Cyber Security
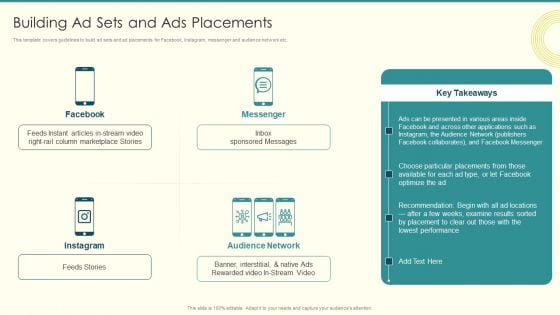
Security And Performance Digital Marketing Building Ad Sets And Ads Placements Professional PDF
This template covers guidelines to build ad sets and ad placements for Facebook, Instagram, messenger and audience network etc. Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Building Ad Sets And Ads Placements Professional PDF. Use them to share invaluable insights on Column Marketplace, Presented Various, Choose Particular and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
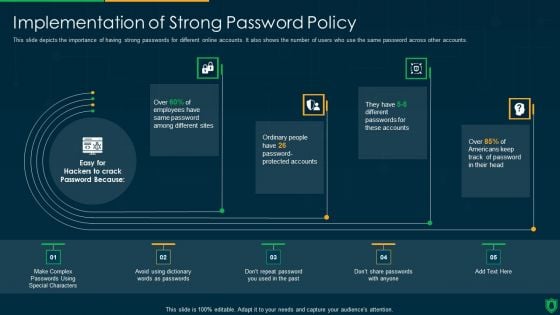
Info Security Implementation Of Strong Password Policy Ppt PowerPoint Presentation File Slide Download PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Deliver an awe inspiring pitch with this creative info security implementation of strong password policy ppt powerpoint presentation file slide download pdf bundle. Topics like implementation strong, password policy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
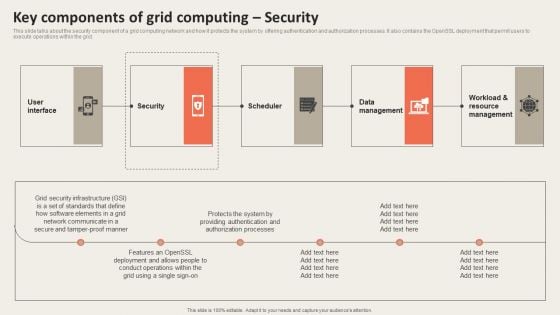
Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. This modern and well arranged Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
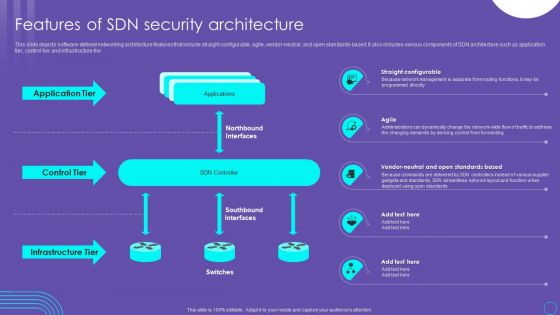
Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF
This slide depicts software defined networking architecture features that include straight configurable, agile, vendor neutral, and open standards based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier. Find highly impressive Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
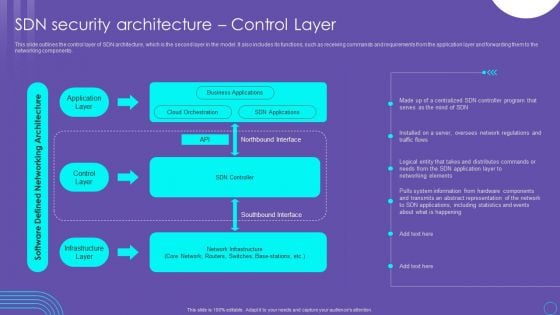
SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. If you are looking for a format to display your unique thoughts, then the professionally designed SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
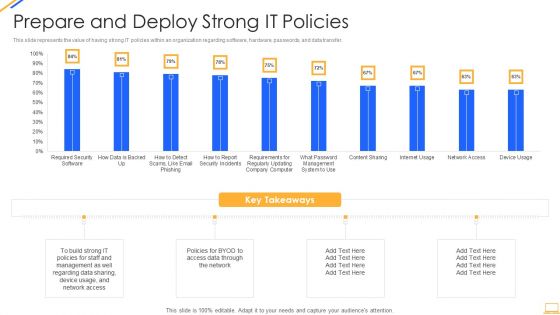
IT Security IT Prepare And Deploy Strong IT Policies Ppt Icon Design Ideas PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security it prepare and deploy strong it policies ppt icon design ideas pdf bundle. Topics like it policies, management, access, policies, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Desktop Security Management Prepare And Deploy Strong It Policies Template PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this desktop security management prepare and deploy strong it policies template pdf. Use them to share invaluable insights on management, data, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Example PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security prepare and deploy strong it policies ppt icon graphics example pdf bundle. Topics like management, it policies, network access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
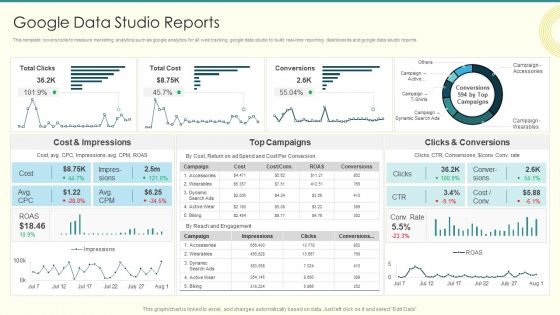
Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF bundle. Topics like Impressions, Clicks Conversions, Cost Impressions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black. Aim for the skies with our Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides. You will come out on top.
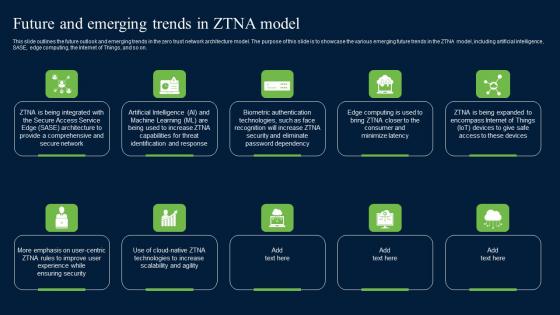
Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.
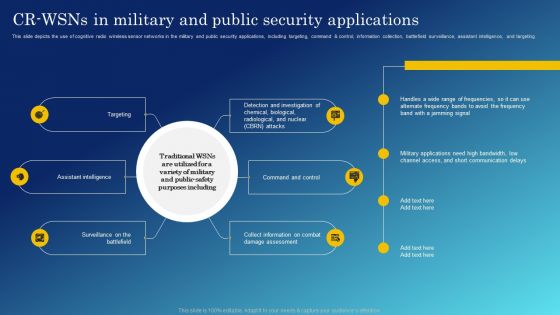
Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF
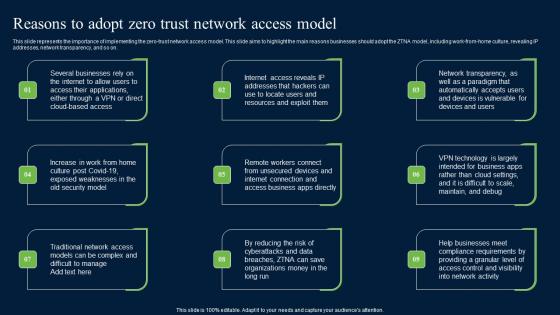
Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.
IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
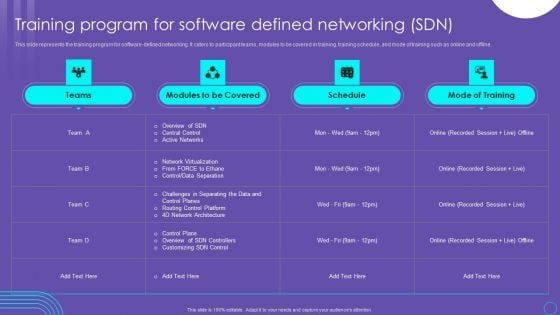
SDN Security Architecture Training Program For Software Defined Networking SDN Mockup PDF
This slide represents the training program for software defined networking. It caters to participant teams, modules to be covered in training, training schedule, and mode of training such as online and offline. There are so many reasons you need a SDN Security Architecture Training Program For Software Defined Networking SDN Mockup PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
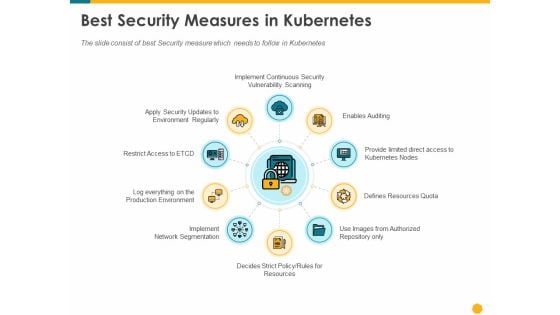
Deploying Docker Container And Kubernetes Within Organization Best Security Measures In Kubernetes Ppt PowerPoint Presentation PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization best security measures in kubernetes ppt powerpoint presentation pdf. This is a ten stage process. The stages in this process are enables auditing provide limited direct access kubernetes nodes, resources quota, authorized repository, rules resources, implement, network segmentation, log everything production environment, restrict access to etcd. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
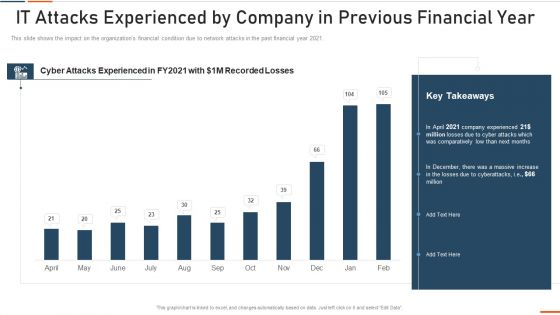
Information Technology Security IT Attacks Experienced By Company Ppt Show Grid PDF
This slide shows the impact on the organizations financial condition due to network attacks in the past financial year 2021. Deliver an awe inspiring pitch with this creative information technology security it attacks experienced by company ppt show grid pdf bundle. Topics like it attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
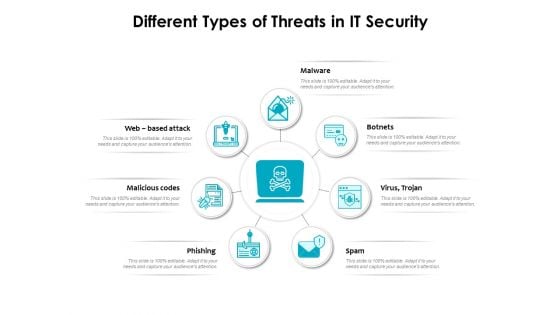
Different Types Of Threats In IT Security Ppt PowerPoint Presentation Portfolio Model PDF
Persuade your audience using this different types of threats in it security ppt powerpoint presentation portfolio model pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including malware, botnets, virus, trojan, spam, phishing, malicious codes, web based attack. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
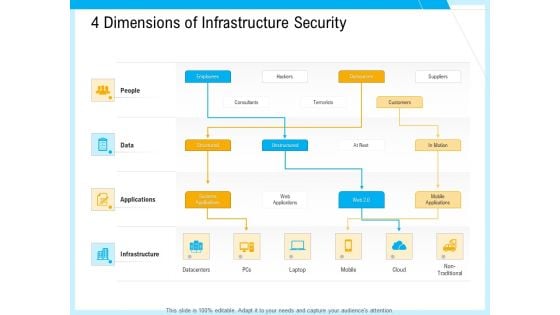
IT And Cloud Facilities Management 4 Dimensions Of Infrastructure Security Professional PDF
This is a it and cloud facilities management 4 dimensions of infrastructure security professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like structured, unstructured, systems applications, web applications, outsources, mobile applications, non traditional, datacenters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
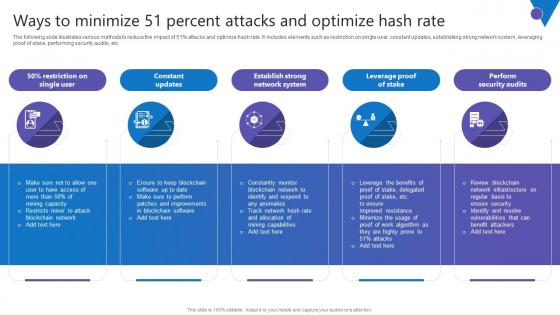
Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Present like a pro with Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc.

Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF
This template covers the cold calling email campaign strategy. It also depicts that TOFU should include introductory content focusing on brand, MOFU should include useful information about brand and, BOFU should include social proofs.Presenting Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Sample Reports, Testimonials, Landing Pages. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
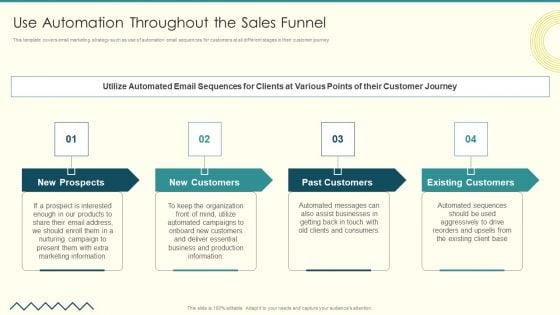
Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF
This template covers email marketing strategy such as use of automation email sequences for customers at all different stages in their customer journey . Presenting Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Past Customers, Existing Customers, Assist Businesses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Get a simple yet stunning designed How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc.
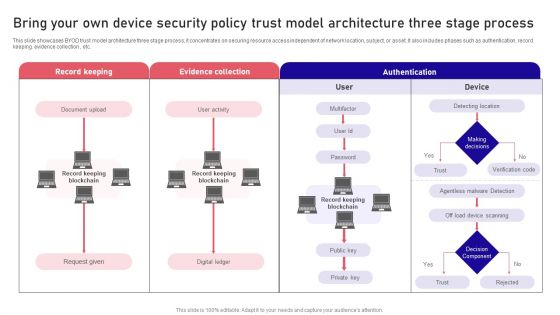
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Employee Awareness Training Budget For FY2020 IT Security IT Ppt Show Slides PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. This is a employee awareness training budget for fy2020 it security it ppt show slides pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like maintain, vulnerability, management, secure, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
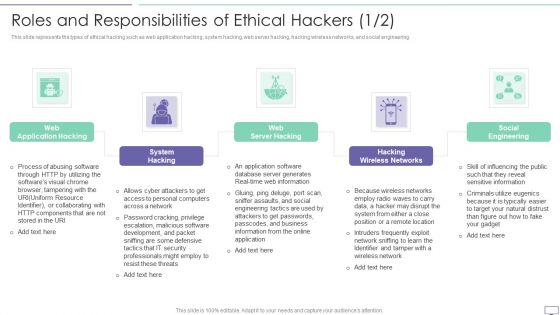
IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF
This template covers the use of automated software for email marketing. It also depicts that email marketing platforms engage allows users to create multiple sales flow with combination of manual and automated emails and phone calls.Presenting Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Combination Manual, Leads Prioritize, Identify Most. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
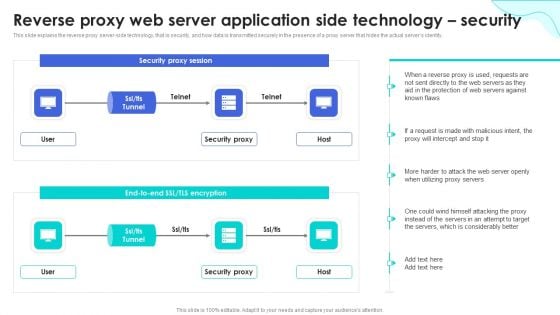
Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

