Computer Virus

IT Consultancy Services Company Profile Company Introduction And Its Core Values Sample PDF
This slide focuses on detailed company introduction which includes founded year, industry, headquarters and specialities with core values such as sustainability, honesty, integrity, ethical, innovation and authenticity.Presenting IT Consultancy Services Company Profile Company Introduction And Its Core Values Sample PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Sustainability, Authenticity, Innovation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
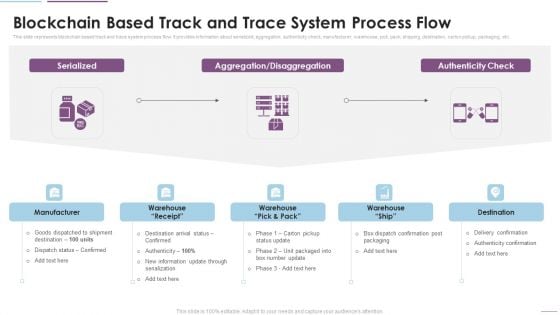
Supply Chain Management Blockchain Based Track And Trace System Process Flow Graphics PDF
This slide represents blockchain based track and trace system process flow. It provides information about serialized, aggregation, authenticity check, manufacturer, warehouse, pick, pack, shipping, destination, carton pickup, packaging, etc. Presenting Supply Chain Management Blockchain Based Track And Trace System Process Flow Graphics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Authenticity Check, Manufacturer, Serialized. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing 5G Wireless Cellular Network Determine Identity And Access Management With 5G Download PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. This is a Developing 5G Wireless Cellular Network Determine Identity And Access Management With 5G Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 5G Identifiers, 5G Authentication . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Brand Promotion Communication Strategy Techniques To Improve Brand Communication Microsoft PDF
This slide covers various tactics to enhance the brand communication process. It includes techniques such as authentic communication strategy, showcasing brand personality, maintaining transparency, and providing solutions to customers problems. Presenting Brand Promotion Communication Strategy Techniques To Improve Brand Communication Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authentic Communication Strategy, Showcase Brand Personality, Maintain Transparency. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
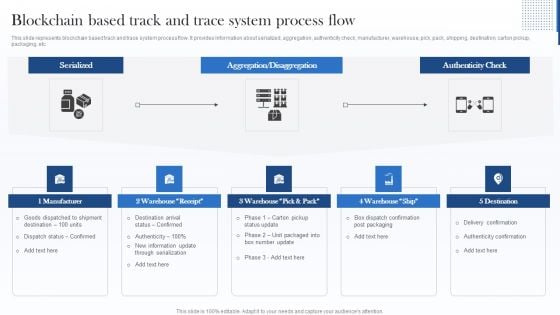
Blockchain Based Track And Trace System Process Flow Professional PDF
This slide represents blockchain based track and trace system process flow. It provides information about serialized, aggregation, authenticity check, manufacturer, warehouse, pick, pack, shipping, destination, carton pickup, packaging, etc. Presenting Blockchain Based Track And Trace System Process Flow Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Delivery Confirmation, Authenticity Confirmation, Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Different Supportive Leadership Models Deployed In Organization Guidelines PDF
This slide covers four types of leadership models and description of its working. It involves four models such as authoritative model, authentic exec, coaching leader and group think model. Pitch your topic with ease and precision using this Different Supportive Leadership Models Deployed In Organization Guidelines PDF. This layout presents information on Leadership Models, Authoritative Model, Authentic Exec. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
