Cyber Security Dashboard

Secure Your Internet Data PowerPoint Templates Ppt Backgrounds For Slides 0713
Brace yourself, arm your thoughts. Prepare for the hustle with our Secure Your Internet Data PowerPoint Templates PPT Backgrounds For Slides 0713. Generate ecstasy with our Technology PowerPoint Templates. Your thoughts will delight your audience. Delight them with our Security PowerPoint Templates. Your audience will be ecstatic. Get your audience all activated to go. Emit exhilirating energy with our Secure Your Internet Data PowerPoint Templates Ppt Backgrounds For Slides 0713.

Key Benefits Of Using Secure Web Gateway Web Threat Protection System
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Welcome to our selection of the Key Benefits Of Using Secure Web Gateway Web Threat Protection System. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc.
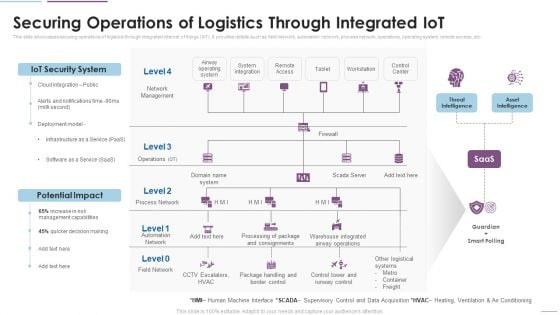
Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. This is a Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IoT Security System, Potential Impact, Network Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

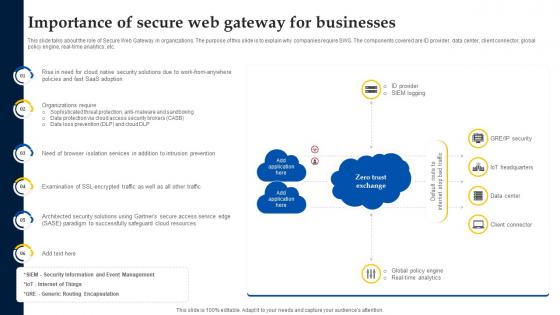
Importance Of Secure Web Gateway For Businesses Web Threat Protection System
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Secure Web Gateway For Businesses Web Threat Protection System. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc.
Web Access Control Solution Importance Of Secure Web Gateway For Businesses
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Explore a selection of the finest Web Access Control Solution Importance Of Secure Web Gateway For Businesses here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Web Access Control Solution Importance Of Secure Web Gateway For Businesses to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc.

