Cyber Attack
Virus On Screen Online Crime Threat From Hacker Vector Icon Ppt PowerPoint Presentation Gallery Smartart PDF
Presenting virus on screen online crime threat from hacker vector icon ppt powerpoint presentation gallery smartart pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including virus on screen online crime threat from hacker vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Hacker Icon For Online Security Ppt PowerPoint Presentation Styles Example PDF
Persuade your audience using this hacker icon for online security ppt powerpoint presentation styles example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including hacker icon for online security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Hacker Stealing Business Confidential Data Base Through Internet Threats Ppt PowerPoint Presentation File Pictures PDF
Persuade your audience using this hacker stealing business confidential data base through internet threats ppt powerpoint presentation file pictures pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including hacker stealing business confidential data base through internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Various Channels Used By Hackers To Launch Internet Threats Ppt PowerPoint Presentation File Show PDF
Presenting various channels used by hackers to launch internet threats ppt powerpoint presentation file show pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including various channels used by hackers to launch internet threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Vector Illustrating Hacker Launching Internet Threats Through Malware Ppt PowerPoint Presentation Icon Backgrounds PDF
Persuade your audience using this vector illustrating hacker launching internet threats through malware ppt powerpoint presentation icon backgrounds pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector illustrating hacker launching internet threats through malware. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
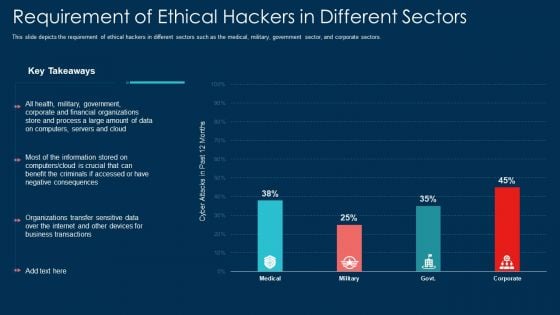
Requirement Of Ethical Hackers In Different Sectors Ppt Model Example File PDF
This slide depicts the requirement of ethical hackers in different sectors such as the medical, military, government sector, and corporate sectors. Deliver and pitch your topic in the best possible manner with this requirement of ethical hackers in different sectors ppt model example file pdf. Use them to share invaluable insights on information, benefit, process, organizations, financial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Data Services Certification Programs Certified Ethical Hacker CEH Career Path Graphics PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc. Presenting IT Data Services Certification Programs Certified Ethical Hacker CEH Career Path Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Information, Management, Requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
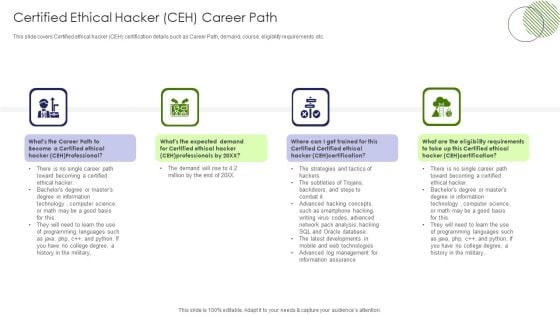
IT Professional Data Certification Program Certified Ethical Hacker CEH Career Path Guidelines PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc. Presenting IT Professional Data Certification Program Certified Ethical Hacker CEH Career Path Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Information, Demand, Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF
This slide talks about the skills required for security operation teams. The purpose of this slide is to showcase the various skills that can help SecOps to secure an organization completely. The primary skills include no-code automation, communicating modern threats from first principles, peer influence, and so on. Are you searching for a Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF from Slidegeeks today.

Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF
This slide outlines the critical outcomes that are handled by the security operations team. The purpose of this slide is to demonstrate the various key outcomes, their activities, responsible person and remarks. The main outcomes include incident management, incident preparation and threat intelligence. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
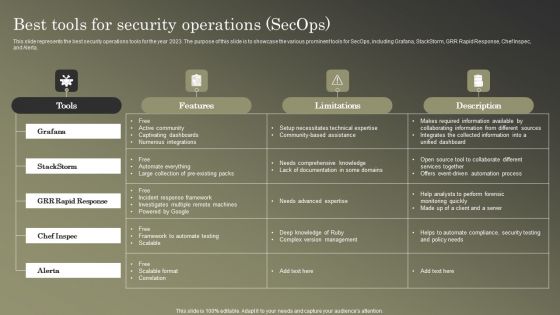
Cybersecurity Operations Cybersecops Best Tools For Security Operations Secops Graphics PDF

Cybersecurity Operations Cybersecops Steps To Build Security Operations Center Structure PDF
This slide represents the main steps to developing a security operations center. The purpose of this slide is to highlight the main building steps involved in a SecOps creation. These steps include selecting a service model, location, technology, people and processes. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cybersecurity Operations Cybersecops Steps To Build Security Operations Center Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

IT Data Services Certification Programs Certified Ethical Hacker CEH Ob Description Clipart PDF
This slide covers Certified ethical hacker CEH certifications Training and Exam Cost, Job Description, Roles and responsibilities and average salary package etc. Presenting IT Data Services Certification Programs Certified Ethical Hacker CEH Ob Description Clipart PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Organization, Networks Check Periodically, Purchases. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
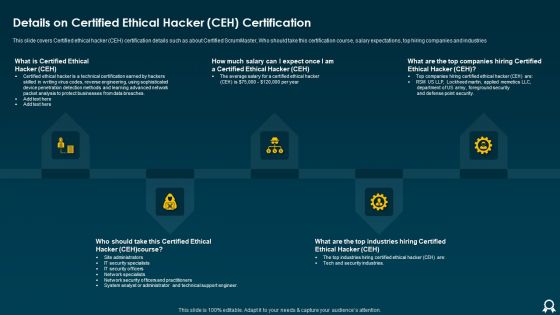
IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries. This is a IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Average Salary, Point Security, Methods. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
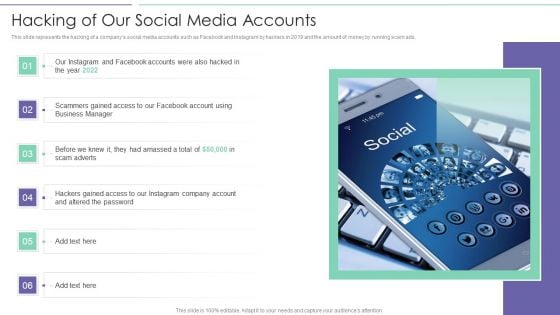
IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2019 and the amount of money by running scam ads.Presenting IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Scammers Gained, Business Manager, Altered The Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
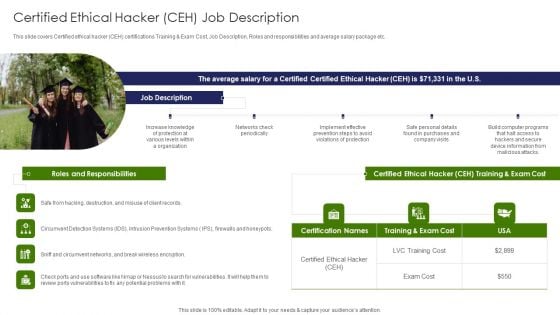
IT Professional Data Certification Program Certified Ethical Hacker CEH Job Description Mockup PDF
This slide covers Certified ethical hacker CEH certifications Training And Exam Cost, Job Description, Roles and responsibilities and average salary package etc. Presenting IT Professional Data Certification Program Certified Ethical Hacker CEH Job Description Mockup PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Potential, Exam Cost, Device Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Certified Ethical Hacker CEH Job Description IT Certifications To Enhance Icons PDF
This slide covers Certified ethical hacker CEH certifications Training Exam Cost, Job Description, Roles and responsibilities and average salary package etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Certified Ethical Hacker CEH Job Description IT Certifications To Enhance Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
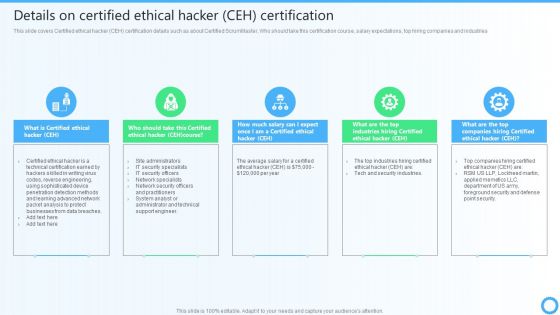
Details On Certified Ethical Hacker CEH Certification IT Certifications To Enhance Slides PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries.Slidegeeks has constructed Details On Certified Ethical Hacker CEH Certification IT Certifications To Enhance Slides PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Stock Photo Chess Pawns Checkmate PowerPoint Slide
This image slide is designed with graphics of chess pawns. This image contains white chess pawn wearing American hat and standing with black pawn depicting concepts of leadership, business, game strategy etc. You can use this layout to display your content in an interesting, eye-catching manner.
