Cyber Safety

Cloud Managed Services Pricing Guide Agenda For Managed Services Pricing Guidelines Ppt Infographics Background PDF
Presenting this set of slides with name cloud managed services pricing guide agenda for managed services pricing guidelines ppt infographics background pdf. This is a six stage process. The stages in this process are infrastructure, analyzing, cyber security, monitoring, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
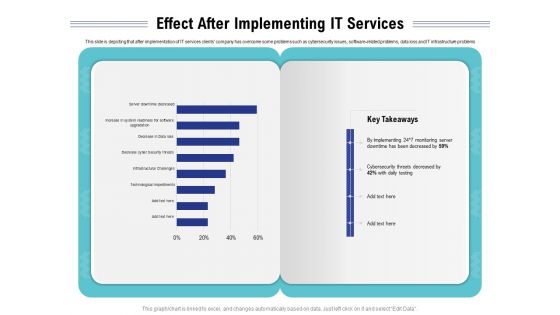
Cloud Managed Services Pricing Guide Effect After Implementing IT Services Ppt Styles Mockup PDF
Presenting this set of slides with name cloud managed services pricing guide effect after implementing it services ppt styles mockup pdf. The topics discussed in these slides are technological, cyber security, implementing, monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Support And Monitoring Services Pricing Agenda For IT Support And Monitoring Services Pricing Elements PDF
Presenting this set of slides with name it support and monitoring services pricing agenda for it support and monitoring services pricing elements pdf. This is a six stage process. The stages in this process are infrastructure, analyzing, monitoring, cyber security, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
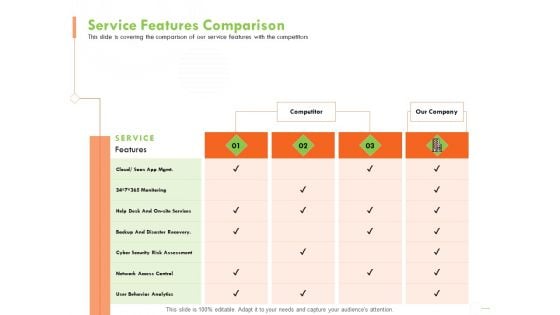
Welfare Work Value Service Features Comparison Ppt Outline Themes PDF
Presenting this set of slides with name welfare work value service features comparison ppt outline themes pdf. The topics discussed in these slides are monitoring, services, cyber security, analytics, network access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Tech Support Services Cost And Pricing Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name tech support services cost and pricing ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are monitoring, cyber security, infrastructure, implementing, services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
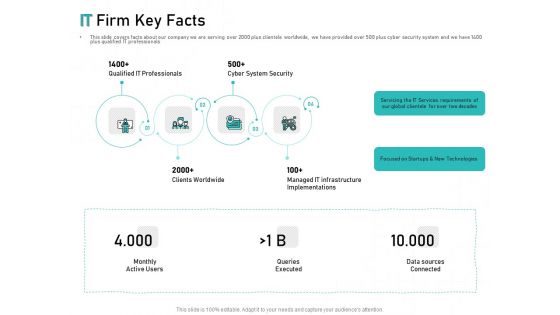
Tech Support Services Cost And Pricing IT Firm Key Facts Ppt PowerPoint Presentation Slides File Formats
Presenting this set of slides with name tech support services cost and pricing it firm key facts ppt powerpoint presentation slides file formats. This is a four stage process. The stages in this process are technologies, services, implementations, infrastructure, cyber system security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Managed Services Pricing Guide IT Firm Key Facts Ppt Infographics Visuals PDF
Presenting this set of slides with name cloud managed services pricing guide it firm key facts ppt infographics visuals pdf. The topics discussed in these slides are qualified it professionals, clients worldwide, cyber system security, managed it infrastructure implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
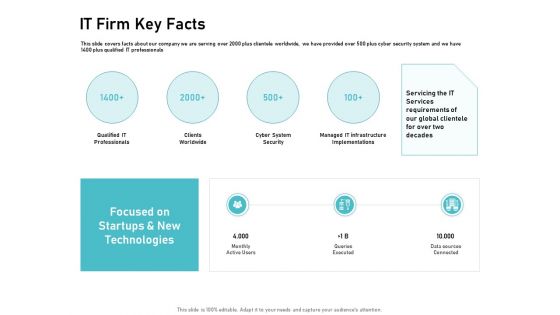
IT Support And Monitoring Services Pricing IT Firm Key Facts Ppt Portfolio Styles PDF
Presenting this set of slides with name it support and monitoring services pricing it firm key facts ppt portfolio styles pdf. The topics discussed in these slides are qualified it professionals, clients worldwide, cyber system security, managed it infrastructure implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
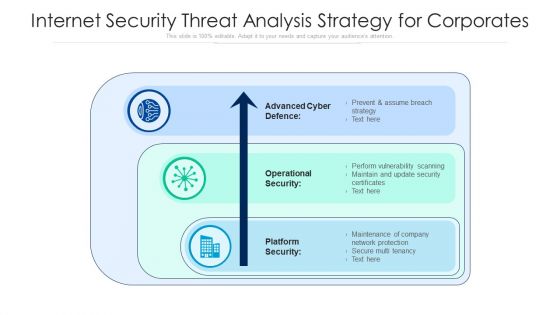
Internet Security Threat Analysis Strategy For Corporates Ppt PowerPoint Presentation File Picture PDF
Pitch your topic with ease and precision using this internet security threat analysis strategy for corporates ppt powerpoint presentation file picture pdf. This layout presents information on advanced cyber defence, operational security, platform security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Email Security Market Research Report Ppt PowerPoint Presentation Complete Deck With Slides