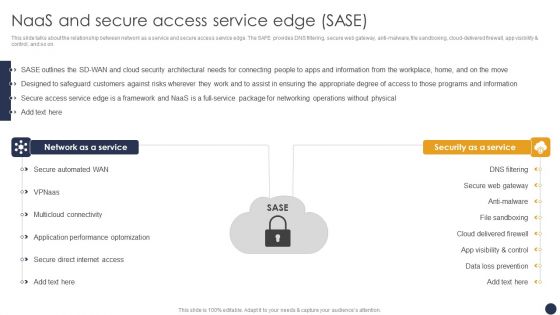
Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF.
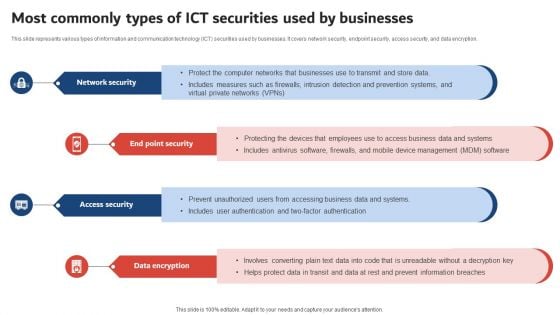
Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF
This slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Data Transfer On Secured Network Vector Icon Ppt PowerPoint Presentation File Demonstration PDF
Presenting this set of slides with name data transfer on secured network vector icon ppt powerpoint presentation file demonstration pdf. This is a two stage process. The stages in this process are data transfer on secured network vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Integrating Naas Service Model Naas And Secure Access Service Edge Sase Ppt Model Picture PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. The Integrating Naas Service Model Naas And Secure Access Service Edge Sase Ppt Model Picture PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
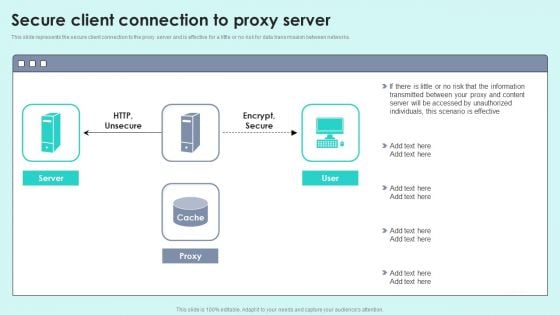
Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks.Deliver an awe inspiring pitch with this creative Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF bundle. Topics like Transmitted Between, Accessed Unauthorized, Scenario Effective can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Secure Web Gateway SWG Importance For Businesses Ppt Professional Graphics PDF
This slide outlines the importance of secure web gateways to businesses. The purpose of this slide is to demonstrate the need for SWGs for companies to protect their critical data and applications from malicious activities and actors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Secure Web Gateway SWG Importance For Businesses Ppt Professional Graphics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Smart Phone Data Transfer Via Secured Network Image Ppt Show Graphics PDF
Presenting smart phone data transfer via secured network image ppt show graphics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including smart phone data safety application with protection shield. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
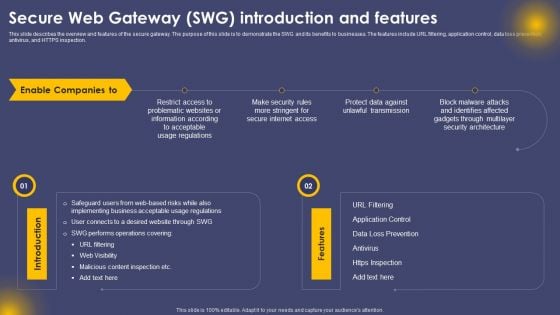
Secure Web Gateway SWG Introduction And Features Ppt Portfolio Master Slide PDF
This slide describes the overview and features of the secure gateway. The purpose of this slide is to demonstrate the SWG and its benefits to businesses. The features include URL filtering, application control, data loss prevention, antivirus, and HTTPS inspection. Present like a pro with Secure Web Gateway SWG Introduction And Features Ppt Portfolio Master Slide PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Reverse Proxy Server IT Secure Client Connection To Proxy Server Ppt Icon Graphics Template PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks. This is a reverse proxy server it secure client connection to proxy server ppt icon graphics template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server, proxy, cache. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Stock Photo 3d Globe With Social Web For Data Protection Concept PowerPoint Slide