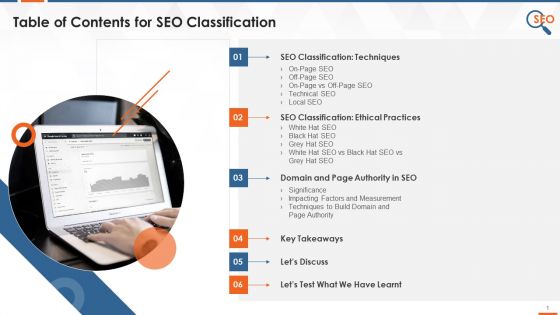
Table Of Contents For SEO Types Training Ppt
This slide showcases the table of contents for the session SEO classification. The topics covered are SEO classification based on techniques On-Page, Off-Page, Local and Technical SEO and ethical practices White, Grey and Black Hat SEO, domain and page authority in SEO.
Cloud Computing Wifi Safety Upload Social Network Ppt Slides Graphics
This power point icon template has been designed with graphic of cloud computing, wifi and social network. These icons can be used for data upload safety features and social networking. Use these icons for social network and technology related presentations.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF
This slide outlines the roles and responsibilities of the security operations center team. The purpose of this slide is to showcase the roles as well as duties of the SOC team. The prominent roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Welcome to our selection of the Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
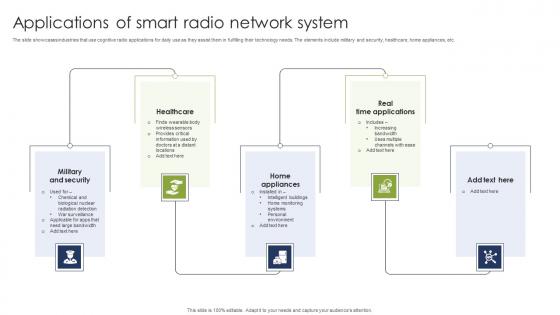
Applications Of Smart Radio Network System Summary Pdf
The slide showcases industries that use cognitive radio applications for daily use as they assist them in fulfilling their technology needs. The elements include military and security, healthcare, home appliances, etc. Showcasing this set of slides titled Applications Of Smart Radio Network System Summary Pdf. The topics addressed in these templates are Military Security, Healthcare, Home Appliances. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases industries that use cognitive radio applications for daily use as they assist them in fulfilling their technology needs. The elements include military and security, healthcare, home appliances, etc.
Ukraine Cyberwarfare Hacker Group Anonymous Has Waged A Cyberwar Against Russia Icons Pdf
This slide depicts the anonymous organization and how they have started a cyberwar against Russia by gathering worldwide hackers through Twitter. This is a ukraine cyberwarfare hacker group anonymous has waged a cyberwar against russia icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like the organization was accused of taking down the websites of the Russian energy company Gazprom, the state controlled Russian news channel RT, and many Russian and Belarusian government entities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
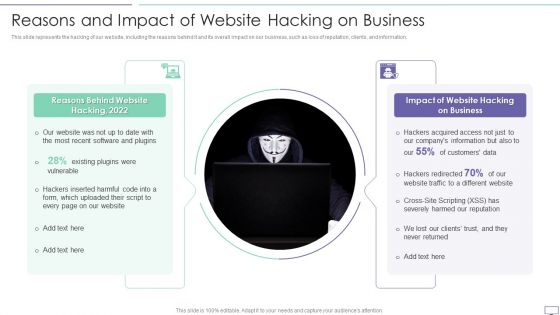
IT Security Hacker Reasons And Impact Of Website Hacking On Business Template PDF
This slide represents the hacking of our website, including the reasons behind it and its overall impact on our business, such as loss of reputation, clients, and information.Deliver an awe inspiring pitch with this creative IT Security Hacker Reasons And Impact Of Website Hacking On Business Template PDF bundle. Topics like Recent Software, Inserted Harmful, Companys Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
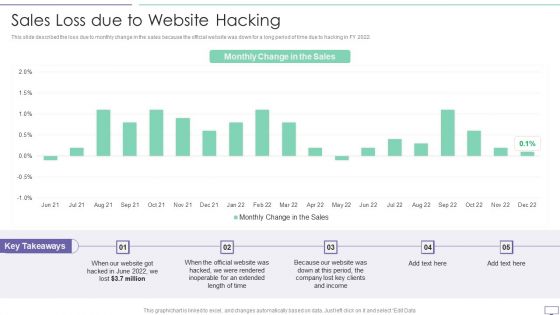
IT Security Hacker Sales Loss Due To Website Hacking Introduction PDF
This slide described the loss due to monthly change in the sales because the official website was down for a long period of time due to hacking in FY 2022.Deliver an awe inspiring pitch with this creative IT Security Hacker Sales Loss Due To Website Hacking Introduction PDF bundle. Topics like Inoperable, Extended, Clients Income can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Network Access Computer PowerPoint Templates And PowerPoint Backgrounds 0411
Microsoft PowerPoint Template and Background with network access of computer Clip the wings of failure with our Network Access Computer PowerPoint Templates And PowerPoint Backgrounds 0411. You will come out on top.

