Cyber Safety
Cyber Security Disaster Recuperation Quarterly Roadmap To Eradicate Intrusion Icons
Introducing our cyber security disaster recuperation quarterly roadmap to eradicate intrusion icons. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
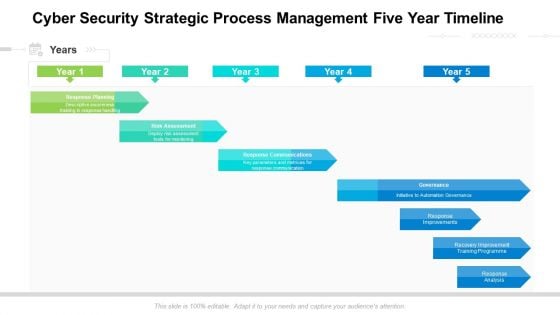
Cyber Security Strategic Process Management Five Year Timeline Inspiration
Presenting our jaw dropping cyber security strategic process management five year timeline inspiration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
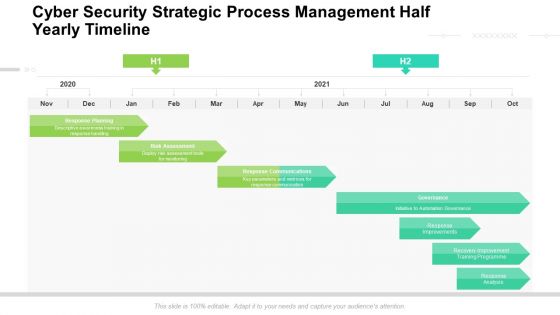
Cyber Security Strategic Process Management Half Yearly Timeline Rules
Presenting our innovatively structured cyber security strategic process management half yearly timeline rules Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Strategic Process Management Six Months Timeline Structure
Introducing our cyber security strategic process management six months timeline structure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
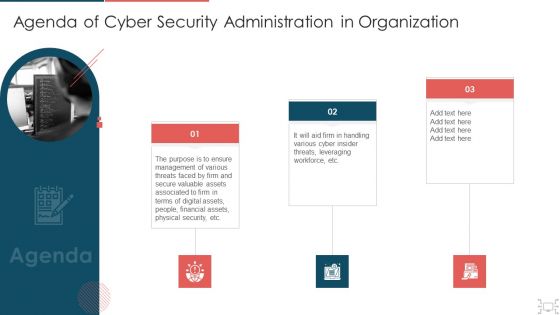
Agenda Of Cyber Security Administration In Organization Information PDF
This is a agenda of cyber security administration in organization information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda, purpose, management, valuable, assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
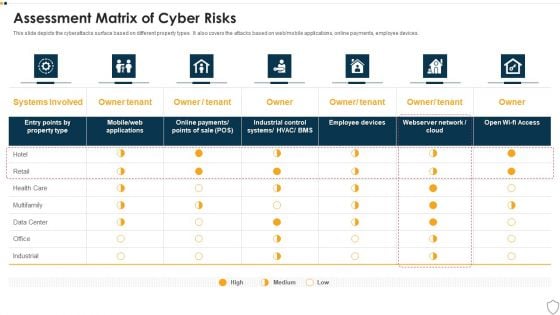
IT Security Assessment Matrix Of Cyber Risks Infographics PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative it security assessment matrix of cyber risks infographics pdf bundle. Topics like data center, industrial, retail, health care can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
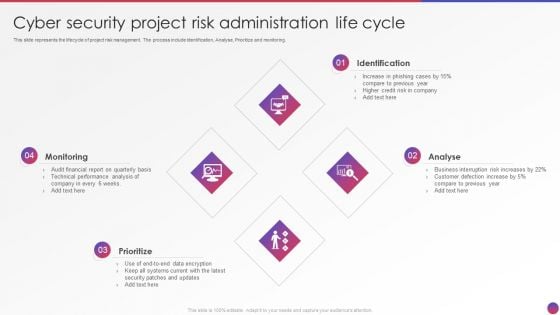
Cyber Security Project Risk Administration Life Cycle Summary PDF
This slide represents the lifecycle of project risk management. The process include Identification, Analyse, Prioritize and monitoring. Presenting Cyber Security Project Risk Administration Life Cycle Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Monitoring, Identification, Analyse, Prioritize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents Cyber Security Automation Framework Ideas PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Cyber Security Automation Framework Ideas PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
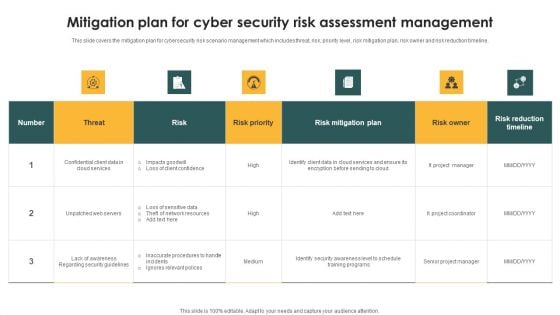
Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF
This slide covers the mitigation plan for cybersecurity risk scenario management which includes threat, risk, priority level, risk mitigation plan, risk owner and risk reduction timeline. Showcasing this set of slides titled Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF. The topics addressed in these templates are Threat, Risk, Risk Priority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
