Construction Safety Plan

Environment And Data Security For Devsecops Process Role Of Devsecops Ppt Example
This slide discusses the environment and data security for DevSecOps. The purpose of this slide is to highlight the process, including standardizing and automating the environment, centralizing user identity and access control, isolating containers for security, and so on. The Environment And Data Security For Devsecops Process Role Of Devsecops Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide discusses the environment and data security for DevSecOps. The purpose of this slide is to highlight the process, including standardizing and automating the environment, centralizing user identity and access control, isolating containers for security, and so on.
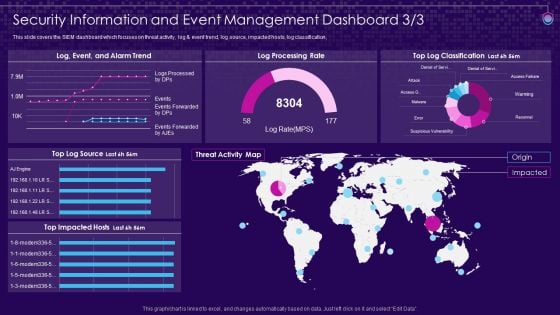
SIEM Services Security Information And Event Management Dashboard Source Ppt Outline Design Inspiration PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative siem services security information and event management dashboard source ppt outline design inspiration pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
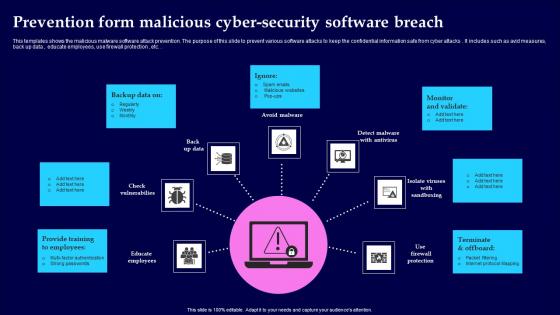
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc.
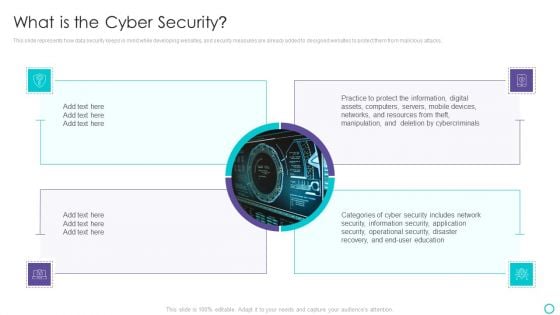
Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
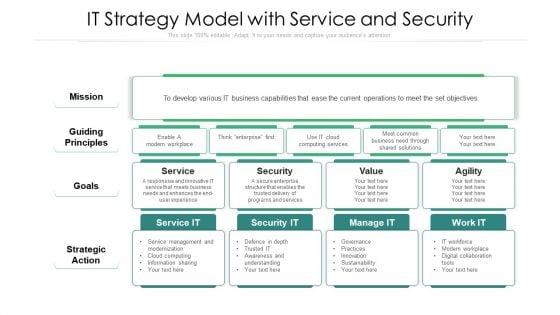
IT Strategy Model With Service And Security Ppt Professional Aids PDF
Showcasing this set of slides titled it strategy model with service and security ppt professional aids pdf. The topics addressed in these templates are strategic action, mission, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
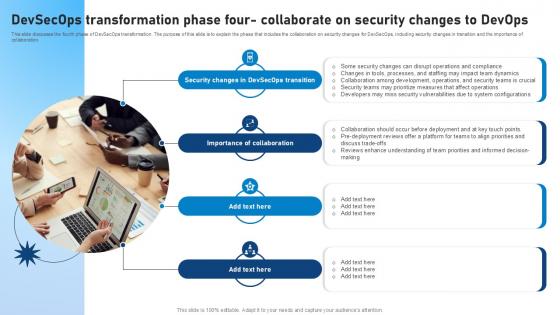
Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide
This slide discusses the fourth phase of DevSecOps transformation. The purpose of this slide is to explain the phase that includes the collaboration on security changes for DevSecOps, including security changes in transition and the importance of collaboration. This Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the fourth phase of DevSecOps transformation. The purpose of this slide is to explain the phase that includes the collaboration on security changes for DevSecOps, including security changes in transition and the importance of collaboration.
