Computer Virus
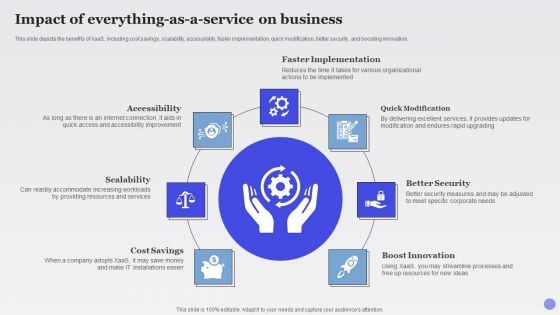
Impact Of Everything As A Service On Business Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Grid PDF
This slide depicts the benefits of XaaS, including cost savings, scalability, accessibility, faster implementation, quick modification, better security, and boosting innovation.This is a Impact Of Everything As A Service On Business Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Grid PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Faster Implementation, Quick Modification, Boost Innovation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Features And Benefits Of Cloud Project Management Integrating Cloud Computing To Enhance Projects Effectiveness Inspiration PDF
The following slide depicts major features and benefits of cloud based project management. It provides details about reliability, integration, collaboration, secure backup, free monthly trials, remote team support, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Features And Benefits Of Cloud Project Management Integrating Cloud Computing To Enhance Projects Effectiveness Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
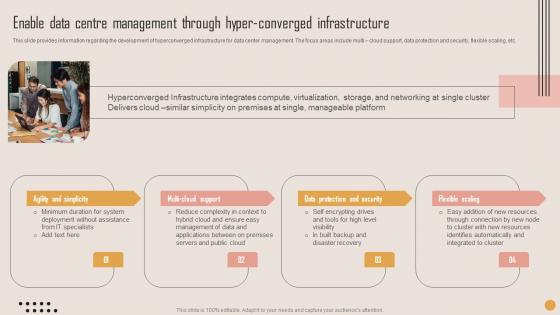
Enable Data Centre Management Playbook For Strategic Actions To Improve IT Performance Structure Pdf
This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Enable Data Centre Management Playbook For Strategic Actions To Improve IT Performance Structure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Enable Data Centre Management Playbook For Strategic Actions To Improve IT Performance Structure Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc.