Network Access Computer PowerPoint Themes And PowerPoint Slides 0411
Microsoft PowerPoint Theme and Slide with network access of computer Put in our Network Access Computer PowerPoint Themes And PowerPoint Slides 0411 as the catalyst. Churn out new equations with your ideas.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
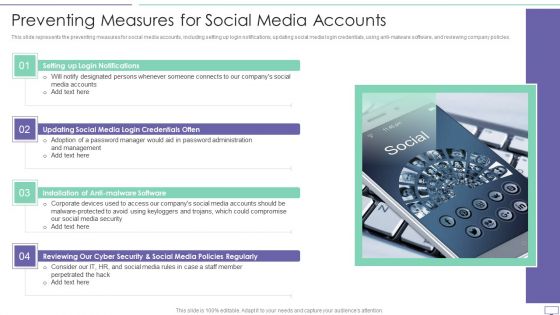
IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies.Presenting IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Login Notifications, Malware Software, Policies Regularly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
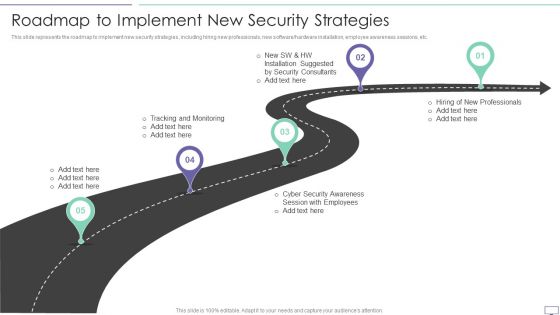
IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software hardware installation, employee awareness sessions, etc.This is a IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking And Monitoring, Security Awareness, Installation Suggested. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
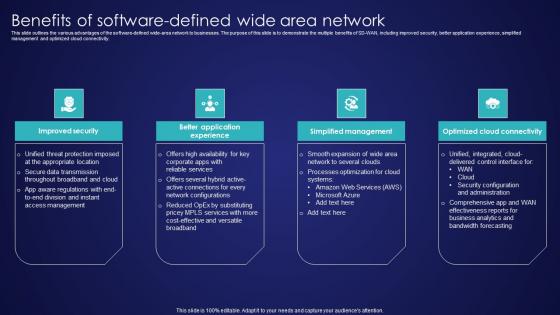
Benefits Of Software Defined Wide Area Network Wide Area Network Services Summary Pdf
This slide outlines the various advantages of the software-defined wide-area network to businesses. The purpose of this slide is to demonstrate the multiple benefits of SD-WAN, including improved security, better application experience, simplified management and optimized cloud connectivity. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Software Defined Wide Area Network Wide Area Network Services Summary Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the various advantages of the software-defined wide-area network to businesses. The purpose of this slide is to demonstrate the multiple benefits of SD-WAN, including improved security, better application experience, simplified management and optimized cloud connectivity.
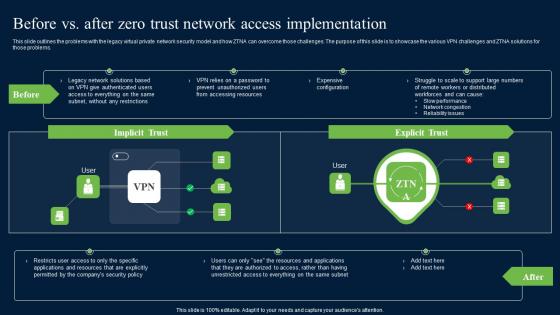
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
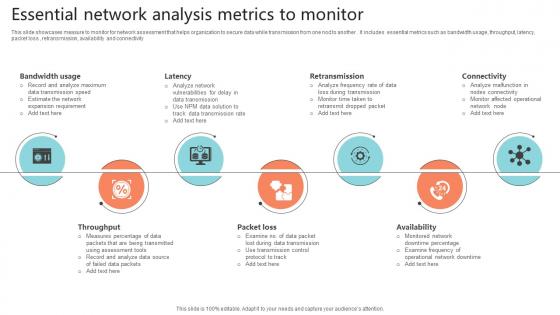
Essential Network Analysis Metrics To Monitor Portrait Pdf
This slide showcases measure to monitor for network assessment that helps organization to secure data while transmission from one nod to another . It includes essential metrics such as bandwidth usage, throughput, latency, packet loss , retransmission, availability and connectivity.Pitch your topic with ease and precision using this Essential Network Analysis Metrics To Monitor Portrait Pdf This layout presents information on Bandwidth Usage, Retransmission, Throughput It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases measure to monitor for network assessment that helps organization to secure data while transmission from one nod to another . It includes essential metrics such as bandwidth usage, throughput, latency, packet loss , retransmission, availability and connectivity

Impact Network Marketing Strategic Plan Develop Multi Level Marketing Structure Pdf
This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Network Marketing Strategic Plan Develop Multi Level Marketing Structure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Network Marketing Strategic Plan Develop Multi Level Marketing Structure Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation.

