Cybersecurity Icons

Info Security Cyber Safety Tips Protection Against Cyberattacks Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a info security cyber safety tips protection against cyberattacks ppt powerpoint presentation gallery designs download pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect the network, email attachment, time interval. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
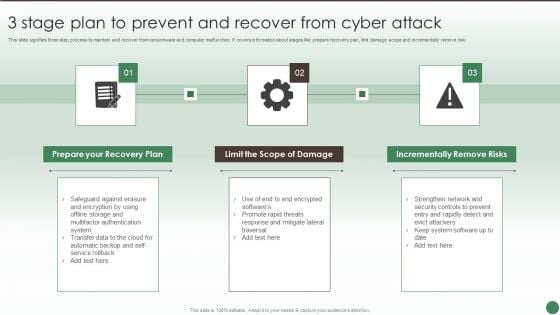
3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF
This slide signifies three step process to maintain and recover from ransomware and computer malfunction. It covers information about stages like prepare recovery plan, limit damage scope and incrementally remove risk. Persuade your audience using this 3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Recovery Plan, Limit Scope Damage, Incrementally Remove Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
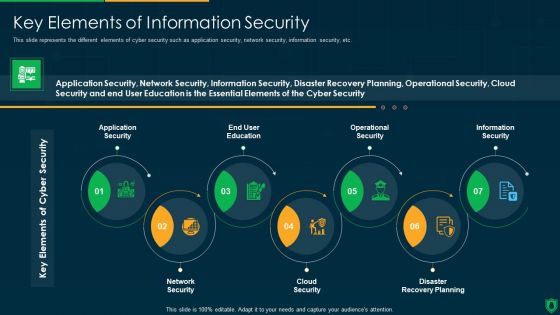
Info Security Key Elements Of Information Security Ppt PowerPoint Presentation Gallery Slide Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. Presenting info security key elements of information security ppt powerpoint presentation gallery slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like application security, end user education, operational security, information security, network security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
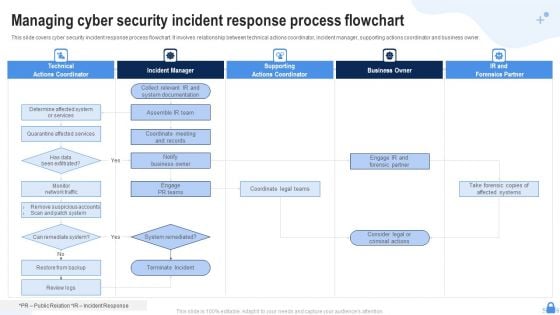
Managing Cyber Security Incident Response Process Flowchart Ppt Templates PDF
This slide covers cyber security incident response process flowchart. It involves relationship between technical actions coordinator, incident manager, supporting actions coordinator and business owner. Presenting Managing Cyber Security Incident Response Process Flowchart Ppt Templates PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Technical Actions Coordinator, Incident Manager, Supporting Actions Coordinator. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
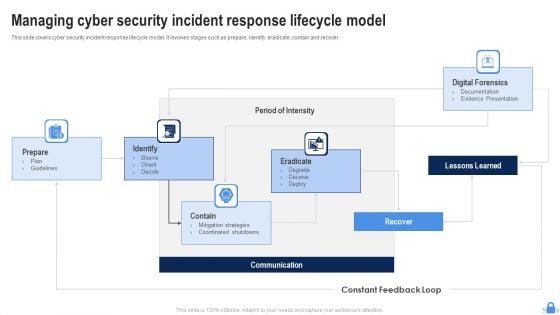
Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF
This slide covers cyber security incident response lifecycle model. It involves stages such as prepare, identify, eradicate, contain and recover. Persuade your audience using this Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare, Identify, Contain, Communication, Eradicate, Lessons Learned. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
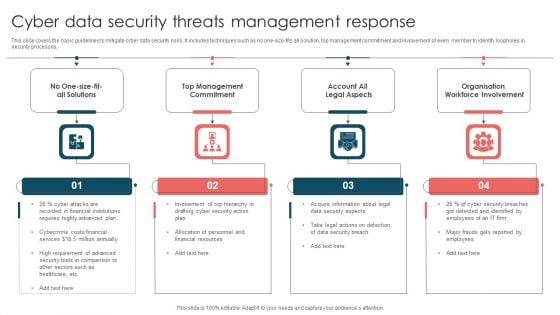
Cyber Data Security Threats Management Response Ppt Summary Skills PDF
This slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one-size-fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Presenting Cyber Data Security Threats Management Response Ppt Summary Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organisation Workforce Involvement, Account Legal Aspects, Top Management Commitment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
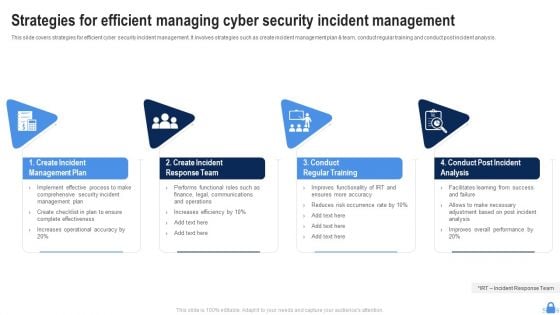
Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF
This slide covers strategies for efficient cyber security incident management. It involves strategies such as create incident management plan and team, conduct regular training and conduct post incident analysis. Presenting Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Incident Management Plan, Create Incident, Response Team, Conduct Regular Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
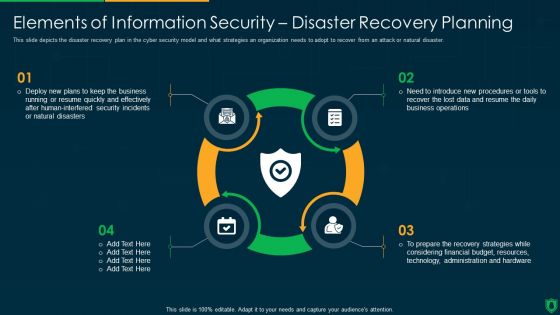
Info Security Elements Of Information Security Disaster Recovery Planning Ppt PowerPoint Presentation Gallery Designs PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a info security elements of information security disaster recovery planning ppt powerpoint presentation gallery designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deploy new plans, quickly and effectively, security incidents, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Pillars Of Cloud Security Network Security Ppt Inspiration Layouts PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. Presenting Cloud Information Security Pillars Of Cloud Security Network Security Ppt Inspiration Layouts PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Premises Conditions, Micro Segmentation, Cloud Based Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Staff Learning Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting organizational network staff learning security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security awareness program, implementing security awareness, sustaining security awareness. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
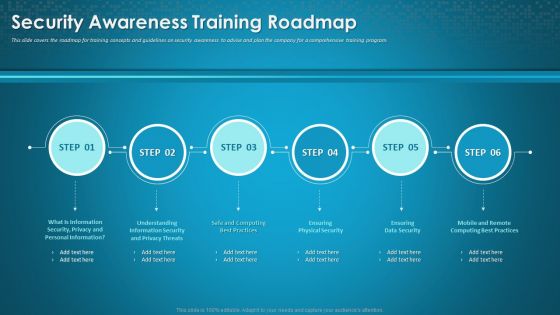
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
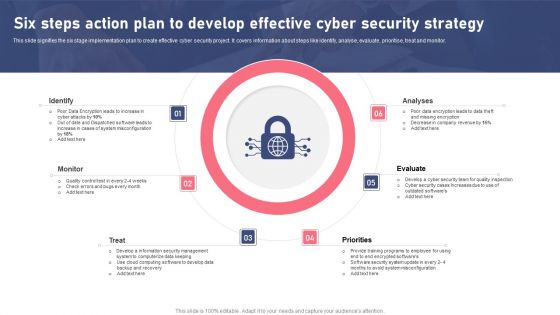
Six Steps Action Plan To Develop Effective Cyber Security Strategy Ppt Layouts Designs Download PDF
This slide signifies the six stage implementation plan to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor. Presenting Six Steps Action Plan To Develop Effective Cyber Security Strategy Ppt Layouts Designs Download PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Identify, Monitor, Priorities, Evaluate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
