Cyber Security Risk Management

Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Do you know about Slidesgeeks Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
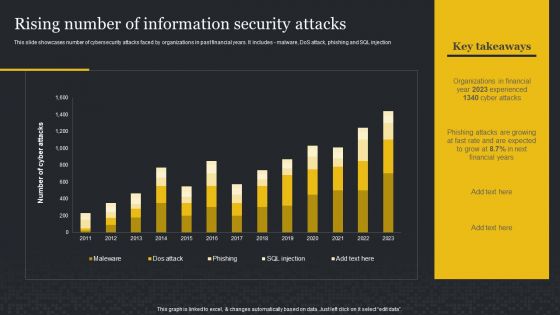
Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Boost your pitch with our creative Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Take your projects to the next level with our ultimate collection of Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. Find a pre-designed and impeccable Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
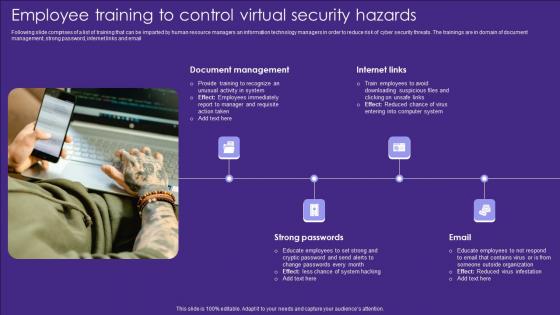
Employee Training To Control Virtual Security Hazards Designs Pdf
Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Pitch your topic with ease and precision using this Employee Training To Control Virtual Security Hazards Designs Pdf. This layout presents information on Internet Links, Email, Strong Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email
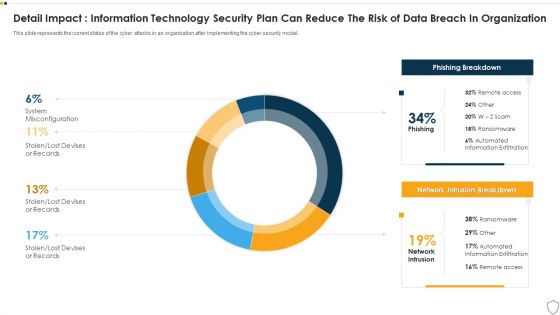
IT Security Detail Impact Information Technology Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Layouts Show PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this it security detail impact information technology security plan can reduce the risk of data breach in organization ppt layouts show pdf. Use them to share invaluable insights on detail impact information technology security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
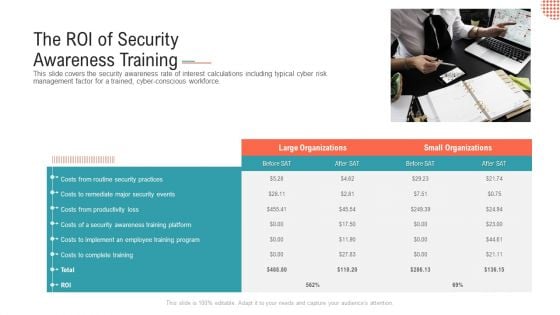
The ROI Of Security Awareness Training Ppt Slides Background PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyberconscious workforce.This is a the roi of security awareness training ppt slides background pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs from routine security practices, costs from productivity loss. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
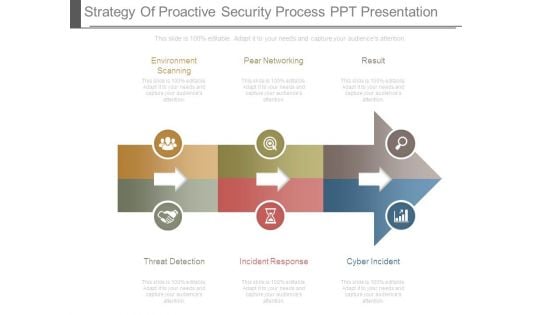
Strategy Of Proactive Security Process Ppt Presentation
This is a strategy of proactive security process ppt presentation. This is a three stage process. The stages in this process are environment scanning, pear networking, result, threat detection, incident response, cyber incident.
