Cyber Security
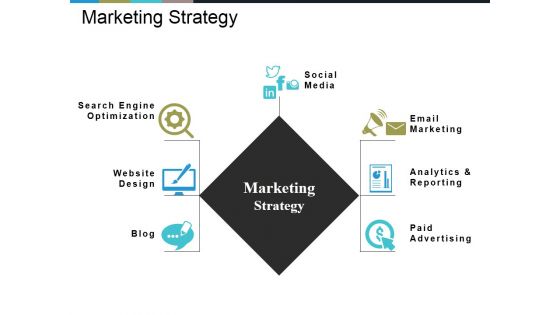
Marketing Strategy Ppt PowerPoint Presentation File Formats
This is a marketing strategy ppt powerpoint presentation file formats. This is a six stage process. The stages in this process are website design, blog, social media, paid advertising, email marketing.
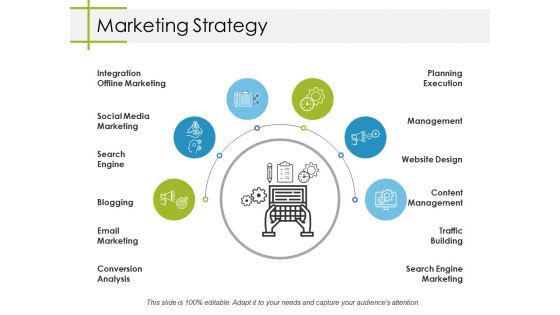
Marketing Strategy Ppt PowerPoint Presentation Clipart
This is a marketing strategy ppt powerpoint presentation clipart. This is a six stage process. The stages in this process are social media marketing, search engine, blogging, email marketing, conversion analysis.

Sales Strategy Consulting Scope Of Marketing Services Advisory Proposal Inspiration PDF
Presenting this set of slides with name sales strategy consulting scope of marketing services advisory proposal inspiration pdf. This is a five stage process. The stages in this process are research, planning and development, guest posts and email campaigns, sales process workshop, social media management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
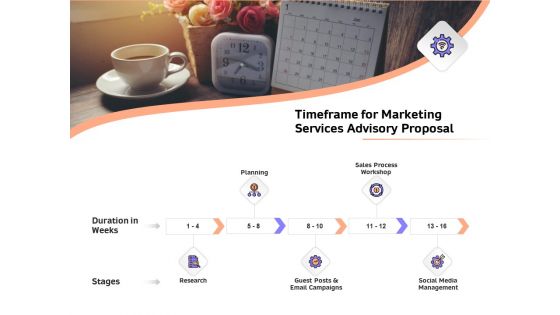
Sales Strategy Consulting Timeframe For Marketing Services Advisory Proposal Background PDF
Presenting this set of slides with name sales strategy consulting timeframe for marketing services advisory proposal background pdf. This is a five stage process. The stages in this process are research, planning and development, guest posts and email campaigns, sales process workshop, social media management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Sales Strategy Consulting Your Investment For Marketing Services Advisory Proposal Cost Information PDF
Presenting this set of slides with name sales strategy consulting your investment for marketing services advisory proposal cost information pdf. The topics discussed in these slides are research, planning and development, guest posts and email campaigns, sales process workshop, social media management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
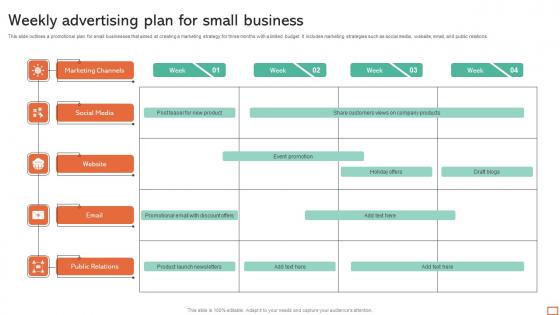
Weekly Advertising Plan For Small Business Infographics Pdf
This slide outlines a promotional plan for small businesses that aimed at creating a marketing strategy for three months with a limited budget. It includes marketing strategies such as social media, website, email, and public relations. Showcasing this set of slides titled Weekly Advertising Plan For Small Business Infographics Pdf. The topics addressed in these templates are Marketing Channels, Social Media, Public Relations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines a promotional plan for small businesses that aimed at creating a marketing strategy for three months with a limited budget. It includes marketing strategies such as social media, website, email, and public relations.
