Cyber Threat
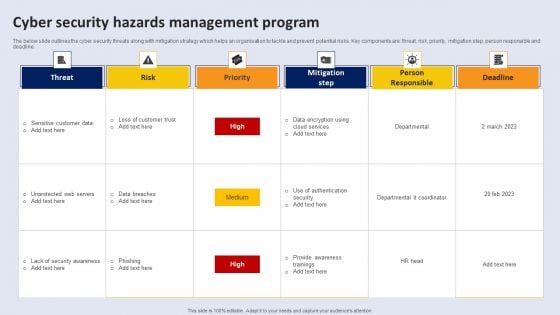
Cyber Security Hazards Management Program Pictures PDF
The below slide outlines the cyber security threats along with mitigation strategy which helps an organisation to tackle and prevent potential risks. Key components are threat, risk, priority, mitigation step, person responsible and deadline.Showcasing this set of slides titled Cyber Security Hazards Management Program Pictures PDF. The topics addressed in these templates are Sensitive Customer, Data Encryption Using. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
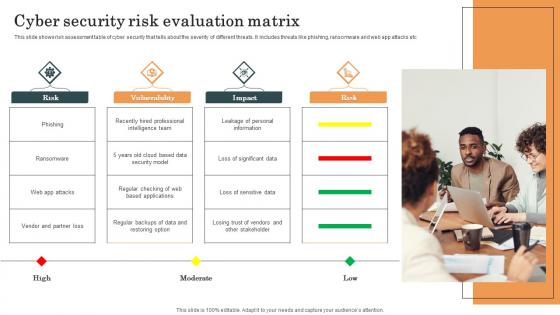
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.
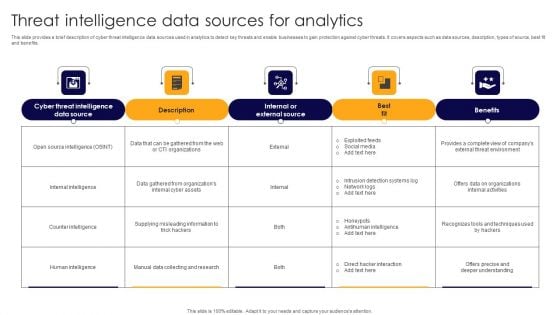
Threat Intelligence Data Sources For Analytics Ideas PDF
This slide provides a brief description of cyber threat intelligence data sources used in analytics to detect key threats and enable businesses to gain protection against cyber threats. It covers aspects such as data sources, description, types of source, best fit and benefits. Showcasing this set of slides titled Threat Intelligence Data Sources For Analytics Ideas PDF. The topics addressed in these templates are Exploited Feeds, Social Media, Intrusion Detection Systems Log. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
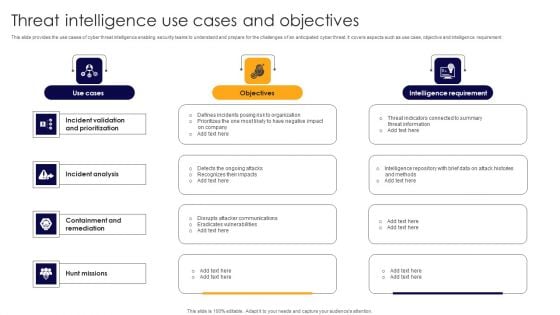
Threat Intelligence Use Cases And Objectives Demonstration PDF
This slide provides the use cases of cyber threat intelligence enabling security teams to understand and prepare for the challenges of an anticipated cyber threat. It covers aspects such as use case, objective and intelligence requirement. Presenting Threat Intelligence Use Cases And Objectives Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Analysis, Containment Remediation, Hunt Missions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
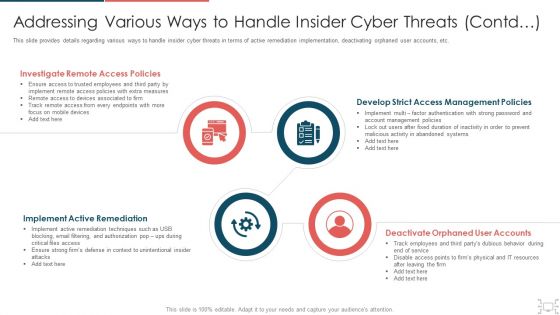
cyber security administration in organization addressing various ways to handle insider cyber active template pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting cyber security administration in organization addressing various ways to handle insider cyber active template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like investigate, access, policies, remediation, implement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
