Cyber Security
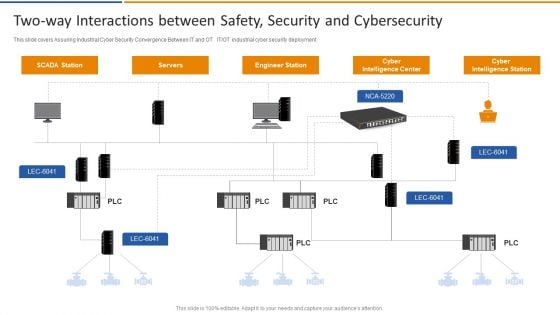
Smart Venture Digitial Transformation Two Way Interactions Between Safety Security Template PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment. This is a Smart Venture Digitial Transformation Two Way Interactions Between Safety Security Template PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like SCADA Station Servers, Engineer Station, Cyber Intelligence Center. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
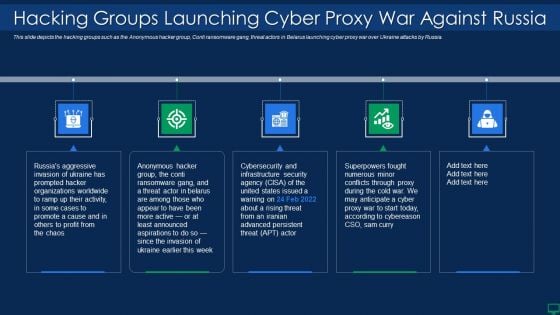
Russian Cyber Attacks On Ukraine IT Hacking Groups Launching Cyber Rules PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting russian cyber attacks on ukraine it hacking groups launching cyber rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Breach Prevention Recognition IT Infrastructure Security Budget Rules PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition it infrastructure security budget rules pdf. Use them to share invaluable insights on it infrastructure security budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Managing Electronic Information Security 60 Days Plan Ppt Ideas Graphics Tutorials PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative cybersecurity managing electronic information security 60 days plan ppt ideas graphics tutorials pdf bundle. Topics like measured, security, team, organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Loss Due To Different Cyber Attacks Designs PDF
This slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Deliver an awe inspiring pitch with this creative cyber exploitation it loss due to different cyber attacks designs pdf bundle. Topics like loss due to different cyber attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
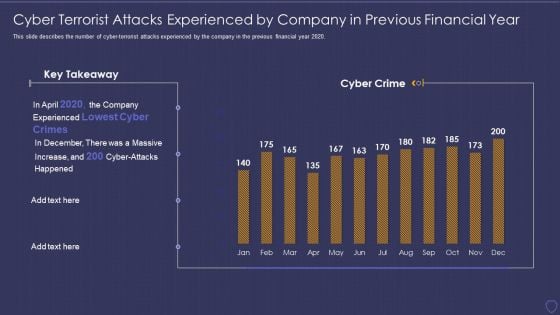
Global Cyber Terrorism Incidents On The Rise IT Cyber Terrorist Attacks Experienced Formats PDF
This slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2020. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it cyber terrorist attacks experienced formats pdf bundle. Topics like cyber terrorist attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Russian Cyber Attacks On Ukraine IT Hybrid Warfare Cyber Rapid Structure PDF
This slide talks about the cyber rapid response team deployed to protect Ukraine from Russian cyber attacks, including experts from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands. Presenting russian cyber attacks on ukraine it hybrid warfare cyber rapid structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like hybrid warfare cyber rapid response team crrt. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
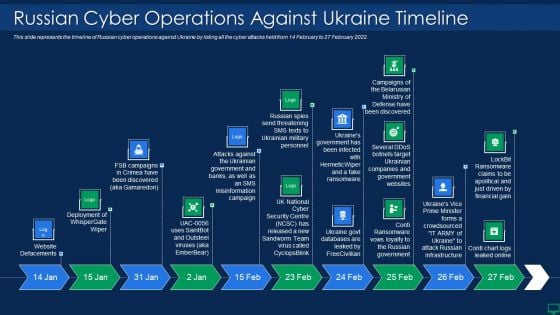
Russian Cyber Attacks On Ukraine IT Russian Cyber Operations Against Themes PDF
This slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. This is a russian cyber attacks on ukraine it russian cyber operations against themes pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like russian cyber operations against ukraine timeline. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