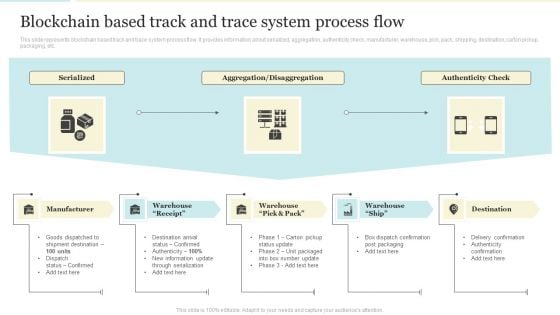
Blockchain Based Track And Trace System Process Flow Diagrams PDF
This slide represents blockchain based track and trace system process flow. It provides information about serialized, aggregation, authenticity check, manufacturer, warehouse, pick, pack, shipping, destination, carton pickup, packaging, etc. This is a Blockchain Based Track And Trace System Process Flow Diagrams PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Manufacturer, Destination, Authenticity Check. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
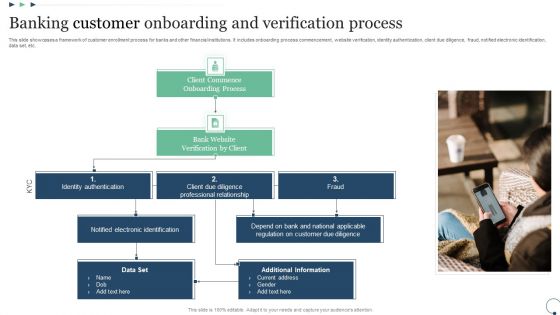
Banking Customer Onboarding And Verification Process Guidelines PDF
This slide showcases a framework of customer enrollment process for banks and other financial institutions. It includes onboarding process commencement, website verification, identity authentication, client due diligence, fraud, notified electronic identification, data set, etc. Presenting Banking Customer Onboarding And Verification Process Guidelines PDF to dispense important information. This template comprises Three stages. It also presents valuable insights into the topics including Client Commence, Bank Website, Identity Authentication. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
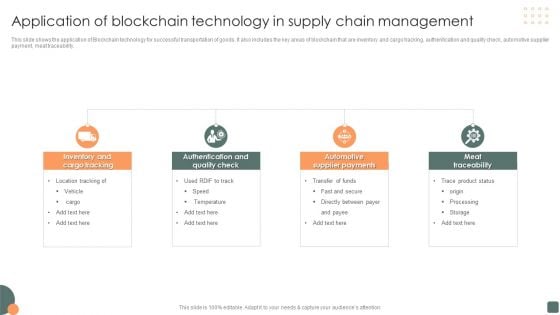
Application Of Blockchain Technology In Supply Chain Management Introduction PDF
This slide shows the application of Blockchain technology for successful transportation of goods. It also includes the key areas of blockchain that are inventory and cargo tracking, authentication and quality check, automotive supplier payment, meat traceability. Persuade your audience using this Application Of Blockchain Technology In Supply Chain Management Introduction PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Inventory And Cargo Tracking, Authentication And Quality Check, Automotive Supplier Payments. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
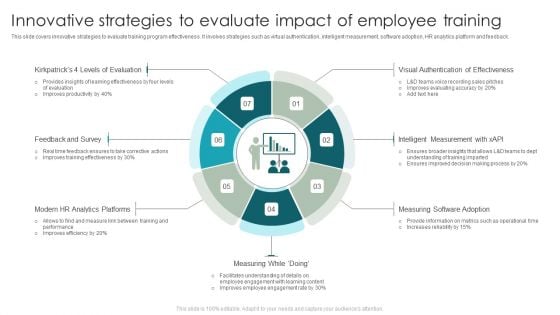
Innovative Strategies To Evaluate Impact Of Employee Training Microsoft PDF
This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback. Persuade your audience using this Innovative Strategies To Evaluate Impact Of Employee Training Microsoft PDF. This PPT design covers Seven stages, thus making it a great tool to use. It also caters to a variety of topics including Feedback And Survey, Measuring Software Adoption, Visual Authentication Of Effectiveness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Three Ways To Decrease Digital Email Bounce Professional PDF
This slide shows various ways which can be used to reduce email bounce rate of the company. It covers points such as maintain email list hygiene, domain authentication and monitor email analytics. Presenting Three Ways To Decrease Digital Email Bounce Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Domain Authentication, Monitor Email Analytics, Maintain Email List Hygiene. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
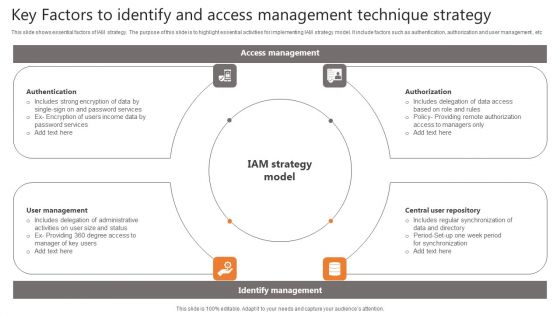
Key Factors To Identify And Access Management Technique Strategy Elements PDF