Graphic of 3d globe and web has been used to craft this power point image template. This PPT contains the concept of data protection and social network. Use this PPT and build quality presentation for your viewers.
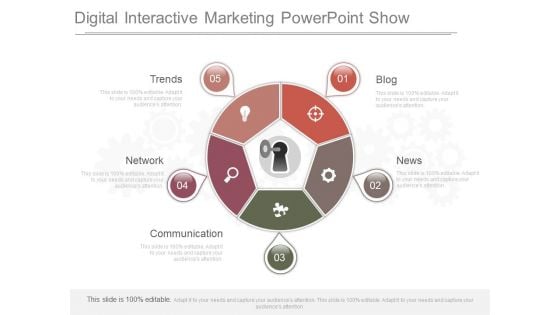
Digital Interactive Marketing Powerpoint Show
This is a digital interactive marketing powerpoint show. This is a five stage process. The stages in this process are blog, news, communication, network, trends.
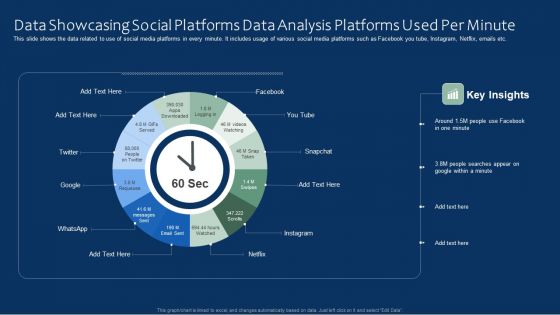
Data Showcasing Social Platforms Data Analysis Platforms Used Per Minute Microsoft PDF
This slide shows the data related to use of social media platforms in every minute. It includes usage of various social media platforms such as Facebook you tube, Instagram, Netflix, emails etc. Persuade your audience using this Data Showcasing Social Platforms Data Analysis Platforms Used Per Minute Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Data Showcasing Social Platforms, Data Analysis Platforms. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
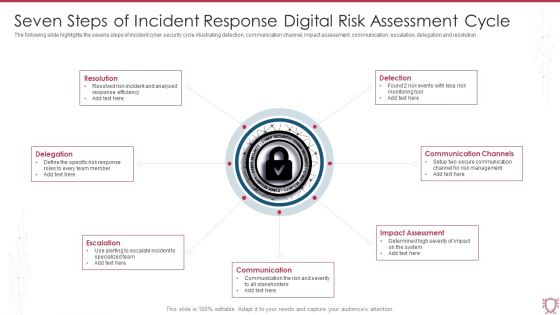
Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF
The following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution, Persuade your audience using this Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Resolution, Detection, Communication Channels, Impact Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Business Diagrams Templates Umbrella And Symbol PowerPoint Ppt Backgrounds For Slides
We present our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides.Download and present our Security PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Present our Business PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Use our Internet PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Present our Computer PowerPoint Templates because you can Set pulses racing with our PowerPoint Templates and Slides. They will raise the expectations of your team.Use these PowerPoint slides for presentations relating to 3d, Access, Business, Close, Computer, Concept, Connection, Data, Digital, Firewall, Global, Guard, Information, Internet, Laptop, Light, Metal, Network, Office, Online, Pc, Personal, Privacy, Protection, Render, Safe, Secure, Security, Shield, Sign, Silver, Steel, Success, Support, Symbol, Technology, Umbrella, Virus, Web. The prominent colors used in the PowerPoint template are Blue, White, Gray. Use our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides will get their audience's attention. We assure you our Digital PowerPoint templates and PPT Slides will get their audience's attention. Use our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Customers tell us our Data PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Presenters tell us our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. PowerPoint presentation experts tell us our Digital PowerPoint templates and PPT Slides will make you look like a winner. Confront disbelievers with our Business Diagrams Templates Umbrella And Symbol PowerPoint Ppt Backgrounds For Slides. They will bow before your convictions.

