Cyber Security Operations

IT Communication Infrastructure Services Download PDF
The following slide demonstrates information and communication technology infrastructure services for optimizing output, mitigate internal and external security threat. It includes components such as operations and network management etc. Persuade your audience using this IT Communication Infrastructure Services Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Applications, Description, Operations Management . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Cost Management Model Components Clipart PDF
This slide shows cloud cost optimization components to make coordination between complex operations of cloud system. It include elements like orchestration, cloud network security and compliance setup etc. Presenting Cloud Cost Management Model Components Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Orchestration Automation, Cloud Network Security, Compliance Governance Setup. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
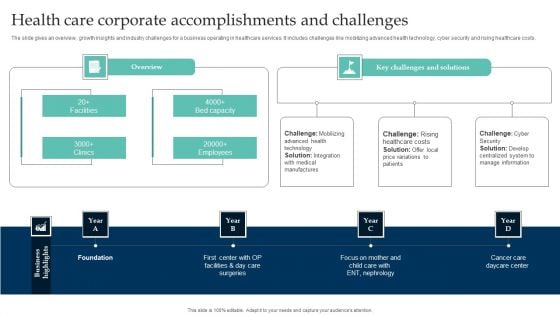
Health Care Corporate Accomplishments And Challenges Professional PDF
The slide gives an overview, growth insights and industry challenges for a business operating in healthcare services. It includes challenges like mobilizing advanced health technology, cyber security and rising healthcare costs. Persuade your audience using this Health Care Corporate Accomplishments And Challenges Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Employees, Healthcare Costs, Price. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Electronic Playbook Digital Transformation Trends We Can Adopt Microsoft PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyperautomation, cyber security tools, usage of AI etc.Presenting electronic playbook digital transformation trends we can adopt microsoft pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like digital transformation trends we can adopt In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Ukraine Cyberwarfare Demonstration Pdf
Presenting table of contents for ukraine cyberwarfare demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like steps to mitigate russian cyber attacks, are there international laws establishing cyber policies, weaknesses of russian cyber cell. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
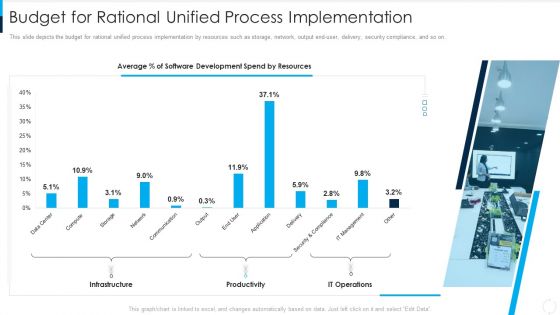
RUP Model Budget For Rational Unified Process Implementation Ppt Outline Layout PDF
