Cyber Attack
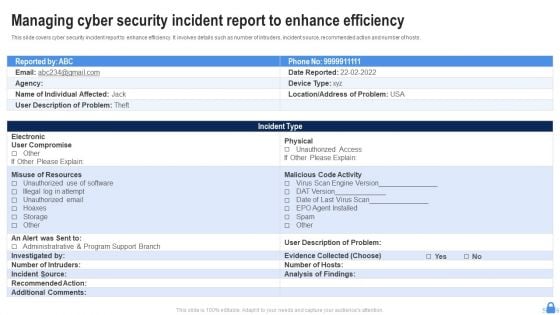
Managing Cyber Security Incident Report To Enhance Efficiency Ppt Professional Clipart PDF
Showcasing this set of slides titled Managing Cyber Security Incident Report To Enhance Efficiency Ppt Professional Clipart PDF. The topics addressed in these templates are Electronic, User Compromise, Misuse Resources. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icons Slide For Deploying Cyber Security Incident Response Administration Elements PDF
Introducing our well designed Icons Slide For Deploying Cyber Security Incident Response Administration Elements PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
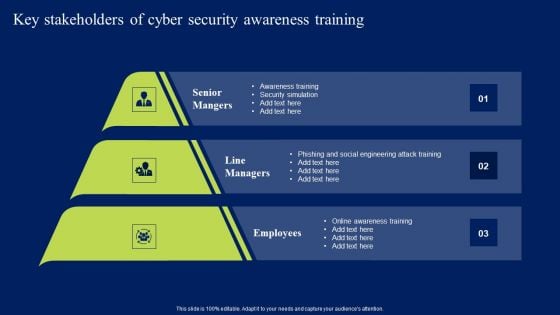
Key Stakeholders Of Cyber Security Awareness Training Ppt Ideas Good PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Key Stakeholders Of Cyber Security Awareness Training Ppt Ideas Good PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Icons Slide Development And Integration Of Cyber Security Incident Administration Slides PDF
Introducing our well designed Icons Slide Development And Integration Of Cyber Security Incident Administration Slides PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
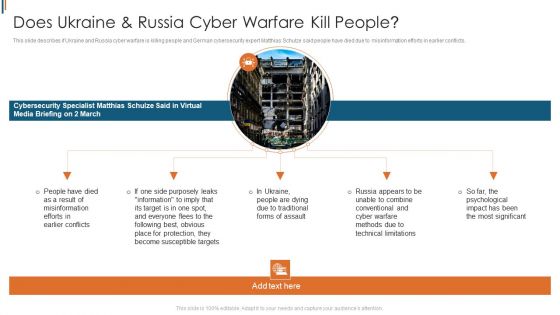
Ukraine Cyberwarfare Does Ukraine Russia Cyber Warfare Kill People Summary Pdf
This slide describes if Ukraine and Russia cyber warfare is killing people and German cybersecurity expert Matthias Schulze said people have died due to misinformation efforts in earlier conflicts. This is a ukraine cyberwarfare does ukraine russia cyber warfare kill people summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people have died as a result of misinformation efforts in earlier conflicts, in ukraine, people are dying due to traditional forms of assault, russia appears to be unable to combine conventional and cyber warfare methods due to technical limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