This slide shows essential factors of IAM strategy. The purpose of this slide is to highlight essential activities for implementing IAM strategy model. It include factors such as authentication, authorization and user management , etc Persuade your audience using this Key Factors To Identify And Access Management Technique Strategy Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Management, Repository. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
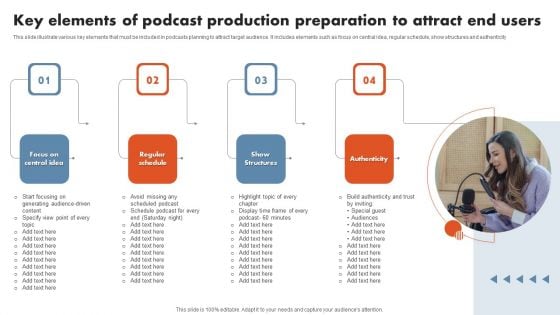
Key Elements Of Podcast Production Preparation To Attract End Users Demonstration PDF
This slide illustrate various key elements that must be included in podcasts planning to attract target audience. It includes elements such as focus on central idea, regular schedule, show structures and authenticity. Presenting Key Elements Of Podcast Production Preparation To Attract End Users Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Authenticity, Show Structures, Regular Schedule. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
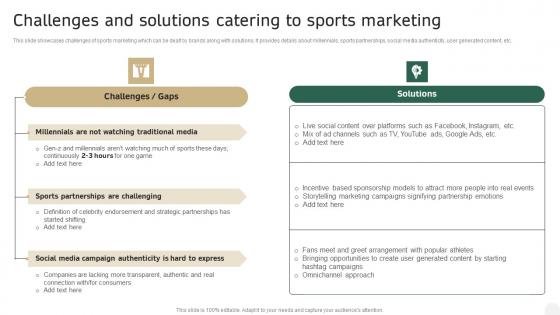
Challenges And Solutions Catering To Sports Marketing In Depth Campaigning Guide Rules PDF
This slide showcases challenges of sports marketing which can be dealt by brands along with solutions. It provides details about millennials, sports partnerships, social media authenticity, user generated content, etc. There are so many reasons you need a Challenges And Solutions Catering To Sports Marketing In Depth Campaigning Guide Rules PDF The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases challenges of sports marketing which can be dealt by brands along with solutions. It provides details about millennials, sports partnerships, social media authenticity, user generated content, etc.
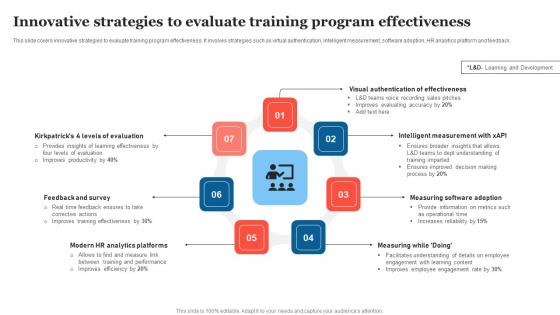
Innovative Strategies To Evaluate Strategic Measures To Boost Employee Efficienc Background Pdf
This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback. There are so many reasons you need a Innovative Strategies To Evaluate Strategic Measures To Boost Employee Efficienc Background Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback.

Solution Customer Engagement Platform Business Model BMC SS V
This slide provides various solutions addressed by our company in order to overcome problems such as user authentication, collaboration platform, sales process automation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Customer Engagement Platform Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides various solutions addressed by our company in order to overcome problems such as user authentication, collaboration platform, sales process automation, etc.

Solution Cloud Based CRM Business Model BMC SS V
This slide provides various solutions addressed by our company in order to overcome problems such as user authentication, collaboration platform, sales process automation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Cloud Based CRM Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides various solutions addressed by our company in order to overcome problems such as user authentication, collaboration platform, sales process automation, etc.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
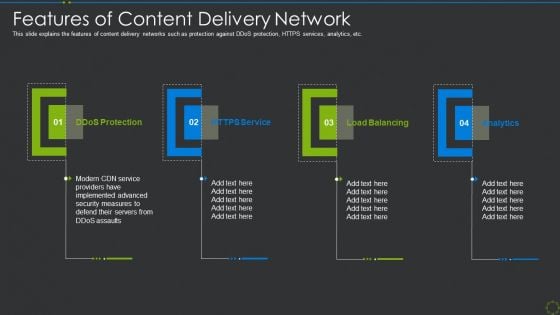