This slide depicts the budget for rational unified process implementation by resources such as storage, network, output end-user, delivery, security compliance, and so on. Deliver an awe inspiring pitch with this creative rup model budget for rational unified process implementation ppt outline layout pdf bundle. Topics like infrastructure, productivity, it operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
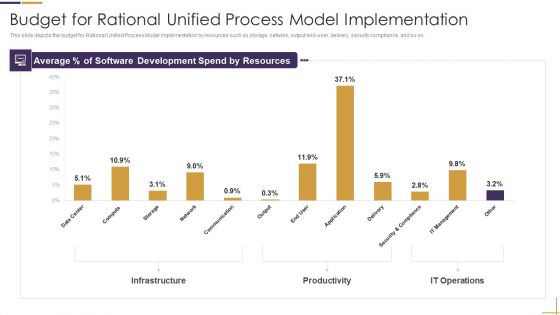
RUP Model Budget For Rational Unified Process Model Implementation Ppt Styles Inspiration PDF
This slide depicts the budget for Rational Unified Process Model implementation by resources such as storage, network, output end-user, delivery, security compliance, and so on. Deliver an awe inspiring pitch with this creative rup model budget for rational unified process model implementation ppt styles inspiration pdf bundle. Topics like infrastructure, productivity, it operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
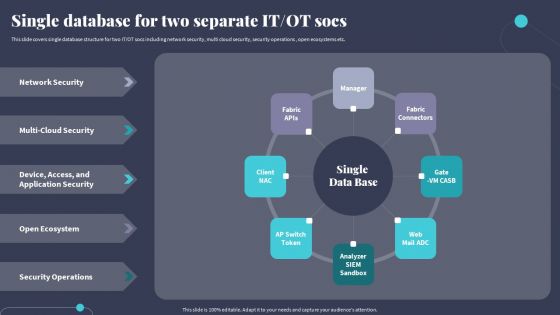
Tactics For Incorporating OT And IT With The Latest PI System Single Database For Two Separate It Ot Socs Template PDF
This slide covers single database structure for two IT OT socs including network security, multi cloud security, security operations , open ecosystems etc. Retrieve professionally designed Tactics For Incorporating OT And IT With The Latest PI System Single Database For Two Separate It Ot Socs Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Slidegeeks is here to make your presentations a breeze with Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

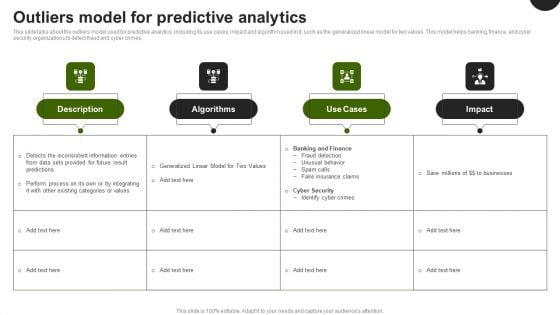
Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF can be your best option for delivering a presentation. Represent everything in detail using Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
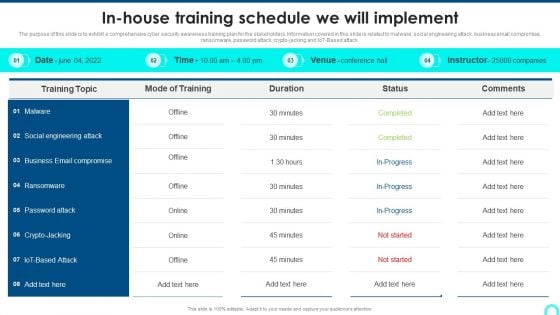
In House Training Schedule We Will Implement Icons PDF
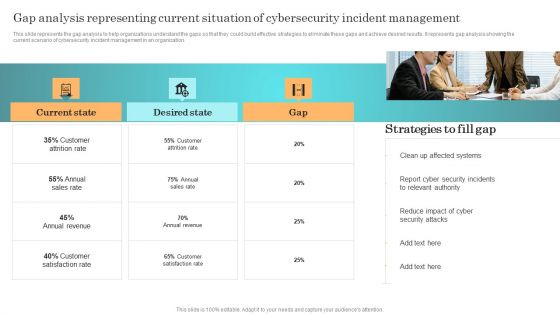
Incident Response Techniques Deployement Gap Analysis Representing Current Situation Of Cybersecurity Designs PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. There are so many reasons you need a Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Prevention Of Information In House Training Schedule We Will Implement Professional PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Prevention Of Information In House Training Schedule We Will Implement Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Key Statistics Ppt PowerPoint Presentation Professional Master Slide
This is a key statistics ppt powerpoint presentation professional master slide. This is a four stage process. The stages in this process are users dont protect their devices, cyber attacks are unnoticed, devices are vulnerable to security.
