Cyber Security Dashboard
Mitigating Cybersecurity Threats And Vulnerabilities Cyber Threats Management Slides PDF
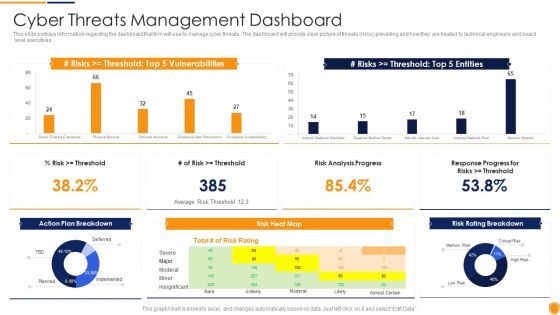
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities cyber threats management slides pdf. Use them to share invaluable insights on cyber threats management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Risk Mitigating Business Information Cyber Protection Strategies Themes PDF
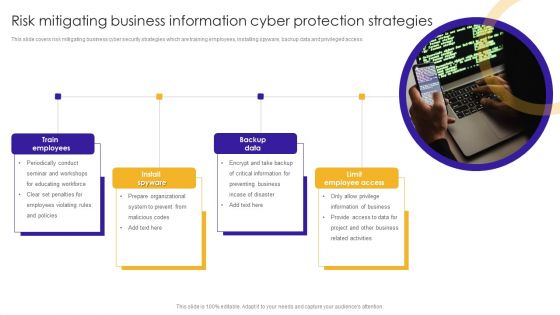
This slide covers risk mitigating business cyber security strategies which are training employees, installing spyware, backup data and privileged access.Presenting Risk Mitigating Business Information Cyber Protection Strategies Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Information Business, Related Activities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents Cyber Safety Incident Management Formats PDF
Presenting table of contents cyber safety incident management formats pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like ensuring financial assets security, leveraging workforce, budget assessment, impact assessment, dashboard . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Key Elements Of IT Security Plan Background PDF
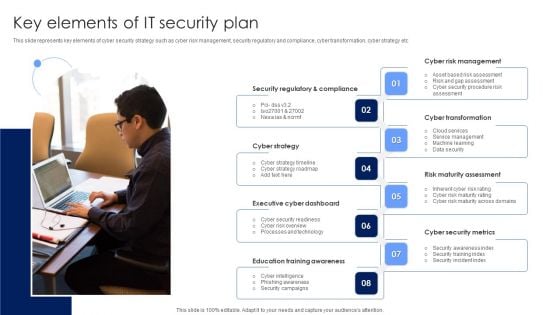
This slide represents key elements of cyber security strategy such as cyber risk management, security regulatory and compliance, cyber transformation, cyber strategy etc. Persuade your audience using this Key Elements Of IT Security Plan Background PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Strategy, Executive Cyber Dashboard, Education Training Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Multiple Challenges Of Business Cyber Threat Prevention Sample PDF
The following slide represent the statistical data of various cyber safety challenges reported by business and organizations which helps to determine the most vulnerable one. Major areas are information security, business agility, automation, integration, etc. Showcasing this set of slides titled Multiple Challenges Of Business Cyber Threat Prevention Sample PDF. The topics addressed in these templates are Key Takeaways, Cyber Safety, Prevention. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Protection Icon To Reduce Data Breaches Clipart PDF
Showcasing this set of slides titled Cyber Protection Icon To Reduce Data Breaches Clipart PDF. The topics addressed in these templates are Reduce Data Breaches, Cyber Protection Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Safety Initiatives Communication Plan For Cyber Breaches Topics PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting data safety initiatives communication plan for cyber breaches topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communicate, delivery method, frequency, responsible, product report. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Internet Security Challenges And Solutions In Banking Industry Download Pdf
This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.Showcasing this set of slides titled Internet Security Challenges And Solutions In Banking Industry Download Pdf The topics addressed in these templates are Installing Intergraded, Introducing Firewall, Learning Algorisms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.

