Cyber Security Risk Management
Distributed Computing IT Dashboard For Edge Computing Tracking Template PDF
This slide depicts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details. Deliver and pitch your topic in the best possible manner with this distributed computing it dashboard for edge computing tracking template pdf. Use them to share invaluable insights on monitoring, security, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF
This slide covers various courses for employees to aware about IT security threats. It includes identification of compliance stands, audit standards, incident trends, organisations security awareness, etc.Showcasing this set of slides titled Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF. The topics addressed in these templates are Compliance Standards, Identify Audit Standards, Security Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
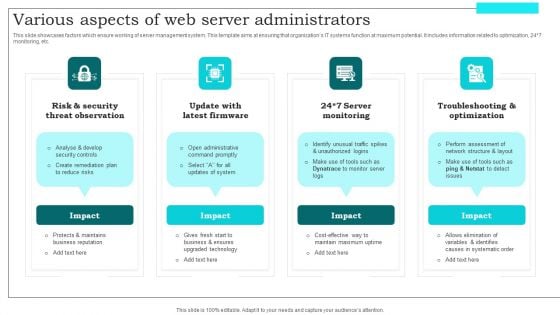
Various Aspects Of Web Server Administrators Themes PDF

Application Protection Ppt Layout Presentation Design
This is a application protection ppt layout presentation design. This is a seven stage process. The stages in this process are content security, risk mitigation, risk assessment, application security, evaluation and assessment, endpoint security, network security.
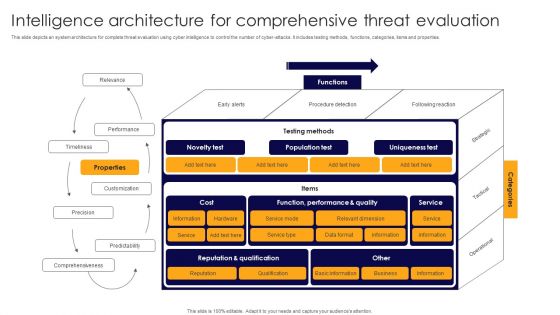
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Tools And Techniques Of Machine Learning Types Of Supervised Machine Learning Algorithms Ppt Infographics Icon PDF
Presenting this set of slides with name tools and techniques of machine learning types of supervised machine learning algorithms ppt infographics icon pdf. This is a two stage process. The stages in this process are classification, regression, risk assessment, score prediction, supervised learning, email spam detection, diagnostics, image classification, fraud detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Boosting Machine Learning Types Of Supervised Machine Learning Algorithms Ppt PowerPoint Presentation Icon Slide PDF
Presenting this set of slides with name boosting machine learning types of supervised machine learning algorithms ppt powerpoint presentation icon slide pdf. This is a two stage process. The stages in this process are supervised learning, classification, regression, risk assessment, score prediction, image classification, diagnostics, email spam detection, fraud detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Team Performance Improvement Functional Optimization Through Agile Methodologies Prioritizing Agile Software Development Tasks Sample PDF
This slide shows some important tasks that need to be done on priority basis in order to implement Agile Technique in the team such as focusing on individual, enhance product features, quickly responding to change, collaborating with the customer for efficient task completion etc. This is a team performance improvement functional optimization through agile methodologies prioritizing agile software development tasks sample pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project deliverables, enhancing team communication, customer collaboration, minimize cyber security risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
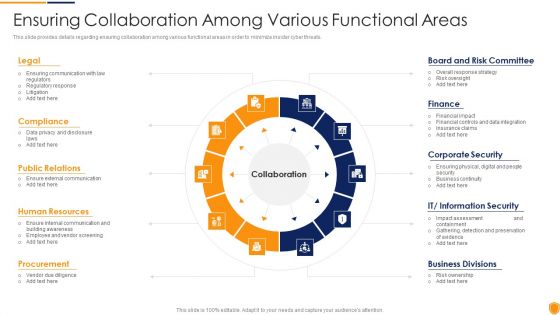
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Collaboration Among Elements PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting mitigating cybersecurity threats and vulnerabilities ensuring collaboration among elements pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like compliance, public relations, human resources, procurement, board and risk committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
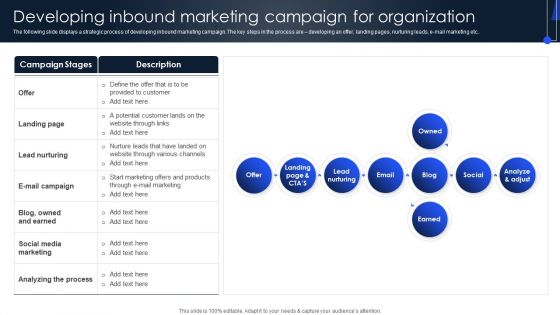
Implementing Marketing Strategies Developing Inbound Marketing Campaign For Summary PDF
The following slide displays a strategic process of developing inbound marketing campaign. The key steps in the process are developing an offer, landing pages, nurturing leads, e-mail marketing etc. Take your projects to the next level with our ultimate collection of Implementing Marketing Strategies Developing Inbound Marketing Campaign For Summary PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
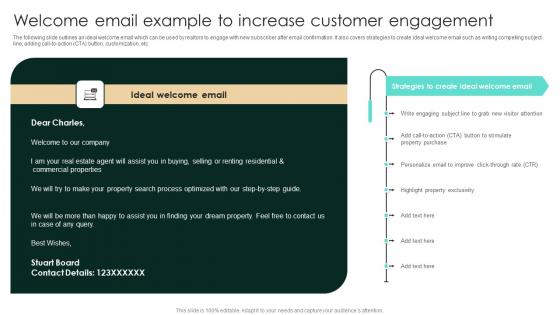
Welcome Email Example To Increase Customer Strategic Real Estate Demonstration Pdf
The following slide outlines an ideal welcome email which can be used by realtors to engage with new subscriber after email confirmation. It also covers strategies to create ideal welcome email such as writing compelling subject line, adding call-to-action CTA button, customization, etc. Take your projects to the next level with our ultimate collection of Welcome Email Example To Increase Customer Strategic Real Estate Demonstration Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. The following slide outlines an ideal welcome email which can be used by realtors to engage with new subscriber after email confirmation. It also covers strategies to create ideal welcome email such as writing compelling subject line, adding call-to-action CTA button, customization, etc.
