Cyber Security Image
Icons Slide For Continuous Development Evaluation Plan To Eliminate Cyber Attacks Structure PDF
Introducing our well designed icons slide for continuous development evaluation plan to eliminate cyber attacks structure pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
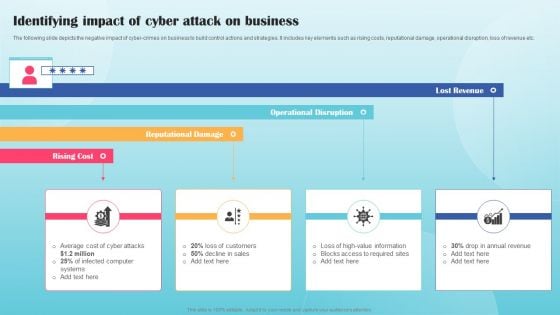
Identifying Impact Of Cyber Attack On Business Ppt PowerPoint Presentation File Infographic Template PDF
The following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Retrieve professionally designed Identifying Impact Of Cyber Attack On Business Ppt PowerPoint Presentation File Infographic Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
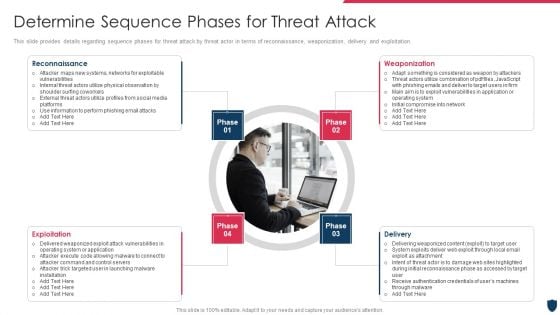
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.This is a IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ransomware Attacks, Cyberthreat Complaints, Trillion Annually. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Five Steps To Prevent Cyber Attacks Ppt PowerPoint Presentation Infographic Template Inspiration
Presenting this set of slides with name five steps to prevent cyber attacks ppt powerpoint presentation infographic template inspiration. This is a five stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Steps To Stay Safe From Cyber Attacks Threat Modelling Ppt PowerPoint Presentation Infographics Gallery
Presenting this set of slides with name steps to stay safe from cyber attacks threat modelling ppt powerpoint presentation infographics gallery. This is a six stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
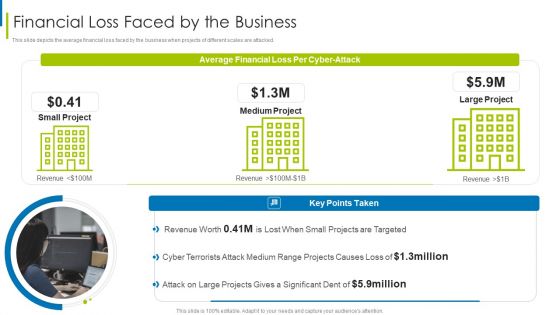
Cyber Terrorism Assault Financial Loss Faced By The Business Summary PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked.This is a cyber terrorism assault financial loss faced by the business summary pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like projects are targeted, cyber terrorists, attack on large You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
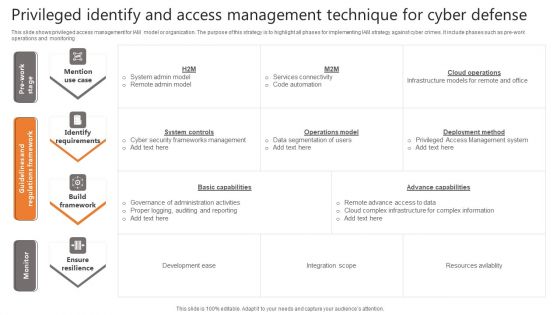
Privileged Identify And Access Management Technique For Cyber Defense Infographics PDF
This slide shows privileged access management for IAM model or organization. The purpose of this strategy is to highlight all phases for implementing IAM strategy against cyber crimes. It include phases such as pre work operations and monitoring Pitch your topic with ease and precision using this Privileged Identify And Access Management Technique For Cyber Defense Infographics PDF. This layout presents information on Identify Requirements, Build Framework, Ensure Resilience. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Chatgpt Incorporation Into Web Apps How Chatgpt Can Help In Preventing Cyber Crimes Clipart PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Boost your pitch with our creative Chatgpt Incorporation Into Web Apps How Chatgpt Can Help In Preventing Cyber Crimes Clipart PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF
Find highly impressive Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF for your upcoming presentation. All the presentation templates are 100precent editable and you can change the color and personalize the content accordingly. Download now.