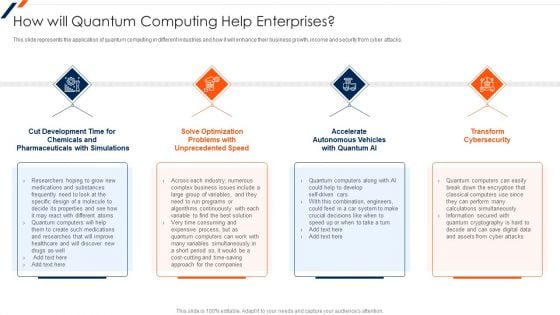
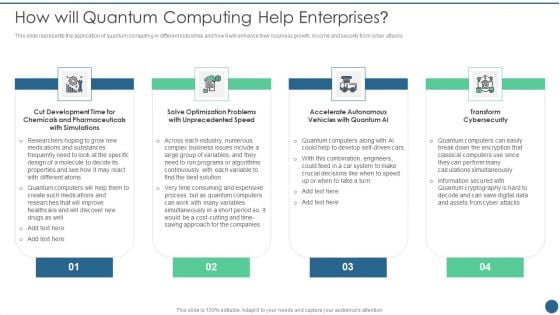
How Will Quantum Computing Help Enterprises Ppt Gallery Ideas PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. This is a How Will Quantum Computing Help Enterprises Ppt Gallery Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Time, Optimization Problems, Transform Cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. Presenting How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Transform Cybersecurity, Complex Business, Accelerate Autonomous Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Quantum Key Distribution How Will Quantum Computing Help Enterprises Portrait PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks.This is a Quantum Key Distribution How Will Quantum Computing Help Enterprises Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Optimization Problems, Accelerate Autonomous, Vehicles Quantum You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
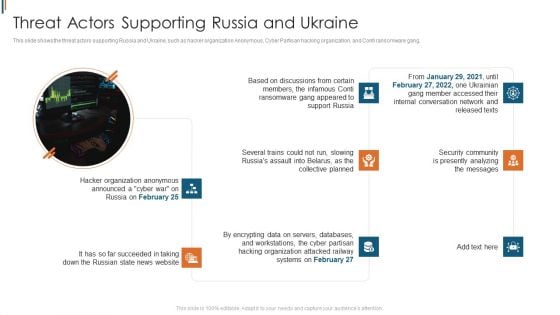
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF
This slide illustrates the incidents of the transition project. It covers the details such as explanation, status, priority, and resolution of the incident to ensure that technological change is successfully completed in the organization. Deliver and pitch your topic in the best possible manner with this Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF. Use them to share invaluable insights on Incident Status Priority, Cyber Attack Sensitive, Added Data Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
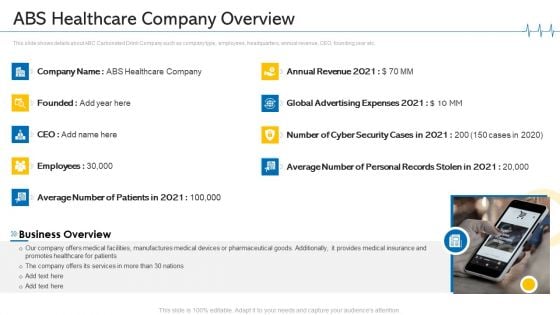
Minimize Cloud Risks Medical Care Business Case Competition ABS Healthcare Company Overview Introduction PDF
This slide shows details about ABC Carbonated Drink Company such as company type, employees, headquarters, annual revenue, CEO, founding year etc. This is a minimize cloud risks medical care business case competition ABS healthcare company overview introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business overview, annual revenue, cyber security cases, manufactures, global advertising expenses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
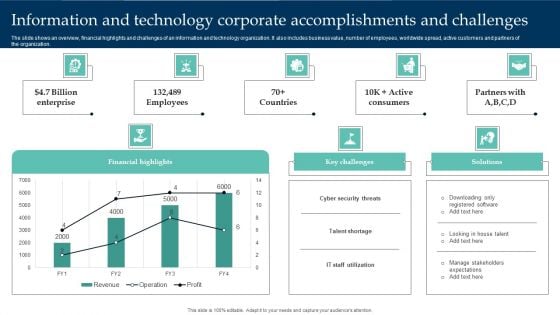
Information And Technology Corporate Accomplishments And Challenges Structure PDF
The slide shows an overview, financial highlights and challenges of an information and technology organization. It also includes business value, number of employees, worldwide spread, active customers and partners of the organization. Pitch your topic with ease and precision using this Information And Technology Corporate Accomplishments And Challenges Structure PDF. This layout presents information on Financial Highlights, Cyber Security Threats, Enterprise. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
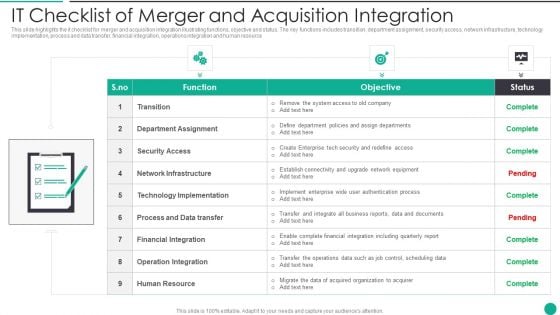
IT Checklist Of Merger And Acquisition Integration Designs PDF
This slide highlights the it checklist for merger and acquisition integration illustrating functions, objective and status. The key functions includes transition, department assignment, security access, network infrastructure, technology implementation, process and data transfer, financial integration, operations integration and human resource Presenting IT Checklist Of Merger And Acquisition Integration Designs PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Department Assignment, Financial Integration, Operation Integration This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