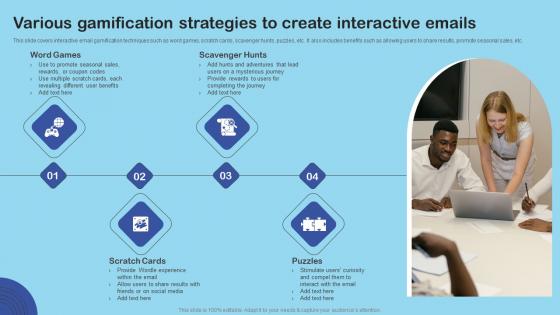
Various Gamification Strategies Enhance Client Engagement With Interactive Advertising Diagrams Pdf
This slide covers interactive email gamification techniques such as word games, scratch cards, scavenger hunts, puzzles, etc. It also includes benefits such as allowing users to share results, promote seasonal sales, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Various Gamification Strategies Enhance Client Engagement With Interactive Advertising Diagrams Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates. This slide covers interactive email gamification techniques such as word games, scratch cards, scavenger hunts, puzzles, etc. It also includes benefits such as allowing users to share results, promote seasonal sales, etc.
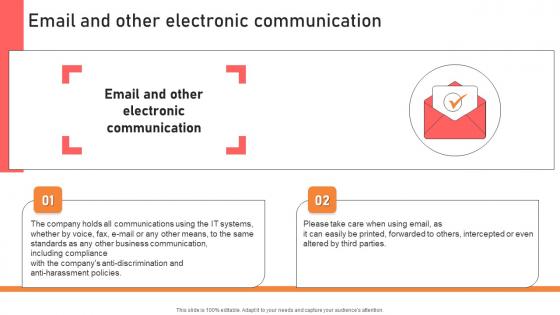
Email And Other Electronic Communication Handbook For Corporate Personnel Rules Pdf
Retrieve professionally designed Email And Other Electronic Communication Handbook For Corporate Personnel Rules Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Following slide exhibits importance of upward communication strategies to solve various business problems. It includes elements such as challenges, workplace environmental conditions, grievances and conflicts and personal problems.
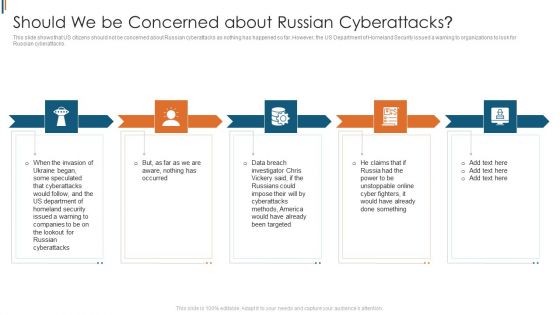
Ukraine Cyberwarfare Should We Be Concerned About Russian Cyberattacks Sample Pdf
This slide shows that US citizens should not be concerned about Russian cyberattacks as nothing has happened so far. However, the US Department of Homeland Security issued a warning to organizations to look for Russian cyberattacks. This is a ukraine cyberwarfare should we be concerned about russian cyberattacks sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like but, as far as we are aware, nothing has occurred, he claims that if russia had the power to be unstoppable online cyber fighters, data breach investigator chris vickery said, if the russians could impose their will by cyberattacks methods. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Evaluating Rank Prospects Gathering Information For Lead Qualifying Process Ppt Icon Influencers PDF
The firm will generate lead crucial information through webinar by collecting the relevant data from prospective leads such as job title, phone number, name, email address, etc. Deliver and pitch your topic in the best possible manner with this evaluating rank prospects gathering information for lead qualifying process ppt icon influencers pdf. Use them to share invaluable insights on project timeframe, gathering information, lead qualifying process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
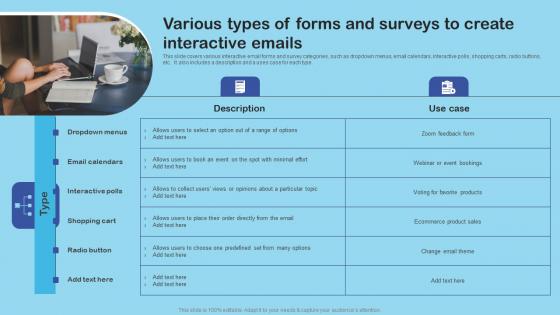
Various Types Of Forms And Surveys Enhance Client Engagement With Interactive Advertising Slides Pdf
This slide covers various interactive email forms and survey categories, such as dropdown menus, email calendars, interactive polls, shopping carts, radio buttons, etc. It also includes a description and a uses case for each type. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Various Types Of Forms And Surveys Enhance Client Engagement With Interactive Advertising Slides Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates. This slide covers various interactive email forms and survey categories, such as dropdown menus, email calendars, interactive polls, shopping carts, radio buttons, etc. It also includes a description and a uses case for each type.
