Cyber Security Risk

Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.

Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.

Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf
This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty.
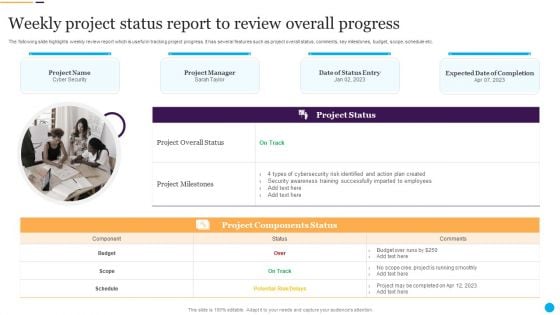
Weekly Project Status Report To Review Overall Progress Information PDF
Persuade your audience using this Weekly Project Status Report To Review Overall Progress Information PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cybersecurity Risk, Action Plan, Security Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
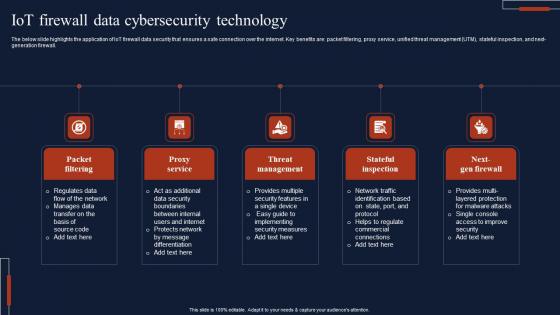
IOT Firewall Data Cybersecurity Technology Brochure Pdf
The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall. Showcasing this set of slides titled IOT Firewall Data Cybersecurity Technology Brochure Pdf The topics addressed in these templates are Packet Filtering, Proxy Service, Threat Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall.
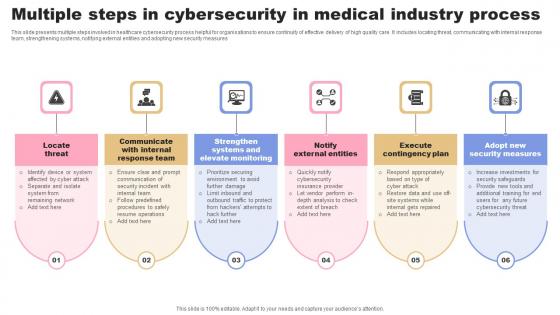
Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf
This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures Pitch your topic with ease and precision using this Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf This layout presents information on Locate Threat, Response Team, Elevate Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures
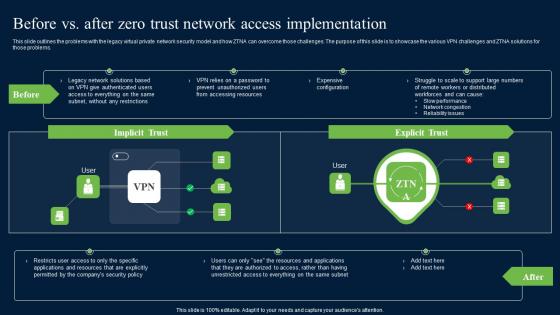
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
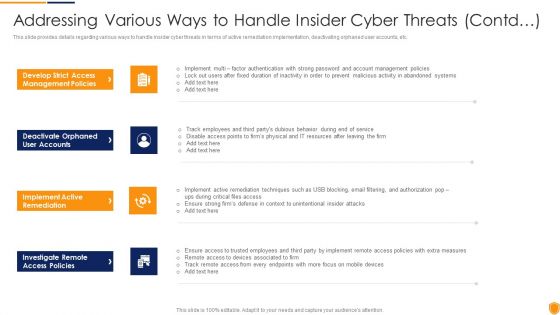
Addressing Various Ways To Handle Mitigating Cybersecurity Threats And Vulnerabilities Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a addressing various ways to handle mitigating cybersecurity threats and vulnerabilities template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like user accounts, implement active remediation, management policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
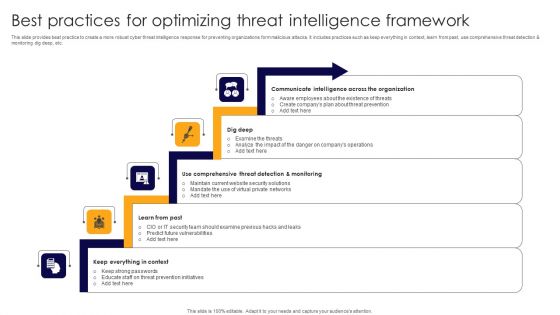
Best Practices For Optimizing Threat Intelligence Framework Formats PDF
This slide provides beat practice to create a more robust cyber threat intelligence response for preventing organizations form malicious attacks. It includes practices such as keep everything in context, learn from past, use comprehensive threat detection and monitoring dig deep, etc. Presenting Best Practices For Optimizing Threat Intelligence Framework Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Communicate Intelligence, Dig Deep, Comprehensive Threat Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF
This slide represents the main advantages of deploying security operations in an organization. The purpose of this slide is to showcase the critical benefits of SecOps implementation, covering an increased workforce to deal with threats, fewer buggy apps, quick response to threats, fewer security breaches, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
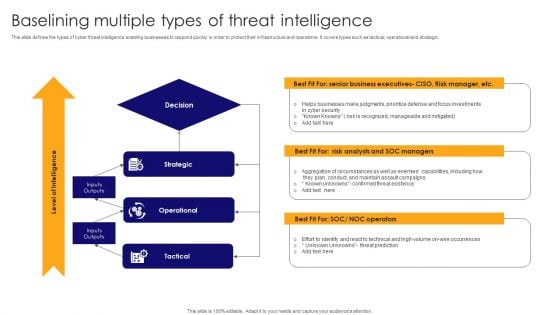