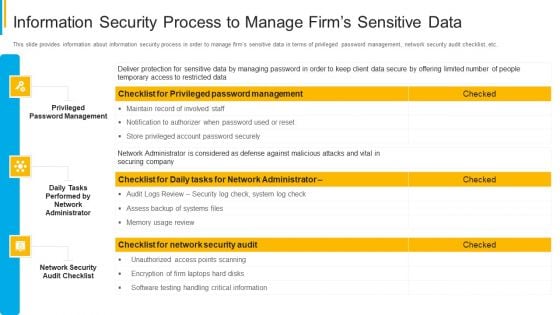
Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
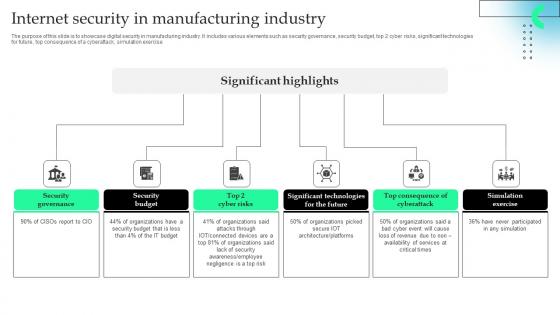
Internet Security In Manufacturing Industry Professional Pdf
The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.Pitch your topic with ease and precision using this Internet Security In Manufacturing Industry Professional Pdf This layout presents information on Security Governance, Security Budget, Significant Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.
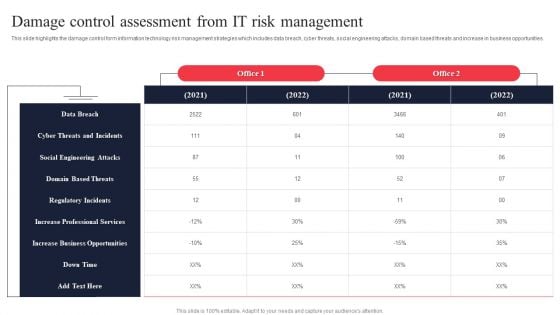
IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF
This slide represents the official announcement from lotem finkelstein, head of threat intelligence at check point software, that anyone can join ukraine and russia cyber warfare. Slidegeeks is here to make your presentations a breeze with Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
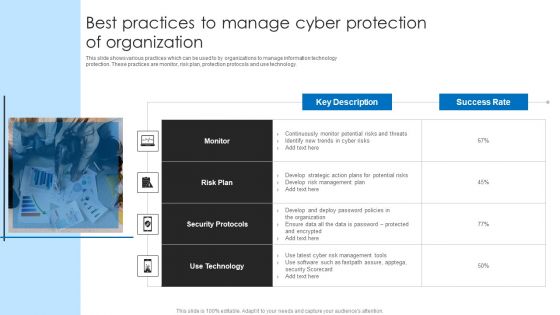
Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
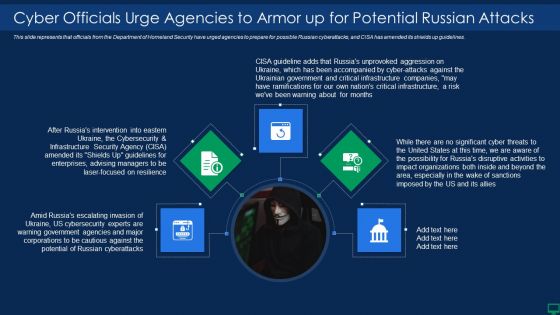
Russian Cyber Attacks On Ukraine IT Cyber Officials Urge Background PDF
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines. Presenting russian cyber attacks on ukraine it cyber officials urge background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, organizations, risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
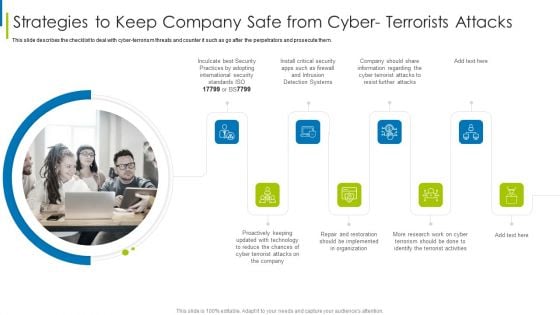
Cyber Terrorism Assault Strategies To Keep Company Safe From Cyber Terrorists Attacks Pictures PDF
This slide describes the checklist to deal with cyber terrorism threats and counter it such as go after the perpetrators and prosecute them.Presenting cyber terrorism assault strategies to keep company safe from cyber terrorists attacks pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like inculcate best security, practices by adopting, international security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Types Of Threats In Information Technology Security Ppt Summary Aids PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting it security types of threats in information technology security ppt summary aids pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Strategies To Manage Cyber Risks Ppt Infographic Template Graphics Template PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a cybersecurity strategies to manage cyber risks ppt infographic template graphics template pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strategic, risk, implementation, awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Technology Stack Powerpoint Ppt Template Bundles