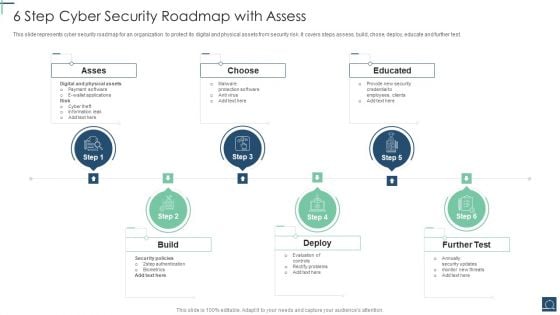
6 Step Cyber Security Roadmap With Assess Ppt PowerPoint Presentation File Objects PDF
This slide represents cyber security roadmap for an organization to protect its digital and physical assets from security risk .It covers steps assess, build, chose, deploy, educate and further test. Persuade your audience using this 6 Step Cyber Security Roadmap With Assess Ppt PowerPoint Presentation File Objects PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Asses, Choose, Educated, Build. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
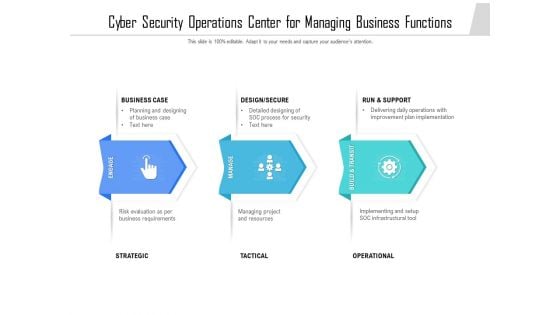
Cyber Security Operations Center For Managing Business Functions Ppt Show Layouts PDF
Presenting cyber security operations center for managing business functions ppt show layouts pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including operational, business, strategic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
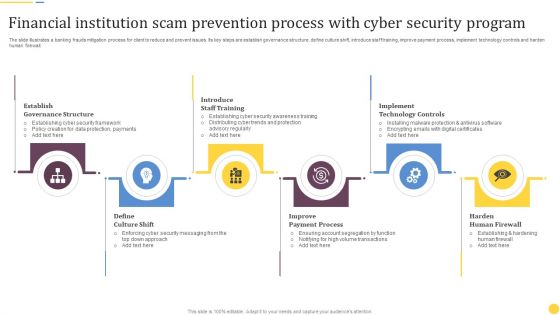
Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
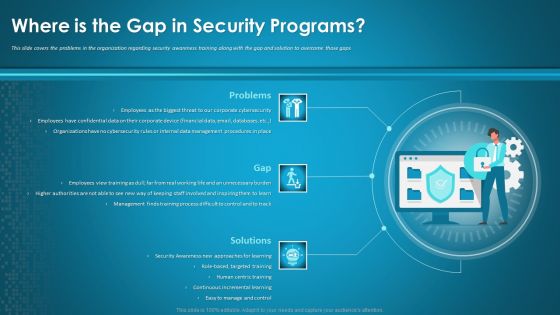
Organizational Network Security Awareness Staff Learning Where Is The Gap In Security Programs Template PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a organizational network security awareness staff learning where is the gap in security programs template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees, management, organizations, targeted training, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF
The following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including People, Process, Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
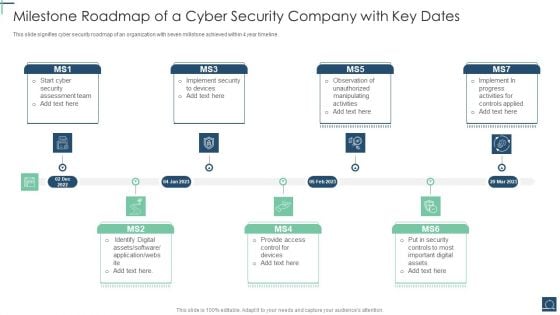
Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
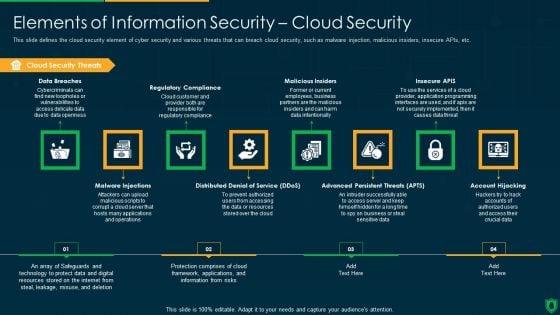
Info Security Elements Of Information Security Cloud Security Ppt PowerPoint Presentation Gallery Graphics Download PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting info security elements of information security cloud security ppt powerpoint presentation gallery graphics download pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like cloud security threats, regulatory compliance, malicious insiders, insecure apis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
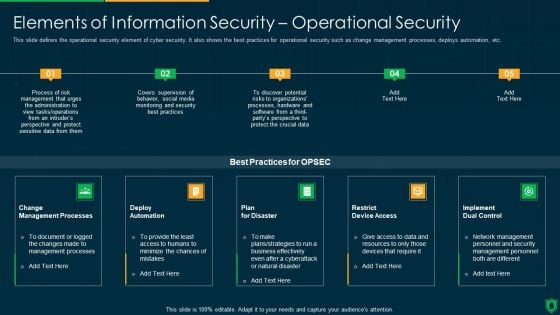
Info Security Elements Of Information Security Operational Security Ppt PowerPoint Presentation File Backgrounds PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a info security elements of information security operational security ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