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Data Wiper Spyware Attack For The First Time In History Anyone Can Join A War Clipart PDF
This slide represents the official announcement from Lotem Finkelstein, head of threat intelligence at Check Point Software, that anyone can join Ukraine and Russia cyber warfare.This is a data wiper spyware attack for the first time in history anyone can join a war clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global digital volunteers, connected to the ukraine russia, official from check You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
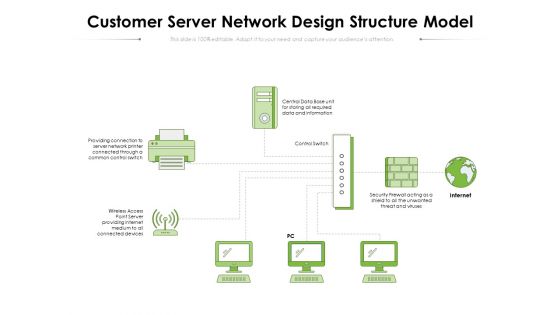
Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
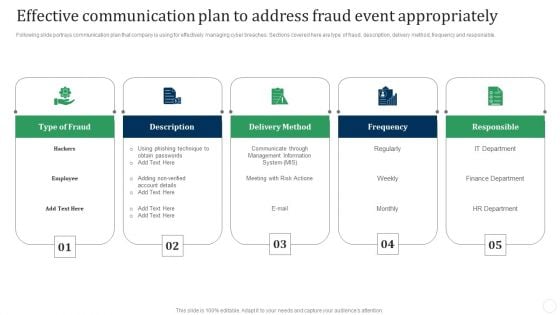
Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible.This is a Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Phishing Technique, Obtain Passwords, Communicate Through. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Software Services Business Profile SWOT Analysis Ppt PowerPoint Presentation Icon Backgrounds PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Presenting Software Services Business Profile SWOT Analysis Ppt PowerPoint Presentation Icon Backgrounds PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Software Products And Solutions Firm Details SWOT Analysis Icons PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Presenting Software Products And Solutions Firm Details SWOT Analysis Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Software Development Company Profile SWOT Analysis Infographics PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Presenting Business Software Development Company Profile SWOT Analysis Infographics PDF to provide visual cues and insights. Share and navigate important information on fpour stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Dashboard For Concurrent Computing Tracking Ppt Visual Aids Ideas PDF
picts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details. Deliver an awe inspiring pitch with this creative dashboard for concurrent computing tracking ppt visual aids ideas pdf bundle. Topics like dashboard for concurrent computing tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Distributed Computing Dashboard For Edge Computing Tracking Brochure PDF
This slide depicts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details.Deliver and pitch your topic in the best possible manner with this Distributed Computing Dashboard For Edge Computing Tracking Brochure PDF Use them to share invaluable insights on Device Recommendation, Most Prevalent, Device Recommendation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf
This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc. Showcasing this set of slides titled Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf. The topics addressed in these templates are Risk Assessment, Cybersecurity Governance, Access Controls. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc.