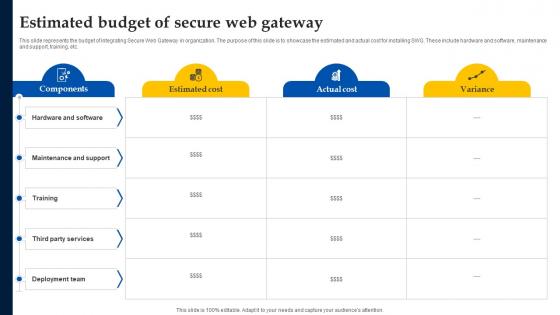
Web Access Control Solution Estimated Budget Of Secure Web Gateway
This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Web Access Control Solution Estimated Budget Of Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Web Access Control Solution Estimated Budget Of Secure Web Gateway. This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc.
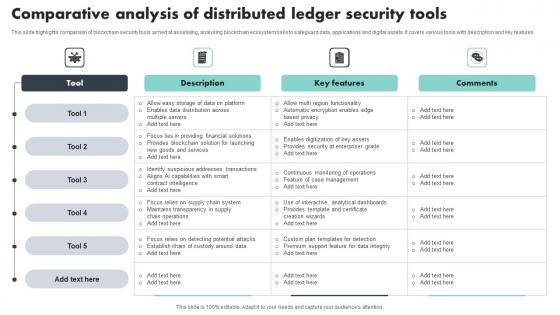
Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf
This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features Showcasing this set of slides titled Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf The topics addressed in these templates are Key Features, Comparative Analysis, Security Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features
Security Analysis Ppt PowerPoint Presentation Slides
This is a security analysis ppt powerpoint presentation slides. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, growth.

Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V
The slide provides a comprehensive overview of the rules and regulations governing the cybersecurity industry. The slide aims to inform stakeholders regarding the laws in different countries such as USA, Europe, China And UK. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V The slide provides a comprehensive overview of the rules and regulations governing the cybersecurity industry. The slide aims to inform stakeholders regarding the laws in different countries such as USA, Europe, China And UK.
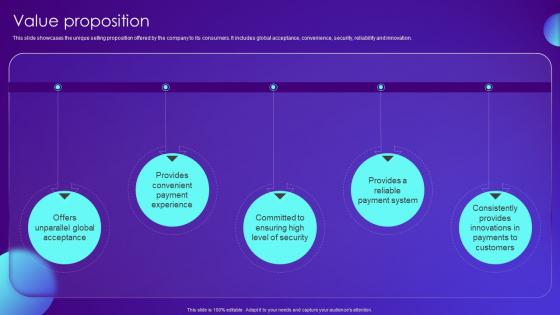
Value Proposition Payment Card Services Business Model BMC SS V
This slide showcases the unique selling proposition offered by the company to its consumers. It includes global acceptance, convenience, security, reliability and innovation. Get a simple yet stunning designed Value Proposition Payment Card Services Business Model BMC SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Value Proposition Payment Card Services Business Model BMC SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases the unique selling proposition offered by the company to its consumers. It includes global acceptance, convenience, security, reliability and innovation.
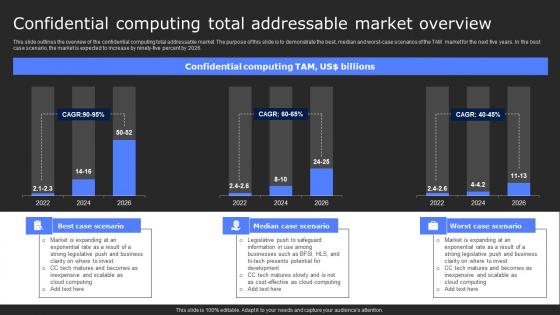
Confidential Computing Total Addressable Secure Computing Framework Themes Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Confidential Computing Total Addressable Secure Computing Framework Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.
