Cyber Security Roadmap

New Website Launch Strategy Web Bug Testing For Improving Virtual Sales Clipart PDF
Mentioned slide provides insights into various testing strategies which can be implemented by web developers to deploy bug free applications. It includes testing strategies such as cross browser, accessibility, HTML and CSS, web security login, performance, and beta testing. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. New Website Launch Strategy Web Bug Testing For Improving Virtual Sales Clipart PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
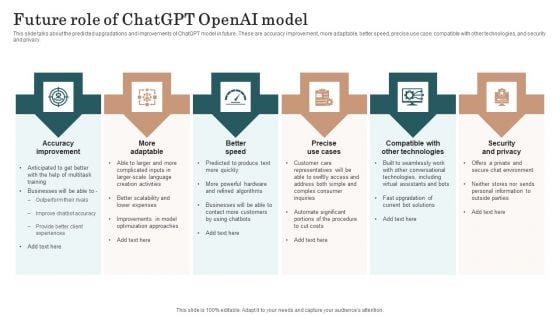
Chatgpt Incorporation Into Web Apps Future Role Of Chatgpt Openai Model Topics PDF
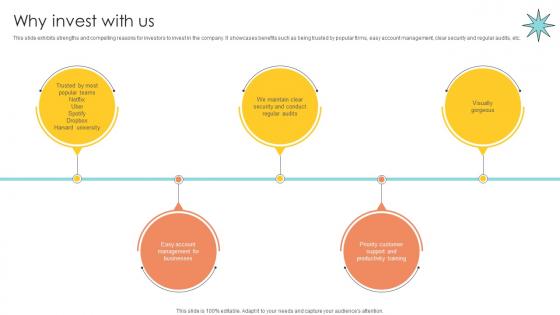
Why Invest With Us Email Management Technology Pitch Deck
This slide exhibits strengths and compelling reasons for investors to invest in the company. It showcases benefits such as being trusted by popular firms, easy account management, clear security and regular audits, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Why Invest With Us Email Management Technology Pitch Deck from Slidegeeks and deliver a wonderful presentation. This slide exhibits strengths and compelling reasons for investors to invest in the company. It showcases benefits such as being trusted by popular firms, easy account management, clear security and regular audits, etc.
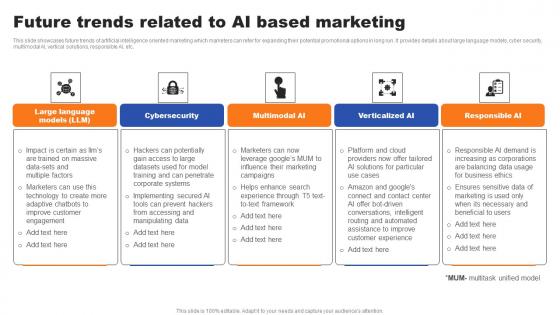
Future Trends Related To AI Based Marketing Ppt File Infographic Template Pdf
This slide showcases future trends of artificial intelligence oriented marketing which marketers can refer for expanding their potential promotional options in long run. It provides details about large language models, cyber security, multimodal AI, vertical solutions, responsible AI, etc. Get a simple yet stunning designed Future Trends Related To AI Based Marketing Ppt File Infographic Template Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Future Trends Related To AI Based Marketing Ppt File Infographic Template Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases future trends of artificial intelligence oriented marketing which marketers can refer for expanding their potential promotional options in long run. It provides details about large language models, cyber security, multimodal AI, vertical solutions, responsible AI, etc.
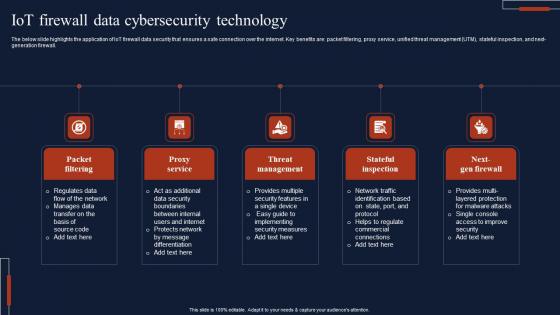
IOT Firewall Data Cybersecurity Technology Brochure Pdf
The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall. Showcasing this set of slides titled IOT Firewall Data Cybersecurity Technology Brochure Pdf The topics addressed in these templates are Packet Filtering, Proxy Service, Threat Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall.