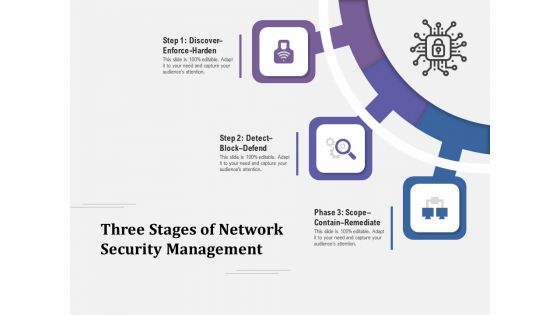
Three Stages Of Network Security Management Ppt PowerPoint Presentation Layouts Influencers PDF
Presenting three stages of network security management ppt powerpoint presentation layouts influencers pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
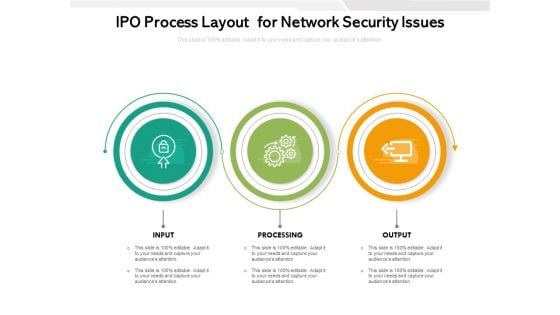
IPO Process Layout For Network Security Issues Ppt PowerPoint Presentation Outline Graphics Template PDF
Persuade your audience using this ipo process layout for network security issues ppt powerpoint presentation outline graphics template pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including processing, output, input. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
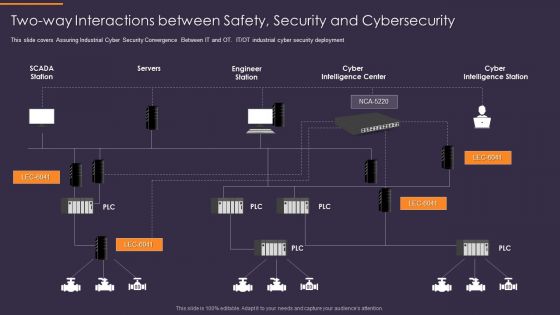
Convergence Strategy Information Two Way Interactions Between Safety Security Rules PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment. Presenting Convergence Strategy Information Two Way Interactions Between Safety Security Rules PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Servers, Engineer Station, Cyber Intelligence Center, Cyber Intelligence Station. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
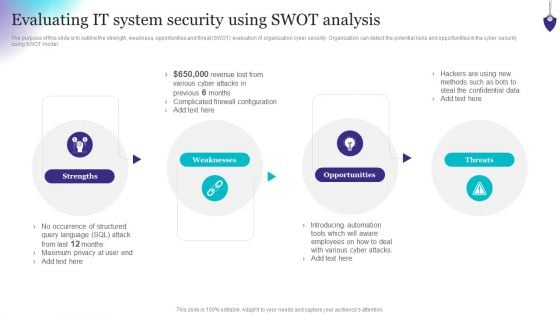
Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Slidegeeks is here to make your presentations a breeze with Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
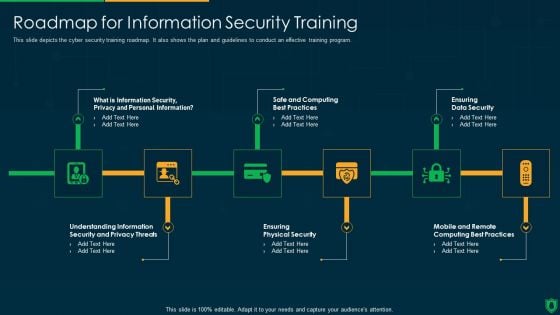
Info Security Roadmap For Information Security Training Ppt PowerPoint Presentation File Inspiration PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a info security roadmap for information security training ppt powerpoint presentation file inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, personal information, safe and computing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
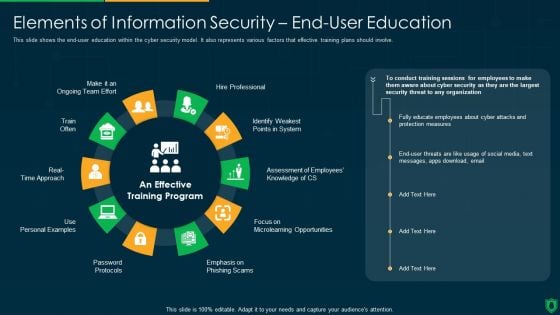
Info Security Elements Of Information Security End User Education Ppt PowerPoint Presentation File Example File PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. Presenting info security elements of information security end user education ppt powerpoint presentation file example file pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like hire professional, emphasis on phishing scam, password protocols, train often. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
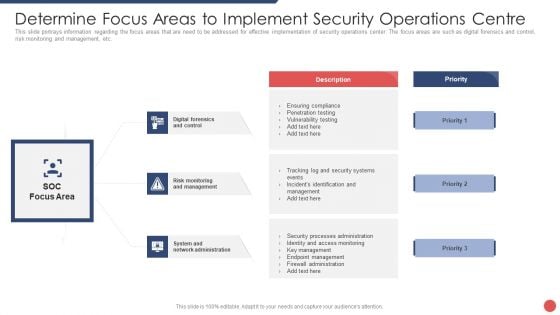