Table Of Contents Enhancing Cyber Safety With Vulnerability Administration Portrait PDF
Presenting table of contents enhancing cyber safety with vulnerability administration portrait pdf to provide visual cues and insights. Share and navigate important information on eleven stages that need your due attention. This template can be used to pitch topics like company overview, challenges and solutions, services offered, features and benefits, siem architecture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
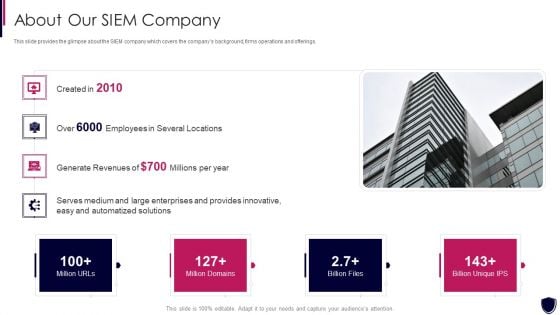
Enhancing Cyber Safety With Vulnerability Administration About Our SIEM Company Summary PDF
This slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. Presenting enhancing cyber safety with vulnerability administration about our siem company summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like about our siem company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Enhancing Cyber Safety With Vulnerability Administration Log Management Services Metrics Icons PDF
Presenting enhancing cyber safety with vulnerability administration log management services metrics icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like logfiles, configurations, messages, metrics, scripts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF
The following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti-virus, preventing to open suspicious emails, keeping systems up-to date etc. Find highly impressive Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
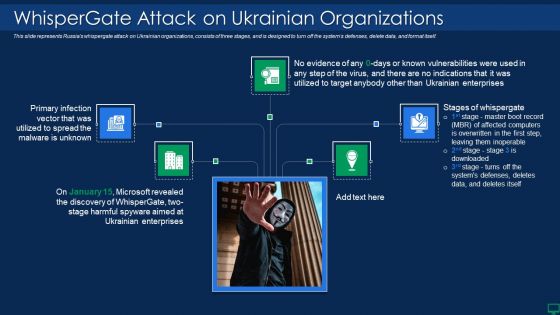
Russian Cyber Attacks On Ukraine IT Whispergate Attack On Ukrainian Microsoft PDF
This is a russian cyber attacks on ukraine it whispergate attack on ukrainian microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like target, enterprises. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
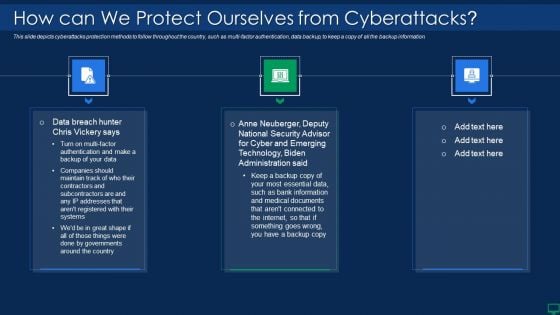
Russian Cyber Attacks On Ukraine IT How Can We Protect Ourselves Rules PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. This is a russian cyber attacks on ukraine it how can we protect ourselves rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internet, documents, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
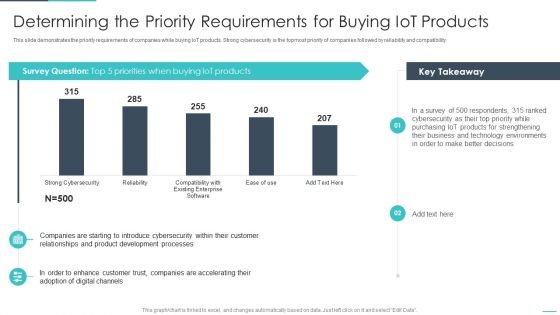
Handling Cyber Threats Digital Era Determining The Priority Requirements Ppt Outline Visual Aids PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative handling cyber threats digital era determining the priority requirements ppt outline visual aids pdf bundle. Topics like determining the priority requirements for buying iot products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
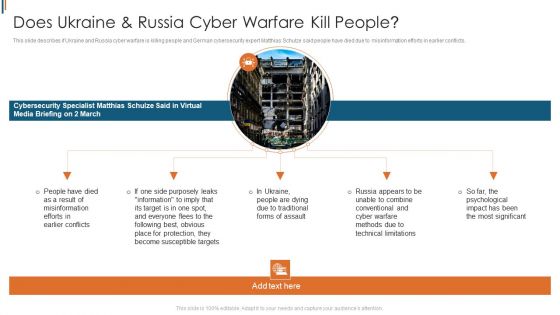
Ukraine Cyberwarfare Does Ukraine Russia Cyber Warfare Kill People Summary Pdf