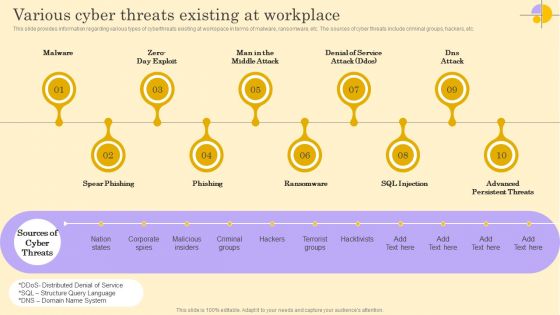
Various Cyber Threats Existing At Workplace Ppt Infographic Template Designs Download PDF
This slide provides information regarding various types of cyberthreats existing at workspace in terms of malware, ransomware, etc. The sources of cyber threats include criminal groups, hackers, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Various Cyber Threats Existing At Workplace Ppt Infographic Template Designs Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
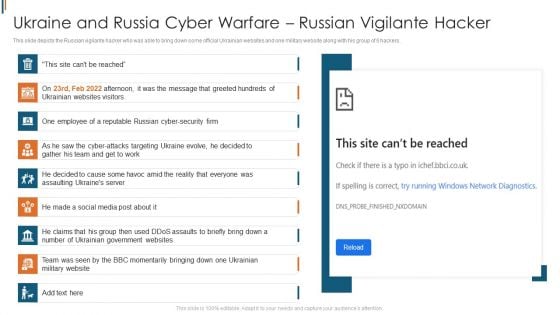
Ukraine Cyberwarfare Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Inspiration Pdf
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers. This is a ukraine cyberwarfare ukraine and russia cyber warfare russian vigilante hacker inspiration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like he made a social media post about it, one employee of a reputable russian cyber security firm, team was seen by the bbc momentarily bringing down one ukrainian military website. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
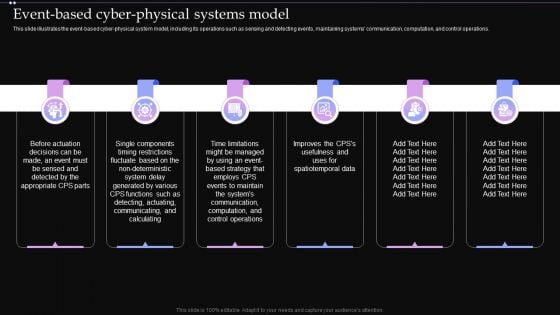
Event Based Cyber Physical Systems Model Ppt PowerPoint Presentation File Diagrams PDF
This slide illustrates the event based cyber physical system model, including its operations such as sensing and detecting events, maintaining systems communication, computation, and control operations. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Event Based Cyber Physical Systems Model Ppt PowerPoint Presentation File Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Event Based Cyber Physical Systems Model Ppt PowerPoint Presentation File Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
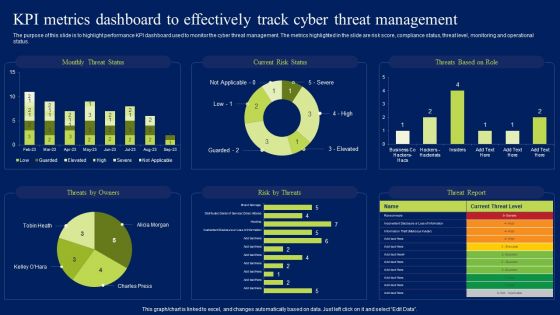
Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF.