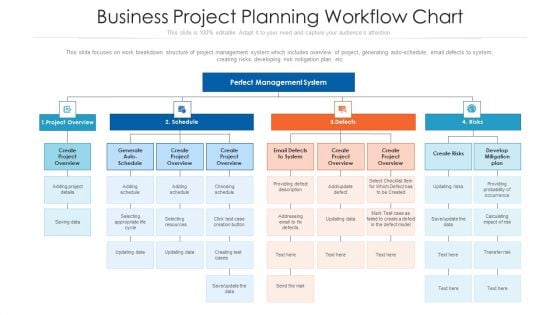
Business Project Planning Workflow Chart Ppt PowerPoint Presentation Gallery Design Inspiration PDF
This slide focuses on work breakdown structure of project management system which includes overview of project, generating auto-schedule, email defects to system, creating risks, developing risk mitigation plan, etc. Presenting business project planning workflow chart ppt powerpoint presentation gallery design inspiration pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including schedule, defects, risks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
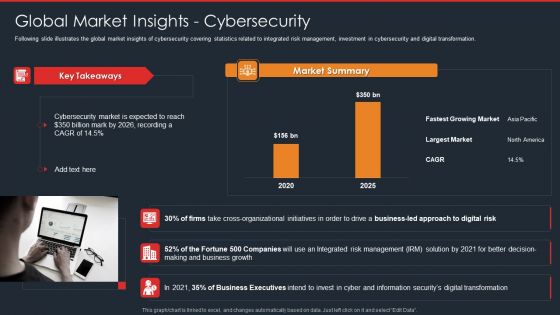
Data Safety Initiatives Global Market Insights Cybersecurity Rules PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver and pitch your topic in the best possible manner with this data safety initiatives global market insights cybersecurity rules pdf. Use them to share invaluable insights on cybersecurity market, market summary, cross organizational initiatives, digital risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
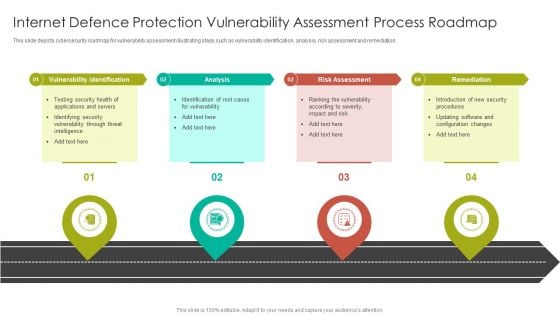
Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF
This slide depicts cybersecurity roadmap for vulnerability assessment illustrating steps such as vulnerability identification, analysis, risk assessment and remediation.Presenting Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vulnerability Identification, Risk Assessment, Remediation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
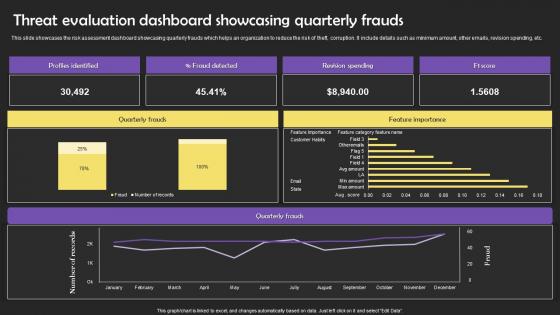
Threat Evaluation Dashboard Showcasing Quarterly Frauds Slides Pdf
This slide showcases the risk assessment dashboard showcasing quarterly frauds which helps an organization to reduce the risk of theft, corruption. It include details such as minimum amount, other emails, revision spending, etc. Pitch your topic with ease and precision using this Threat Evaluation Dashboard Showcasing Quarterly Frauds Slides Pdf This layout presents information on Threat Evaluation Dashboard Showcasing Quarterly Frauds Slides Pdf It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the risk assessment dashboard showcasing quarterly frauds which helps an organization to reduce the risk of theft, corruption. It include details such as minimum amount, other emails, revision spending, etc.