Technology Trends In Online Insurance Essential Personnel Required For Digital Transformation Team
The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business or technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Technology Trends In Online Insurance Essential Personnel Required For Digital Transformation Team from Slidegeeks and deliver a wonderful presentation. The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business or technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists.
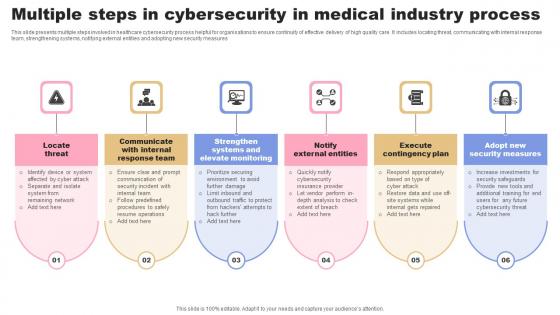
Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf
This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures Pitch your topic with ease and precision using this Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf This layout presents information on Locate Threat, Response Team, Elevate Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures
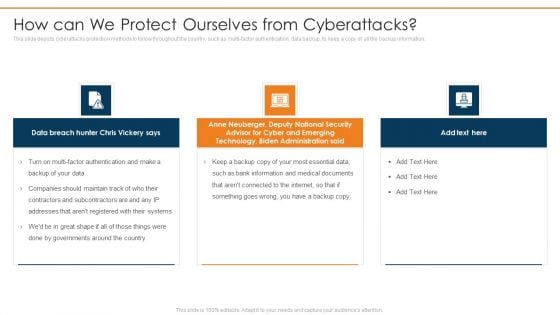
Data Wiper Spyware Attack How Can We Protect Ourselves From Cyberattacks Infographics PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information.This is a data wiper spyware attack how can we protect ourselves from cyberattacks infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like anne neuberger, advisor for cyber and emerging, technology, biden administration You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
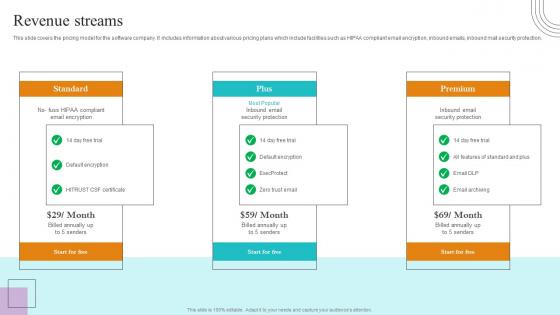
Revenue Streams Paubox Capital Funding Pitch Deck Structure Pdf
This slide covers the pricing model for the software company. It includes information about various pricing plans which include facilities such as HIPAA compliant email encryption, inbound emails, inbound mail security protection. The Revenue Streams Paubox Capital Funding Pitch Deck Structure Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers the pricing model for the software company. It includes information about various pricing plans which include facilities such as HIPAA compliant email encryption, inbound emails, inbound mail security protection.

Web Consulting Business Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. The Web Consulting Business Estimated Annual Budget Plan For Web Company is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
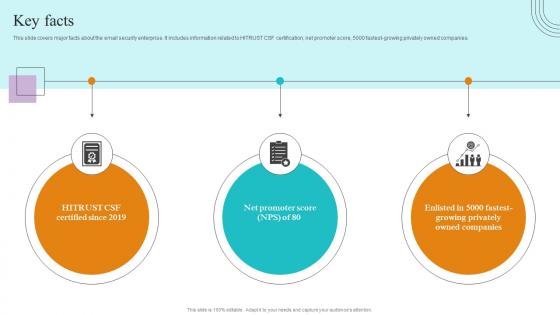
Key Facts Paubox Capital Funding Pitch Deck Graphics Pdf
This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest growing privately owned companies. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Facts Paubox Capital Funding Pitch Deck Graphics Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest growing privately owned companies.

