Cyber Security Communication Visualization
Digital Investigation Icon For Cyber Attack Prevention Ppt PowerPoint Presentation Gallery Summary PDF
Persuade your audience using this digital investigation icon for cyber attack prevention ppt powerpoint presentation gallery summary pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including digital investigation icon for cyber attack prevention. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
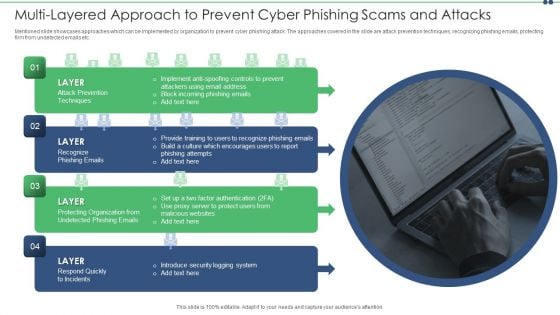
Multi Layered Approach To Prevent Cyber Phishing Scams And Attacks Themes PDF
Mentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting multi layered approach to prevent cyber phishing scams and attacks themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including email, implement, system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
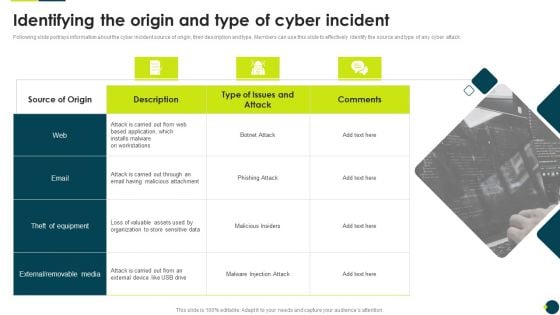
IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
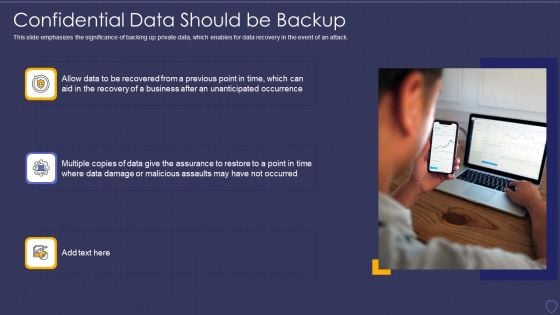
Global Cyber Terrorism Incidents On The Rise IT Confidential Data Should Be Backup Structure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack. Presenting global cyber terrorism incidents on the rise it confidential data should be backup structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like confidential data should be backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Backup Methods For Cyber Defense Planning Improving Cybersecurity With Incident Information PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental.There are so many reasons you need a Backup Methods For Cyber Defense Planning Improving Cybersecurity With Incident Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
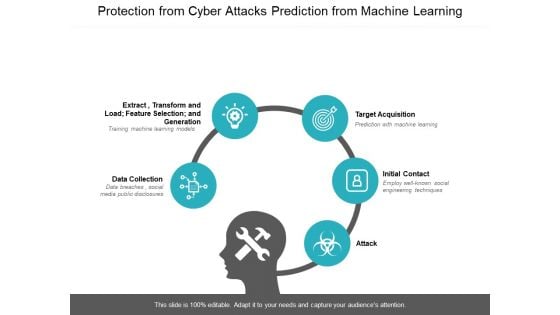
Protection From Cyber Attacks Prediction From Machine Learning Ppt PowerPoint Presentation File Show
Presenting this set of slides with name protection from cyber attacks prediction from machine learning ppt powerpoint presentation file show. This is a five stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
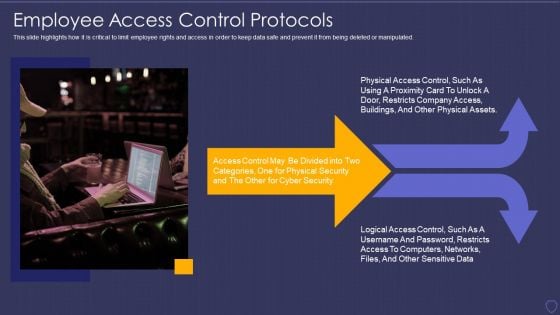
Global Cyber Terrorism Incidents On The Rise IT Employee Access Control Protocols Download PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Presenting global cyber terrorism incidents on the rise it employee access control protocols download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like employee access control protocols. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
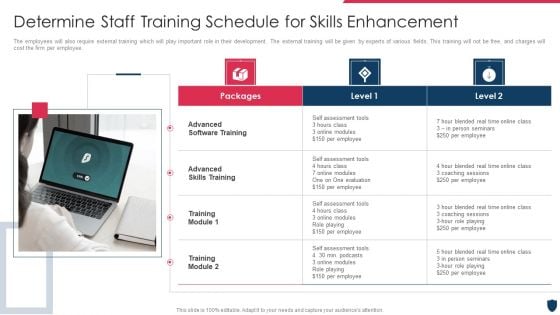