Security And Performance Digital Marketing Google Data Studio To Build Realtime Reporting Dashboards Information PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio To Build Realtime Reporting Dashboards Information PDF bundle. Topics like Operating Breakdown, Session Duration, Goal Completions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Elements Of Internet Security In Website Development Formats Pdf
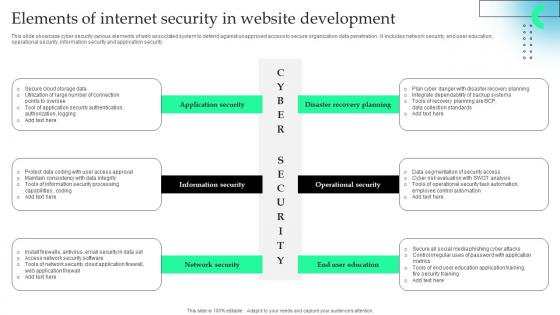
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.
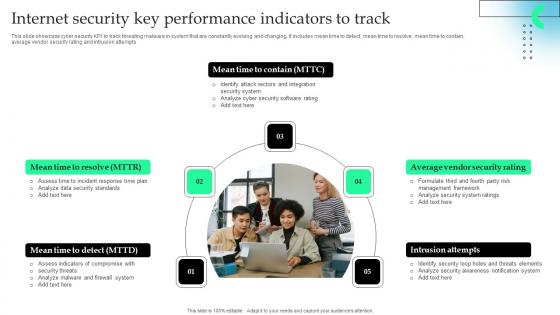
Internet Security Key Performance Indicators To Track Microsoft Pdf
This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.Showcasing this set of slides titled Internet Security Key Performance Indicators To Track Microsoft Pdf The topics addressed in these templates are Firewall System, Security Standards, Identify Attack All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.
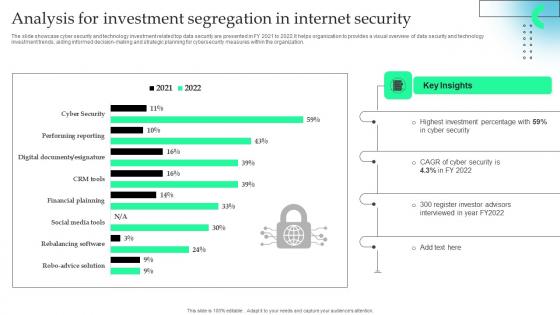
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.

Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Operational Outlook Of Security Awareness Training Software Icons PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Deliver an awe inspiring pitch with this creative Operational Outlook Of Security Awareness Training Software Icons PDF bundle. Topics like Educate Employees, Dynamic Training, Customized Content can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

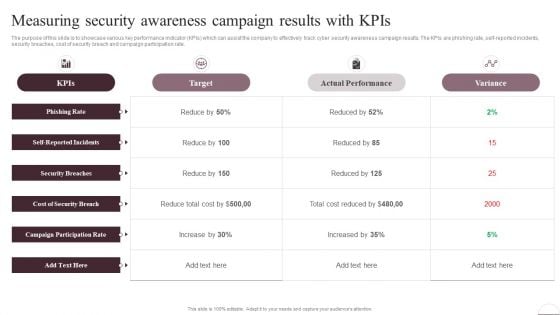
Measuring Security Awareness Campaign Results With Kpis Template PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self reported incidents, security breaches, cost of security breach and campaign participation rateDeliver an awe inspiring pitch with this creative Measuring Security Awareness Campaign Results With Kpis Template PDF bundle. Topics like Security Breaches, Cost Of Security, Campaign Participation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
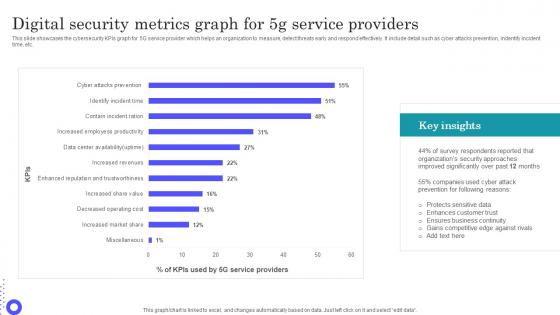
Digital Security Metrics Graph For 5g Service Providers Guidelines Pdf
Showcasing this set of slides titled Digital Security Metrics Graph For 5g Service Providers Guidelines Pdf The topics addressed in these templates are Protects Sensitive, Enhances Customer, Ensures Business Continuity All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs graph for 5G service provider which helps an organization to measure, detect threats early and respond effectively. It include detail such as cyber attacks prevention, indentify incident time, etc.
Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF from Slidegeeks and deliver a wonderful presentation.
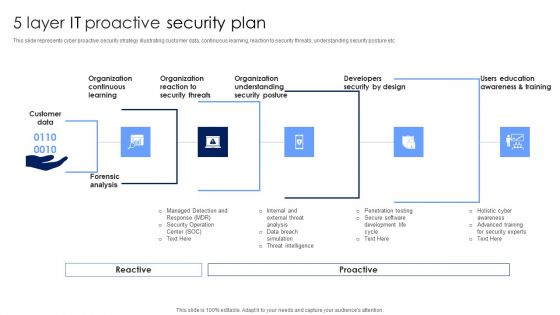
5 Layer IT Proactive Security Plan Topics PDF
This slide represents cyber proactive security strategy illustrating customer data, continuous learning, reaction to security threats, understanding security posture etc. Persuade your audience using this 5 Layer IT Proactive Security Plan Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization Understanding, Organization Reaction, Organization Continuous Learning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Latest Trends For Mobile Smart Phone Security Icons PDF
This slide shows current trends for securing mobile phone against potential cyber attacks and loss of sensitive data. It include trends such as rise in security automation, increasing threat modelling and SAST-DAST integration etc qPresenting Latest Trends For Mobile Smart Phone Security Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increasing Security, SAST DAST Integration, Increasing Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
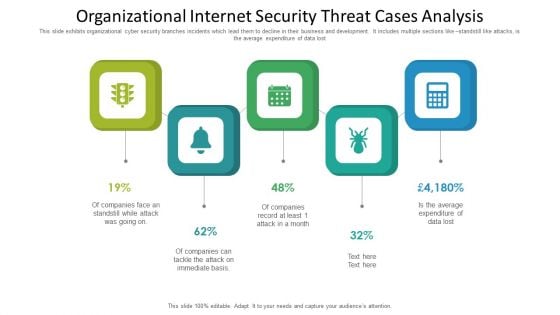
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
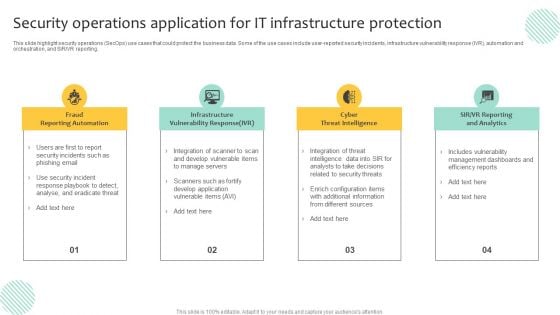
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
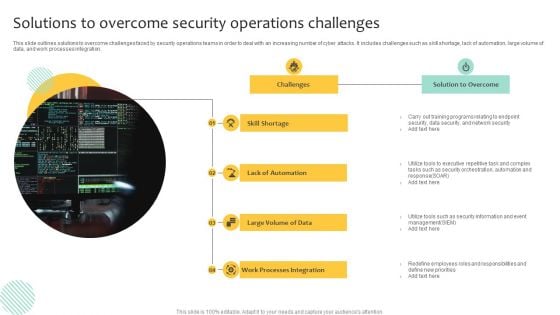
Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Asset Identification For Information Security Risk Management Topics PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack This is a Asset Identification For Information Security Risk Management Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers Database, Products Database, Sales Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
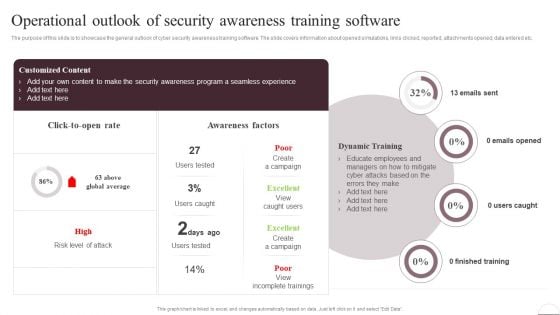
Prevention Of Information Operational Outlook Of Security Awareness Structure PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered. Slidegeeks has constructed Prevention Of Information Operational Outlook Of Security Awareness Structure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
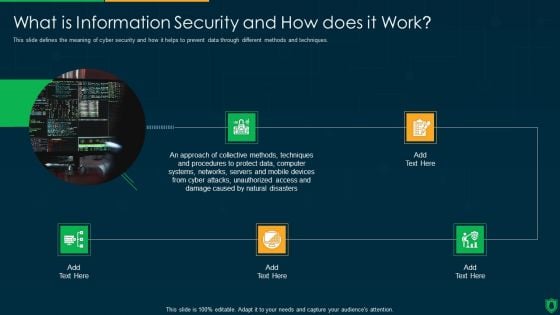