Data Wiper Spyware Attack Information And Technology Army Of Ukraine Structure PDF
This slide represents the information and technology army of Ukraine, a Telegram group against Russia. In total, 308,000 users have joined this group to help Ukraine mitigate Russian cyber attacks.This is a data wiper spyware attack information and technology army of ukraine structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like prevent misinformation, provide factual information, russian residents You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Monitoring Plan Steps In Detail Aligning The Incident Management Policies Sample PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Aligning the Incident Management Policies and Plan. Presenting cybersecurity monitoring plan steps in detail aligning the incident management policies sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security monitoring solutions, ongoing management, incident logging, incident categorization, incident prioritization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
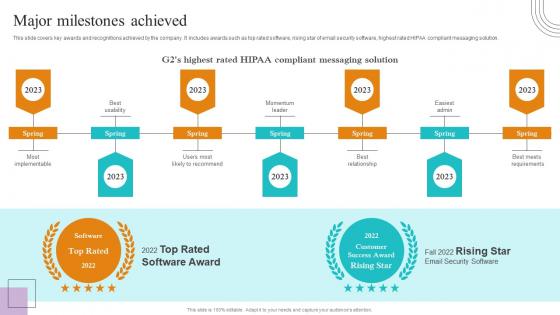
Major Milestones Achieved Paubox Capital Funding Pitch Deck Inspiration Pdf
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Milestones Achieved Paubox Capital Funding Pitch Deck Inspiration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.
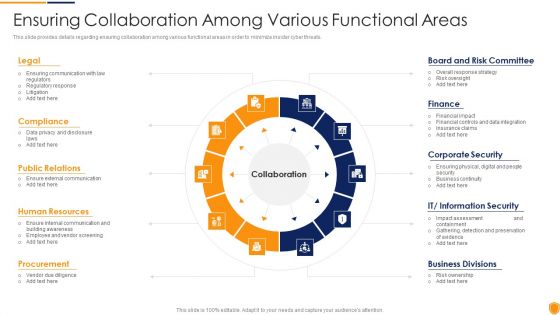
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Collaboration Among Elements PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting mitigating cybersecurity threats and vulnerabilities ensuring collaboration among elements pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like compliance, public relations, human resources, procurement, board and risk committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
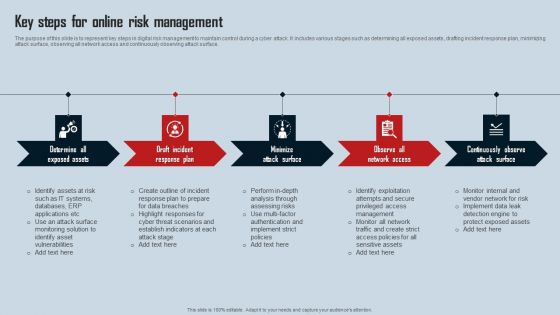
Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF
The slide showcases the interconnected functions of a framework used to guide the organizations security measures. It covers identify, protect, detect, respond and recover. Presenting Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify, Protect, Detect. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Mobile Cloud Computing Challenges And Solutions Application Areas Of Mobile Cloud Computing
The given slide highlights the various challenges associated with mobile cloud computing along with desired solutions and impacts. The issues include less network bandwidth, network connectivity, and security concern. Retrieve professionally designed Mobile Cloud Computing Challenges And Solutions Application Areas Of Mobile Cloud Computing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The given slide highlights the various challenges associated with mobile cloud computing along with desired solutions and impacts. The issues include less network bandwidth, network connectivity, and security concern

Cybersecurity Risk Scorecard 30 60 90 Days Plan Topics PDF
This is a cybersecurity risk scorecard 30 60 90 days plan topics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 8 essential information security risk scorecard for organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
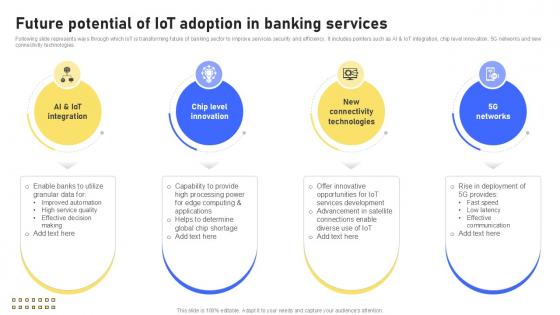
Future Potential Of IoT Adoption Banking Future With IoT Ppt Presentation IoT SS V
Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies. There are so many reasons you need a Future Potential Of IoT Adoption Banking Future With IoT Ppt Presentation IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies.

Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf
This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty.
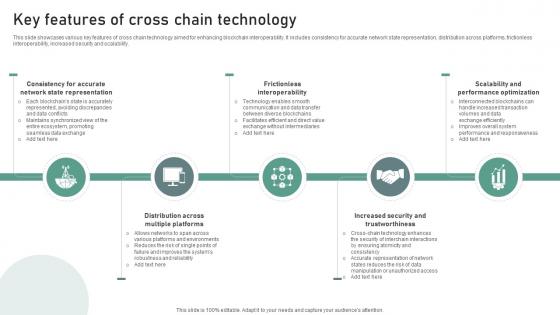
Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Slidegeeks has constructed Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.