Mesh Computing Technology Hybrid Vs Private Vs Public And Iaas Vs Paas Vs Saas Workplan Ppt PowerPoint Presentation Complete Deck With Slides
Mesh Computing Technology Hybrid Vs Private Vs Public And Iaas Vs Paas Vs Saas Workplan, Service, Security, Management
Cyber Crime Security PowerPoint Template 0810
An open door with hands holding guns surrounded by words like cyber-crime stolen identity virus phishing and security Carry your team with our Cyber Crime Security PowerPoint Template 0810. You will come out on top.
Password Manager Mac In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Password Manager Mac In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Password Manager Mac that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Password Manager Mac In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Password Manager Comparison In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Password Manager Comparison In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Password Manager Comparison that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Password Manager Comparison In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Tips Keeping Passwords Safe In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Tips Keeping Passwords Safe In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Tips Keeping Passwords Safe that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Tips Keeping Passwords Safe In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf
The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc.
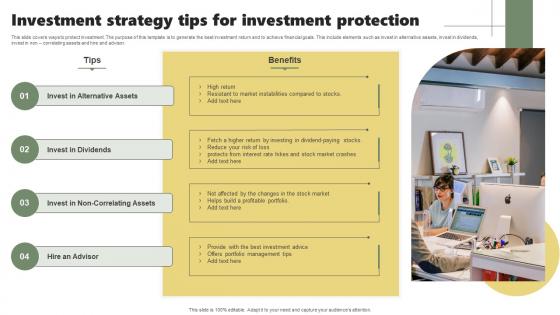
Investment Strategy Tips For Investment Protection Download Pdf
This slide covers ways to protect investment. The purpose of this template is to generate the best investment return and to achieve financial goals. This include elements such as invest in alternative assets, invest in dividends, invest in non correlating assets and hire and advisor. Showcasing this set of slides titled Investment Strategy Tips For Investment Protection Download Pdf. The topics addressed in these templates are Invest Alternative Assets, Invest Dividends, Hire Advisor. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers ways to protect investment. The purpose of this template is to generate the best investment return and to achieve financial goals. This include elements such as invest in alternative assets, invest in dividends, invest in non correlating assets and hire and advisor.
Protection Cell Phones In Powerpoint And Google Slides Cpb
Introducing our well designed Protection Cell Phones In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Protection Cell Phones. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Protection Cell Phones In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
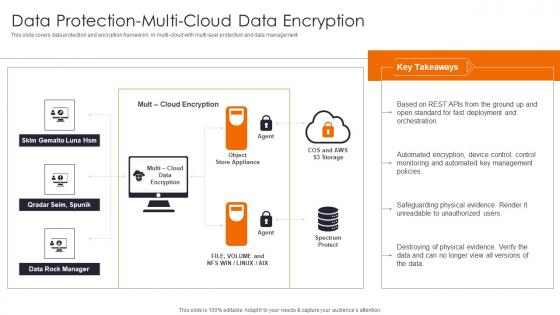
Data Protection Multi Cloud Enhancing Workload Efficiency Through Cloud Architecture Background Pdf
This slide covers data protection and encryption framework in multi cloud with multi layer protection and data management The Data Protection Multi Cloud Enhancing Workload Efficiency Through Cloud Architecture Background Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers data protection and encryption framework in multi cloud with multi layer protection and data management
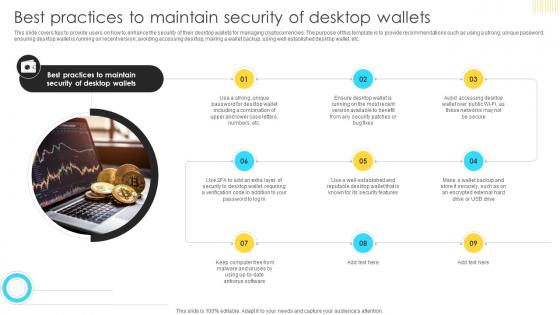
Mastering Blockchain Wallets Best Practices To Maintain Security Of Desktop BCT SS V
This slide covers tips to provide users on how to enhance the security of their desktop wallets for managing cryptocurrencies. The purpose of this template is to provide recommendations such as using a strong, unique password, ensuring desktop wallet is running on recent version, avoiding accessing desktop, making a wallet backup, using well established desktop wallet, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Mastering Blockchain Wallets Best Practices To Maintain Security Of Desktop BCT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Mastering Blockchain Wallets Best Practices To Maintain Security Of Desktop BCT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers tips to provide users on how to enhance the security of their desktop wallets for managing cryptocurrencies. The purpose of this template is to provide recommendations such as using a strong, unique password, ensuring desktop wallet is running on recent version, avoiding accessing desktop, making a wallet backup, using well established desktop wallet, etc.