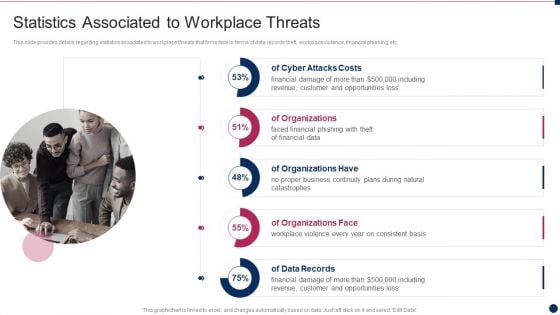
Threat Management At Workplace Statistics Associated To Workplace Threats Summary PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver an awe inspiring pitch with this creative threat management at workplace statistics associated to workplace threats summary pdf bundle. Topics like cyber attacks costs, organization, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
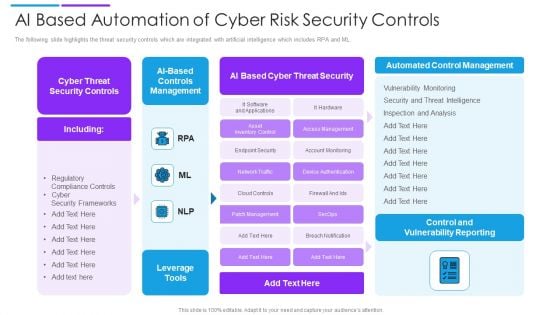
AI Based Automation Of Cyber Risk Security Controls Summary PDF
The following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Showcasing this set of slides titled ai based automation of cyber risk security controls summary pdf. The topics addressed in these templates are controls management, cyber threat security controls, ai based cyber threat security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Present like a pro with Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
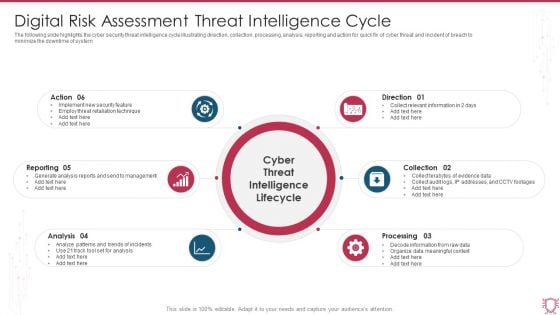
Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF
The following slide highlights the cyber security threat intelligence cycle illustrating direction, collection, processing, analysis, reporting and action for quick fix of cyber threat and incident of breach to minimize the downtime of system. Persuade your audience using this Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Reporting, Analysis, Processing, Direction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
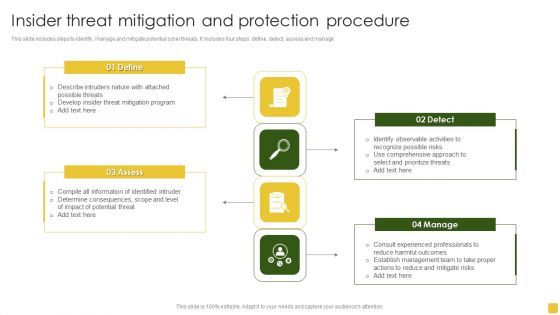
Insider Threat Mitigation And Protection Procedure Professional PDF
This slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage.Presenting Insider Threat Mitigation And Protection Procedure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigation Program, Compile Information, Determine Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
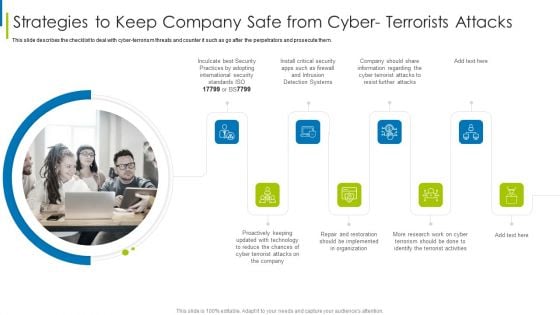
Cyber Terrorism Assault Strategies To Keep Company Safe From Cyber Terrorists Attacks Pictures PDF
This slide describes the checklist to deal with cyber terrorism threats and counter it such as go after the perpetrators and prosecute them.Presenting cyber terrorism assault strategies to keep company safe from cyber terrorists attacks pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like inculcate best security, practices by adopting, international security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
