Cyber Security Strategy
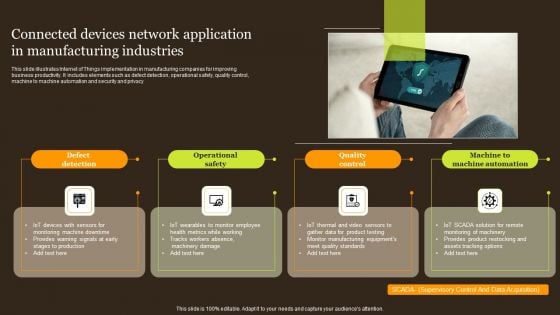
Connected Devices Network Application In Manufacturing Industries Portrait PDF
This slide illustrates Internet of Things implementation in manufacturing companies for improving business productivity. It includes elements such as defect detection, operational safety, quality control, machine to machine automation and security and privacy. Presenting Connected Devices Network Application In Manufacturing Industries Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Defect Detection, Operational Safety, Quality Control . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cybersecurity Awareness Program To Prevent Attacks Understanding The Frequency And Weightage Topics PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Slidegeeks is here to make your presentations a breeze with Implementing Cybersecurity Awareness Program To Prevent Attacks Understanding The Frequency And Weightage Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
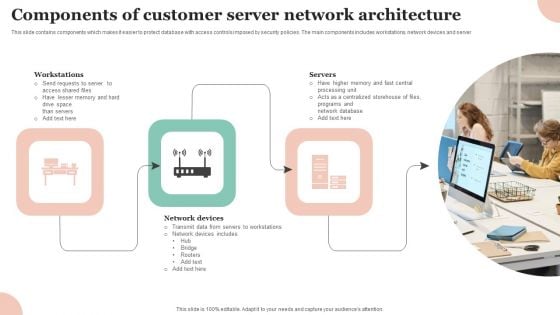
Components Of Customer Server Network Architecture Professional PDF
This slide contains components which makes it easier to protect database with access controls imposed by security policies. The main components includes workstations, network devices and server Persuade your audience using this Components Of Customer Server Network Architecture Professional PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Workstations, Network Devices, Servers . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Features And Disadvantages Of 5Th Generation System Wireless Technology Transformation Diagrams PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Features And Disadvantages Of 5Th Generation System Wireless Technology Transformation Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Use Case Of Online Risk Management For Health Care Sector Background PDF
This slide represents a use case of digital risk management in health care sector to understand its impact. It includes components like goal, issues faced by hospital, risk mitigation action steps and result. Presenting Use Case Of Online Risk Management For Health Care Sector Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Threats, Risk Mitigation Action Steps, Results. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
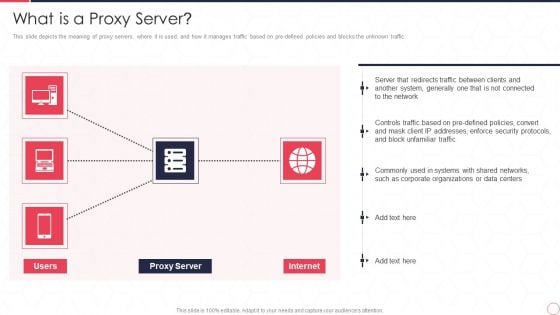
Reverse Proxy Server IT What Is A Proxy Server Ppt Infographics Infographics PDF
This slide depicts the meaning of proxy servers, where it is used, and how it manages traffic based on pre-defined policies and blocks the unknown traffic. This is a reverse proxy server it what is a proxy server ppt infographics infographics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, unfamiliar traffic, enforce security protocols, controls traffic based. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Allocate Team Roles And Responsibilities Ppt PowerPoint Presentation File Show PDF
The following slide showcases the key roles and responsibilities of cyber security team to enhance decision making and goal accomplishment. It includes activities such as developing information security strategies, managing security architecture, planning disaster recovery etc. Slidegeeks is here to make your presentations a breeze with Allocate Team Roles And Responsibilities Ppt PowerPoint Presentation File Show PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
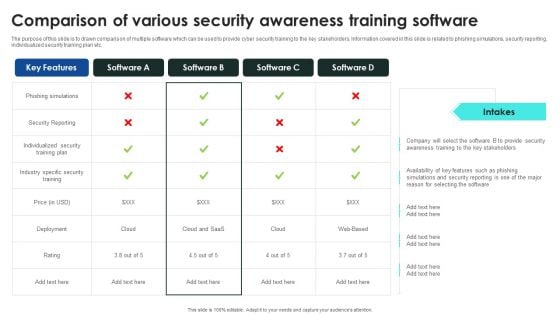
Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Consumer Journey Mapping Techniques Thank You Emails For Better Customer Relationships Elements PDF