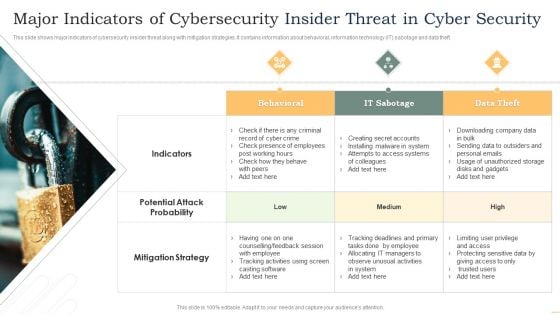
Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
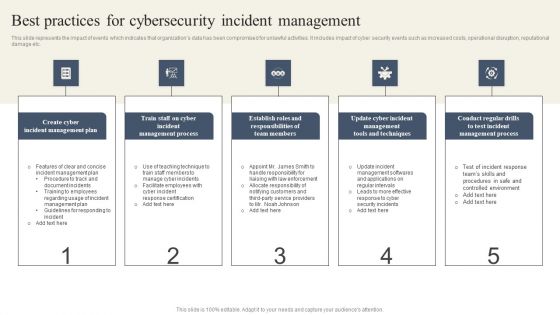
CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Key Safety Audits For Cyber Threat Prevention Ppt PowerPoint Presentation Icon Example PDF
Presenting key safety audits for cyber threat prevention ppt powerpoint presentation icon example pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including security, awareness, training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For E Business And Cyber Risk Management Ppt Slides Layout PDF
Deliver an awe inspiring pitch with this creative table of contents for e business and cyber risk management ppt slides layout pdf bundle. Topics like global market, security, requirements, communication plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
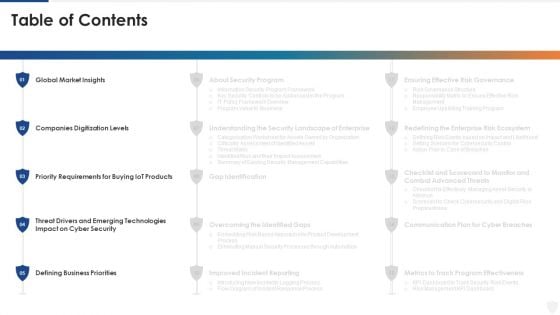
E Business And Cyber Risk Management Table Of Contents Elements PDF
Deliver and pitch your topic in the best possible manner with this e business and cyber risk management table of contents elements pdf. Use them to share invaluable insights on global market, requirements, security, technologies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
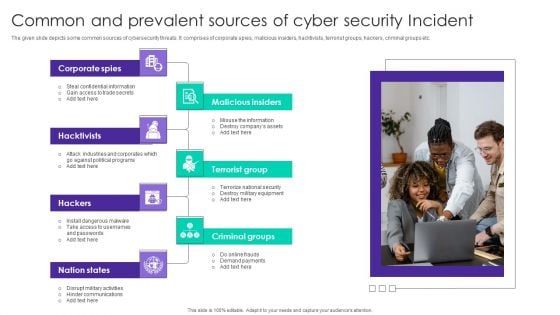
Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Cyber Terrorism Incidents On The Rise IT Our Creative Team Information PDF
Presenting global cyber terrorism incidents on the rise it our creative team information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like our creative team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
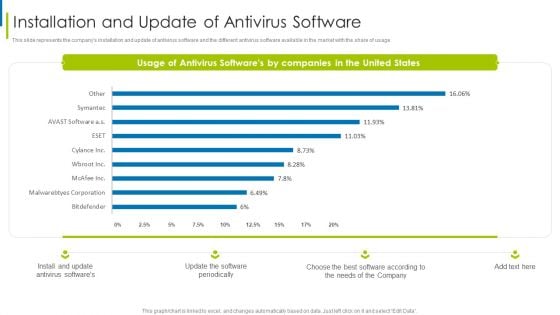
Cyber Terrorism Assault Installation And Update Of Antivirus Software Slides PDF
This slide represents the companys installation and update of antivirus software and the different antivirus software available in the market with the share of usage.Deliver an awe inspiring pitch with this creative cyber terrorism assault installation and update of antivirus software slides pdf bundle. Topics like antivirus softwares, software periodically, softwares by companies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Terrorism Assault Use Of Strong Encrypted Password In The Company Icons PDF
This slide demonstrates the need to have encrypted passwords for various online accounts and indicates how almost every employee has the same password.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault use of strong encrypted password in the company icons pdf Use them to share invaluable insights on use of strong encrypted password in the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Metrics To Manage Cyber Risk With Application Control Ppt PowerPoint Presentation Pictures Slide PDF
This slide covers cyber risk measure dashboard. It also includes application control, patch application, patch operating system, restrict admin privileges, disable untrusted Microsoft office macros, user application hardening, multi factor authentication and daily backup of important data. Pitch your topic with ease and precision using this key metrics to manage cyber risk with application control ppt powerpoint presentation pictures slide pdf. This layout presents information on disable untrusted microsoft office macros, application control, patch operating systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