Global Cloud Based Email Security Market Ppt PowerPoint Presentation Complete Deck With Slides

Internet Security Threat Analysis Plan With Agents And Tactics Ppt PowerPoint Presentation Gallery Infographic Template PDF
Showcasing this set of slides titled internet security threat analysis plan with agents and tactics ppt powerpoint presentation gallery infographic template pdf. The topics addressed in these templates are corporations, hacktivists, cyber fighters. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Welfare Work Value Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name welfare work value ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are infrastructure, analyzing, cyber security, implementing, service. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
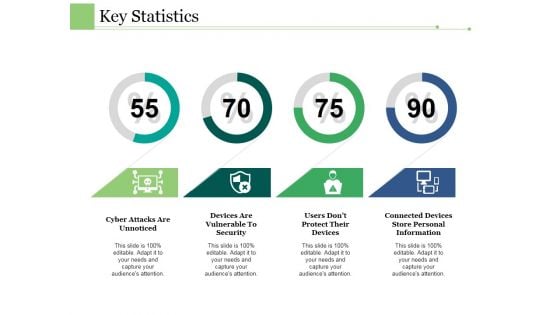
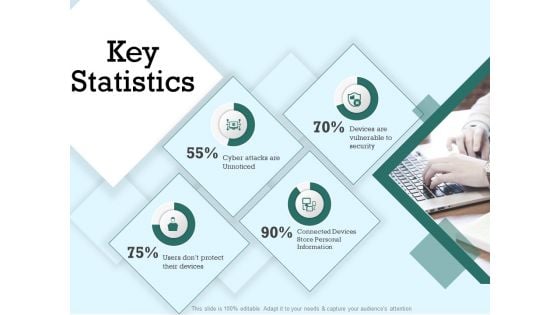
Key Statistics Ppt PowerPoint Presentation Show Sample
This is a key statistics ppt powerpoint presentation show sample. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users do not protect their devices, connected devices store personal information.
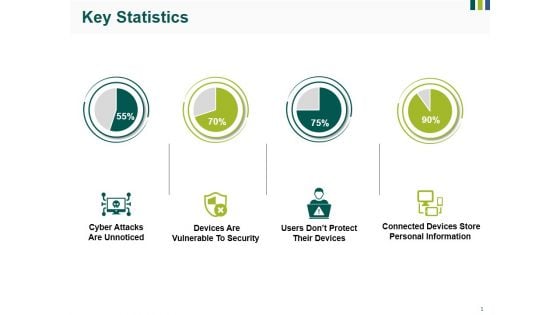
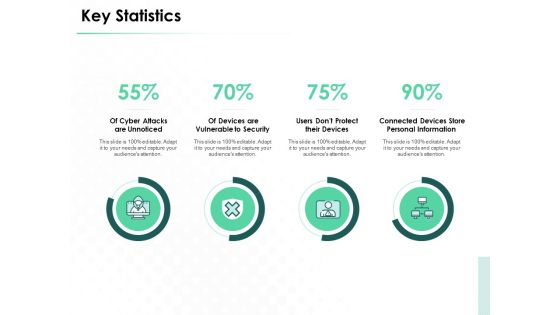
Key Statistics Ppt PowerPoint Presentation Gallery Format Ideas
This is a key statistics ppt powerpoint presentation gallery format ideas. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users dont protect their devices, connected devices store personal information.
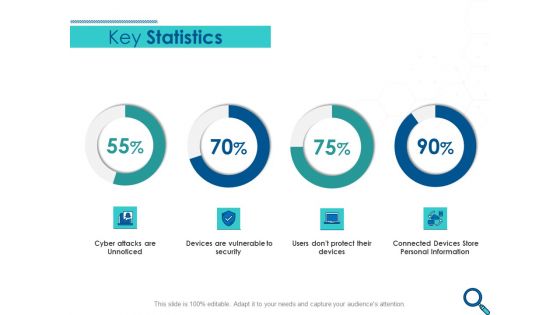
Evaluating Competitive Marketing Effectiveness Key Statistics Ppt Portfolio Ideas PDF
Presenting this set of slides with name evaluating competitive marketing effectiveness key statistics ppt portfolio ideas pdf. The topics discussed in these slides are cyber attacks are unnoticed, devices are vulnerable to security, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Survey Analysis Gain Marketing Insights Key Statistics Sample PDF
Presenting this set of slides with name survey analysis gain marketing insights key statistics sample pdf. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Welfare Work Value IT Firm Key Facts Ppt Pictures Icon PDF
Presenting this set of slides with name welfare work value it firm key facts ppt pictures icon pdf. This is a four stage process. The stages in this process are clients worldwide, cyber system security, infrastructure, implementations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Welfare Work Value Agenda For Welfare Work Value Ppt Professional Show PDF
Presenting this set of slides with name welfare work value agenda for welfare work value ppt professional show pdf. This is a six stage process. The stages in this process are analyzing, infrastructure, monitoring, cyber security, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
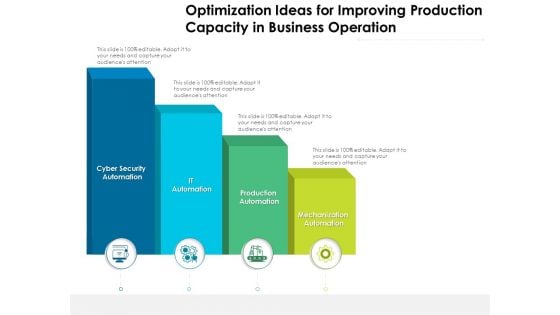
Optimization Ideas For Improving Production Capacity In Business Operation Ppt PowerPoint Presentation Outline Visual Aids PDF