This slide describes if Ukraine and Russia cyber warfare is killing people and German cybersecurity expert Matthias Schulze said people have died due to misinformation efforts in earlier conflicts. This is a ukraine cyberwarfare does ukraine russia cyber warfare kill people summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people have died as a result of misinformation efforts in earlier conflicts, in ukraine, people are dying due to traditional forms of assault, russia appears to be unable to combine conventional and cyber warfare methods due to technical limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault How To Protect Company From Trojan Attacks Demonstration PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a cyber terrorism assault how to protect company from trojan attacks demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device conventional, next generation antivirus, prevent trojan infection You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Metrics To Manage Cyber Risk With Application Control Ppt PowerPoint Presentation Pictures Slide PDF
This slide covers cyber risk measure dashboard. It also includes application control, patch application, patch operating system, restrict admin privileges, disable untrusted Microsoft office macros, user application hardening, multi factor authentication and daily backup of important data. Pitch your topic with ease and precision using this key metrics to manage cyber risk with application control ppt powerpoint presentation pictures slide pdf. This layout presents information on disable untrusted microsoft office macros, application control, patch operating systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Ukraine Cyberwarfare Cyber Attacks On Ukraine Are Conspicuous By Their Absence Topics Pdf
This slide represents the conspicuous Russian cyber attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. This is a ukraine cyberwarfare cyber attacks on ukraine are conspicuous by their absence topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like government and bank websites of ukraine were momentarily taken offline, team of anti war belarusian hackers claimed that the conflict had affected the countrys railways computer networks, hackers aided by ukraine launched distributed denial of service operations to take down russian websites. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
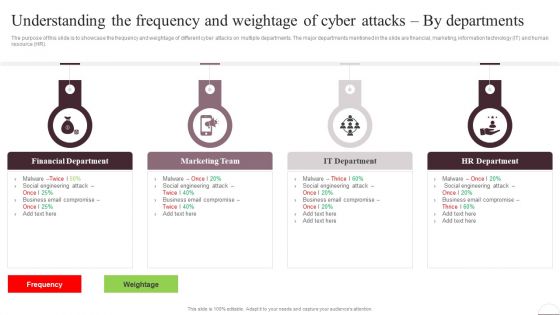
Prevention Of Information Understanding The Frequency And Weightage Of Cyber Attacks Professional PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Present like a pro with Prevention Of Information Understanding The Frequency And Weightage Of Cyber Attacks Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases the various types of cyber-attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Present like a pro with Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
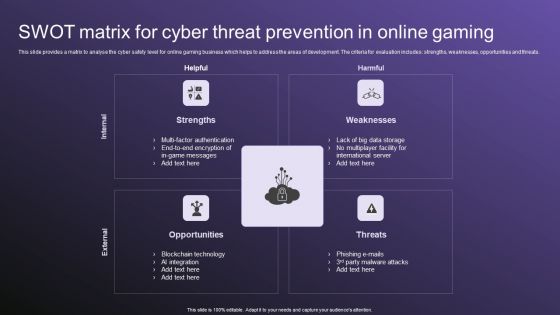
SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF
This slide provides a matrix to analyse the cyber safety level for online gaming business which helps to address the areas of development. The criteria for evaluation includes strengths, weaknesses, opportunities and threats. Persuade your audience using this SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
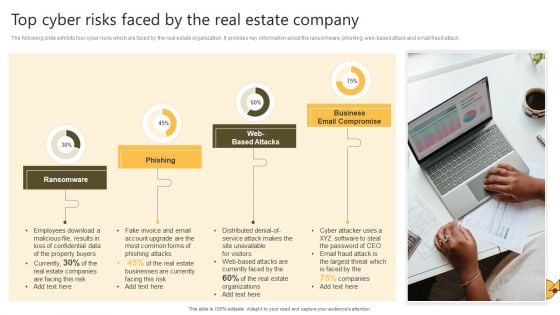
Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. The Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Table Of Contents For Russian Cyber Attacks On Ukraineteam Mockup PDF
This is a table of contents for russian cyber attacks on ukraineteam mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, technology, potential, accounts, team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