Optimizing Banking Operations Model Strategic Plan Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase a strategic plan to optimize the traditional banking operations model to simplify the various tasks. The attributes include goal, objective, operational strategy, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Optimizing Banking Operations Model Strategic Plan Incorporating Banking Operational Growth a try. Our experts have put a lot of knowledge and effort into creating this impeccable Optimizing Banking Operations Model Strategic Plan Incorporating Banking Operational Growth. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of the mentioned slide is to showcase a strategic plan to optimize the traditional banking operations model to simplify the various tasks. The attributes include goal, objective, operational strategy, etc.
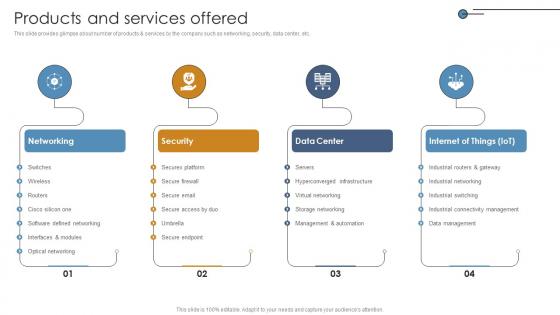
Products And Services Offered Networking Solutions Manufacturer Investor Funding Elevator Pitch Deck
This slide provides glimpse about number of products services by the company such as networking, security, data center, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Networking Solutions Manufacturer Investor Funding Elevator Pitch Deck to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide provides glimpse about number of products services by the company such as networking, security, data center, etc.
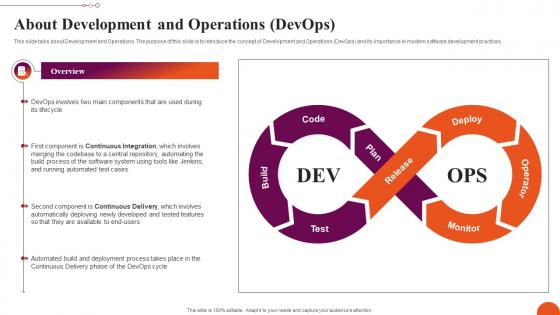
About Development And Operations Exploring Machine Learning Operations Portrait Pdf
This slide talks about Development and Operations. The purpose of this slide is to introduce the concept of Development and Operations DevOps and its importance in modern software development practices. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our About Development And Operations Exploring Machine Learning Operations Portrait Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into About Development And Operations Exploring Machine Learning Operations Portrait Pdf This slide talks about Development and Operations. The purpose of this slide is to introduce the concept of Development and Operations DevOps and its importance in modern software development practices.
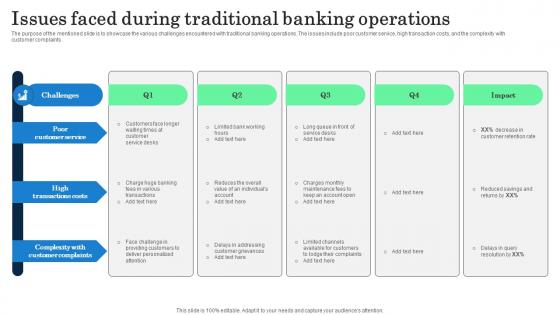
Issues Faced During Traditional Banking Operations Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various challenges encountered with traditional banking operations. The issues include poor customer service, high transaction costs, and the complexity with customer complaints. Presenting this PowerPoint presentation, titled Issues Faced During Traditional Banking Operations Incorporating Banking Operational Growth, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Issues Faced During Traditional Banking Operations Incorporating Banking Operational Growth. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Issues Faced During Traditional Banking Operations Incorporating Banking Operational Growth that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The purpose of the mentioned slide is to showcase the various challenges encountered with traditional banking operations. The issues include poor customer service, high transaction costs, and the complexity with customer complaints.
