Cyber Security Challenges
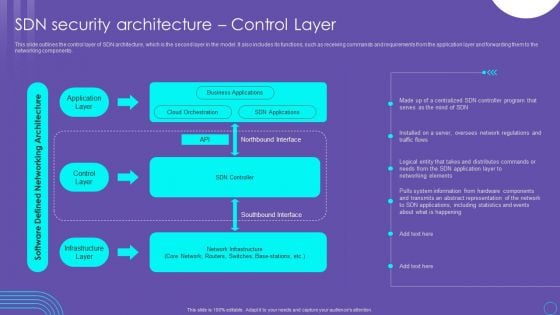
SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. If you are looking for a format to display your unique thoughts, then the professionally designed SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock On Keyboard Data Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas.Use these PowerPoint slides for presentations relating to A padlock on keyboard, computer, technology, marketing, business, success. The prominent colors used in the PowerPoint template are Yellow, Blue navy, White. Professionals tell us our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our marketing PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. You can be sure our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter look like a pro even if they are not computer savvy. PowerPoint presentation experts tell us our on PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. We assure you our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides look good visually. With our Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0113 there is no need to exaggerate. They are always brief and accurate.
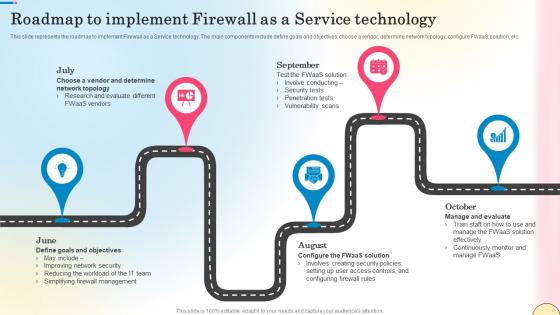
Roadmap To Implement Firewall As A Service Technology Network Security Themes Pdf
This slide represents the roadmap to implement Firewall as a Service technology. The main components include define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Roadmap To Implement Firewall As A Service Technology Network Security Themes Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the roadmap to implement Firewall as a Service technology. The main components include define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc.
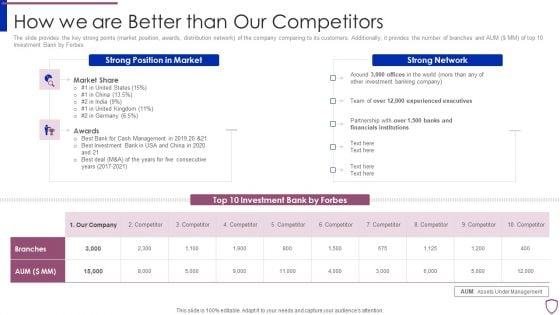
Financing Catalogue For Security Underwriting Agreement How We Are Better Than Our Competitors Template PDF
The slide provides the key strong points market position, awards, distribution network of the company comparing to its customers. Additionally, it provides the number of branches and AUM MM of top 10 Investment Bank by Forbes. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement how we are better than our competitors template pdf bundle. Topics like strong position in market, strong network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

House And Question Mark Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our House And Question Mark Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Network diagrams PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Download our Communication PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune.Use these PowerPoint slides for presentations relating to Question mark with house,business, finance, success, signs, marketing . The prominent colors used in the PowerPoint template are Blue, Gray, Blue. Specify paths to success with our House And Question Mark Security PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.

Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Login Screen And Credit Card Services Security PowerPoint Templates And PowerPoint Themes 1112
We present our Login Screen And Credit Card Services Security PowerPoint Templates And PowerPoint Themes 1112.Use our Technology PowerPoint Templates because, The structure of our templates allows you to effectively highlight the key issues concerning the growth of your business. Use our Business PowerPoint Templates because, Let your words be the drops of wisdom spreading knowledge and peace like ripples through the expectant minds of your devoted followers. Use our Computer PowerPoint Templates because, Present your views using our innovative slides and be assured of leaving a lasting impression. Use our Internet PowerPoint Templates because,The basic stages are in place, you need to build upon them with our PowerPoint templates. Use our Success PowerPoint Templates because, You have some great folks working with you, thinking with you.Use these PowerPoint slides for presentations relating to laptop screen, internet, computer, technology, business, success. The prominent colors used in the PowerPoint template are Gray, Blue, Black Your thoughts andour Login Screen And Credit Card Services Security PowerPoint Templates And PowerPoint Themes 1112 are destined to amalgamate. They will create a champion team.

Use Internet Security For Business PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Use Internet Security For Business PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download and present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team. Present our Globe PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to Computer mouse is connected to a globe - surfing and browsing is blocked by a red do not enter sign that cuts the cable, technology, communication, signs, globe, business. The prominent colors used in the PowerPoint template are Blue, White, Black. Our Use Internet Security For Business PowerPoint Templates Ppt Backgrounds For Slides 0413 will keep the faith. They will show allegiance to your thoughts.
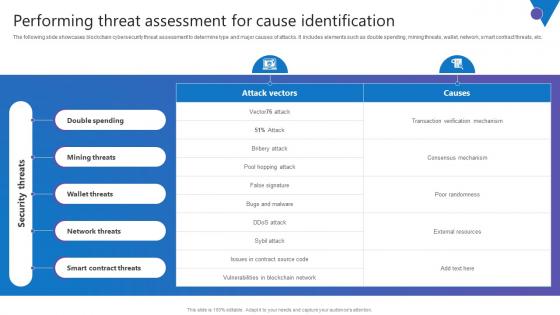
Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf
The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf. The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc.

Keys Tied To Chain Security PowerPoint Templates Ppt Background For Slides 1112
We present our Keys Tied To Chain Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because, Spell out your advertising plans to increase market share. The feedback has been positive and productive Use our Success PowerPoint Templates because,This Slide offers an excellent background to build up the various stages of your business process. Use our Chains PowerPoint Templates because,Our PowerPoint templates designed for your ideas to sell. Use our Finance PowerPoint Templates because,Let this slide illustrates others piggyback on you to see well over the horizon Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Keys tied to chain, business, success, chains, finance, marketing. The prominent colors used in the PowerPoint template are Yellow, Brown, White Pioneer changes with our Keys Tied To Chain Security PowerPoint Templates Ppt Background For Slides 1112. Download without worries with our money back guaranteee.

Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112
We present our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because,You too have got the framework of your companys growth in place. Use our Success PowerPoint Templates because, You can Transmit this concern to your staff using our helpful slides. Use our Puzzles or jigsaws PowerPoint Templates because,We all know that alphabetical order is a time honoured concept. Use our Shapes PowerPoint Templates because,you can put it up there for all to see. Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Key chain tied with puzzle piece, business, success, puzzles or jigsaws, shapes, marketing. The prominent colors used in the PowerPoint template are Yellow, Black, Red Engineer growth with our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112. Download without worries with our money back guaranteee.
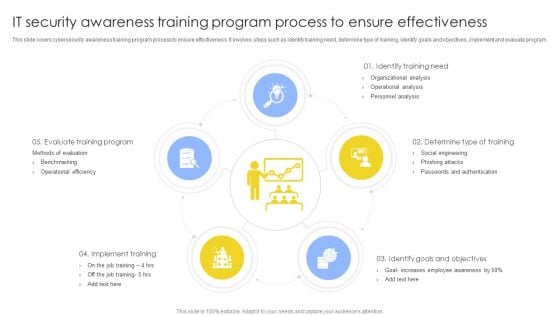
IT Security Awareness Training Program Process To Ensure Effectiveness Diagrams PDF
This slide covers cybersecurity awareness training program process to ensure effectiveness. It involves steps such as identify training need, determine type of training, identify goals and objectives, implement and evaluate program. Persuade your audience using this IT Security Awareness Training Program Process To Ensure Effectiveness Diagrams PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Implement Training, Determine Type Training, Identify Training Need. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
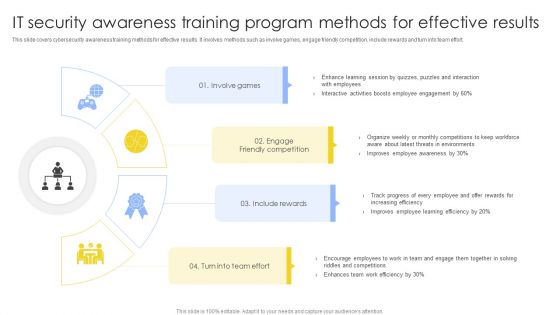
IT Security Awareness Training Program Methods For Effective Results Summary PDF
This slide covers cybersecurity awareness training methods for effective results. It involves methods such as involve games, engage friendly competition, include rewards and turn into team effort. Presenting IT Security Awareness Training Program Methods For Effective Results Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Involve Games, Engage Friendly Competition, Include Rewards. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
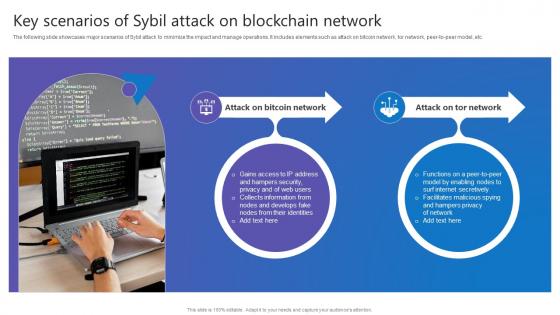
Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Scenarios Sybil Attack Comprehensive Guide To Blockchain Digital Security Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer to peer model, etc.
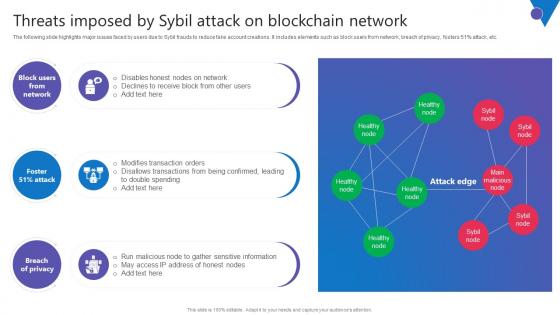
Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc.
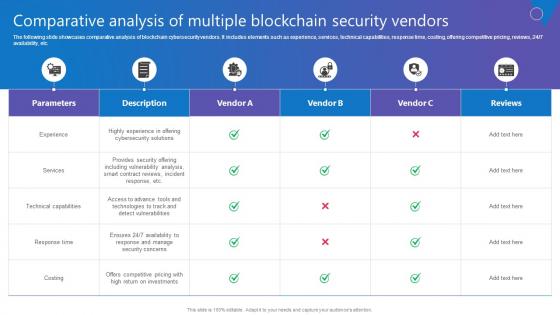
Comparative Analysis Multiple Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc. Do you know about Slidesgeeks Comparative Analysis Multiple Comprehensive Guide To Blockchain Digital Security Introduction Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc.
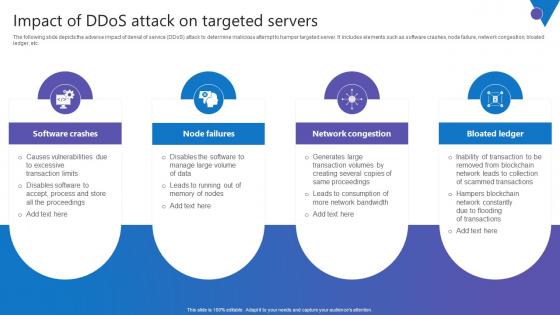
Impact Of DDoS Attack Comprehensive Guide To Blockchain Digital Security Sample Pdf
The following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc. Slidegeeks is here to make your presentations a breeze with Impact Of DDoS Attack Comprehensive Guide To Blockchain Digital Security Sample Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Measures And Ways To Mitigate Rules PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach measures and ways to mitigate rules pdf. Use them to share invaluable insights on measures and ways to mitigate security monitoring challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

