Cyber Security Strategy
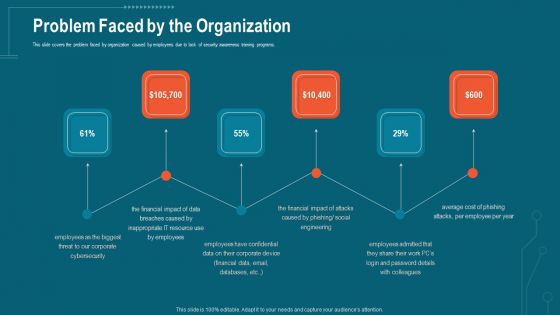
Companys Data Safety Recognition Problem Faced By The Organization Portrait PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a companys data safety recognition problem faced by the organization portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, financial impact, resource, social engineering, cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Communication Infrastructure Services Download PDF
The following slide demonstrates information and communication technology infrastructure services for optimizing output, mitigate internal and external security threat. It includes components such as operations and network management etc. Persuade your audience using this IT Communication Infrastructure Services Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Applications, Description, Operations Management . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
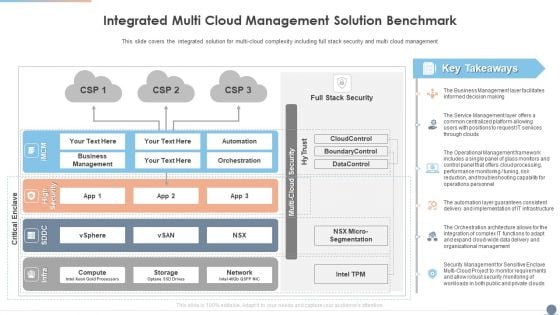
Multi Cloud Complexity Management Integrated Multi Cloud Management Solution Benchmark Elements PDF
This slide covers the integrated solution for multi cloud complexity including full stack security and multi cloud management. Presenting Multi Cloud Complexity Management Integrated Multi Cloud Management Solution Benchmark Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Business Management, Network, Service Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
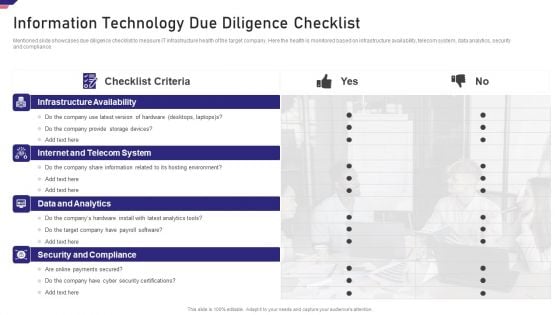
Mergers Acquisition Playbook Mergers Acquisition Playbook Information Technology Due Ideas PDF
Mentioned slide showcases due diligence checklist to measure IT infrastructure health of the target company. Here the health is monitored based on infrastructure availability, telecom system, data analytics, security and compliance.This is a Mergers Acquisition Playbook Mergers Acquisition Playbook Information Technology Due Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Infrastructure Availability, Internet And Telecom System, Data And Analytics You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Collection Of Information Technology Certifications Comptia A Certification Courses Details Icons PDF
This slide covers certification details about CompTIA A such as who should take these certifications, courses offered in this certification etc. This is a collection of information technology certifications comptia a certification courses details icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems administrator, network administrator, security administrator, designed. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