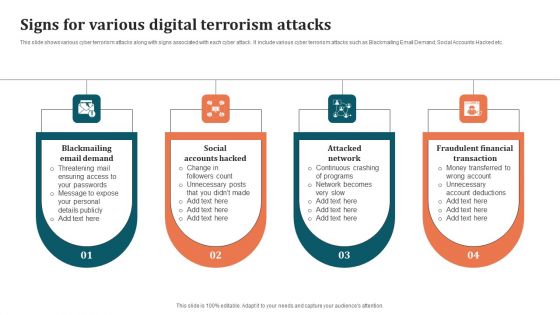
Signs For Various Digital Terrorism Attacks Brochure PDF
This slide shows various cyber terrorism attacks along with signs associated with each cyber attack. It include various cyber terrorism attacks such as Blackmailing Email Demand, Social Accounts Hacked etc. Presenting Signs For Various Digital Terrorism Attacks Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Attacked Network, Fraudulent Financial Transaction, Social Accounts Hacked. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
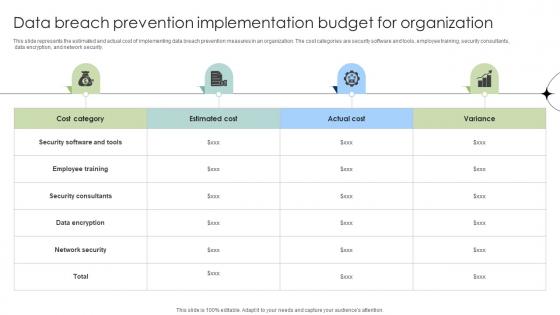
Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.

Data Breach Awareness Training Program Data Breach Prevention Professional Pdf
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs. Find highly impressive Data Breach Awareness Training Program Data Breach Prevention Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Breach Prevention Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Data Breach Awareness Training Program Data Fortification Strengthening Defenses
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.Find highly impressive Data Breach Awareness Training Program Data Fortification Strengthening Defenses on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Fortification Strengthening Defenses for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF
This slide covers various courses for employees to aware about IT security threats. It includes identification of compliance stands, audit standards, incident trends, organisations security awareness, etc.Showcasing this set of slides titled Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF. The topics addressed in these templates are Compliance Standards, Identify Audit Standards, Security Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
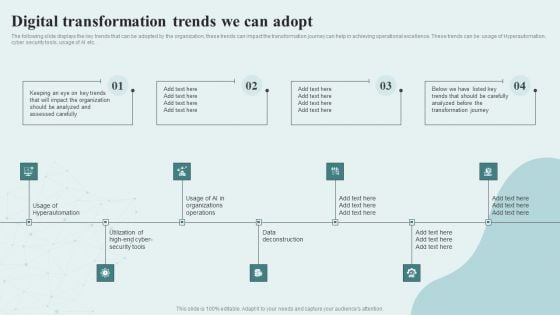
Digital Competency Evaluation And Modification Digital Transformation Trends We Can Adopt Themes PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyperautomation, cyber security tools, usage of AI etc. Want to ace your presentation in front of a live audience Our Digital Competency Evaluation And Modification Digital Transformation Trends We Can Adopt Themes PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Best Practices For Online Risk Management Graphics PDF
The purpose of this slide is to represent digital risk areas and solutions for effective risk management. It includes various risks such as mitigating cyber risk attack, managing third party, handling dynamic workforce, securing cloud migration etc. Presenting Best Practices For Online Risk Management Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigating Cyber Risk Attack, Managing Third Party, Handling Dynamic Workforce. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents Data Wiper Spyware Attack Microsoft PDF
Presenting table of contents data wiper spyware attack microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cyber attacks on ukraine, reasons behind ukraine, russian cyber warfare In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Trends In Business Management Template Ppt Design
This is a trends in business management template ppt design. This is a three stage process. The stages in this process are business strategy focus on growth, corporate strategy, preventing cyber attacks.