Cyber Safety Incident Management Determine Staff Training Schedule For Skills Enhancement Ideas PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting cyber safety incident management determine staff training schedule for skills enhancement ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advanced software training, advanced skills training, training module . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Preventing Measures For Social Media Accounts Themes PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies. Presenting cyber exploitation it preventing measures for social media accounts themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like social media policies, anti malware software, social media login credentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
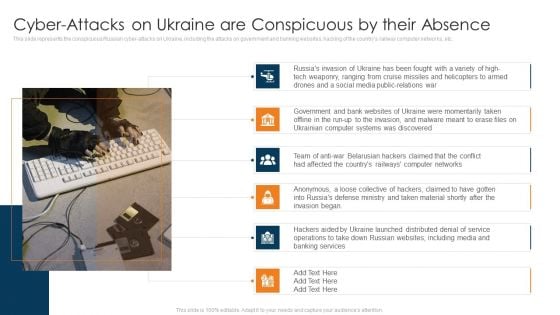
Data Wiper Spyware Attack Cyber Attacks On Ukraine Are Conspicuous Elements PDF
This slide represents the conspicuous Russian cyber-attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc.This is a data wiper spyware attack cyber attacks on ukraine are conspicuous elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine launched distributed, russian websites, belarusian hackers You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Banks On Alert For Russian Reprisal Cyber Attacks On Swift Sample PDF
This slide represents that banks are on alert for Russian reprisal cyber attacks on Society for Worldwide Interbank Financial Telecommunication Swift. This is a data wiper spyware attack banks on alert for russian reprisal cyber attacks on swift sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like payments messaging system, military industrial complex, institutions suspended You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Log Management Services Structure PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Presenting enhancing cyber safety with vulnerability administration log management services structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like collection and normalization, search speed, real time analysis, decision making process, log data filtering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
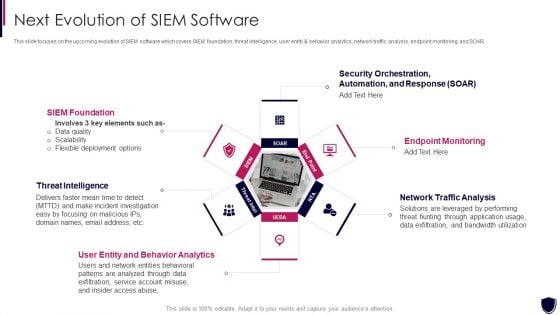
Enhancing Cyber Safety With Vulnerability Administration Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting enhancing cyber safety with vulnerability administration next evolution of siem software sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like endpoint monitoring, network traffic analysis, user entity and behavior analytics, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
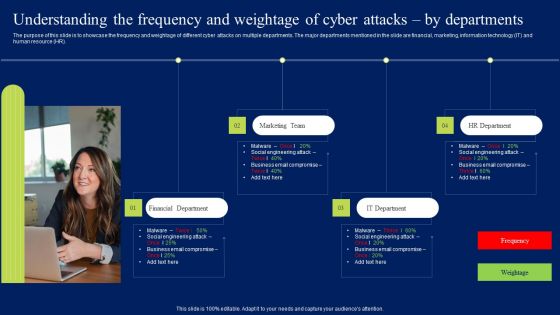
Understanding The Frequency And Weightage Of Cyber Attacks By Departments Professional PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Understanding The Frequency And Weightage Of Cyber Attacks By Departments Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Understanding The Frequency And Weightage Of Cyber Attacks By Departments Professional PDF today and make your presentation stand out from the rest.

IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.This is a IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ransomware Attacks, Cyberthreat Complaints, Trillion Annually. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
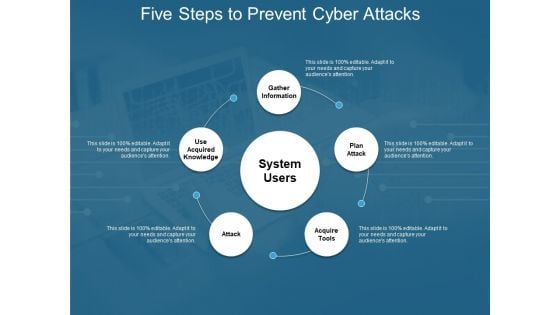
Five Steps To Prevent Cyber Attacks Ppt PowerPoint Presentation Infographic Template Inspiration
Presenting this set of slides with name five steps to prevent cyber attacks ppt powerpoint presentation infographic template inspiration. This is a five stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
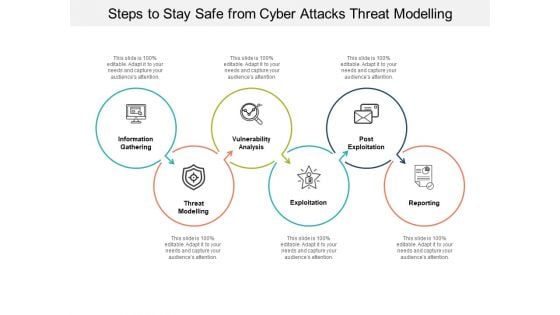
Steps To Stay Safe From Cyber Attacks Threat Modelling Ppt PowerPoint Presentation Infographics Gallery
Presenting this set of slides with name steps to stay safe from cyber attacks threat modelling ppt powerpoint presentation infographics gallery. This is a six stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
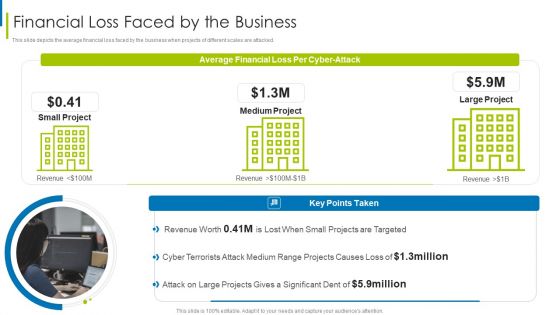
Cyber Terrorism Assault Financial Loss Faced By The Business Summary PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked.This is a cyber terrorism assault financial loss faced by the business summary pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like projects are targeted, cyber terrorists, attack on large You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
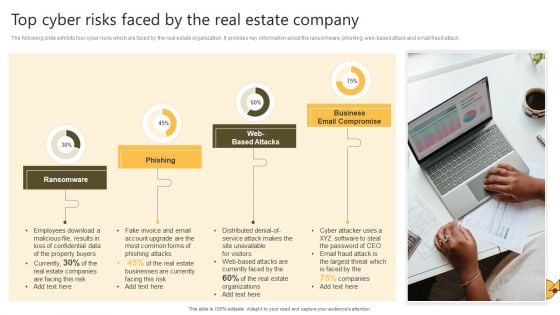
Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. The Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Ukraine Cyberwarfare Cyber Attacks On Ukraine Are Conspicuous By Their Absence Topics Pdf
This slide represents the conspicuous Russian cyber attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. This is a ukraine cyberwarfare cyber attacks on ukraine are conspicuous by their absence topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like government and bank websites of ukraine were momentarily taken offline, team of anti war belarusian hackers claimed that the conflict had affected the countrys railways computer networks, hackers aided by ukraine launched distributed denial of service operations to take down russian websites. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
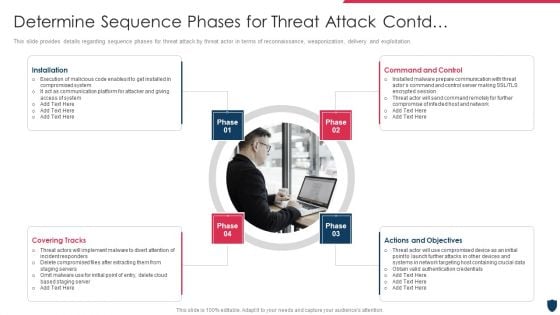
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Impact Of Defacement Attacks Portrait PDF
This slide shows the impact of defacement attacks and fake news on the public, and Meta has banned Russian media on its platforms, and Russia has restricted access to Facebook. This is a russian cyber attacks on ukraine it impact of defacement attacks portrait pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, fundamental, method, material, social media. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
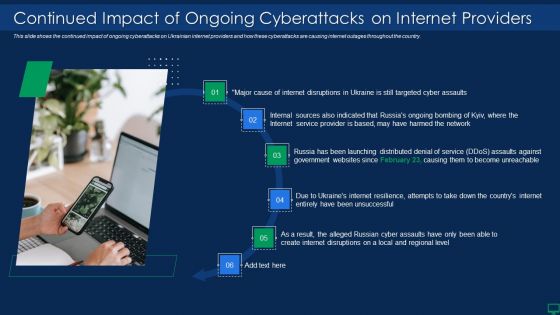