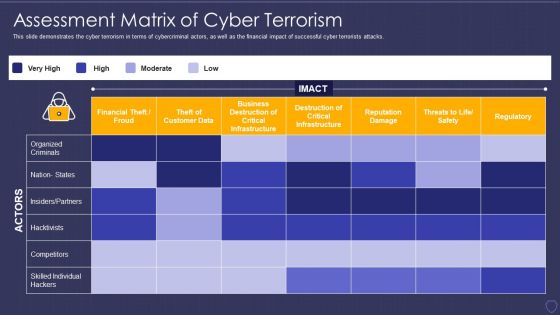
Global Cyber Terrorism Incidents On The Rise IT Assessment Matrix Of Cyber Terrorism Ideas PDF
This slide demonstrates the cyber terrorism in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it assessment matrix of cyber terrorism ideas pdf bundle. Topics like financial theft or froud, reputation damage, regulatory, competitors, destruction of critical infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
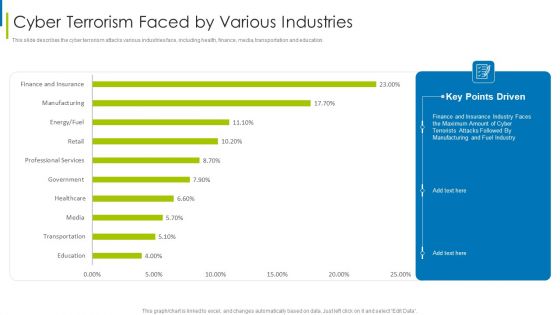
Cyber Terrorism Assault Cyber Terrorism Faced By Various Industries Pictures PDF
This slide describes the cyber terrorism attacks various industries face, including health, finance, media, transportation and education.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorism faced by various industries pictures pdf bundle. Topics like Cyber Terrorism Faced By Companies In US can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Terrorism Assault Dashboard For Threat Tracking Of Cyber Terrorism Themes PDF
This slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault dashboard for threat tracking of cyber terrorism themes pdf Use them to share invaluable insights on Massive Increase, Cyber Attacks Happened, Company Experienced and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
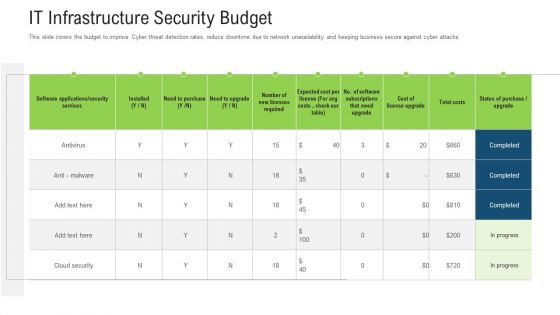
It Infrastructure Security Budget Ppt Outline Mockup PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this it infrastructure security budget ppt outline mockup pdf. Use them to share invaluable insights on services, software, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
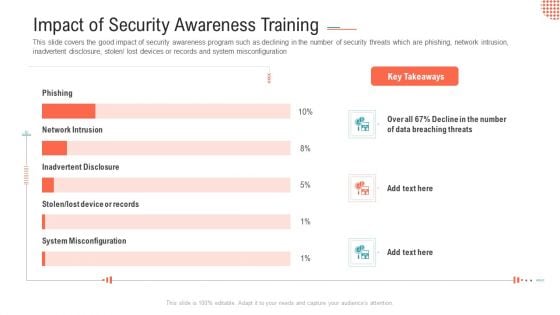
Impact Of Security Awareness Training Ppt Pictures Design Templates PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this impact of security awareness training ppt pictures design templates pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Russian Cyber Attacks On Ukraine IT Ukraine And Russia Cyber Warfare Elements PDF
This slide represents the Ukraine and Russia cyber warfare impact on western countries such as the United States, United Kingdom, and Estonia. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it ukraine and russia cyber warfare elements pdf bundle. Topics like businesses, networks, internet, cybersecurity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Russian Cyber Attacks On Ukraine IT Shuckworm Continues Cyber Espionage Ideas PDF
Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it shuckworm continues cyber espionage ideas pdf bundle. Topics like organization, devices, emails can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
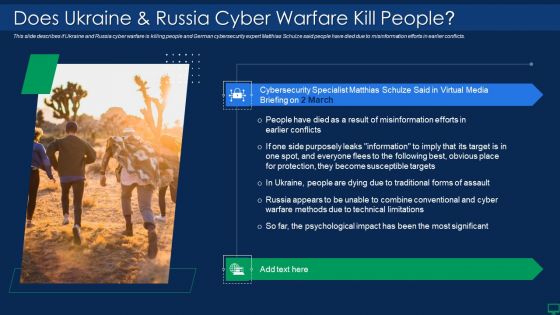
Russian Cyber Attacks On Ukraine IT Does Ukraine And Russia Cyber Diagrams PDF
This slide describes if Ukraine and Russia cyber warfare is killing people and German cybersecurity expert Matthias Schulze said people have died due to misinformation efforts in earlier conflicts. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it does ukraine and russia cyber diagrams pdf bundle. Topics like does ukraine and russia cyber warfare kill people can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