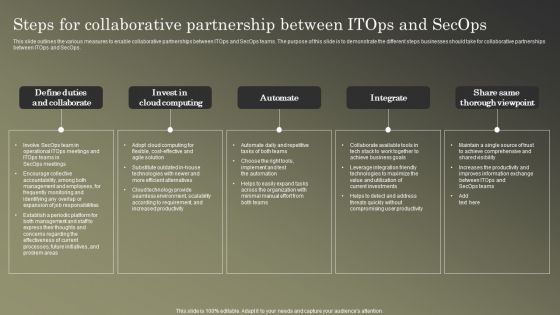
Cybersecurity Operations Cybersecops Steps For Collaborative Partnership Background PDF
This slide outlines the various measures to enable collaborative partnerships between ITOps and SecOps teams. The purpose of this slide is to demonstrate the different steps businesses should take for collaborative partnerships between ITOps and SecOps. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cybersecurity Operations Cybersecops Steps For Collaborative Partnership Background PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cybersecurity Operations Cybersecops Steps For Collaborative Partnership Background PDF today and make your presentation stand out from the rest.

Cybersecurity Operations Cybersecops Case Study Pharmaceutical Company Summary PDF
This slide depicts the overview of a case study of the pharmaceutical company. The purpose of this slide is to highlight the clients requirements, services offered by the SecOps service provider and the impact of provided solutions on the client company. Create an editable Cybersecurity Operations Cybersecops Case Study Pharmaceutical Company Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cybersecurity Operations Cybersecops Case Study Pharmaceutical Company Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cybersecurity Operations Cybersecops Before Vs After Secops Implementation Inspiration PDF
This slide represents the impact of the successful implementation of SecOps in the organization by showing the reduced number of malware attacks on departments. The purpose of this slide is to highlight the reduced number of malware attacks on different departments after implementing SecOps. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops Before Vs After Secops Implementation Inspiration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops Before Vs After Secops Implementation Inspiration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
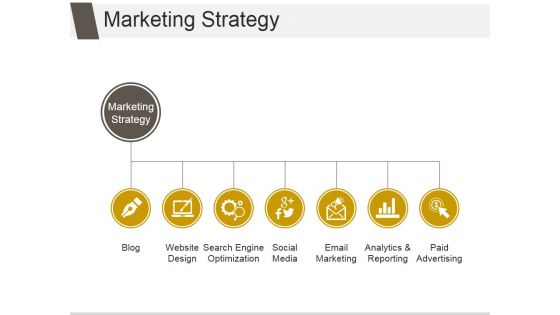
Marketing Strategy Ppt PowerPoint Presentation Summary
This is a marketing strategy ppt powerpoint presentation summary. This is a seven stage process. The stages in this process are blog, website design, search engine optimization, social media, email marketing, analytics and reporting, paid advertising.

Marketing Strategy Ppt PowerPoint Presentation Layouts Background
This is a marketing strategy ppt powerpoint presentation layouts background. This is a seven stage process. The stages in this process are social media, email marketing, analytics and reporting, paid advertising, search engine optimization, website design, blog.
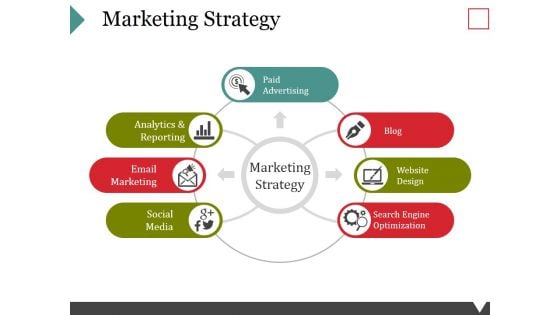
Marketing Strategy Ppt PowerPoint Presentation Portfolio Inspiration
This is a marketing strategy ppt powerpoint presentation portfolio inspiration. This is a seven stage process. The stages in this process are paid advertising, analytics and reporting, email marketing, social media blog, website design, search engine optimization.