Features Of Content Delivery Network Ppt Outline Vector PDF
This slide explains the features of content delivery networks such as protection against DDoS protection, HTTPS services, analytics, etc. Presenting features of content delivery network ppt outline vector pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like ddos protection, https service, load balancing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
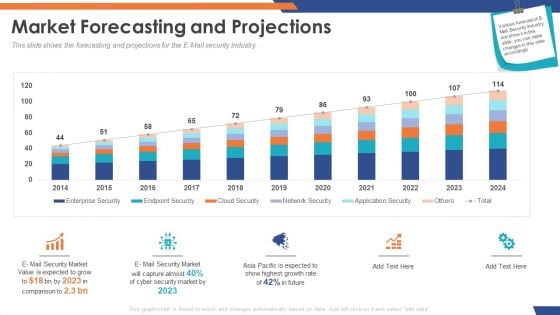
Email Security Market Research Report Market Forecasting And Projections Infographics PDF
Presenting this set of slides with name email security market research report market forecasting and projections infographics pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
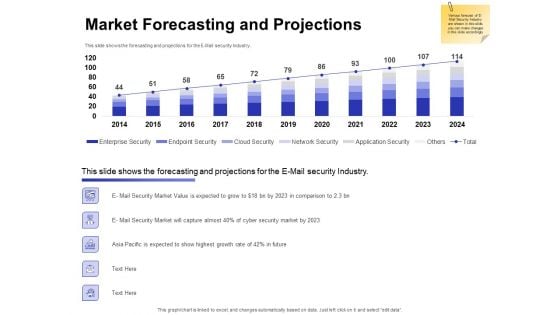
Global Cloud Based Email Security Market Market Forecasting And Projections Professional PDF
Presenting this set of slides with name global cloud based email security market market forecasting and projections professional pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cybersecurity Key Elements Of Electronic Information Security Ppt Styles Smartart PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a cybersecurity key elements of electronic information security ppt styles smartart pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Green Globe Environment PowerPoint Template 0810
Globe on plant representing environmental protection concept Europe version Air your ideas on our Green Globe Environment PowerPoint Template 0810. They will reach the furthest corners.

Green Planet Environment PowerPoint Template 0810
concept for earth protection. green planet on white background Recieve bountiful returns with our Green Planet Environment PowerPoint Template 0810. Get abundant applause from the audience.

Balance Globe On Finger Earth PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with hands and earth symbol of environmental protection Encourage your community to take action. Get them to back the cause you champion.
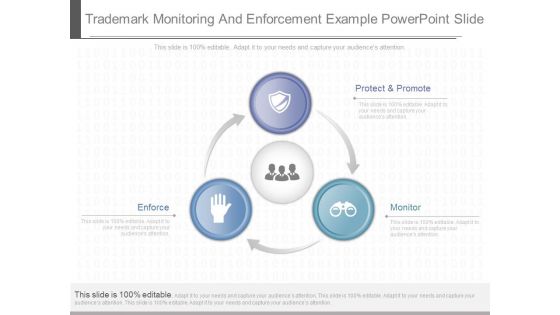
Trademark Monitoring And Enforcement Example Powerpoint Slide
This is a trademark monitoring and enforcement example powerpoint slide. This is a three stage process. The stages in this process are protect and promote, enforce, monitor.
Life Insurance Marketing Plan Template Ppt Summary
This is a life insurance marketing plan template ppt summary. This is a five stage process. The stages in this process are safety, help, confidence, protection, coverage.

Sample Of Information Filtering Template Presentation Examples
This is a sample of information filtering template presentation examples. This is a five stage process. The stages in this process are coverage, protection, intelligence, reliability, performance.
Company Overview Template 2 Ppt PowerPoint Presentation Graphics
This is a company overview template 2 ppt powerpoint presentation graphics. This is a four stage process. The stages in this process are build, connect, power, protect.

Hands Parrying Over Bible Ppt PowerPoint Presentation Pictures Slide Portrait
This is a hands parrying over bible ppt powerpoint presentation pictures slide portrait. This is a one stage process. The stages in this process are protection, blessing, favor.