This slide covers the benefit of sending thank you emails for building an emotional connection with consumers. It also includes key insights such as improving customers brand perception, honest customer feedback ,etc. Deliver an awe inspiring pitch with this creative Consumer Journey Mapping Techniques Thank You Emails For Better Customer Relationships Elements PDF bundle. Topics like Organizations Customer, Opportunity, Consumer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Initiatives To Produce Effective Concept For Logistic Firm Risks Involved In Technology Formats PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high and Key Strategies or Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this initiatives to produce effective concept for logistic firm risks involved in technology formats pdf. Use them to share invaluable insights on connectivity risk, cyber security risk, inventory management risk, technology risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
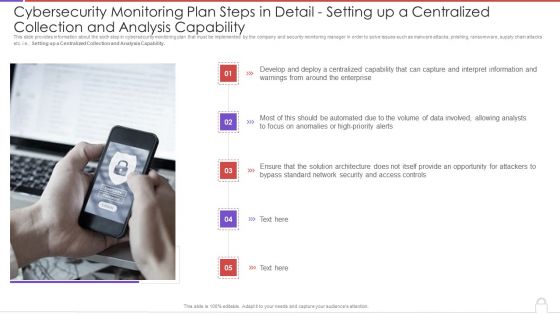
Cybersecurity Monitoring Plan Steps In Detail Setting Up A Centralized Collection And Elements PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Setting up a Centralized Collection and Analysis Capability. This is a cybersecurity monitoring plan steps in detail setting up a centralized collection and elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interpret information, high priority alerts, analysts, access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Operations Cybersecops Dedicated SOC Overview Pros And Cons Guidelines PDF
This slide outlines the overview of dedicated SOC, including its goal and advantages and disadvantages. The purpose of this slide is to showcase the dedicated security operations center covering its benefits and drawbacks. The goal of this SOC center is to monitor information systems around the clock. Create an editable Cybersecurity Operations Cybersecops Dedicated SOC Overview Pros And Cons Guidelines PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cybersecurity Operations Cybersecops Dedicated SOC Overview Pros And Cons Guidelines PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. Presenting Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Tracking Products, Securing Operations, Managing Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Vulnerability Administration Overview Structure PDF
This is a company vulnerability administration overview structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it is a security weakness or flaw of a component in the technology stack of an organization, vulnerabilities may exist on network devices, servers pcs mobile devices applications or any other elements connected to the network, a typical organizations network has many vulnerabilities per device or system therefore even a small organization may have tens of thousands of vulnerabilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Customized Marketing Campaign Through Email And Video Icon Ppt Pictures Shapes PDF
Pitch your topic with ease and precision using this Customized Marketing Campaign Through Email And Video Icon Ppt Pictures Shapes PDF. This layout presents information on Customized Marketing, Campaign Through, Email, Video Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF
This slide explains the working of a reverse proxy server in two ways proxying for load balancing and proxy as a stand-in for a server which is further divided into three parts such as secure client to proxy, secure proxy to content server and secure client to proxy and secure proxy to content server. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF.