Info Security What Is Information Security And How Does It Work Ppt PowerPoint Presentation File Clipart PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a info security what is information security and how does it work ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collective methods, techniques and procedures, protect data, computer systems, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Security Market Research Report Industry Challenges Ppt Ideas PDF
Presenting this set of slides with name email security market research report industry challenges ppt ideas pdf. This is a five stage process. The stages in this process are threat of ransomware, threat of serverless apps, iot threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Internet Security And Data Audit Icon Pictures Pdf
Pitch your topic with ease and precision using this Internet Security And Data Audit Icon Pictures Pdf This layout presents information on Internet Security, Data Audit Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Internet Security And Data Audit Icon Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
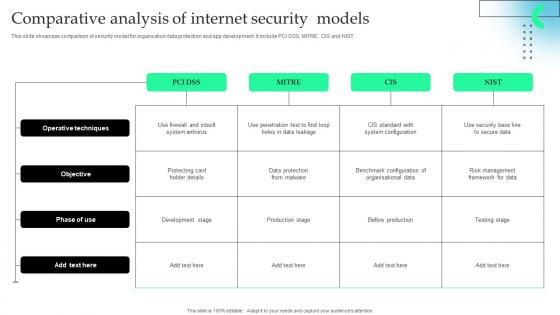
Comparative Analysis Of Internet Security Models Slides Pdf
This slide showcase comparison of security model for organsation data protection and app development. It include PCI DSS, MITRE, CIS and NIST Pitch your topic with ease and precision using this Comparative Analysis Of Internet Security Models Slides Pdf This layout presents information on Operative Techniques, Development Stage, Benchmark Configuration It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase comparison of security model for organsation data protection and app development. It include PCI DSS, MITRE, CIS and NIST

Green Computing Improving Security By Green Computing Technology
This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. The Green Computing Improving Security By Green Computing Technology is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
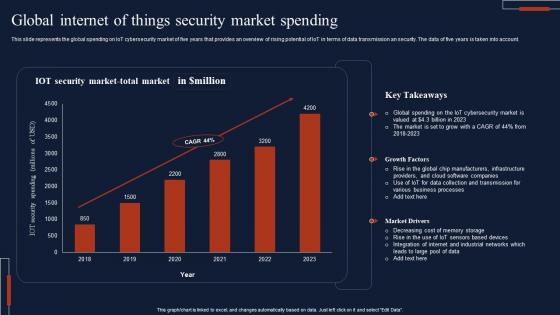
Global Internet Of Things Security Market Spending Download Pdf
This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account. Pitch your topic with ease and precision using this Global Internet Of Things Security Market Spending Download Pdf This layout presents information on IOT Security, Market Total, Key Takeaways It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account.