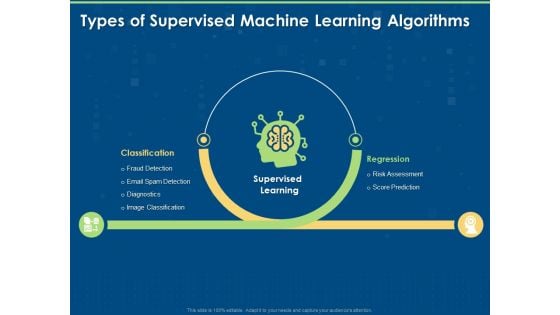
Artificial Intelligence Machine Learning Deep Learning Types Of Supervised Machine Learning Algorithms Ppt PowerPoint Presentation Outline Topics PDF
Presenting this set of slides with name artificial intelligence machine learning deep learning types of supervised machine learning algorithms ppt powerpoint presentation outline topics pdf. This is a two stage process. The stages in this process are classification, risk assessment, regression, supervised learning, risk assessment, score prediction, fraud detection, email spam detection, diagnostics, image classification. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
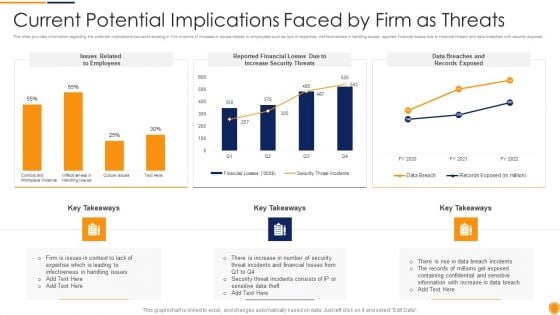
Mitigating Cybersecurity Threats And Vulnerabilities Current Potential Implications Formats PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities current potential implications formats pdf bundle. Topics like employees, increase security threats, data breaches and records exposed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
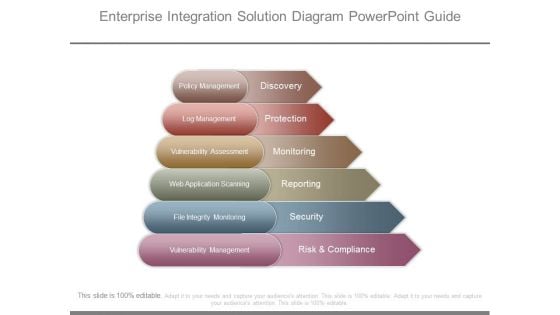
Enterprise Integration Solution Diagram Powerpoint Guide
This is a enterprise integration solution diagram powerpoint guide. This is a six stage process. The stages in this process are policy management, log management, vulnerability assessment, web application scanning, file integrity monitoring, vulnerability management, discovery, protection, monitoring, reporting, security, risk and compliance.