Cybersecurity Minimize Administrative And Staff Privileges Ppt Layouts Grid PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting cybersecurity minimize administrative and staff privileges ppt layouts grid pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimize administrative and staff privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Critical Business Information PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities addressing critical business information pdf bundle. Topics like addressing critical business functions recovery priorities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Natural Calamities Template PDF
This slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities addressing natural calamities template pdf bundle. Topics like threat management checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Mitigating Cybersecurity Threats And Vulnerabilities Determine Threat Scenario Rules PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities determine threat scenario rules pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Evaluating Financial Practices Themes PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities evaluating financial practices themes pdf bundle. Topics like evaluating financial practices in firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Mitigating Cybersecurity Threats And Vulnerabilities Financial Performance Tracking Designs PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities financial performance tracking designs pdf. Use them to share invaluable insights on receivables analysis, revenue and expense trends and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Technological Assessment Sample PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities technological assessment sample pdf bundle. Topics like Industry Standard, Firms Standard, Client Onboarding, Service Failure Rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
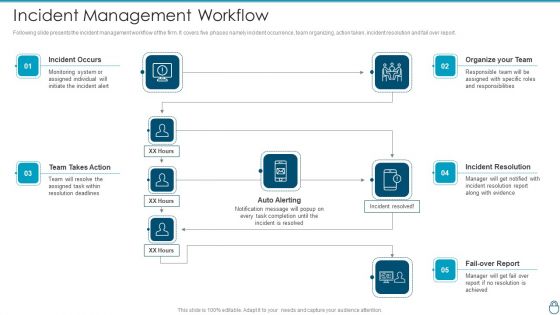
Cybersecurity Risk Administration Plan Incident Management Workflow Guidelines PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Incident Management Workflow Guidelines PDF bundle. Topics like Organize Your Team, Incident Resolution, Team Takes Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
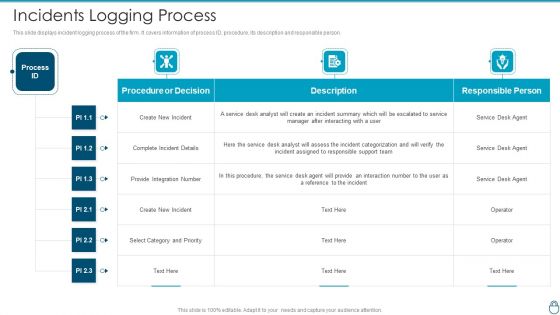
Cybersecurity Risk Administration Plan Incidents Logging Process Sample PDF
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Incidents Logging Process Sample PDF Use them to share invaluable insights on Incident Assigned, Select Category And Priority, Reference To The Incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
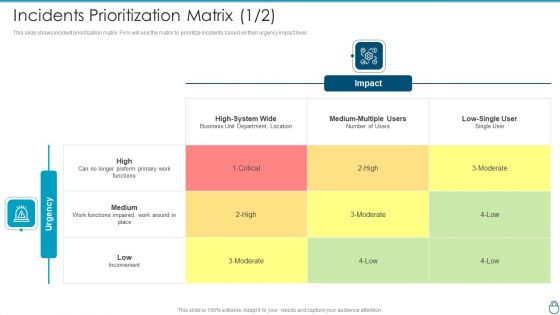
Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Business Introduction PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Business Introduction PDF bundle. Topics like Business Unit Department, Functions Impaired, Medium Multiple can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Service Information PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Service Information PDF Use them to share invaluable insights on Enterprise Or Multiple Segments, Event Imminent, Affecting Service and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Risk Reporting And Likelihood Summary PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Risk Reporting And Likelihood Summary PDF bundle. Topics like Unavailability Of Power, Risk Encountered, Attack Scenario can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
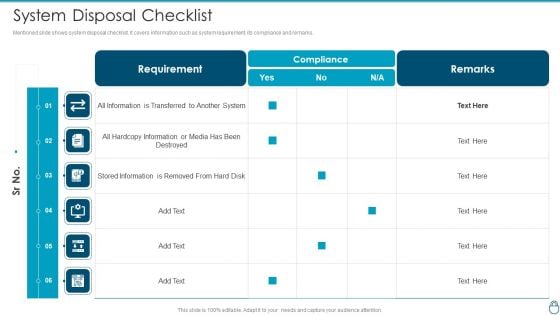
Cybersecurity Risk Administration Plan System Disposal Checklist Guidelines PDF
Mentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan System Disposal Checklist Guidelines PDF bundle. Topics like Information Is Transferred, Hardcopy Information, Stored Information Is Removed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cybersecurity Risk Administration Plan Defining Risk Level Icons PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Defining Risk Level Icons PDF bundle. Topics like Extremely Critical, Requires Immediate, Operations Of Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF Use them to share invaluable insights on Organization Is Not Capable, Resisting The Occurrence Of Attack, Drawback Is Identified and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
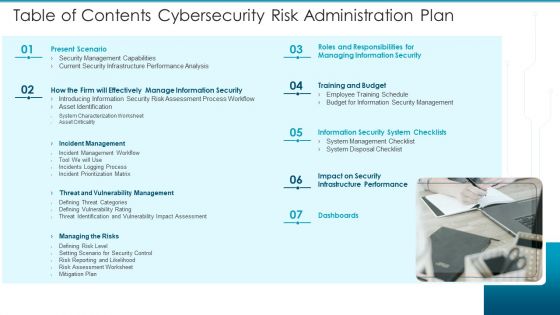
Table Of Contents Cybersecurity Risk Administration Plan Introduction PDF
This is a Table Of Contents Cybersecurity Risk Administration Plan Introduction PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Present Scenario, Training And Budget, Managing The Risks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financial Cybersecurity Risk Assessment And Administration Plan Professional PDF
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Financial Cybersecurity Risk Assessment And Administration Plan Professional PDF from Slidegeeks and deliver a wonderful presentation.
Roadmap Cybersecurity Risk Assessment And Administration Plan Themes PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Roadmap Cybersecurity Risk Assessment And Administration Plan Themes PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

SWOT Analysis Cybersecurity Risk Assessment And Administration Plan Summary PDF
Want to ace your presentation in front of a live audience Our SWOT Analysis Cybersecurity Risk Assessment And Administration Plan Summary PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Table Of Contents Improving Cybersecurity With Incident Summary PDF