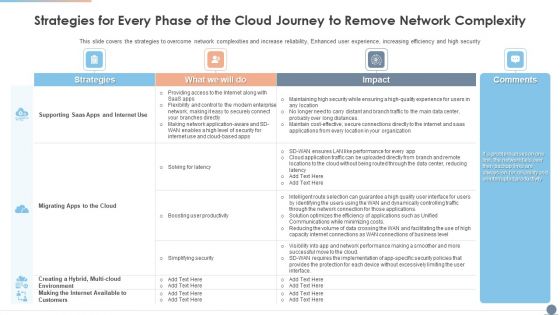
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Deliver and pitch your topic in the best possible manner with this Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF. Use them to share invaluable insights on Environment, Strategies, Productivity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
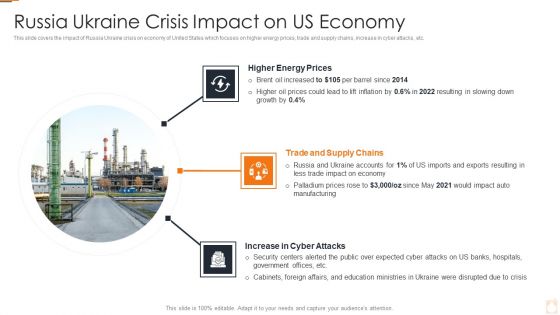
Ukraine Russia Conflict Effect On Petroleum Industry Russia Ukraine Crisis Summary PDF
This slide covers the impact of Russia Ukraine crisis on economy of United States which focuses on higher energy prices, trade and supply chains, increase in cyber attacks, etc.Presenting Ukraine Russia Conflict Effect On Petroleum Industry Russia Ukraine Crisis Summary PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Russian Crude Oil Exports To China In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF
This slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
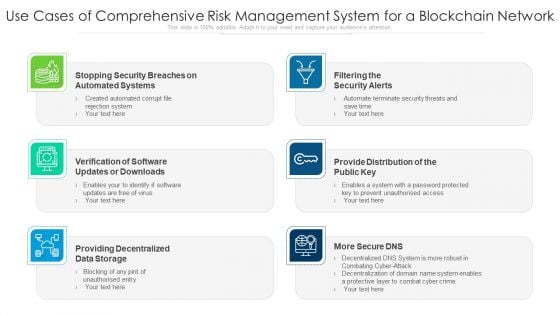
Use Cases Of Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Outline Background Designs PDF
Presenting use cases of comprehensive risk management system for a blockchain network ppt powerpoint presentation outline background designs pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including filtering the security alerts, provide distribution of the public key, providing decentralized data storage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
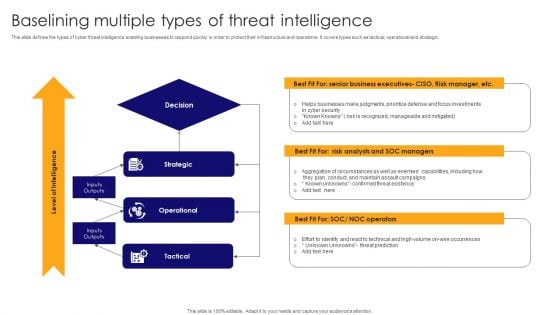
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
SIEM Integrations SIEM Services Ppt Icon Graphic Tips PDF
Presenting siem integrations siem services ppt icon graphic tips pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
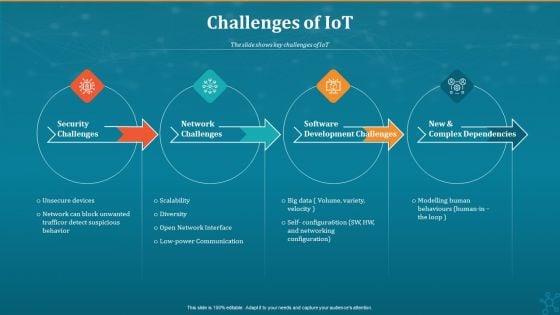
Machine To Machine Communication Challenges Of Iot Professional PDF
The slide shows key challenges of IoT.Presenting machine to machine communication challenges of iot professional pdf. to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security challenges, network challenges, software development challenges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
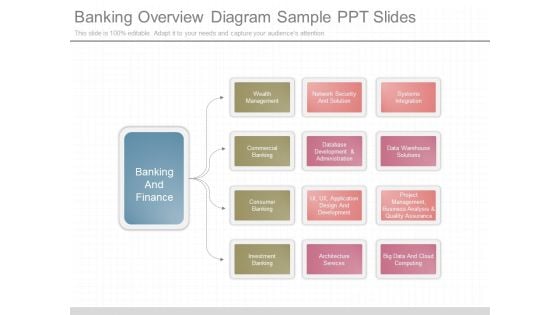
Banking Overview Diagram Sample Ppt Slides
