Cyber Security Icons
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF
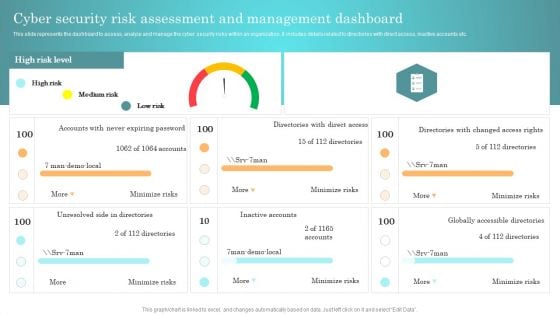
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
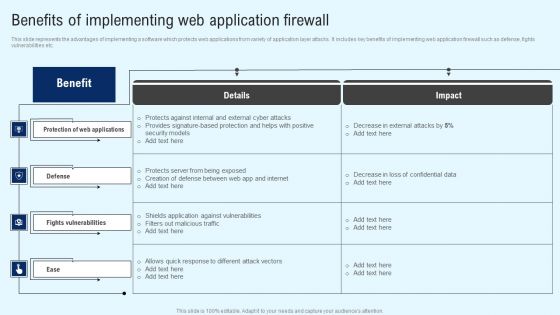
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
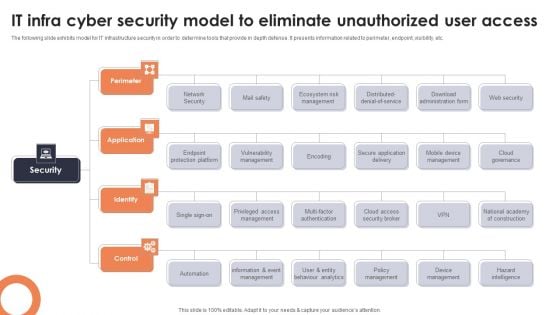
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF
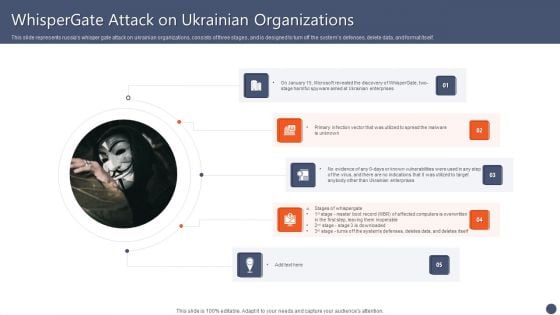
This slide represents russias whisper gate attack on ukrainian organizations, consists of three stages, and is designed to turn off the systems defenses, delete data, and format itself. Are you searching for a Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF from Slidegeeks today.
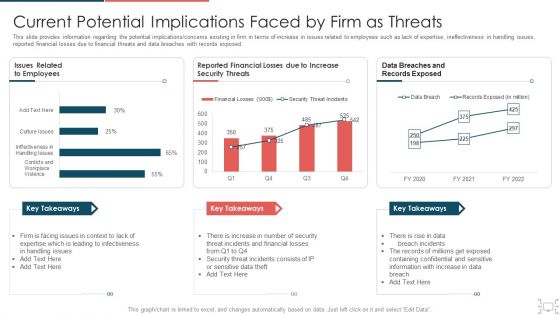
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
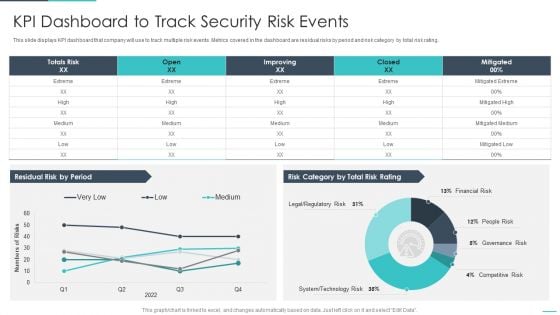
Handling Cyber Threats Digital Era KPI Dashboard To Track Security Risk Events Ppt Inspiration PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era kpi dashboard to track security risk events ppt inspiration pdf. Use them to share invaluable insights on kpi dashboard to track security risk events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
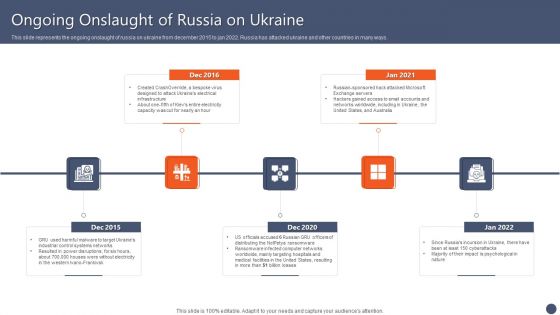
Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF
This slide represents the ongoing onslaught of russia on ukraine from december 2015 to jan 2022. Russia has attacked ukraine and other countries in many ways. If you are looking for a format to display your unique thoughts, then the professionally designed Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.