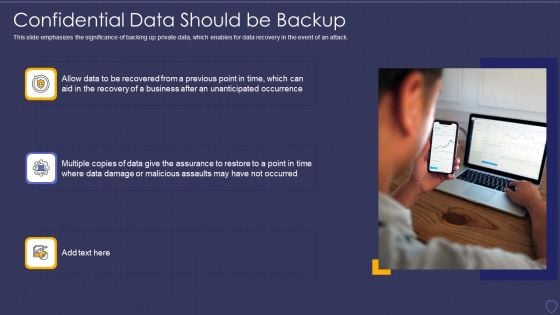
Global Cyber Terrorism Incidents On The Rise IT Confidential Data Should Be Backup Structure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack. Presenting global cyber terrorism incidents on the rise it confidential data should be backup structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like confidential data should be backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Evaluating Financial Practices In Firm Graphics PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver and pitch your topic in the best possible manner with this cyber safety incident management evaluating financial practices in firm graphics pdf. Use them to share invaluable insights on evaluating financial practices in firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
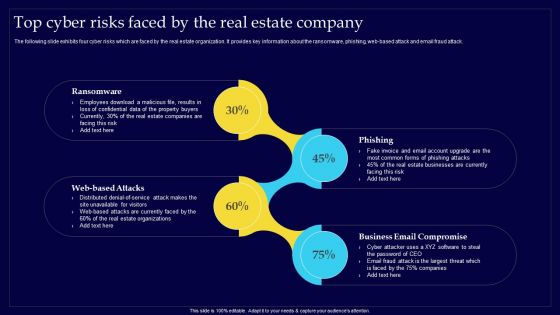
Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Retrieve professionally designed Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Top Cyber Risks Faced By The Real Estate Company Enhancing Process Improvement By Regularly Information PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Top Cyber Risks Faced By The Real Estate Company Enhancing Process Improvement By Regularly Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
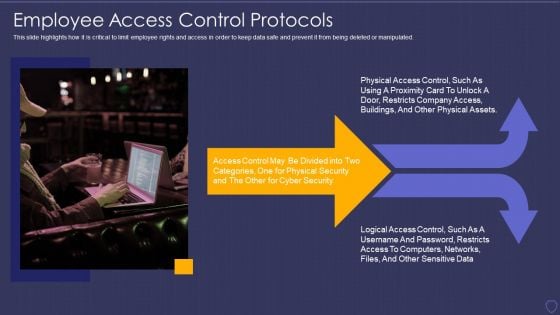
Global Cyber Terrorism Incidents On The Rise IT Employee Access Control Protocols Download PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Presenting global cyber terrorism incidents on the rise it employee access control protocols download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like employee access control protocols. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Impact On Organization After Implementing Computer Security Strategy And Training Ideas PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. This is a impact on organization after implementing computer security strategy and training ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network intrusion, system misconfiguration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Preventing Measures For Social Media Accounts Themes PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies. Presenting cyber exploitation it preventing measures for social media accounts themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like social media policies, anti malware software, social media login credentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
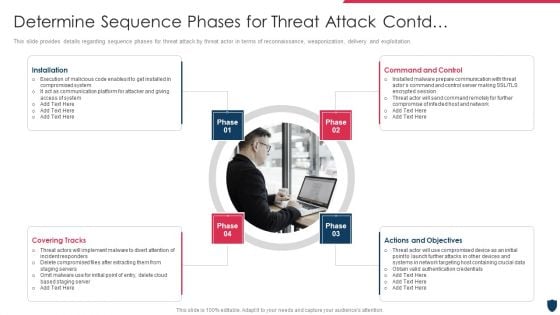
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration What Our Clients Say About Us Pictures PDF
This slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation. Presenting enhancing cyber safety with vulnerability administration what our clients say about us pictures pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like what our clients say about us. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
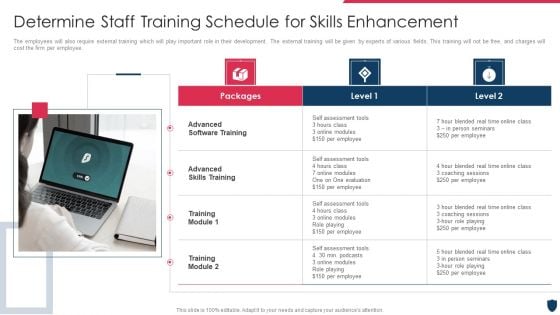
Cyber Safety Incident Management Determine Staff Training Schedule For Skills Enhancement Ideas PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting cyber safety incident management determine staff training schedule for skills enhancement ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advanced software training, advanced skills training, training module . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