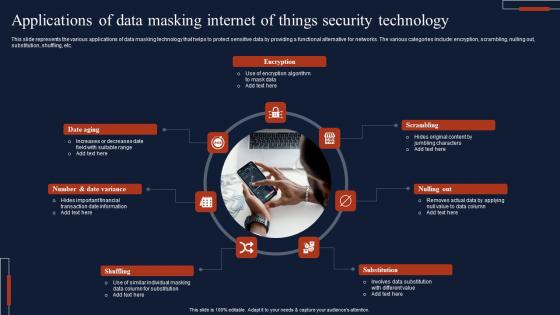
Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc.
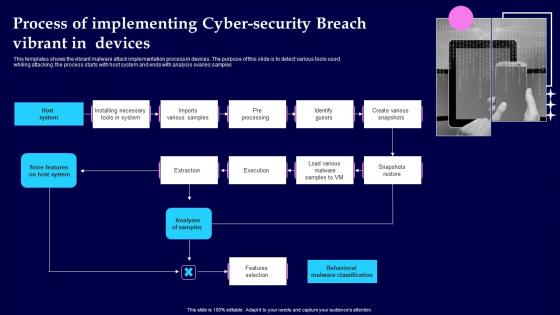
Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf
This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples Pitch your topic with ease and precision using this Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf This layout presents information on Analyses Of Samples, Features Selection, Pre Processing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples

Damage Security Insurance Proposal Cover Letter For Liability Insurance Proposal Ppt Slides Graphic Tips PDF
Presenting damage security insurance proposal cover letter for liability insurance proposal ppt slides graphic tips pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cover letter. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault How To Prevent Ddos Attacks In The Company Inspiration PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc.Presenting cyber terrorism assault how to prevent ddos attacks in the company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like service providers bandwidth capacity, network monitoring, update security components In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Enterprise Architecture Strategy Ppt Powerpoint Slides Designs
This is a enterprise architecture strategy ppt powerpoint slides designs. This is a six stage process. The stages in this process are business view, business layer, data layer, security layer, business architecture, process layer.
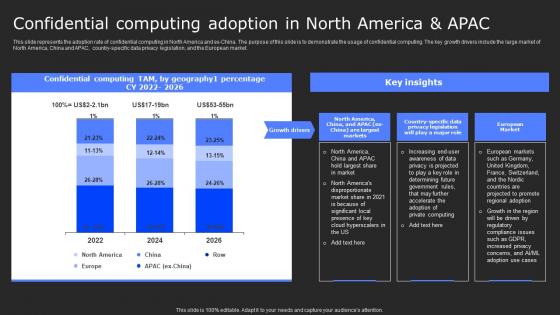
Confidential Computing Adoption In North Secure Computing Framework Template Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In North Secure Computing Framework Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In North Secure Computing Framework Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
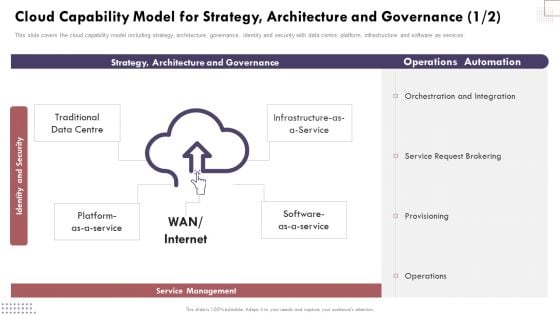
Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. Explore a selection of the finest Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
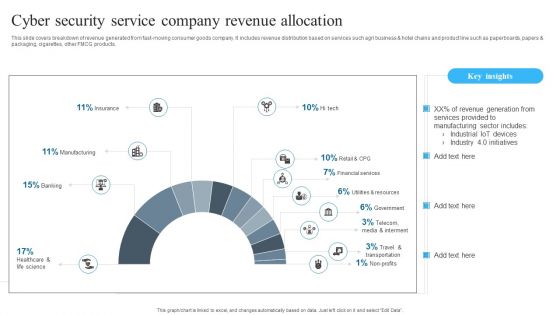
Cyber Security Service Company Revenue Allocation Background PDF
Showcasing this set of slides titled Cyber Security Service Company Revenue Allocation Background PDF. The topics addressed in these templates are Cyber Security, Service Company, Revenue Allocation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
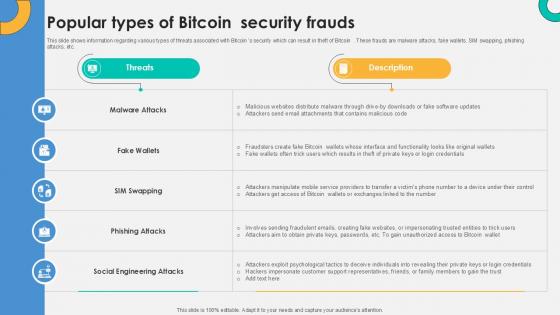
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.