Russian Cyber Attacks On Ukraine IT Continued Impact Of Ongoing Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. This is a russian cyber attacks on ukraine it continued impact of ongoing microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sources, service, network, internet. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Cyber Terrorism Incidents On The Rise IT Financial Loss Faced By The Business Designs PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked. This is a global cyber terrorism incidents on the rise it financial loss faced by the business designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, revenue, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Different Kinds Of Insider Digital Threats Download PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber safety incident management different kinds of insider digital threats download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malicious insider, negligent or careless insider, third party insider. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Estimating Total Cost Of Ownership Designs PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support. This is a enhancing cyber safety with vulnerability administration estimating total cost of ownership designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hardware, infrastructure, software, support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Table Of Contents For IT Security IT Cont Tracking Ppt Infographics Graphics Example PDF
Presenting table of contents for it security it cont tracking ppt infographics graphics example pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cyber security, implementation, communication, administrative, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF from Slidegeeks and deliver a wonderful presentation.
Cyber Network Simulation Platform Capital Funding Pitch Deck Understanding The Market Potential Icons PDF
Purpose of the following slide is to show the TAM SAM and SOM of the VR Industry market as it displays the total addressable market, the serviceable available market and the actual target market for the organization This is a cyber network simulation platform capital funding pitch deck understanding the market potential icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like total available market, serviceable available market, actual target market You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
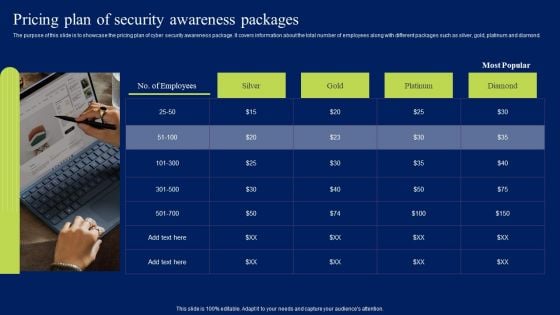
Pricing Plan Of Security Awareness Packages Ppt Ideas Graphic Tips PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Pricing Plan Of Security Awareness Packages Ppt Ideas Graphic Tips PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Pricing Plan Of Security Awareness Packages Ppt Ideas Graphic Tips PDF today and make your presentation stand out from the rest.