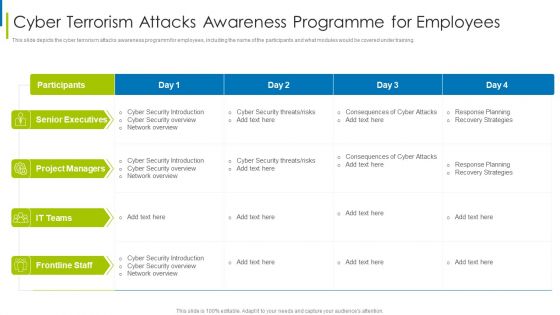
Cyber Terrorism Assault Cyber Terrorism Attacks Awareness Programme For Employees Clipart PDF
This slide depicts the cyber terrorism attacks awareness programm for employees, including the name of the participants and what modules would be covered under training.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorism attacks awareness programme for employees clipart pdf bundle. Topics like Unanticipated Occurrence, Multiple Copies Of Data, Malicious Assaults can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Russian Cyber Attacks On Ukraine IT Hermetic Wiper Cyber Attack Infographics PDF
Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it hermetic wiper cyber attack infographics pdf bundle. Topics like information, management, system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
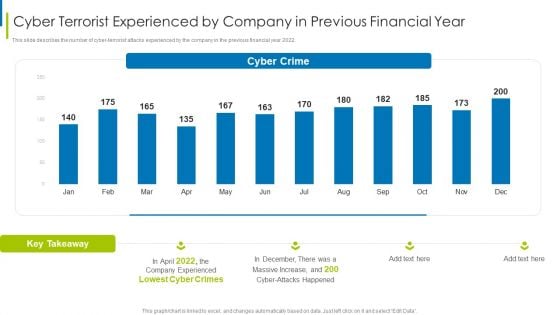
Cyber Terrorism Assault Cyber Terrorist Experienced By Company In Previous Financial Year Sample PDF
This slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2022.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorist experienced by company in previous financial year sample pdf bundle. Topics like Increased Costs, Reputational Damage, Intellectual Property Theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
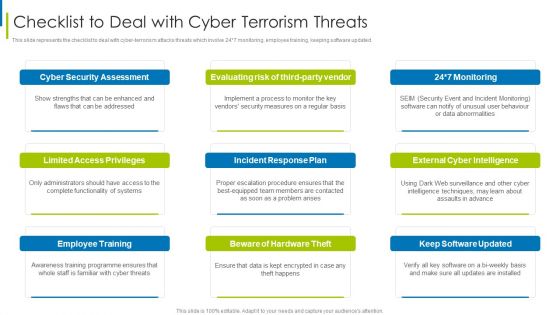
Cyber Terrorism Assault Checklist To Deal With Cyber Terrorism Threats Guidelines PDF
This slide represents the checklist to deal with cyber-terrorism attacks threats which involve 24 7 monitoring, employee training, keeping software updated.This is a cyber terrorism assault checklist to deal with cyber terrorism threats guidelines pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like German Businesses, Average Loss , Cyber Terrorist Attack You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
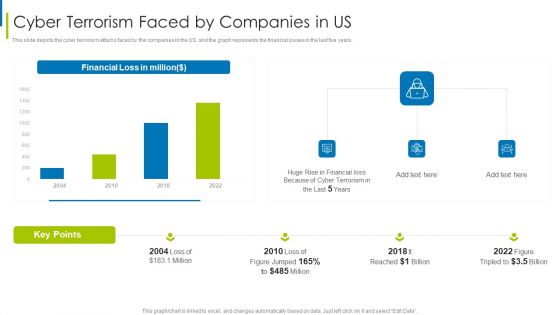
Cyber Terrorism Assault Cyber Terrorism Faced By Companies In US Mockup PDF
This slide depicts the cyber terrorism attacks faced by the companies in the US, and the graph represents the financial losses in the last five years. Deliver and pitch your topic in the best possible manner with this cyber terrorism assault cyber terrorism faced by companies in us mockup pdf Use them to share invaluable insights on Consequences Of Cyber Attacks, Response Planning, Recovery Strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
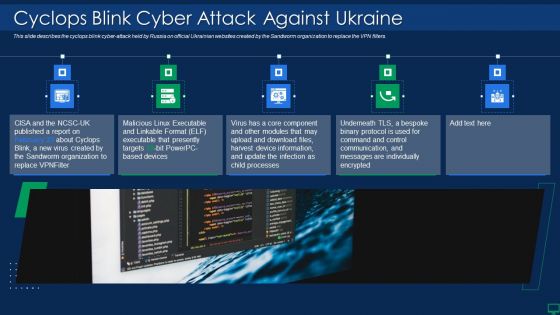
Russian Cyber Attacks On Ukraine IT Cyclops Blink Cyber Attack Mockup PDF
This slide describes the cyclops blink cyber attack held by Russia on official Ukrainian websites created by the Sandworm organization to replace the VPN filters. This is a russian cyber attacks on ukraine it cyclops blink cyber attack mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device, processes, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Cyber Attacks On Ukraine Information PDF