Develop Corporate Cyber Security Risk Mitigation Plan Timeline For Organization Protection Proposal Themes PDF
This is a develop corporate cyber security risk mitigation plan timeline for organization protection proposal themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2019 to 2022. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
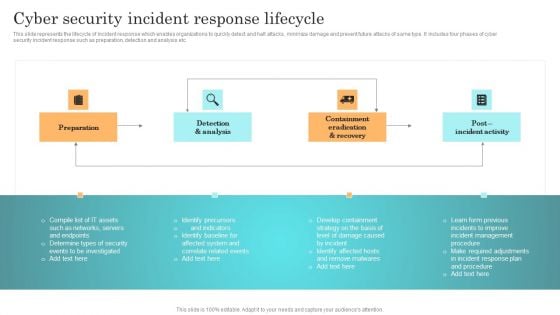
Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
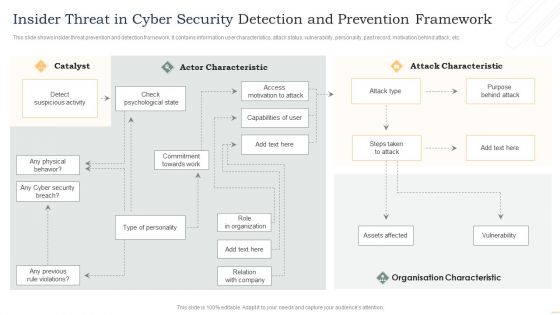
Insider Threat In Cyber Security Detection And Prevention Framework Information PDF
This slide shows insider threat prevention and detection framework. It contains information user characteristics, attack status, vulnerability, personality, past record, motivation behind attack, etc. Presenting Insider Threat In Cyber Security Detection And Prevention Framework Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Actor Characteristic, Attack Characteristic, Organisation Characteristic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
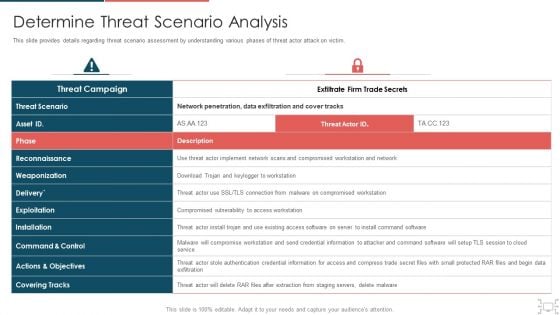
Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
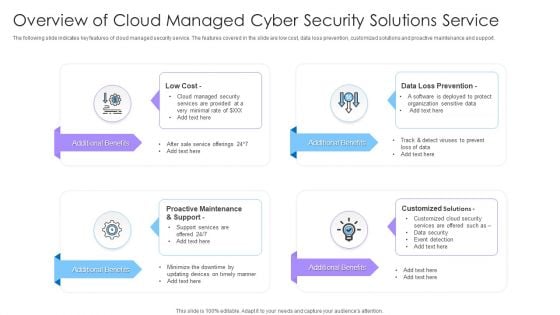
Overview Of Cloud Managed Cyber Security Solutions Service Ppt Portfolio Structure PDF
The following slide indicates key features of cloud managed security service. The features covered in the slide are low cost, data loss prevention, customized solutions and proactive maintenance and support. Presenting Overview Of Cloud Managed Cyber Security Solutions Service Ppt Portfolio Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Low Cost, Customized Solutions, Additional Benefits. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
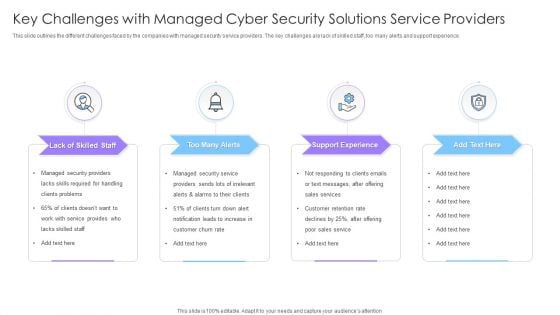
Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF