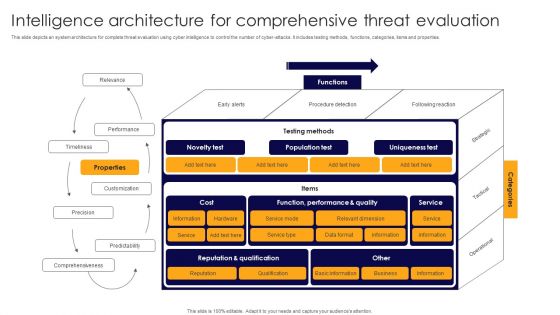
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Evolving BI Infrastructure Tracking Intelligence Infrastructure Activities Dashboard Demonstration PDF
This slide portrays information regarding tracking essential activities in intelligence infrastructure dashboard in terms of IT operations, security, business analytics, internet of things, etc. Deliver an awe inspiring pitch with this creative evolving bi infrastructure tracking intelligence infrastructure activities dashboard demonstration pdf bundle. Topics like application delivery, business analytics, internet of things, it operations, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
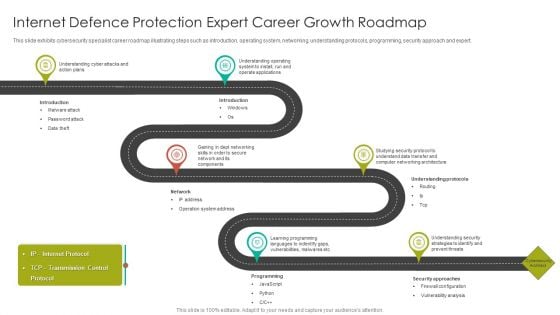
Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cybersecurity Awareness Program To Prevent Attacks Assessment Test To Measure Brochure PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Assessment Test To Measure Brochure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
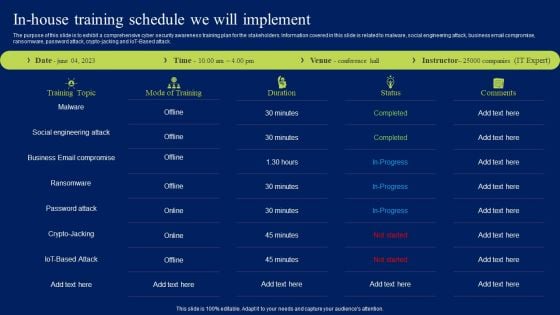
In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Prevention Of Information Assessment Test To Measure Effectiveness Of Training Plan Inspiration PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Create an editable Prevention Of Information Assessment Test To Measure Effectiveness Of Training Plan Inspiration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Prevention Of Information Assessment Test To Measure Effectiveness Of Training Plan Inspiration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Improving Corporate Performance Key Trends That Drive The Industry Graphics PDF
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. If you are looking for a format to display your unique thoughts, then the professionally designed Improving Corporate Performance Key Trends That Drive The Industry Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Improving Corporate Performance Key Trends That Drive The Industry Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Key Trends That Drive The Industry Ppt Layouts Images PDF