Slidegeeks has constructed Table Of Contents Improving Cybersecurity With Incident Summary PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
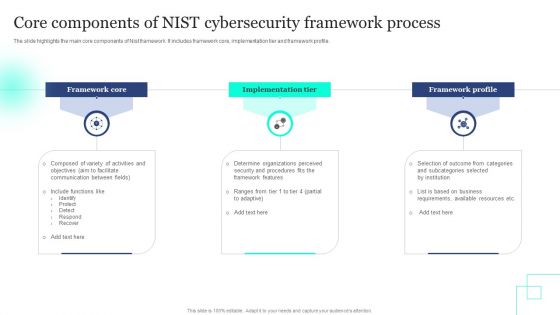
Core Components Of NIST Cybersecurity Framework Process Topics PDF
The slide highlights the main core components of Nist framework. It includes framework core, implementation tier and framework profile. Presenting Core Components Of NIST Cybersecurity Framework Process Topics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Framework Core, Implementation Tier, Framework Profile. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
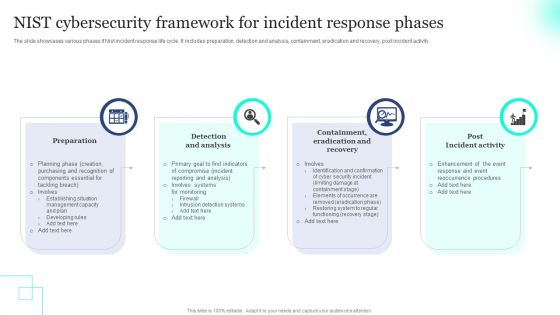
NIST Cybersecurity Framework For Incident Response Phases Pictures PDF
The slide showcases various phases if Nist incident response life cycle. It includes preparation, detection and analysis, containment, eradication and recovery, post incident activity. Presenting NIST Cybersecurity Framework For Incident Response Phases Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Preparation, Recovery, Incident Activity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops Comparison Between Secops And Ideas PDF
This slide outlines the difference between SecOps and ITOps teams. The purpose of this slide is to highlight the critical differences between SecOps and ITOps teams based on focus, responsibilities, skills, and output. There are so many reasons you need a Cybersecurity Operations Cybersecops Comparison Between Secops And Ideas PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Marketing Strategy Ppt PowerPoint Presentation Slides Visual Aids
This is a marketing strategy ppt powerpoint presentation slides visual aids. This is a eight stage process. The stages in this process are email marketing, analytics and reporting, paid advertising, collaboration, website design.
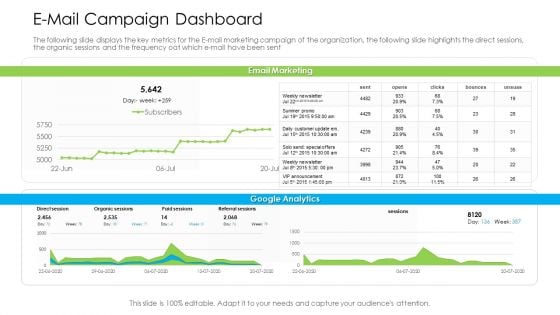
Marketing Techniques Online Offline Commercial Activities E Mail Campaign Dashboard Information PDF
The following slide displays the key metrics for the E-mail marketing campaign of the organization, the following slide highlights the direct sessions, the organic sessions and the frequency oat which e-mail have been sent Deliver an awe inspiring pitch with this creative marketing techniques online offline commercial activities e mail campaign dashboard information pdf bundle. Topics like e mail campaign dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
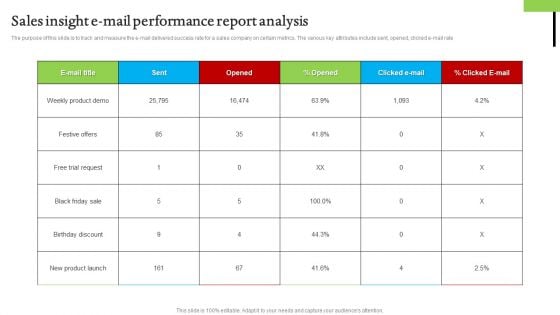
Sales Insight E Mail Performance Report Analysis Brochure PDF
The purpose of this slide is to track and measure the e-mail delivered success rate for a sales company on certain metrics. The various key attributes include sent, opened, clicked e-mail rate Showcasing this set of slides titled Sales Insight E Mail Performance Report Analysis Brochure PDF. The topics addressed in these templates are Sales Insight E Mail, Performance Report Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