This slide outlines the different challenges faced by the companies with managed security service providers. The key challenges are lack of skilled staff, too many alerts and support experience. Presenting Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Too Many Alerts, Support Experience, Lack Skilled Staff. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
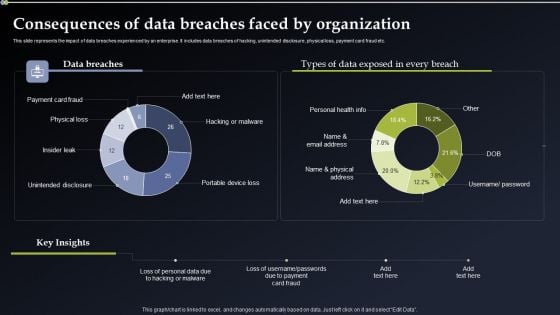
Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
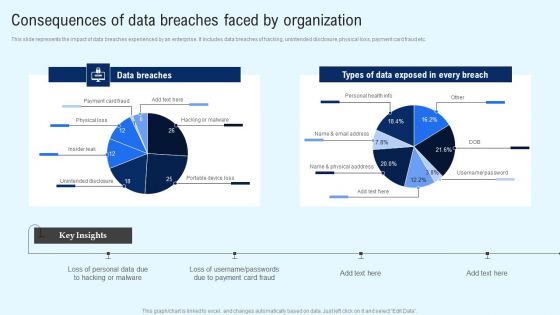
Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
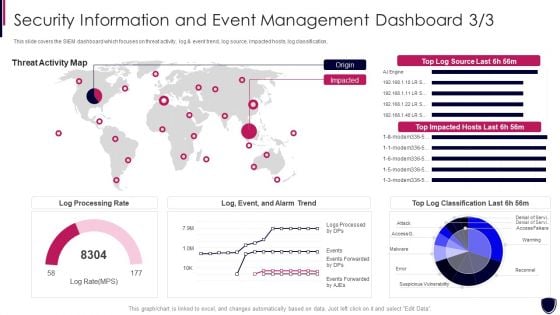
Security Information And Event Enhancing Cyber Safety With Vulnerability Administration Portrait PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event enhancing cyber safety with vulnerability administration portrait pdf bundle. Topics like log processing rate, threat activity map can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
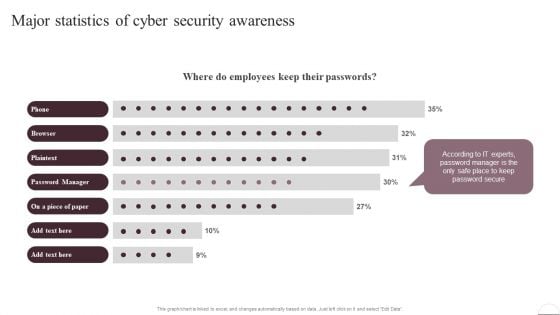
Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. There are so many reasons you need a Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cyber Security Risk Management Plan Addressing The Incidents Logging Process Diagrams PDF
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Deliver an awe inspiring pitch with this creative cyber security risk management plan addressing the incidents logging process diagrams pdf bundle. Topics like process id, procedure, description, responsible person can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
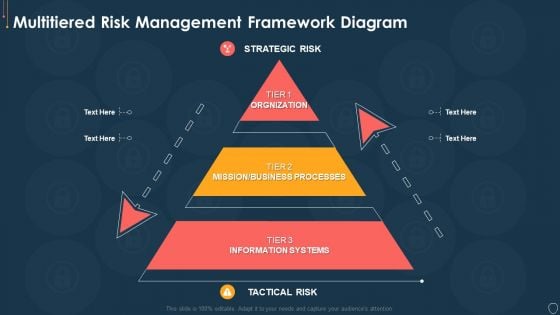
Cyber Security Risk Management Plan Multitiered Risk Management Framework Diagram Inspiration PDF
This is a cyber security risk management plan multitiered risk management framework diagram inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like orgnization, mission or business processes, information systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF