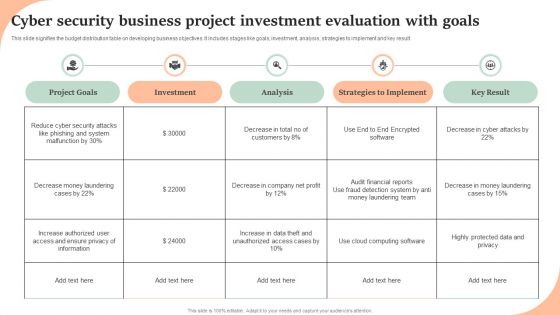
Cyber Security Business Project Investment Evaluation With Goals Structure PDF
This slide signifies the budget distribution table on developing business objectives. It includes stages like goals, investment, analysis, strategies to implement and key result. Showcasing this set of slides titled Cyber Security Business Project Investment Evaluation With Goals Structure PDF. The topics addressed in these templates are Project Goals, Investment, Analysis, Strategies To Implement, Key Result. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
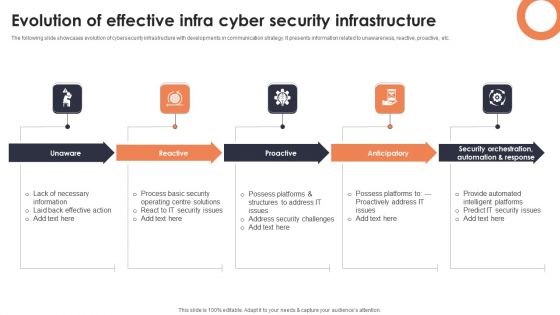
Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF
The following slide showcases evolution of cybersecurity infrastructure with developments in communication strategy. It presents information related to unawareness, reactive, proactive, etc. Presenting Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Unaware, Reactive, Proactive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
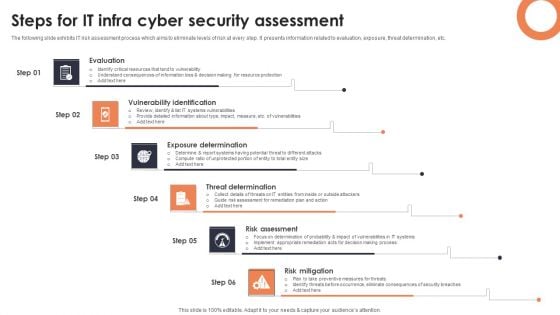
Steps For IT Infra Cyber Security Assessment Background PDF
The following slide exhibits IT risk assessment process which aims to eliminate levels of risk at every step. It presents information related to evaluation, exposure, threat determination, etc. Presenting Steps For IT Infra Cyber Security Assessment Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Evaluation, Vulnerability Identification, Exposure Determination. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
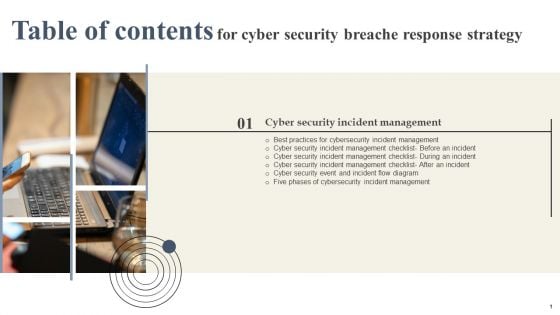
Cyber Security Breache Response Strategy Table Of Contents Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Breache Response Strategy Table Of Contents Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Cyber Exploitation IT Interview Schedule For New Professionals Icons PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking. Deliver and pitch your topic in the best possible manner with this cyber exploitation it interview schedule for new professionals icons pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
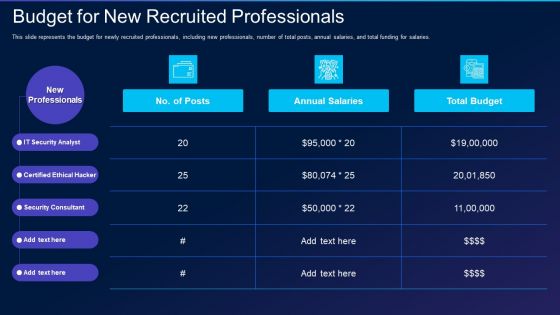
Cyber Exploitation IT Budget For New Recruited Professionals Demonstration PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries. Deliver and pitch your topic in the best possible manner with this cyber exploitation it budget for new recruited professionals demonstration pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