Bath Staph Infection In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Bath Staph Infection In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Bath Staph Infection that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Bath Staph Infection In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Wisdom Tooth Infection Symptoms In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Wisdom Tooth Infection Symptoms In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Wisdom Tooth Infection Symptoms that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Wisdom Tooth Infection Symptoms In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Virtual Security Hazards And Network Hacking Icon Diagrams Pdf
Pitch your topic with ease and precision using this Virtual Security Hazards And Network Hacking Icon Diagrams Pdf. This layout presents information on Virtual Security, Hazards, Network Hacking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Virtual Security Hazards And Network Hacking Icon Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
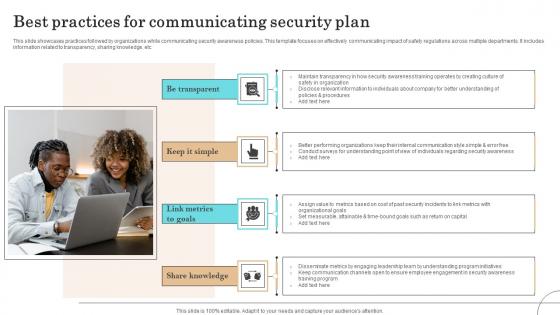
Best Practices For Communicating Security Plan Infographics Pdf
This slide showcases practices followed by organizations while communicating security awareness policies. This template focuses on effectively communicating impact of safety regulations across multiple departments. It includes information related to transparency, sharing knowledge, etc Pitch your topic with ease and precision using this Best Practices For Communicating Security Plan Infographics Pdf This layout presents information on Measurable Attainable, Keep Communication, Maintain Transparency It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases practices followed by organizations while communicating security awareness policies. This template focuses on effectively communicating impact of safety regulations across multiple departments. It includes information related to transparency, sharing knowledge, etc
Security Analytics Use Cases In Powerpoint And Google Slides Cpb
Introducing our well designed Security Analytics Use Cases In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Analytics Use Cases. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Analytics Use Cases In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Gate Icon In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Gate Icon In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Gate Icon that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Gate Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Data Science In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Security Data Science In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Security Data Science. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Security Data Science In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Spyware Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Spyware Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Spyware Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Spyware Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Web Consulting Business Performance Best Practices For Web Security
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Web Consulting Business Performance Best Practices For Web Security a try. Our experts have put a lot of knowledge and effort into creating this impeccable Web Consulting Business Performance Best Practices For Web Security. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup

Digital Security Metrics Used By Threat Analysts Graphics Pdf
Showcasing this set of slides titled Digital Security Metrics Used By Threat Analysts Graphics Pdf The topics addressed in these templates are Regulatory Requirements, Large Increase, Scanning Outweighs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc.
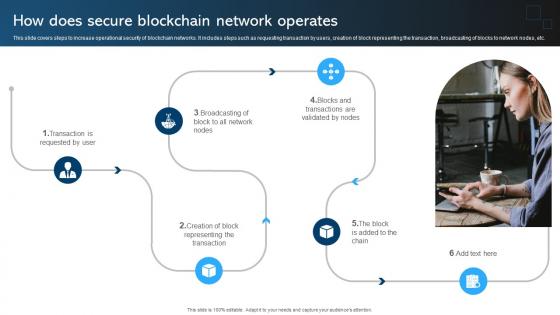
Comprehensive Manual For How Does Secure Blockchain Network Operates BCT SS V
This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc. Create an editable Comprehensive Manual For How Does Secure Blockchain Network Operates BCT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Comprehensive Manual For How Does Secure Blockchain Network Operates BCT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc.

Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc.

Problem Statement Voice Assistance Security Platform Investor Funding Presentation Graphics Pdf
This slide showcases identified problems that are commonly faced by customers. It consists of issues related to customer privacy and data security concerns. Take your projects to the next level with our ultimate collection of Problem Statement Voice Assistance Security Platform Investor Funding Presentation Graphics Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide showcases identified problems that are commonly faced by customers. It consists of issues related to customer privacy and data security concerns.
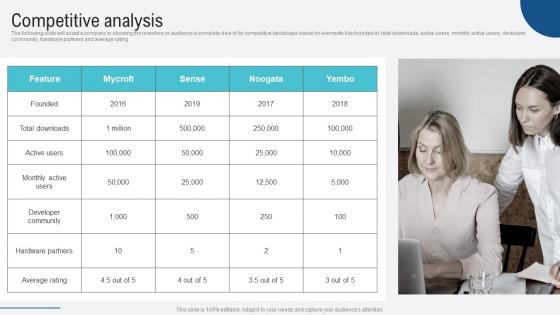
Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf
The following slide will assist a company in showing the investors or audience a complete view of its competitive landscape based on elements like founded in, total downloads, active users, monthly active users, developer community, hardware partners and average rating. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf The following slide will assist a company in showing the investors or audience a complete view of its competitive landscape based on elements like founded in, total downloads, active users, monthly active users, developer community, hardware partners and average rating.

Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name. Make sure to capture your audiences attention in your business displays with our gratis customizable Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name.

Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The following slide showcases various factors that presents how company is becoming a leading in market. It highlights growth rate, current ratio, quick ratio, gross profit, net profit and EPS. Retrieve professionally designed Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide showcases various factors that presents how company is becoming a leading in market. It highlights growth rate, current ratio, quick ratio, gross profit, net profit and EPS.
Fibers IT Photonic Engineer Requirements Professional Experience
This slide depicts the professional experience required to be a photonic engineer that includes the knowledge of computer-aided design and computer-aided manufacturing software for better designing and creating prototypes. Create an editable Fibers IT Photonic Engineer Requirements Professional Experience that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Fibers IT Photonic Engineer Requirements Professional Experience is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide depicts the professional experience required to be a photonic engineer that includes the knowledge of computer-aided design and computer-aided manufacturing software for better designing and creating prototypes.

Mastering Blockchain Wallets Best Practices For Enabling Blockchain Wallet Safety BCT SS V
This slide covers tips for enabling safety of blockchain wallets helping users. The purpose of this template is to provide an overview on key practices to be followed such as keeping small quantities of crypto assets in online, generating impenetrable wallets requiring authentication, ensuring wallet software and mobile is constantly updated, securing wallets with Fort Knox by using complex long form password, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Mastering Blockchain Wallets Best Practices For Enabling Blockchain Wallet Safety BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide covers tips for enabling safety of blockchain wallets helping users. The purpose of this template is to provide an overview on key practices to be followed such as keeping small quantities of crypto assets in online, generating impenetrable wallets requiring authentication, ensuring wallet software and mobile is constantly updated, securing wallets with Fort Knox by using complex long form password, etc.
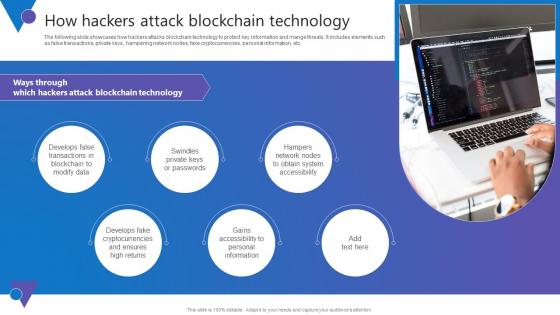
How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc.

Overview And Working Process Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. The Overview And Working Process Comprehensive Guide To Blockchain Digital Security Template Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc.
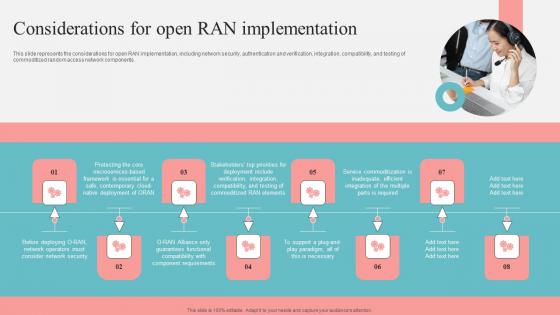
Considerations For Open Ran Implementation Unlocking The Potential Of Open Ran Brochure Pdf
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Considerations For Open Ran Implementation Unlocking The Potential Of Open Ran Brochure Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components.

Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf
The following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc.
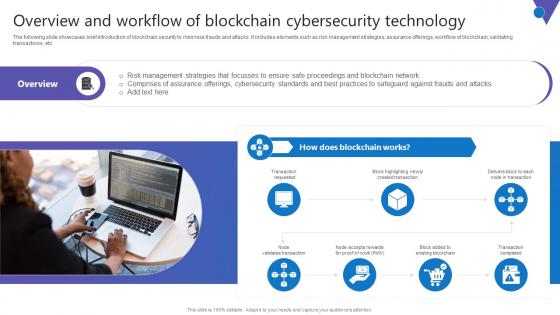
Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Explore a selection of the finest Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc.
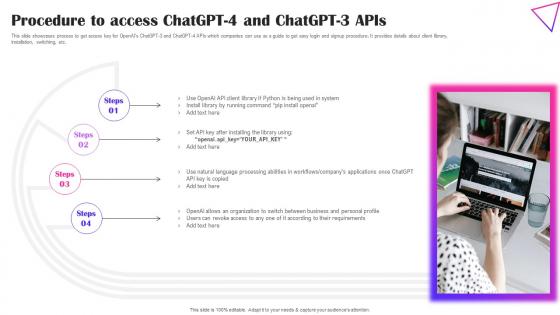
Procedure To Access ChatGPT 4 And ChatGPT Creative Applications For Open AI Professional Pdf
This slide showcases process to get access key for OpenAIs ChatGPT-3 and ChatGPT-4 APIs which companies can use as a guide to get easy login and signup procedure. It provides details about client library, installation, switching, etc. Presenting this PowerPoint presentation, titled Procedure To Access ChatGPT 4 And ChatGPT Creative Applications For Open AI Professional Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Procedure To Access ChatGPT 4 And ChatGPT Creative Applications For Open AI Professional Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Procedure To Access ChatGPT 4 And ChatGPT Creative Applications For Open AI Professional Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide showcases process to get access key for OpenAIs ChatGPT-3 and ChatGPT-4 APIs which companies can use as a guide to get easy login and signup procedure. It provides details about client library, installation, switching, etc.