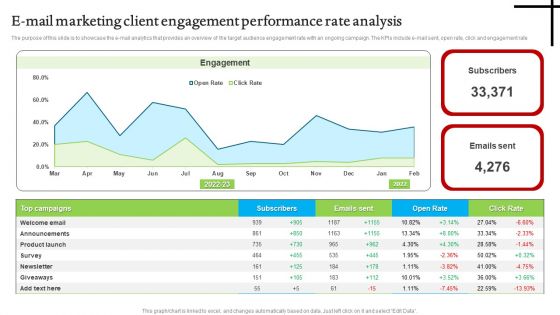
E Mail Marketing Client Engagement Performance Rate Analysis Ideas PDF
The purpose of this slide is to showcase the e-mail analytics that provides an overview of the target audience engagement rate with an ongoing campaign. The KPIs include e-mail sent, open rate, click and engagement rate. Showcasing this set of slides titled E Mail Marketing Client Engagement Performance Rate Analysis Ideas PDF. The topics addressed in these templates are E Mail Marketing, Client Engagement Performance, Rate Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
E Mail Performance Analytics Metrics Tracking Report Analysis Demonstration PDF
The purpose of this slide is to showcase an e-mail analytics mechanism in order to track the performance of certain e-mail marketing based on various metrics. Certain KPIs include open rate, click rate, unsubscribe rate etc. Pitch your topic with ease and precision using this E Mail Performance Analytics Metrics Tracking Report Analysis Demonstration PDF. This layout presents information on E Mail Performance Analytics, Metrics Tracking Report Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
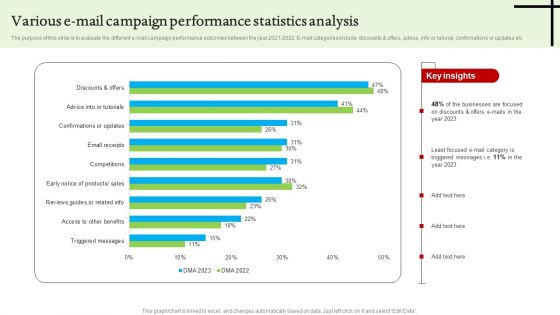
Various E Mail Campaign Performance Statistics Analysis Graphics PDF
The purpose of this slide is to evaluate the different e-mail campaign performance outcomes between the year 2021-2022. E-mail categories include discounts and offers, advice, info or tutorial, confirmations or updates etc. Showcasing this set of slides titled Various E Mail Campaign Performance Statistics Analysis Graphics PDF. The topics addressed in these templates are Various E Mail Campaign, Performance Statistics Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
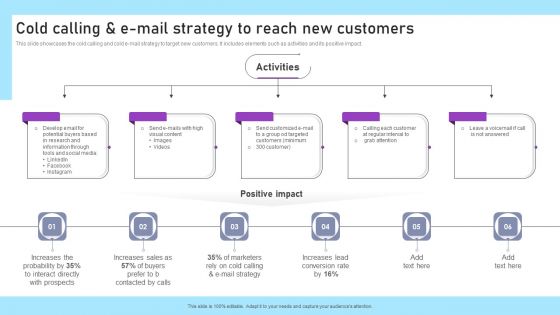
Inbound And Outbound Marketing Tactics Cold Calling And E Mail Strategy To Reach New Customers Sample PDF
This slide showcases the cold calling and cold e-mail strategy to target new customers. It includes elements such as activities and its positive impact. Make sure to capture your audiences attention in your business displays with our gratis customizable Inbound And Outbound Marketing Tactics Cold Calling And E Mail Strategy To Reach New Customers Sample PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
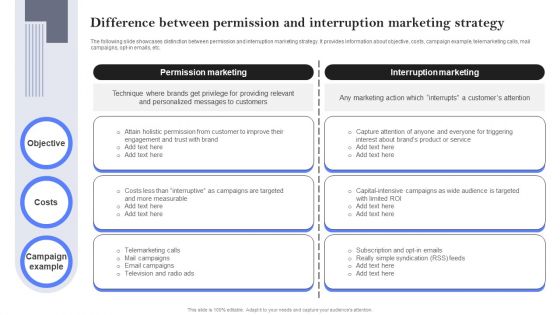
Difference Between Permission And Interruption Marketing Strategy Microsoft PDF
Cybersecurity Types Of Disaster Recovery Plan Ppt Icon Styles PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud based disaster recovery plans, etc. Presenting cybersecurity types of disaster recovery plan ppt icon styles pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like types of disaster recovery plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