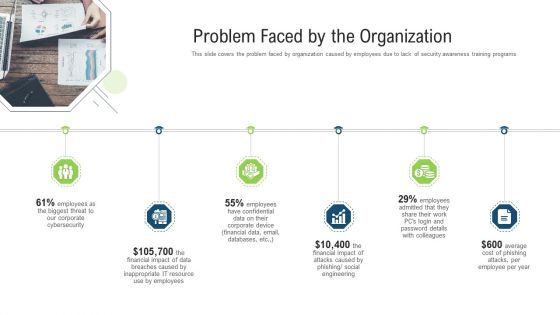
Problem Faced By The Organization Ppt Styles Layouts PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. Presenting problem faced by the organization ppt styles layouts pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like financial impact, email databases, financial data, average. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Present like a pro with Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
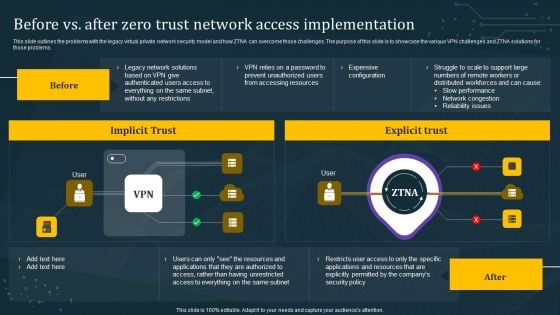
Before Vs After Zero Trust Network Access Implementation Background PDF
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Before Vs After Zero Trust Network Access Implementation Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
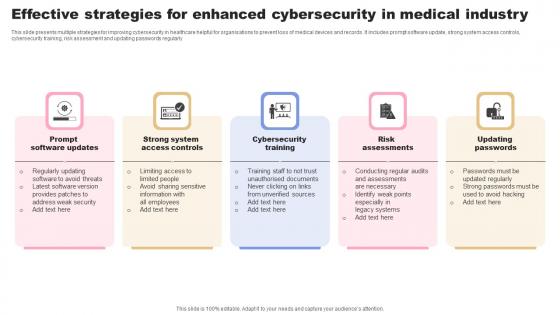
Effective Strategies For Enhanced Cybersecurity In Medical Industry Brochure Pdf
This slide presents multiple strategies for improving cybersecurity in healthcare helpful for organisations to prevent loss of medical devices and records. It includes prompt software update, strong system access controls, cybersecurity training, risk assessment and updating passwords regularly Pitch your topic with ease and precision using this Effective Strategies For Enhanced Cybersecurity In Medical Industry Brochure Pdf. This layout presents information on Cybersecurity Training, Risk Assessments, Updating Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple strategies for improving cybersecurity in healthcare helpful for organisations to prevent loss of medical devices and records. It includes prompt software update, strong system access controls, cybersecurity training, risk assessment and updating passwords regularly
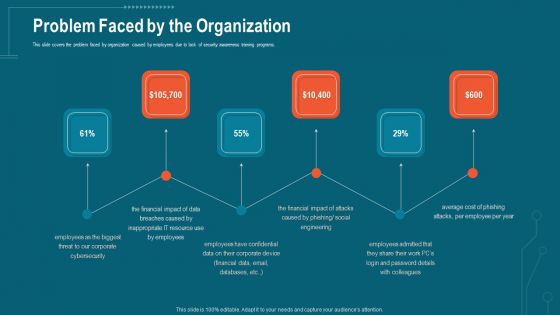
Companys Data Safety Recognition Problem Faced By The Organization Portrait PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a companys data safety recognition problem faced by the organization portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, financial impact, resource, social engineering, cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Communication Infrastructure Services Download PDF
The following slide demonstrates information and communication technology infrastructure services for optimizing output, mitigate internal and external security threat. It includes components such as operations and network management etc. Persuade your audience using this IT Communication Infrastructure Services Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Applications, Description, Operations Management . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Reverse Proxy Web Server Problems Faced By Company Ppt Slides Icons PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Reverse Proxy Web Server Problems Faced By Company Ppt Slides Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Reverse Proxy Web Server Problems Faced By Company Ppt Slides Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Digital Application Software Development Business Profile SWOT Analysis Structure PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth This Digital Application Software Development Business Profile SWOT Analysis Structure PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Digital Products Company Outline SWOT Analysis Diagrams PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Find highly impressive Digital Products Company Outline SWOT Analysis Diagrams PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Products Company Outline SWOT Analysis Diagrams PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
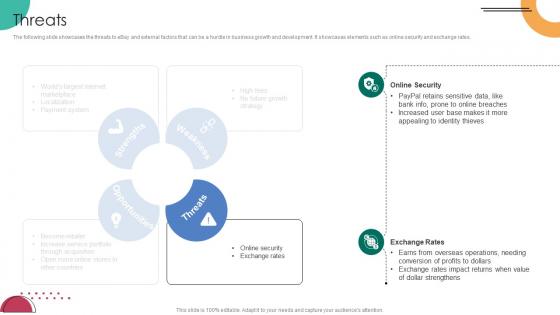
Threats C2C Ecommerce Platform Company Profile CP SS V
The following slide showcases the threats to eBay and external factors that can be a hurdle in business growth and development. It showcases elements such as online security and exchange rates.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Threats C2C Ecommerce Platform Company Profile CP SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Threats C2C Ecommerce Platform Company Profile CP SS V. The following slide showcases the threats to eBay and external factors that can be a hurdle in business growth and development. It showcases elements such as online security and exchange rates.