IT Security IT Awareness Training For Staff Ppt Gallery Example Introduction PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this it security it awareness training for staff ppt gallery example introduction pdf. Use them to share invaluable insights on developers, organizations, senior executives, planning, strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
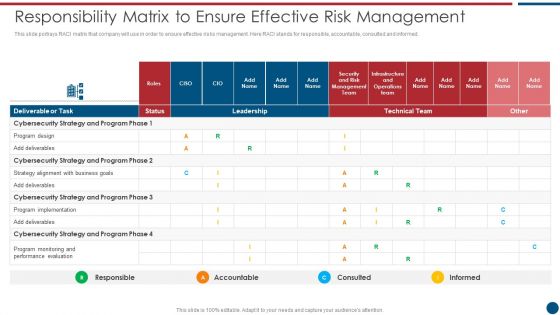
Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
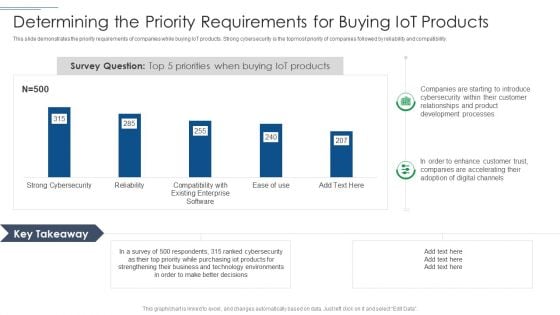
IT Security Risk Management Approach Introduction Determining The Priority Requirements Diagrams PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Determining The Priority Requirements Diagrams PDF bundle. Topics like Development Processes, Technology Environments, Purchasing Iot Products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
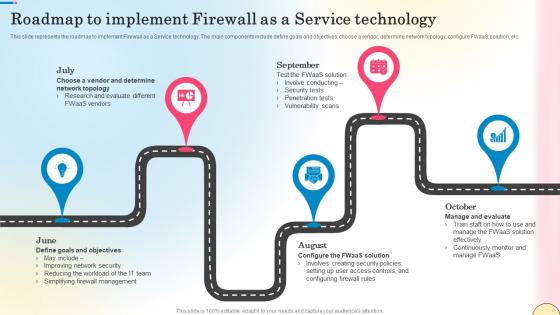
Roadmap To Implement Firewall As A Service Technology Network Security Themes Pdf
This slide represents the roadmap to implement Firewall as a Service technology. The main components include define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Roadmap To Implement Firewall As A Service Technology Network Security Themes Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the roadmap to implement Firewall as a Service technology. The main components include define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc.
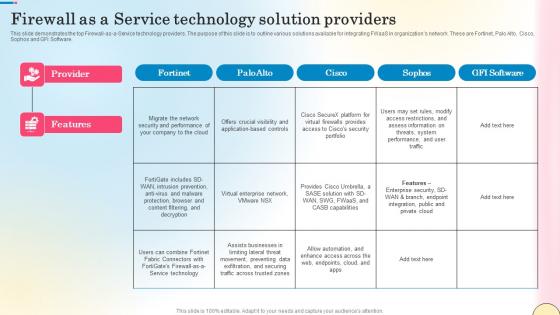
Firewall As A Service Technology Solution Providers Network Security Pictures Pdf
This slide demonstrates the top Firewall-as-a-Service technology providers. The purpose of this slide is to outline various solutions available for integrating FWaaS in organizations network. These are Fortinet, Palo Alto, Cisco, Sophos and GFI Software. Make sure to capture your audiences attention in your business displays with our gratis customizable Firewall As A Service Technology Solution Providers Network Security Pictures Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the top Firewall-as-a-Service technology providers. The purpose of this slide is to outline various solutions available for integrating FWaaS in organizations network. These are Fortinet, Palo Alto, Cisco, Sophos and GFI Software.