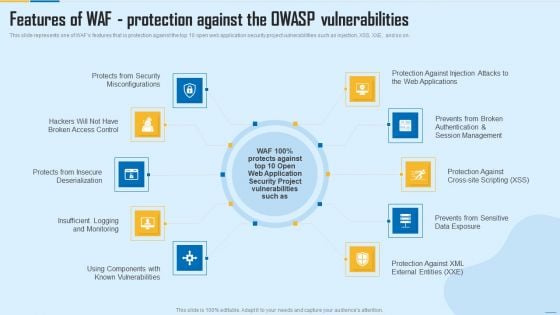
Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Misconfigurations, Session Management, Security Project. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
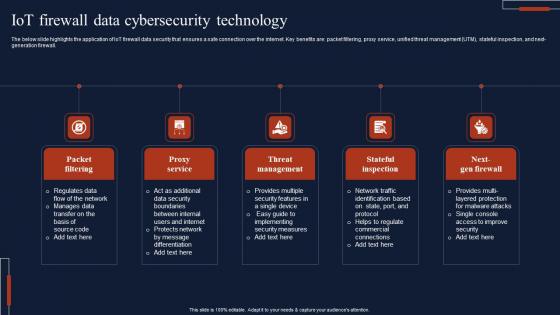
IOT Firewall Data Cybersecurity Technology Brochure Pdf
The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall. Showcasing this set of slides titled IOT Firewall Data Cybersecurity Technology Brochure Pdf The topics addressed in these templates are Packet Filtering, Proxy Service, Threat Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall.

Zero Trust Network Access Implementation Challenges Mockup Pdf
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Get a simple yet stunning designed Zero Trust Network Access Implementation Challenges Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Network Access Implementation Challenges Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Zero Trust Model Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Model Zero Trust Network Access Implementation Challenges from Slidegeeks and deliver a wonderful presentation. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Online Gaming Funding Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Portrait PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver an awe inspiring pitch with this creative online gaming funding pitch deck what video game experience challenges are faced by prospect portrait pdf bundle. Topics like security threats, regulatory compliances can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Online Gaming Fundraising Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Slides PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver and pitch your topic in the best possible manner with this online gaming fundraising pitch deck what video game experience challenges are faced by prospect slides pdf. Use them to share invaluable insights on security threats, regulatory compliances and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
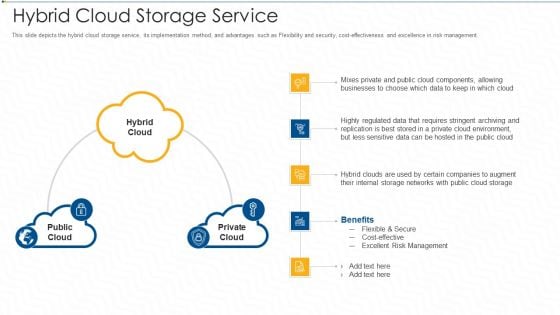
Hybrid Cloud Storage Service Ppt Shapes PDF
This slide depicts the hybrid cloud storage service, its implementation method, and advantages such as Flexibility and security, cost-effectiveness and excellence in risk management. Presenting hybrid cloud storage service ppt shapes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like environment, requires, businesses, networks, benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist For Auditing Current Financial Scenario Infographics PDF
This slide illustrates auditing current financial scenario through checklist. It provides information about current assets, current liabilities, cash flows, insurance plan, risk mitigation, online payment, financial security, growth, net worth, etc. Create an editable Checklist For Auditing Current Financial Scenario Infographics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Checklist For Auditing Current Financial Scenario Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