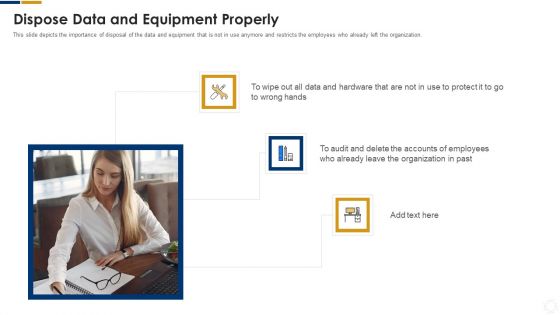
Cybersecurity Dispose Data And Equipment Properly Ppt Model Templates PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting cybersecurity dispose data and equipment properly ppt model templates pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
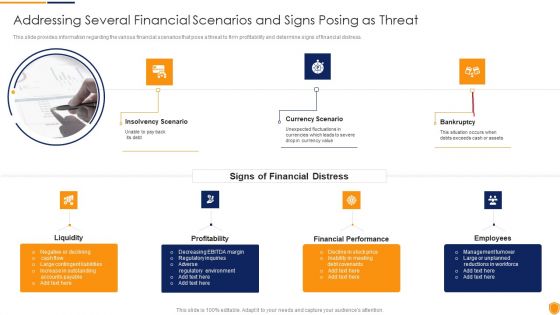
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Several Financial Diagrams PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. This is a mitigating cybersecurity threats and vulnerabilities addressing several financial diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insolvency scenario, currency scenario, bankruptcy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
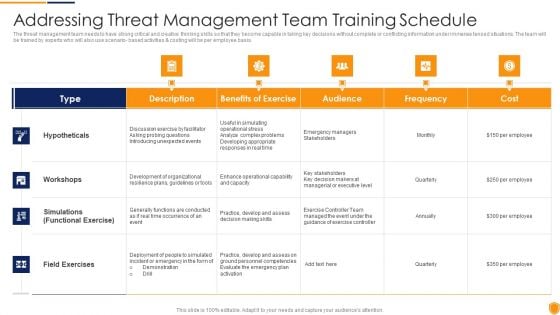
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Threat Management Download PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities addressing threat management download pdf bundle. Topics like hypotheticals, workshops, field exercises can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user
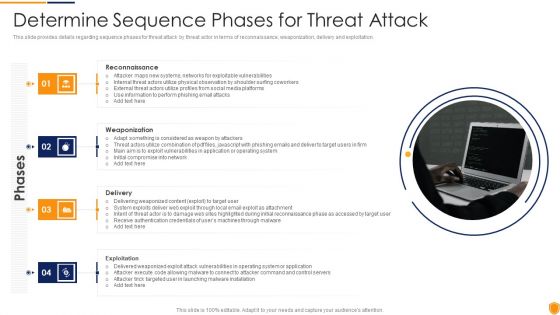
Mitigating Cybersecurity Threats And Vulnerabilities Determine Sequence Phases Elements PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a mitigating cybersecurity threats and vulnerabilities determine sequence phases elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
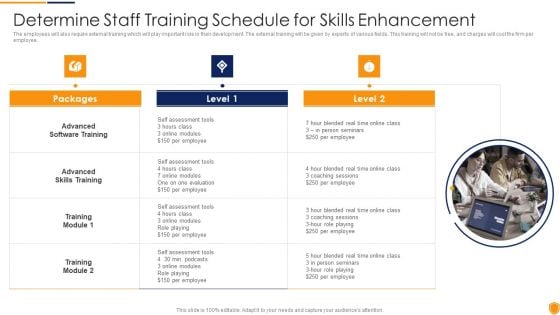
Mitigating Cybersecurity Threats And Vulnerabilities Determine Staff Training Rules PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This is a mitigating cybersecurity threats and vulnerabilities determine staff training rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advanced software training, advanced skills training, training module. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Determine Threat Management Brochure PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting mitigating cybersecurity threats and vulnerabilities determine threat management brochure pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
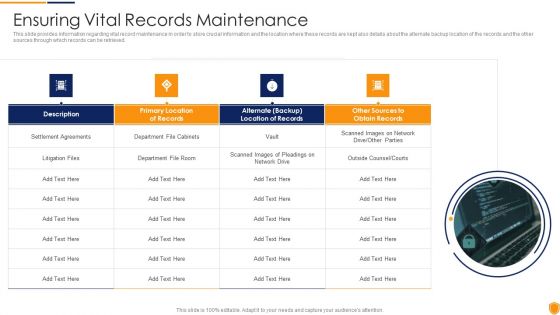
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Vital Records Inspiration PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. This is a mitigating cybersecurity threats and vulnerabilities ensuring vital records inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring vital records maintenance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities How Financial Risk Formats PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting mitigating cybersecurity threats and vulnerabilities how financial risk formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like liquidity risk, exchange risk, credit exchange risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Themes PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting mitigating cybersecurity threats and vulnerabilities incident reporting themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