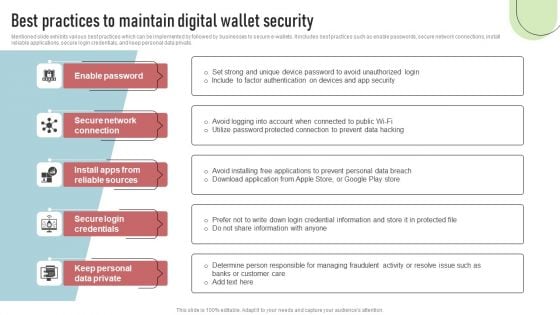
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
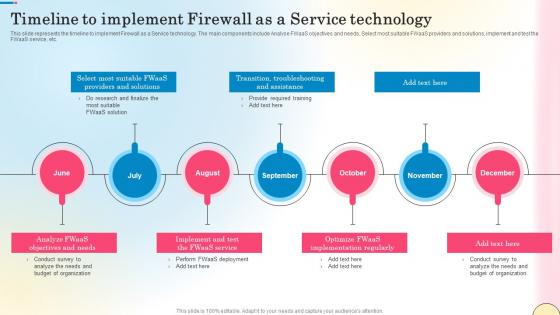
Timeline To Implement Firewall As A Service Technology Network Security Template Pdf
This slide represents the timeline to implement Firewall as a Service technology. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Firewall As A Service Technology Network Security Template Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the timeline to implement Firewall as a Service technology. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc.

Various Types Of Crypto Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. qDo you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Various Types Of Crypto Comprehensive Guide To Blockchain Digital Security Clipart Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Various Types Of Crypto Comprehensive Guide To Blockchain Digital Security Clipart Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc.

Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock On Keyboard Data Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas.Use these PowerPoint slides for presentations relating to A padlock on keyboard, computer, technology, marketing, business, success. The prominent colors used in the PowerPoint template are Yellow, Blue navy, White. Professionals tell us our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our marketing PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. You can be sure our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter look like a pro even if they are not computer savvy. PowerPoint presentation experts tell us our on PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. We assure you our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides look good visually. With our Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0113 there is no need to exaggerate. They are always brief and accurate.

Technologies Used In Zero Trust Network Access Zero Trust Network Security Portrait Pdf
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Present like a pro with Technologies Used In Zero Trust Network Access Zero Trust Network Security Portrait Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer.
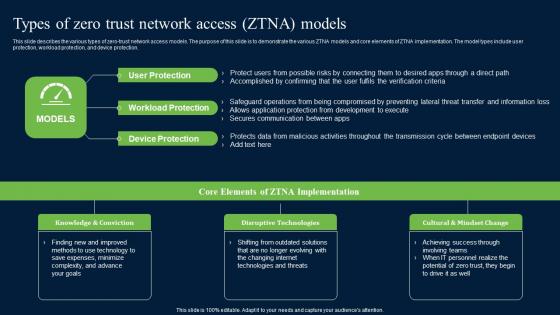
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
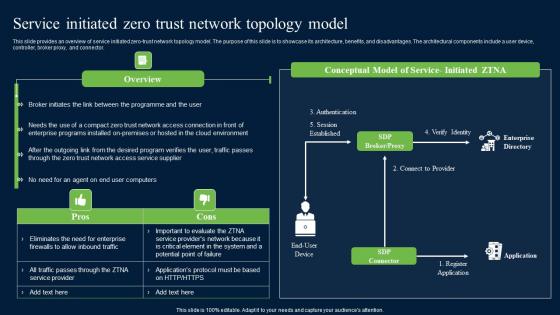
Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
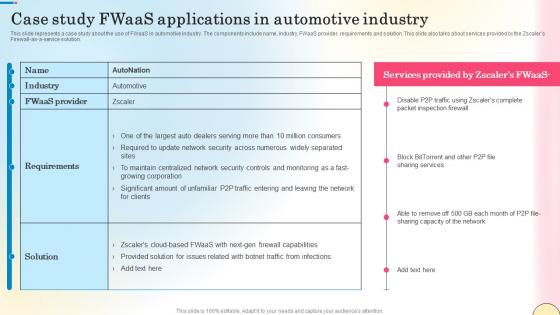
Case Study Fwaas Applications In Automotive Industry Network Security Clipart Pdf
This slide represents a case study about the use of FWaaS in automotive industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about services provided by the Zscalers Firewall-as-a-service solution. Present like a pro with Case Study Fwaas Applications In Automotive Industry Network Security Clipart Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents a case study about the use of FWaaS in automotive industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about services provided by the Zscalers Firewall-as-a-service solution.