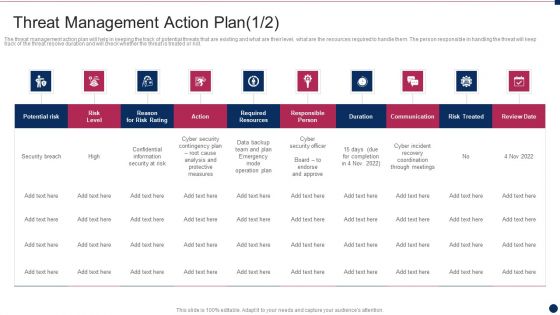
Threat Management At Workplace Threat Management Action Plan Responsible Person Template PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this threat management at workplace threat management action plan responsible person template pdf. Use them to share invaluable insights on cyber incident recovery coordination through meetings, confidential information security at risk, cyber security officer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
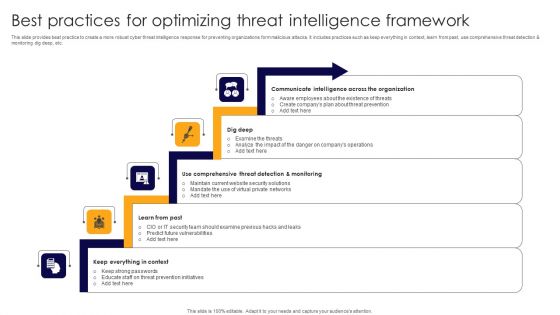
Best Practices For Optimizing Threat Intelligence Framework Formats PDF
This slide provides beat practice to create a more robust cyber threat intelligence response for preventing organizations form malicious attacks. It includes practices such as keep everything in context, learn from past, use comprehensive threat detection and monitoring dig deep, etc. Presenting Best Practices For Optimizing Threat Intelligence Framework Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Communicate Intelligence, Dig Deep, Comprehensive Threat Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
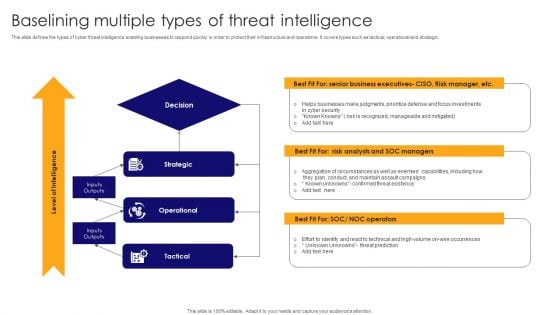
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
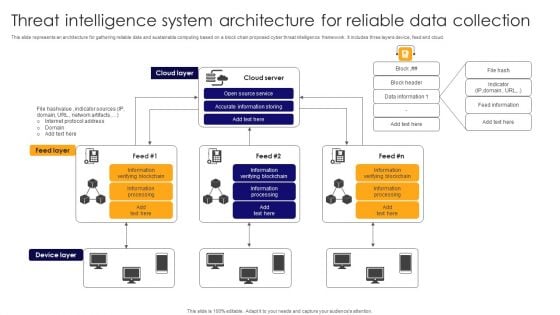
Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF
This slide represents an architecture for gathering reliable data and sustainable computing based on a block chain proposed cyber threat intelligence framework . It includes three layers device, feed and cloud. Showcasing this set of slides titled Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF. The topics addressed in these templates are Cloud Server, Accurate Information Storing, Open Source Service. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
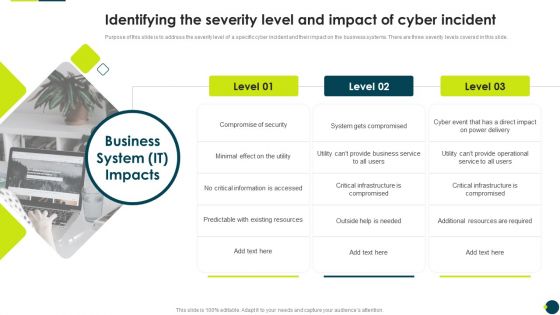
IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Presenting IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Compromise Security, Information Accessed, Existing Resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
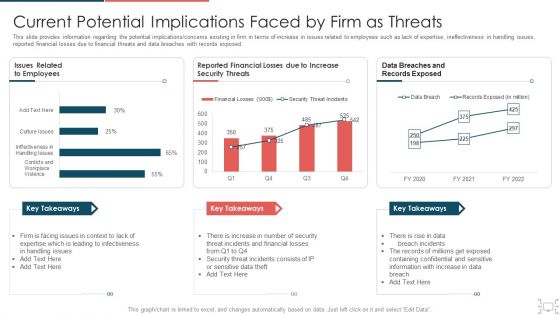
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
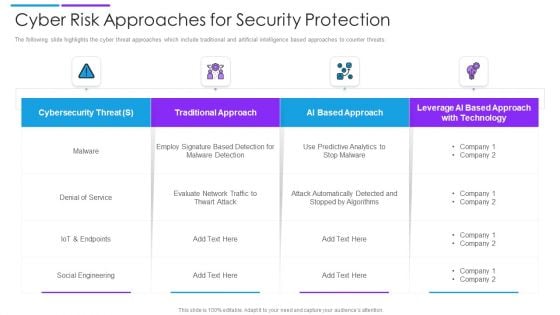
Cyber Risk Approaches For Security Protection Structure PDF