Information Gathered For Lead Qualification Process Diagrams PDF
The sales department will generate crucial information of potential lead through webinar by collecting the relevant data from prospective leads such as job title, phone number, name, email address, etc. Deliver and pitch your topic in the best possible manner with this Information Gathered For Lead Qualification Process Diagrams PDF. Use them to share invaluable insights on Determine Targets, Email Marketing Campaign, Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
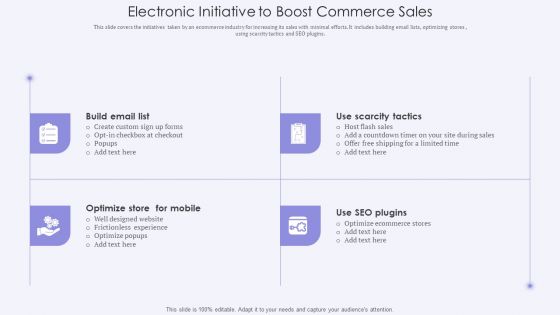
Electronic Initiative To Boost Commerce Sales Structure PDF
This slide covers the initiatives taken by an ecommerce industry for increasing its sales with minimal efforts. It includes building email lists, optimizing stores , using scarcity tactics and SEO plugins. Showcasing this set of slides titled Electronic Initiative To Boost Commerce Sales Structure PDF. The topics addressed in these templates are Optimize Ecommerce, Sales. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
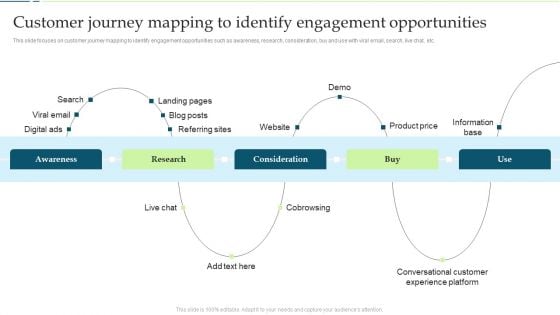
Customer Journey Mapping To Identify Engagement Opportunities Pictures PDF
This slide focuses on customer journey mapping to identify engagement opportunities such as awareness, research, consideration, buy and use with viral email, search, live chat, etc.Deliver an awe inspiring pitch with this creative Customer Journey Mapping To Identify Engagement Opportunities Pictures PDF bundle. Topics like Landing Pages, Referring Sites, Consideration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
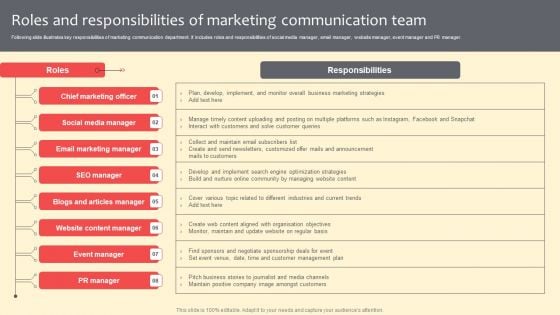
Roles And Responsibilities Of Marketing Communication Team Background PDF
Following slide illustrates key responsibilities of marketing communication department. It includes roles and responsibilities of social media manager, email manager, website manager, event manager and PR manager. There are so many reasons you need a Roles And Responsibilities Of Marketing Communication Team Background PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
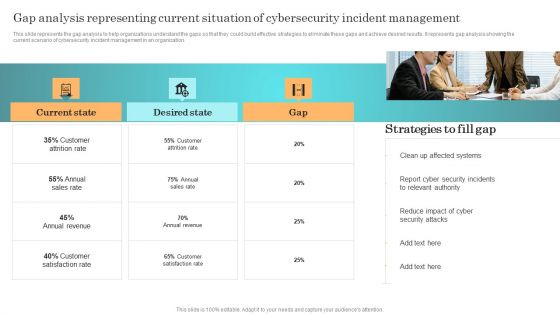
Incident Response Techniques Deployement Gap Analysis Representing Current Situation Of Cybersecurity Designs PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. There are so many reasons you need a Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
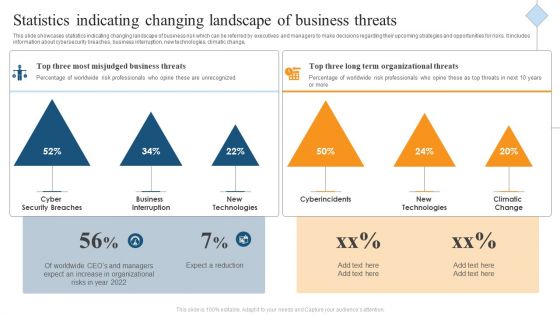
Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF
This slide showcases statistics indicating changing landscape of business risk which can be referred by executives and managers to make decisions regarding their upcoming strategies and opportunities for risks. It includes information about cybersecurity breaches, business interruption, new technologies, climatic change, Persuade your audience using this Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Breaches, Business Interruption, New Technologies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
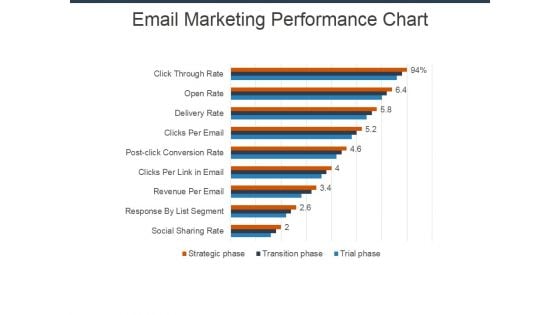
Email Marketing Performance Chart Ppt Powerpoint Presentation Pictures Show
This is a email marketing performance chart ppt powerpoint presentation pictures show. This is a nine stage process. The stages in this process are finance, planning, marketing, business, management, strategy.