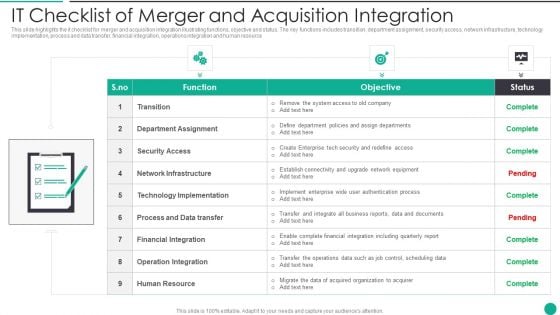
IT Checklist Of Merger And Acquisition Integration Designs PDF
This slide highlights the it checklist for merger and acquisition integration illustrating functions, objective and status. The key functions includes transition, department assignment, security access, network infrastructure, technology implementation, process and data transfer, financial integration, operations integration and human resource Presenting IT Checklist Of Merger And Acquisition Integration Designs PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Department Assignment, Financial Integration, Operation Integration This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
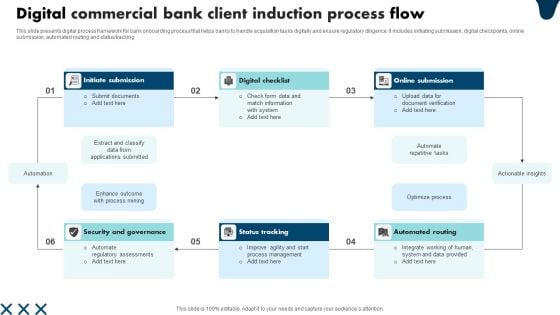
Digital Commercial Bank Client Induction Process Flow Background PDF
This slide presents digital process framework for bank onboarding process that helps banks to handle acquisition tasks digitally and ensure regulatory diligence. It includes initiating submission, digital checkpoints, online submission, automated routing and status tracking. Presenting Digital Commercial Bank Client Induction Process Flow Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security And Governance, Status Tracking, Automated Routing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
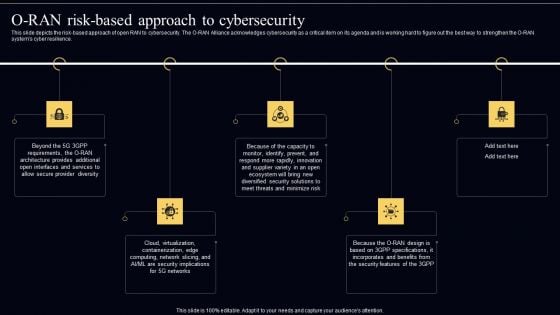
Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF
This slide depicts the risk based approach of open RAN to cybersecurity. The O RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O RAN systems cyber resilience. Get a simple yet stunning designed Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
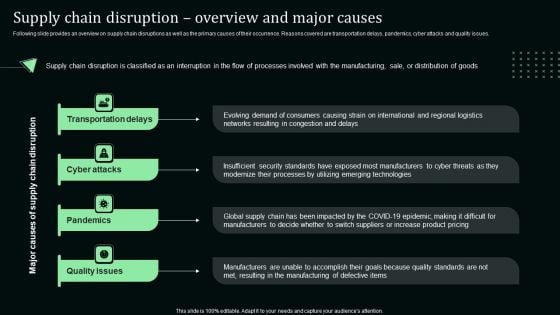
Supply Chain Disruption Overview And Major Causes Stand Out Digital Supply Chain Tactics Enhancing Slides PDF
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Supply Chain Disruption Overview And Major Causes Stand Out Digital Supply Chain Tactics Enhancing Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Supply Chain Disruption Overview And Major Causes Stand Out Digital Supply Chain Tactics Enhancing Slides PDF
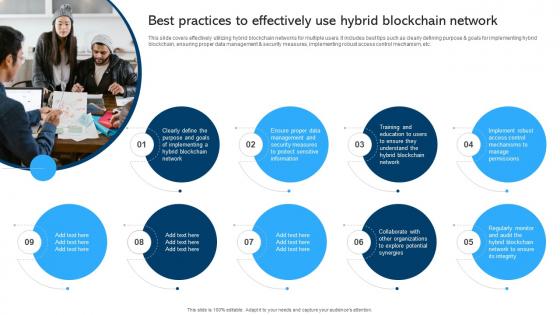
Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V
This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc. Welcome to our selection of the Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
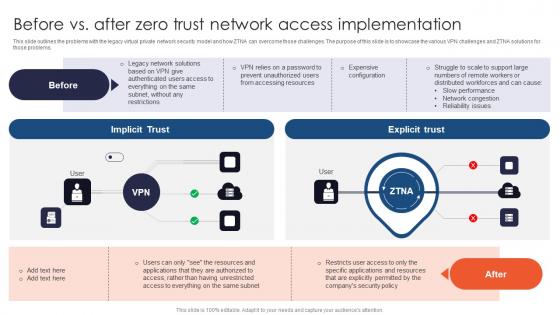
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
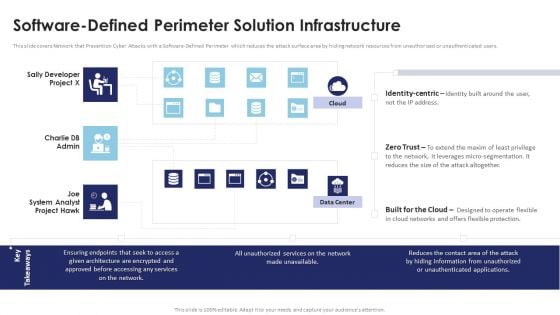
Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Are you searching for a Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF from Slidegeeks today.