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. Get a simple yet stunning designed Key Trends That Drive The Industry Ppt Layouts Images PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Key Trends That Drive The Industry Ppt Layouts Images PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
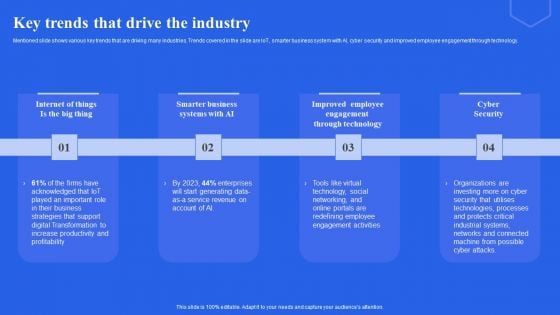
Key Trends That Drive The Industry Ppt Professional Templates PDF
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. If you are looking for a format to display your unique thoughts, then the professionally designed Key Trends That Drive The Industry Ppt Professional Templates PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Trends That Drive The Industry Ppt Professional Templates PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
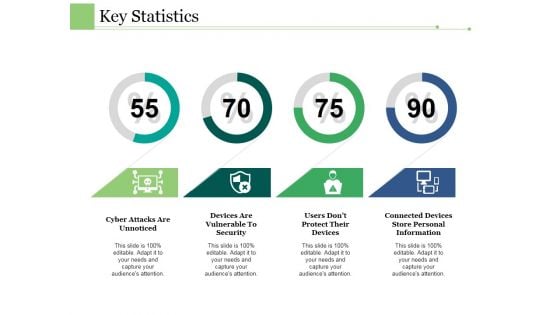
Key Statistics Ppt PowerPoint Presentation Show Sample
This is a key statistics ppt powerpoint presentation show sample. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users do not protect their devices, connected devices store personal information.
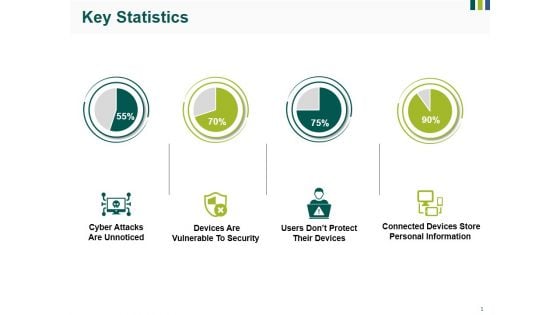
Key Statistics Ppt PowerPoint Presentation Gallery Format Ideas
This is a key statistics ppt powerpoint presentation gallery format ideas. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users dont protect their devices, connected devices store personal information.
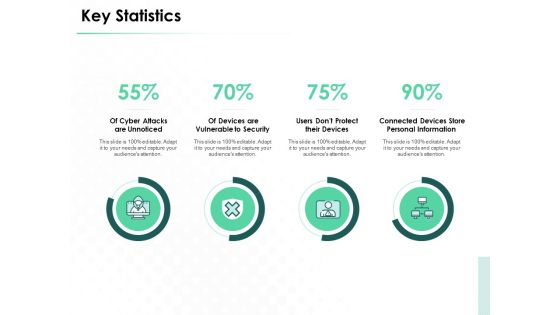
Market Approach To Business Valuation Key Statistics Summary PDF
Presenting this set of slides with name market approach to business valuation key statistics summary pdf. This is a four stage process. The stages in this process are cyber attacks unnoticed, devices vulnerable security, users dont protect devices, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