This slide represents the conspicuous Russian cyber attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. Presenting russian cyber attacks on ukraine it cyber attacks on ukraine information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like social media, systems, networks, services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
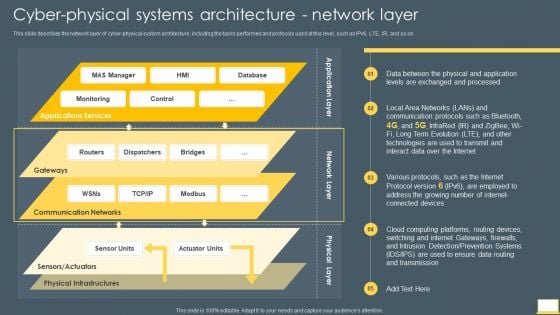
Cyber Intelligent Computing System Cyber Physical Systems Architecture Network Layer Topics PDF
This slide describes the network layer of cyber physical system architecture, including the tasks performed and protocols used at this level, such as IPv6, LTE, IR, and so on. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Cyber Physical Systems Architecture Network Layer Topics PDF bundle. Topics like Communication Networks, Physical Infrastructures, Application can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
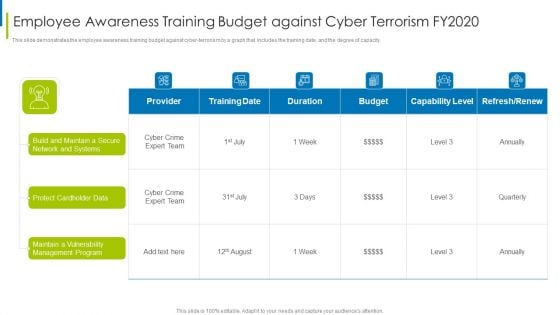
Cyber Terrorism Assault Employee Awareness Training Budget Against Cyber Terrorism FY2020 Inspiration PDF
This slide demonstrates the employee awareness training budget against cyber-terrorism by a graph that includes the training date, and the degree of capacity. Deliver an awe inspiring pitch with this creative cyber terrorism assault employee awareness training budget against cyber terrorism fy2020 inspiration pdf bundle. Topics like Protect Cardholder Data, Maintain A Vulnerability, Management Program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Cyber Terrorism Incidents On The Rise IT Phishing Techniques Misused For Cyber Assault Ideas PDF
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Presenting global cyber terrorism incidents on the rise it phishing techniques misused for cyber assault ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like spear phishing, smishing and vishing, whaling, email phishing scams. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Intelligent Computing System Cyber Physical Systems In Healthcare Diagrams PDF
This slide describes the application of CPS in the healthcare industry, including its benefits such as reducing hospitalizations, better treatment for disabled and elderly patients, and so on. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Cyber Physical Systems In Healthcare Diagrams PDF bundle. Topics like Network, Cyber Physical Systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
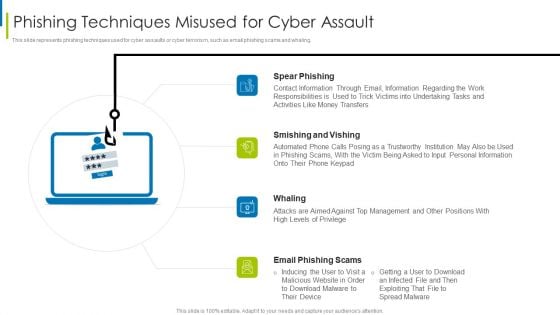
Cyber Terrorism Assault Phishing Techniques Misused For Cyber Assault Slides PDF
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. This is a cyber terrorism assault phishing techniques misused for cyber assault slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like smishing and vishing, spear phishing, contact information through You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
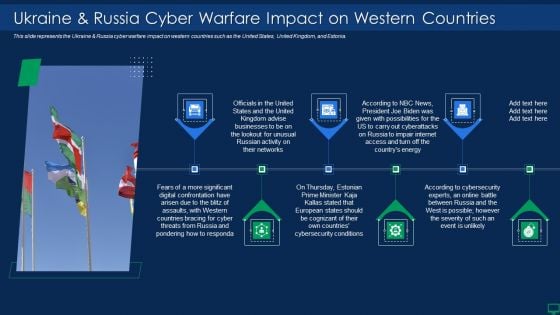