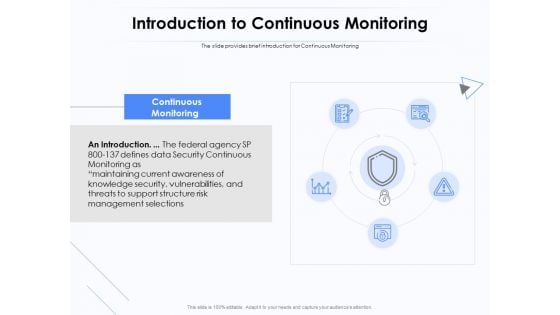
Network Monitoring Tool Overview Introduction To Continuous Monitoring Ppt PowerPoint Presentation Model Slide Download PDF
Presenting this set of slides with name network monitoring tool overview introduction to continuous monitoring ppt powerpoint presentation model slide download pdf. This is a five stage process. The stages in this process are continuous monitoring, introduction, data security, support structure, risk management selections, knowledge security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
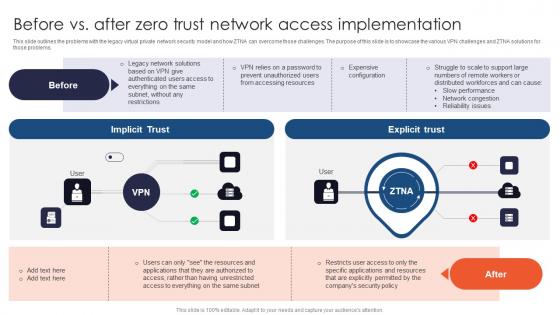
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.
Cybersecurity Threat Management Activities Tracking Dashboard Pictures PDF
This slide provides details regarding cybersecurity threat management activities tracking dashboard in terms of breach risk trends, risk issues by owner, breach likelihood, etc. Want to ace your presentation in front of a live audience Our Cybersecurity Threat Management Activities Tracking Dashboard Pictures PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
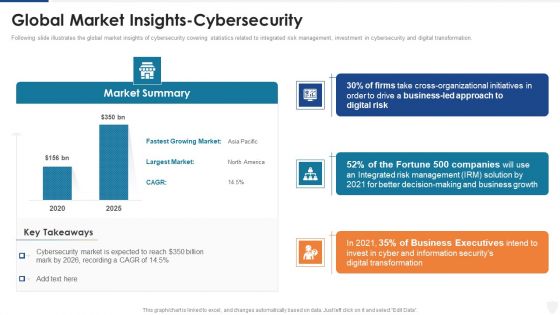
Global Market Insights Cybersecurity Ppt Infographic Template Diagrams PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Presenting global market insights cybersecurity ppt infographic template diagrams pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like risk management, growth, organizational, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Estate Development Project Prioritization Slide Download PDF
The following slide exhibits various types of cybersecurity risk faced by the real estate company. Ransomware, phishing, web-based attack and business email compromise are some of the major risks which are mentioned in the slide.Deliver and pitch your topic in the best possible manner with this Real Estate Development Project Prioritization Slide Download PDF. Use them to share invaluable insights on Ransomware, Phishing, Management Response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
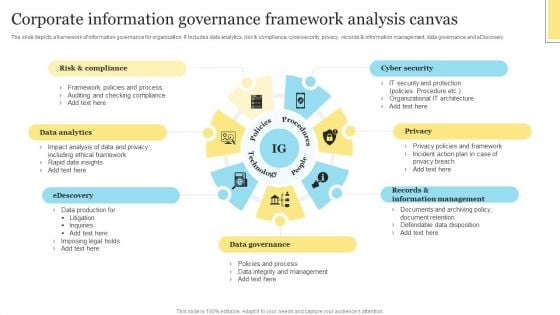
Corporate Information Governance Framework Analysis Canvas Clipart PDF