Broken Wall Metaphor PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Broken Wall Metaphor PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides are like the strings of a tennis racquet. Well strung to help you serve aces. Download our Construction PowerPoint Templates because you should once Tap the ingenuity of our PowerPoint Templates and Slides. They are programmed to succeed. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune.Use these PowerPoint slides for presentations relating to Broken Brick Wall, security, construction, shapes, business, success. The prominent colors used in the PowerPoint template are Red, Black, Maroon. Use our Broken Wall Metaphor PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by a team of presentation professionals. The feedback we get is that our shapes PowerPoint templates and PPT Slides will help them to explain complicated concepts. Customers tell us our Broken Wall Metaphor PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Customers tell us our business PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Presenters tell us our Broken Wall Metaphor PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Presenters tell us our shapes PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Examine data with our Broken Wall Metaphor PowerPoint Templates Ppt Backgrounds For Slides 0113. You will come out on top.

Debit Card With Lock For Safe Transactions Ppt PowerPoint Presentation Infographics Tips PDF
Presenting this set of slides with name data network security with lock showing online safety icon ppt powerpoint presentation infographic template graphics pdf. This is a three stage process. The stages in this process are debit card with lock for safe transactions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
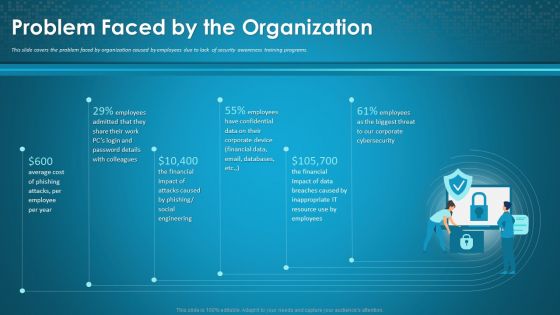
Organizational Network Staff Learning Problem Faced By The Organization Topics PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a organizational network staff learning problem faced by the organization topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, financial data, resource use by employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Table Of Contents Infographics PDF
Presenting mitigating cybersecurity threats and vulnerabilities table of contents infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like leveraging workforce, budget assessment, dashboard, impact assessment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Cybersecurity Challenges With Required Actions Ppt Pictures Background Designs PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges This is a major cybersecurity challenges with required actions ppt pictures background designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, cybersecurity strategy, performing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Project Analysis Diagram Powerpoint Template
Our above PPT slide contains graphics of cloud with technology icons. This PowerPoint template may be used for project related to cloud computing. Use this diagram to impart more clarity to data and to create more sound impact on viewers.

Examples Of Data Breaches Ppt PowerPoint Presentation Summary Portrait PDF
Presenting this set of slides with name examples of data breaches ppt powerpoint presentation summary portrait pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Types Of Data Breach Ppt PowerPoint Presentation Inspiration Ideas PDF
Presenting this set of slides with name types of data breach ppt powerpoint presentation inspiration ideas pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cybersecurity Key Performance Indicators With Applications Summary Pdf
Pitch your topic with ease and precision using this Cybersecurity Key Performance Indicators With Applications Summary Pdf This layout presents information on Identify Weaknesses, Review Improvement, Security Policies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cyber security key performance indicators with applications which helps an organization to determine readiness. It include details such as security policies, identify weaknesses, obligation to compliance framework, etc.

Predictive Data Model Outliers Model For Predictive Analytics Introduction PDF

Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API.

Data Analysis Reporting Tools Ppt PowerPoint Presentation Professional Layout Cpb Pdf
Presenting this set of slides with name data analysis reporting tools ppt powerpoint presentation professional layout cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber security detection response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Optimizing Business Integration Key Trends That Drive The Industry Information Pdf
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Optimizing Business Integration Key Trends That Drive The Industry Information Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology.