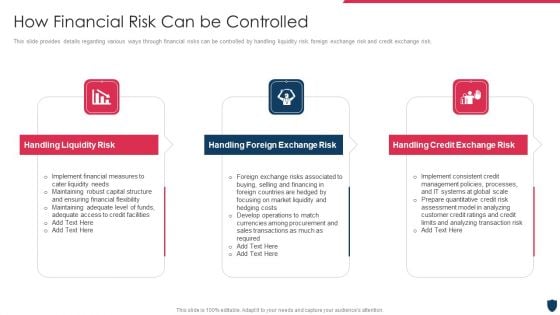
Cyber Safety Incident Management How Financial Risk Can Be Controlled Formats PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting cyber safety incident management how financial risk can be controlled formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Incident Reporting By Different Departments Brochure PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting cyber safety incident management incident reporting by different departments brochure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enhancing Cyber Safety With Vulnerability Administration Log Management Services Structure PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Presenting enhancing cyber safety with vulnerability administration log management services structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like collection and normalization, search speed, real time analysis, decision making process, log data filtering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
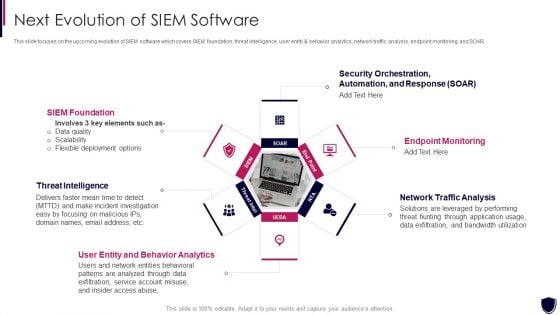
Enhancing Cyber Safety With Vulnerability Administration Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting enhancing cyber safety with vulnerability administration next evolution of siem software sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like endpoint monitoring, network traffic analysis, user entity and behavior analytics, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
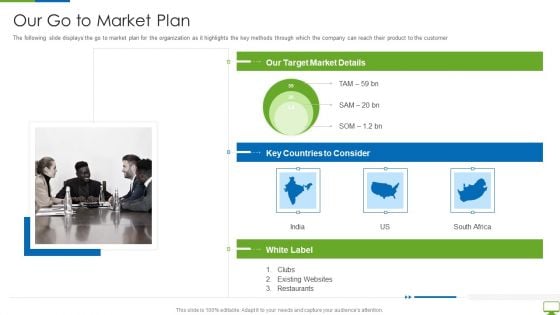
Cyber Network Simulation Platform Capital Funding Pitch Deck Our Go To Market Plan Slides PDF
The following slide displays the go to market plan for the organization as it highlights the key methods through which the company can reach their product to the customer Presenting cyber network simulation platform capital funding pitch deck our go to market plan slides pdf to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like our go to market plan In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Russian Cyber Attacks On Ukraine IT Impact Of Defacement Attacks Portrait PDF
This slide shows the impact of defacement attacks and fake news on the public, and Meta has banned Russian media on its platforms, and Russia has restricted access to Facebook. This is a russian cyber attacks on ukraine it impact of defacement attacks portrait pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, fundamental, method, material, social media. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
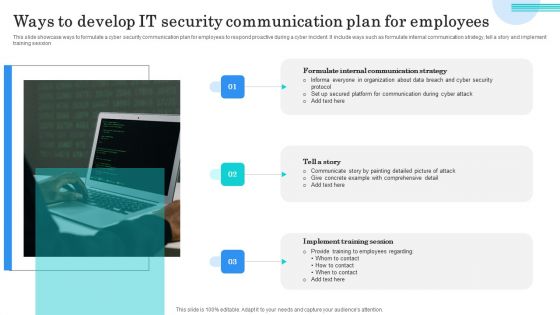
Ways To Develop IT Security Communication Plan For Employees Elements PDF
This slide showcase ways to formulate a cyber security communication plan for employees to respond proactive during a cyber incident. It include ways such as formulate internal communication strategy, tell a story and implement training session. Presenting Ways To Develop IT Security Communication Plan For Employees Elements PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Formulate Internal Communication, Tell Story, Implement Training Session. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Russian Cyber Attacks On Ukraine IT Ongoing Onslaught Of Russia Structure PDF