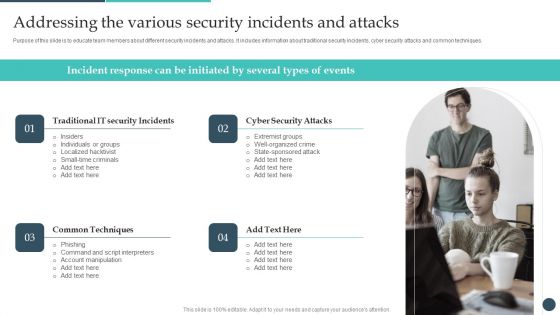
Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
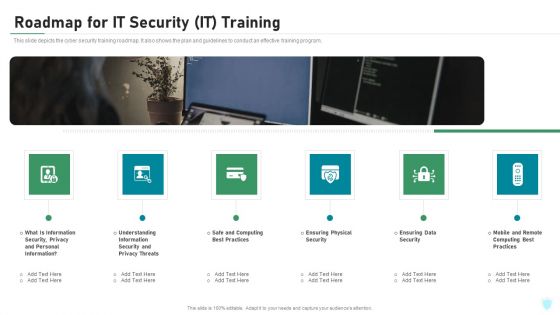
Roadmap For IT Security IT Training Ppt Slides Format Ideas PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting roadmap for it security it training ppt slides format ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, privacy, safe and computing, ensuring physical security, mobile and remote. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
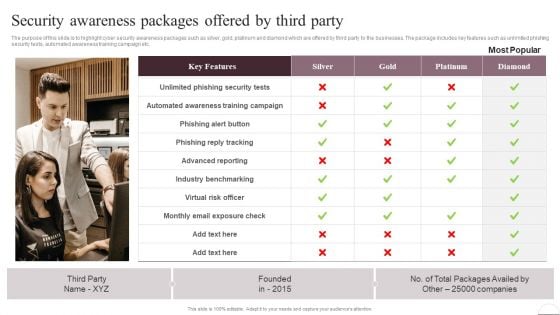
Prevention Of Information Security Awareness Packages Offered By Third Party Information PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Prevention Of Information Security Awareness Packages Offered By Third Party Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Hardware And Software Update In Company IT Security IT Ppt Model Infographics PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting hardware and software update in company it security it ppt model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technology, security, data across. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
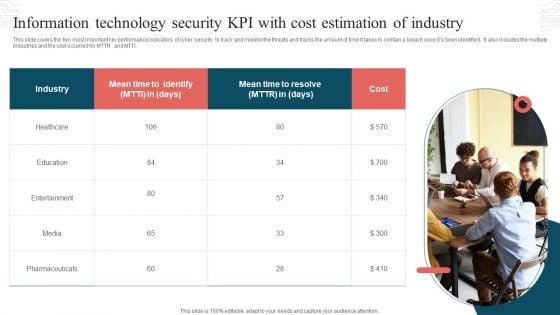
Information Technology Security KPI With Cost Estimation Of Industry Topics PDF
This slide covers the two most important key performance indicators of cyber security to track and monitor the threats and tracks the amount of time it takes to contain a breach once its been identified. It also includes the multiple industries and the cost occurred for MTTR and MTTI. Persuade your audience using this Information Technology Security KPI With Cost Estimation Of Industry Topics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Industry, Mean Time, Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
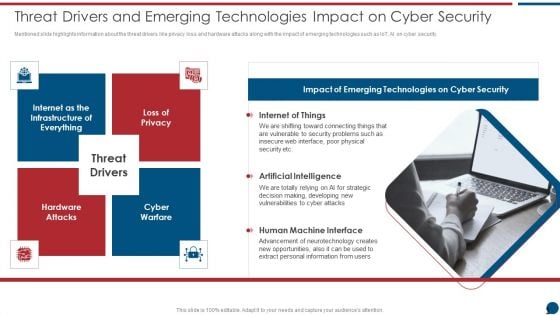
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
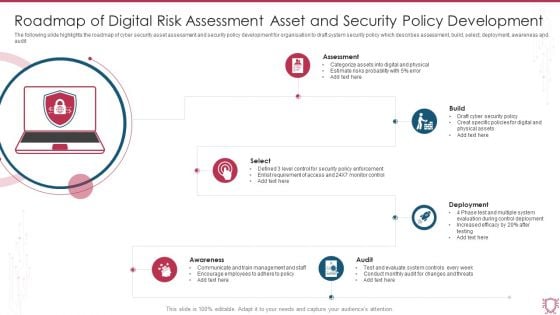
Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
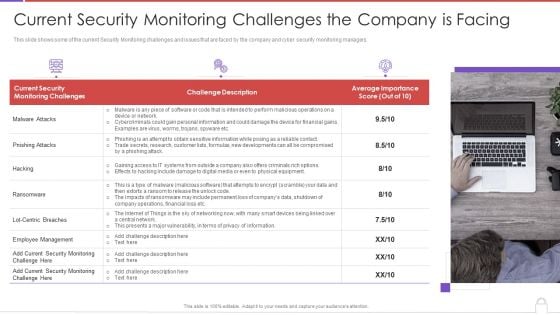