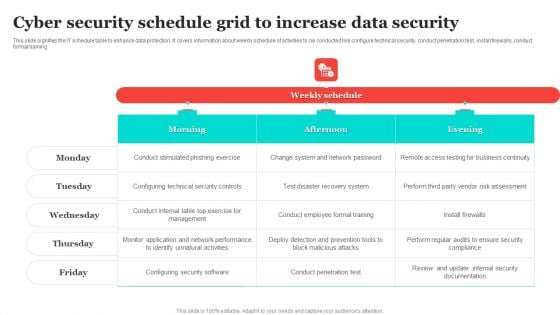
Cyber Security Schedule Grid To Increase Data Security Structure PDF
This slide signifies the IT schedule table to enhance data protection. It covers information about weekly schedule of activities to be conducted like configure technical security, conduct penetration test, install firewalls, conduct formal training. Pitch your topic with ease and precision using this Cyber Security Schedule Grid To Increase Data Security Structure PDF. This layout presents information on Recovery System, Vendor Risk Assessment, Configuring Security Software. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
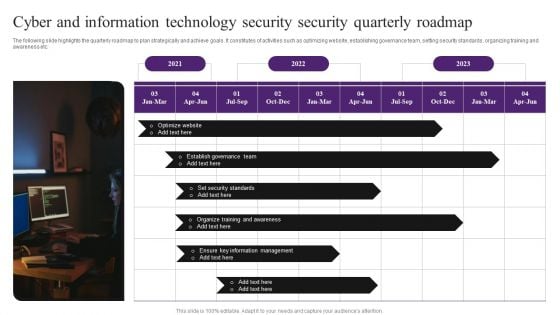
Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF
The following slide highlights the quarterly roadmap to plan strategically and achieve goals. It constitutes of activities such as optimizing website, establishing governance team, setting security standards, organizing training and awareness etc. Presenting Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Optimize Website, Information Management, Organize Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Exploitation IT Purpose Of Ethical Hacking Portrait PDF
This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities. Deliver an awe inspiring pitch with this creative cyber exploitation it purpose of ethical hacking portrait pdf bundle. Topics like vulnerabilities, management, process, weaknesses, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
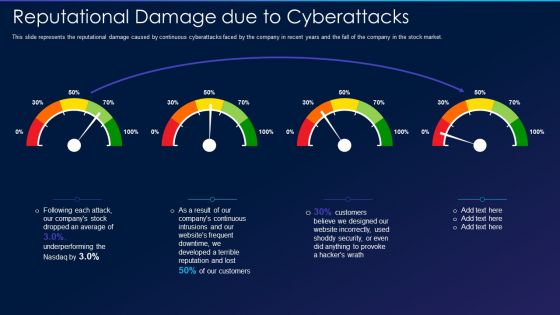
Cyber Exploitation IT Reputational Damage Due To Cyberattacks Professional PDF
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market. Deliver an awe inspiring pitch with this creative cyber exploitation it reputational damage due to cyberattacks professional pdf bundle. Topics like continuous, developed, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Use Of Security Programs Mockup PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks. Presenting cyber exploitation it use of security programs mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secure sockets layer, web application firewall, website and software scanners. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effective Security Operations Tools To Prevent Cyber Threats Formats PDF
This slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Pitch your topic with ease and precision using this Effective Security Operations Tools To Prevent Cyber Threats Formats PDF. This layout presents information on Develops, Organization Security, Compliance Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