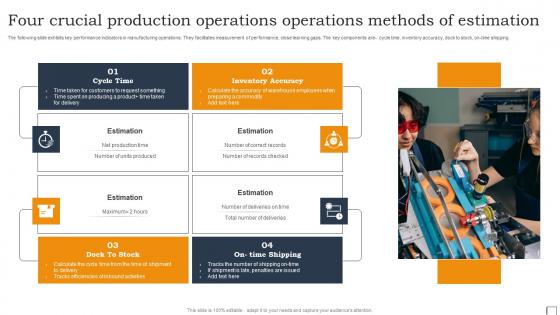
Four Crucial Production Operations Operations Methods Of Estimation Infographics Pdf
The following slide exhibits key performance indicators in manufacturing operations. They facilitates measurement of performance, close learning gaps. The key components are- cycle time, inventory accuracy, dock to stock, on-time shipping. Showcasing this set of slides titled Four Crucial Production Operations Operations Methods Of Estimation Infographics Pdf. The topics addressed in these templates are Cycle Time, Inventory Accuracy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide exhibits key performance indicators in manufacturing operations. They facilitates measurement of performance, close learning gaps. The key components are- cycle time, inventory accuracy, dock to stock, on-time shipping.
Banking Operations Performance Tracking Dashboard Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase a performance tracking dashboard of banking operations. It includes metrics such as accounts opened and closed, total deposits, referrals by product, etc. Want to ace your presentation in front of a live audience Our Banking Operations Performance Tracking Dashboard Incorporating Banking Operational Growth can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of the mentioned slide is to showcase a performance tracking dashboard of banking operations. It includes metrics such as accounts opened and closed, total deposits, referrals by product, etc.

Goals And Objectives Of Operations Strategy Incorporating Banking Operational Growth
The mentioned slide showcases the banking operations transformation strategy by outlining various strategies, missions, and visions along with KPIs to track the overall performance. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Goals And Objectives Of Operations Strategy Incorporating Banking Operational Growth from Slidegeeks and deliver a wonderful presentation. The mentioned slide showcases the banking operations transformation strategy by outlining various strategies, missions, and visions along with KPIs to track the overall performance
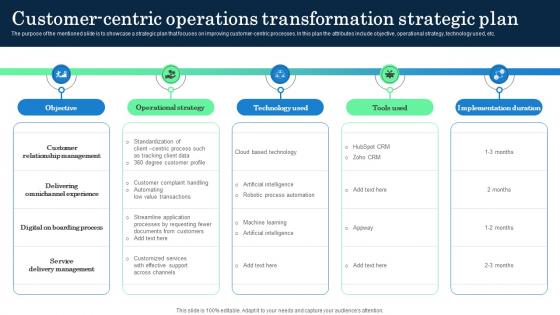
Customer Centric Operations Transformation Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase a strategic plan that focuses on improving customer-centric processes. In this plan the attributes include objective, operational strategy, technology used, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Customer Centric Operations Transformation Incorporating Banking Operational Growth is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Customer Centric Operations Transformation Incorporating Banking Operational Growth and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The purpose of the mentioned slide is to showcase a strategic plan that focuses on improving customer-centric processes. In this plan the attributes include objective, operational strategy, technology used, etc.
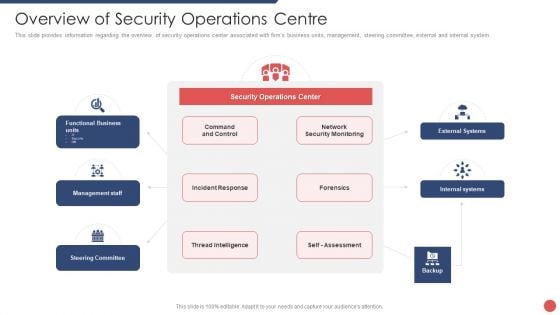
Security Functioning Centre Overview Of Security Operations Centre Summary PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security functioning centre overview of security operations centre summary pdf. Use them to share invaluable insights on management, thread intelligence, network security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
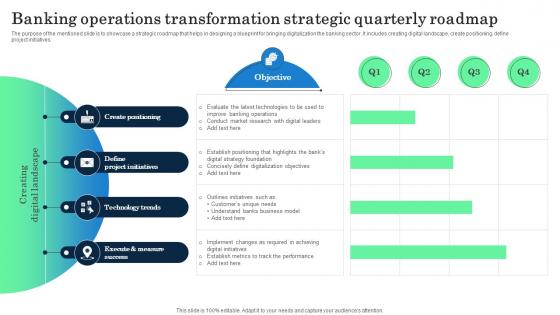
Banking Operations Transformation Strategic Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase a strategic roadmap that helps in designing a blueprint for bringing digitalization the banking sector. It includes creating digital landscape, create positioning, define project initiatives. There are so many reasons you need a Banking Operations Transformation Strategic Incorporating Banking Operational Growth. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of the mentioned slide is to showcase a strategic roadmap that helps in designing a blueprint for bringing digitalization the banking sector. It includes creating digital landscape, create positioning, define project initiatives.