Ethics To Layout Workplace Guidelines Ideas PDF
This slide conveys office ethics for outlining guidelines aimed at developing code of conduct to inform members of ethical responsibilities. It covers data protection, workplace diversity, whistleblower protection, transparency and compensation. Presenting Ethics To Layout Workplace Guidelines Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Protection, Workplace Diversity, Whistleblower Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF
The following slide highlights key responsibilities of the digitization of security systems team with the position level and requirements. The various positions mentioned in the slide are security engineer, senior security engineer, distinguished security engineer and digitization of security systems manager. Showcasing this set of slides titled Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF. The topics addressed in these templates are Security Engineer, Senior Security Engineer, Security Automation Manager. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
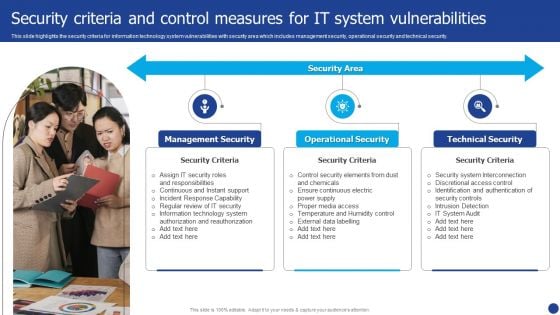
Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
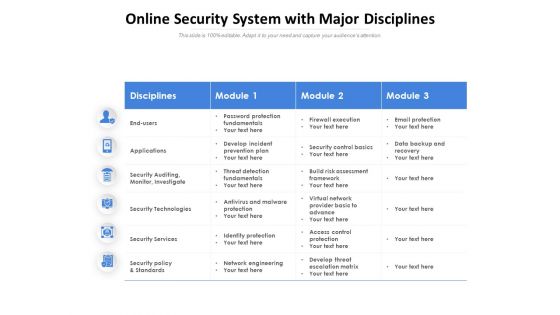
Online Security System With Major Disciplines Ppt PowerPoint Presentation Ideas Inspiration PDF
Presenting this set of slides with name online security system with major disciplines ppt powerpoint presentation ideas inspiration pdf. The topics discussed in these slides are disciplines, module, applications, security auditing, monitor, investigate, security technologies, security services, security policy and standards. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
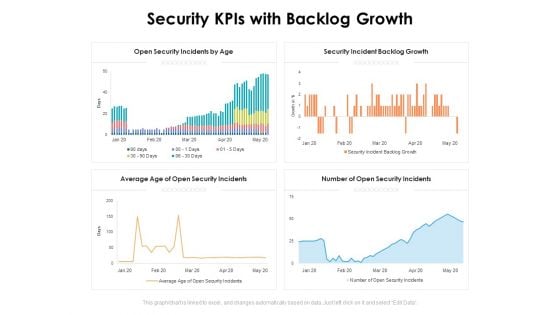
Security Kpis With Backlog Growth Ppt PowerPoint Presentation Inspiration Ideas PDF
Presenting this set of slides with name security kpis with backlog growth ppt powerpoint presentation inspiration ideas pdf. The topics discussed in these slides are open security incidents by age, security incident backlog growth, number of open security incidents, average age of open security incidents. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
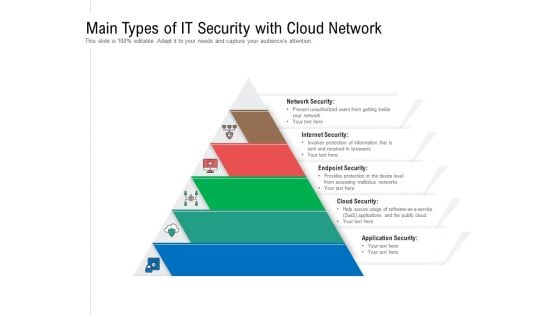
Main Types Of IT Security With Cloud Network Ppt PowerPoint Presentation Gallery Design Ideas PDF
Persuade your audience using this main types of it security with cloud network ppt powerpoint presentation gallery design ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including network security, internet security, endpoint security, cloud security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. Presenting Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Security Policy, Asset Management, Physical And Environmental Security, Operational Security, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
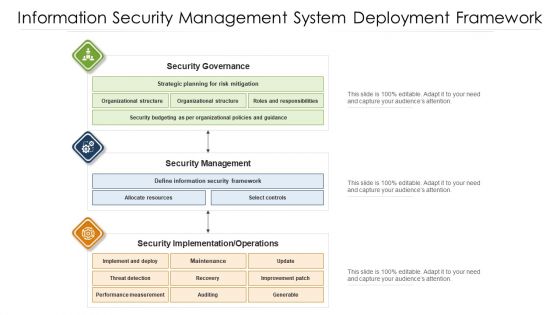
Information Security Management System Deployment Framework Ppt PowerPoint Presentation File Structure PDF
Showcasing this set of slides titled information security management system deployment framework ppt powerpoint presentation file structure pdf. The topics addressed in these templates are security management, security governance, security implementation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
