Cryptography
Quantum Computing For Everyone IT Key Requirements Faithful Transmission Of Flying Qubits Icons PDF
This slide represents the faithful transmission of flying qubits in quantum computers. It also shows that organizations are expecting to create quantum cryptography that will be helpful in the secure transmission of data. Deliver and pitch your topic in the best possible manner with this quantum computing for everyone it key requirements faithful transmission of flying qubits icons pdf. Use them to share invaluable insights on organizations, communication, quantum networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
International Organization Standardization 270001 Security Domains That Will Be Addressed By Isms Icons PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a international organization standardization 270001 security domains that will be addressed by isms icons pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization of information security, human resources security, asset management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. Presenting Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Security Policy, Asset Management, Physical And Environmental Security, Operational Security, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Quantum Computing Key Requirements Faithful Transmission Of Flying Qubits Designs PDF
This slide represents the faithful transmission of flying qubits in quantum computers. It also shows that organizations are expecting to create quantum cryptography that will be helpful in the secure transmission of data. This is a Quantum Computing Key Requirements Faithful Transmission Of Flying Qubits Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Quantum Networks, Communication, Trial Arrangement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policy, Organization Information, Human Resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Quantum Computing Key Requirements Faithful Transmission Of Flying Qubits Ppt Portfolio Templates PDF
This slide represents the faithful transmission of flying qubits in quantum computers. It also shows that organizations are expecting to create quantum cryptography that will be helpful in the secure transmission of data. Presenting Quantum Computing Key Requirements Faithful Transmission Of Flying Qubits Ppt Portfolio Templates PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Organizations Imagined, Reliable Communication, Quantum Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Quantum Key Distribution Applications Of Quantum Computing Background PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc.This is a Quantum Key Distribution Applications Of Quantum Computing Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Artificial Intelligence, Design And Development, Cybersecurity And Cryptography You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Quantum Key Distribution Key Requirements Faithful Transmission Of Flying Qubits Diagrams PDF
This slide represents the faithful transmission of flying qubits in quantum computers. It also shows that organizations are expecting to create quantum cryptography that will be helpful in the secure transmission of data. This is a Quantum Key Distribution Key Requirements Faithful Transmission Of Flying Qubits Diagrams PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Trial Arrangement, Quantum Networks, Reliable Communication You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
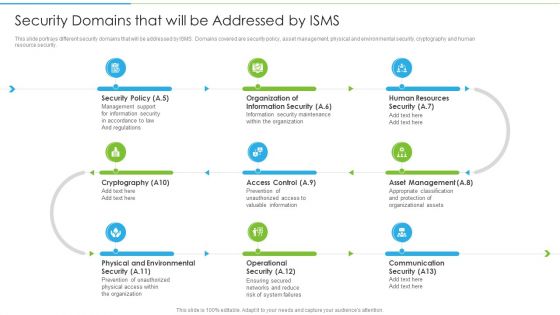
Security Domains That Will Be Addressed By ISMS Diagrams PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.This is a Security Domains That Will Be Addressed By ISMS Diagrams PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Support, Resources Security, Prevention Of Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.Presenting ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Asset Management, Operational Security, Physical And Environmental. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
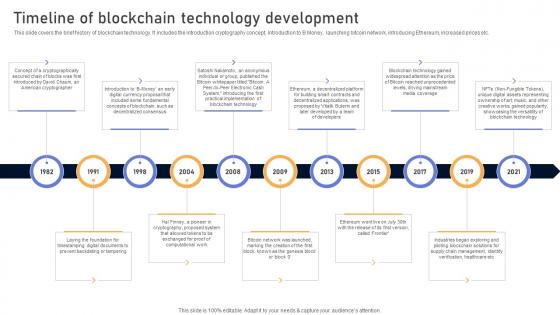
Comprehensive Look At Blockchain Timeline Of Blockchain Technology Development BCT SS V
This slide covers the brief history of blockchain technology. It includes the introduction cryptography concept, introduction to B Money, launching bitcoin network, introducing Ethereum, increased prices etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comprehensive Look At Blockchain Timeline Of Blockchain Technology Development BCT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comprehensive Look At Blockchain Timeline Of Blockchain Technology Development BCT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers the brief history of blockchain technology. It includes the introduction cryptography concept, introduction to B Money, launching bitcoin network, introducing Ethereum, increased prices etc.
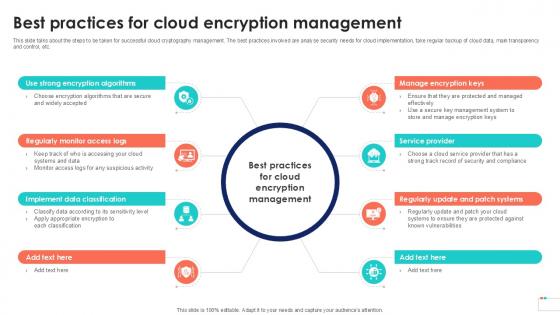
Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template today and make your presentation stand out from the rest This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.
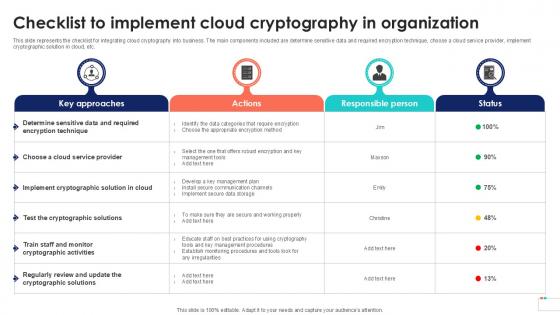
Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.

Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.
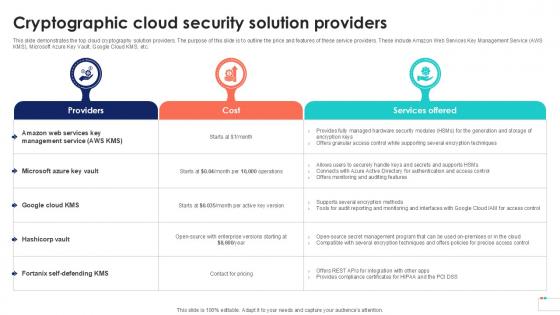
Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.
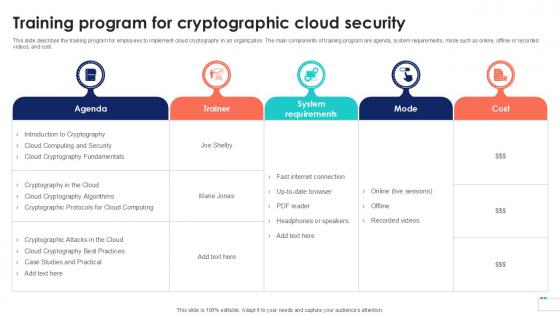
Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Types Of Attacks Prevented By Data Security In Cloud Computing Ppt Template
This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man-in-the-middle MitM attacks, data breaches, insider attacks, etc. Find highly impressive Types Of Attacks Prevented By Data Security In Cloud Computing Ppt Template on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Types Of Attacks Prevented By Data Security In Cloud Computing Ppt Template for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man-in-the-middle MitM attacks, data breaches, insider attacks, etc.
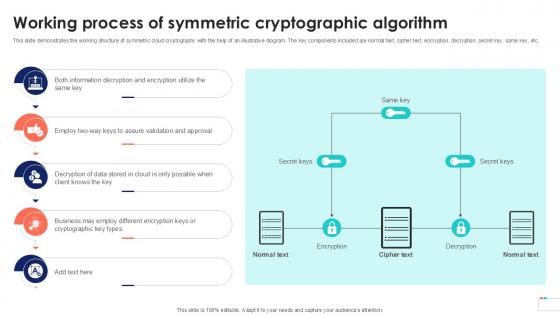
Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Process Of Symmetric Data Security In Cloud Computing Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Process Of Symmetric Data Security In Cloud Computing Ppt Template This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.
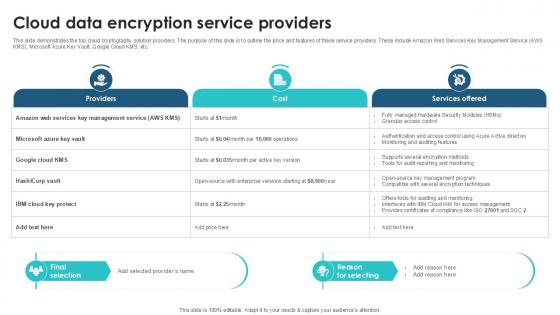
Cloud Data Encryption Service Client Side Encryption PPT PowerPoint
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Slidegeeks is here to make your presentations a breeze with Cloud Data Encryption Service Client Side Encryption PPT PowerPoint With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.

Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Take your projects to the next level with our ultimate collection of Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc.
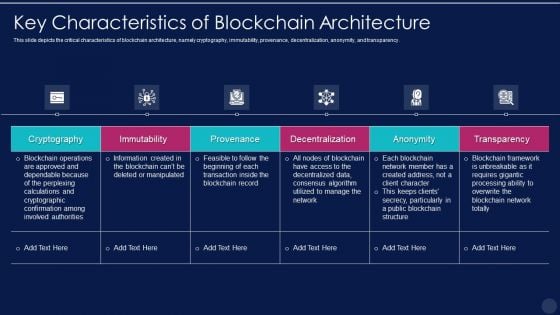
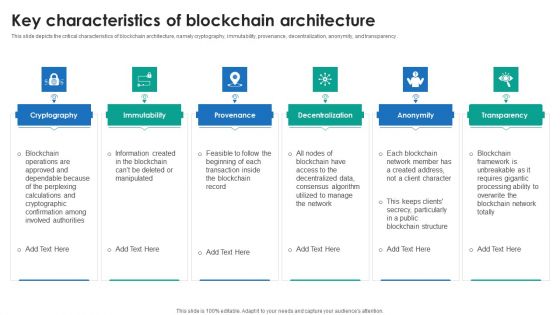
Blockchain Technology Framework IT Key Characteristics Of Blockchain Architecture Elements PDF
This slide depicts the critical characteristics of blockchain architecture, namely cryptography, immutability, provenance, decentralization, anonymity, and transparency. Deliver and pitch your topic in the best possible manner with this blockchain technology framework it key characteristics of blockchain architecture elements pdf. Use them to share invaluable insights on cryptography, immutability, provenance, decentralization, anonymity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
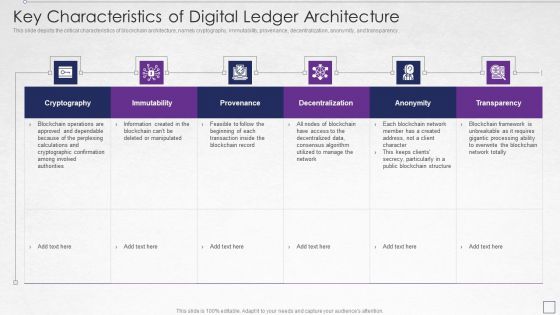
Digitized Record Book Technology Key Characteristics Of Digital Ledger Architecture Brochure PDF
This slide depicts the critical characteristics of blockchain architecture, namely cryptography, immutability, provenance, decentralization, anonymity, and transparency. Deliver and pitch your topic in the best possible manner with this digitized record book technology key characteristics of digital ledger architecture brochure pdf. Use them to share invaluable insights on cryptography, immutability, provenance, decentralization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Blockchain And DLT Framework Key Characteristics Of Blockchain Architecture Sample PDF
This slide depicts the critical characteristics of blockchain architecture, namely cryptography, immutability, provenance, decentralization, anonymity, and transparency. Presenting Blockchain And DLT Framework Key Characteristics Of Blockchain Architecture Sample PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Cryptography, Immutability, Provenance, Decentralization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
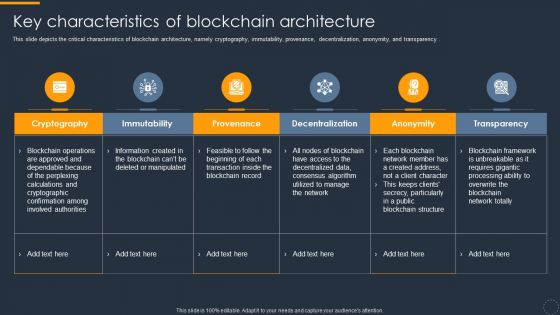
Cryptocurrency Ledger Key Characteristics Of Blockchain Architecture Microsoft PDF
This slide depicts the critical characteristics of blockchain architecture, namely cryptography, immutability, provenance, decentralization, anonymity, and transparency. This is a Cryptocurrency Ledger Key Characteristics Of Blockchain Architecture Microsoft PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Immutability, Cryptography, Decentralization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Quantum Computing For Everyone IT Ways Quantum Computing Can Help Businesses Guidelines PDF
This slide depicts the seven ways in which quantum computing can help businesses to grow, such as cryptography, self-driven cars, medical research, aviation, etc. This is a quantum computing for everyone it ways quantum computing can help businesses guidelines pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cryptography, medical research, pattern matching, forecasting, data analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ways Quantum Computing Can Help Businesses Ppt Infographics Portrait PDF
This slide depicts the seven ways in which quantum computing can help businesses to grow, such as cryptography, self driven cars, medical research, aviation, etc. This is a Ways Quantum Computing Can Help Businesses Ppt Infographics Portrait PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cryptography, Data Analysis, Pattern Matching. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3 Key Areas For Document Management Security Controls Ideas PDF
This slide presents the key areas of security control that enable companies to manage information access and permissions. It includes cryptography, best practice guidelines, compliance certifications and attestations. Persuade your audience using this 3 Key Areas For Document Management Security Controls Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cryptography, Practice Guidelines, Attestations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Privacy Processes Ppt Powerpoint Presentation Summary Images
Presenting this set of slides with name privacy processes ppt powerpoint presentation summary images. This is a four stage process. The stages in this process are privacy, transactions, cryptography, processes, participants. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
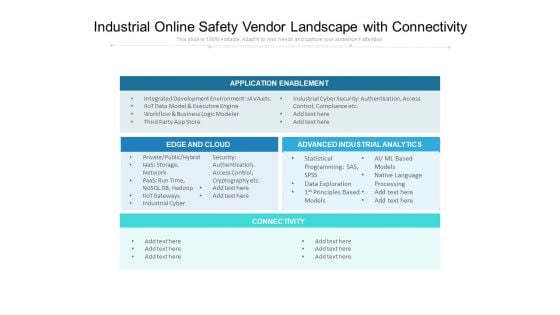
Industrial Online Safety Vendor Landscape With Connectivity Ppt PowerPoint Presentation Infographic Template Graphics Download PDF
Showcasing this set of slides titled industrial online safety vendor landscape with connectivity ppt powerpoint presentation infographic template graphics download pdf. The topics addressed in these templates are network, security,authentication, access control, cryptography, processing, business, analytics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
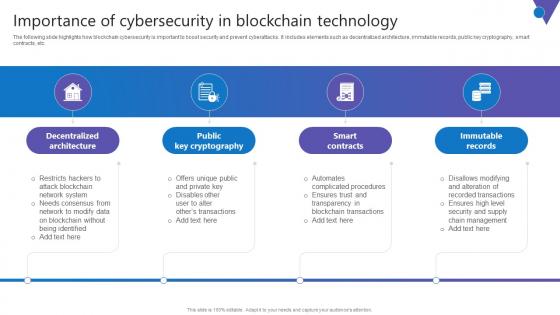
Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Find highly impressive Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc.