This slide represents the ongoing onslaught of Russia on Ukraine from December 2015 to Jan 2022. Russia has attacked Ukraine and other countries in many ways. This is a russian cyber attacks on ukraine it ongoing onslaught of russia structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, industrial, networks, email. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
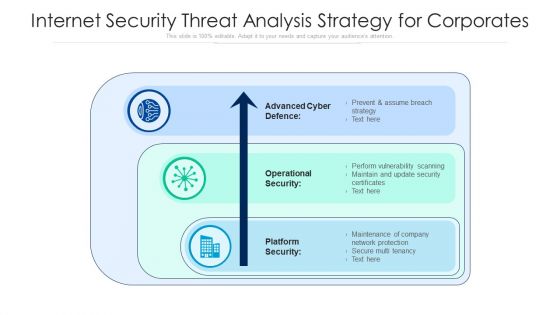
Internet Security Threat Analysis Strategy For Corporates Ppt PowerPoint Presentation File Picture PDF
Pitch your topic with ease and precision using this internet security threat analysis strategy for corporates ppt powerpoint presentation file picture pdf. This layout presents information on advanced cyber defence, operational security, platform security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Terrorism Assault Types Of Ddos Attacks In The Company Sample PDF
This slide demonstrates the types of DDoS attacks happening in the company, which include volume-based attacks, protocol-based attacks, and application layer attacks. This is a cyber terrorism assault types of ddos attacks in the company sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like volume based attacks, protocol based attacks, application layer attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
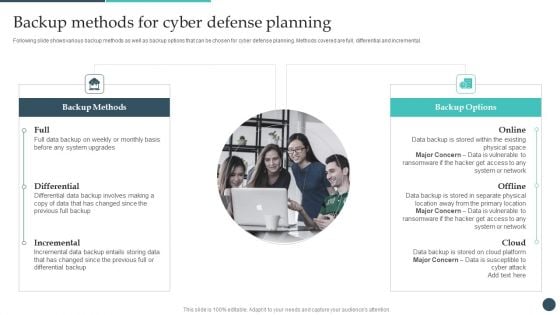
Safety Breach Response Playbook Backup Methods For Cyber Defense Planning Demonstration PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental. Welcome to our selection of the Safety Breach Response Playbook Backup Methods For Cyber Defense Planning Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
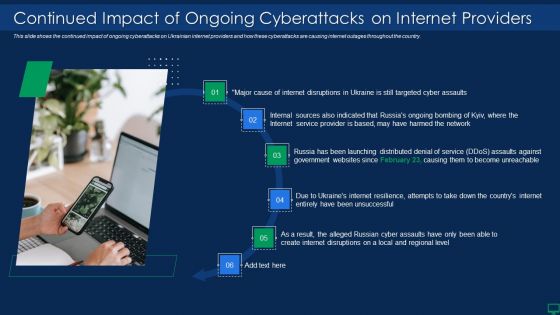
Russian Cyber Attacks On Ukraine IT Continued Impact Of Ongoing Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. This is a russian cyber attacks on ukraine it continued impact of ongoing microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sources, service, network, internet. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
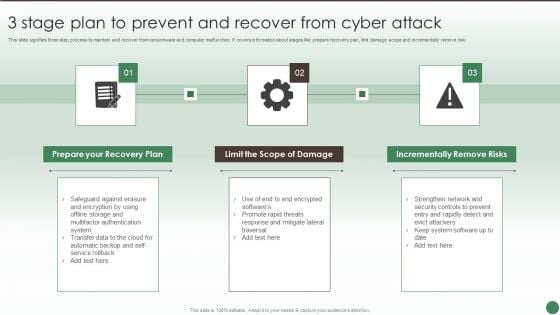
3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF
This slide signifies three step process to maintain and recover from ransomware and computer malfunction. It covers information about stages like prepare recovery plan, limit damage scope and incrementally remove risk. Persuade your audience using this 3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Recovery Plan, Limit Scope Damage, Incrementally Remove Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Enhancing Cyber Safety With Vulnerability Administration Need For SIEM Software In Your Company Graphics PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. This is a enhancing cyber safety with vulnerability administration need for siem software in your company graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like detecting incidents, compliance with regulation, efficient incident management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Continuous Development Evaluation Plan To Eliminate Cyber Attacks Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This continuous development evaluation plan to eliminate cyber attacks ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of forty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Enhancing Cyber Safety With Vulnerability Administration How SIEM Works Summary PDF