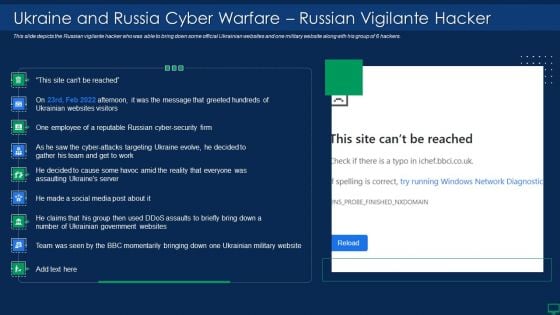
Russian Cyber Attacks On Ukraine IT Ukraine And Russia Cyber Warfare Impact Information PDF
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it ukraine and russia cyber warfare impact information pdf bundle. Topics like ukraine and russia cyber warfare russian vigilante hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
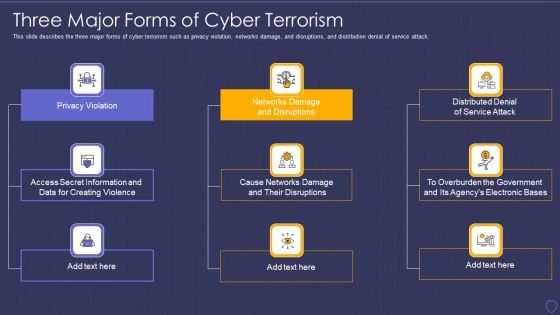
Global Cyber Terrorism Incidents On The Rise IT Three Major Forms Of Cyber Terrorism Topics PDF
This slide describes the three major forms of cyber terrorism such as privacy violation, networks damage, and disruptions, and distribution denial of service attack. Presenting global cyber terrorism incidents on the rise it three major forms of cyber terrorism topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like privacy violation, networks damage and disruptions, distributed denial of service attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
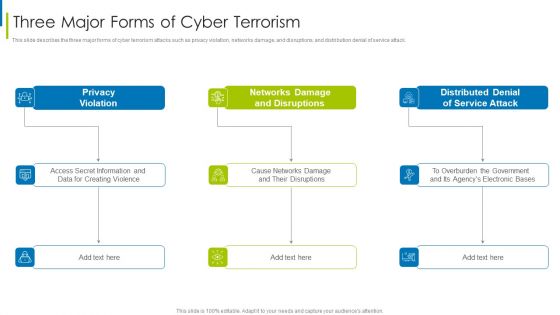
Cyber Terrorism Assault Three Major Forms Of Cyber Terrorism Brochure PDF
This slide describes the three major forms of cyber terrorism attacks such as privacy violation, networks damage, and disruptions, and distribution denial of service attack.This is a cyber terrorism assault three major forms of cyber terrorism brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privacy violation, networks damage and disruptions, distributed denial You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
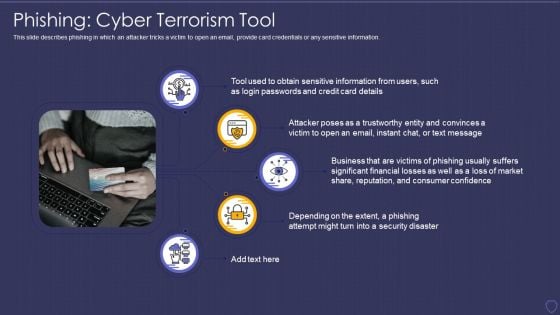
Global Cyber Terrorism Incidents On The Rise IT Phishing Cyber Terrorism Tool Rules PDF
This slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Presenting global cyber terrorism incidents on the rise it phishing cyber terrorism tool rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like phishing cyber terrorism tool. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Intelligent Computing System Cyber Physical Systems In Water Distribution Systems Portrait PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Cyber Physical Systems In Water Distribution Systems Portrait PDF bundle. Topics like Network, Data Acquisition Systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Cyber Terrorism Incidents On The Rise IT What Is Cyber Terrorism Infographics PDF
This slide describes cyber-terrorism and how it is used to access sensitive information and political or psychological aimed attacks. This is a global cyber terrorism incidents on the rise it what is cyber terrorism infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like political, ideological gain, networks, violating privacy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
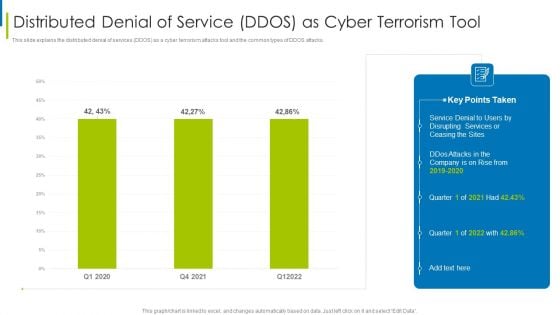
Cyber Terrorism Assault Distributed Denial Of Service DDOS As Cyber Terrorism Tool Slides PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism attacks tool and the common types of DDOS attacks.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault distributed denial of service ddos as cyber terrorism tool slides pdf Use them to share invaluable insights on Make A Risk Assessment, Determine The Importance Of Assets, Make A Complete Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Terrorism Assault Malicious Code Malware Misused For Cyber Terrorism Pictures PDF