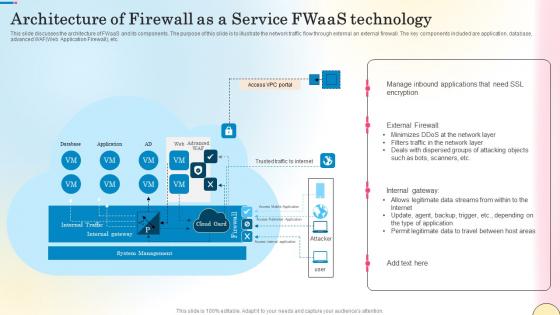
Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf
This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc. Want to ace your presentation in front of a live audience Our Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc.
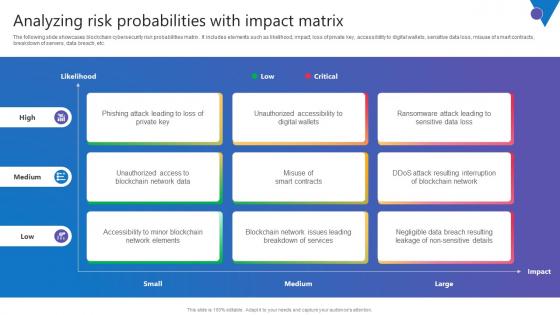
Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Presenting this PowerPoint presentation, titled Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc.
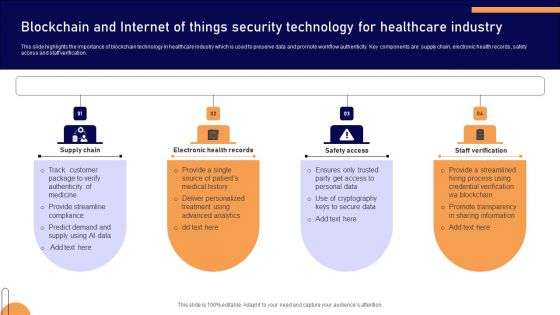
Blockchain And Internet Of Things Security Technology For Healthcare Industry Mockup PDF

Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

House And Question Mark Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our House And Question Mark Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Network diagrams PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Download our Communication PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune.Use these PowerPoint slides for presentations relating to Question mark with house,business, finance, success, signs, marketing . The prominent colors used in the PowerPoint template are Blue, Gray, Blue. Specify paths to success with our House And Question Mark Security PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.
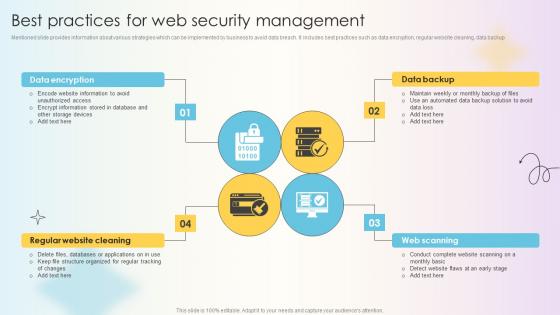
Managing Technical And Non Technical Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup Present like a pro with Managing Technical And Non Technical Best Practices For Web Security Management. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.