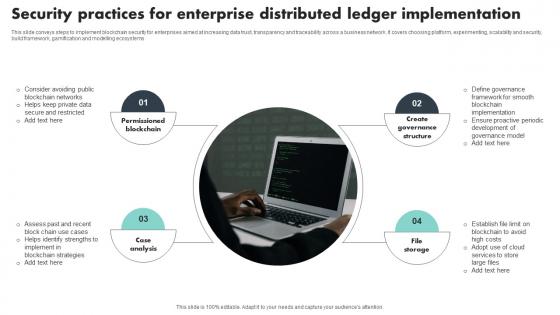
Security Practices For Enterprise Distributed Ledger Implementation Template Pdf
This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems Showcasing this set of slides titled Security Practices For Enterprise Distributed Ledger Implementation Template Pdf The topics addressed in these templates are Permissioned Blockchain, Case Analysis, Create Governance Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems
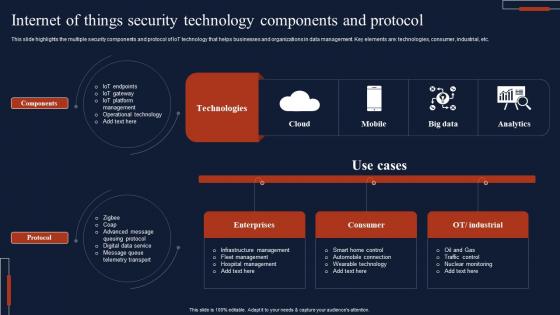
Internet Of Things Security Technology Components And Protocol Rules Pdf
This slide highlights the multiple security components and protocol of IoT technology that helps businesses and organizations in data management. Key elements are technologies, consumer, industrial, etc. Pitch your topic with ease and precision using this Internet Of Things Security Technology Components And Protocol Rules Pdf This layout presents information on Components, Protocol, Technologies, Consumer It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights the multiple security components and protocol of IoT technology that helps businesses and organizations in data management. Key elements are technologies, consumer, industrial, etc.
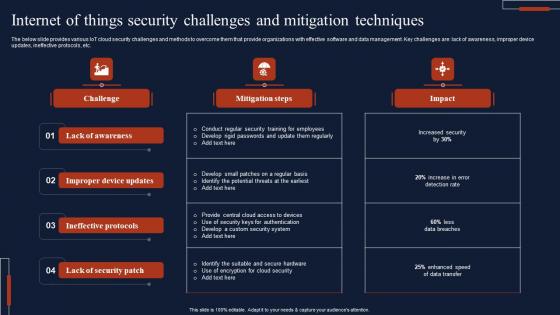
Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf
The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc. Pitch your topic with ease and precision using this Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf This layout presents information on Lack Of Awareness, Ineffective Protocols, Lack Of Security Patch It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc.
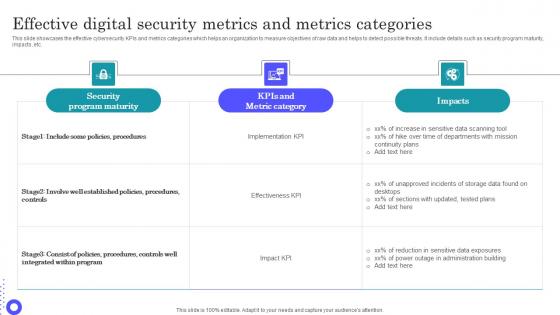
Effective Digital Security Metrics And Metrics Categories Microsoft Pdf
Pitch your topic with ease and precision using this Effective Digital Security Metrics And Metrics Categories Microsoft Pdf This layout presents information on Security Program Maturity, Metric Category, Sensitive Data Scanning It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the effective cybersecurity KPIs and metrics categories which helps an organization to measure objectives of raw data and helps to detect possible threats. It include details such as security program maturity, impacts, etc.
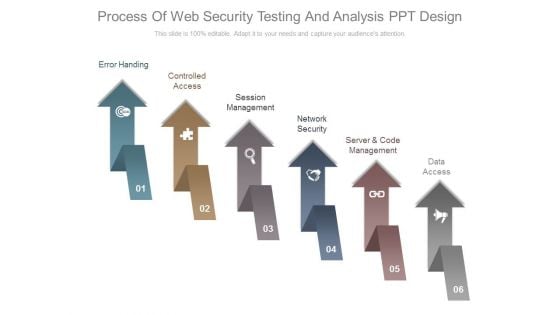
Process Of Web Security Testing And Analysis Ppt Design
This is a process of web security testing and analysis ppt design. This is a six stage process. The stages in this process are error handing, controlled access, session management, network security, server and code management, data access.