Presenting this set of slides with name optimization ideas for improving production capacity in business operation ppt powerpoint presentation outline visual aids pdf. This is a four stage process. The stages in this process are mechanization automation, production automation, it automation, cyber security automation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Market Approach To Business Valuation Key Statistics Summary PDF
Presenting this set of slides with name market approach to business valuation key statistics summary pdf. This is a four stage process. The stages in this process are cyber attacks unnoticed, devices vulnerable security, users dont protect devices, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
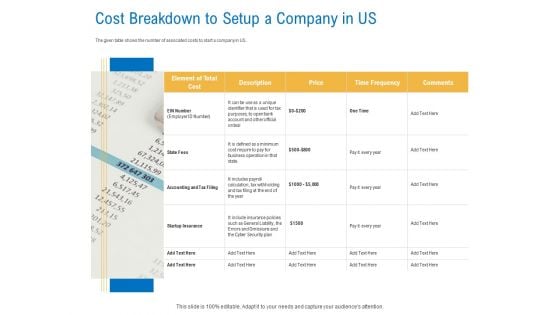
Digital Businesses Ecosystems Cost Breakdown To Setup A Company In Us Professional PDF
Deliver an awe inspiring pitch with this creative digital businesses ecosystems cost breakdown to setup a company in us professional pdf bundle. Topics like cyber security, plan, business, cost, price can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agile Best Practices For Effective Team Project Scope Management Plan For Agile Implementation Pictures PDF
Deliver an awe inspiring pitch with this creative agile best practices for effective team project scope management plan for agile implementation pictures pdf bundle. Topics like team communication, cyber security, budget, measurement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Evaluation Results Showing Bank Risk Ppt PowerPoint Presentation File Influencers PDF
Presenting evaluation results showing bank risk ppt powerpoint presentation file influencers pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including cyber security, perform, legal audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Incident Response Planning And Reporting Chart With Primary Skills Ppt PowerPoint Presentation Icon Ideas PDF
Pitch your topic with ease and precision using this incident response planning and reporting chart with primary skills ppt powerpoint presentation icon ideas pdf. This layout presents information on management, technical, cyber security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Incident Response Planning And Reporting Matrix With Activities Ppt PowerPoint Presentation Gallery Slide Download PDF
Pitch your topic with ease and precision using this incident response planning and reporting matrix with activities ppt powerpoint presentation gallery slide download pdf. This layout presents information on cyber security, technical, accountable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
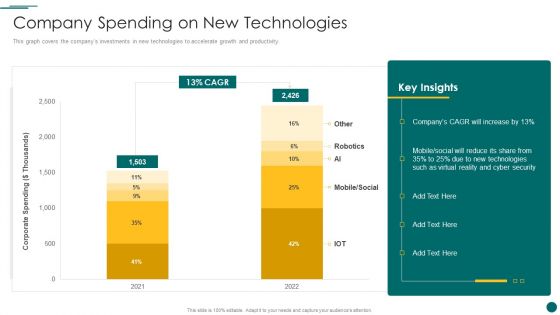
Organization Reinvention Company Spending On New Technologies Microsoft PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Reinvention Company Spending On New Technologies Microsoft PDF bundle. Topics like Social, Technologies, Cyber Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Andcryptography With Quantum Computing Ppt Pictures Backgrounds PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Andcryptography With Quantum Computing Ppt Pictures Backgrounds PDF. Use them to share invaluable insights on Cyber Security, Globally, Measurement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Find highly impressive Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.

Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Predictive Analytics For Empowering Outliers Model For Predictive Analytics Rules Pdf today and make your presentation stand out from the rest. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
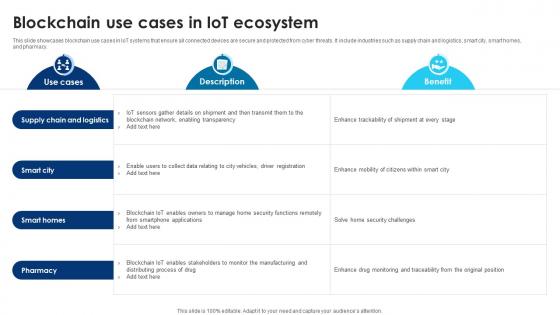
Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V
This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy.

Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf today and make your presentation stand out from the rest This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
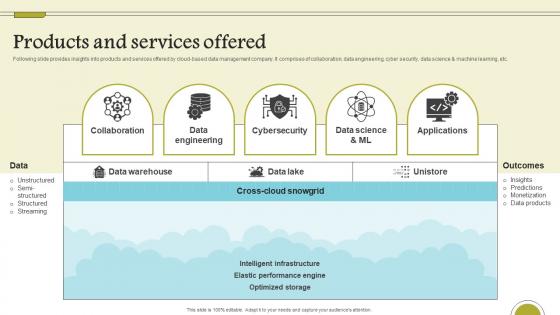
Products And Services Offered Cloud Data Computing Company Fund Raising Introduction Pdf
Following slide provides insights into products and services offered by cloud-based data management company. It comprises of collaboration, data engineering, cyber security, data science and machine learning, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Products And Services Offered Cloud Data Computing Company Fund Raising Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide provides insights into products and services offered by cloud-based data management company. It comprises of collaboration, data engineering, cyber security, data science and machine learning, etc.
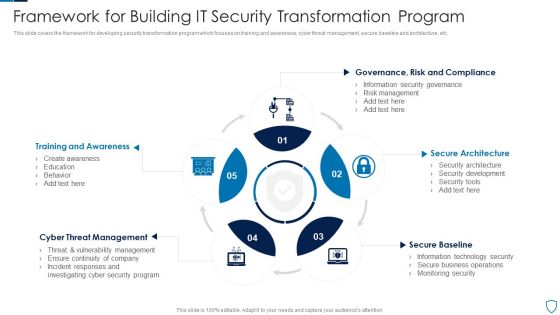
Framework For Building IT Security Transformation Program Pictures PDF
This slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc.Presenting Framework For Building IT Security Transformation Program Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Training Awareness, Threat Management, Secure Architecture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global 5G Network Security Market Dynamics Designs Pdf
This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc. Showcasing this set of slides titled Global 5G Network Security Market Dynamics Designs Pdf. The topics addressed in these templates are Market Dynamics, Description. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc.
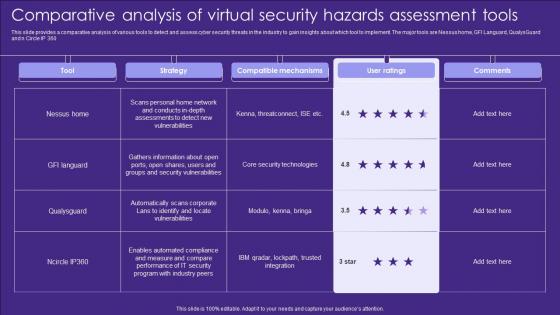
Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf
This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Pitch your topic with ease and precision using this Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf. This layout presents information on Strategy, Compatible Mechanisms, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360
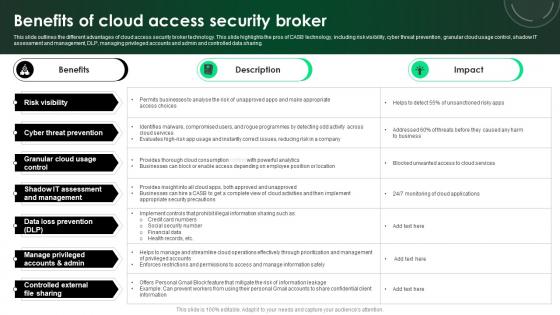
CASB 2 0 IT Benefits Of Cloud Access Security Broker
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. There are so many reasons you need a CASB 2 0 IT Benefits Of Cloud Access Security Broker. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing.