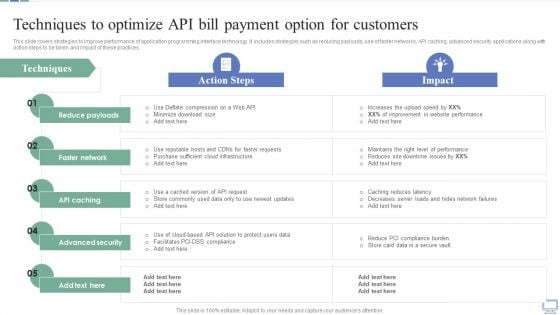
Omnichannel Banking Services Platform Techniques To Optimize API Bill Payment Option For Customers Demonstration PDF
This slide covers strategies to improve performance of application programming interface technology. It includes strategies such as reducing payloads, use of faster networks, API caching, advanced security applications along with action steps to be taken and impact of these practices. Present like a pro with Omnichannel Banking Services Platform Techniques To Optimize API Bill Payment Option For Customers Demonstration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
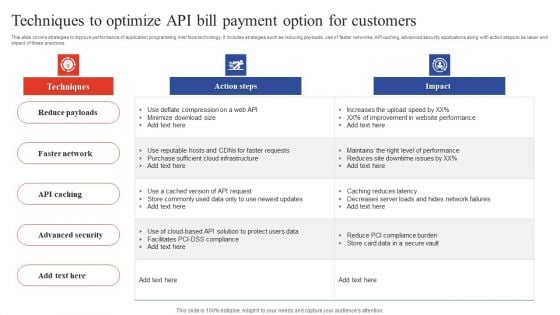
Deployment Of Omnichannel Banking Solutions Techniques To Optimize API Bill Payment Option For Customers Professional PDF
This slide covers strategies to improve performance of application programming interface technology. It includes strategies such as reducing payloads, use of faster networks, API caching, advanced security applications along with action steps to be taken and impact of these practices. Slidegeeks is here to make your presentations a breeze with Deployment Of Omnichannel Banking Solutions Techniques To Optimize API Bill Payment Option For Customers Professional PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
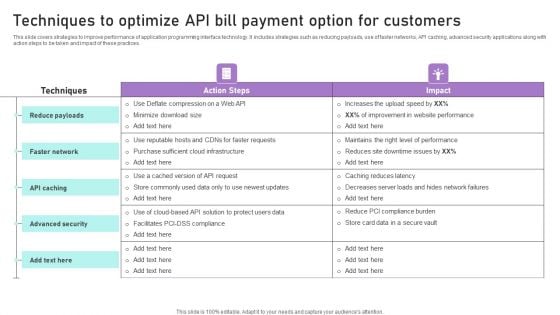
Techniques To Optimize API Bill Payment Option For Customers Ppt Infographics Example PDF
This slide covers strategies to improve performance of application programming interface technology. It includes strategies such as reducing payloads, use of faster networks, API caching, advanced security applications along with action steps to be taken and impact of these practices. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Techniques To Optimize API Bill Payment Option For Customers Ppt Infographics Example PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Techniques To Optimize API Bill Payment Option For Customers Ppt Infographics Example PDF.
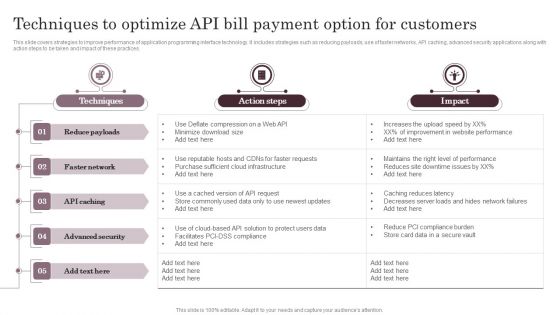
Techniques To Optimize API Bill Payment Option For Customers Information PDF
This slide covers strategies to improve performance of application programming interface technology. It includes strategies such as reducing payloads, use of faster networks, API caching, advanced security applications along with action steps to be taken and impact of these practices. The Techniques To Optimize API Bill Payment Option For Customers Information PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
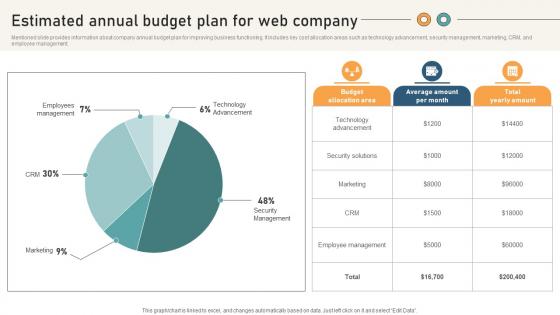
Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company. Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management.