Business Analysis Ability Mapping Model With Techniques Sample Pdf
This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc. Showcasing this set of slides titled Business Analysis Ability Mapping Model With Techniques Sample Pdf The topics addressed in these templates are Business Competency, Proficiency Scale, Specialized Areas All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc.
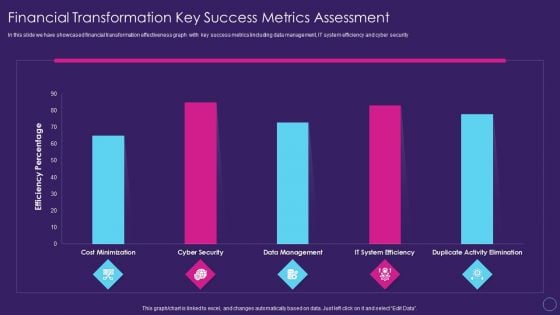
Financial Transformation Key Success Metrics Assessment Digital Transformation Toolkit Accounting Finance Introduction PDF
In this slide we have showcased financial transformation effectiveness graph with key success metrics lincluding data management, IT system efficiency and cyber security Deliver an awe inspiring pitch with this creative financial transformation key success metrics assessment digital transformation toolkit accounting finance introduction pdf bundle. Topics like financial transformation key success metrics assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
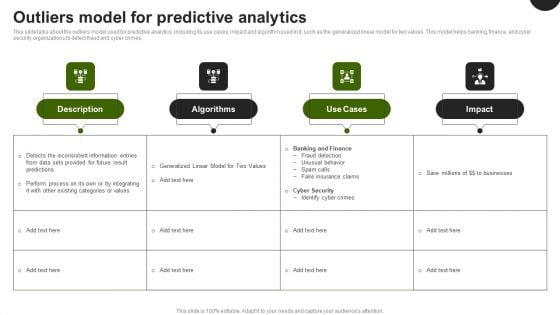
Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF can be your best option for delivering a presentation. Represent everything in detail using Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
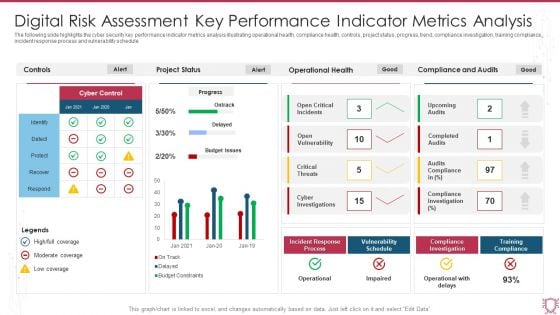
Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF
The following slide highlights the cyber security key performance indicator metrics analysis illustrating operational health, compliance health, controls, project status, progress, trend, compliance investigation, training compliance, incident response process and vulnerability schedule. Showcasing this set of slides titled Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF. The topics addressed in these templates are Project Status, Operational Health, Compliance And Audits. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.
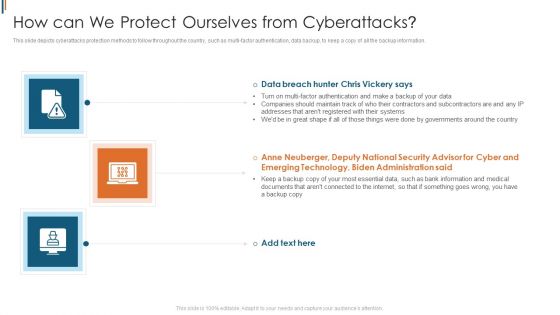
Ukraine Cyberwarfare How Can We Protect Ourselves From Cyberattacks Designs Pdf
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Presenting ukraine cyberwarfare how can we protect ourselves from cyberattacks designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like anne neuberger, deputy national security advisor for cyber and emerging technology, biden administration said. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
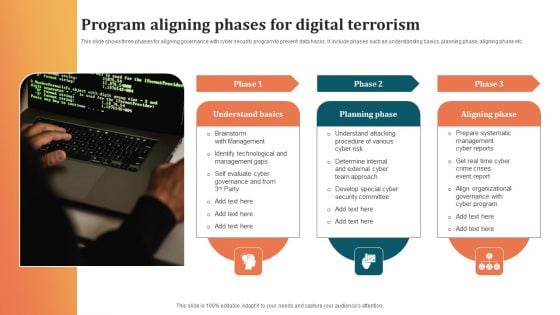