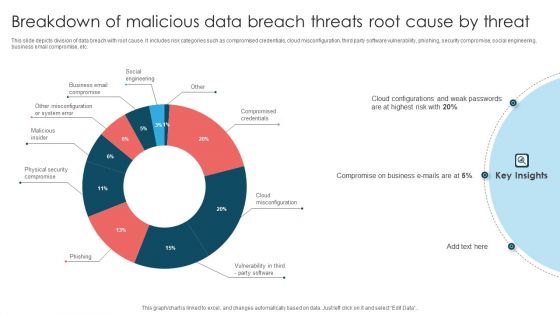
Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF
This slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Showcasing this set of slides titled Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF. The topics addressed in these templates are Compromise On Business, Cloud Configurations, Weak Passwords. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
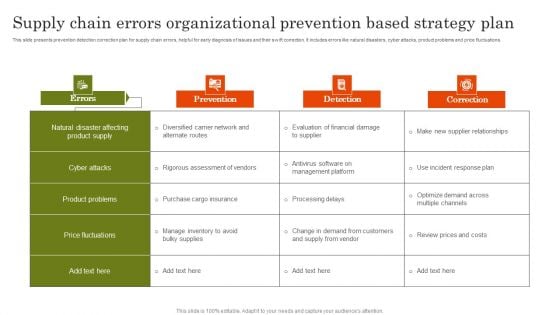
Supply Chain Errors Organizational Prevention Based Strategy Plan Topics PDF
This slide presents prevention detection correction plan for supply chain errors, helpful for early diagnosis of issues and their swift correction. It includes errors like natural disasters, cyber attacks, product problems and price fluctuations. Present the topic in a bit more detail with this Supply Chain Errors Organizational Prevention Based Strategy Plan Topics PDF. Use it as a tool for discussion and navigation on Cyber Attacks, Product Problems, Price Fluctuations. This template is free to edit as deemed fit for your organization. Therefore download it now.
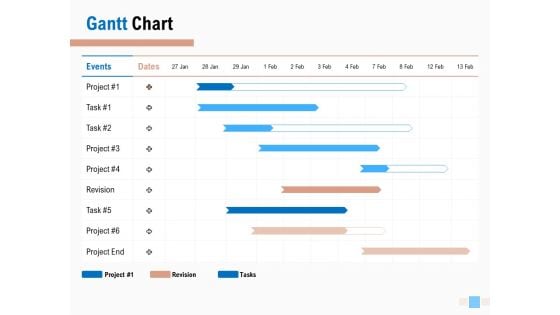
Email Advertising Proposal Gantt Chart Ppt Model Infographic Template PDF
Your complex projects can be managed and organized simultaneously using this detailed email advertising proposal gantt chart ppt model infographic template pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.
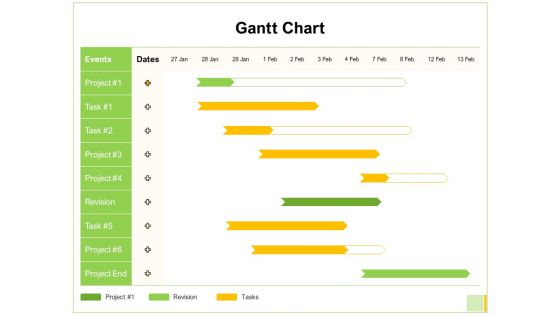
Electronic Mail Proposal Gantt Chart Ppt Outline Layout Ideas PDF
Your complex projects can be managed and organized simultaneously using this detailed electronic mail proposal gantt chart ppt outline layout ideas pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.
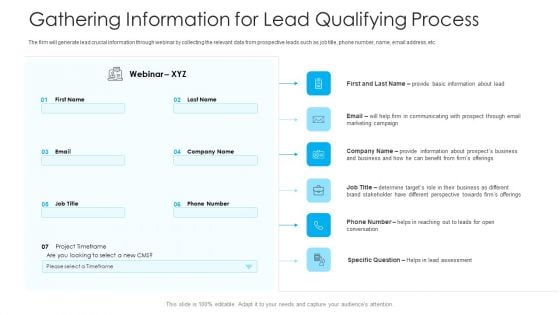
How To Build A Revenue Funnel Gathering Information For Lead Qualifying Process Demonstration PDF
The firm will generate lead crucial information through webinar by collecting the relevant data from prospective leads such as job title, phone number, name, email address, etc. Deliver an awe inspiring pitch with this creative how to build a revenue funnel gathering information for lead qualifying process demonstration pdf bundle. Topics like email marketing, project, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
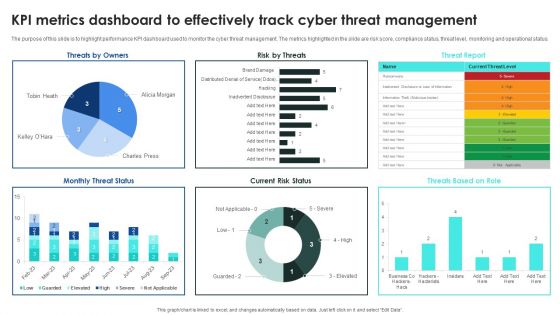
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Welcome to our selection of the Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
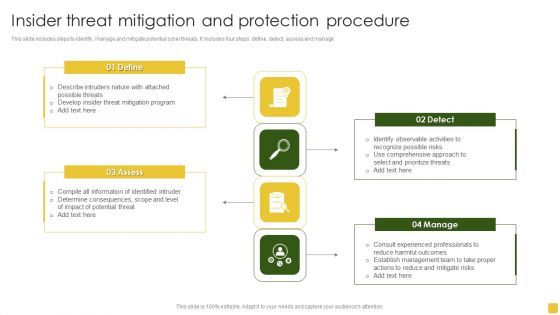
Insider Threat Mitigation And Protection Procedure Professional PDF
This slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage.Presenting Insider Threat Mitigation And Protection Procedure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigation Program, Compile Information, Determine Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