The slide depicts a framework of information governance for organization. It includes data analytics, risk and compliance, cybersecurity, privacy, records and information management, data governance and eDiscovery. Persuade your audience using this Corporate Information Governance Framework Analysis Canvas Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Compliance, Data Analytics, Edescovery. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
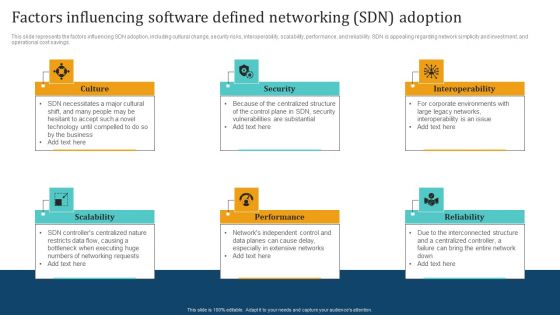
Empowering Network Agility Through SDN Factors Influencing Software Defined Networking SDN Adoption Slides PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Empowering Network Agility Through SDN Factors Influencing Software Defined Networking SDN Adoption Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Empowering Network Agility Through SDN Factors Influencing Software Defined Networking SDN Adoption Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
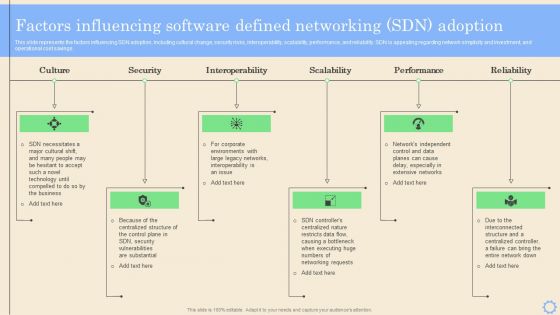
Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Zero Trust Network Access Implementation Challenges Rules PDF
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Implementation Challenges Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Implementation Challenges Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Implementation Challenges Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Factors Influencing Software Defined Networking SDN Adoption Ppt Portfolio Pictures PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged Factors Influencing Software Defined Networking SDN Adoption Ppt Portfolio Pictures PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
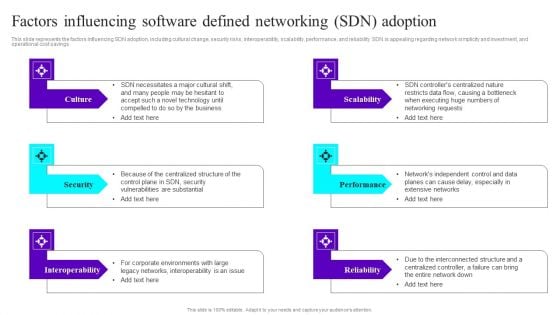
Factors Influencing Software Defined Networking SDN Adoption Ppt Summary Grid PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged Factors Influencing Software Defined Networking SDN Adoption Ppt Summary Grid PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
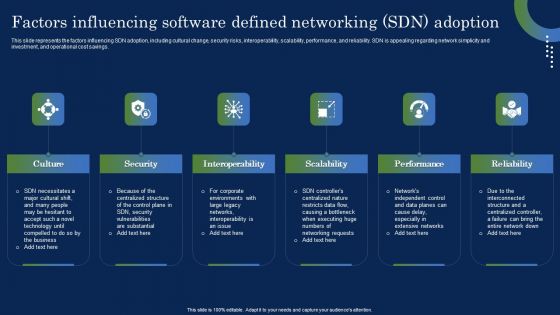
Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
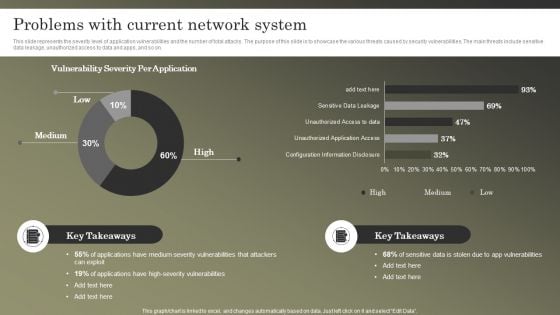
Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
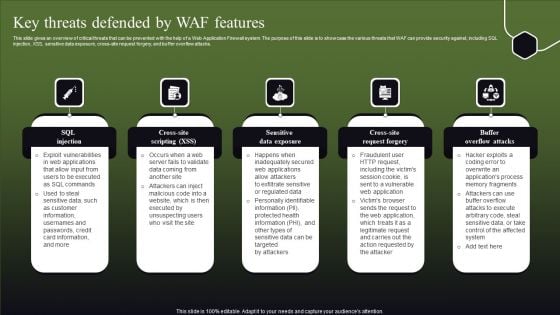
Key Threats Defended By WAF Features Ppt Pictures Elements PDF