Want to ace your presentation in front of a live audience Our Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
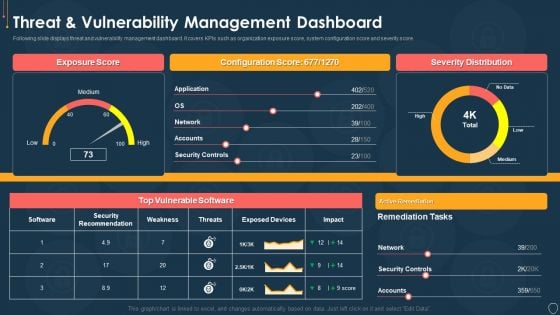
Cyber Security Risk Management Plan Threat And Vulnerability Management Dashboard Portrait PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat and vulnerability management dashboard portrait pdf. Use them to share invaluable insights on exposure score, configuration score, severity distribution, vulnerable software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Security Administration In Organization Financial Performance Tracking Dashboard Microsoft PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization financial performance tracking dashboard microsoft pdf. Use them to share invaluable insights on financial performance tracking dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
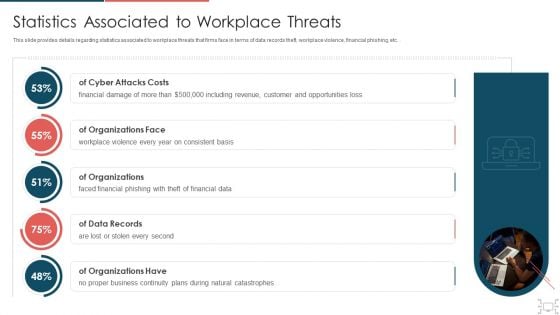
Cyber Security Administration In Organization Statistics Associated To Workplace Threats Microsoft PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc.. Deliver an awe inspiring pitch with this creative cyber security administration in organization statistics associated to workplace threats microsoft pdf bundle. Topics like organizations, consistent, financial, business, catastrophes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
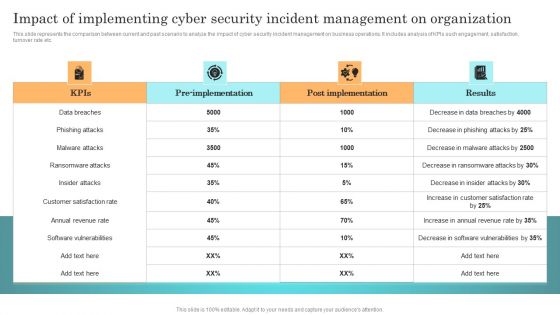
Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
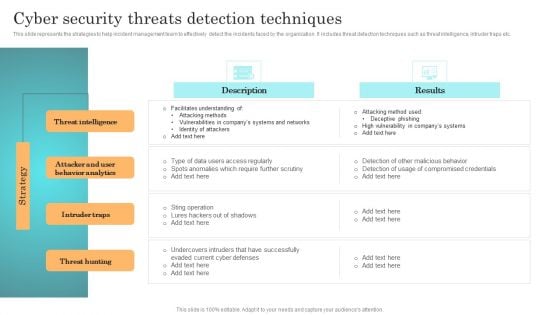
Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.
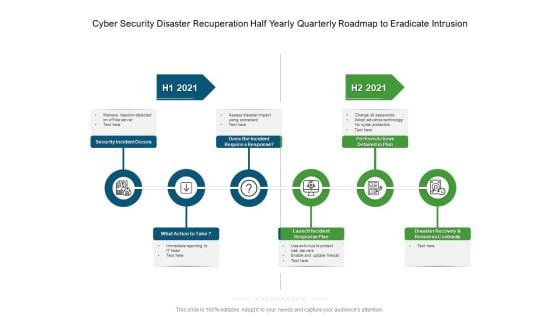
Cyber Security Disaster Recuperation Half Yearly Quarterly Roadmap To Eradicate Intrusion Graphics
Presenting our innovatively-structured cyber security disaster recuperation half yearly quarterly roadmap to eradicate intrusion graphics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
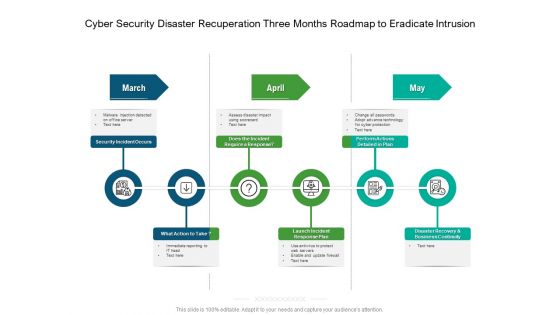