This is a enhancing cyber safety with vulnerability administration how siem works summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like correlation, behavior analytics, normalization, taxonomy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Cyber Terrorism Incidents On The Rise IT Financial Loss Faced By The Business Designs PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked. This is a global cyber terrorism incidents on the rise it financial loss faced by the business designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, revenue, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Enhancing Cyber Safety With Vulnerability Administration Our Management Team Information PDF
This slide covers the details of the management team along with their job profile and brief description about their work. This is a enhancing cyber safety with vulnerability administration our management team information pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our management team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
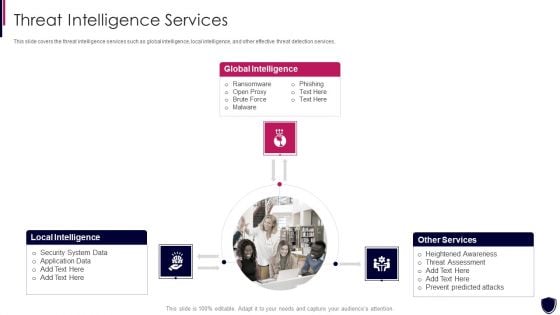
Enhancing Cyber Safety With Vulnerability Administration Threat Intelligence Services Information PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. This is a enhancing cyber safety with vulnerability administration threat intelligence services information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global intelligence, local intelligence, other services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Determine Threat Management Team Structure Professional PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a cyber safety incident management determine threat management team structure professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Different Kinds Of Insider Digital Threats Download PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber safety incident management different kinds of insider digital threats download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malicious insider, negligent or careless insider, third party insider. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
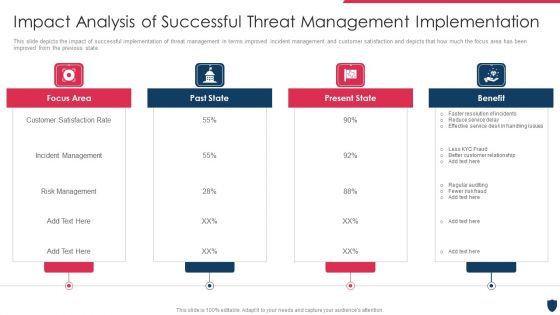
Cyber Safety Incident Management Impact Analysis Of Successful Threat Management Implementation Summary PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. This is a cyber safety incident management impact analysis of successful threat management implementation summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like focus area, past state, present state, benefit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Various Types Of Workplace Violence And Threats Infographics PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber safety incident management various types of workplace violence and threats infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stalking, physical assault, harassment or intimidation, property damage, weapon assault . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