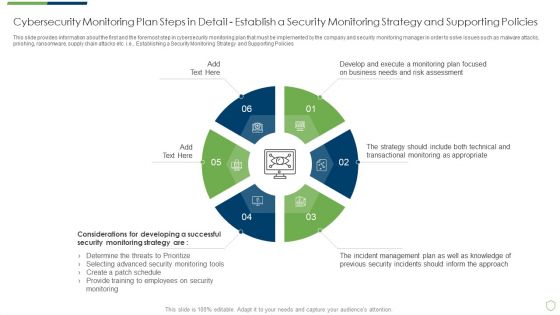
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
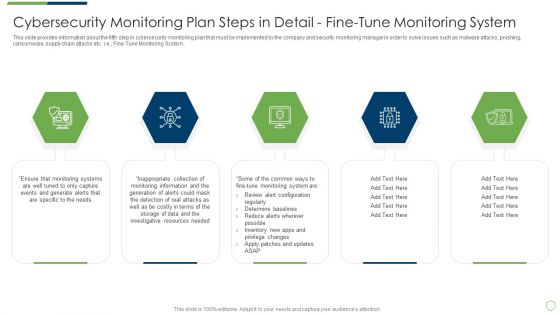
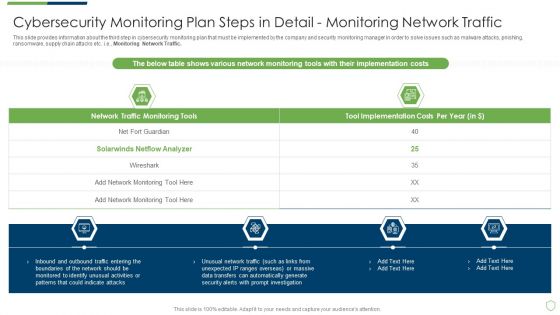
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
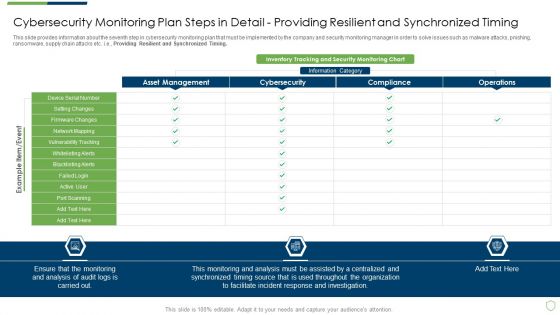
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
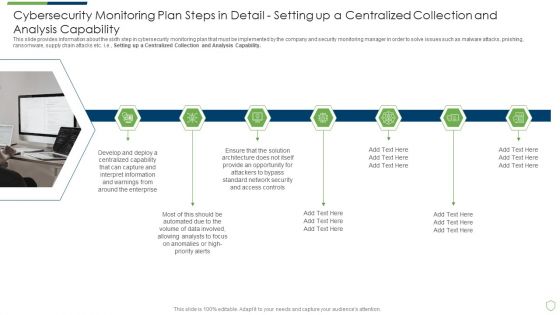
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Lock With Three Key Steps Powerpoint Templates
This PowerPoint template has been designed with lock and three key steps. This editable slide helps to display the key concepts for business success. Use this PPT slide for your business and marketing related presentations.

Data Is Secure Internet PowerPoint Template 1110
3d illustration of a lock sitting in front of a computer display showing a file folder Approve plans with our Data Is Secure Internet PowerPoint Template 1110. You will come out on top.