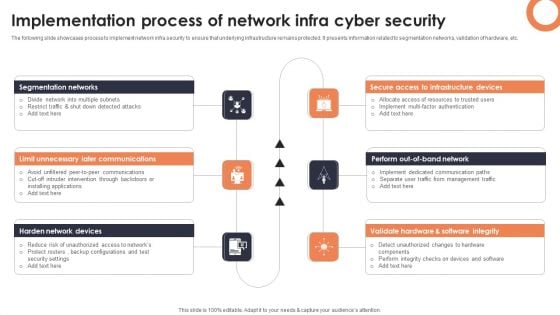
Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
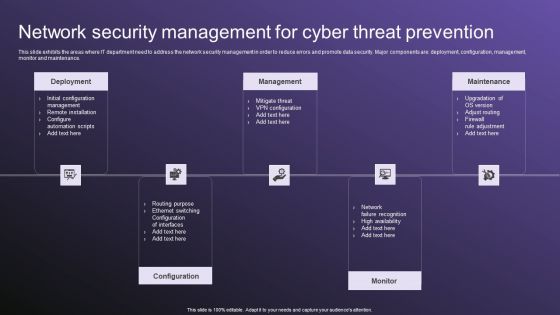
Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
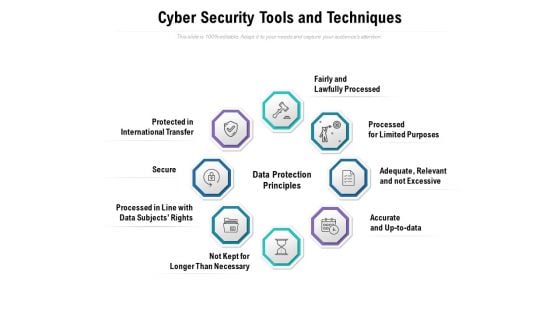
Cyber Security Tools And Techniques Ppt PowerPoint Presentation Styles Vector
Presenting this set of slides with name cyber security tools and techniques ppt powerpoint presentation styles vector. This is a eight stage process. The stages in this process are fairly and lawfully processed, processed for limited purposes, adequate, relevant and not excessive, accurate and up to data, not kept for longer than necessary, processed in line with data subjects rights, secure, protected in international transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
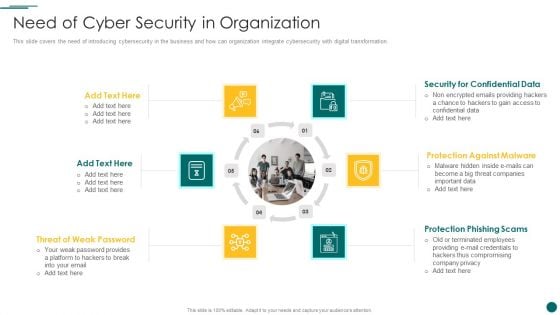
Organization Reinvention Need Of Cyber Security In Organization Graphics PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Reinvention Need Of Cyber Security In Organization Graphics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Security Confidential Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
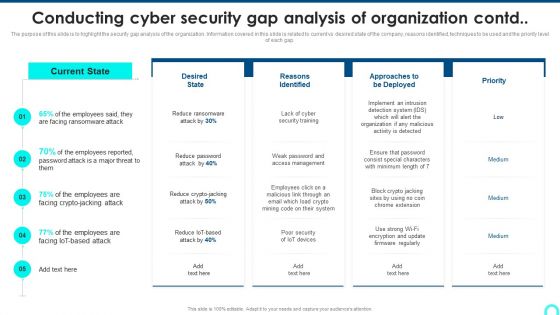
Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF
The purpose of this slide is to highlight the security gap analysis of the organization. Information covered in this slide is related to current vs desired state of the company, reasons identified, techniques to be used and the priority level.Deliver an awe inspiring pitch with this creative Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF bundle. Topics like Facing Ransomware, Reasons Identified, Organization Malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
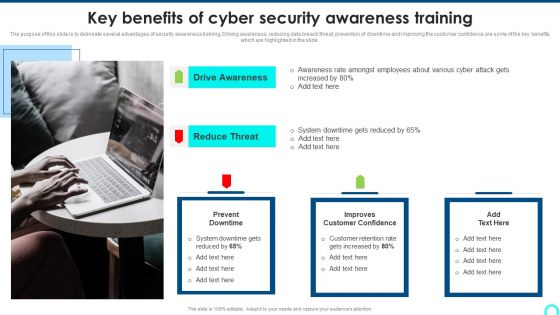
Key Benefits Of Cyber Security Awareness Training Background PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide.This is a Key Benefits Of Cyber Security Awareness Training Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drive Awareness, Reduce Threat, Amongst Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
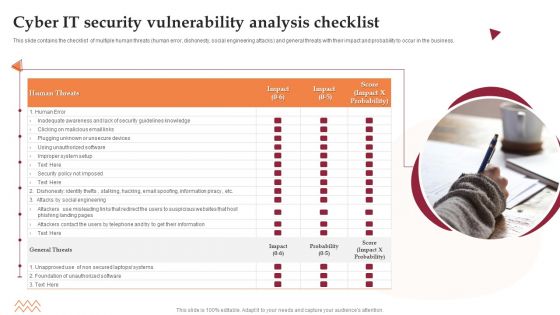
Cyber IT Security Vulnerability Analysis Checklist Microsoft PDF
This slide contains the checklist of multiple human threats human error, dishonesty, social engineering attacks and general threats with their impact and probability to occur in the business. Persuade your audience using this Cyber IT Security Vulnerability Analysis Checklist Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Security, Awareness, Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF
This slide defines the flowchart for web attack incident response. It includes information related to the steps taken to resolve the web attack incident taken place using the cybersecurity. Persuade your audience using this Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Prioritizing Security Response, Investigating, Preparing Report Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills

Conducting Cyber Security Gap Analysis Of Organization Formats PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Boost your pitch with our creative Conducting Cyber Security Gap Analysis Of Organization Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
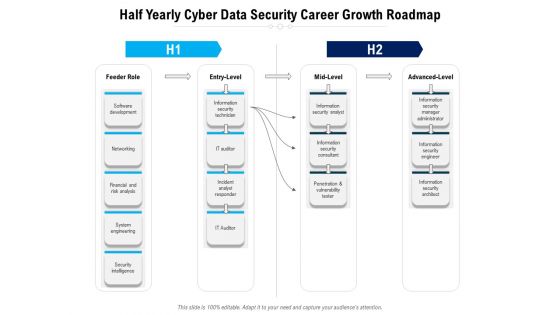
Half Yearly Cyber Data Security Career Growth Roadmap Topics
Presenting the half yearly cyber data security career growth roadmap topics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
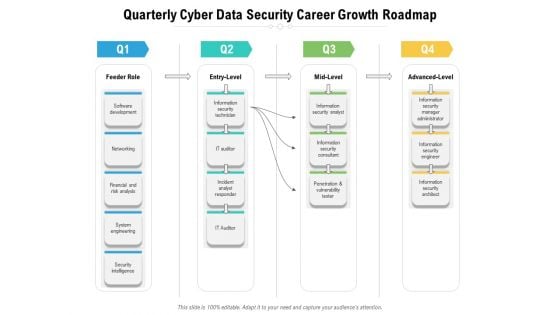
Quarterly Cyber Data Security Career Growth Roadmap Infographics
Presenting the quarterly cyber data security career growth roadmap infographics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
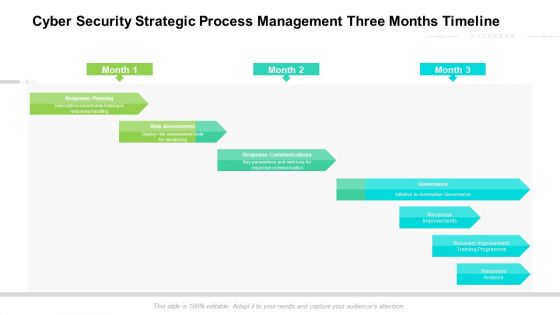
Cyber Security Strategic Process Management Three Months Timeline Introduction
Presenting the cyber security strategic process management three months timeline introduction. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Case Study 2 Banks Cyber Security Infrastructure Topics PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges Presenting case study 2 banks cyber security infrastructure topics pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like implemented, integrated, our approach. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Assessment Matrix Of Cyber Risks Infographics PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Presenting desktop security management assessment matrix of cyber risks infographics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like retail, systems, systems, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Statistics Of Cyber Security Awareness Ppt Professional Deck PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Statistics Of Cyber Security Awareness Ppt Professional Deck PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

CYBER Security Breache Response Strategy Ppt PowerPoint Presentation Complete Deck
Whether it is for your individual use or business purpose, providing information in a clear format is often an added advantage, as this CYBER Security Breache Response Strategy Ppt PowerPoint Presentation Complete Deck does so wonderfully well. Incorporate this content-ready, versatile PowerPoint complete deck in sixty eight slides to significantly enhance your chances of success. It will help you talk about multiple components of business and be more efficient. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.