This slide depicts the malicious code or malware misused for cyber terrorism attacks to hijack or access information from computers.Presenting cyber terrorism assault malicious code malware misused for cyber terrorism pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like broad spectrum, executed by changing, programmer by stopping In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
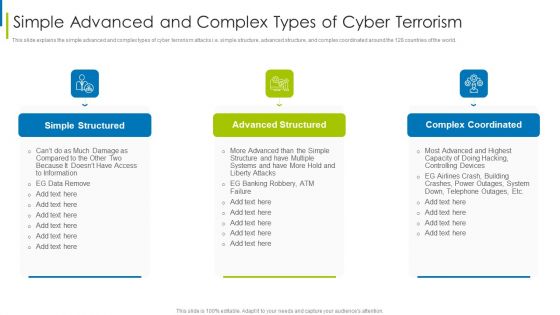
Cyber Terrorism Assault Simple Advanced And Complex Types Of Cyber Terrorism Structure PDF
This slide explains the simple advanced and complex types of cyber terrorism attacks i.e. simple structure, advanced structure, and complex coordinated around the 128 countries of the world.This is a cyber terrorism assault simple advanced and complex types of cyber terrorism structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like simple structured, advanced structured, complex coordinated You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Types Of Trojans Misused In Cyber Terrorism Background PDF
This slide describes the types of trojans misused in cyber terrorism attacks such as downloader trojan, spyware, backdoor trojan, and rootkit trojans. Presenting cyber terrorism assault types of trojans misused in cyber terrorism background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like backdoor trojan, downloader trojan, rootkit trojans In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
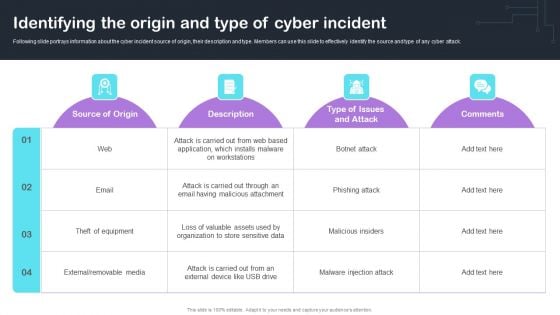
Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
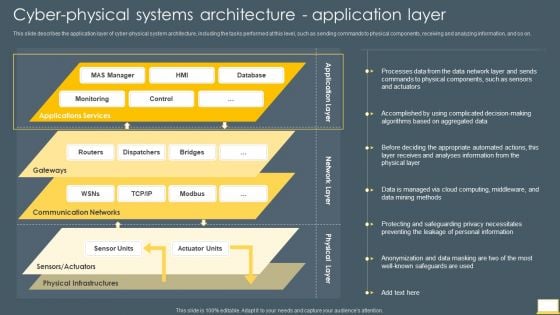
Cyber Intelligent Computing System Cyber Physical Systems Architecture Application Layer Clipart PDF
This slide describes the application layer of cyber physical system architecture, including the tasks performed at this level, such as sending commands to physical components, receiving and analyzing information, and so on. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Cyber Physical Systems Architecture Application Layer Clipart PDF. Use them to share invaluable insights on Communication Networks, Physical Infrastructures, Database and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
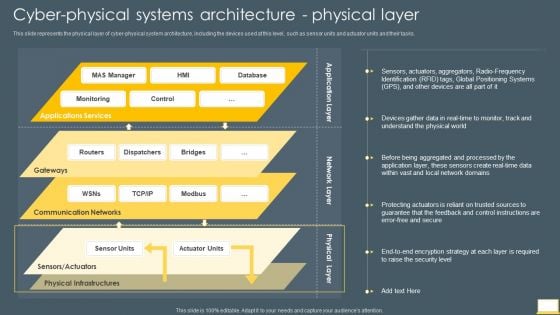
Cyber Intelligent Computing System Cyber Physical Systems Architecture Physical Layer Designs PDF
This slide represents the physical layer of cyber physical system architecture, including the devices used at this level, such as sensor units and actuator units and their tasks. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Cyber Physical Systems Architecture Physical Layer Designs PDF. Use them to share invaluable insights on Physical Infrastructures, Communication Networks, Global Positioning Systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