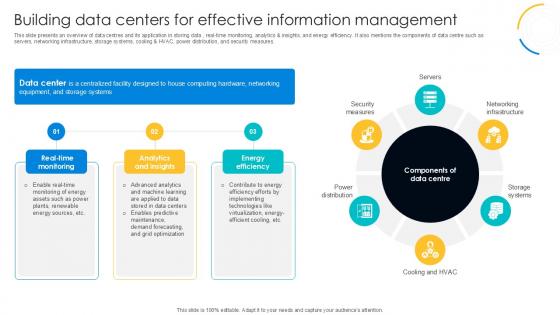
Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V
This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures. If you are looking for a format to display your unique thoughts, then the professionally designed Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures.
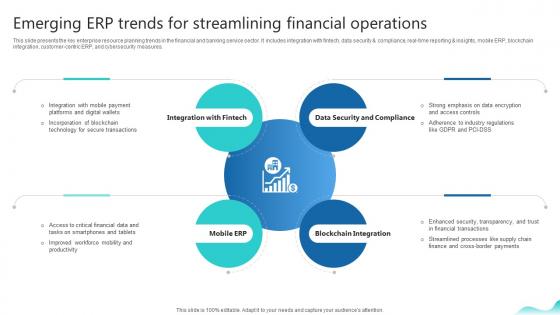
Emerging Erp Trends For Streamlining Financial Operations Erp And Digital Transformation For Maximizing DT SS V
This slide presents the key enterprise resource planning trends in the financial and banking service sector. It includes integration with fintech, data security and compliance, real-time reporting and insights, mobile ERP, blockchain integration, customer-centric ERP, and cybersecurity measures.Welcome to our selection of the Emerging Erp Trends For Streamlining Financial Operations Erp And Digital Transformation For Maximizing DT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide presents the key enterprise resource planning trends in the financial and banking service sector. It includes integration with fintech, data security and compliance, real-time reporting and insights, mobile ERP, blockchain integration, customer-centric ERP, and cybersecurity measures.

Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V
This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc. Get a simple yet stunning designed Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc.

WAF Introduction Web Application Firewall Use Cases Topics PDF
This slide outlines the main application areas of web application firewall systems. The purpose of this slide is to showcase the various use cases of WAF, including patching vulnerabilities, complying with security and regulatory regulations, enforcing content policies, securing websites and applications, and so on. Presenting this PowerPoint presentation, titledWAF Introduction Web Application Firewall Use Cases Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting thisWAF Introduction Web Application Firewall Use Cases Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizableWAF Introduction Web Application Firewall Use Cases Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
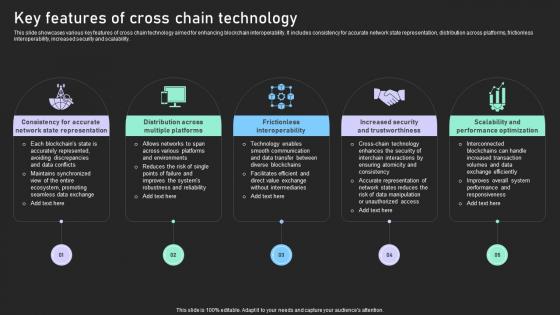
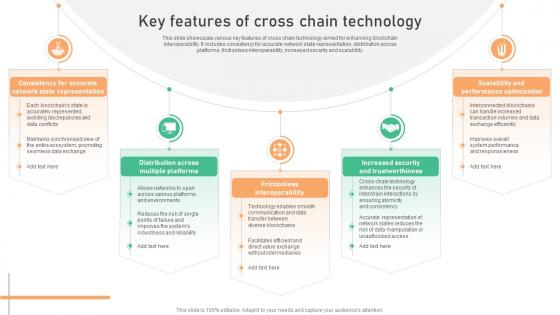
Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.
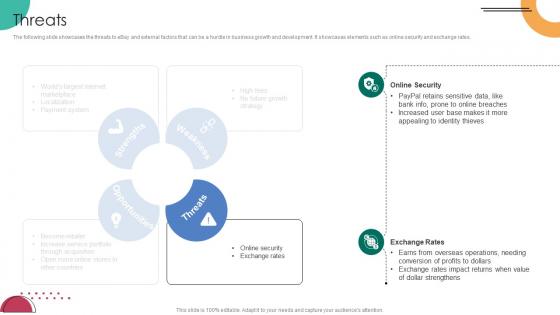
Threats C2C Ecommerce Platform Company Profile CP SS V
The following slide showcases the threats to eBay and external factors that can be a hurdle in business growth and development. It showcases elements such as online security and exchange rates.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Threats C2C Ecommerce Platform Company Profile CP SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Threats C2C Ecommerce Platform Company Profile CP SS V. The following slide showcases the threats to eBay and external factors that can be a hurdle in business growth and development. It showcases elements such as online security and exchange rates.