Program Aligning Phases For Digital Terrorism Infographics PDF
This slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc. Persuade your audience using this Program Aligning Phases For Digital Terrorism Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Planning Phase, Aligning Phase, Understand Basics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
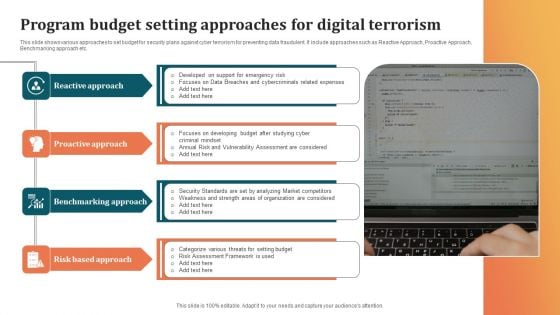
Program Budget Setting Approaches For Digital Terrorism Background PDF
This slide shows various approaches to set budget for security plans against cyber terrorism for preventing data fraudulent. It include approaches such as Reactive Approach, Proactive Approach, Benchmarking approach etc. Presenting Program Budget Setting Approaches For Digital Terrorism Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benchmarking Approach, Risk Based Approach, Proactive Approach. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
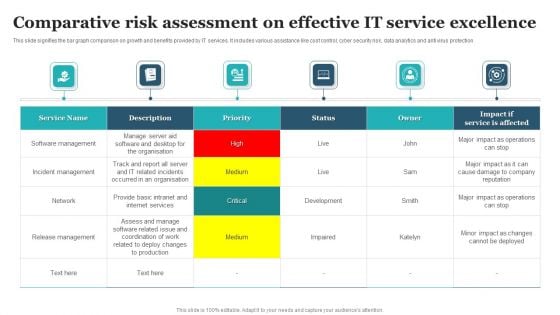
Comparative Risk Assessment On Effective IT Service Excellence Designs PDF
This slide signifies the bar graph comparison on growth and benefits provided by IT services. It includes various assistance like cost control, cyber security risk, data analytics and anti virus protection. Showcasing this set of slides titled Comparative Risk Assessment On Effective IT Service Excellence Designs PDF. The topics addressed in these templates are Software Management, Incident Management, Release Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
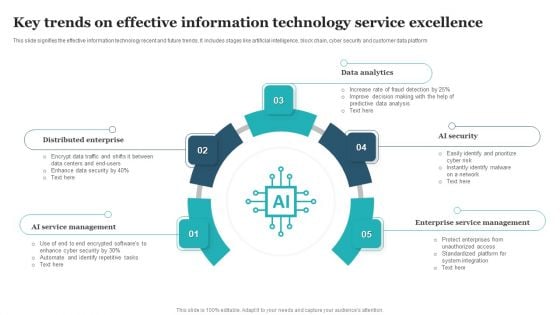
Key Trends On Effective Information Technology Service Excellence Themes PDF
This slide signifies the effective information technology recent and future trends. It includes stages like artificial intelligence, block chain, cyber security and customer data platform. Persuade your audience using this Key Trends On Effective Information Technology Service Excellence Themes PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Analytics, Distributed Enterprise, Enterprise Service Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Healthcare Information Technology Healthcare Information Tech Enhance Medical Facilities Professional Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Healthcare Information Technology Healthcare Information Tech Enhance Medical Facilities Professional Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