Methods To Ensure Smart Comprehensive Guide To Blockchain Digital Security Mockup Pdf
The following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. This modern and well arranged Methods To Ensure Smart Comprehensive Guide To Blockchain Digital Security Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc.
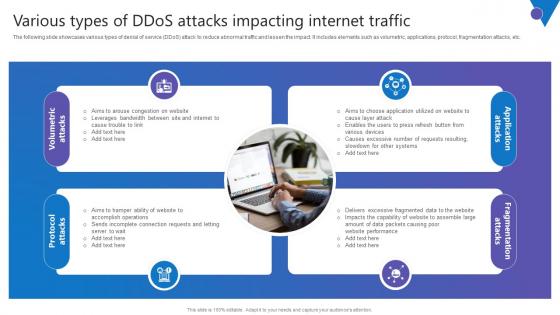
Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Get a simple yet stunning designed Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc.
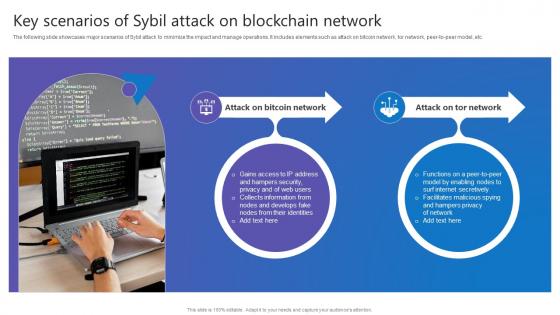
Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc.

Various Types Of Crypto Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. qDo you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Various Types Of Crypto Comprehensive Guide To Blockchain Digital Security Clipart Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Various Types Of Crypto Comprehensive Guide To Blockchain Digital Security Clipart Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc.

Major Cryptocurrency Blockchain Comprehensive Guide To Blockchain Digital Security Download Pdf
The following slide showcases major cryptocurrency and blockchain cybersecurity scams throughout the globe. It includes elements such as Decentralized autonomous organization DAO attack, gox attack, plus token scams, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Major Cryptocurrency Blockchain Comprehensive Guide To Blockchain Digital Security Download Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The following slide showcases major cryptocurrency and blockchain cybersecurity scams throughout the globe. It includes elements such as Decentralized autonomous organization DAO attack, gox attack, plus token scams, etc.
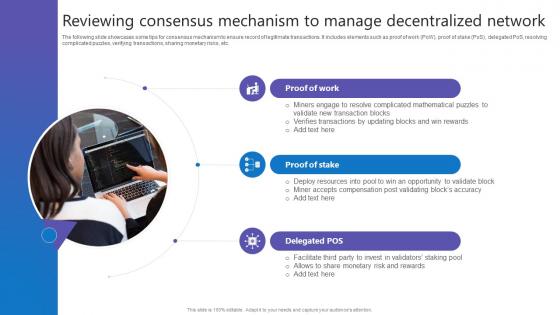
Reviewing Consensus Mechanism Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases some tips for consensus mechanism to ensure record of legitimate transactions. It includes elements such as proof of work PoW, proof of stake PoS, delegated PoS, resolving complicated puzzles, verifying transactions, sharing monetary risks, etc. Find a pre designed and impeccable Reviewing Consensus Mechanism Comprehensive Guide To Blockchain Digital Security Summary Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide showcases some tips for consensus mechanism to ensure record of legitimate transactions. It includes elements such as proof of work PoW, proof of stake PoS, delegated PoS, resolving complicated puzzles, verifying transactions, sharing monetary risks, etc.
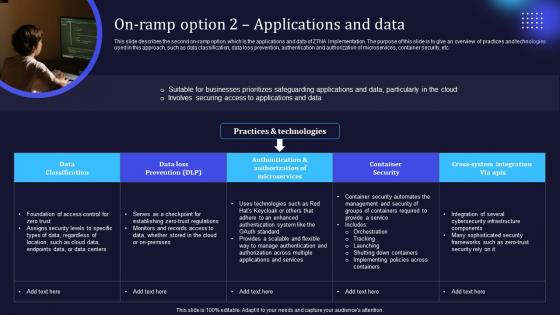
Zero Trust Model On Ramp Option 2 Applications And Data
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks has constructed Zero Trust Model On Ramp Option 2 Applications And Data after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