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Security Technology Stack Powerpoint Ppt Template Bundles has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has Encryption Tools, API Security, Cloud Technology, Network Security, Zero Trust-slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance. Enhance your cybersecurity expertise with our Security Technology Stack PowerPoint presentation. Explore the intricacies of cybersecurity tech stacks through practical examples and insights to safeguard your digital assets. The presentation covers various tech stacks such as web development and Microsoft technology. Learn how to build a robust security technology stack to protect your organization from emerging threats and vulnerabilities. Designed for IT professionals, developers, or business leaders, this PPT provides tools and strategies to create a resilient defense system.
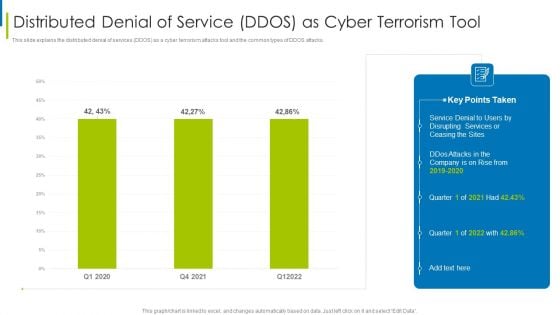
Cyber Terrorism Assault Distributed Denial Of Service DDOS As Cyber Terrorism Tool Slides PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism attacks tool and the common types of DDOS attacks.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault distributed denial of service ddos as cyber terrorism tool slides pdf Use them to share invaluable insights on Make A Risk Assessment, Determine The Importance Of Assets, Make A Complete Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
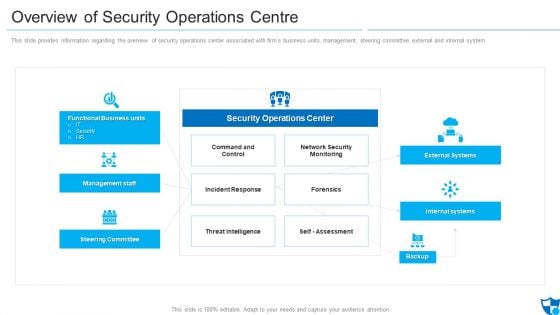
Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
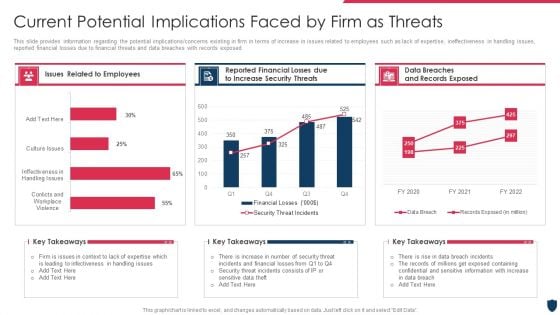
Cyber Safety Incident Management Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative cyber safety incident management current potential implications faced by firm as threats clipart pdf bundle. Topics like issues related to employees, data breaches and records exposed, reported financial losses due to increase security threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
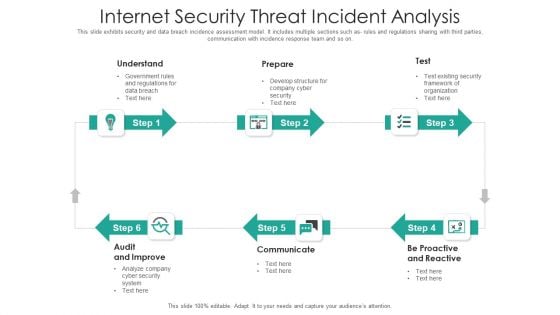
Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
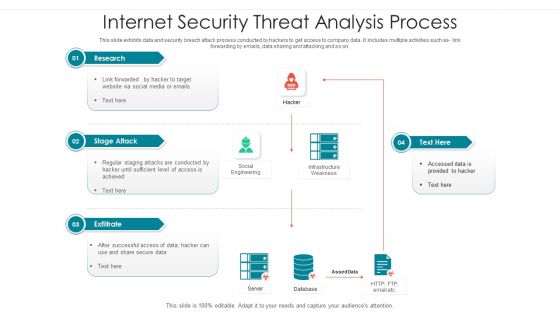
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
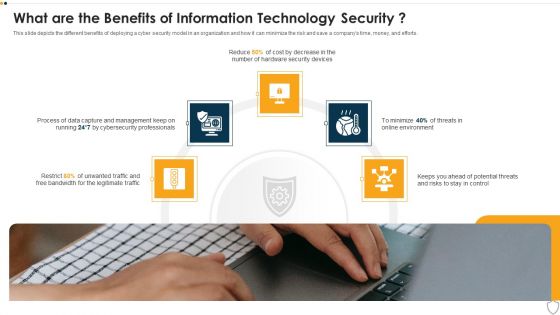
IT Security What Are The Benefits Of Information Technology Security Ppt Layouts Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a it security what are the benefits of information technology security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, process, potential threats, security devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
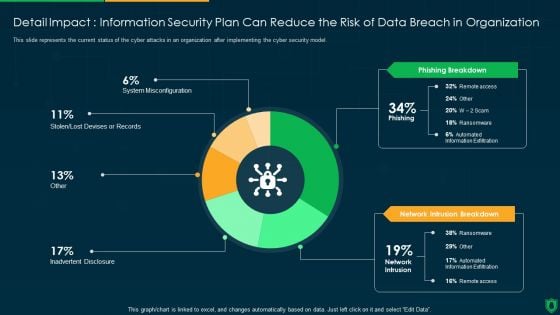
Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Types Of Threats In Information Security Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting info security types of threats in information security ppt powerpoint presentation gallery layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Measures And Ways To Mitigate Rules PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach measures and ways to mitigate rules pdf. Use them to share invaluable insights on measures and ways to mitigate security monitoring challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
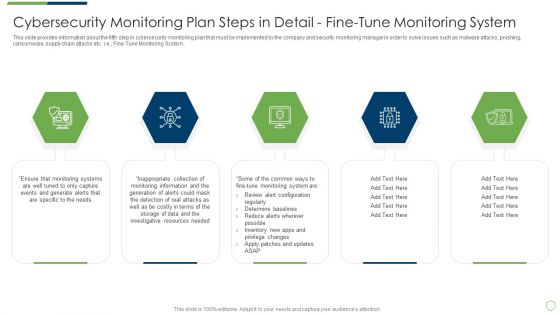
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
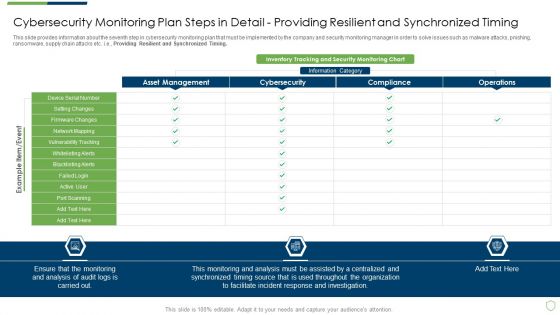
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
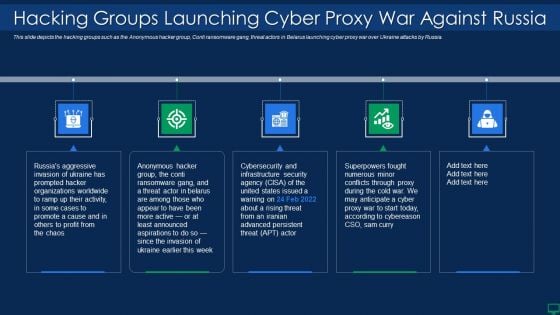
Russian Cyber Attacks On Ukraine IT Hacking Groups Launching Cyber Rules PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting russian cyber attacks on ukraine it hacking groups launching cyber rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Info Security Dashboard For Threat Tracking In Information Security Ppt PowerPoint Presentation File Example Introduction PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative info security dashboard for threat tracking in information security ppt powerpoint presentation file example introduction pdf bundle. Topics like threats by owners, risk by threats, threat report, monthly threat status, current risk status, threats based on role can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Dashboard For Threat Tracking In Information Technology Security Ppt Inspiration Gallery PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative it security dashboard for threat tracking in information technology security ppt inspiration gallery pdf bundle. Topics like current risk status, threat report, risk by threats, threats based on role, threats by owners can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