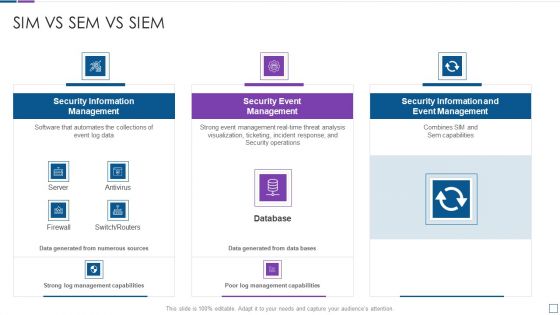
Real Time Assessment Of Security Threats Sim Vs Sem Vs SIEM Diagrams PDF
Deliver an awe inspiring pitch with this creative real time assessment of security threats sim vs sem vs siem diagrams pdf bundle. Topics like security information management, security event management, security information and event management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
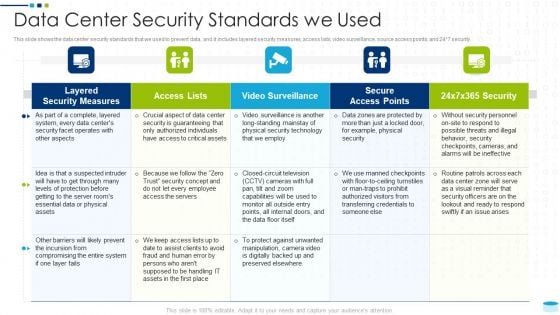
Data Center Infrastructure Management IT Data Center Security Standards We Used Professional PDF
This slide shows the data center security standards that we used to prevent data, and it includes layered security measures, access lists, video surveillance, source access points, and 24 7 security. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it data center security standards we used professional pdf. Use them to share invaluable insights on layered security measures, access lists, video surveillance, secure access points, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
International Organization Standardization 270001 Security Domains That Will Be Addressed By Isms Icons PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a international organization standardization 270001 security domains that will be addressed by isms icons pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization of information security, human resources security, asset management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
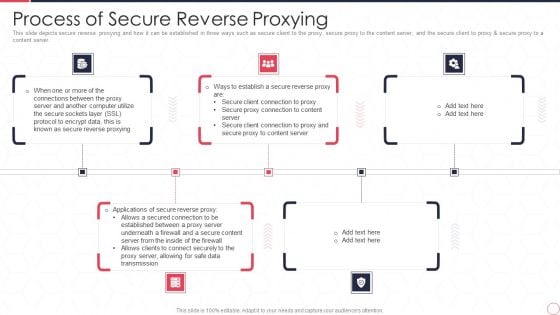
Reverse Proxy Server IT Process Of Secure Reverse Proxying Ppt Slides Mockup PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Presenting reverse proxy server it process of secure reverse proxying ppt slides mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like proxy server, data transmission, secure content server. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
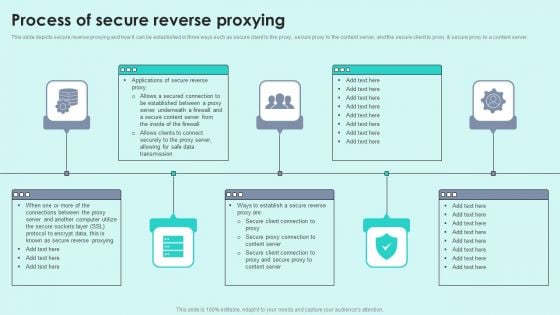
Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy secure proxy to a content server.This is a Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secured Connection, Established Between, Underneath Firewall. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
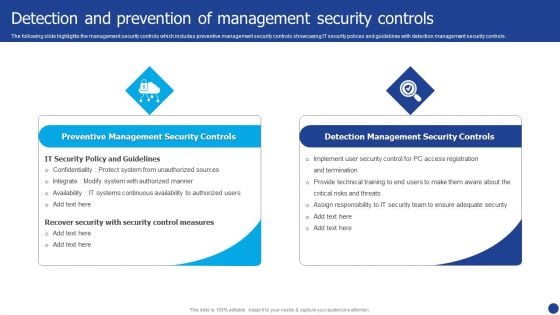
Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Presenting Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Preventive Management Security Controls, Detection Management Security Controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
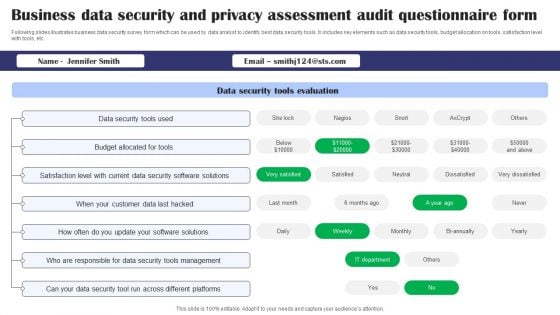
Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS
Following slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Showcasing this set of slides titled Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS. The topics addressed in these templates are Data Security Tools Evaluation, Data Security Tools Used, Budget Allocated For Tools, Data Security Software Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Strategic Tips To Improve Physical Data Center Management Security Download PDF