Complete Guide To Launch Best Practices For Website Security Management
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Get a simple yet stunning designed Complete Guide To Launch Best Practices For Website Security Management. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Guide To Launch Best Practices For Website Security Management can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.
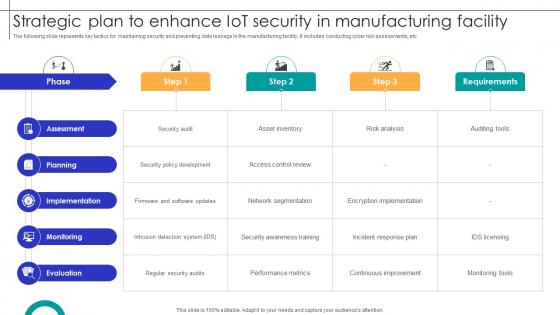
Strategic Plan To Enhance IOT Security In Manufacturing Facility Streamlining Production Ppt Sample
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Strategic Plan To Enhance IOT Security In Manufacturing Facility Streamlining Production Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.

Best Practices For Website Security Management Step By Step Guide Ideas PDF
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices For Website Security Management Step By Step Guide Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.
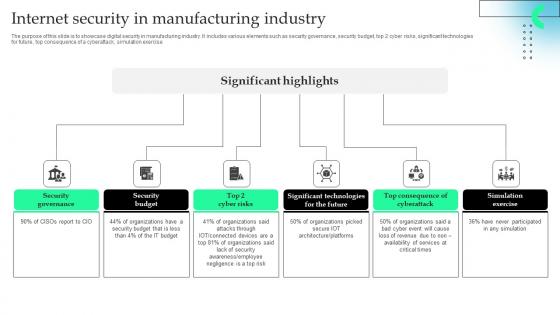
Internet Security In Manufacturing Industry Professional Pdf
The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.Pitch your topic with ease and precision using this Internet Security In Manufacturing Industry Professional Pdf This layout presents information on Security Governance, Security Budget, Significant Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.
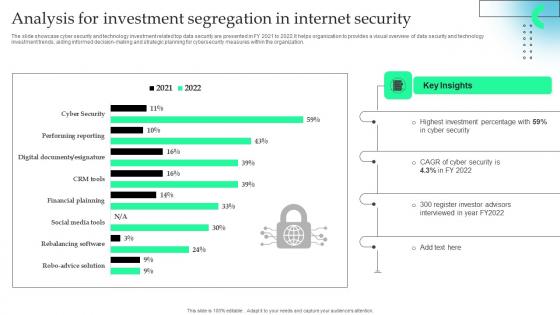
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.