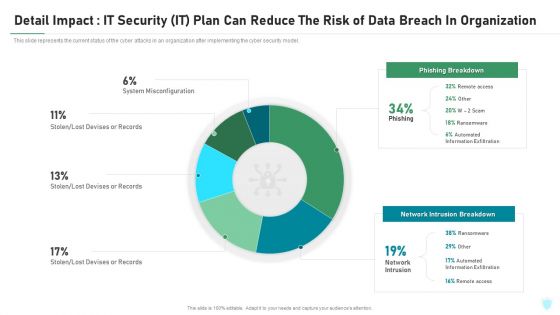
Detail Impact IT Security IT Plan Can Reduce The Risk Of Data Breach In Organization Ppt Infographic Template Objects PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this detail impact it security it plan can reduce the risk of data breach in organization ppt infographic template objects pdf. Use them to share invaluable insights on detail impact it security it plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
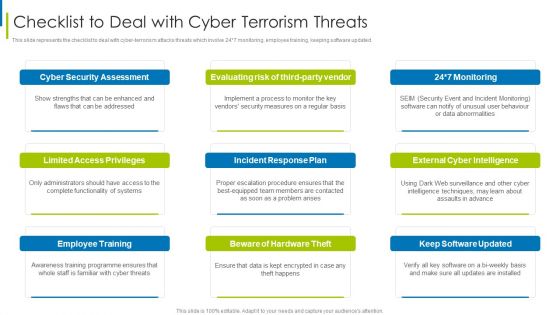
Cyber Terrorism Assault Checklist To Deal With Cyber Terrorism Threats Guidelines PDF
This slide represents the checklist to deal with cyber-terrorism attacks threats which involve 24 7 monitoring, employee training, keeping software updated.This is a cyber terrorism assault checklist to deal with cyber terrorism threats guidelines pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like German Businesses, Average Loss , Cyber Terrorist Attack You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
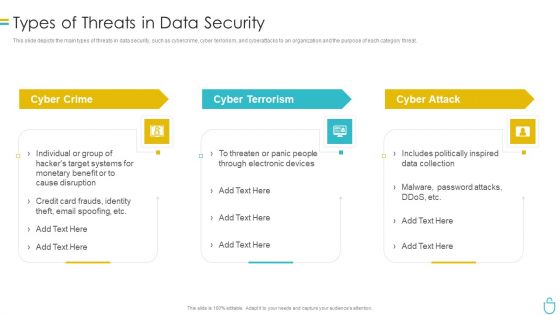
Information Security Types Of Threats In Data Security Ppt Layouts File Formats PDF
This slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a information security types of threats in data security ppt layouts file formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
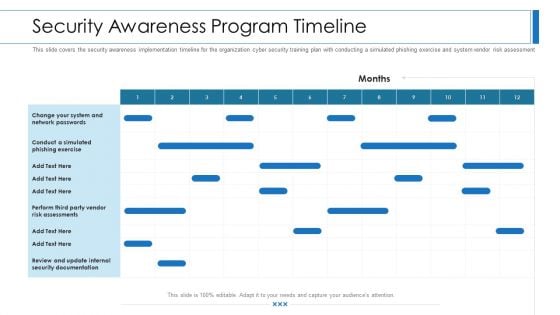
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
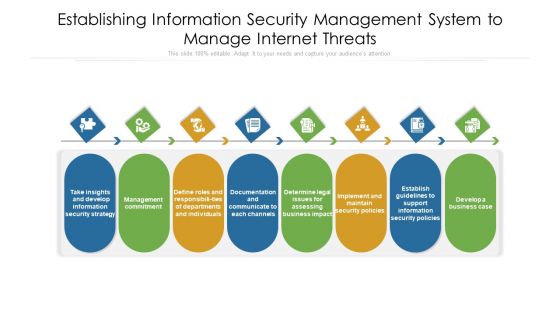
Establishing Information Security Management System To Manage Internet Threats Ppt PowerPoint Presentation File Visuals PDF
Persuade your audience using this establishing information security management system to manage internet threats ppt powerpoint presentation file visuals pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including documentation, departments, management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
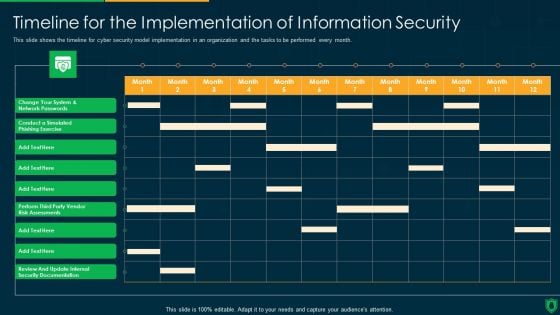