This slide highlights tips to improve security of physical datacentre by having a thorough understanding of security measures and service level agreements. It covers secure location, physical access controls with building management security. Presenting Strategic Tips To Improve Physical Data Center Management Security Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Location, Physical Access Controls, Secure Building Management Systems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Information Technology Security Ppt File Mockup PDF
Presenting table of contents for information technology security ppt file mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security implementation, managing it security, it security budget, it security roadmap timeline . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Info Security Ppt PowerPoint Presentation File Sample PDF
Presenting table of contents for info security ppt powerpoint presentation file sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like managing information security, information security budget, information security roadmap timeline, information security implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
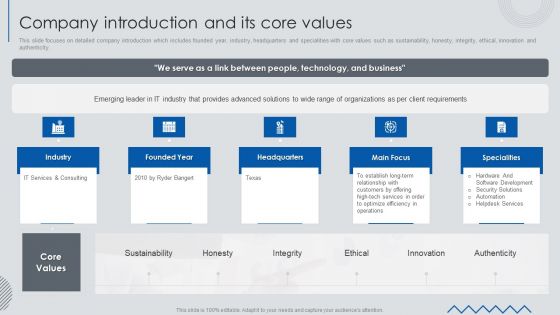
Information Technology Solutions Business Profile Company Introduction And Its Core Values Infographics PDF
This slide focuses on detailed company introduction which includes founded year, industry, headquarters and specialities with core values such as sustainability, honesty, integrity, ethical, innovation and authenticity.Presenting Information Technology Solutions Business Profile Company Introduction And Its Core Values Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Software Development, Security Solutions, Customers Offering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
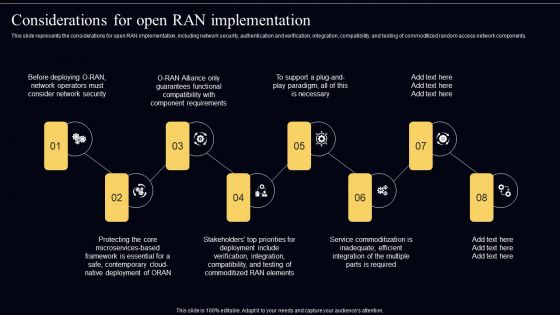
Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Boost your pitch with our creative Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Solutions To Overcome Various Personal Banking Relationship Challenges Structure PDF
This slide signifies the solutions to overcome various banking relationship challenges. It covers information about challenges like security breach, regulatory compliance and changing business model with implemented strategies to overcome.Presenting Solutions To Overcome Various Personal Banking Relationship Challenges Structure PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Regulatory Compliance, Changing Business, Authentication System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
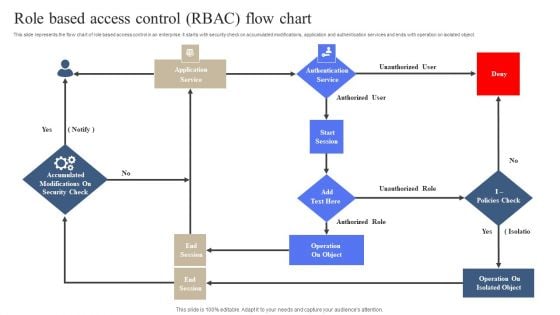
Role Based Access Control RBAC Flow Chart Slides PDF
This slide represents the flow chart of role based access control in an enterprise. It starts with security check on accumulated modifications, application and authentication services and ends with operation on isolated object. Persuade your audience using this Role Based Access Control RBAC Flow Chart Slides PDF. This PPT design covers One stage, thus making it a great tool to use. It also caters to a variety of topics including Operation On Object, Operation On Isolated Object. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
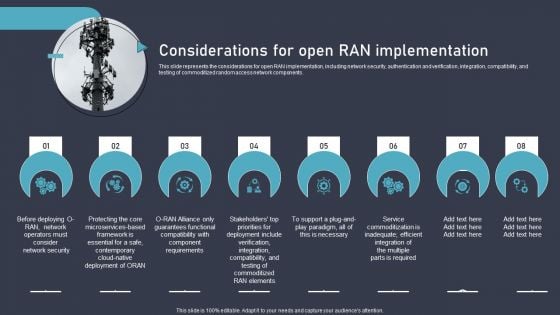