The following slide highlights the cyber threat approaches which include traditional and artificial intelligence based approaches to counter threats. Showcasing this set of slides titled cyber risk approaches for security protection structure pdf. The topics addressed in these templates are traditional approach, ai based approach, cybersecurity threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
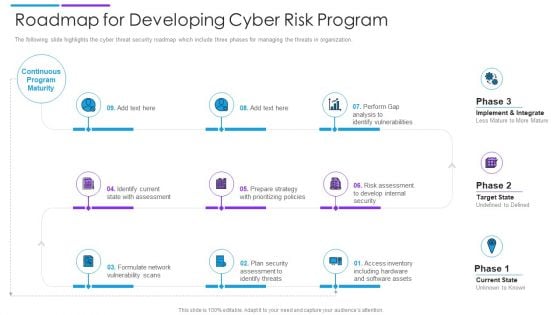
Roadmap For Developing Cyber Risk Program Download PDF
The following slide highlights the cyber threat security roadmap which include three phases for managing the threats in organization. Persuade your audience using this roadmap for developing cyber risk program download pdf. This PPT design covers nine stages, thus making it a great tool to use. It also caters to a variety of topics including internal security, software assets, identify threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
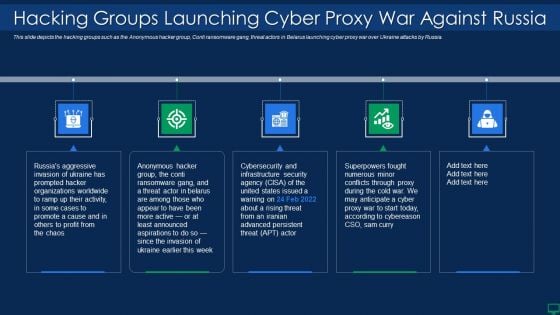
Russian Cyber Attacks On Ukraine IT Hacking Groups Launching Cyber Rules PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting russian cyber attacks on ukraine it hacking groups launching cyber rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
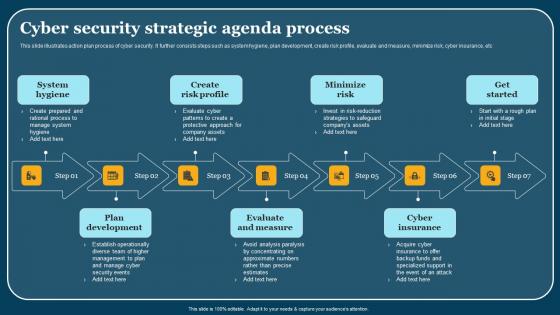
Cyber Security Strategic Agenda Process Demonstration Pdf
This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc. Showcasing this set of slides titled Cyber Security Strategic Agenda Process Demonstration Pdf. The topics addressed in these templates are System Hygiene, Plan Development, Evaluate And Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc.
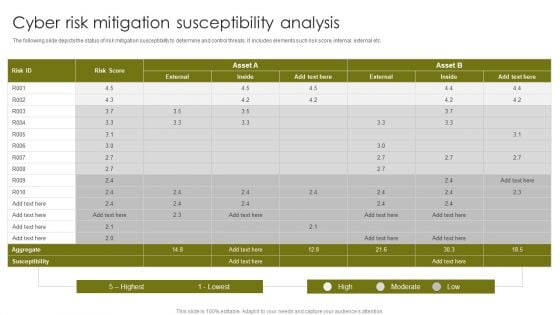
Cyber Risk Mitigation Susceptibility Analysis Diagrams PDF
The following slide depicts the status of risk mitigation susceptibility to determine and control threats. It includes elements such risk score, internal, external etc. Pitch your topic with ease and precision using this Cyber Risk Mitigation Susceptibility Analysis Diagrams PDF. This layout presents information on Cyber Risk Mitigation, Susceptibility Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Management Template Presentation Background Images
This is a cyber management template presentation background images. This is a six stage process. The stages in this process are risk review, policy, audit, cyber security life cycle, implementation, administration.