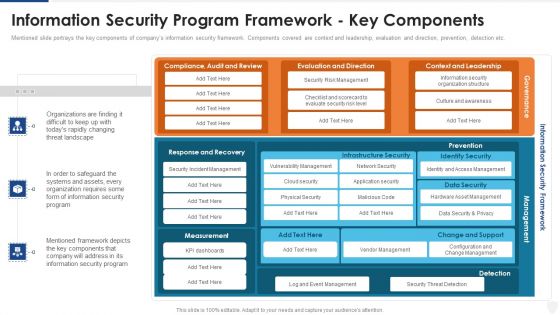
Information Security Program Framework Key Components Ppt Inspiration Ideas PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this information security program framework key components ppt inspiration ideas pdf. Use them to share invaluable insights on network security, application security, vendor management, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
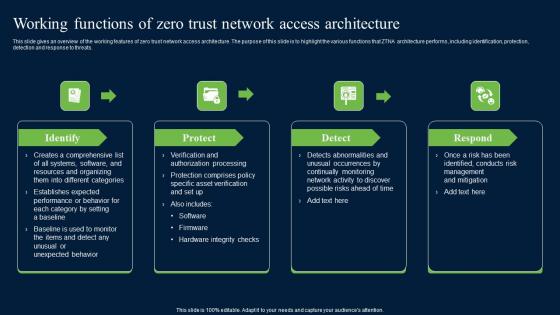
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
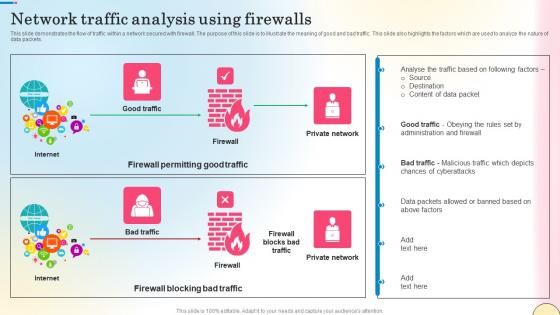
Network Traffic Analysis Using Firewalls Network Security Themes Pdf
This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc. Take your projects to the next level with our ultimate collection of Network Traffic Analysis Using Firewalls Network Security Themes Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc.
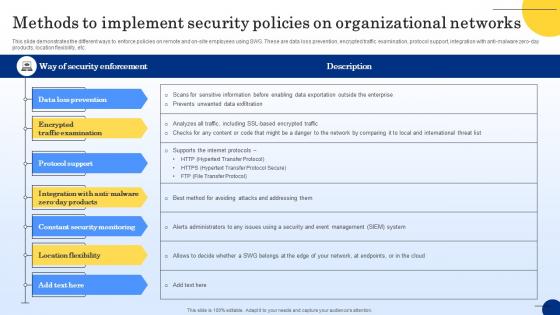
Methods To Implement Security Policies On Web Threat Protection System
This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Are you searching for a Methods To Implement Security Policies On Web Threat Protection System that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Methods To Implement Security Policies On Web Threat Protection System from Slidegeeks today. This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc.
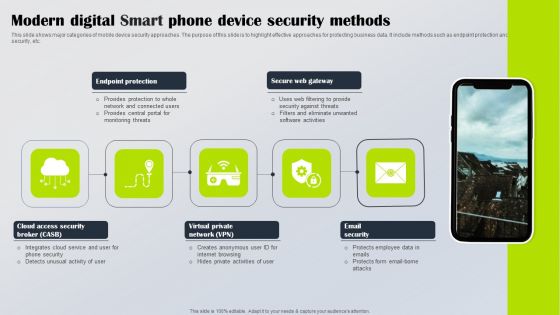
Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
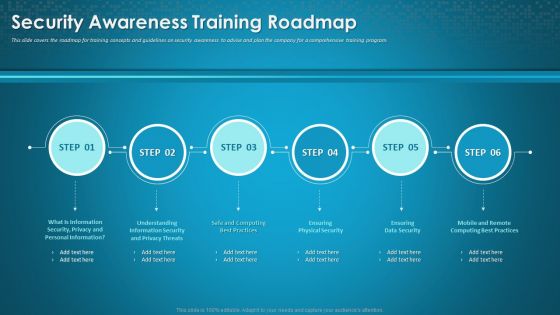
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
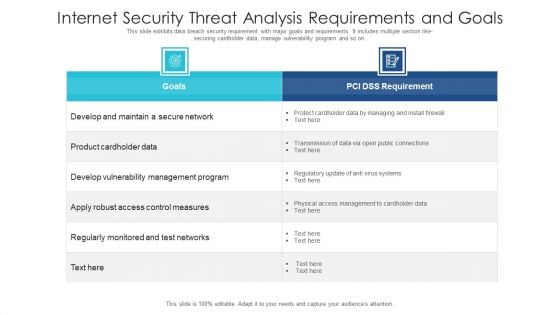
Internet Security Threat Analysis Requirements And Goals Ideas PDF
This slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like- securing cardholder data, manage vulnerability program and so on. Showcasing this set of slides titled internet security threat analysis requirements and goals ideas pdf. The topics addressed in these templates are internet security threat analysis requirements and goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
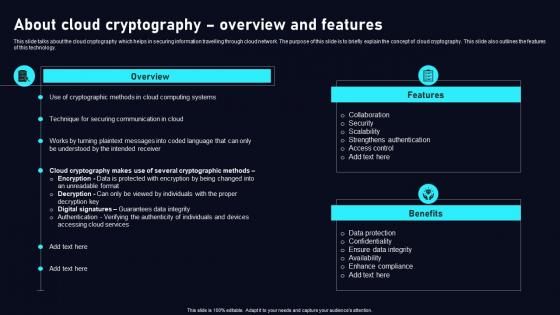
About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Present like a pro with About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology.

Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
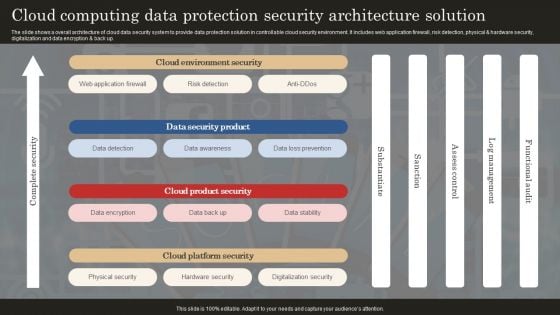
Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
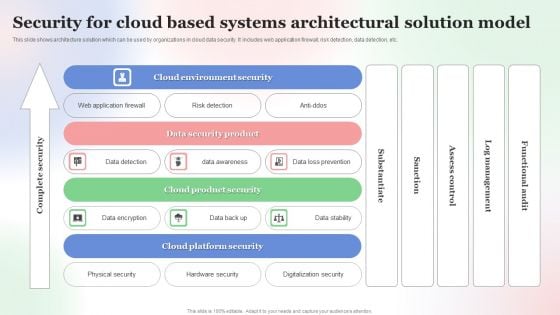
Security For Cloud Based Systems Architectural Solution Model Background PDF
This slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Showcasing this set of slides titled Security For Cloud Based Systems Architectural Solution Model Background PDF. The topics addressed in these templates are Security For Cloud Based, Systems Architectural Solution Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Digital Security Metrics Used By Threat Analysts Graphics Pdf
Showcasing this set of slides titled Digital Security Metrics Used By Threat Analysts Graphics Pdf The topics addressed in these templates are Regulatory Requirements, Large Increase, Scanning Outweighs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc.
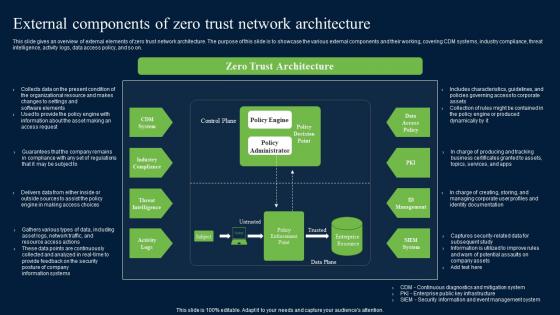
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
Web Acceleration Security Software Shopping Carts Ppt Example
This is a web acceleration security software shopping carts ppt example. This is a eight stage process. The stages in this process are web acceleration, security software, shopping carts, data services, portals and intranets, domain name services, hosted application, cloud computing.