Cyber Security Disaster Recuperation Three Months Roadmap To Eradicate Intrusion Topics
Presenting our jaw-dropping cyber security disaster recuperation three months roadmap to eradicate intrusion topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
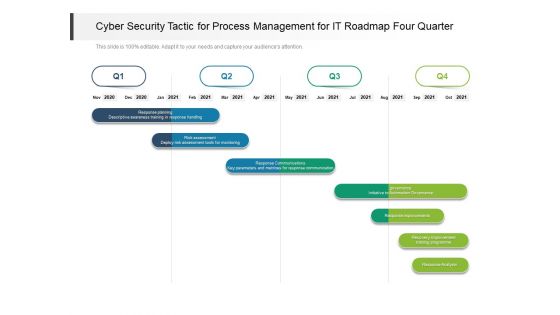
Cyber Security Tactic For Process Management For IT Roadmap Four Quarter Pictures
Presenting our innovatively structured cyber security tactic for process management for it roadmap four quarter pictures Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
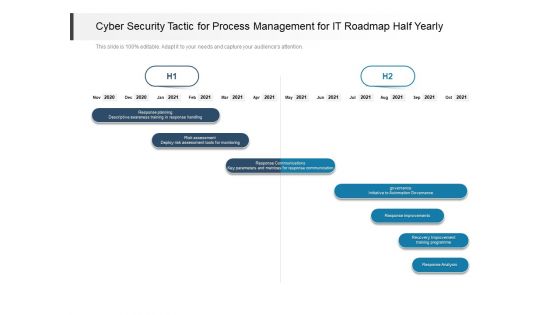
Cyber Security Tactic For Process Management For IT Roadmap Half Yearly Topics
Introducing our cyber security tactic for process management for it roadmap half yearly topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Prevention Of Information Security Awareness Training Program Challenges Icons PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Prevention Of Information Security Awareness Training Program Challenges Icons PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
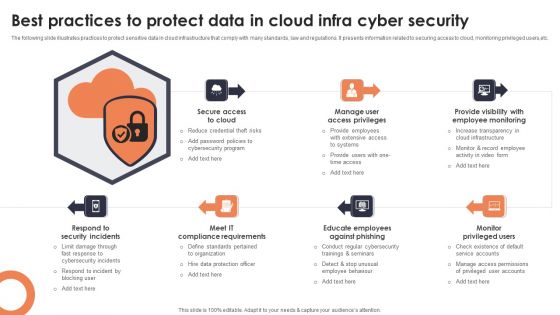
Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF
The following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users,etc. Presenting Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Secure Access Cloud, Manage User Access Privileges, Provide Visibility Employee. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
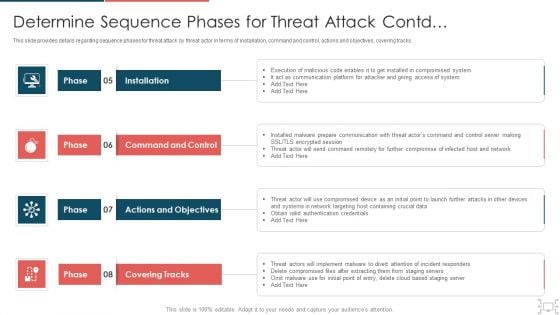
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
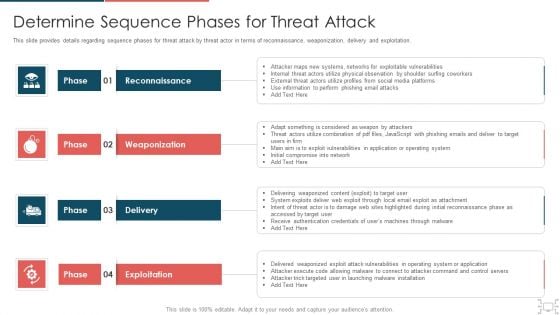
cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
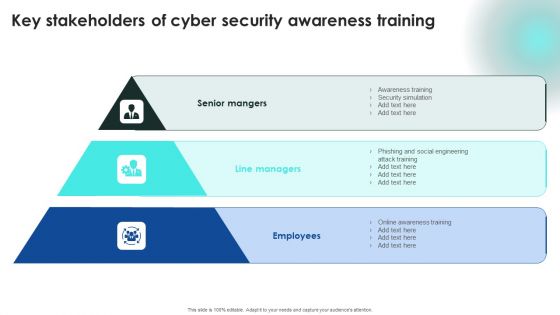
Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
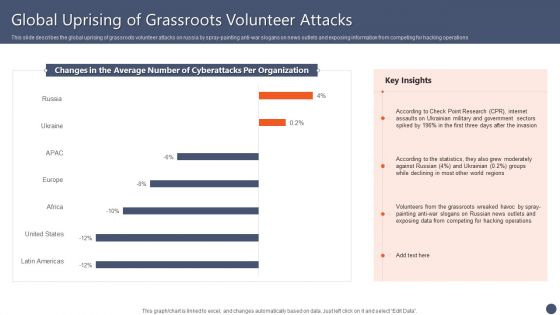
Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF
This slide describes the global uprising of grassroots volunteer attacks on russia by spray-painting anti-war slogans on news outlets and exposing information from competing for hacking operations. Boost your pitch with our creative Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
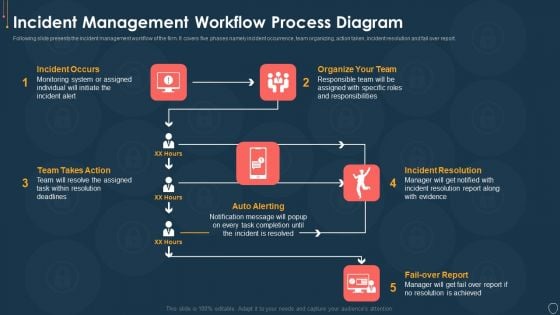
Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
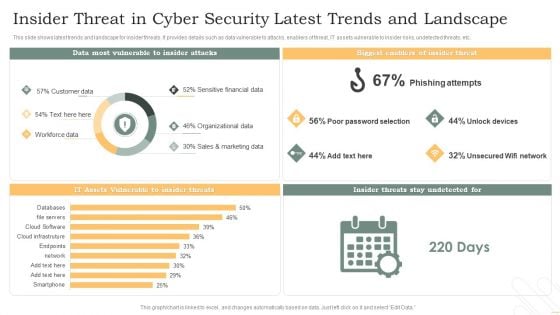
Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF
This slide shows latest trends and landscape for insider threats. It provides details such as data vulnerable to attacks, enablers of threat, IT assets vulnerable to insider risks, undetected threats, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF. The topics addressed in these templates are Phishing Attempts, Unlock Devices, Unsecured Wifi Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
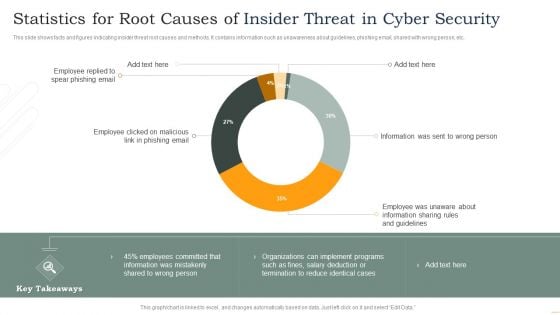
Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
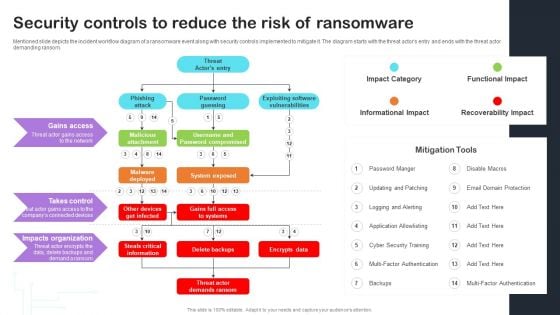
Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Take your projects to the next level with our ultimate collection of Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
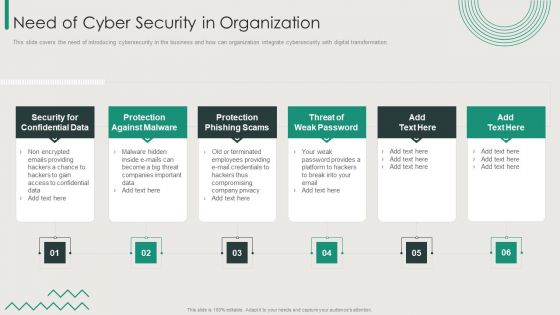
Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF
The following slide showcases various approaches to AI infrastructure which bodes well for future of organizations association. It presents information related to regulatory framework, expert consultations, etc. Presenting Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Regulatory Framework, Protect AI Related Data, Involve Cybersecurity Experts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF
Retrieve professionally designed Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
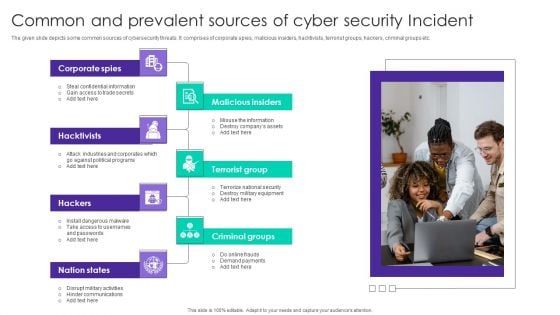
Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
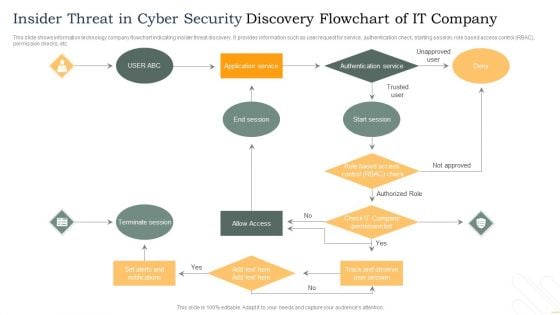
Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
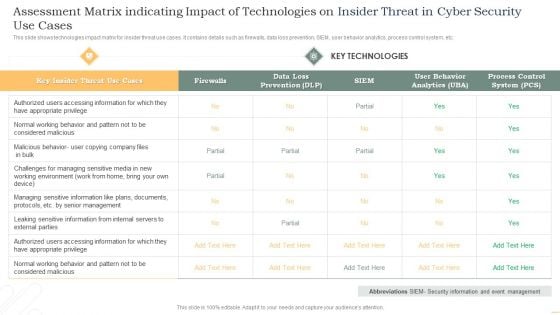
Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
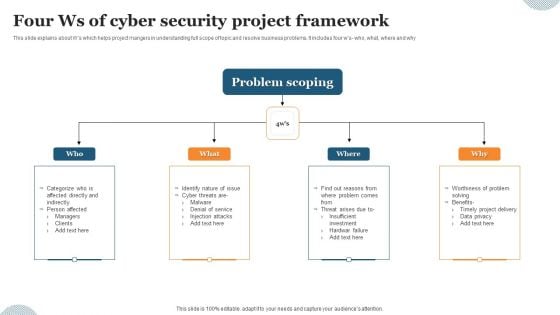
Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF
This slide explains about Ws which helps project mangers in understanding full scope of topic and resolve business problems. It includes four ws- who, what, where and why. Presenting Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Problem Scoping, Denial Service, Injection Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
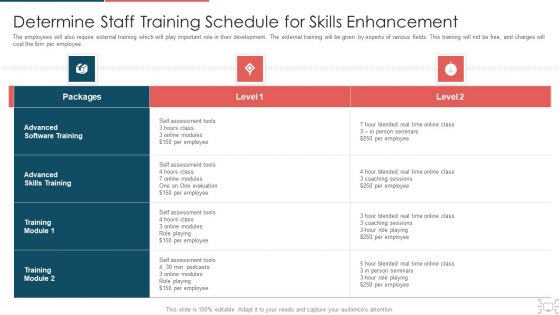
Cyber Security Administration In Organization Determine Staff Training Schedule For Skills Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine staff training schedule for skills diagrams pdf bundle. Topics like determine staff training schedule for skills enhancement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
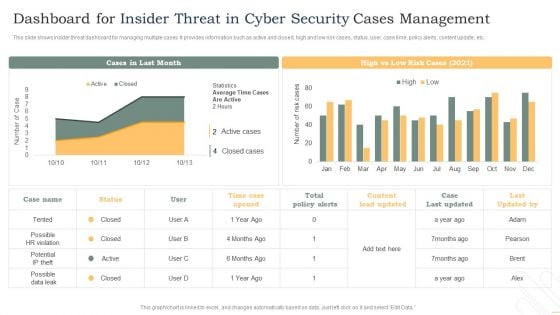
Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
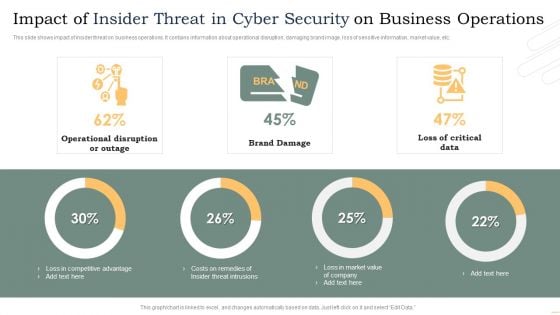
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF
This slide shows user details tracked by insider threat dashboard. It provides information such as exposure events, file activity, archive, document, image, pdf, ppt, scripts, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF. This layout presents information on Private Data, Exposure Events, User Activity, File Activity, Over Time. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
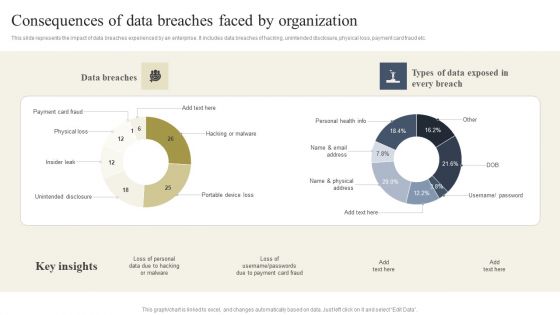
Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Implementing Cyber Security Incident Management Ppt PowerPoint Presentation Complete Deck With Slides
This Implementing Cyber Security Incident Management Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This seventy slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence.