On Ramp Option 2 Applications And Data Zero Trust Network Access
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks is here to make your presentations a breeze with On Ramp Option 2 Applications And Data Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Take your projects to the next level with our ultimate collection of The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc.
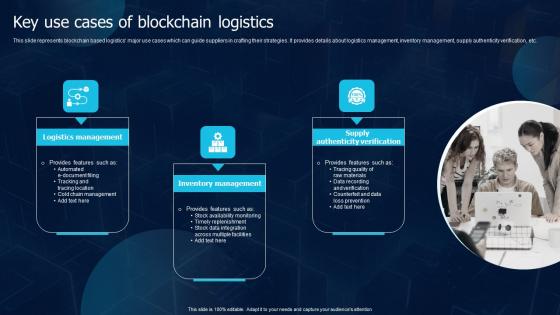
Key Use Cases Of Blockchain Logistics Blockchain Transportation Rules Pdf
This slide represents blockchain based logistics major use cases which can guide suppliers in crafting their strategies. It provides details about logistics management, inventory management, supply authenticity verification, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Use Cases Of Blockchain Logistics Blockchain Transportation Rules Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Use Cases Of Blockchain Logistics Blockchain Transportation Rules Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents blockchain based logistics major use cases which can guide suppliers in crafting their strategies. It provides details about logistics management, inventory management, supply authenticity verification, etc.
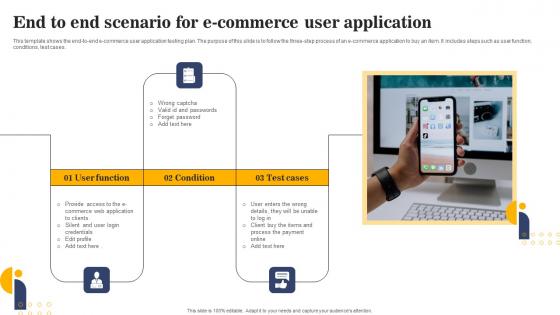
End To End Scenario For E Commerce User Application Elements Pdf
This template shows the end-to-end e-commerce user application testing plan. The purpose of this slide is to follow the three-step process of an e-commerce application to buy an item. It includes steps such as user function, conditions, test cases.Showcasing this set of slides titled End To End Scenario For E Commerce User Application Elements Pdf The topics addressed in these templates are Provide Access, Process Payment, Forget Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This template shows the end to end e commerce user application testing plan. The purpose of this slide is to follow the three step process of an e commerce application to buy an item. It includes steps such as user function, conditions, test cases.