Methods To Develop Advanced Current Security Monitoring Challenges The Company Is Facing Professional PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a methods to develop advanced current security monitoring challenges the company is facing professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current security, monitoring challenges, challenge description, average importance score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Minimize Administrative And Staff Privileges Ppt PowerPoint Presentation Icon Files PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting info security minimize administrative and staff privileges ppt powerpoint presentation icon files pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like employees, prevent cyber attacks, administrative staff. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
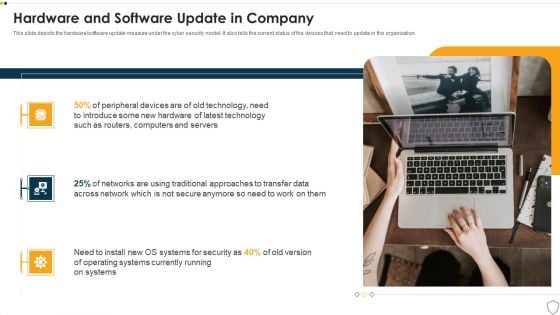
IT Security Hardware And Software Update In Company Ppt Infographics Ideas PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a it security hardware and software update in company ppt infographics ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, security, operating systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Hardware And Software Update In Company Ppt Outline Graphics Pictures PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a information security hardware and software update in company ppt outline graphics pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, technology, devices, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
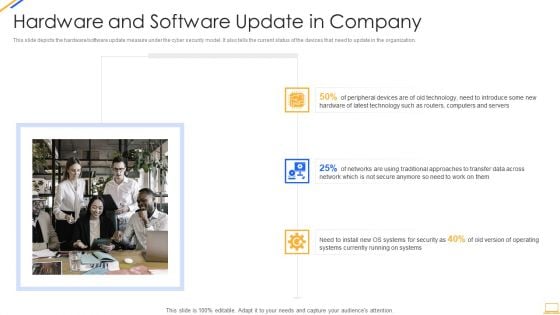
Desktop Security Management Hardware And Software Update In Company Portrait PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a desktop security management hardware and software update in company portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, servers, devices, network, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
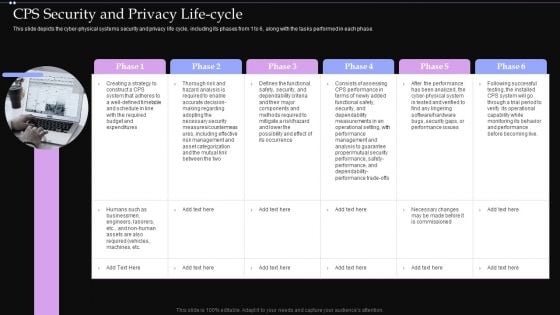
CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Enhancing Cyber Safety With Vulnerability Administration Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of sixty one slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.