Comprehensive Manual For Blockchain Essential Elements Of Blockchain BCT SS V
This slide covers key components of blockchain networks technology. It includes essential elements such as nodes, blockchain, cryptography, consensus mechanism, smart contracts, etc. for effective deployment and execution of blockchain networks. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Comprehensive Manual For Blockchain Essential Elements Of Blockchain BCT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide covers key components of blockchain networks technology. It includes essential elements such as nodes, blockchain, cryptography, consensus mechanism, smart contracts, etc. for effective deployment and execution of blockchain networks.
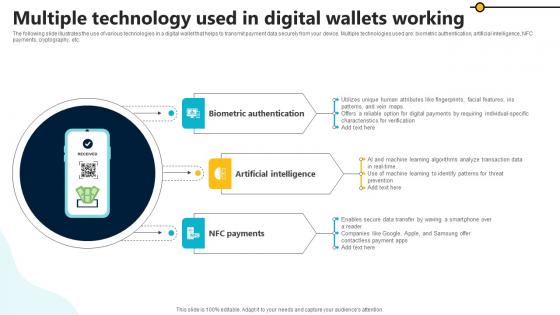
Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V
The following slide illustrates the use of various technologies in a digital wallet that helps to transmit payment data securely from your device. Multiple technologies used are biometric authentication, artificial intelligence, NFC payments, cryptography, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide illustrates the use of various technologies in a digital wallet that helps to transmit payment data securely from your device. Multiple technologies used are biometric authentication, artificial intelligence, NFC payments, cryptography, etc.
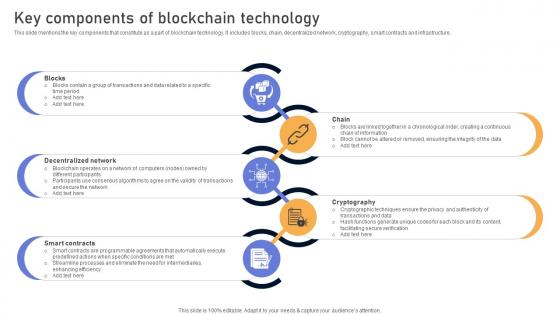
Comprehensive Look At Blockchain Key Components Of Blockchain Technology BCT SS V
This slide mentions the key components that constitute as a part of blockchain technology. It includes blocks, chain, decentralized network, cryptography, smart contracts and infrastructure. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Comprehensive Look At Blockchain Key Components Of Blockchain Technology BCT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Comprehensive Look At Blockchain Key Components Of Blockchain Technology BCT SS V. This slide mentions the key components that constitute as a part of blockchain technology. It includes blocks, chain, decentralized network, cryptography, smart contracts and infrastructure.
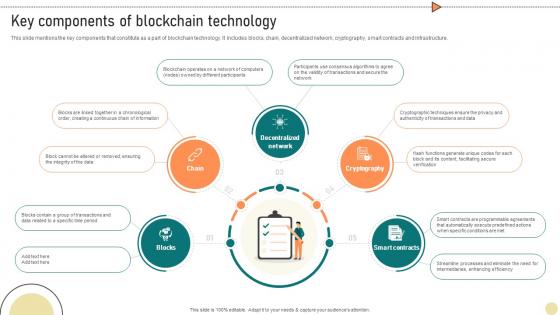
Visionary Guide To Blockchain Key Components Of Blockchain Technology BCT SS V
This slide mentions the key components that constitute as a part of blockchain technology. It includes blocks, chain, decentralized network, cryptography, smart contracts and infrastructure. This Visionary Guide To Blockchain Key Components Of Blockchain Technology BCT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide mentions the key components that constitute as a part of blockchain technology. It includes blocks, chain, decentralized network, cryptography, smart contracts and infrastructure.
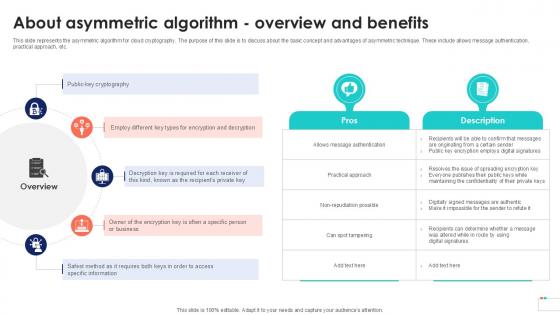
About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Boost your pitch with our creative About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.