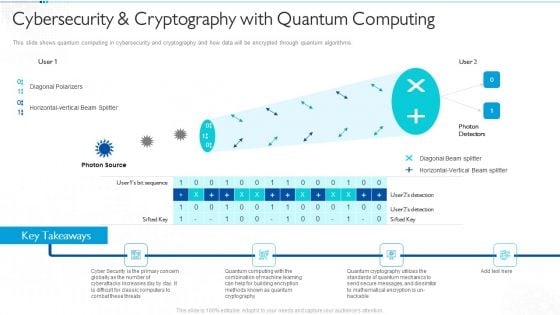
Quantum Computing For Everyone IT Cybersecurity And Cryptography With Quantum Computing Ideas PDF
This slide shows quantum computing in cybersecurity and cryptography and how data will be encrypted through quantum algorithms. Presenting quantum computing for everyone it cybersecurity and cryptography with quantum computing ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cryptography, quantum computing, cyberattacks, globally. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
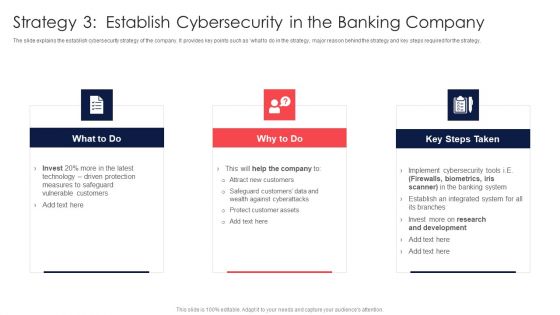
Digital Transformation Of Consumer Strategy 3 Establish Cybersecurity In The Banking Company Ideas PDF
The slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy. Presenting Digital Transformation Of Consumer Strategy 3 Establish Cybersecurity In The Banking Company Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Driven Protection, Vulnerable Customers, Against Cyberattack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
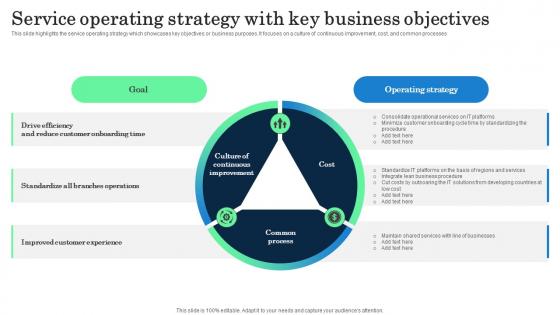
Service Operating Strategy With Key Business Objectives Incorporating Banking Operational Growth
This slide highlights the service operating strategy which showcases key objectives or business purposes. It focuses on a culture of continuous improvement, cost, and common processes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Service Operating Strategy With Key Business Objectives Incorporating Banking Operational Growth. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Service Operating Strategy With Key Business Objectives Incorporating Banking Operational Growth today and make your presentation stand out from the rest This slide highlights the service operating strategy which showcases key objectives or business purposes. It focuses on a culture of continuous improvement, cost, and common processes
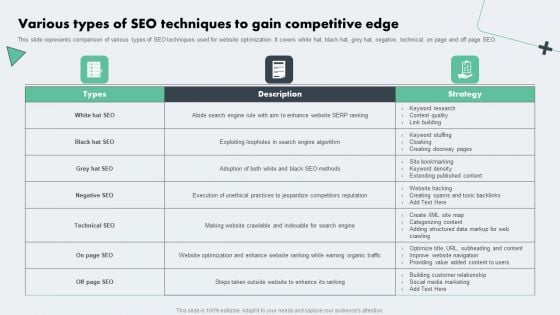
Deploying Online Marketing Various Types Of SEO Techniques To Gain Competitive Edge Clipart PDF
This slide represents comparison of various types of SEO techniques used for website optimization. It covers white hat, black hat, grey hat, negative, technical, on page and off page SEO. Do you know about Slidesgeeks Deploying Online Marketing Various Types Of SEO Techniques To Gain Competitive Edge Clipart PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
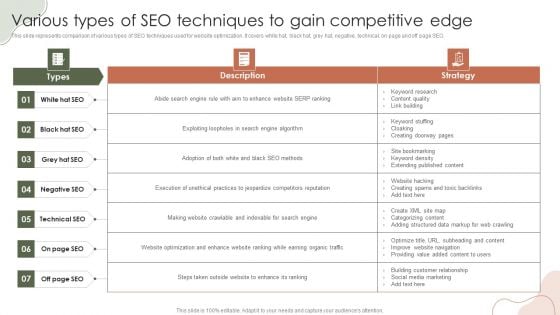
Digital Marketing Approach For Brand Awareness Various Types Of SEO Techniques To Gain Competitive Edge Diagrams PDF
This slide represents comparison of various types of SEO techniques used for website optimization. It covers white hat, black hat, grey hat, negative, technical, on page and off page SEO. Slidegeeks is here to make your presentations a breeze with Digital Marketing Approach For Brand Awareness Various Types Of SEO Techniques To Gain Competitive Edge Diagrams PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