O RAN Architecture Considerations For Open Ran Implementation Brochure PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Create an editable O RAN Architecture Considerations For Open Ran Implementation Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. O RAN Architecture Considerations For Open Ran Implementation Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
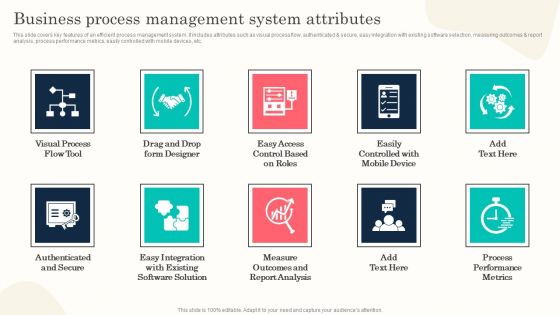
Business Process Management System Attributes Formats PDF
This slide covers key features of an efficient process management system. It includes attributes such as visual process flow, authenticated and secure, easy integration with existing software selection, measuring outcomes and report analysis, process performance metrics, easily controlled with mobile devices, etc. There are so many reasons you need a Business Process Management System Attributes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF
This slide depicts the career opportunities in cybersecurity, including various job roles such as chief information security officer, chief security office, security engineers, architects, analysts and penetration testers. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Google Cloud Console IT Google Cloud Services Identity And Security Ppt Icon Graphics Design PDF
This slide describes the identity and security service of Google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security. This is a google cloud console it google cloud services identity and security ppt icon graphics design pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cloud resource manager, cloud platform security, cloud security scanner, cloud iam. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
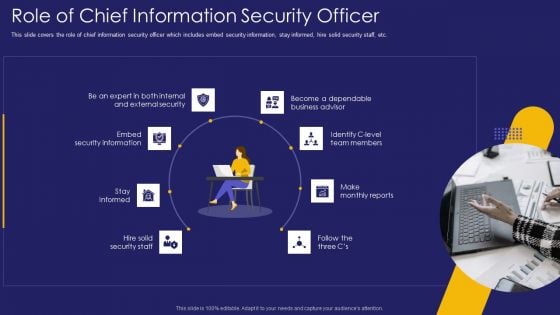
Role IT Team Digital Transformation Role Of Chief Information Security Officer Summary PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting role it team digital transformation role of chief information security officer summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like security information, security staff, monthly reports. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
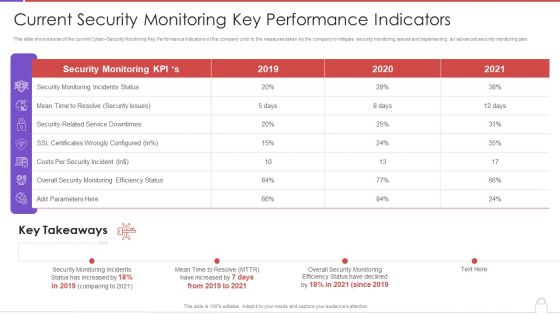
Methods To Develop Advanced Current Security Monitoring Key Performance Indicators Formats PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative methods to develop advanced current security monitoring key performance indicators formats pdf bundle. Topics like monitoring incidents status, security issues, costs per security incident, 2019 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
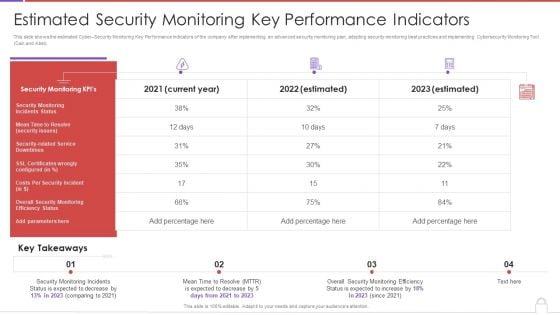
Methods To Develop Advanced Estimated Security Monitoring Key Performance Indicators Structure PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver an awe inspiring pitch with this creative methods to develop advanced estimated security monitoring key performance indicators structure pdf bundle. Topics like security monitoring kpis, costs per security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
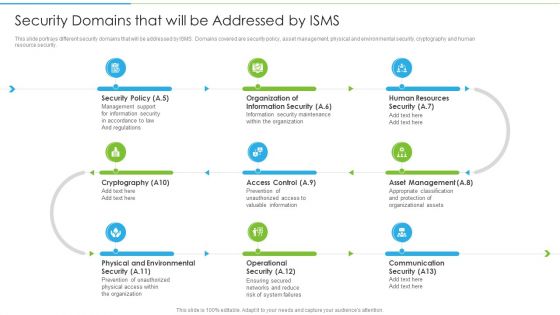
Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policy, Organization Information, Human Resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