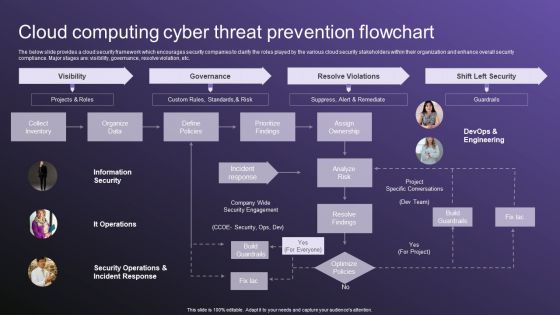
Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
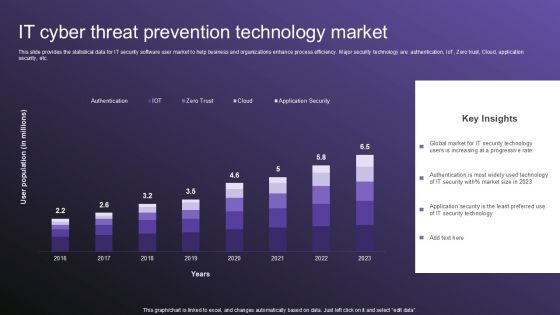
IT Cyber Threat Prevention Technology Market Topics PDF
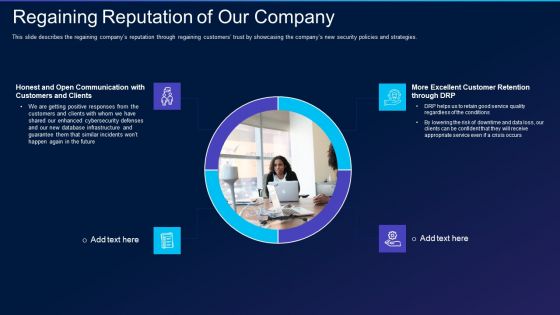
Cyber Exploitation IT Regaining Reputation Of Our Company Demonstration PDF
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies. This is a cyber exploitation it regaining reputation of our company demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like regaining reputation of our company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
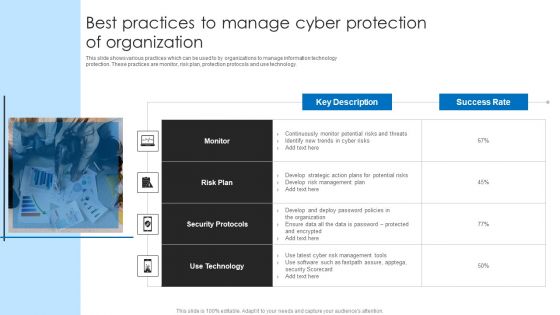
Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
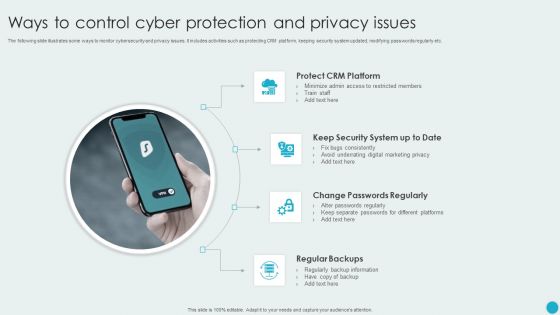
Ways To Control Cyber Protection And Privacy Issues Diagrams PDF
The following slide illustrates some ways to monitor cybersecurity and privacy issues. It includes activities such as protecting CRM platform, keeping security system updated, modifying passwords regularly etc. Persuade your audience using this Ways To Control Cyber Protection And Privacy Issues Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Change Passwords Regularly, Regular Backups, Protect CRM Platform. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Integration Architecture To Manage Cyber Risk Pictures PDF
This slide showcases the structure to manage cybersecurity threats and risk of any organization. It includes steps such as identifying user with data access, protecting data accessibility, secure networks, install and updating antivirus, developing plan for managing disasters etc. Presenting Identify, Protect, Detect to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Data Integration Architecture To Manage Cyber Risk Pictures PDF. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Awareness Trends In 2022 Diagrams PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Presenting Cyber Security Awareness Trends In 2022 Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Malware Ransomware, Advanced Challenging, Malware Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Awareness Trends In 2023 Ppt Graphics PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Awareness Trends In 2023 Ppt Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cyber Security Dashboard Ppt PowerPoint Presentation Complete With Slides