IT Policies And Procedures Email And Chat Policy Objective And Guidelines Themes PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. If you are looking for a format to display your unique thoughts, then the professionally designed IT Policies And Procedures Email And Chat Policy Objective And Guidelines Themes PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Policies And Procedures Email And Chat Policy Objective And Guidelines Themes PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
PowerPoint Slide Designs Growth Chains Flowchart Ppt Design
PowerPoint Slide Designs Growth Chains Flowchart PPT Design--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Imagine your audience applauding with our PowerPoint Slide Designs Growth Chains Flowchart Ppt Design. Make sure your presentation gets the attention it deserves.
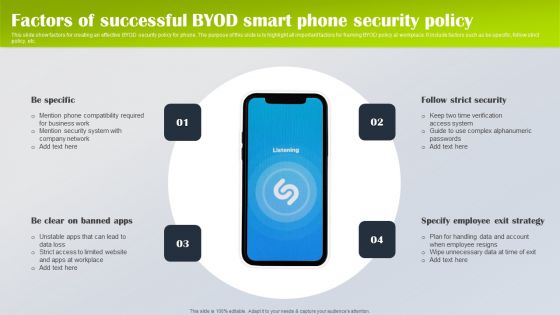
Factors Of Successful Byod Smart Phone Security Policy Designs PDF
This slide show factors for creating an effective BYOD security policy for phone. The purpose of this slide is to highlight all important factors for framing BYOD policy at workplace. It include factors such as be specific, follow strict policy, etc. Presenting Factors Of Successful Byod Smart Phone Security Policy Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Be Specific, Specify Employee Exit Strategy, Follow Strict Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security And Human Resource Services Business Profile Employee And Staff Welfare Inspiration PDF
This slide highlights the staff and employee welfare services which includes social security, insurance, medical, accommodation, pick and drop services. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Security And Human Resource Services Business Profile Employee And Staff Welfare Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
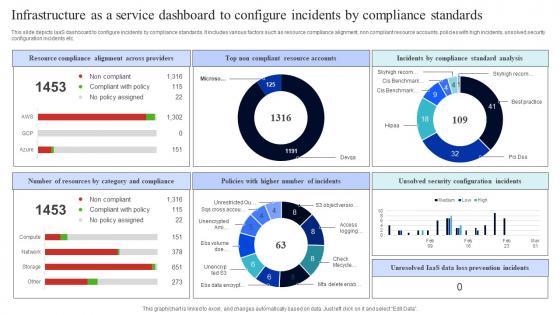
Infrastructure As A Service Dashboard To Configure Incidents By Compliance Standards Rules Pdf
This slide depicts IaaS dashboard to configure incidents by compliance standards. It includes various factors such as resource compliance alignment, non compliant resource accounts, policies with high incidents, unsolved security configuration incidents etc. Pitch your topic with ease and precision using this Infrastructure As A Service Dashboard To Configure Incidents By Compliance Standards Rules Pdf. This layout presents information on Resource Compliance Alignment, Across Providers, Top Non Compliant, Resource Accounts. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts IaaS dashboard to configure incidents by compliance standards. It includes various factors such as resource compliance alignment, non compliant resource accounts, policies with high incidents, unsolved security configuration incidents etc.