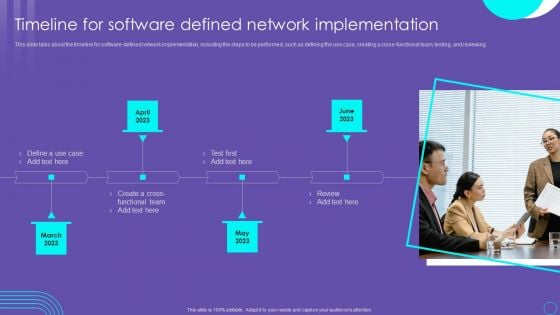
SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF
This slide talks about the timeline for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Want to ace your presentation in front of a live audience Our SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
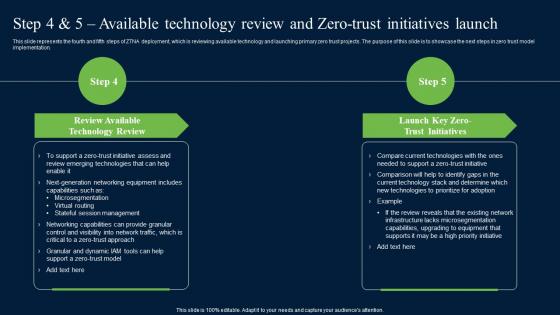
Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. There are so many reasons you need a Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
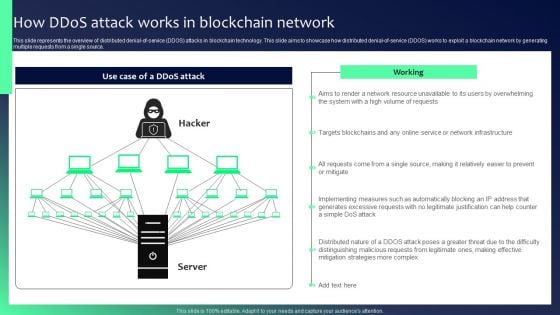
Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF
This slide represents the overview of distributed denial-of-service DDOS attacks in blockchain technology. This slide aims to showcase how distributed denial-of-service DDOS works to exploit a blockchain network by generating multiple requests from a single source. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
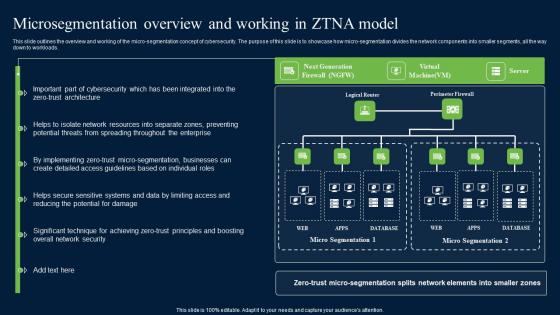
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF
This slide represents the impact of software defined networking that has majorly impacted IT infrastructure management and network architecture. It also includes how it enables access to network switches and routers rather than restricted and licensed firmware. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF from Slidegeeks and deliver a wonderful presentation.
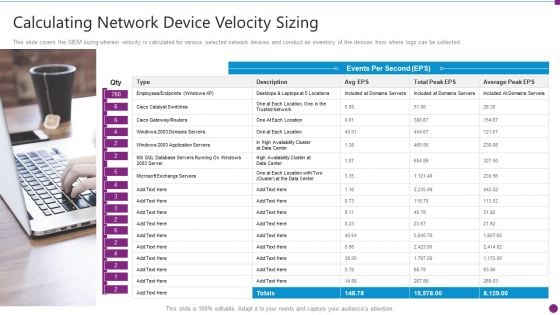
Security Information And Event Management Strategies For Financial Audit And Compliance Calculating Network Device Inspiration PDF
This slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Presenting security information and event management strategies for financial audit and compliance calculating network device inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like calculating network device velocity sizing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
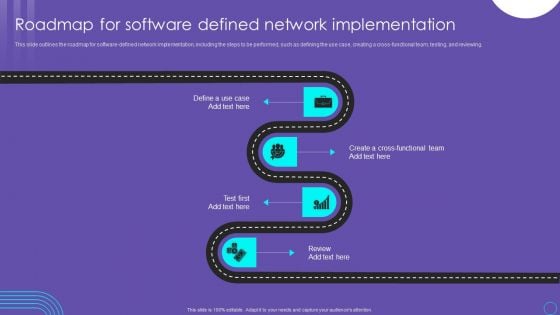
SDN Security Architecture Roadmap For Software Defined Network Implementation Slides PDF
This slide outlines the roadmap for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Find a pre designed and impeccable SDN Security Architecture Roadmap For Software Defined Network Implementation Slides PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Organizational Network Security Awareness Staff Learning Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in-house and outside by utilizing this complete deck. This organizational network security awareness staff learning ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well-researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.


 Continue with Email
Continue with Email

 Home
Home


