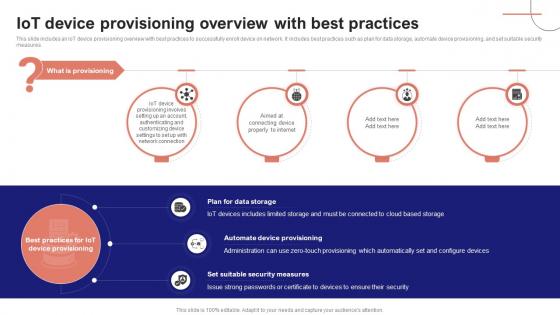
IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT Ss V
This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V can be your best option for delivering a presentation. Represent everything in detail using IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures.
Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Are you searching for a Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V from Slidegeeks today. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.

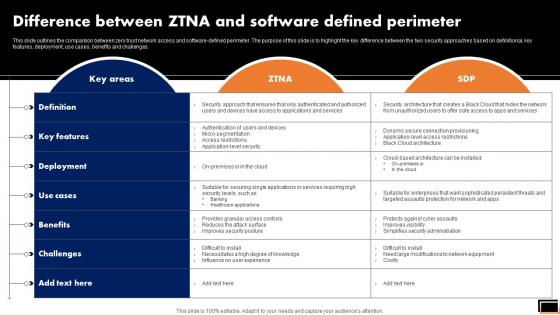
Zero Trust Model Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Difference Between ZTNA And Software Defined Perimeter and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.

Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. This Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Roadmap To Implement Zero Trust Network Access Model Structure PDF
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Want to ace your presentation in front of a live audience Our Roadmap To Implement Zero Trust Network Access Model Structure PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
Cybersecurity Guidelines IT Information Technology Policy Implementation Budget For FY2022 Icons PDF
This slide represents the companys IT policy implementation budget for FY2022. It covers the details of the software application and security services that need to be purchased and updated. This Cybersecurity Guidelines IT Information Technology Policy Implementation Budget For FY2022 Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cybersecurity Guidelines IT Information Technology Policy Implementation Budget For FY2022 Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Guidelines To Successfully Develop Flexible Work Policy Professional PDF
The following slide showcases important instructions related to the work from home WFH policy that can assist corporates to draft rules and regulations for remote employees. It contains information about security protocols, online meeting etiquette, expenditure, and team building activities. Welcome to our selection of the Guidelines To Successfully Develop Flexible Work Policy Professional PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
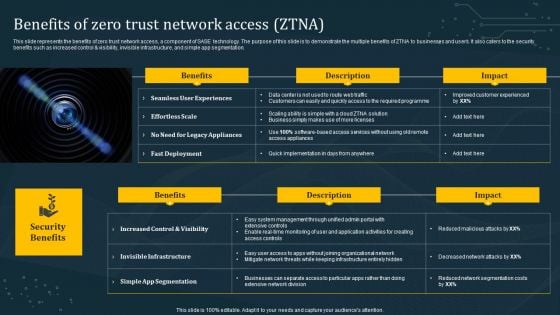
Benefits Of Zero Trust Network Access ZTNA Download PDF
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Present like a pro with Benefits Of Zero Trust Network Access ZTNA Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Implementing Adaptive Work Arrangements Guidelines To Successfully Develop Flexible Work Policy Pictures PDF
The following slide showcases important instructions related to the work from home WFH policy that can assist corporates to draft rules and regulations for remote employees. It contains information about security protocols, online meeting etiquette, expenditure, and team building activities. This modern and well arranged Implementing Adaptive Work Arrangements Guidelines To Successfully Develop Flexible Work Policy Pictures PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
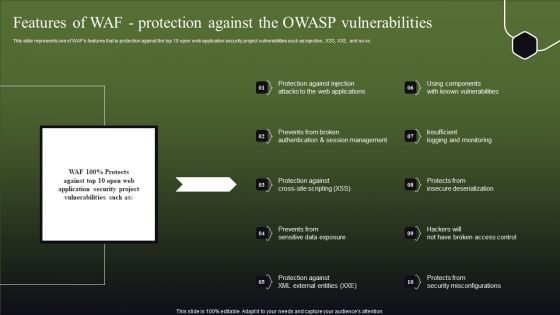
Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
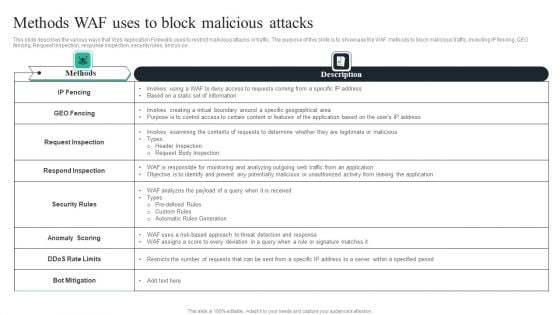
WAF Introduction Methods WAF Uses To Block Malicious Attacks Graphics PDF