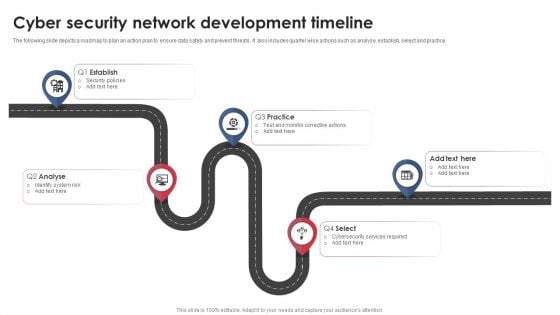
Cyber Security Network Development Timeline Download PDF
The following slide depicts a roadmap to plan an action plan to ensure data safety and prevent threats. It also includes quarter wise actions such as analyse, establish, select and practice. Presenting Cyber Security Network Development Timeline Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Establish, Analyse, Practice. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
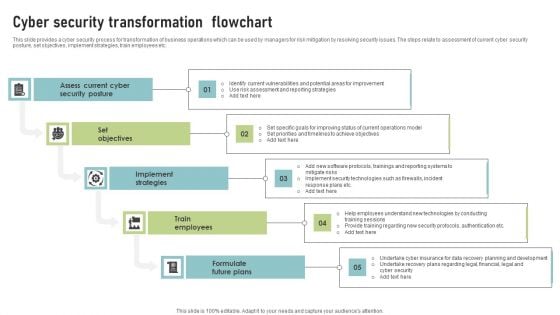
Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
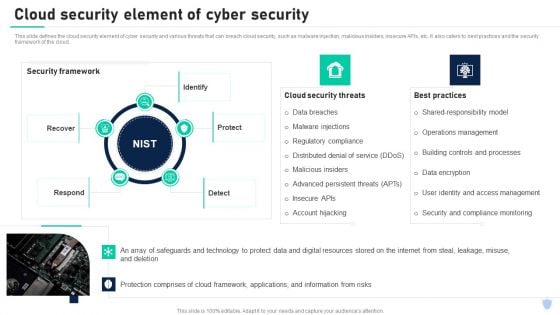
Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. It also caters to best practices and the security framework of the cloud. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
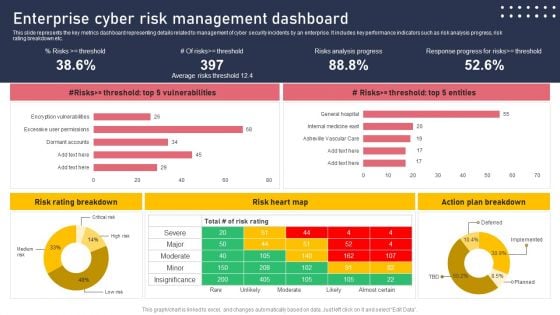
Enterprise Cyber Risk Management Dashboard Sample PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. There are so many reasons you need a Enterprise Cyber Risk Management Dashboard Sample PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
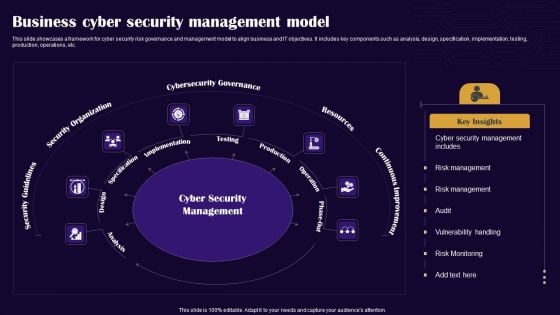
Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Risk Mitigation Framework Demonstration PDF
The following slide showcases the risk mitigation framework to plan preventive and reactive actions. It includes elements such as categorize, select, implement, assess, authorize and monitor etc. Persuade your audience using this Cyber Security Risk Mitigation Framework Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Categorize System, Select Security Controls, Implement Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
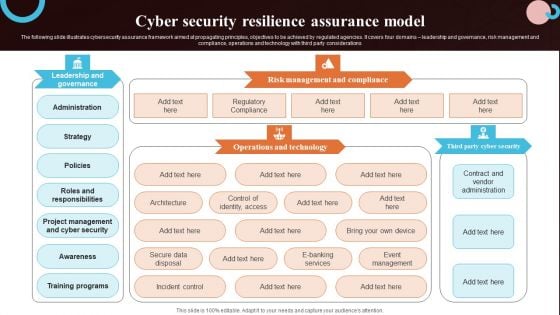
Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
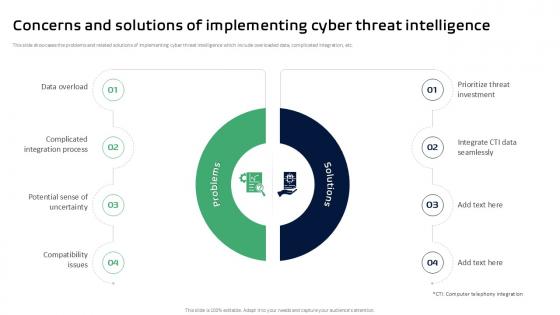
Concerns And Solutions Of Implementing Cyber Ppt Sample
This slide showcases the problems and related solutions of implementing cyber threat intelligence which include overloaded data, complicated integration, etc. Get a simple yet stunning designed Concerns And Solutions Of Implementing Cyber Ppt Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Concerns And Solutions Of Implementing Cyber Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases the problems and related solutions of implementing cyber threat intelligence which include overloaded data, complicated integration, etc.