Zero Trust Model Zero Trust Network Access Architecture Overview
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Welcome to our selection of the Zero Trust Model Zero Trust Network Access Architecture Overview. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

A49 Zero Trust Network Access Architecture Overview
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Create an editable A49 Zero Trust Network Access Architecture Overview that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. A49 Zero Trust Network Access Architecture Overview is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

Investment Diversification Financial Investment Strategy Topics Pdf
This slide covers investment diversification approaches to protect against risk of inflation, interact rates etc. The key strategies are diversify across asset classes, diversify according to risk tolerance, diversify by location and diversify within asset classes. Pitch your topic with ease and precision using this Investment Diversification Financial Investment Strategy Topics Pdf. This layout presents information on Diversify Across Asset Classes, Diversify Location, Diversify Asset Classes. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide covers investment diversification approaches to protect against risk of inflation, interact rates etc. The key strategies are diversify across asset classes, diversify according to risk tolerance, diversify by location and diversify within asset classes.
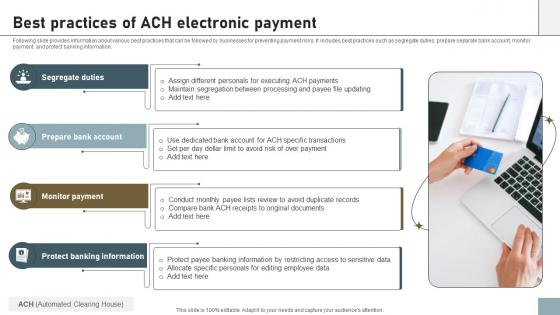
Online Payment Techniques Best Practices Of Ach Electronic Payment
Following slide provides information about various best practices that can be followed by businesses for preventing payment risks. It includes best practices such as segregate duties, prepare separate bank account, monitor payment, and protect banking information. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Online Payment Techniques Best Practices Of Ach Electronic Payment and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates Following slide provides information about various best practices that can be followed by businesses for preventing payment risks. It includes best practices such as segregate duties, prepare separate bank account, monitor payment, and protect banking information.
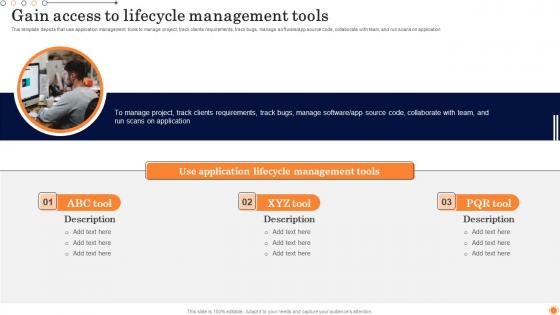
Gain Access To Lifecycle Design And Develop Customized Software Guides Template Pdf
This template depicts that use application management tools to manage project, track clients requirements, track bugs, manage software app source code, collaborate with team, and run scans on application Make sure to capture your audiences attention in your business displays with our gratis customizable Gain Access To Lifecycle Design And Develop Customized Software Guides Template Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This template depicts that use application management tools to manage project, track clients requirements, track bugs, manage software app source code, collaborate with team, and run scans on application
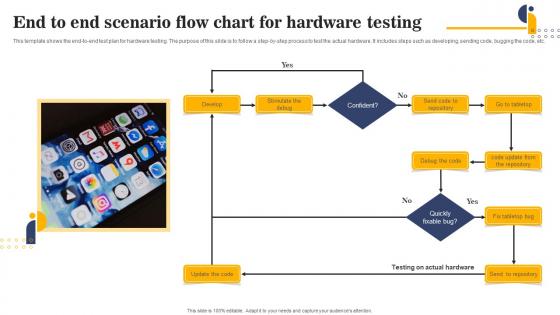
End To End Scenario Flow Chart For Hardware Testing Portrait Pdf
This template shows the end-to-end test plan for hardware testing. The purpose of this slide is to follow a step-by-step process to test the actual hardware. It includes steps such as developing, sending code, bugging the code, etc.Pitch your topic with ease and precision using this End To End Scenario Flow Chart For Hardware Testing Portrait Pdf This layout presents information on End To End, Scenario Flow Chart, Hardware Testing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This template shows the end to end test plan for hardware testing. The purpose of this slide is to follow a step by step process to test the actual hardware. It includes steps such as developing, sending code, bugging the code, etc.