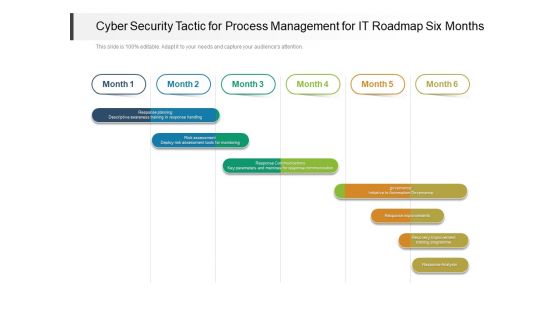
Cyber Security Tactic For Process Management For IT Roadmap Six Months Clipart
Presenting the cyber security tactic for process management for it roadmap six months clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
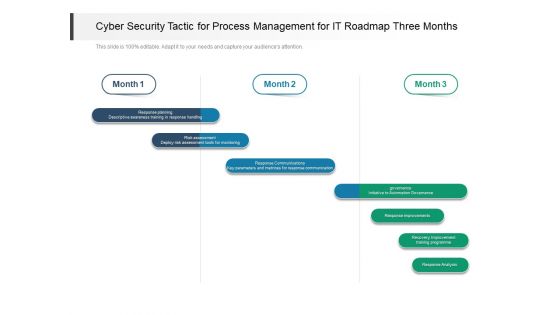
Cyber Security Tactic For Process Management For IT Roadmap Three Months Demonstration
Presenting our jaw dropping cyber security tactic for process management for it roadmap three months demonstration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
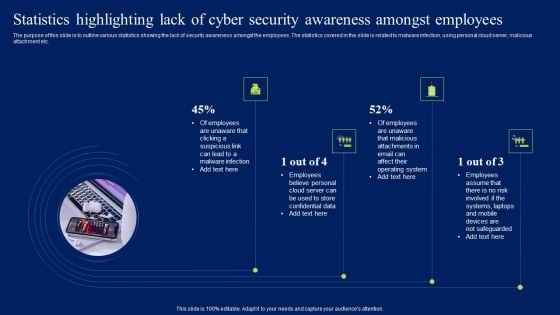
Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Present like a pro with Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
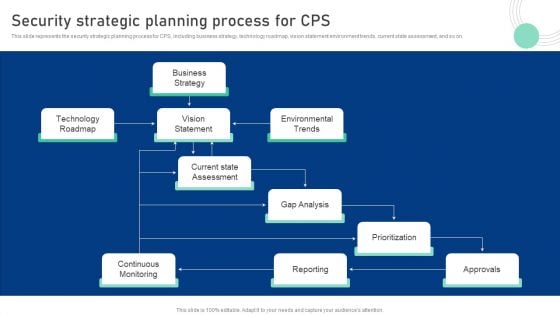
Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Slidegeeks is here to make your presentations a breeze with Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
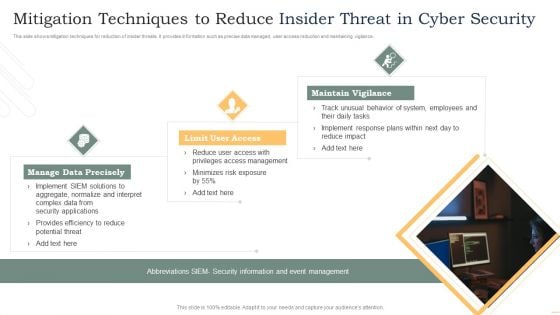
Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides
This Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twenty slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.


 Continue with Email
Continue with Email

 Home
Home


