Email Marketing Roi Template 2 Ppt Powerpoint Presentation Icon Skills
This is a email marketing roi template 2 ppt powerpoint presentation icon skills. This is a eight stage process. The stages in this process are product, planning, marketing, business, management, strategy.

Email Marketing Ppt PowerPoint Presentation Example File
This is a email marketing ppt powerpoint presentation example file. This is a three stage process. The stages in this process are business, marketing, strategy, analysis, email marketing.
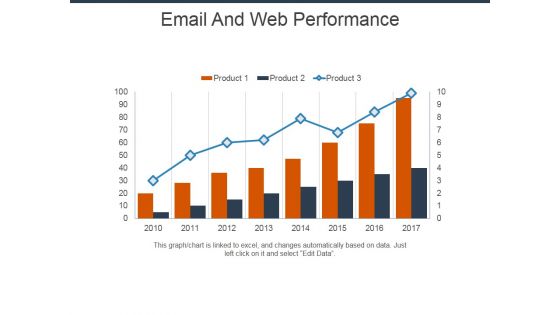
Email And Web Performance Ppt Powerpoint Presentation Summary File Formats
This is a email and web performance ppt powerpoint presentation summary file formats. This is a eight stage process. The stages in this process are marketing, business, management, strategy, process.

Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Email And Marketing Automation Ppt PowerPoint Presentation Icon Slide Download
This is a email and marketing automation ppt powerpoint presentation icon slide download. This is a five stage process. The stages in this process are cta email follow up, nurture email, email break up email, intro email, business.
Monitor Employees Emails Ppt PowerPoint Presentation Infographic Template Sample Cpb
This is a monitor employees emails ppt powerpoint presentation infographic template sample cpb. This is a four stage process. The stages in this process are monitor employees emails.
Automated Email Flow Chart Ppt Powerpoint Presentation Infographics Show
This is a automated email flow chart ppt powerpoint presentation infographics show. This is a three stage process. The stages in this process are check email, achieve, process inbox, do i want replay now, create task in task manager.
Email Client Usage Pattern Ppt Powerpoint Presentation Summary Maker
This is a email client usage pattern ppt powerpoint presentation summary maker. This is a eight stage process. The stages in this process are email client, popularity, subscribers, microsoft outlook.

Email Marketing Metrics Ppt Powerpoint Presentation Outline Sample
This is a email marketing metrics ppt powerpoint presentation outline sample. This is a four stage process. The stages in this process are receive, aware, interest, trial, email marketing activities, metrics, volume, efficiency, speed, cost.
Email Marketing Roi Template 1 Ppt Powerpoint Presentation Outline Template
This is a email marketing roi template 1 ppt powerpoint presentation outline template. This is a four stage process. The stages in this process are email, catalogs, internet displays, product.

Social Media And Email Marketing Ppt PowerPoint Presentation File Model
This is a social media and email marketing ppt powerpoint presentation file model. This is a three stage process. The stages in this process are search engine optimization, social media, email marketing.