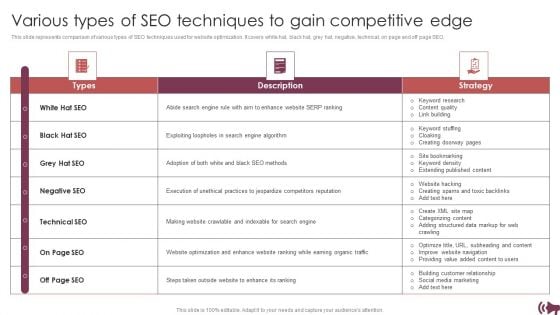
Guide Digital Advertising Optimize Lead Targeting Various Types Of Seo Techniques To Gain Competitive Edge Ideas PDF
This slide represents comparison of various types of SEO techniques used for website optimization. It covers white hat, black hat, grey hat, negative, technical, on page and off page SEO. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Guide Digital Advertising Optimize Lead Targeting Various Types Of Seo Techniques To Gain Competitive Edge Ideas PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
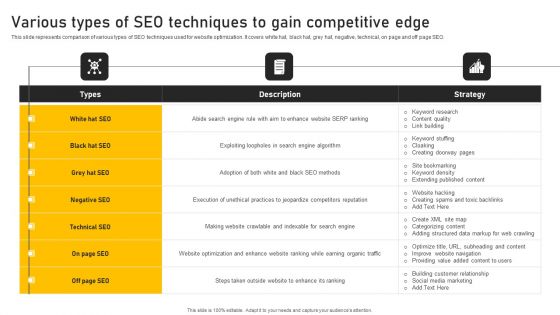
Online Ads Strategic Plan For Effective Marketing Various Types Of SEO Techniques To Gain Competitive Edge Professional PDF
This slide represents comparison of various types of SEO techniques used for website optimization. It covers white hat, black hat, grey hat, negative, technical, on page and off page SEO. Slidegeeks has constructed Online Ads Strategic Plan For Effective Marketing Various Types Of SEO Techniques To Gain Competitive Edge Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
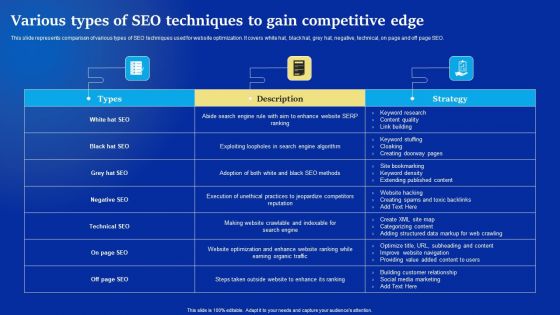
Online Advertising Campaign For Brand Recognition Various Types Of SEO Techniques To Gain Competitive Edge Designs PDF
This slide represents comparison of various types of SEO techniques used for website optimization. It covers white hat, black hat, grey hat, negative, technical, on page and off page SEO. Slidegeeks has constructed Online Advertising Campaign For Brand Recognition Various Types Of SEO Techniques To Gain Competitive Edge Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Agenda Incorporating Banking Operational Growth Strategies
Find a pre-designed and impeccable Agenda Incorporating Banking Operational Growth Strategies. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda Incorporating Banking Operational Growth Strategies are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
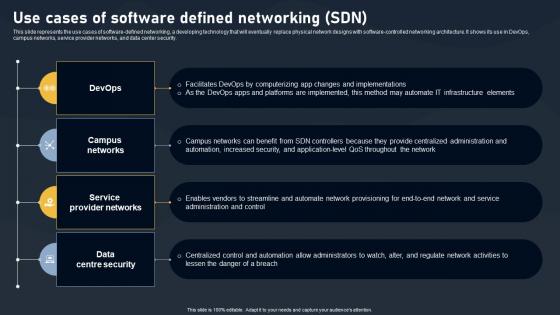
Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf. This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Key Elements Of Business Operations Developing Extensive Plan For Operational Brochure Pdf
Welcome to our selection of the Key Elements Of Business Operations Developing Extensive Plan For Operational Brochure Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. Our Key Elements Of Business Operations Developing Extensive Plan For Operational Brochure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