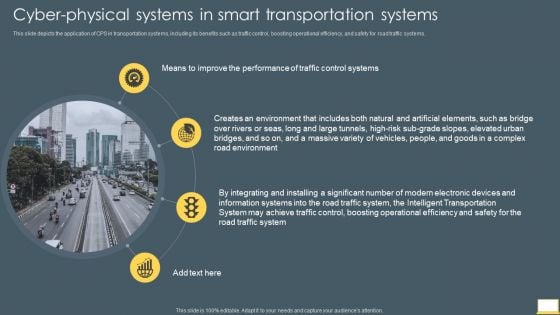
Cyber Intelligent Computing System Cyber Physical Systems In Smart Transportation Systems Themes PDF
This slide depicts the application of CPS in transportation systems, including its benefits such as traffic control, boosting operational efficiency, and safety for road traffic systems. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Cyber Physical Systems In Smart Transportation Systems Themes PDF bundle. Topics like Environment, Traffic Control Systems, Information Systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
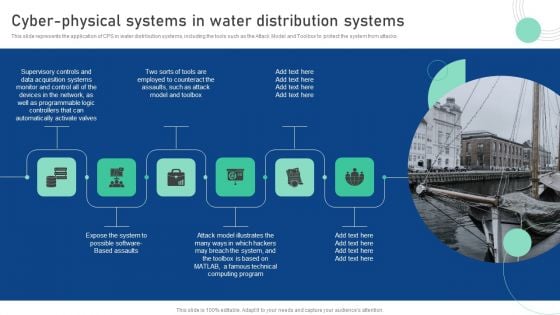
Cyber Physical System To Enhance Cyber Physical Systems In Water Distribution Summary PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. This Cyber Physical System To Enhance Cyber Physical Systems In Water Distribution Summary PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Cyber Physical System To Enhance Cyber Physical Systems In Smart Transportation Systems Icons PDF
This slide depicts the application of CPS in transportation systems, including its benefits such as traffic control, boosting operational efficiency, and safety for road traffic systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Physical System To Enhance Cyber Physical Systems In Smart Transportation Systems Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
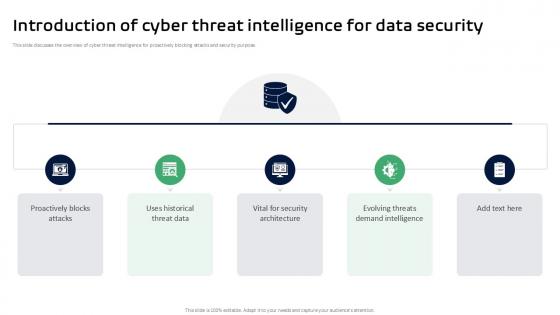
Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template
This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose.
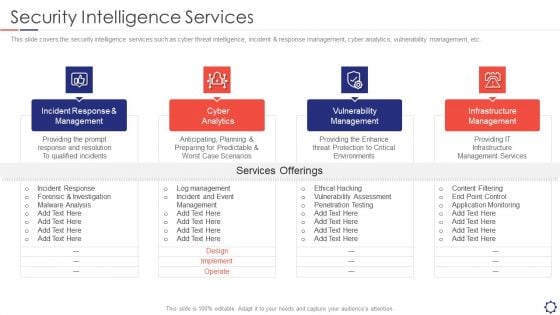
SIEM Security Intelligence Services Ppt Professional Format PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem security intelligence services ppt professional format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
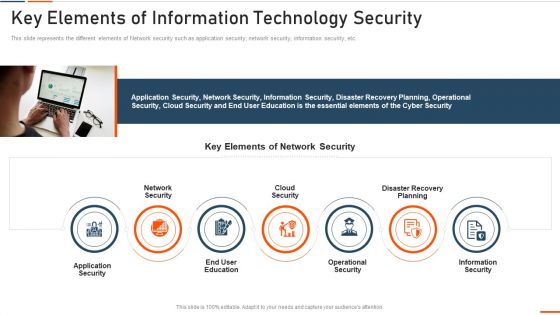
Key Elements Of Information Technology Security Ppt Styles Example PDF
This slide defines the meaning of network security and how it helps to prevent data through different methods and techniques. Presenting key elements of information technology security ppt styles example pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like approach, collective, methods, techniques, procedures, protect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security Prepare Data Backup Ppt Layouts Slides PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information technology security prepare data backup ppt layouts slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, information, manipulation, deletion, prevent . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
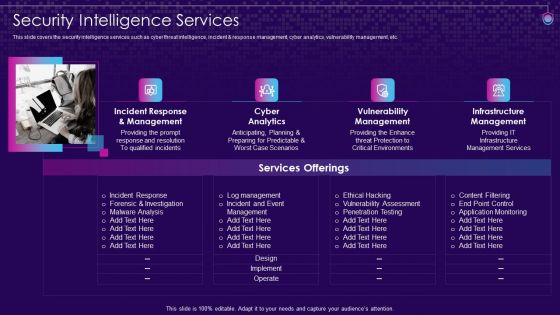
SIEM Services Security Intelligence Services Ppt Show Layouts PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem services security intelligence services ppt show layouts pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management cyber, analytics vulnerability, management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