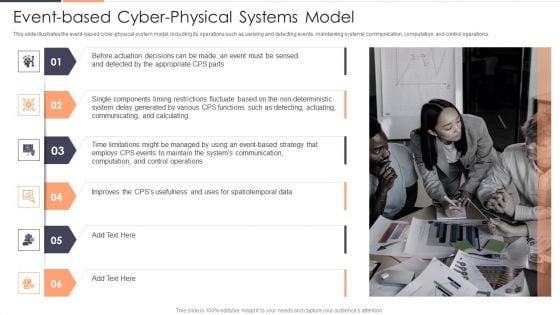
Event Based Cyber Physical Systems Model Ppt Professional Graphics Example PDF
This slide illustrates the event based cyber physical system model, including its operations such as sensing and detecting events, maintaining systems communication, computation, and control operations. Presenting Event Based Cyber Physical Systems Model Ppt Professional Graphics Example PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like System Delay, Communication, Strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
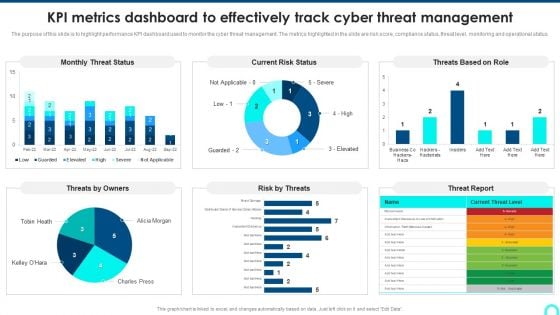
KPI Metrics Dashboard To Effectively Track Cyber Threat Management Demonstration PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Deliver an awe inspiring pitch with this creative KPI Metrics Dashboard To Effectively Track Cyber Threat Management Demonstration PDF bundle. Topics like Threat Status, Current Risk, Threat Report can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
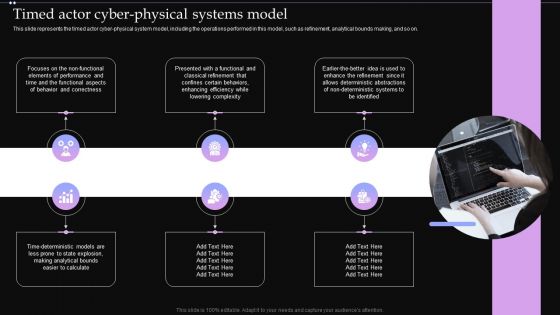
Timed Actor Cyber Physical Systems Model Ppt PowerPoint Presentation File Professional PDF
This slide represents the timed actor cyber physical system model, including the operations performed in this model, such as refinement, analytical bounds making, and so on. Slidegeeks has constructed Timed Actor Cyber Physical Systems Model Ppt PowerPoint Presentation File Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
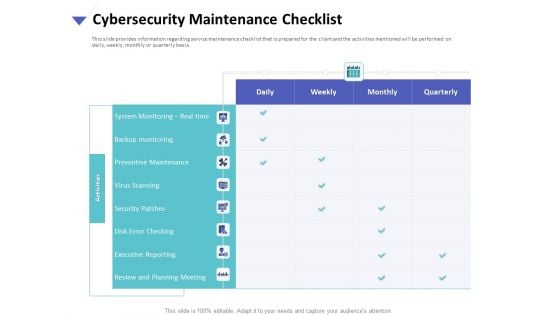
Strategies To Mitigate Cyber Security Risks Cybersecurity Maintenance Checklist Ppt Slides Graphics Tutorials PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity maintenance checklist ppt slides graphics tutorials pdf. The topics discussed in these slides are system monitoring, real time, backup monitoring, preventive maintenance, virus scanning, security patches, disk error checking, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Budget For Effective Cybersecurity Management Ppt Ideas Objects PDF
Presenting this set of slides with name cyber security for your organization budget for effective cybersecurity management ppt ideas objects pdf. This is a one stage process. The stages in this process are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Cybersecurity Contingency Plan Business Impact Analysis Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity contingency plan business impact analysis brochure pdf. This is a three stage process. The stages in this process are determining vital it resources, determining issues impacts and acceptable outage time, assign recovery priorities, settlement agreements, litigation files, department file cabinets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Crime And IT Fraud Icon Exclamation Ppt PowerPoint Presentation Complete Deck
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cyber crime and it fraud icon exclamation ppt powerpoint presentation complete deck is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc.Welcome to our selection of the Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.