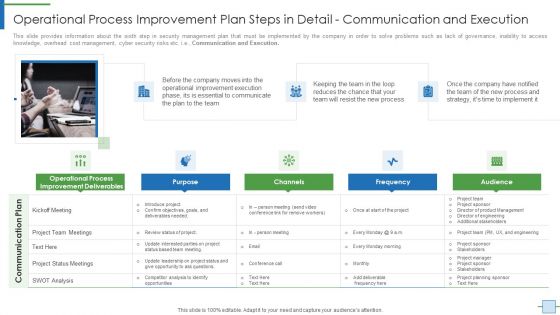
Operational Process Improvement Plan Steps In Detail Communication And Execution Information PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like communicate, team, process, reduces, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
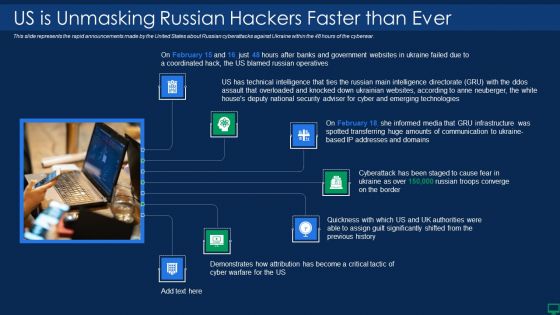
Russian Cyber Attacks On Ukraine IT Us Is Unmasking Russian Inspiration PDF
This slide represents the rapid announcements made by the United States about Russian cyberattacks against Ukraine within the 48 hours of the cyberwar. Presenting russian cyber attacks on ukraine it us is unmasking russian inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like technical, security, communication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Prevention Of Information Practices To Improve Security Awareness Level Amongst Download PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Take your projects to the next level with our ultimate collection of Prevention Of Information Practices To Improve Security Awareness Level Amongst Download PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest

Handling Cyber Threats Digital Era Defining Business Priorities To Ensure Ppt Gallery Brochure PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting handling cyber threats digital era defining business priorities to ensure ppt gallery brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like efficient risk management, standardized incident management process, transparent communication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Communication And Execution Guidelines PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improvement, communicate, team, process, implement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Stock Photo 3d Blue Folder With Lock For Data Security PowerPoint Slide
This power point image template has been crafted with graphic of 3d blue folder and lock. This image contains the concept of data security. Use this image PPT for your technology and security related presentations.

Global Data Security Industry Report Major Market Trends Impacting Cybersecurity Industry IR SS V
The slide highlights the market trends in the global cybersecurity industry. These trends are having a significant impact on the way the industry operates, and they are likely to continue in the coming years. It cover trends such as artificial intelligence, real-time data monitoring, managed services, users as an attack surface, and quantum cryptography. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Global Data Security Industry Report Major Market Trends Impacting Cybersecurity Industry IR SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The slide highlights the market trends in the global cybersecurity industry. These trends are having a significant impact on the way the industry operates, and they are likely to continue in the coming years. It cover trends such as artificial intelligence, real-time data monitoring, managed services, users as an attack surface, and quantum cryptography.
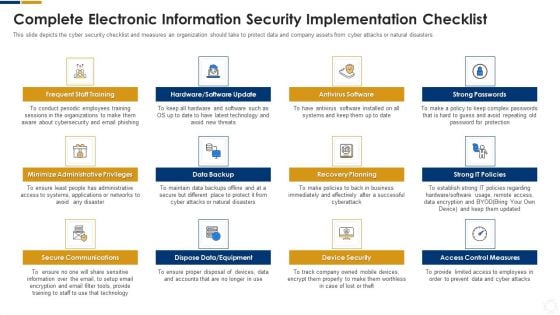
Cybersecurity Complete Electronic Information Security Implementation Checklist Ppt Inspiration Outline PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting cybersecurity complete electronic information security implementation checklist ppt inspiration outline pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, equipment, secure communications, data backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Wireless Network Security System To Prevent Unauthorized Access To Internet Elements PDF
Presenting wireless network security system to prevent unauthorized access to internet elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system to prevent unauthorized access to internet. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Phone Internet Security Vector Icon Ppt PowerPoint Presentation File Graphics PDF
Presenting smart phone internet security vector icon ppt powerpoint presentation file graphics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including smart phone internet security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Common Network Security Threats Vector Icon Ppt PowerPoint Presentation Ideas Elements PDF
Presenting common network security threats vector icon ppt powerpoint presentation ideas elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including common network security threats vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Threat Prevention And Security Vector Icon Ppt PowerPoint Presentation Outline Example Introduction PDF
Presenting network threat prevention and security vector icon ppt powerpoint presentation outline example introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network threat prevention and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