Internet Security Management In Powerpoint And Google Slides Cpb
Introducing our well designed Internet Security Management In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Internet Security Management. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Internet Security Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
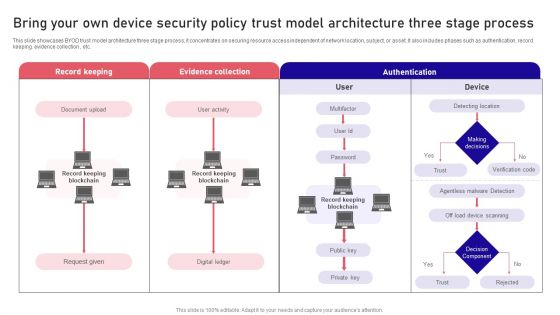
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
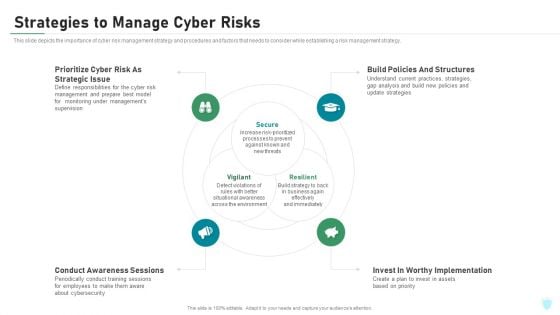
Strategies To Manage Cyber Risks IT Security IT Ppt Visual Aids Portfolio PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting strategies to manage cyber risks it security it ppt visual aids portfolio pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like prioritize cyber risk as strategic issue, conduct awareness sessions, build policies and structures, invest in worthy implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. This Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
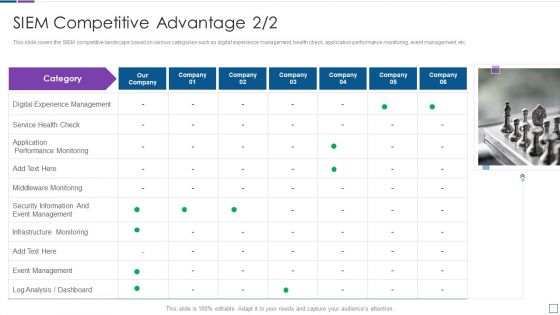
Real Time Assessment Of Security Threats SIEM Competitive Advantage Service Structure PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Presenting real time assessment of security threats siem competitive advantage service structure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like digital experience management, service health check, application performance monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
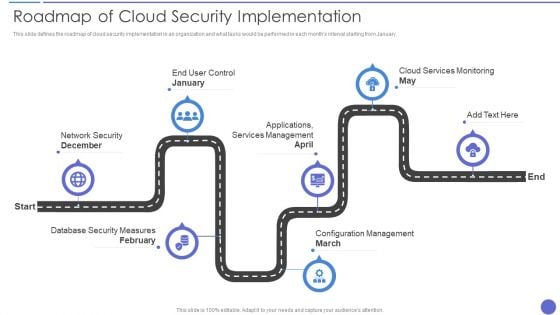
Roadmap Of Cloud Security Implementation Infographics PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Roadmap Of Cloud Security Implementation Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Applications Services Management, Cloud Services Monitoring, Network Security December. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
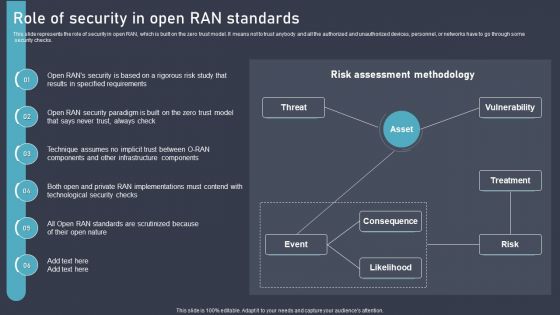
O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Retrieve professionally designed O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc. Find highly impressive Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc.

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
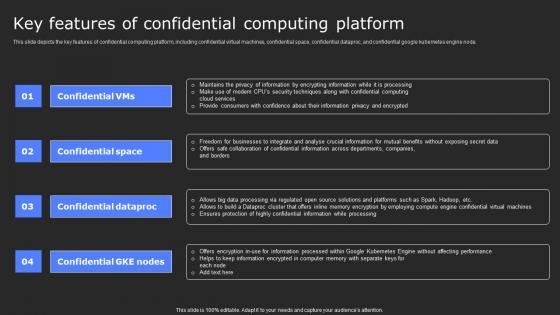
Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential google kubernetes engine node. Create an editable Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential google kubernetes engine node.