This slide describes the various ways that Web Application Firewalls uses to restrict malicious attacks or traffic. The purpose of this slide is to showcase the WAF methods to block malicious traffic, including IP fencing, GEO fencing, Request Inspection, response inspection, security rules, and so on. Welcome to our selection of the WAF Introduction Methods WAF Uses To Block Malicious Attacks Graphics PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
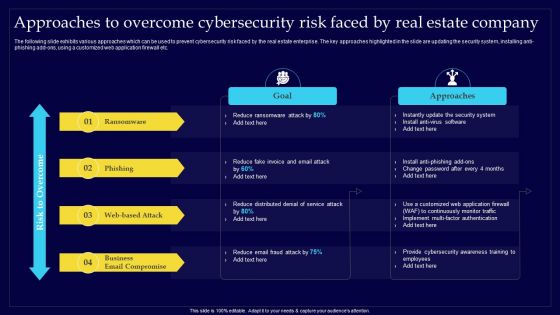
Executing Risk Mitigation Approaches To Overcome Cybersecurity Risk Faced By Real Background PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Create an editable Executing Risk Mitigation Approaches To Overcome Cybersecurity Risk Faced By Real Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Executing Risk Mitigation Approaches To Overcome Cybersecurity Risk Faced By Real Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add-ons, using a customized web application firewall etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF today and make your presentation stand out from the rest.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF

Successful Risk Administration Approaches To Overcome Cybersecurity Risk Faced By Real Summary PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Successful Risk Administration Approaches To Overcome Cybersecurity Risk Faced By Real Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
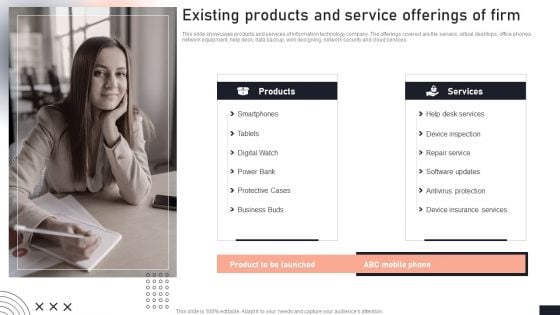
Existing Products And Service Offerings Of Firm Stakeholder Engagement Plan For Launch Event Ideas PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Take your projects to the next level with our ultimate collection of Existing Products And Service Offerings Of Firm Stakeholder Engagement Plan For Launch Event Ideas PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.
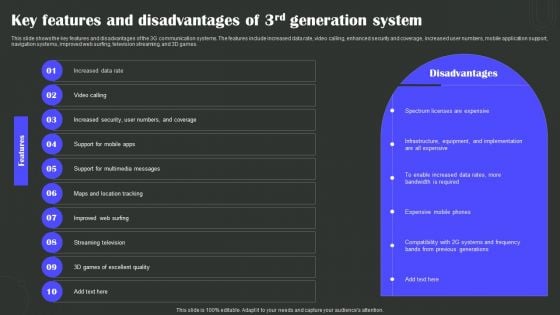
Key Features And Disadvantages Of 3Rd Generation System Wireless Technology Transformation Introduction PDF
This slide shows the key features and disadvantages of the 3G communication systems. The features include increased data rate, video calling, enhanced security and coverage, increased user numbers, mobile application support, navigation systems, improved web surfing, television streaming, and 3D games. Welcome to our selection of the Key Features And Disadvantages Of 3Rd Generation System Wireless Technology Transformation Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
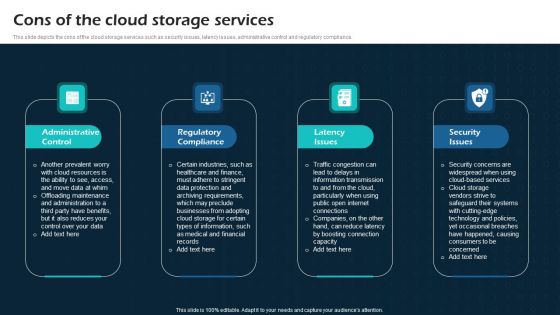
Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF
This slide depicts the cons of the cloud storage services such as security issues, latency issues, administrative control and regulatory compliance. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Factors Influencing Software Defined Networking SDN Adoption Ppt Portfolio Pictures PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged Factors Influencing Software Defined Networking SDN Adoption Ppt Portfolio Pictures PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
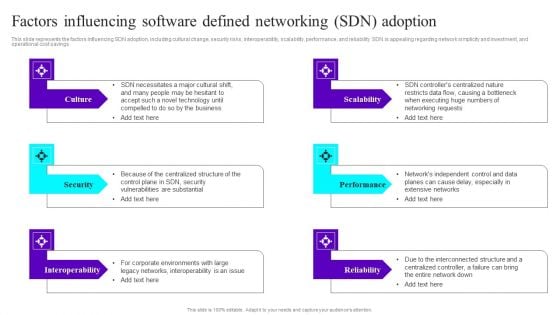
Factors Influencing Software Defined Networking SDN Adoption Ppt Summary Grid PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged Factors Influencing Software Defined Networking SDN Adoption Ppt Summary Grid PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