Trends In Business Management Template Ppt Design
This is a trends in business management template ppt design. This is a three stage process. The stages in this process are business strategy focus on growth, corporate strategy, preventing cyber attacks.

IOT Technology Trends In Cybersecurity Management Inspiration Pdf
This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection. Pitch your topic with ease and precision using this IOT Technology Trends In Cybersecurity Management Inspiration Pdf This layout presents information on Cybersecurity Mesh, Security At Manufacturing, Network Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection.
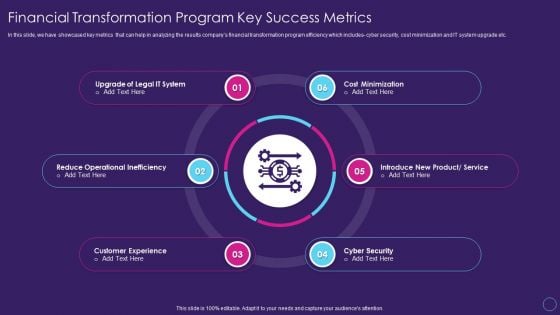
Financial Transformation Program Key Success Metrics Digital Transformation Toolkit Accounting Finance Portrait PDF
In this slide, we have showcased key metrics that can help in analyzing the results companys financial transformation program efficiency which includes cyber security, cost minimization and IT system upgrade etc. Presenting financial transformation program key success metrics digital transformation toolkit accounting finance portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like customer experience, reduce operational inefficiency, cyber security, cost minimization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Challenges Faced By Companies In Online Marketing Efficient Marketing Tactics Structure Pdf
Following slide outlines major challenges of ecommerce websites and potential solutions to overcome them. It include issues such as cyber security, online data verification, data management and customer experiences. There are so many reasons you need a Challenges Faced By Companies In Online Marketing Efficient Marketing Tactics Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide outlines major challenges of ecommerce websites and potential solutions to overcome them. It include issues such as cyber security, online data verification, data management and customer experiences.

Digital Technology Adoption In Banking Industry Case Competition Emerging Technological Infographics PDF
This slide shows the latest technological trends which should be adopted by the ABC Bank which includes cyber security, upgraded ATMs, Chatbot, Artificial Intelligence etc.Presenting Digital Technology Adoption In Banking Industry Case Competition Emerging Technological Infographics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Cyber Security, Artificial Intelligence, Cloud Computing In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
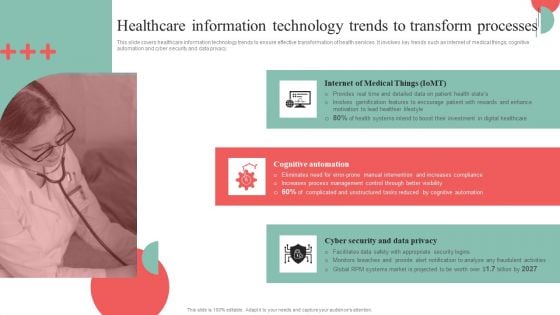
Incorporating HIS To Enhance Healthcare Services Healthcare Information Technology Trends To Transform Processes Professional PDF
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Incorporating HIS To Enhance Healthcare Services Healthcare Information Technology Trends To Transform Processes Professional PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Incorporating HIS To Enhance Healthcare Services Healthcare Information Technology Trends To Transform Processes Professional PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Stock Photo Ball With Big Data Text For Data Protection Concept PowerPoint Slide
Graphic of ball with big data text has been used to craft this power point template. This image template contains the concept of data protection. Use this image for data security related topics in any presentation.