About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.

Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example
This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc. This modern and well-arranged Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc.
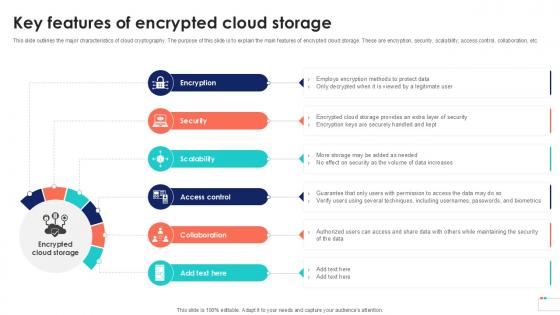
Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. This Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.

Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Boost your pitch with our creative Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.

Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Get a simple yet stunning designed Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.

What Are Benefits Of Using Data Security In Cloud Computing Ppt Template
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit What Are Benefits Of Using Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.

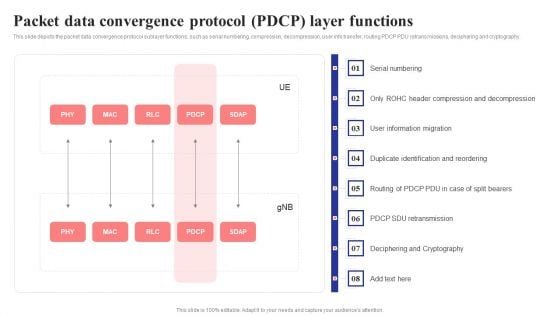
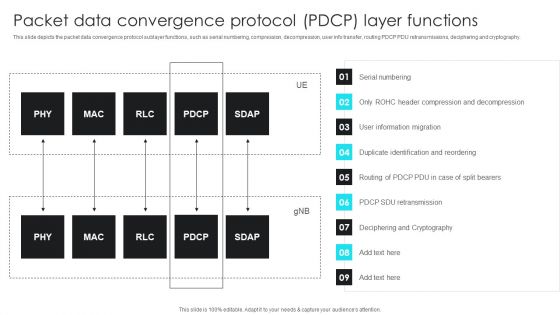
Packet Data Convergence Protocol Pdcp Layer Functions 5G Functional Architecture Slides PDF
This slide depicts the packet data convergence protocol sublayer functions, such as serial numbering, compression, decompression, user info transfer, routing PDCP PDU retransmissions, deciphering and cryptography.Deliver and pitch your topic in the best possible manner with this Packet Data Convergence Protocol Pdcp Layer Functions 5G Functional Architecture Slides PDF. Use them to share invaluable insights on Compression Decompression, Information Migration, Duplicate Identification and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
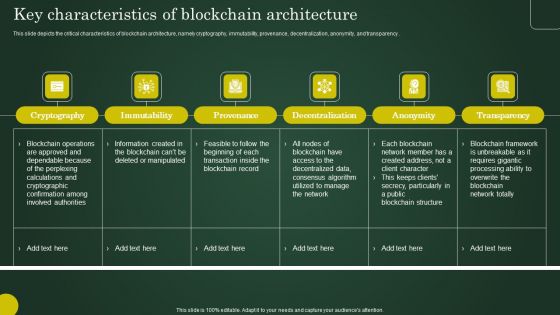
Key Characteristics Of Blockchain Architecture Involving Cryptographic Ledger To Enhance Background PDF
This slide depicts the critical characteristics of blockchain architecture, namely cryptography, immutability, provenance, decentralization, anonymity, and transparency. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Characteristics Of Blockchain Architecture Involving Cryptographic Ledger To Enhance Background PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
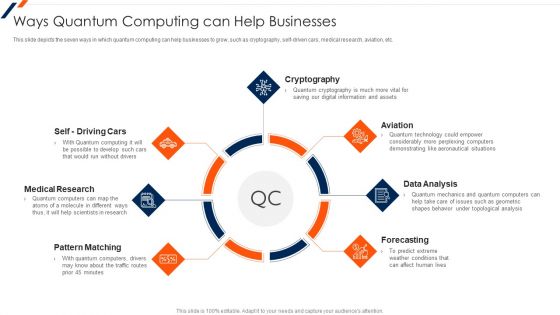
Ways Quantum Computing Can Help Businesses Ppt Outline Template PDF
This slide depicts the seven ways in which quantum computing can help businesses to grow, such as cryptography, self driven cars, medical research, aviation, etc. This is a Ways Quantum Computing Can Help Businesses Ppt Outline Template PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Analysis, Aviation, Medical Research, Pattern Matching, Forecasting. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
P2P Ledger Key Characteristics Of Blockchain Architecture Microsoft PDF
This slide depicts the critical characteristics of blockchain architecture, namely cryptography, immutability, provenance, decentralization, anonymity, and transparency .This P2P Ledger Key Characteristics Of Blockchain Architecture Microsoft PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The P2P Ledger Key Characteristics Of Blockchain Architecture Microsoft PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Structure Introduction PDF