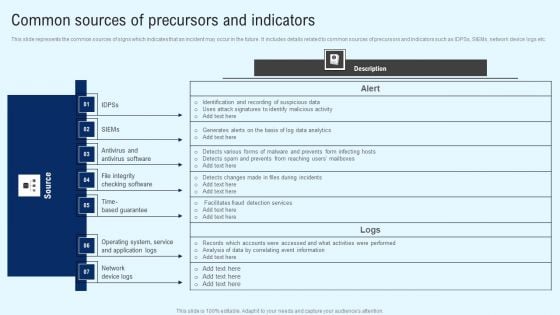
Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
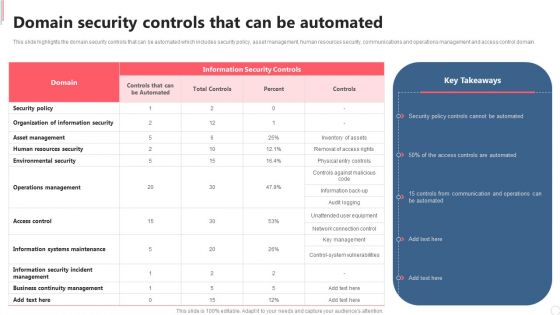
Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF.
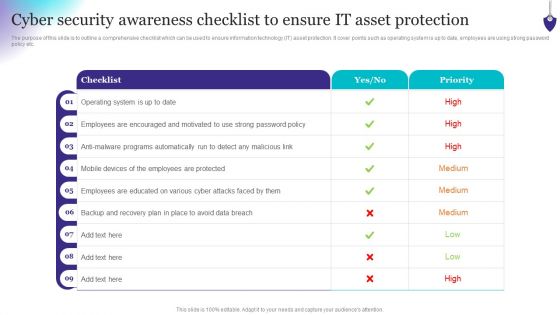
Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
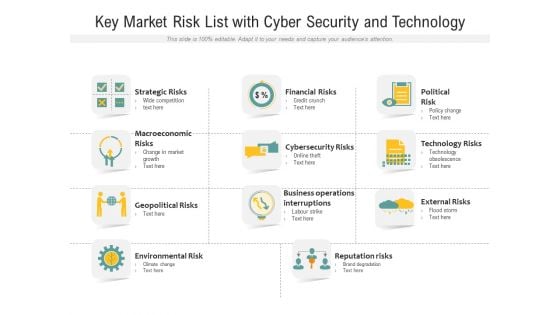
Key Market Risk List With Cyber Security And Technology Ppt PowerPoint Presentation File Show PDF
Showcasing this set of slides titled key market risk list with cyber security and technology ppt powerpoint presentation file show pdf. The topics addressed in these templates are strategic risks, macroeconomic, geopolitical risks, environmental risk, financial risks, cybersecurity risks, political risk, technology risks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Case Study 2 Banks Cyber Security Infrastructure Ppt Pictures Example PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges Deliver an awe inspiring pitch with this creative case study 2 banks cyber security infrastructure ppt pictures example pdf bundle. Topics like implemented, integrated, approach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Budget For Effective Threat Management At Workplace Structure PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative cyber security administration in organization budget for effective threat management at workplace structure pdf bundle. Topics like incident management, onboarding, process, release can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Create an editable Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
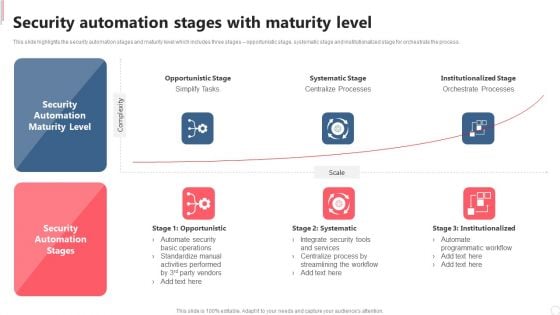
Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
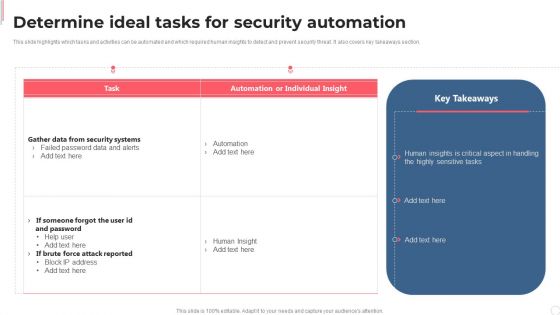
Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