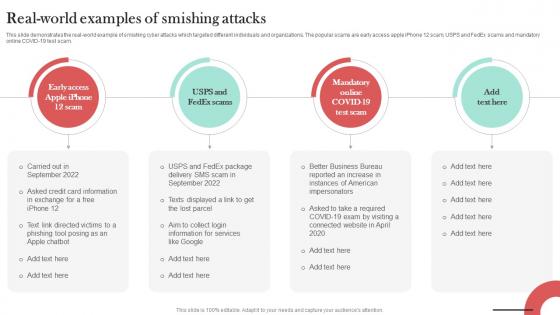
Real World Examples Of Smishing Attacks Man In The Middle Phishing IT
This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Real World Examples Of Smishing Attacks Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Real World Examples Of Smishing Attacks Man In The Middle Phishing IT today and make your presentation stand out from the rest This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam.

Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc.
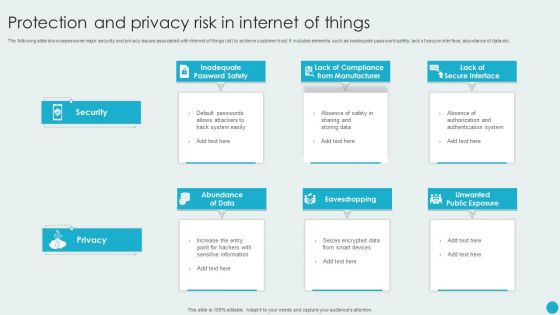
Protection And Privacy Risk In Internet Of Things Topics PDF
The following slide showcases some major security and privacy issues associated with internet of things iot to achieve customer trust. It includes elements such as inadequate password safety, lack of secure interface, abundance of data etc. Presenting Protection And Privacy Risk In Internet Of Things Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Abundance Of Data, Eavesdropping, Unwanted Public Exposure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
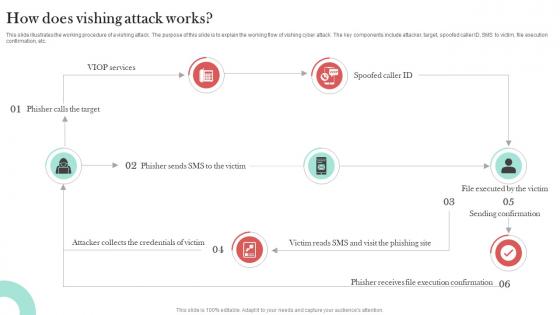
How Does Vishing Attack Works Man In The Middle Phishing IT
This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc. The How Does Vishing Attack Works Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc.
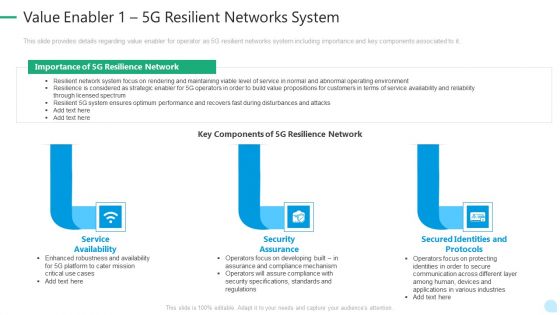
5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Value Enabler 1 5G Resilient Networks System Professional PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Value Enabler 1 5G Resilient Networks System Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Availability, Security Assurance, Secured Identities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names.

Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues. If you are looking for a format to display your unique thoughts, then the professionally designed Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues.

Emerging Technology Trends For Business Growth Diagrams PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Emerging Technology Trends For Business Growth Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Emerging Technology Trends For Business Growth Diagrams PDF.