This slide depicts the packet data convergence protocol sublayer functions, such as serial numbering, compression, decompression, user info transfer, routing PDCP PDU retransmissions, deciphering and cryptography.Welcome to our selection of the Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Structure Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
5G Network Operations Packet Data Convergence Protocol PDCP Layer Functions Themes PDF
This slide depicts the packet data convergence protocol sublayer functions, such as serial numbering, compression, decompression, user info transfer, routing PDCP PDU retransmissions, deciphering and cryptography. The 5G Network Operations Packet Data Convergence Protocol PDCP Layer Functions Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
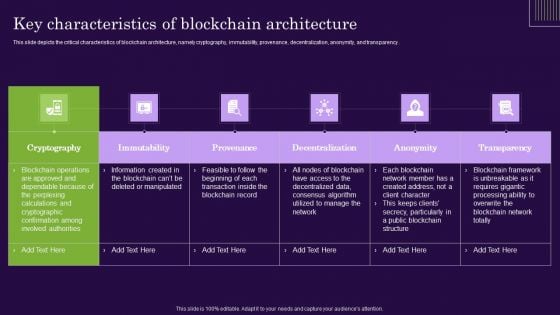
DLT Technology Key Characteristics Of Blockchain Architecture Graphics PDF
This slide depicts the critical characteristics of blockchain architecture, namely cryptography, immutability, provenance, decentralization, anonymity, and transparency . The DLT Technology Key Characteristics Of Blockchain Architecture Graphics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
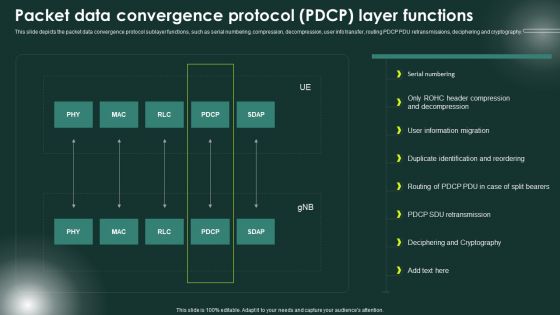
5G Network Applications And Features Packet Data Convergence Protocol PDCP Layer Functions Guidelines PDF
This slide depicts the packet data convergence protocol sublayer functions, such as serial numbering, compression, decompression, user info transfer, routing PDCP PDU retransmissions, deciphering and cryptography. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. 5G Network Applications And Features Packet Data Convergence Protocol PDCP Layer Functions Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Global Data Security Industry Report Major Market Trends Impacting Cybersecurity Industry IR SS V
The slide highlights the market trends in the global cybersecurity industry. These trends are having a significant impact on the way the industry operates, and they are likely to continue in the coming years. It cover trends such as artificial intelligence, real-time data monitoring, managed services, users as an attack surface, and quantum cryptography. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Global Data Security Industry Report Major Market Trends Impacting Cybersecurity Industry IR SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The slide highlights the market trends in the global cybersecurity industry. These trends are having a significant impact on the way the industry operates, and they are likely to continue in the coming years. It cover trends such as artificial intelligence, real-time data monitoring, managed services, users as an attack surface, and quantum cryptography.

Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.

Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Create an editable Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.
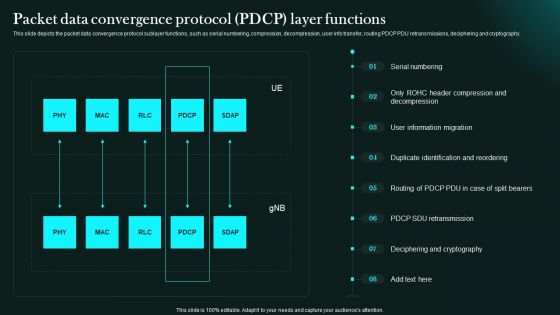
Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Functional Architecture Demonstration PDF
This slide depicts the packet data convergence protocol sublayer functions, such as serial numbering, compression, decompression, user info transfer, routing PDCP PDU retransmissions, deciphering and cryptography.Explore a selection of the finest Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Functional Architecture Demonstration PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Packet Data Convergence Protocol Pdcp Layer Functions 5G Network Functional Architecture Demonstration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Best Practices For Implementing Big Data Security Monitoring Sample pdf
This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc. Showcasing this set of slides titled Best Practices For Implementing Big Data Security Monitoring Sample pdf. The topics addressed in these templates are Preserve Data Privacy, Big Data Cryptography, Granular Access Control. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc.


 Continue with Email
Continue with Email

 Home
Home


































