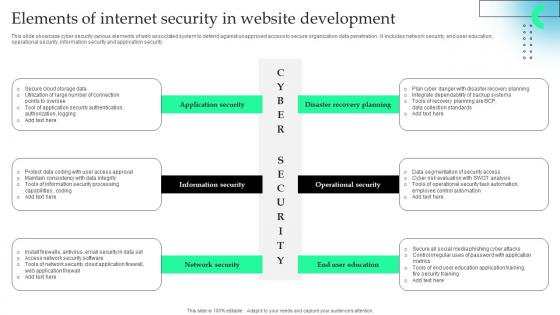
Elements Of Internet Security In Website Development Formats Pdf
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.
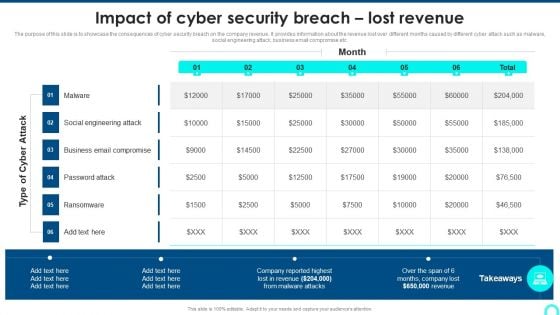
Impact Of Cyber Security Breach Lost Revenue Portrait PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Deliver an awe inspiring pitch with this creative Impact Of Cyber Security Breach Lost Revenue Portrait PDF bundle. Topics like Social Engineering, Password Attack, Ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
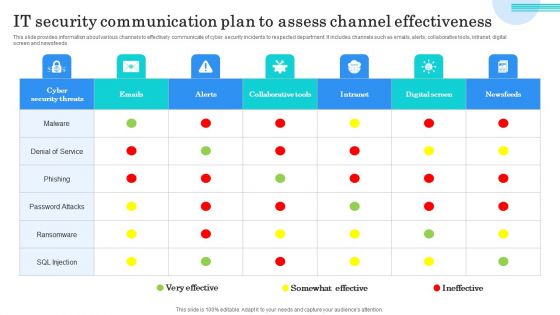
IT Security Communication Plan To Assess Channel Effectiveness Themes PDF
This slide provides information about various channels to effectively communicate of cyber security incidents to respected department. It includes channels such as emails, alerts, collaborative tools, intranet, digitalscreen and newsfeeds. Showcasing this set of slides titled IT Security Communication Plan To Assess Channel Effectiveness Themes PDF. The topics addressed in these templates are Denial Service, Phishing, Password Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
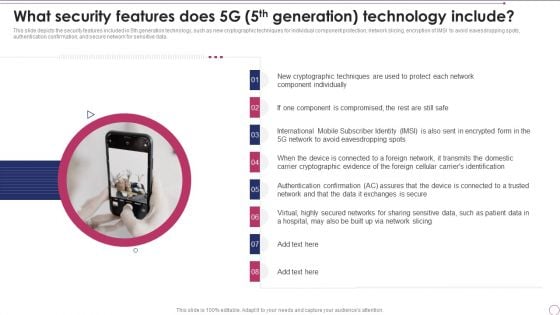
1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Presenting 1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Cryptographic Evidence, Domestic, Via Network Slicing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CASB 2 0 IT Cloud Access Security Broker Pillar Data Security
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. The CASB 2 0 IT Cloud Access Security Broker Pillar Data Security is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen.

Application Security Case Study Kroll Application Security Testing
This slide highlights the overview of the company, problems faced, and their related solutions in the case study. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Application Security Case Study Kroll Application Security Testing for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights the overview of the company, problems faced, and their related solutions in the case study.