Secured Internet Connection PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Secured Internet Connection PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Security PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Present our Technology PowerPoint Templates because you can Break through with our PowerPoint Templates and Slides. Bring down the mental barriers of your audience. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Download and present our Shapes PowerPoint Templates because You will get more than you ever bargained for. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience.Use these PowerPoint slides for presentations relating to Browser window with a Key, security, business, technology, signs, shapes. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Advertise your expertise with our Secured Internet Connection PowerPoint Templates Ppt Backgrounds For Slides 0313. Establish your undeniable command over the subject.

Open Innovation Challenge And The Internet Of Things Ppt Sample Ppt Files
This is a open innovation challenge and the internet of things ppt sample ppt files. This is a seven stage process. The stages in this process are internet of things, security, industrial internet, smart city, public safety, health, automotive, connectivity.

Secure Internet Access Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a large chrome key protruding out from the window Fight off critics with our Secure Internet Access Computer PowerPoint Themes And PowerPoint Slides 0811. Be confident and convinced of your assessment.

Secure Digital Mail Internet PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface With our Secure Digital Mail Internet PowerPoint Presentation Slides S you will get far ahead. Let your competitors play catch up.
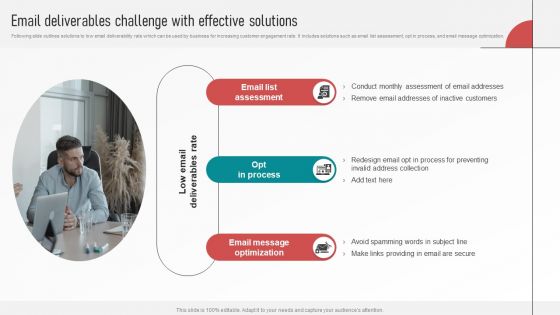
Customer Retention With Email Advertising Campaign Plan Email Deliverables Challenge With Effective Solutions Formats PDF
Following slide outlines solutions to low email deliverability rate which can be used by business for increasing customer engagement rate. It includes solutions such as email list assessment, opt in process, and email message optimization. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Customer Retention With Email Advertising Campaign Plan Email Deliverables Challenge With Effective Solutions Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Customer Retention With Email Advertising Campaign Plan Email Deliverables Challenge With Effective Solutions Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
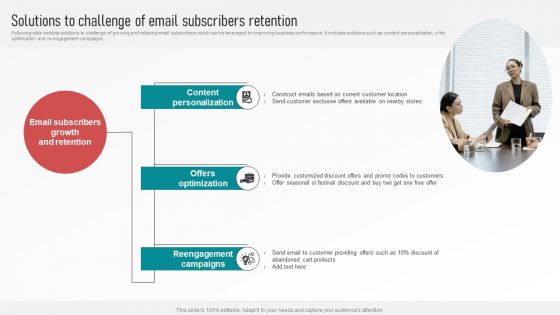
Customer Retention With Email Advertising Campaign Plan Solutions To Challenge Of Email Subscribers Retention Microsoft PDF
Following slide exhibits solutions to challenge of growing and retaining email subscribers which can be leveraged for improving business performance. It includes solutions such as content personalization, offer optimization and re-engagement campaigns. The Customer Retention With Email Advertising Campaign Plan Solutions To Challenge Of Email Subscribers Retention Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Customer Retention With Email Advertising Campaign Plan Challenge Of New Subscribers Engagement Topics PDF
Following slide exhibits solutions for engaging new email subscribers which can be used by businesses to increase their email list. It includes key points such as welcome email, easy sign up option and leverage old customers. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Customer Retention With Email Advertising Campaign Plan Challenge Of New Subscribers Engagement Topics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Zero Trust Model Comparison Between ZTNA And Secure Access Service
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Model Comparison Between ZTNA And Secure Access Service and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Comparison Between ZTNA And Secure Access Service Edge Professional PDF
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparison Between ZTNA And Secure Access Service Edge Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Mitigating Cybersecurity Threats And Vulnerabilities Selecting Secured Threat Formats PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities selecting secured threat formats pdf bundle. Topics like information security prevention, api integration, security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Checklist To Implement Secure Web Gateway Web Threat Protection System
This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Get a simple yet stunning designed Checklist To Implement Secure Web Gateway Web Threat Protection System. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Checklist To Implement Secure Web Gateway Web Threat Protection System can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.