Email Marketing Process Ppt Powerpoint Presentation Show Visuals
This is a email marketing process ppt powerpoint presentation show visuals. This is a five stage process. The stages in this process are define, test, send, measure, report.

Email Activity Dashboard Ppt Powerpoint Presentation Styles Summary
This is a email activity dashboard ppt powerpoint presentation styles summary. This is a three stage process. The stages in this process are sent, opens, clicks, visits, unsubscribed, bounced, qualifying campaign.
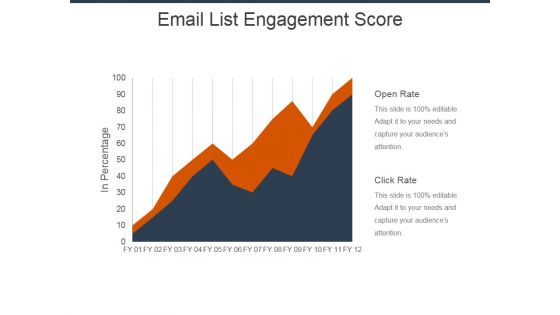
Email List Engagement Score Ppt Powerpoint Presentation Model Design Ideas
This is a email list engagement score ppt powerpoint presentation model design ideas. This is a two stage process. The stages in this process are open rate, click rate, business, management.
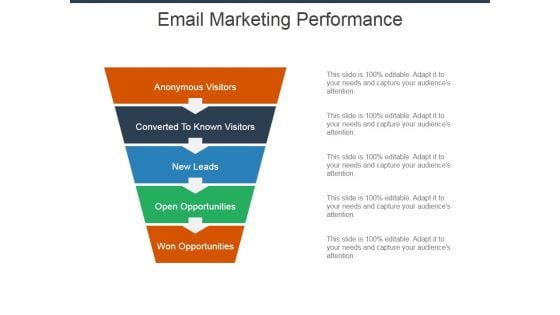
Email Marketing Performance Ppt Powerpoint Presentation Infographics Clipart
This is a email marketing performance ppt powerpoint presentation infographics clipart. This is a five stage process. The stages in this process are anonymous visitors, converted to known visitors, new leads, open opportunities, won opportunities.
Email Marketing Objectives Ppt Powerpoint Presentation Icon Demonstration
This is a email marketing objectives ppt powerpoint presentation icon demonstration. This is a seven stage process. The stages in this process are build brand awareness, enhance customer retention, drive immediate sales, provide company or product information, objectives, build stronger relationships with existing customer clients.

Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
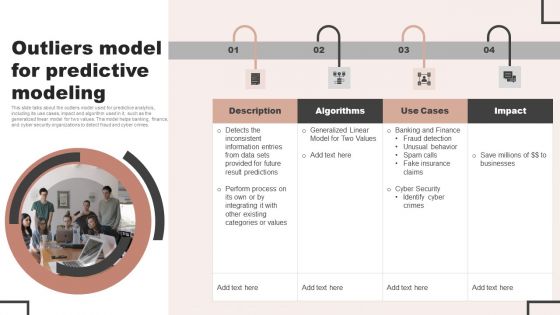
Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Slidegeeks is here to make your presentations a breeze with Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Best Practices For Cybersecurity Incident Management Summary PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Best Practices For Cybersecurity Incident Management Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Best Practices For Cybersecurity Incident Management Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
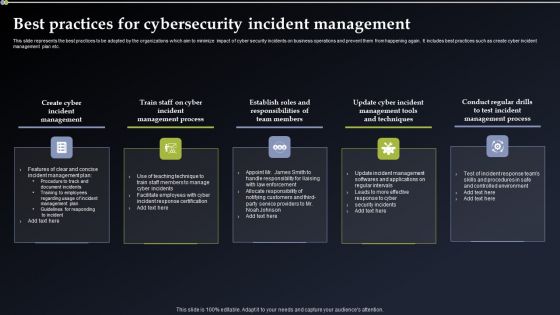
Best Practices For Cybersecurity Incident Management Infographics PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Boost your pitch with our creative Best Practices For Cybersecurity Incident Management Infographics PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Projection Model Outliers Model For Predictive Analytics Topics PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Welcome to our selection of the Projection Model Outliers Model For Predictive Analytics Topics PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

30 60 90 Day Plan Ppt PowerPoint Presentation Model Images
This is a 30 60 90 day plan ppt powerpoint presentation model images. This is a three stage process. The stages in this process are watch product and customer videos, review the opening introductory pitch and related call scripts, review poor follow up emails and good email tips, review and practice current sales pitch, master the sales pitch with different persons and industries.

Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
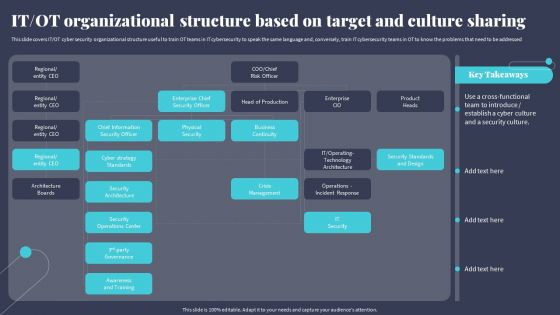
IT OT Organizational Structure Based On Target And Culture Sharing Rules PDF
This slide covers IT OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. Make sure to capture your audiences attention in your business displays with our gratis customizable IT OT Organizational Structure Based On Target And Culture Sharing Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Digital Marketing Development Plan Ppt Example File
This is a digital marketing development plan ppt example file. This is a four stage process. The stages in this process are content, paid organic search, email marketing, social media, analytics implementation, competitive analysis, keyword research.
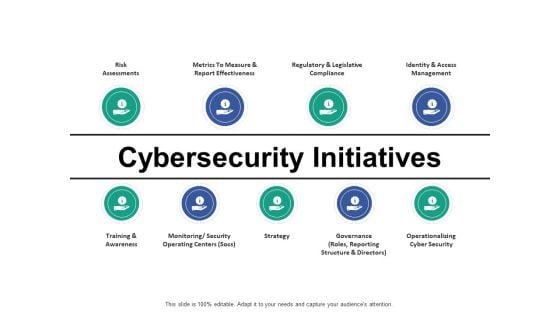
Cybersecurity Initiatives Ppt PowerPoint Presentation Layouts Slideshow
This is a cybersecurity initiatives ppt powerpoint presentation layouts slideshow. This is a nine stage process. The stages in this process are business, management, planning, strategy, marketing.

NIST Cybersecurity Framework Successful Implementation Guide Rules PDF
The slide showcases a guide for the implementation of Nist cyber security framework that help in improving existing capacity of the system or develop a new one. It includes steps like prioritizing and defining scope, identifying and determining a current profile, risk evaluation, target determining, analyzing gaps and implementation stage. Showcasing this set of slides titled NIST Cybersecurity Framework Successful Implementation Guide Rules PDF. The topics addressed in these templates are Define Scope, Current Profile, Risk Evaluation . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Prevention Of Information In House Training Schedule We Will Implement Professional PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Prevention Of Information In House Training Schedule We Will Implement Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
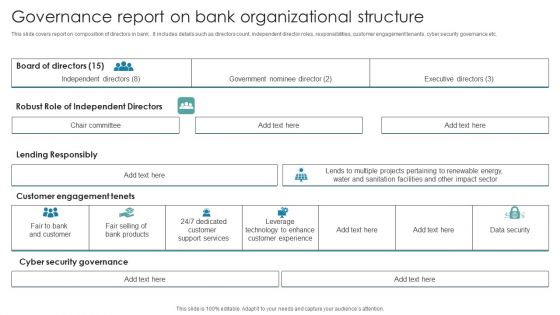
Governance Report On Bank Organizational Structure Slides PDF
This slide covers report on composition of directors in bank . It includes details such as directors count, independent director roles, responsibilities, customer engagement tenants, cyber security governance etc. Showcasing this set of slides titled Governance Report On Bank Organizational Structure Slides PDF. The topics addressed in these templates are Executive Directors, Leverage Technology, Customer Support Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
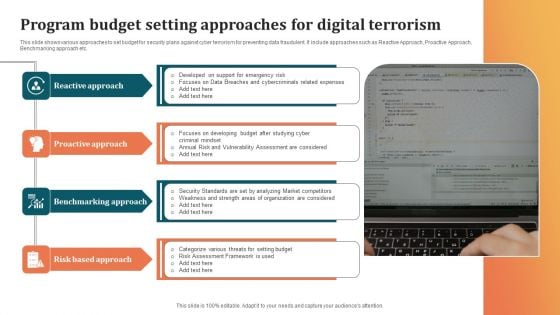
Program Budget Setting Approaches For Digital Terrorism Background PDF