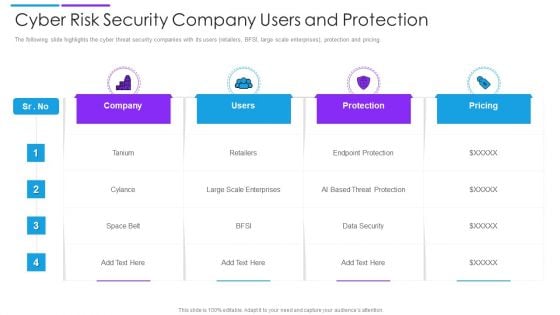
Cyber Risk Security Company Users And Protection Introduction PDF
The following slide highlights the cyber threat security companies with its users retailers, BFSI, large scale enterprises, protection and pricing. Showcasing this set of slides titled cyber risk security company users and protection introduction pdf. The topics addressed in these templates are company, users, protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Components To Enhance Processes Types Of Cyber Attackers Professional PDF
This slide represents the types of cyber attackers, including cyber criminals, hacktivists, state sponsored attackers, and insider threats. Insider threats can be occurred from within the organization and can be malicious, accidental or negligent. Present like a pro with Cyber Security Components To Enhance Processes Types Of Cyber Attackers Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
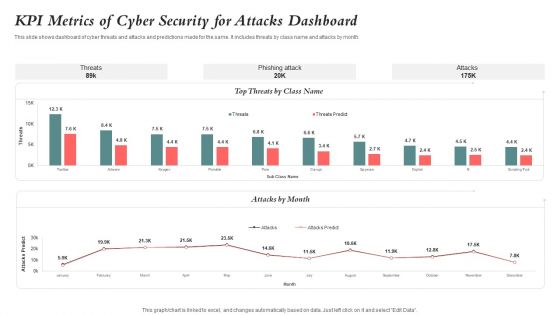
KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF
This slide shows dashboard of cyber threats and attacks and predictions made for the same. It includes threats by class name and attacks by month. Showcasing this set of slides titled KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF. The topics addressed in these templates are Kpi Metrics, Cyber Security, Attacks Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents Cyber Safety Incident Management Security Microsoft PDF
This is a table of contents cyber safety incident management security microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current scenario assessment, handling cyber threats to secure digital assets, ensuring physical security, securing firm from natural calamity threats . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
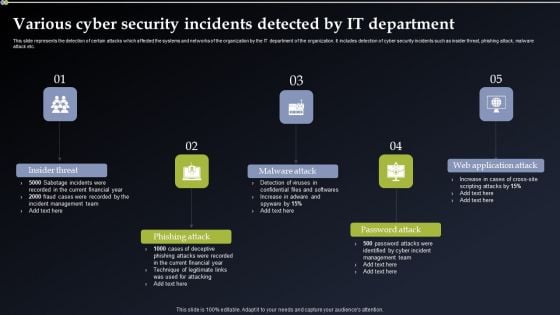
Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you searching for a Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF from Slidegeeks today.
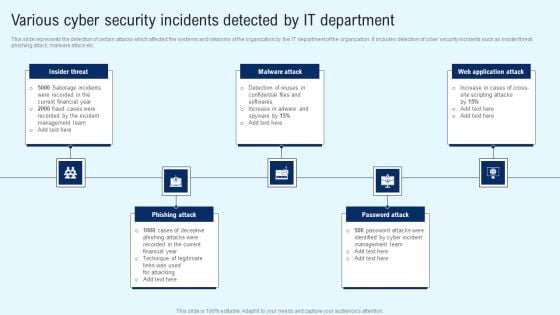
Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
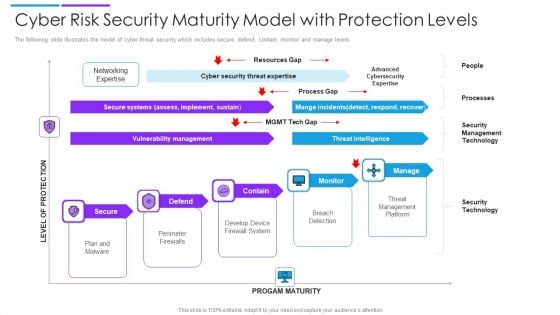
Cyber Risk Security Maturity Model With Protection Levels Mockup PDF
The following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Persuade your audience using this cyber risk security maturity model with protection levels mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including secure systems, vulnerability management, threat intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
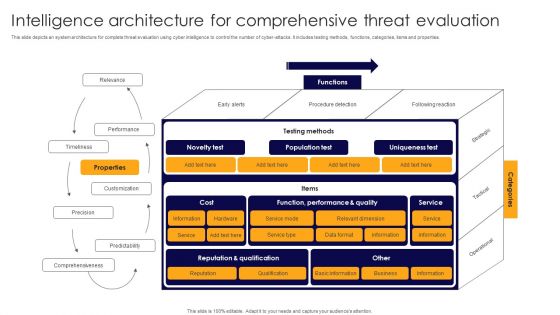
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
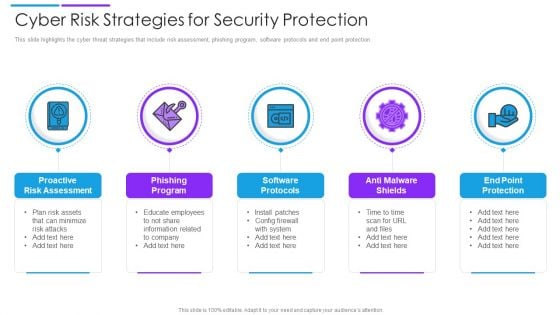
Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Cyber Security Risk Assessment Process Inspiration PDF
The slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Persuade your audience using this Business Cyber Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Detect, Respond, Protect, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