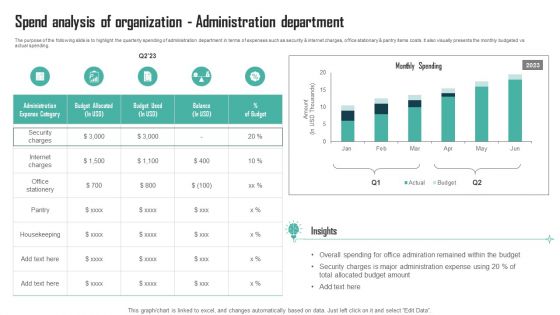
Expenses Management Plan Spend Analysis Of Organization Administration Department Professional PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Expenses Management Plan Spend Analysis Of Organization Administration Department Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cybersecurity Operations Cybersecops Secops Vs Devops Slides PDF
This slide represents the comparison between the security operations center and DevOps. The purpose of this slide is to highlight the key differences between SecOps and DevOps teams based on definition, scope, approach, way of processing, goal and implementation of changes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cybersecurity Operations Cybersecops Secops Vs Devops Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cybersecurity Operations Cybersecops Secops Vs Devops Slides PDF today and make your presentation stand out from the rest.
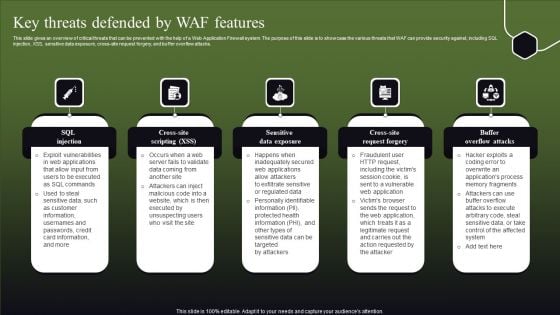
Key Threats Defended By WAF Features Ppt Pictures Elements PDF
This slide gives an overview of critical threats that can be prevented with the help of a Web Application Firewall system. The purpose of this slide is to showcase the various threats that WAF can provide security against, including SQL injection, XSS, sensitive data exposure, cross-site request forgery, and buffer overflow attacks. Explore a selection of the finest Key Threats Defended By WAF Features Ppt Pictures Elements PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Threats Defended By WAF Features Ppt Pictures Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Introduction To B2B Online Shopping Payment Options Key Challenges Faced By Businesses Formats PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. This modern and well arranged Introduction To B2B Online Shopping Payment Options Key Challenges Faced By Businesses Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112
Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112-Use our Security PowerPoint Templates because, Present your views using our innovative slides and be assured of leaving a lasting impression. Use our Arrows PowerPoint Templates because; Help them develop their thoughts along the way. Use our Business PowerPoint Templates because; emphasize the process of your business/corporate growth. Use our Computer PowerPoint Templates because, Clarity of thought has been the key to your growth. Use our Internet PowerPoint Templates because; transmit this concern to your staff using our helpful slides.-Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-Upload download folder icon, Computer, Arrows, Symbol, Internet, Business Environmental awareness is the call to answer. Our Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112 will fit the bill.

Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF
This slide represents the overview, benefits and disadvantages of virtual security operation center model. The purpose of this slide is to highlight the advantage, disadvantages and alternative approaches for VSOC such as outsourcing of virtual SOC model. This modern and well arranged Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.