Improve your presentation delivery using this Cyber Security Dashboard Ppt PowerPoint Presentation Complete With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising tweleve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Business Cyber Security Assessment Ppt PowerPoint Presentation Complete With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Business Cyber Security Assessment Ppt PowerPoint Presentation Complete With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the tweleve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Cyber Security Attack Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Cyber Security Attack Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Cyber Security Automation Framework Ppt PowerPoint Presentation Complete With Slides
In the rainbow of business colours of any PPT Presentation, it is important to realise that structure and framework is the real pain point that the customer wants to resolve through a presentation. Our products are the answer, as illustrated through this Cyber Security Automation Framework Ppt PowerPoint Presentation Complete With Slides. Learn how the structure of a business presentation is to be fleshed out using this forty two slide complete deck. Examine the relevance of concepts like business planning, market strategies and customer pain points etc to arrive at a comprehensive understanding of the needs of all stakeholders. This can serve as the master blueprint to help you analyze any business scenario you may face. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.

Infra Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Infra Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of seventeen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
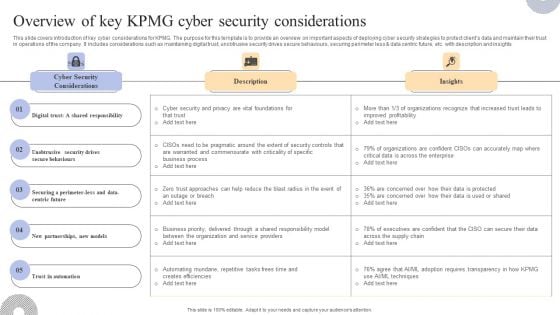
Overview Of Key KPMG Cyber Security Considerations Inspiration PDF
This slide covers an introduction to KPMG company ESG strategy to improve reporting to stakeholders. The purpose of this template is to provide overview on introducing ESG strategy, benefits along with reporting insights. It includes benefits such as helping organization assess and improve sustainable performance, establishing strong reputation and trust, attracting investors and customers, etc. Welcome to our selection of the Overview Of Key KPMG Cyber Security Considerations Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
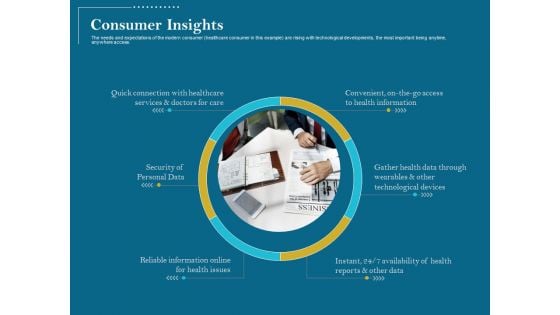
Utilizing Cyber Technology For Change Process Consumer Insights Microsoft PDF