Web Access Control Solution Checklist To Implement Secure Web Gateway
This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Web Access Control Solution Checklist To Implement Secure Web Gateway and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.
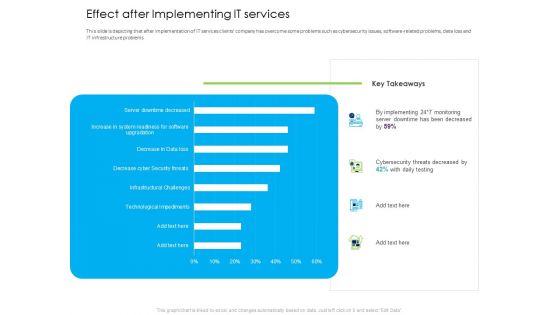
Managed IT Services Pricing Model Effect After Implementing IT Services Professional PDF
This slide is depicting that after implementation of IT services clients company has overcome some problems such as cybersecurity issues, software-related problems, data loss and IT infrastructure problems. Deliver and pitch your topic in the best possible manner with this managed it services pricing model effect after implementing it services professional pdf. Use them to share invaluable insights on infrastructural challenges, technological impediments, decrease cyber security threats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Business Diagram Three Circles With Lock For Safety Presentation Template
Three air balloons with text boxes are used to craft this power point template slide. This PPT slide contains the concept of business text representation. This slide is usable for business and marketing related presentations.

NIST Cybersecurity Framework Best Practices Topics PDF
The slide highlights the best practices to be followed in order to overcome various implementation challenges of Nist framework for cyber security. It covers understand, automate, prioritize and talent acquisition. Persuade your audience using this NIST Cybersecurity Framework Best Practices Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Automate, Talent Acquisition. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
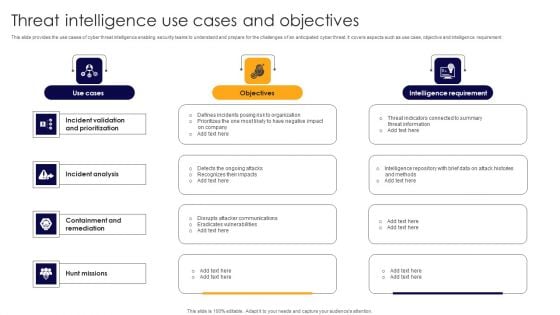
Threat Intelligence Use Cases And Objectives Demonstration PDF
This slide provides the use cases of cyber threat intelligence enabling security teams to understand and prepare for the challenges of an anticipated cyber threat. It covers aspects such as use case, objective and intelligence requirement. Presenting Threat Intelligence Use Cases And Objectives Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Analysis, Containment Remediation, Hunt Missions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
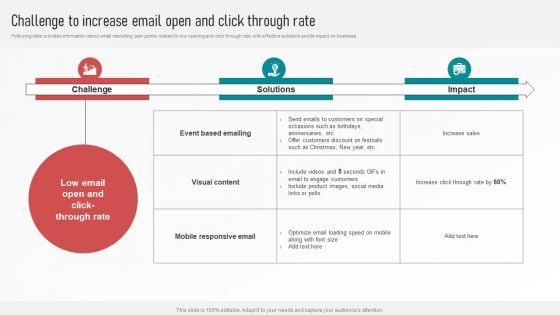
Customer Retention With Email Advertising Campaign Plan Challenge To Increase Email Open And Click Through Rate Template PDF
Following slide provides information about email marketing pain points related to low opening and click through rate with effective solutions and its impact on business. If you are looking for a format to display your unique thoughts, then the professionally designed Customer Retention With Email Advertising Campaign Plan Challenge To Increase Email Open And Click Through Rate Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Customer Retention With Email Advertising Campaign Plan Challenge To Increase Email Open And Click Through Rate Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.
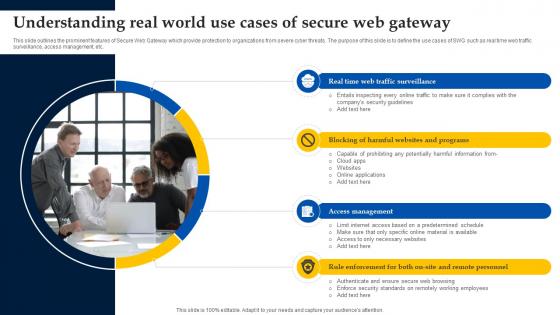
Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.