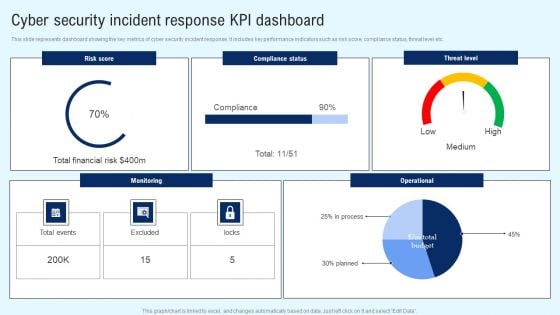
Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
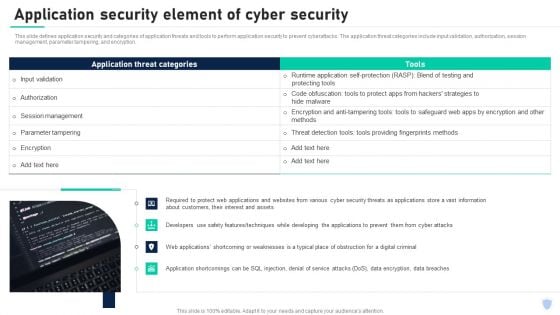
Cyber Security Components To Enhance Processes Application Security Element Of Cyber Security Infographics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Boost your pitch with our creative Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF
This slide depicts the hermetic wiper attack on ukrainian corporations, detected by a threat intelligence agency on february 23rd, and it damaged the master boot record through eases partition master. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
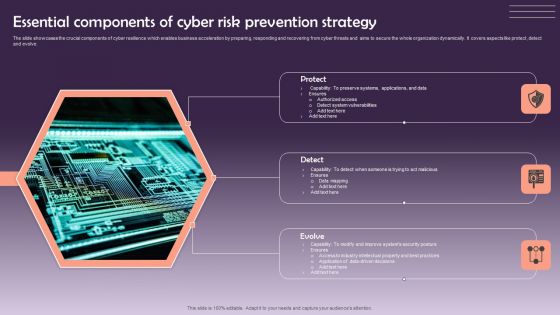
Essential Components Of Cyber Risk Prevention Strategy Information PDF
The slide showcases the crucial components of cyber resilience which enables business acceleration by preparing, responding and recovering from cyber threats and aims to secure the whole organization dynamically. It covers aspects like protect ,detect and evolve. Presenting Essential Components Of Cyber Risk Prevention Strategy Information PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Protect, Detect, Evolve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
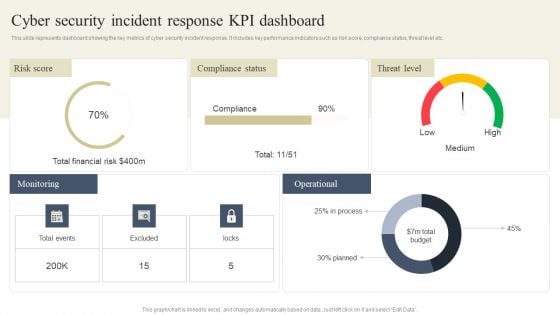
CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Determine Several Threat Actors Profile Monitoring Digital Assets Topics Pdf
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Determine Several Threat Actors Profile Monitoring Digital Assets Topics Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc.
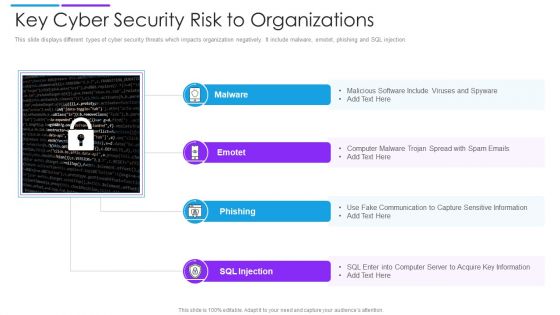
Key Cyber Security Risk To Organizations Structure PDF
This slide displays different types of cyber security threats which impacts organization negatively. It include malware, emotet, phishing and SQL injection. Presenting key cyber security risk to organizations structure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including malware, phishing, sql injection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
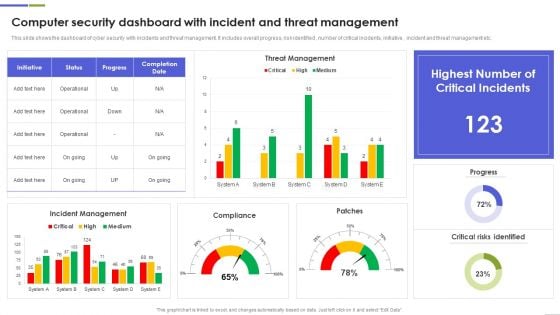
Computer Security Dashboard With Incident And Threat Management Rules PDF
This slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc.Showcasing this set of slides titled Computer Security Dashboard With Incident And Threat Management Rules PDF The topics addressed in these templates are Critical Incidents, Risks Identified, Compliance All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
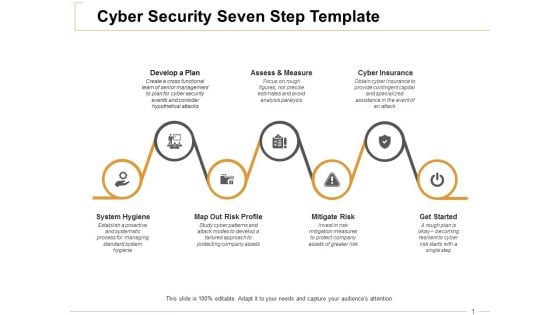
Cyber Security Seven Step Cyber Insurance Ppt PowerPoint Presentation Infographic Template Graphic Tips
This is a cyber security seven step cyber insurance ppt powerpoint presentation infographic template graphic tips. This is a seven stage process. The stages in this process are develop a plan, assess and measure, cyber insurance, mitigate risk, get started.