This slide gives an overview of critical threats that can be prevented with the help of a Web Application Firewall system. The purpose of this slide is to showcase the various threats that WAF can provide security against, including SQL injection, XSS, sensitive data exposure, cross-site request forgery, and buffer overflow attacks. Explore a selection of the finest Key Threats Defended By WAF Features Ppt Pictures Elements PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Threats Defended By WAF Features Ppt Pictures Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Mitigating Cybersecurity Threats And Vulnerabilities Budget For Effective Threat Ideas PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities budget for effective threat ideas pdf bundle. Topics like incident management, risk management, client onboarding process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Small Business Venture Company Profile Strategic Approach To Improve Client Base Pictures PDF
This slide focuses on strategic approach to improve client base which represents investment in hardware, software, network resources and other latest technologies by delivering risk assessment solutions, support to personnel, etc.This is a Small Business Venture Company Profile Strategic Approach To Improve Client Base Pictures PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Potential Vulnerabilities, Adopted Security, Incorporate Cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
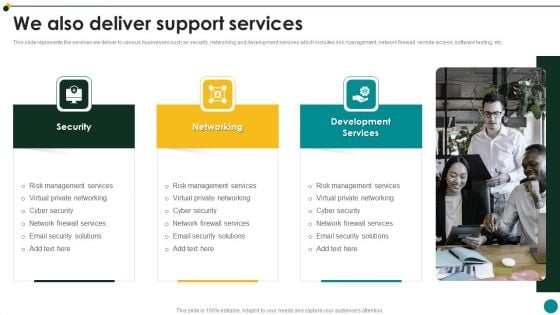
IT Services And Consulting Company Profile We Also Deliver Support Services Guidelines PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a IT Services And Consulting Company Profile We Also Deliver Support Services Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Virtual Private Networking, Management Services You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Solutions Business Profile We Also Deliver Support Services Clipart PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a Information Technology Solutions Business Profile We Also Deliver Support Services Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Private Networking, Network Firewall. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
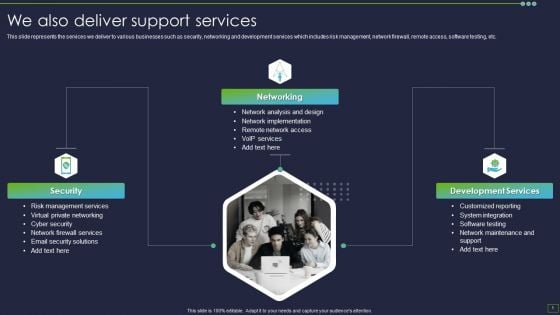
IT Consultancy Services Company Profile We Also Deliver Support Services Structure PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a IT Consultancy Services Company Profile We Also Deliver Support Services Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Services, Management Services, Network Implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