Secure Internet Browser Networking PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Secure Internet Browser Networking PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Internet PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Present our Technology PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Communication PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Use our Business PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate.Use these PowerPoint slides for presentations relating to Secure internet browser, internet, technology, security, communication, business. The prominent colors used in the PowerPoint template are Yellow, Orange, Gray. Report problems with our Secure Internet Browser Networking PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.

Secure Data In A Hard Disk PowerPoint Templates Ppt Backgrounds For Slides 0713
Our Secure Data In A Hard Disk PowerPoint Templates PPT Backgrounds For Slides allow you to do it with ease. Just like picking the low hanging fruit. Boil the ocean with your thoughts. Our Internet PowerPoint Templates will help create waves. Make some dough with our Security PowerPoint Templates. Your assets will rise significantly. Have a field day with our Secure Data In A Hard Disk PowerPoint Templates Ppt Backgrounds For Slides 0713. You will enjoy the outcome of your effort.

Secure Your Pc From Viruses PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Secure Your PC From Viruses PowerPoint Templates PPT Backgrounds For Slides 0413.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Download our Technology PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Use our Services PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Download our Marketing PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity.Use these PowerPoint slides for presentations relating to Computer security concept from viruses, security, technology, services, business, marketing. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. Formalize plans with our Secure Your Pc From Viruses PowerPoint Templates Ppt Backgrounds For Slides 0413. Download without worries with our money back guaranteee.

Secured Laptop Global Business PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Secured Laptop Global Business PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Security PowerPoint Templates because You can Create a matrix with our PowerPoint Templates and Slides. Feel the strength of your ideas click into place. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience. Present our Business PowerPoint Templates because It will get your audience in sync. Use our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Computer PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas.Use these PowerPoint slides for presentations relating to Key on laptop, security, success, business, technology, computer. The prominent colors used in the PowerPoint template are Black, Yellow, Blue. Get in contention with our Secured Laptop Global Business PowerPoint Templates Ppt Backgrounds For Slides 0213. The audience will add your name to the list.

Secure Internet Browser Internet PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Use our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Present our Security PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Download our Business PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time.Use these PowerPoint slides for presentations relating to Secure Internet Browser, technology, arrows, security, business, success. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Professionals tell us our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. You can be sure our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113 are topically designed to provide an attractive backdrop to any subject. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. We assure you our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113 are the best it can get when it comes to presenting. PowerPoint presentation experts tell us our Browser PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. Make your audience feel exclusive with our Secure Internet Browser Internet PowerPoint Templates Ppt Backgrounds For Slides 0113. Give them special attention with your thoughts.
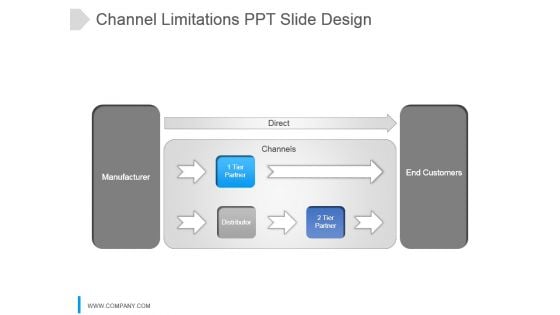
Channel Limitations Ppt Slide Design
This is a channel limitations ppt slide design. This is a three stage process. The stages in this process are direct, manufacturer, 1 tier partner, distributor, channels, 2 tier partner, end customers.

Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Get a simple yet stunning designed Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
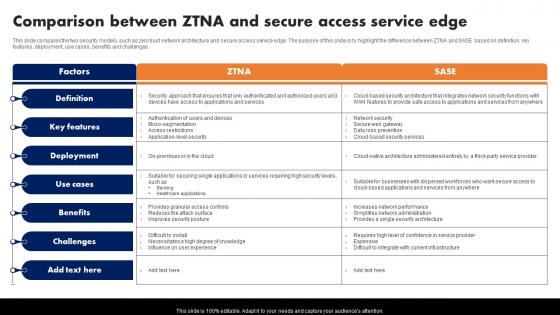
Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Global Market Analysis Of Secure Web Gateway Web Threat Protection System
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. If you are looking for a format to display your unique thoughts, then the professionally designed Global Market Analysis Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Market Analysis Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.

Online Venue Advertising Plan Hyundai Venue Campaign For Securing Millennial Influencers Strategy SS V
This slide represents the case study of Hyundai Venue Take On The City Campaign in order to provide understanding of real life use of venue marketing. It includes details related to challenges, strategy implemented and results of Hyundai venue Take on the city campaign. Present like a pro with Online Venue Advertising Plan Hyundai Venue Campaign For Securing Millennial Influencers Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the case study of Hyundai Venue Take On The City Campaign in order to provide understanding of real life use of venue marketing. It includes details related to challenges, strategy implemented and results of Hyundai venue Take on the city campaign.
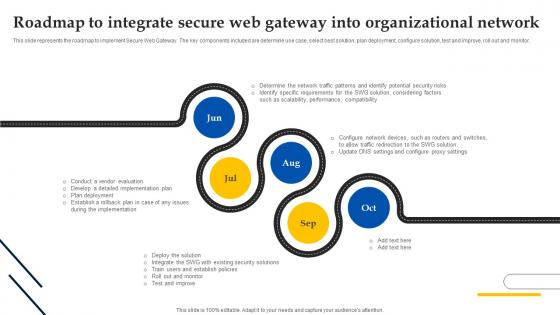
Web Access Control Solution Roadmap To Integrate Secure Web Gateway Into Organizational Network
This slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Create an editable Web Access Control Solution Roadmap To Integrate Secure Web Gateway Into Organizational Network that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Web Access Control Solution Roadmap To Integrate Secure Web Gateway Into Organizational Network is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.
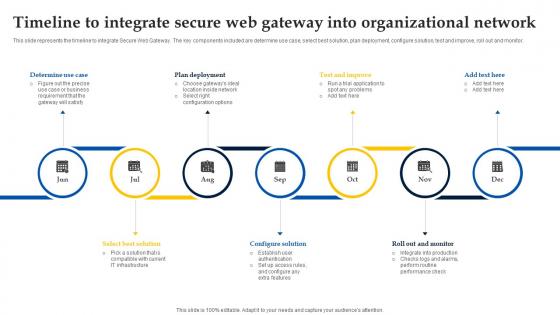
Web Access Control Solution Timeline To Integrate Secure Web Gateway Into Organizational Network
This slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Web Access Control Solution Timeline To Integrate Secure Web Gateway Into Organizational Network and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.

Timeline To Integrate Secure Web Gateway Into Web Threat Protection System
This slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Timeline To Integrate Secure Web Gateway Into Web Threat Protection System and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.


 Continue with Email
Continue with Email

 Home
Home


