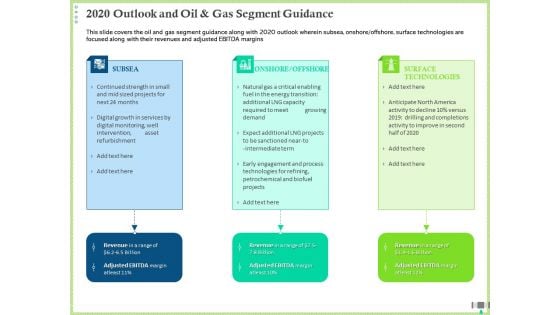
Post COVID Recovery Strategy Oil Gas Industry 2020 Outlook And Oil And Gas Segment Guidance Portrait PDF
This slide provides the four ways how digitalization helps O and G companies to survive COVID such as reducing costs, working remotely, ensuring cybersecurity, enhancing decision making, etc. This is a post covid recovery strategy oil gas industry 2020 outlook and oil and gas segment guidance portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reducing costs, working remotely, enhancing decision-making and risk management, ensuring cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
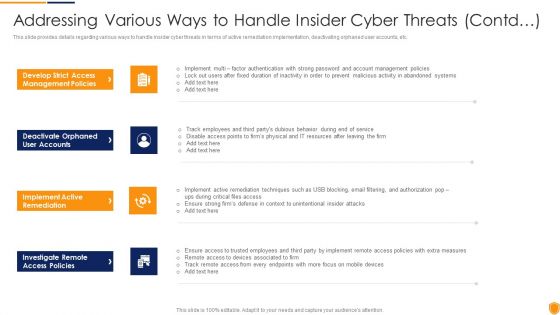
Addressing Various Ways To Handle Mitigating Cybersecurity Threats And Vulnerabilities Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a addressing various ways to handle mitigating cybersecurity threats and vulnerabilities template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like user accounts, implement active remediation, management policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Impact Analysis For Effective Threat Graphics PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. This is a mitigating cybersecurity threats and vulnerabilities impact analysis for effective threat graphics pdf template with various stages. Focus and dispense information one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis for effective threat management in securing workplace. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
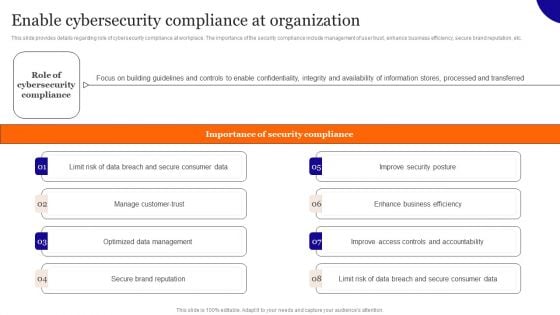
Enable Cybersecurity Compliance At Organization Mockup PDF
This slide provides details regarding role of cybersecurity compliance at workplace. The importance of the security compliance include management of user trust, enhance business efficiency, secure brand reputation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Enable Cybersecurity Compliance At Organization Mockup PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

IT Communication Infrastructure Services Download PDF
The following slide demonstrates information and communication technology infrastructure services for optimizing output, mitigate internal and external security threat. It includes components such as operations and network management etc. Persuade your audience using this IT Communication Infrastructure Services Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Applications, Description, Operations Management . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
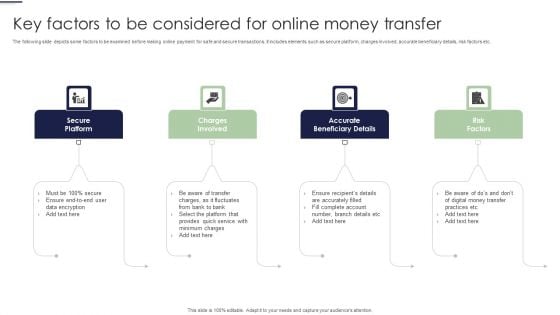
Key Factors To Be Considered For Online Money Transfer Ppt Professional Maker PDF
The following slide depicts some factors to be examined before making online payment for safe and secure transactions. It includes elements such as secure platform, charges involved, accurate beneficiary details, risk factors etc. Presenting Key Factors To Be Considered For Online Money Transfer Ppt Professional Maker PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Secure Platform, Charges Involved, Accurate Beneficiary Details, Risk Factors. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