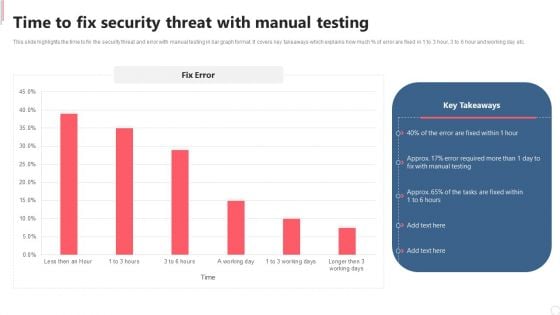
Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. This Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This modern and well-arranged Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
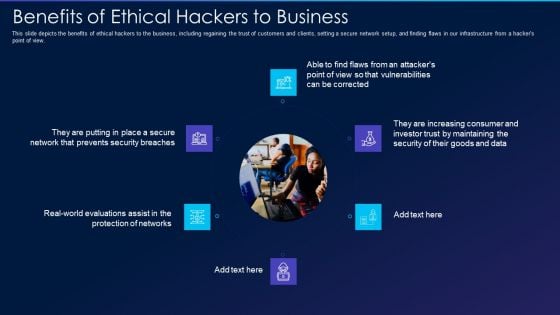
Cyber Exploitation IT Benefits Of Ethical Hackers To Business Brochure PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view. Presenting cyber exploitation it benefits of ethical hackers to business brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, evaluations, maintaining. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Mitigate Cyber Security Risks Selecting Security Incident Management Software Ppt Styles Influencers PDF
Presenting this set of slides with name strategies to mitigate cyber security risks selecting security incident management software ppt styles influencers pdf. This is a one stage process. The stages in this process are security incident forms, automated workflows, centralized platform, access rights, api integration, information security prevention, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Risk Management Plan Current Security Infrastructure Performance Analysis Icons PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative cyber security risk management plan current security infrastructure performance analysis icons pdf bundle. Topics like technology, target, plan, vulnerability intelligence, security infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
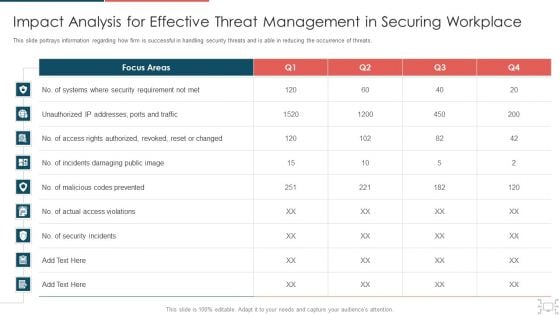
Cyber Security Administration In Organization Impact Analysis For Effective Threat Management Securing Rules PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative cyber security administration in organization impact analysis for effective threat management securing rules pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