Introduction To Blockchain In Telehealth How Blockchain Is Reshaping BCT SS V
This slide provides an overview of telehealth or telemedicine technology in blockchain based healthcare management systems. Key features include privacy protection, immutable audit trail, patient control, data exchange and data accuracy. If you are looking for a format to display your unique thoughts, then the professionally designed Introduction To Blockchain In Telehealth How Blockchain Is Reshaping BCT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Introduction To Blockchain In Telehealth How Blockchain Is Reshaping BCT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides an overview of telehealth or telemedicine technology in blockchain based healthcare management systems. Key features include privacy protection, immutable audit trail, patient control, data exchange and data accuracy.
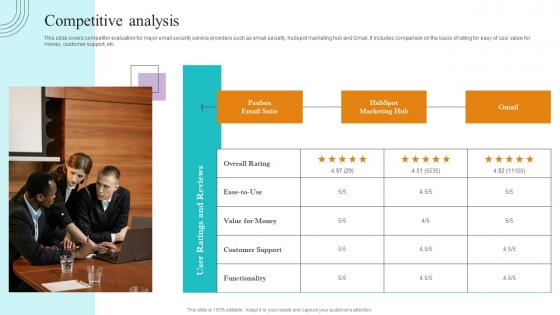
Competitive Analysis Paubox Capital Funding Pitch Deck Graphics Pdf
This slide covers competitor evaluation for major email security service providers such as email security, hubspot marketing hub and Gmail. It includes comparison on the basis of rating for easy of use, value for money, customer support, etc. Present like a pro with Competitive Analysis Paubox Capital Funding Pitch Deck Graphics Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers competitor evaluation for major email security service providers such as email security, hubspot marketing hub and Gmail. It includes comparison on the basis of rating for easy of use, value for money, customer support, etc.

Unlocking The Potential Of Impact Of Smart Contracts In Gaming BCT SS V
This slide mentions the impact of integrating smart contracts within the blockchain games. It includes enhanced security, decentralized ownership, trustworthy economies and decentralized governance. This slide mentions the impact of integrating smart contracts within the blockchain games. It includes enhanced security, decentralized ownership, trustworthy economies and decentralized governance. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Unlocking The Potential Of Impact Of Smart Contracts In Gaming BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide mentions the impact of integrating smart contracts within the blockchain games. It includes enhanced security, decentralized ownership, trustworthy economies and decentralized governance.
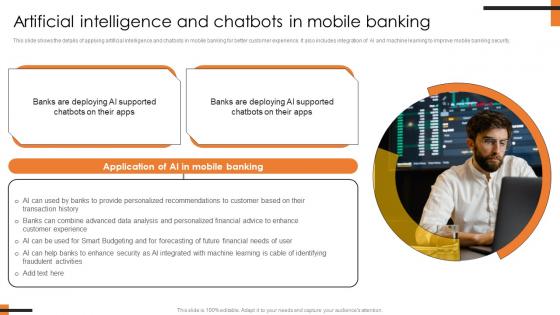
Artificial Intelligence And Chatbots In Comprehensive Smartphone Banking Download Pdf
This slide shows the details of applying artificial intelligence and chatbots in mobile banking for better customer experience. It also includes integration of AI and machine learning to improve mobile banking security.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Artificial Intelligence And Chatbots In Comprehensive Smartphone Banking Download Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide shows the details of applying artificial intelligence and chatbots in mobile banking for better customer experience. It also includes integration of AI and machine learning to improve mobile banking security.

Introduction Modern Billing Enhancing Customer Service Operations Using CRM Technology Formats Pdf
Following slide provide overview of modern billing software that helps to increase business operations efficiency. It include benefits such as high data security, flexibility, resource optimization etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Introduction Modern Billing Enhancing Customer Service Operations Using CRM Technology Formats Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Following slide provide overview of modern billing software that helps to increase business operations efficiency. It include benefits such as high data security, flexibility, resource optimization etc.

Exit Strategy Paubox Capital Funding Pitch Deck Clipart Pdf
This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering. Find highly impressive Exit Strategy Paubox Capital Funding Pitch Deck Clipart Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Exit Strategy Paubox Capital Funding Pitch Deck Clipart Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering.


 Continue with Email
Continue with Email

 Home
Home


