This slide shows various approaches to set budget for security plans against cyber terrorism for preventing data fraudulent. It include approaches such as Reactive Approach, Proactive Approach, Benchmarking approach etc. Presenting Program Budget Setting Approaches For Digital Terrorism Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benchmarking Approach, Risk Based Approach, Proactive Approach. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
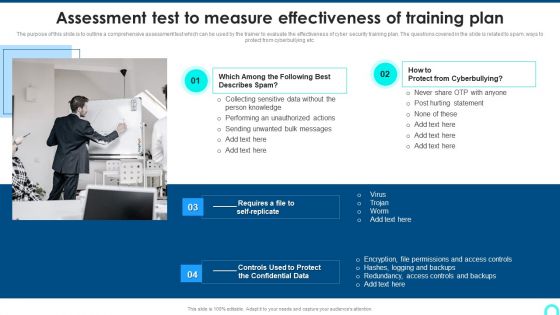
Assessment Test To Measure Effectiveness Of Training Plan Professional PDF
purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Presenting Assessment Test To Measure Effectiveness Of Training Plan Professional PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Collecting Sensitive, Performing Unauthorized, Hurting Statement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
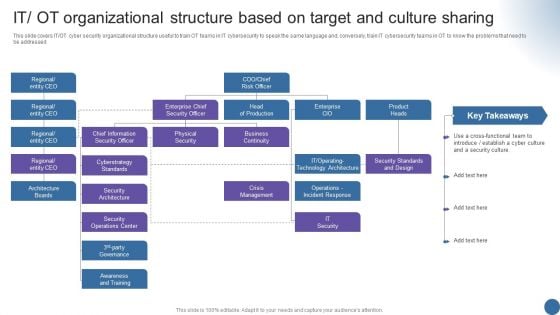
IT OT Organizational Structure Based On Managing Organizational Transformation Designs PDF
This slide covers IT OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. Deliver and pitch your topic in the best possible manner with this IT OT Organizational Structure Based On Managing Organizational Transformation Designs PDF. Use them to share invaluable insights on Organizational Structure, Target, Culture Sharing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Marketing Launch Plan Ppt PowerPoint Presentation Infographics Microsoft
This is a marketing launch plan ppt powerpoint presentation infographics microsoft. This is a eight stage process. The stages in this process are create press release, use twitter, use advertising, create email contests, update the website, garner endorsements, build demand, attend tradeshows.
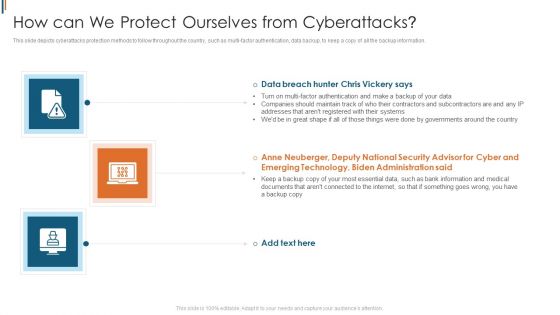
Ukraine Cyberwarfare How Can We Protect Ourselves From Cyberattacks Designs Pdf
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Presenting ukraine cyberwarfare how can we protect ourselves from cyberattacks designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like anne neuberger, deputy national security advisor for cyber and emerging technology, biden administration said. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF
This slide illustrates the incidents of the transition project. It covers the details such as explanation, status, priority, and resolution of the incident to ensure that technological change is successfully completed in the organization. Deliver and pitch your topic in the best possible manner with this Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF. Use them to share invaluable insights on Incident Status Priority, Cyber Attack Sensitive, Added Data Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