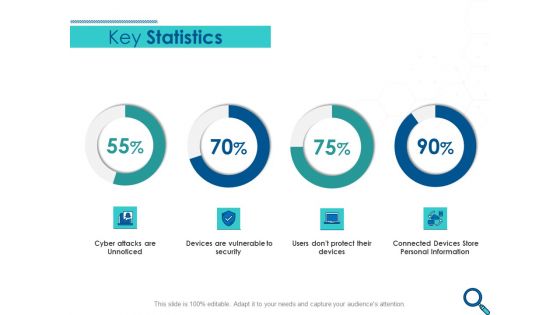
Evaluating Competitive Marketing Effectiveness Key Statistics Ppt Portfolio Ideas PDF
Presenting this set of slides with name evaluating competitive marketing effectiveness key statistics ppt portfolio ideas pdf. The topics discussed in these slides are cyber attacks are unnoticed, devices are vulnerable to security, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
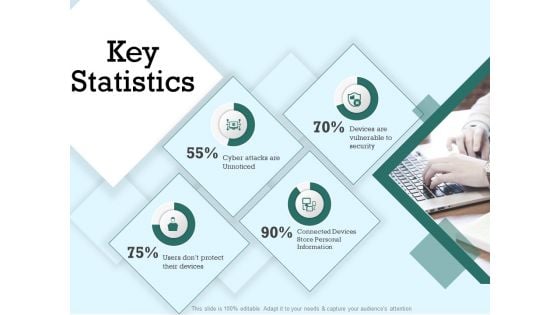
Survey Analysis Gain Marketing Insights Key Statistics Sample PDF
Presenting this set of slides with name survey analysis gain marketing insights key statistics sample pdf. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
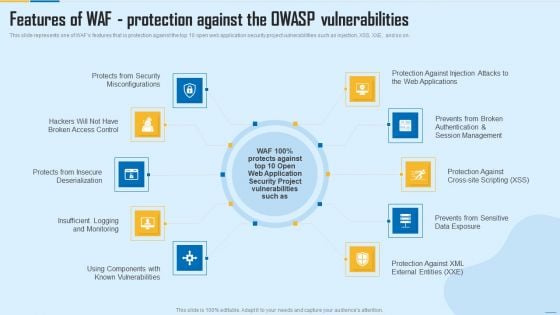
Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Misconfigurations, Session Management, Security Project. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
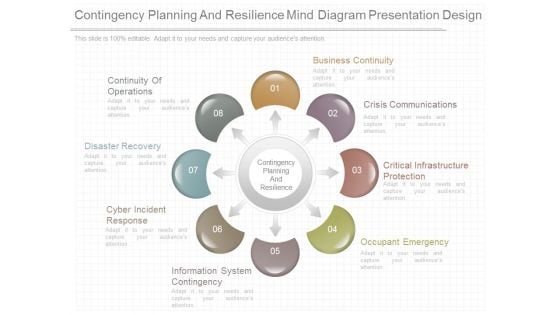
Contingency Planning And Resilience Mind Diagram Presentation Design
This is a contingency planning and resilience mind diagram presentation design. This is a eight stage process. The stages in this process are contingency planning and resilience, business continuity, crisis communications, critical infrastructure protection, occupant emergency, information system contingency, cyber incident response, disaster recovery, continuity of operations.
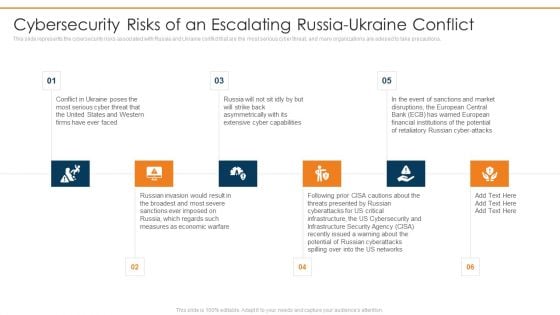
Data Wiper Spyware Attack Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Background PDF
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions.This is a data wiper spyware attack cybersecurity risks of an escalating russia ukraine conflict background pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like extensive cyber capabilities, russian invasion would, measures as economic warfare You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
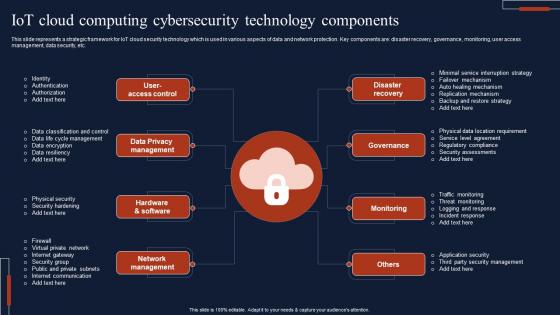
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc.