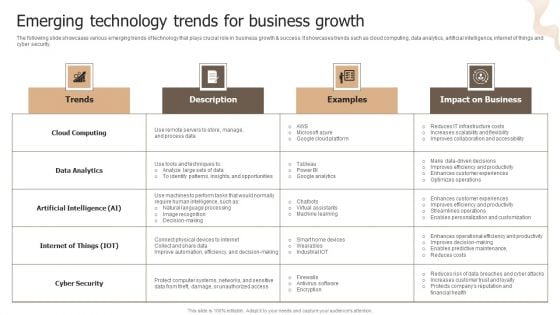
Designing Strategies For Company Growth And Success Emerging Technology Trends For Business Growth Introduction PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. This Designing Strategies For Company Growth And Success Emerging Technology Trends For Business Growth Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Designing Strategies For Company Growth And Success Emerging Technology Trends For Business Growth Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Strategic Brand Growth Plan For Market Leadership Emerging Technology Trends For Business Background PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. Do you know about Slidesgeeks Strategic Brand Growth Plan For Market Leadership Emerging Technology Trends For Business Background PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
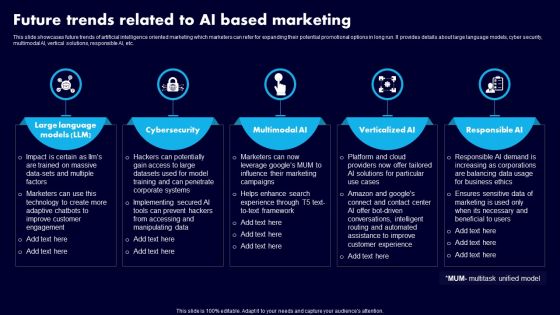
Future Trends Related To AI Based Marketing Ppt Slides Files PDF
This slide showcases future trends of artificial intelligence oriented marketing which marketers can refer for expanding their potential promotional options in long run. It provides details about large language models, cyber security, multimodal AI, vertical solutions, responsible AI, etc. Get a simple yet stunning designed Future Trends Related To AI Based Marketing Ppt Slides Files PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Future Trends Related To AI Based Marketing Ppt Slides Files PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
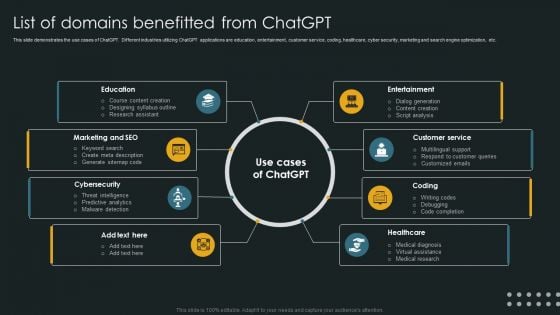
List Of Domains Benefitted From Chatgpt Slides PDF
This slide demonstrates the use cases of ChatGPT. Different industries utilizing ChatGPT applications are education, entertainment, customer service, coding, healthcare, cyber security, marketing and search engine optimization, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give List Of Domains Benefitted From Chatgpt Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable List Of Domains Benefitted From Chatgpt Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic Summary PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring Network Traffic. Presenting cybersecurity monitoring plan steps in detail monitoring network traffic summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like inbound and outbound traffic, could indicate attacks, unusual network traffic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
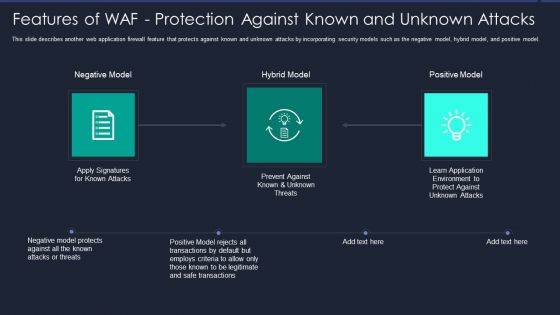
Web App Firewall Services IT Features Of WAF Protection Against Known Clipart PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting web app firewall services it features of waf protection against known clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like negative model, hybrid model, positive model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
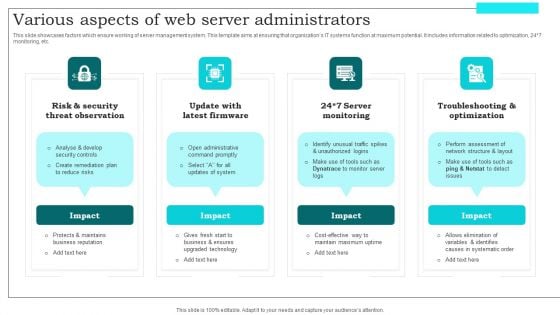
Various Aspects Of Web Server Administrators Themes PDF