Info Security Timeline For The Implementation Of Information Security Ppt PowerPoint Presentation Diagram Templates PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative info security timeline for the implementation of information security ppt powerpoint presentation diagram templates pdf bundle. Topics like perform third party, vendor risk assessments, review and update, internal security documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Elements Of IT Security IT Cloud Security Ppt Infographics Ideas PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting elements of it security it cloud security ppt infographics ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, service, vulnerabilities, implemented, digital resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
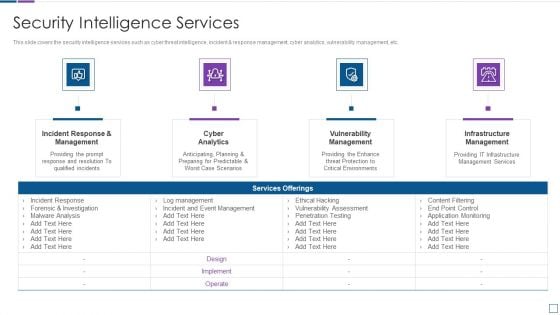
Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Malware Attacks Cloud Computing Security IT Ppt Show Diagrams PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Presenting cloud security threats malware attacks cloud computing security it ppt show diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cloud administrations, cyber criminals, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
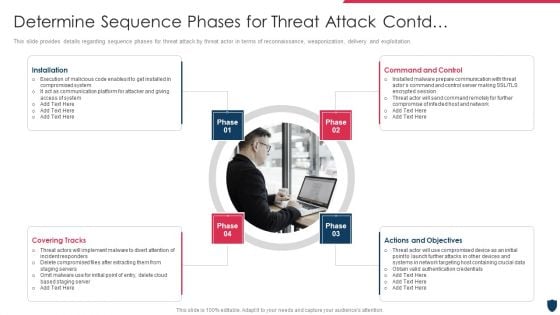
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
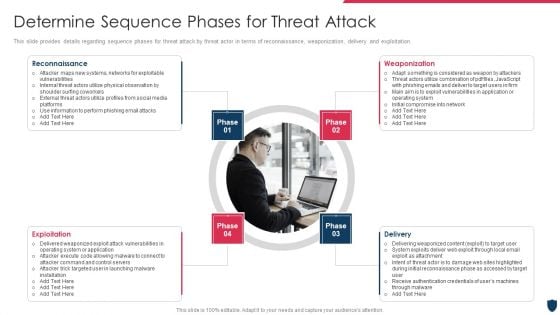
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security How Is Automation Used In Information Technology Security Ppt Diagram Lists PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting it security how is automation used in information technology security ppt diagram lists pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
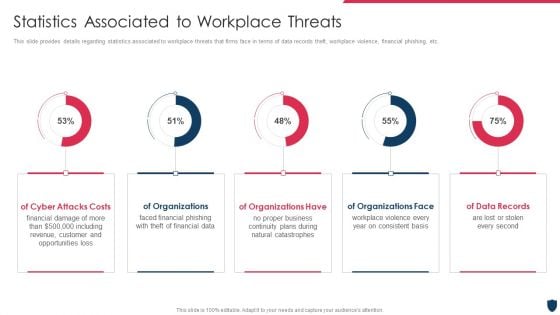
Cyber Safety Incident Management Statistics Associated To Workplace Threats Elements PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver and pitch your topic in the best possible manner with this cyber safety incident management statistics associated to workplace threats elements pdf. Use them to share invaluable insights on cyber attacks costs, organizations, organizations have, organizations face, data records and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Safety Incident Management Different Kinds Of Insider Digital Threats Download PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber safety incident management different kinds of insider digital threats download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malicious insider, negligent or careless insider, third party insider. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Determine Several Threat Actors Profile Themes PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative cyber safety incident management determine several threat actors profile themes pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
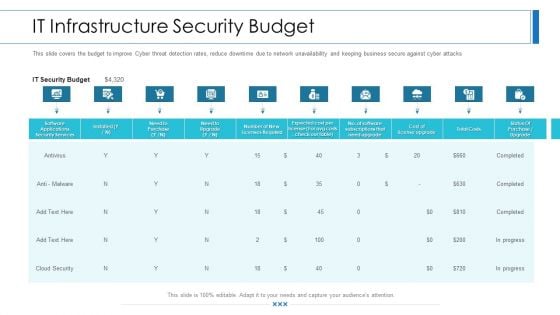
Workforce Security Realization Coaching Plan IT Infrastructure Security Budget Background PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan it infrastructure security budget background pdf bundle. Topics like software applications security services, business, it security budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
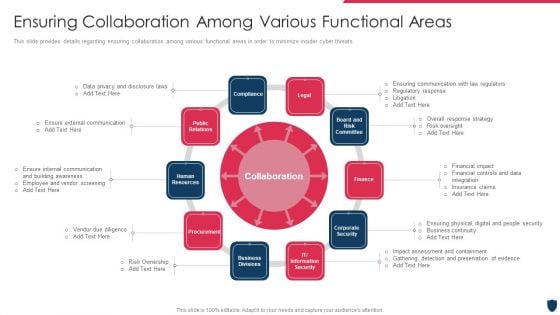
Cyber Safety Incident Management Ensuring Collaboration Among Various Functional Areas Themes PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber safety incident management ensuring collaboration among various functional areas themes pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like legal, finance, procurement, public relations, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Various Types Of Workplace Violence And Threats Infographics PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber safety incident management various types of workplace violence and threats infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stalking, physical assault, harassment or intimidation, property damage, weapon assault . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
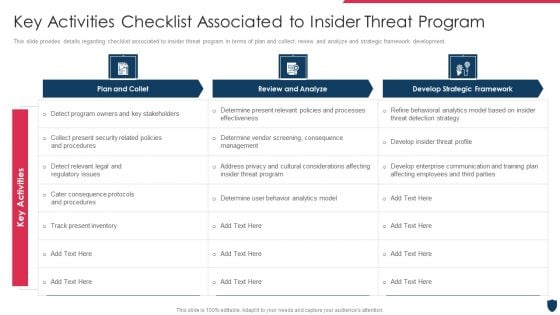
Cyber Safety Incident Management Key Activities Checklist Associated To Insider Threat Program Download PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver and pitch your topic in the best possible manner with this cyber safety incident management key activities checklist associated to insider threat program download pdf. Use them to share invaluable insights on plan and collet, review and analyze, develop strategic framework, key activities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Awareness Program Timeline Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This is a security awareness program timeline hacking prevention awareness training for it security professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perform, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Website Security Management Strategic Plan Step By Step Guide Slides PDF