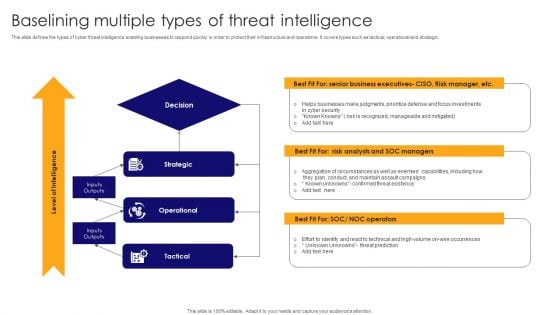
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Ukraine Cyberwarfare Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Topics Pdf
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. This is a ukraine cyberwarfare cybersecurity risks of an escalating russia ukraine conflict topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conflict in ukraine poses the most serious cyber threat that the united states, russia will not sit idly by but will strike back asymmetrically with its extensive cyber capabilities, russian invasion would result in the broadest and most severe sanctions ever imposed on russia. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
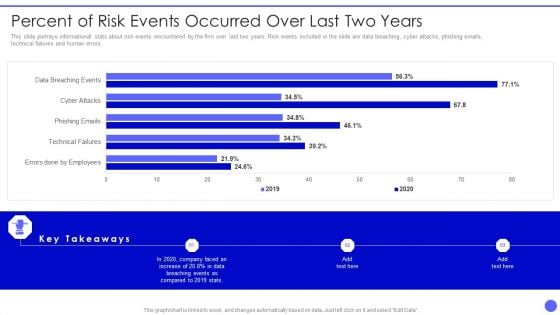
Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF bundle. Topics like Errors Done By Employees, Technical Failures, Phishing Emails, Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Internet Of Things Advantages In Business Ppt PowerPoint Presentation Gallery Icon PDF
Presenting internet of things advantages in business ppt powerpoint presentation gallery icon pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including security system, operational expenditure, rich data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Retail Businesses Internal Strategy With Icons Ppt Ideas Slide Download PDF
This slide covers retail operational processes and its work flow. It includes following problems such as Security related, maintenance and safety related, merchandise related and HR process. Presenting retail businesses internal strategy with icons ppt ideas slide download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including security related problems, maintenance and safety, merchandise related problems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
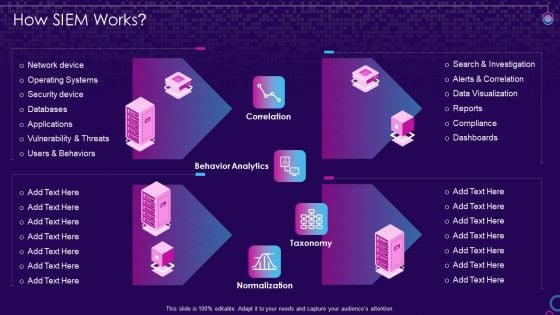
SIEM Services How SIEM Works Ppt Microsoft PDF
Deliver an awe inspiring pitch with this creative siem services how siem works ppt microsoft pdf bundle. Topics like network device, operating systems, security device, vulnerability and threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
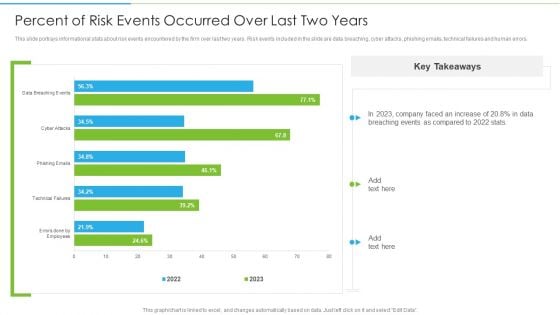
Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF. Use them to share invaluable insights on Technical Failures, Phishing Emails, Cyber Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
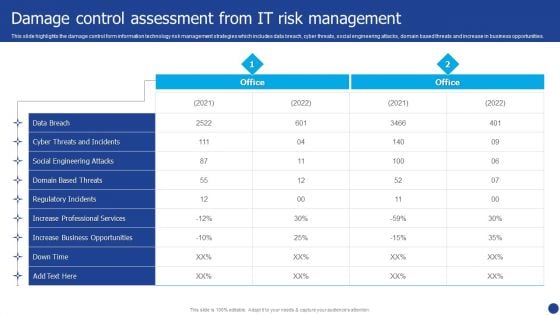
Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF bundle. Topics like Data Breach, Social Engineering Attacks, Cyber Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