The needs and expectations of the modern consumer healthcare consumer in this example are rising with technological developments, the most important being anytime, anywhere access. Presenting utilizing cyber technology for change process consumer insights microsoft pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security of personal data, reliable information online for health issues, gather health data through wearables and other technological devices, convenient, on the go access to health information, quick connection with healthcare services and doctors for care. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
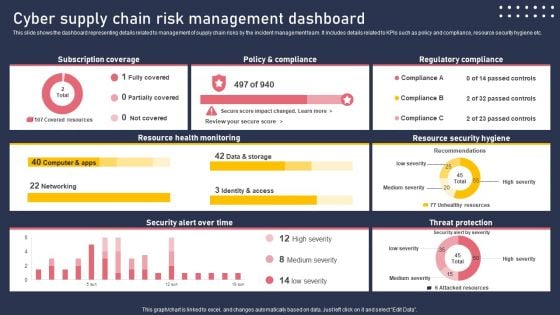
Cyber Supply Chain Risk Management Dashboard Structure PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Supply Chain Risk Management Dashboard Structure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
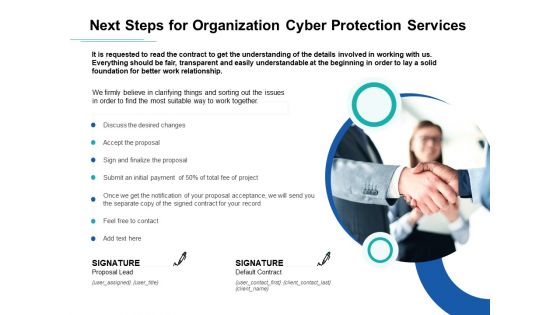
Develop Corporate Cyber Security Risk Mitigation Plan Next Steps For Organization Cyber Protection Services Topics PDF Themes PDF
Presenting develop corporate cyber security risk mitigation plan next steps for organization cyber protection services topics pdf themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like desired changes, initial payment, organization, cyber protection services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Develop Corporate Cyber Security Risk Mitigation Plan Case Study For Organization Cyber Protection Services Themes PDF Sample PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan case study for organization cyber protection services themes pdf sample pdf bundle. Topics like problem, results, our solution, low cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
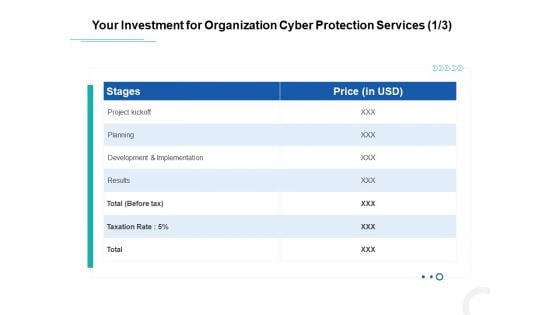
Develop Corporate Cyber Security Risk Mitigation Plan Your Investment For Organization Cyber Protection Services Planning Rules PDF
Deliver and pitch your topic in the best possible manner with this develop corporate cyber security risk mitigation plan your investment for organization cyber protection services planning rules pdf. Use them to share invaluable insights on project kickoff, planning, development and implementation, results and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Hybrid Warfare Cyber Rapid Response Team CRRT Themes PDF
This slide talks about the cyber rapid response team deployed to protect ukraine from russian cyber attacks, including experts from lithuania, croatia, poland, estonia, romania, and the netherlands. Want to ace your presentation in front of a live audience Our Series Of Cyber Security Attacks Against Ukraine 2022 Hybrid Warfare Cyber Rapid Response Team CRRT Themes PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