IT Security Hacker Hacking Of Email Domain Inspiration PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers.This is a IT Security Hacker Hacking Of Email Domain Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like After Entering, Passwords And Other, Technological Upgrades. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
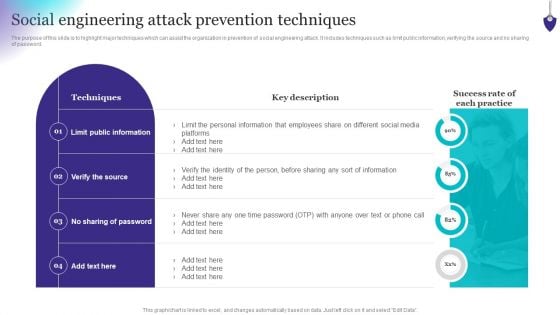
Organizing Security Awareness Social Engineering Attack Prevention Techniques Rules PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Want to ace your presentation in front of a live audience Our Organizing Security Awareness Social Engineering Attack Prevention Techniques Rules PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
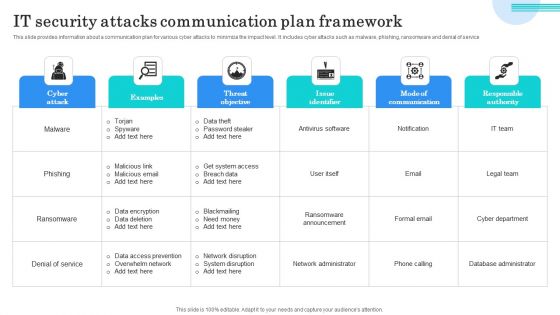
IT Security Attacks Communication Plan Framework Graphics PDF
This slide provides information about a communication plan for various cyber attacks to minimize the impact level. It includes cyber attacks such as malware, phishing, ransomware and denial of service. Showcasing this set of slides titled IT Security Attacks Communication Plan Framework Graphics PDF. The topics addressed in these templates are Data Theft, Password Stealer, Get System Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icon Showcasing Security Network Analysis Structure Pdf
Pitch your topic with ease and precision using this Icon Showcasing Security Network Analysis Structure Pdf This layout presents information on Icon Showcasing Security, Network Analysis It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Icon Showcasing Security Network Analysis Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
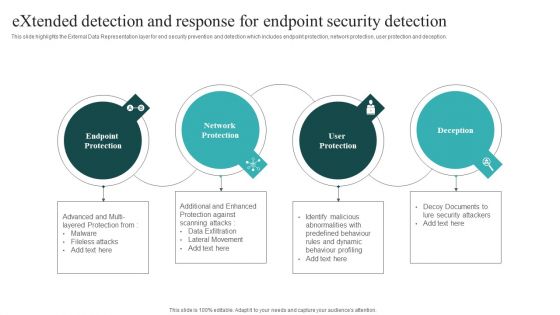
Extended Detection And Response For Endpoint Security Detection Themes PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Boost your pitch with our creative Extended Detection And Response For Endpoint Security Detection Themes PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Links Of Chain Security PowerPoint Templates And PowerPoint Themes 1012
Links Of Chain Security PowerPoint Templates And PowerPoint Themes 1012-Use this Template to elaborate the concept of security using this chain. Security in one's life is essential whether it Get on the boat with our Links Of Chain Security PowerPoint Templates And PowerPoint Themes 1012. Set sail for the port of success.
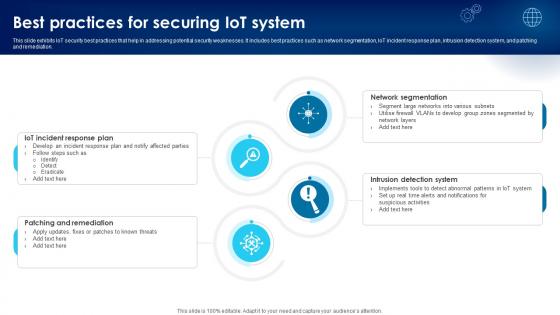
Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V
This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation.

Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V
This slide includes IoT security breaches impact on an organisations operational capabilities, hindering the ability to function properly. It includes impacts such as financial burden, operations disruptions, and reputational damage. Create an editable Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide includes IoT security breaches impact on an organisations operational capabilities, hindering the ability to function properly. It includes impacts such as financial burden, operations disruptions, and reputational damage.

Private Knowledge Security PowerPoint Template 1110
3d illustration of a large brass key inserted into a human brain on a gray reflective surface Fresh concepts are ever evolving. Help the audience absorb them with our Private Knowledge Security PowerPoint Template 1110.


 Continue with Email
Continue with Email

 Home
Home


