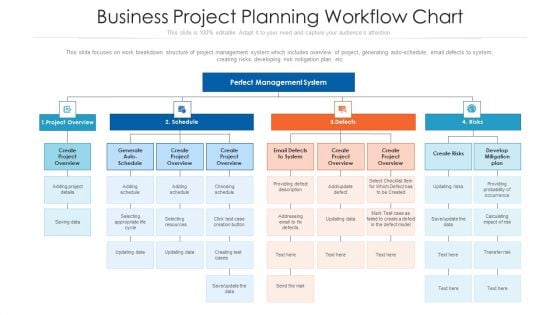
Business Project Planning Workflow Chart Ppt PowerPoint Presentation Gallery Design Inspiration PDF
This slide focuses on work breakdown structure of project management system which includes overview of project, generating auto-schedule, email defects to system, creating risks, developing risk mitigation plan, etc. Presenting business project planning workflow chart ppt powerpoint presentation gallery design inspiration pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including schedule, defects, risks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Retail Businesses Internal Strategy With Icons Ppt Ideas Slide Download PDF
This slide covers retail operational processes and its work flow. It includes following problems such as Security related, maintenance and safety related, merchandise related and HR process. Presenting retail businesses internal strategy with icons ppt ideas slide download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including security related problems, maintenance and safety, merchandise related problems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
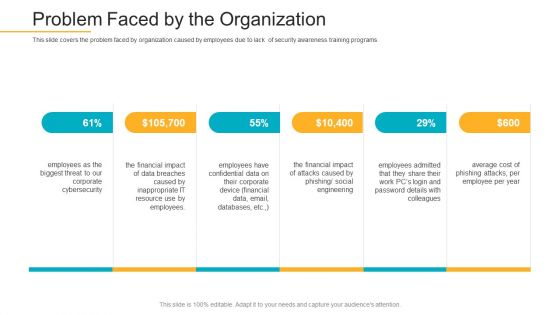
Data Breach Prevention Recognition Problem Faced By The Organization Elements PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a data breach prevention recognition problem faced by the organization elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, organization, problem, security awareness, training programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
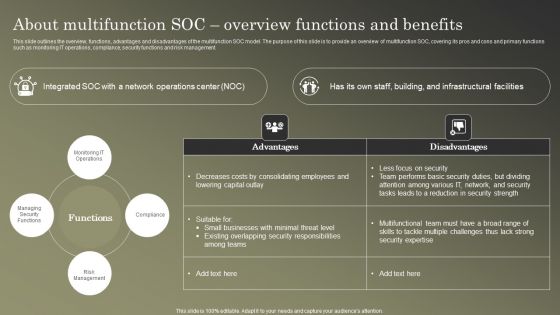
Cybersecurity Operations Cybersecops About Multifunction SOC Overview Functions Microsoft PDF
This slide outlines the overview, functions, advantages and disadvantages of the multifunction SOC model. The purpose of this slide is to provide an overview of multifunction SOC, covering its pros and cons and primary functions such as monitoring IT operations, compliance, security functions and risk management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Operations Cybersecops About Multifunction SOC Overview Functions Microsoft PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
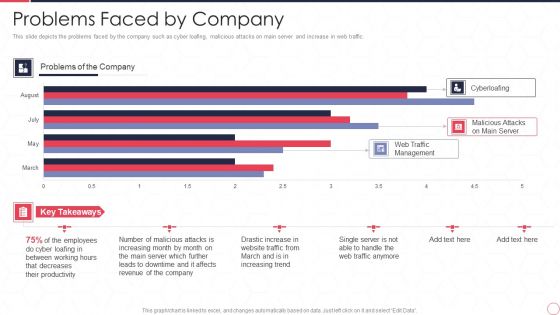
Reverse Proxy Server IT Problems Faced By Company Ppt Summary Inspiration PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic. Deliver and pitch your topic in the best possible manner with this reverse proxy server it problems faced by company ppt summary inspiration pdf. Use them to share invaluable insights on web traffic management, malicious attacks on main server, cyberloafing, employee and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Challenges To Medical Industry Cybersecurity Performance Background Pdf