Future Of Secure Web Gateway Technology Web Threat Protection System
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Future Of Secure Web Gateway Technology Web Threat Protection System and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.
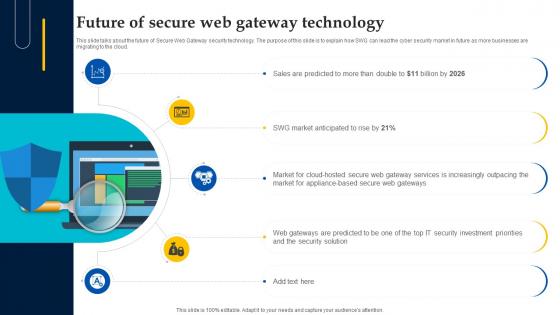
Web Access Control Solution Future Of Secure Web Gateway Technology
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. This modern and well-arranged Web Access Control Solution Future Of Secure Web Gateway Technology provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.
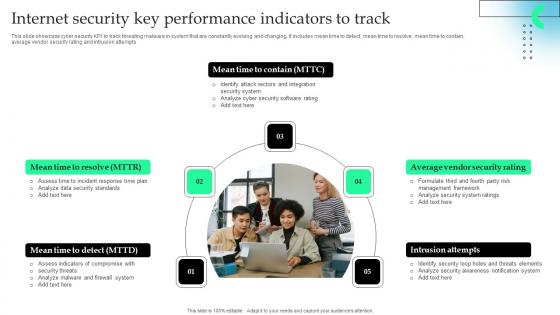
Internet Security Key Performance Indicators To Track Microsoft Pdf
This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.Showcasing this set of slides titled Internet Security Key Performance Indicators To Track Microsoft Pdf The topics addressed in these templates are Firewall System, Security Standards, Identify Attack All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.

Virtual Security Hazards Detection And Response Topics Pdf
This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps Showcasing this set of slides titled Virtual Security Hazards Detection And Response Topics Pdf. The topics addressed in these templates are Security Centre, Access Time, Cybersecurity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps
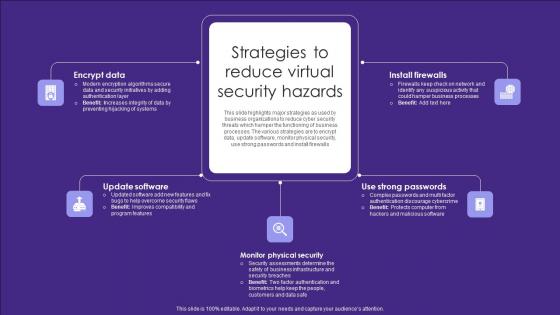
Strategies To Reduce Virtual Security Hazards Summary Pdf
This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls Showcasing this set of slides titled Strategies To Reduce Virtual Security Hazards Summary Pdf. The topics addressed in these templates are Install Firewalls, Strong Passwords, Physical Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls
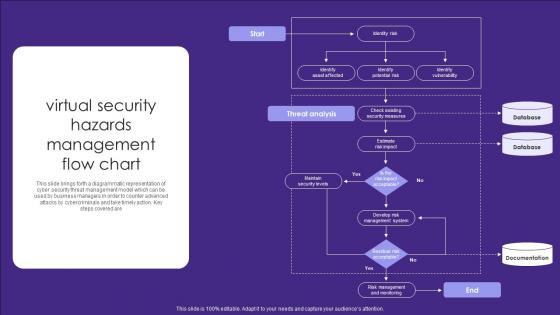
Virtual Security Hazards Management Flow Chart Infographics Pdf
This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Showcasing this set of slides titled Virtual Security Hazards Management Flow Chart Infographics Pdf. The topics addressed in these templates are Security Measures, Database, Documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are
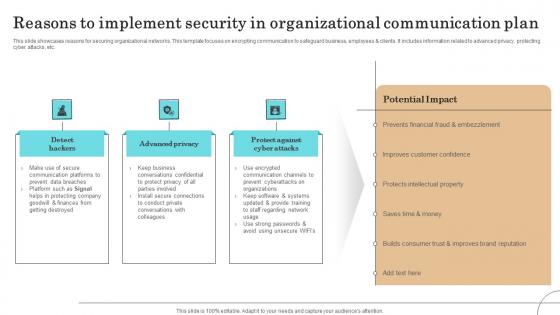
Reasons To Implement Security In Organizational Communication Plan Sample Pdf
This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.Showcasing this set of slides titled Reasons To Implement Security In Organizational Communication Plan Sample Pdf The topics addressed in these templates are Communication Platforms, Protecting Company, Improves Customer Confidence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.
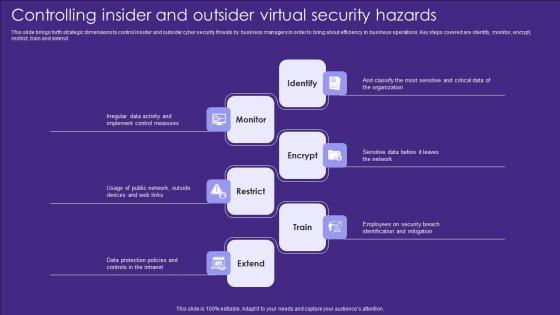
Controlling Insider And Outsider Virtual Security Hazards Designs Pdf
This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend Showcasing this set of slides titled Controlling Insider And Outsider Virtual Security Hazards Designs Pdf. The topics addressed in these templates are Identify, Monitor, Encrypt. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend
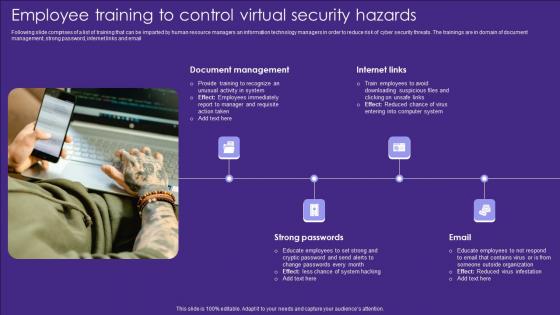
Employee Training To Control Virtual Security Hazards Designs Pdf
Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Pitch your topic with ease and precision using this Employee Training To Control Virtual Security Hazards Designs Pdf. This layout presents information on Internet Links, Email, Strong Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email