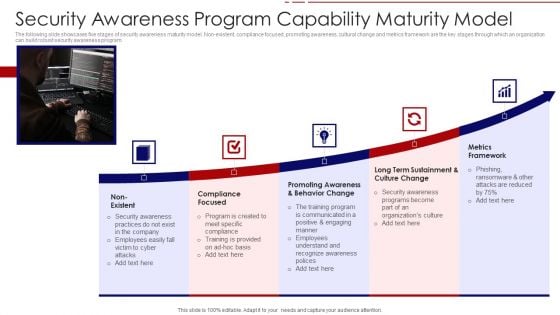
Security Awareness Program Capability Maturity Model Ppt PowerPoint Presentation File Portfolio PDF
The following slide showcases five stages of security awareness maturity model. Non-existent, compliance focused, promoting awareness, cultural change and metrics framework are the key stages through which an organization can build robust security awareness program. Persuade your audience using this security awareness program capability maturity model ppt powerpoint presentation file portfolio pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including non existent, compliance focused, promoting awareness and behavior change, long term sustainment and culture change, metrics framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
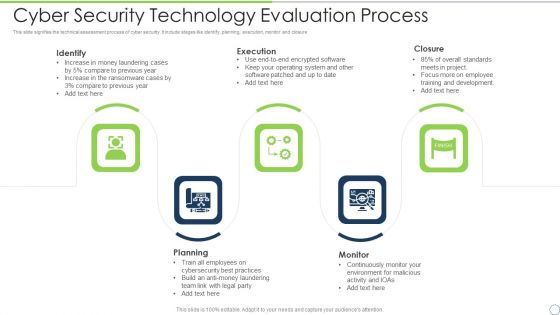
Cyber Security Technology Evaluation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Persuade your audience using this cyber security technology evaluation process ppt powerpoint presentation file visual aids pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identify, execution, closure, monitor, planning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
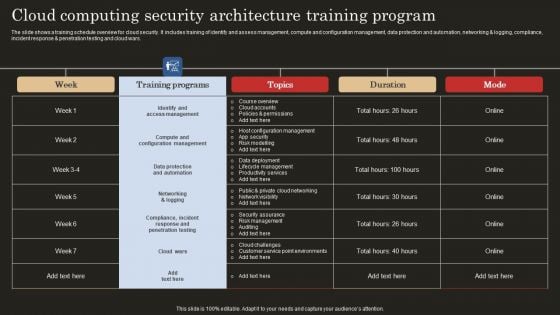
Cloud Computing Security Architecture Training Program Guidelines PDF
The slide shows a training schedule overview for cloud security. It includes training of identify and assess management, compute and configuration management, data protection and automation, networking and logging, compliance, incident response and penetration testing and cloud wars. Showcasing this set of slides titled Cloud Computing Security Architecture Training Program Guidelines PDF. The topics addressed in these templates are Identify Access Management, Compute Configuration Management, Data Protection Automation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
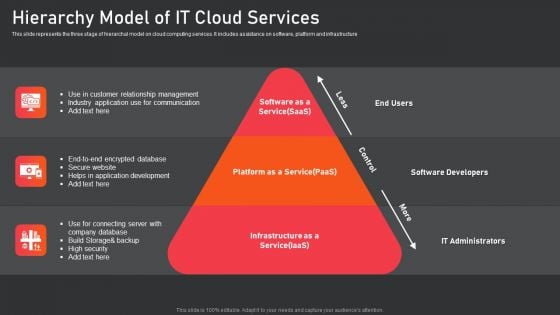
Hierarchy Model Of IT Cloud Services Designs PDF
This slide represents the three stage of hierarchal model on cloud computing services. It includes assistance on software, platform and infrastructure. Presenting hierarchy model of it cloud services designs pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Website, Helps In Application Development, Build Storage And Backup, High Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
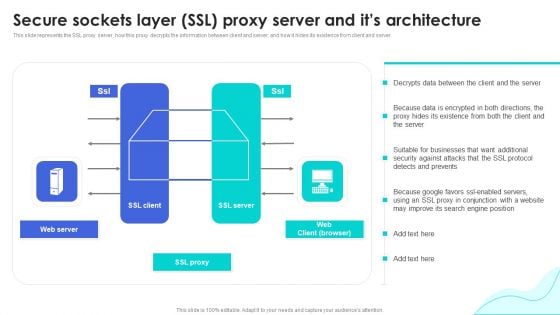
Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF
This slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server. Boost your pitch with our creative Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
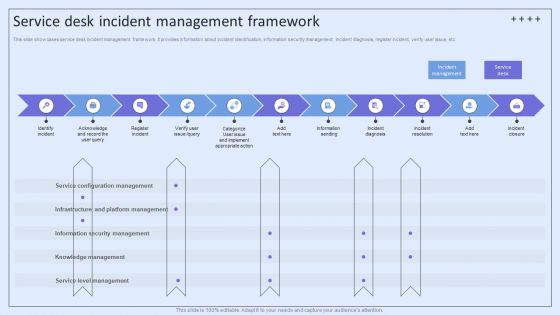
Integrating ITSM To Enhance Service Service Desk Incident Management Framework Download PDF
This slide showcases service desk incident management framework. It provides information about incident identification, information security management, incident diagnosis, register incident, verify user issue, etc. Boost your pitch with our creative Integrating ITSM To Enhance Service Service Desk Incident Management Framework Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Main Data Security Tokenization Techniques Securing Your Data Ppt Sample
This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. The Main Data Security Tokenization Techniques Securing Your Data Ppt Sample is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc.