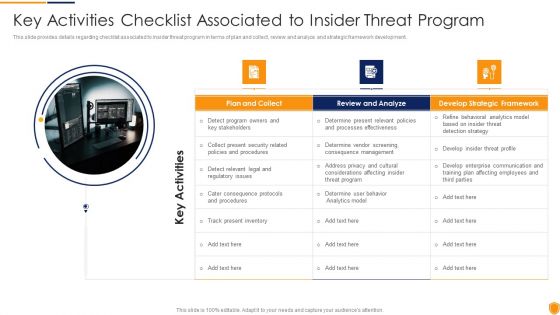
Mitigating Cybersecurity Threats And Vulnerabilities Key Activities Checklist Diagrams PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a mitigating cybersecurity threats and vulnerabilities key activities checklist diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collect, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
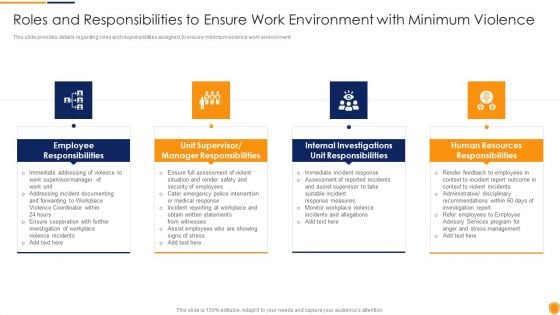
Mitigating Cybersecurity Threats And Vulnerabilities Roles And Responsibilities Introduction PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a mitigating cybersecurity threats and vulnerabilities roles and responsibilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, manager responsibilities, unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Statistics Associated Mockup PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. This is a mitigating cybersecurity threats and vulnerabilities statistics associated mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like statistics associated to workplace threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Threat Management Action Graphics PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities threat management action graphics pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Workplace Employee Rules PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting mitigating cybersecurity threats and vulnerabilities workplace employee rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical services, work and life services, employer services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Risk Administration Plan Employee Training Schedule Graphics PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration.This is a Cybersecurity Risk Administration Plan Employee Training Schedule Graphics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Training Schedule You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
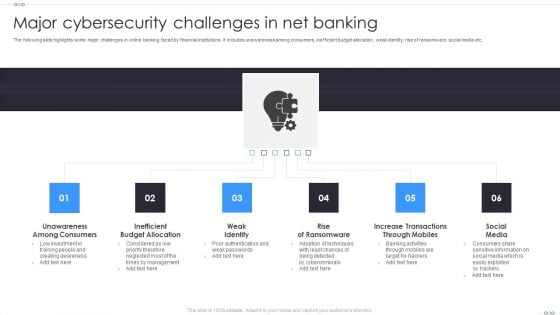
Major Cybersecurity Challenges In Net Banking Graphics PDF
The following slide highlights some major challenges in online banking faced by financial institutions. It includes unawareness among consumers, inefficient budget allocation, weak identity, rise of ransomware, social media etc. Persuade your audience using this Major Cybersecurity Challenges In Net Banking Graphics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Inefficient Budget Allocation, Rise Of Ransomware, Social Media. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