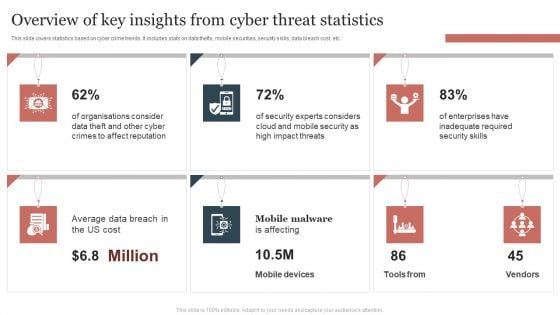
Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Best Practices For Cyber Safety At Job Safety Infographics PDF
This slide covers the best practices for cyber safety at workplace which includes protecting the data, using strong password protection, connecting to the secure wi-fi, investing in security systems, etc. Presenting best practices for cyber safety at job safety infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including protecting data, connect to secure wi fi, invest in security systems, strong password protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Blockchain Technology Applications For Cyber Threat Prevention Icons PDF
This slides represents various application of blockchain technology in enhancing cyber safety which helps to speed up data transfer procedures, offer secure transactions, and lower compliance expenses. Key components are IoT security, secure private messaging, etc. Presenting Blockchain Technology Applications For Cyber Threat Prevention Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prevention, Infrastructure, System . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
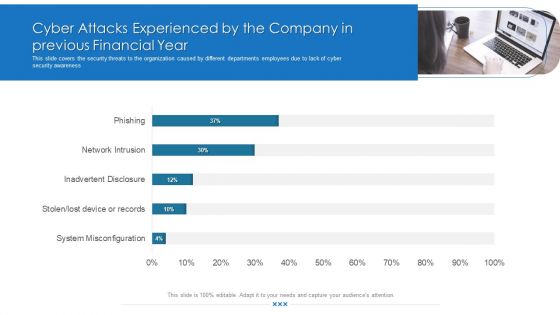
Cyber Attacks Experienced By The Company In Previous Financial Year Download PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this cyber attacks experienced by the company in previous financial year download pdf. Use them to share invaluable insights on cyber attacks experienced by the company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
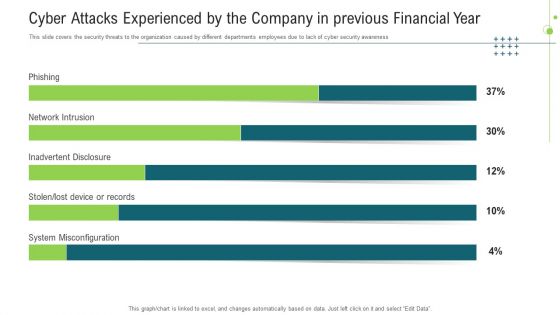
Cyber Attacks Experienced By The Company In Previous Financial Year Ppt Infographics PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year ppt infographics pdf bundle. Topics like cyber attacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
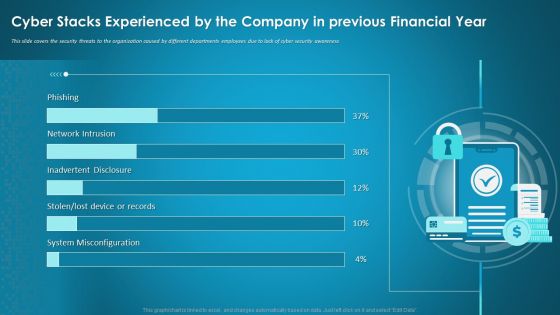
Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Summary PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative cyber stacks experienced by the company in previous financial year ppt summary pdf bundle. Topics like cyber stacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
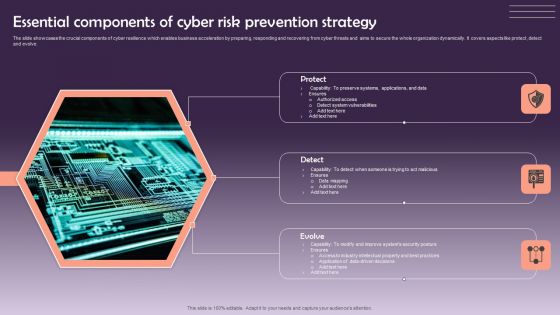
Essential Components Of Cyber Risk Prevention Strategy Information PDF
The slide showcases the crucial components of cyber resilience which enables business acceleration by preparing, responding and recovering from cyber threats and aims to secure the whole organization dynamically. It covers aspects like protect ,detect and evolve. Presenting Essential Components Of Cyber Risk Prevention Strategy Information PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Protect, Detect, Evolve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Email Security Market Research Report Ppt PowerPoint Presentation Complete Deck With Slides

Global Cloud Based Email Security Market Ppt PowerPoint Presentation Complete Deck With Slides


 Continue with Email
Continue with Email

 Home
Home


