This slide presents key challenges faced by cybersecurity in healthcare helpful for organizations to gain knowledge on main obstacles and solve them on priority basis. It includes data breaches, malware and ransomware, insider threats, distributed denial of service, cloud threats and lack of cyber awareness Showcasing this set of slides titled Key Challenges To Medical Industry Cybersecurity Performance Background Pdf. The topics addressed in these templates are Data Breaches, Service, Cloud Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents key challenges faced by cybersecurity in healthcare helpful for organizations to gain knowledge on main obstacles and solve them on priority basis. It includes data breaches, malware and ransomware, insider threats, distributed denial of service, cloud threats and lack of cyber awareness
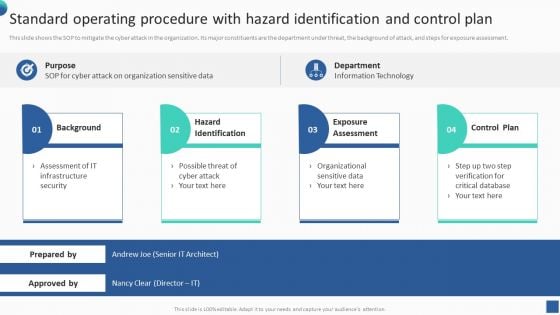
Bundle Of SOP Templates Standard Operating Procedure With Hazard Identification And Control Information PDF
This slide shows the SOP to mitigate the cyber attack in the organization. Its major constituents are the department under threat, the background of attack, and steps for exposure assessment. There are so many reasons you need a Bundle Of SOP Templates Standard Operating Procedure With Hazard Identification And Control Information PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
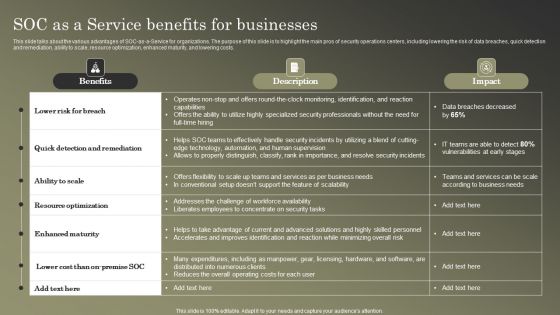
Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF
This slide talks about the various advantages of SOC-as-a-Service for organizations. The purpose of this slide is to highlight the main pros of security operations centers, including lowering the risk of data breaches, quick detection and remediation, ability to scale, resource optimization, enhanced maturity, and lowering costs. Find highly impressive Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
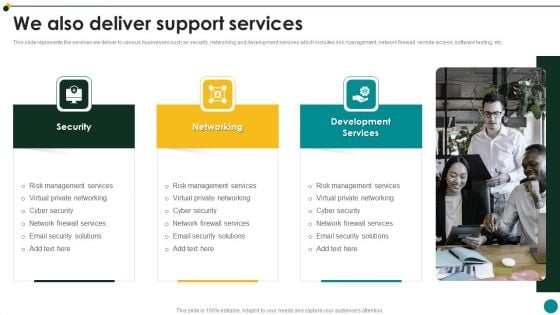
IT Services And Consulting Company Profile We Also Deliver Support Services Guidelines PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a IT Services And Consulting Company Profile We Also Deliver Support Services Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Virtual Private Networking, Management Services You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
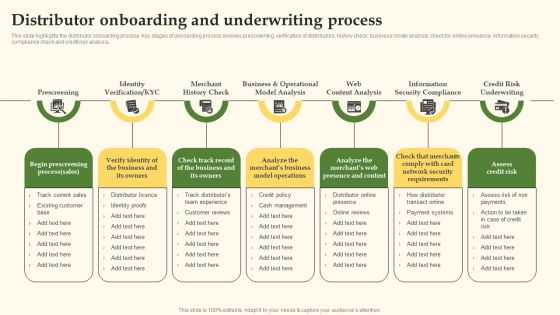
Distributor Onboarding And Underwriting Process Slides PDF
This slide highlights the distributor onboarding process. Key stages of onboarding process involves prescreening, verification of distributors, history check, business model analysis, check for online presence, information security compliance check and credit risk analysis. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Distributor Onboarding And Underwriting Process Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Distributor Onboarding And Underwriting Process Slides PDF.