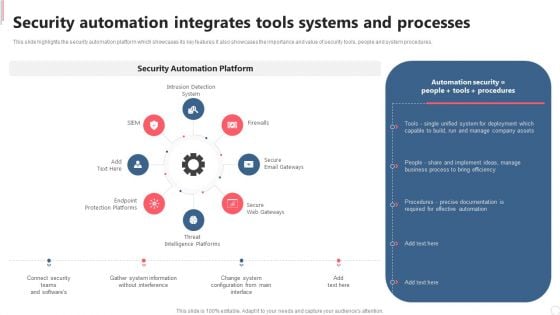
Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. There are so many reasons you need a Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
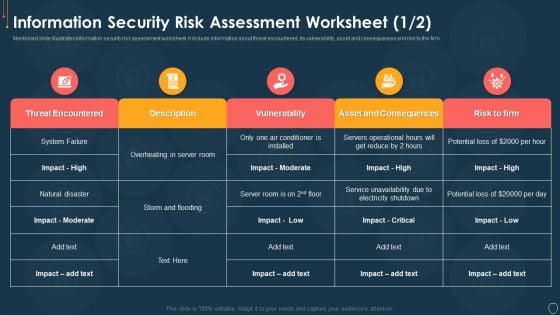
Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Consequences Diagrams PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver an awe inspiring pitch with this creative cyber security risk management plan information security risk assessment worksheet consequences diagrams pdf bundle. Topics like threat encountered, its vulnerability, asset and consequences, risk to the firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
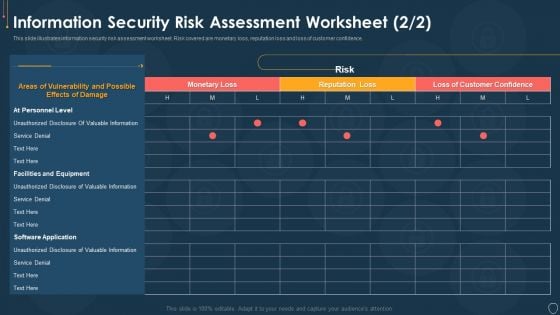
Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Service Graphics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan information security risk assessment worksheet service graphics pdf. Use them to share invaluable insights on monetary loss, reputation loss, loss of customer confidence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
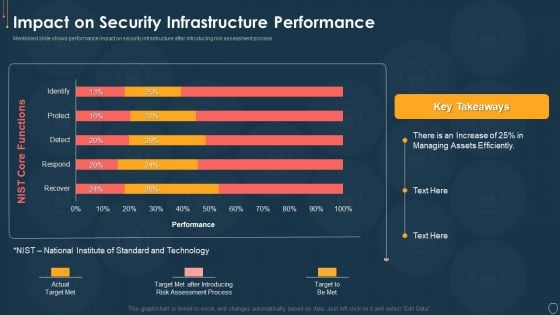
Cyber Security Risk Management Plan Impact On Security Infrastructure Performance Microsoft PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact on security infrastructure performance microsoft pdf. Use them to share invaluable insights on efficiently, process, target, technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Information Security Risk Management Dashboard Sample PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative cyber security risk management plan information security risk management dashboard sample pdf bundle. Topics like vulnerabilities, entities, action plan, risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Cyber Security Administration In Organization Security Sample PDF