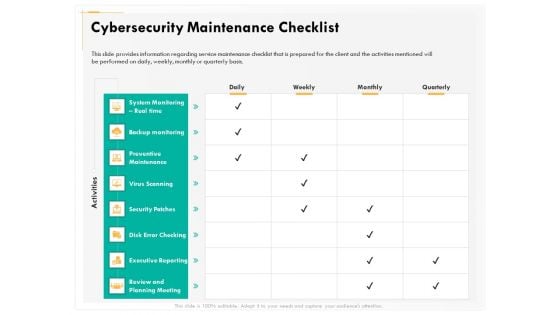
Computer Security Incident Handling Cybersecurity Maintenance Checklist Background PDF
Presenting this set of slides with name computer security incident handling cybersecurity maintenance checklist background pdf. The topics discussed in these slides are system monitoring real time, backup monitoring, preventive maintenance, virus scanning, security patches, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
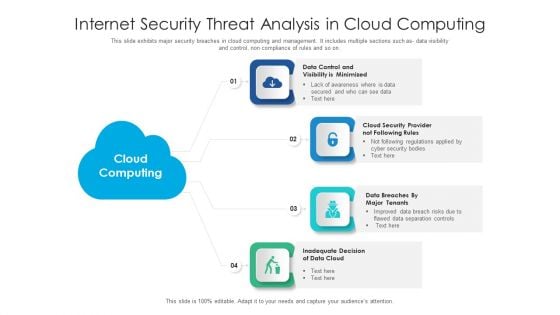
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
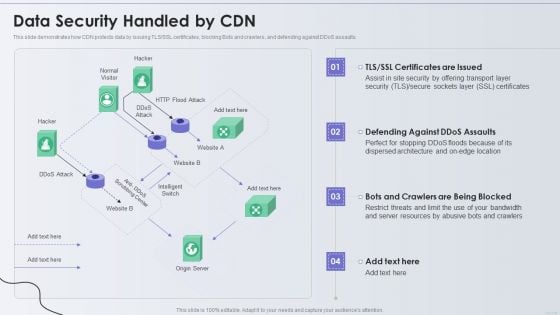
Distribution Network Data Security Handled By CDN Topics PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an awe inspiring pitch with this creative Distribution Network Data Security Handled By CDN Topics PDF bundle. Topics like Security, Resources, Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
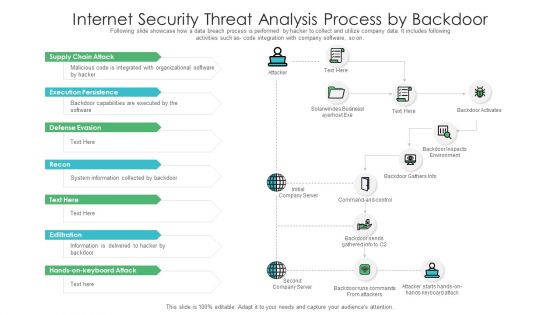
Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
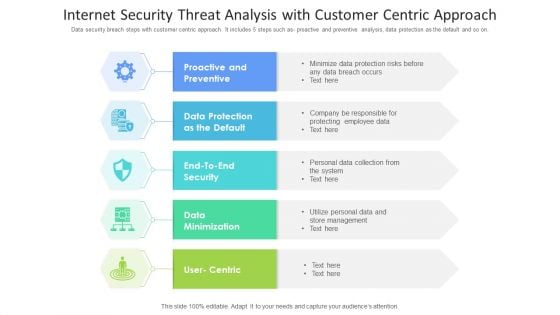
Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Process To Manage Firms Sensitive Data Mockup PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Boost your pitch with our creative Information Security Process To Manage Firms Sensitive Data Mockup PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
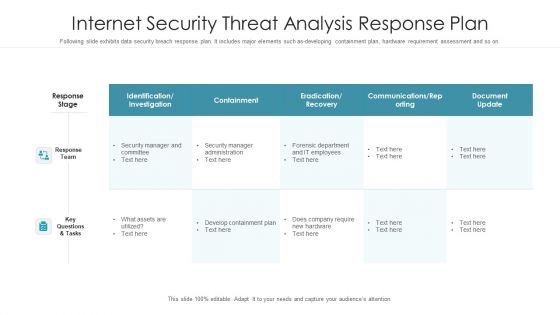
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Email Security Market Research Report About Us Ppt Clipart PDF
Presenting this set of slides with name email security market research report about us ppt clipart pdf. This is a three stage process. The stages in this process are target audiences, premium services, value clients. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