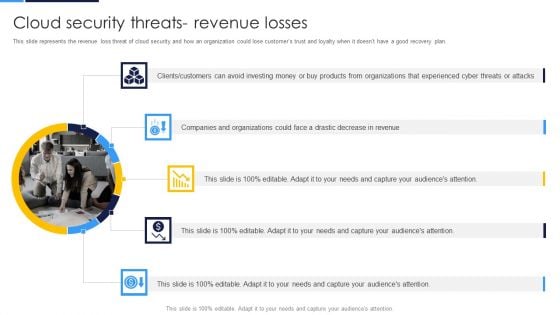
Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Presenting Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Clients Or Customers, Companies And Organizations, Organizations That Experienced. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
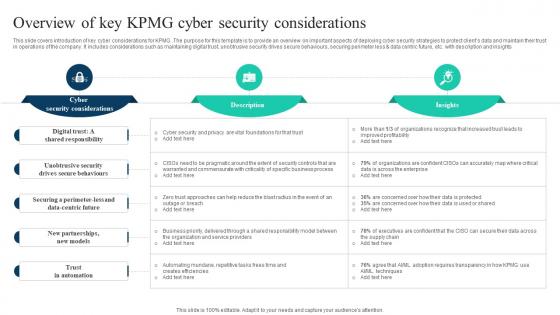
The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V
This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Find a pre-designed and impeccable The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights

Big Data Analysis Requirements Ppt Professional Format Ideas PDF
Deliver and pitch your topic in the best possible manner with this big data analysis requirements ppt professional format ideas pdf. Use them to share invaluable insights on data movement, existing skills, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
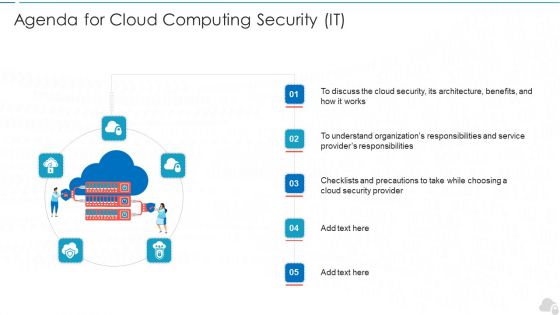
Agenda For Cloud Computing Security IT Ppt Infographic Template Inspiration PDF
Presenting agenda for cloud computing security it ppt infographic template inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cloud security, service, architecture, organizations, responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
PowerPoint Layout Corporate Competition Targets Umbrella Chart Ppt Theme
PowerPoint Layout Corporate Competition Targets Umbrella Chart PPT Theme-These high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Throw a curveballwith our PowerPoint Layout Corporate Competition Targets Umbrella Chart Ppt Theme. You'll deliver your best presentation yet.
PowerPoint Slidelayout Company Success Targets Umbrella Chart Ppt Slides
PowerPoint Slidelayout Company Success Targets Umbrella Chart PPT Slides-These high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Attract the creme-de-la-creme with our PowerPoint Slidelayout Company Success Targets Umbrella Chart Ppt Slides. Give the elite an exclusive experience.