This is a table of contents cyber security administration in organization security sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring, financial, assets, security, workforce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Asset Security Categorization Professional PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Deliver an awe inspiring pitch with this creative cyber security administration in organization addressing asset security categorization professional pdf bundle. Topics like executive, ownership, categorization, integrity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
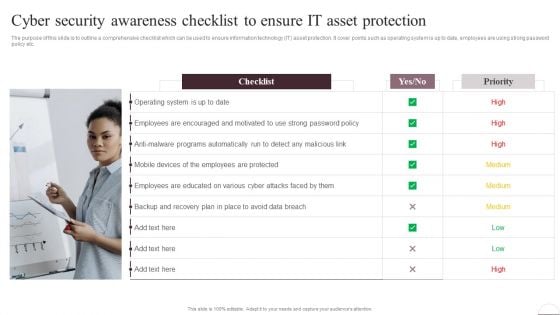
Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Get a simple yet stunning designed Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Slidegeeks has constructed Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
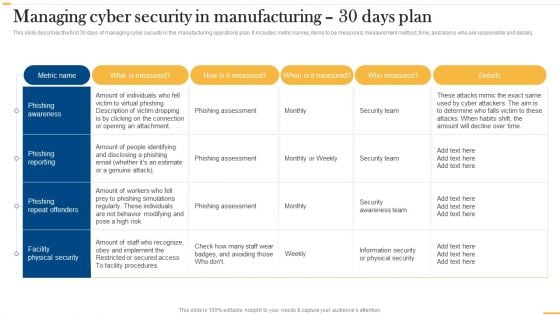
Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Slidegeeks is here to make your presentations a breeze with Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
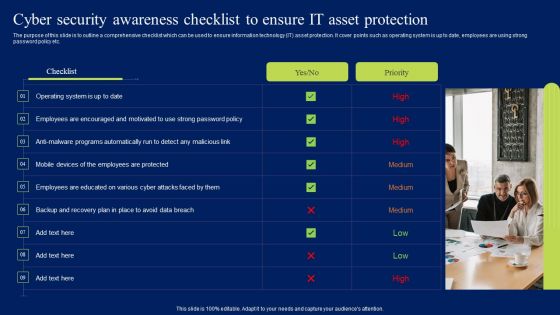
Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
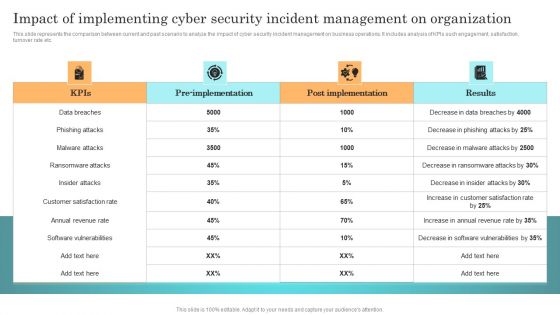
Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
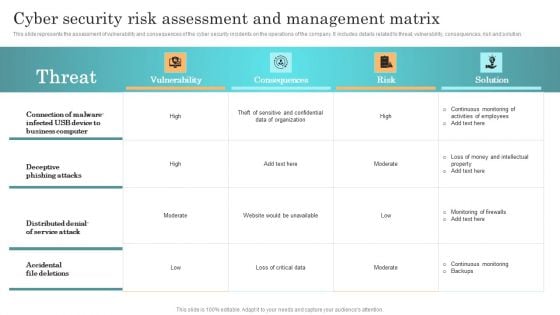
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present like a pro with Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
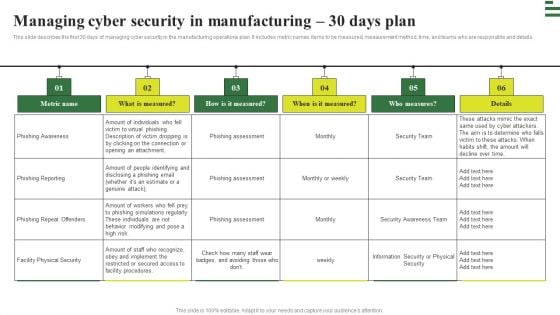
Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.


 Continue with Email
Continue with Email

 Home
Home


