Best Practices For Tokenization In Data Security PPT Slides
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. Boost your pitch with our creative Best Practices For Tokenization In Data Security PPT Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.

Reasons Behind Need For Secure Web Gateway Web Threat Protection System
This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc. Slidegeeks has constructed Reasons Behind Need For Secure Web Gateway Web Threat Protection System after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc.
Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.Create an editable Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.

Risks Associated With Neglecting Security In Devops Role Of Devsecops Ppt Slide
This slide showcases the various challenges associated with DevOps for neglecting security. The purpose of this slide is to explain the risks related to security these include elevated exposure to cyber threats, compliance and legal concerns, and so on. Want to ace your presentation in front of a live audience Our Risks Associated With Neglecting Security In Devops Role Of Devsecops Ppt Slide can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the various challenges associated with DevOps for neglecting security. The purpose of this slide is to explain the risks related to security these include elevated exposure to cyber threats, compliance and legal concerns, and so on.
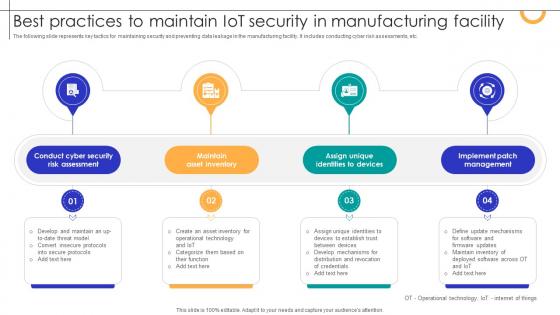
Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template today and make your presentation stand out from the rest The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf
This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc. Showcasing this set of slides titled Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf. The topics addressed in these templates are Analysis Progress, Resolution Progress, Threshold Limit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc.
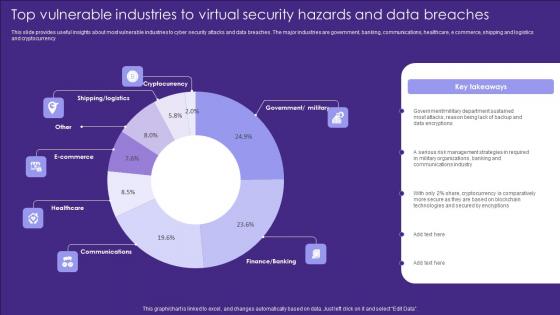
Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf
This slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Pitch your topic with ease and precision using this Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf. This layout presents information on Cryptocurrency, Ecommerce, Healthcare. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency


 Continue with Email
Continue with Email

 Home
Home


