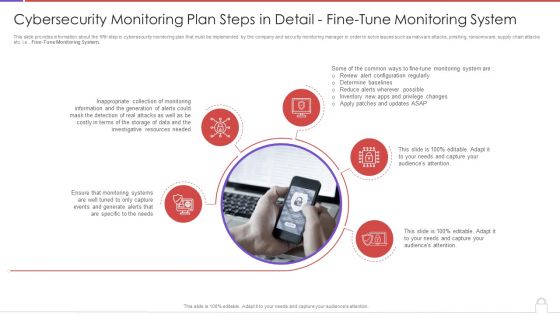
Cybersecurity Monitoring Plan Steps In Detail Fine Tune Monitoring System Slides PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Fine-Tune Monitoring System. Presenting cybersecurity monitoring plan steps in detail fine tune monitoring system slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like inappropriate collection, monitoring information, investigative resources needed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Monitoring User Activity Guidelines PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring User Activity. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring user activity guidelines pdf bundle. Topics like action information, user information, monitoring capability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Providing Resilient And Synchronized Timing Background PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring plan steps in detail providing resilient and synchronized timing background pdf. Use them to share invaluable insights on monitoring and analysis, incident response, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
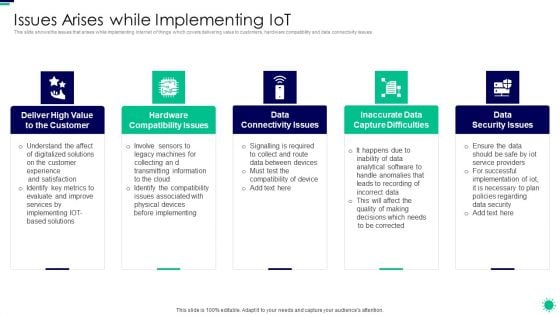
Purpose Digital Twin Internet Things Reducing Costs After COVID Era Issues Arises While Implementing Diagrams PDF
This slide shows the issues that arises while implementing internet of things which covers delivering value to customers, hardware compatibility and data connectivity issues. This is a purpose digital twin internet things reducing costs after covid era issues arises while implementing diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like high value, compatibility issues, connectivity issues, capture difficulties, security issues . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
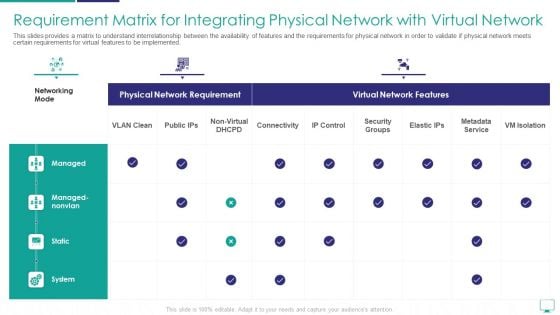
Requirement Matrix For Integrating Physical Network With Virtual Network Sample PDF
This slides provides a matrix to understand interrelationship between the availability of features and the requirements for physical network in order to validate if physical network meets certain requirements for virtual features to be implemented.Deliver an awe inspiring pitch with this creative requirement matrix for integrating physical network with virtual network sample pdf bundle. Topics like metadata service, security groups, managed nonvlan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
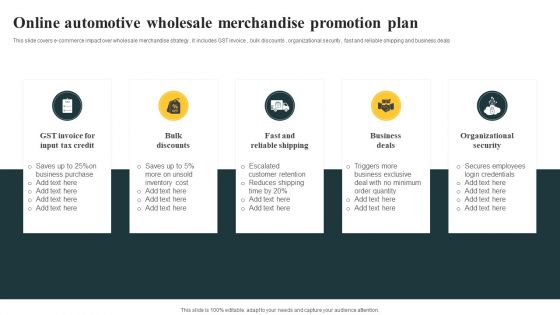
Online Automotive Wholesale Merchandise Promotion Plan Slides PDF
This slide covers e commerce impact over wholesale merchandise strategy . it includes GST invoice , bulk discounts , organizational security , fast and reliable shipping and business deals. Presenting Online Automotive Wholesale Merchandise Promotion Plan Slides PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Merchandise Promotion Plan, Drive Target Audience. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