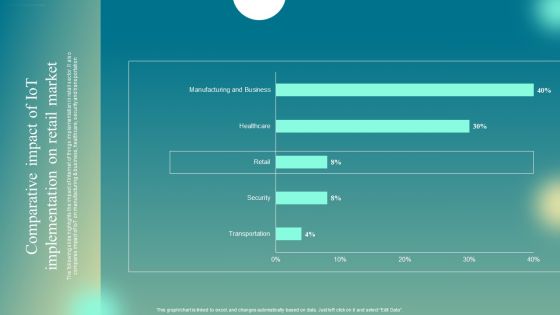
Comparative Impact Of Iot Implementation On Retail Market Clipart PDF
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation. Welcome to our selection of the Comparative Impact Of Iot Implementation On Retail Market Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
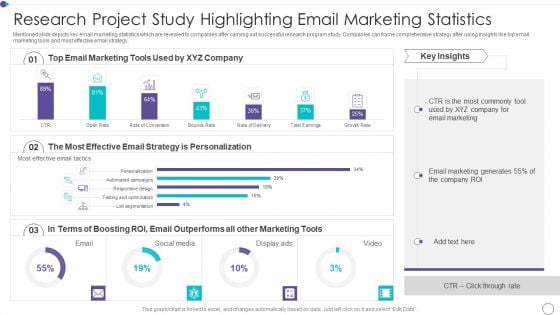
Research Project Study Highlighting Email Marketing Statistics Structure PDF
Mentioned slide depicts key email marketing statistics which are revealed to companies after carrying out successful research program study. Companies can frame comprehensive strategy after using insights like top email marketing tools and most effective email strategy. Showcasing this set of slides titled research project study highlighting email marketing statistics structure pdf. The topics addressed in these templates are marketing, strategy, email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
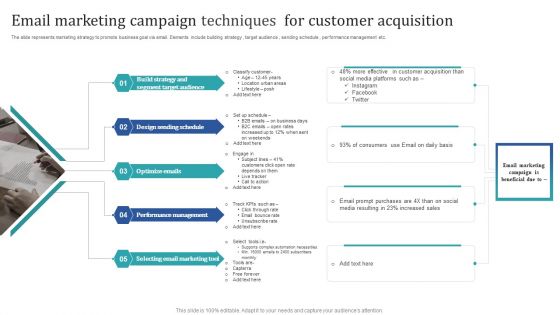
Email Marketing Campaign Techniques For Customer Acquisition Guidelines PDF
The slide represents marketing strategy to promote business goal via email. Elements include building strategy, target audience, sending schedule, performance management etc. Presenting Email Marketing Campaign Techniques For Customer Acquisition Guidelines PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Design Sending Schedule, Optimize Emails, Performance Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Email Folder Internet PowerPoint Templates And PowerPoint Themes 0812
Email Folder Internet PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with email folder Develop a winning strategy with our Email Folder Internet PowerPoint Templates And PowerPoint Themes 0812. You will come out on top.
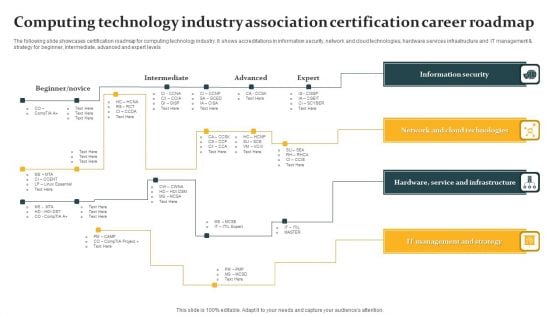
Computing Technology Industry Association Certification Career Roadmap Professional PDF
The following slide showcases certification roadmap for computing technology industry. It shows accreditations in information security, network and cloud technologies, hardware services infrastructure and IT management and strategy for beginner, intermediate, advanced and expert levels. Persuade your audience using this Computing Technology Industry Association Certification Career Roadmap Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security, Network And Cloud Technologies, IT Management And Strategy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
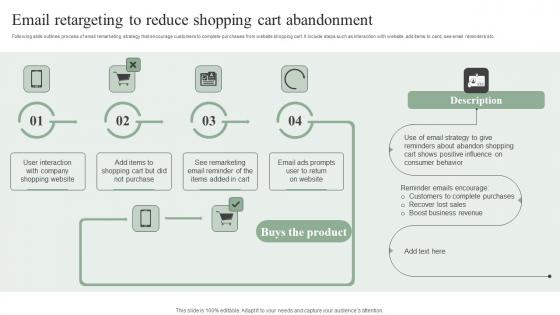
Email Retargeting To Reduce Shopping Cart Efficient Marketing Tactics Slides Pdf
Following slide outlines process of email remarketing strategy that encourage customers to complete purchases from website shopping cart. It include steps such as interaction with website, add items to card, see email reminders etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Email Retargeting To Reduce Shopping Cart Efficient Marketing Tactics Slides Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. Following slide outlines process of email remarketing strategy that encourage customers to complete purchases from website shopping cart. It include steps such as interaction with website, add items to card, see email reminders etc.


 Continue with Email
Continue with Email

 Home
Home


