Page Experience Signals In Google Search Console Training Ppt
This slide covers search signals for page experience largely known as core web vitals. It also includes KPIs such as mobile-friendly experience, safe browsing experience, HTTPS security and no intrusive interstitials.
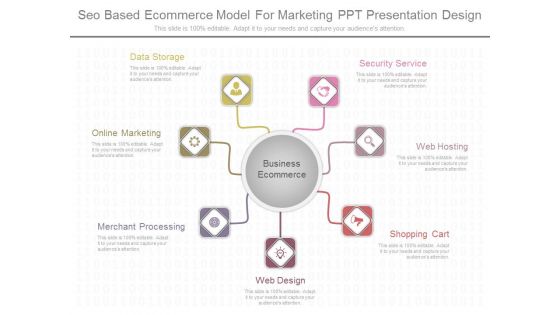
Seo Based Ecommerce Model For Marketing Ppt Presentation Design
This is a seo based ecommerce model for marketing ppt presentation design. This is a seven stage process. The stages in this process are security service, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.
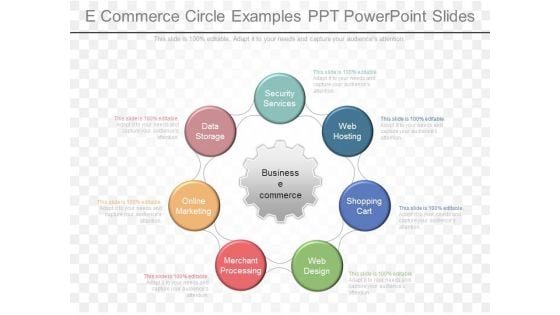
E Commerce Circle Examples Ppt Powerpoint Slides
This is a e commerce circle examples ppt powerpoint slides. This is a seven stage process. The stages in this process are business e commerce, security services, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.
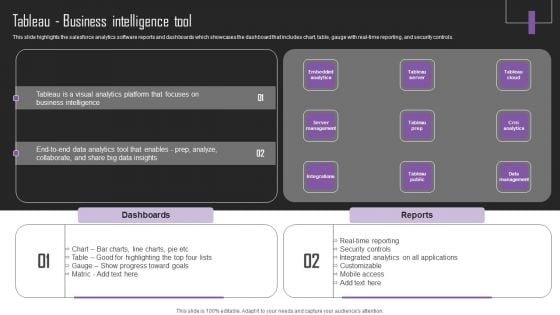
Web Hosting Software Company Outline Tableau Business Intelligence Tool Sample PDF
This slide highlights the salesforce analytics software reports and dashboards which showcases the dashboard that includes chart, table, gauge with real-time reporting, and security controls. This Web Hosting Software Company Outline Tableau Business Intelligence Tool Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
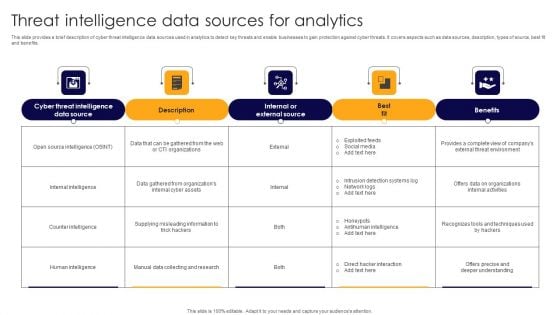
Threat Intelligence Data Sources For Analytics Ideas PDF
This slide provides a brief description of cyber threat intelligence data sources used in analytics to detect key threats and enable businesses to gain protection against cyber threats. It covers aspects such as data sources, description, types of source, best fit and benefits. Showcasing this set of slides titled Threat Intelligence Data Sources For Analytics Ideas PDF. The topics addressed in these templates are Exploited Feeds, Social Media, Intrusion Detection Systems Log. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Boost your pitch with our creative Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
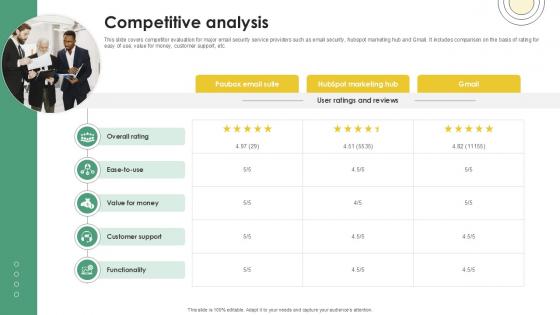
Competitive Analysis Email And Data Protection Platform Capital Funding Pitch Deck PPT Example
This slide covers competitor evaluation for major email security service providers such as email security, hubspot marketing hub and Gmail. It includes comparison on the basis of rating for easy of use, value for money, customer support, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Competitive Analysis Email And Data Protection Platform Capital Funding Pitch Deck PPT Example a try. Our experts have put a lot of knowledge and effort into creating this impeccable Competitive Analysis Email And Data Protection Platform Capital Funding Pitch Deck PPT Example. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers competitor evaluation for major email security service providers such as email security, hubspot marketing hub and Gmail. It includes comparison on the basis of rating for easy of use, value for money, customer support, etc.


 Continue with Email
Continue with Email

 Home
Home


