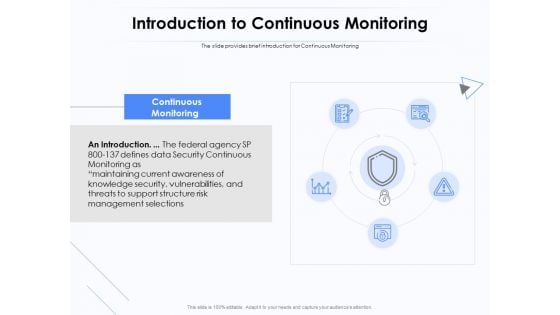
Network Monitoring Tool Overview Introduction To Continuous Monitoring Ppt PowerPoint Presentation Model Slide Download PDF
Presenting this set of slides with name network monitoring tool overview introduction to continuous monitoring ppt powerpoint presentation model slide download pdf. This is a five stage process. The stages in this process are continuous monitoring, introduction, data security, support structure, risk management selections, knowledge security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
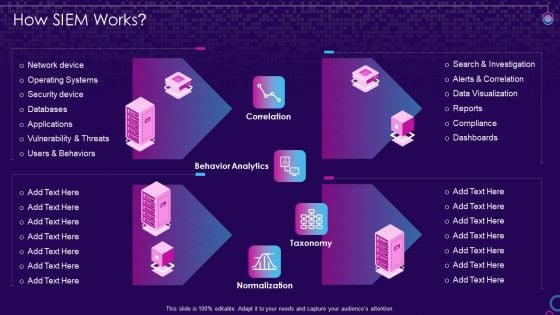
SIEM Services How SIEM Works Ppt Microsoft PDF
Deliver an awe inspiring pitch with this creative siem services how siem works ppt microsoft pdf bundle. Topics like network device, operating systems, security device, vulnerability and threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Online Marketing Key Challenges With Solutions Structure PDF
This slide shows key challenges faced in digital marketing campaigns with appropriate solutions helpful in running successful marketing campaigns. Driving website traffic, targeting right audience, optimizing budget and dealing with security risks should be treated with utmost care. Presenting Online Marketing Key Challenges With Solutions Structure PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Driving Website Traffic, Right Audience Targeting, Generating Quality Lead. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
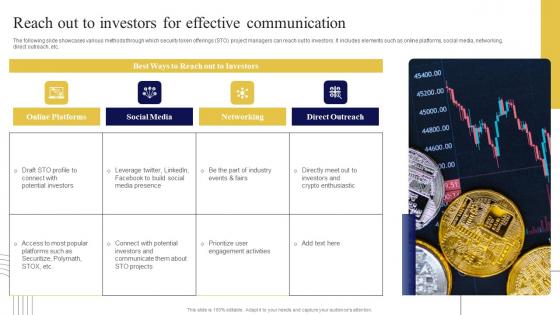
Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf
The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc. Slidegeeks is here to make your presentations a breeze with Reach Out To Investors For Effective Exploring Investment Opportunities Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc.

Technology Transformation Seven Basic Goals Ppt PowerPoint Presentation Ideas Images PDF
Persuade your audience using this technology transformation seven basic goals ppt powerpoint presentation ideas images pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including safeguarding digital resources cyber threats, technology optimization to push faster and respond to changes, technology optimization more productive, secure, track and react to conditions real time, optimizing investment protection to reduce resources and administration, ensuring threats handled and fully complied security, build modern business plan grabbing new opportunities. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.
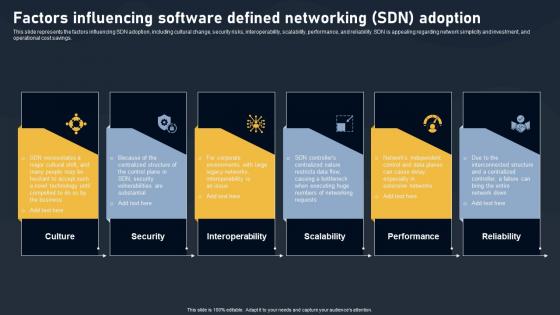
Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.Slidegeeks has constructed Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.

Real Estate Development Project Prioritization Slide Download PDF
The following slide exhibits various types of cybersecurity risk faced by the real estate company. Ransomware, phishing, web-based attack and business email compromise are some of the major risks which are mentioned in the slide.Deliver and pitch your topic in the best possible manner with this Real Estate Development Project Prioritization Slide Download PDF. Use them to share invaluable insights on Ransomware, Phishing, Management Response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
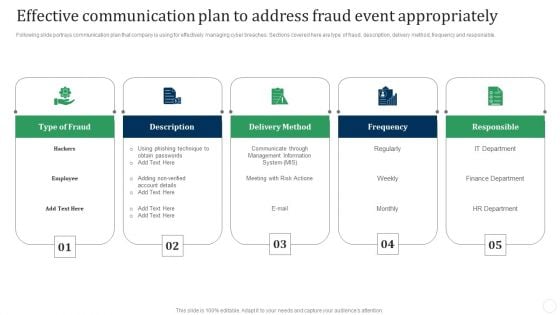
Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible.This is a Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Phishing Technique, Obtain Passwords, Communicate Through. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Solutions Business Profile We Also Deliver Support Services Clipart PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a Information Technology Solutions Business Profile We Also Deliver Support Services Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Private Networking, Network Firewall. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
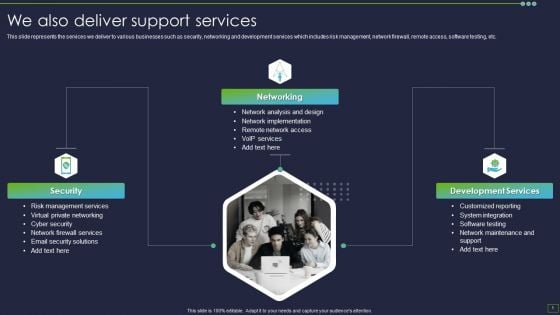
IT Consultancy Services Company Profile We Also Deliver Support Services Structure PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a IT Consultancy Services Company Profile We Also Deliver Support Services Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Services, Management Services, Network Implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Small Business Venture Company Profile We Also Deliver Support Services Summary PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a Small Business Venture Company Profile We Also Deliver Support Services Summary PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Private Networking, Firewall Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf
This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty.

 Home
Home