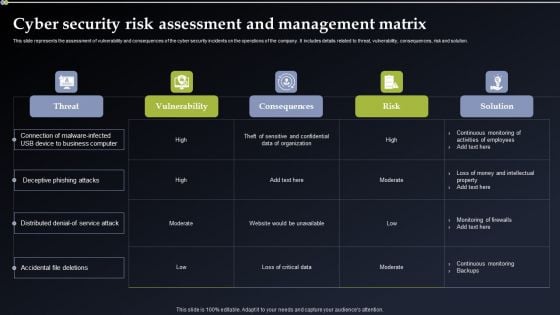
Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment And Management Matrix Rules PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment And Management Matrix Rules PDF from Slidegeeks and deliver a wonderful presentation.
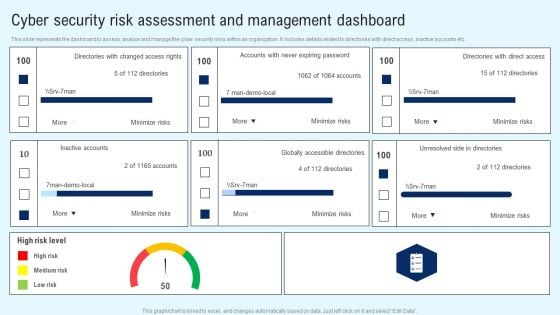
Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
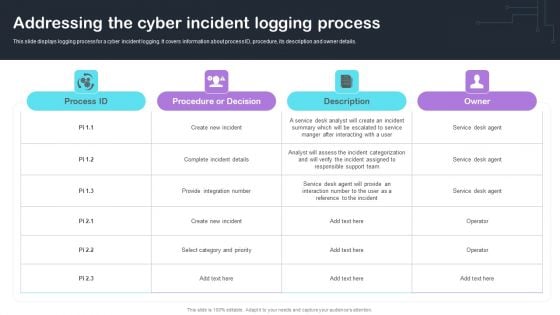
Cyber Risks And Incident Response Playbook Addressing The Cyber Incident Logging Process Background PDF
Cyber Risks And Incident Response Playbook Addressing The Cyber Incident Logging Process Background PDF. Find a pre-designed and impeccable Cyber Risks And Incident Response Playbook Addressing The Cyber Incident Logging Process Background PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for. Download the template from Slidegeeks today and give a unique touch to your presentation.

Develop Corporate Cyber Security Risk Mitigation Plan Contact Us For Organization Cyber Protection Services Portrait PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan contact us for organization cyber protection services portrait pdf bundle. Topics like contact us, organization, cyber protection services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
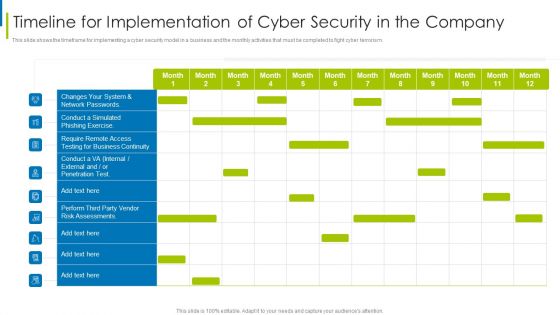
Cyber Terrorism Assault Timeline For Implementation Of Cyber Security In The Company Sample PDF
This slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism.Deliver an awe inspiring pitch with this creative cyber terrorism assault timeline for implementation of cyber security in the company sample pdf bundle. Topics like require remote access, testing for business continuity, risk assessments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
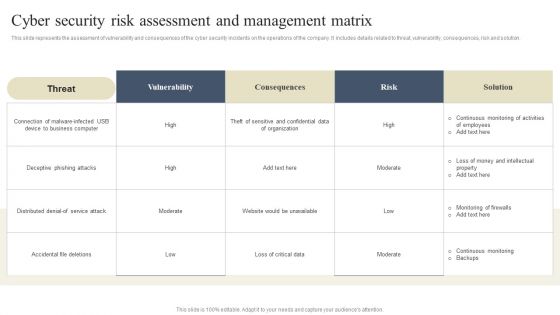
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.


 Continue with Email
Continue with Email

 Home
Home


