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Website Security Management Strategic Plan Step By Step Guide Slides PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Website Security Management Strategic Plan Step By Step Guide Slides PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.

Cybersecurity Elements Of Electronic Information Security Operational Security Ppt Portfolio Rules PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting cybersecurity elements of electronic information security operational security ppt portfolio rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, risk, plans, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Best Practices For Website Security Management Step By Step Guide Ideas PDF
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices For Website Security Management Step By Step Guide Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.
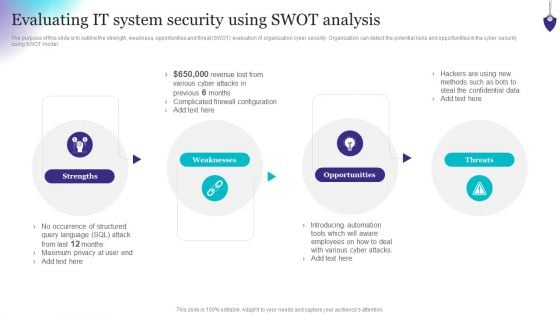
Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Slidegeeks is here to make your presentations a breeze with Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Information Technology Security Strategies To Manage IT Risks Ppt Infographic Template Guidelines PDF
This slide depicts the importance of network risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information technology security strategies to manage it risks ppt infographic template guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct awareness sessions, invest in worthy implementation, build policies and structures, prioritize network . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
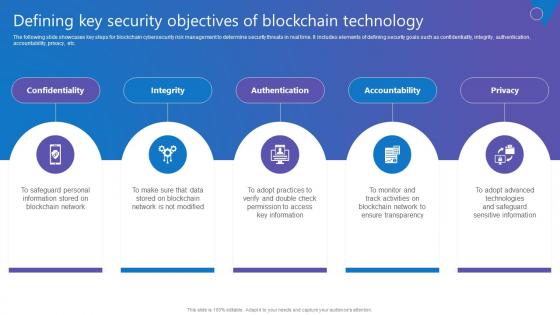
Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf
The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Want to ace your presentation in front of a live audience Our Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc.


 Continue with Email
Continue with Email

 Home
Home


