PowerPoint Slidelayout Corporate Teamwork Targets Umbrella Chart Ppt Presentation
PowerPoint Slidelayout Corporate Teamwork Targets Umbrella Chart PPT Presentation-These high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Hit exceptional ratings with our PowerPoint Slidelayout Corporate Teamwork Targets Umbrella Chart Ppt Presentation. Astound the audience with your display.
Cyber Security Implementation Framework Table Of Contents Ppt PowerPoint Presentation Icon Portfolio PDF
Presenting this set of slides with name cyber security implementation framework table of contents ppt powerpoint presentation icon portfolio pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role of personnel, cost associated to firm, impact analysis, dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
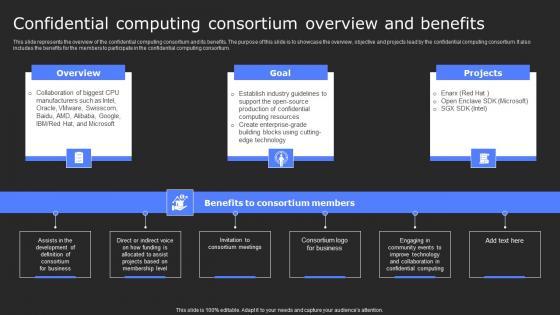
Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
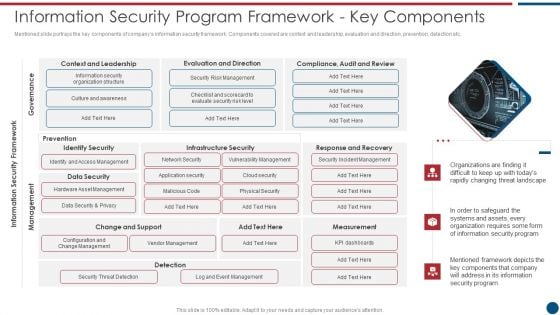
Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. This is a Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Leadership, Evaluation Direction, Change Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
PowerPoint Design Slides Leadership Chains Flowchart Ppt Slidelayout
PowerPoint Design Slides Leadership Chains Flowchart PPT Slidelayout--These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Brace yourself with our PowerPoint Design Slides Leadership Chains Flowchart Ppt Slidelayout. Cater for any adversity that can emerge.
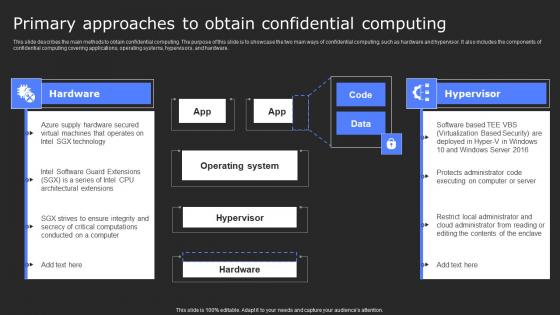
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
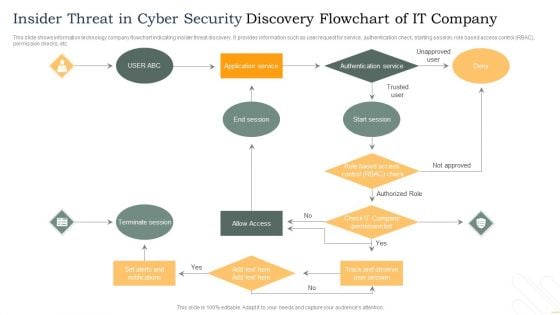
Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.
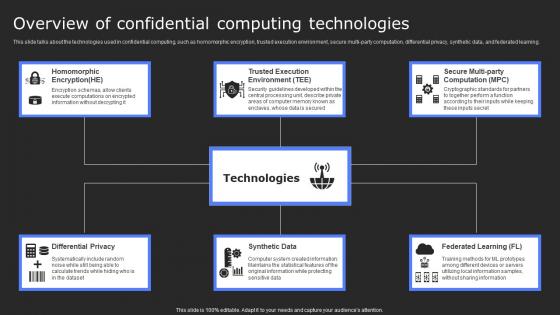
Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Present like a pro with Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.

Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V
This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc.

Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