Security Functioning Centre Determine Focus Areas To Implement Security Operations Centre Demonstration PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security functioning centre determine focus areas to implement security operations centre demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk monitoring, management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
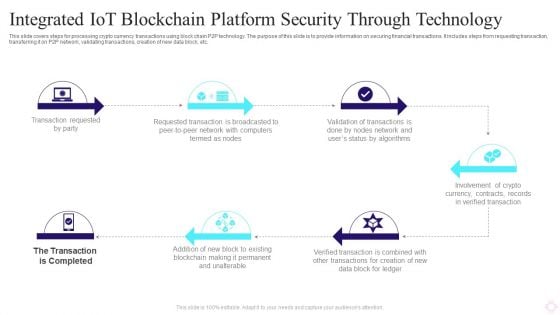
Integrated IOT Blockchain Platform Security Through Technology Background PDF
This slide covers steps for processing crypto currency transactions using block chain P2P technology. The purpose of this slide is to provide information on securing financial transactions. It includes steps from requesting transaction, transferring it on P2P network, validating transactions, creation of new data block, etc. Persuade your audience using this Integrated IOT Blockchain Platform Security Through Technology Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Requested Party, Requested Transaction, Crypto Currency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF
The following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assessment Methodology, Risk QuestionsCyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Integrating Naas Service Model To Enhance Benefits Of Network As A Service Naas Clipart PDF
This slide depicts the benefits of the network as a service, including IT simplicity and automation, access to network services from anywhere, enhanced cloud and on-premise security, visibility and insights, flexibility, and on-demand scalability of the network. There are so many reasons you need a Integrating Naas Service Model To Enhance Benefits Of Network As A Service Naas Clipart PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Integrating Naas Service Model To Enhance Network As A Service Cloud Connections Rules PDF
This slide represents the naas cloud connections, covering metro ethernet, layer 2 virtual private networks, layer 3 virtual private networks, internet protocol secure ipsec MPLS vpns, SD-WAN, firewall, VCPE, remote access gateways, and so on. Explore a selection of the finest Integrating Naas Service Model To Enhance Network As A Service Cloud Connections Rules PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Naas Service Model To Enhance Network As A Service Cloud Connections Rules PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
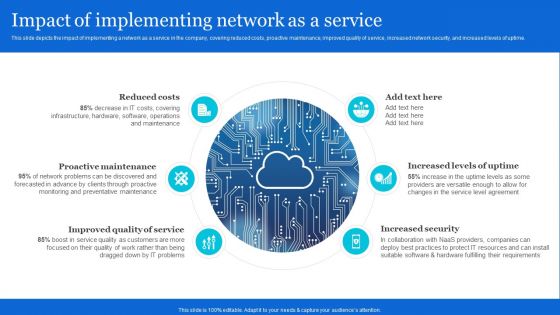
Naas Architectural Framework Impact Of Implementing Network As A Service Structure PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Naas Architectural Framework Impact Of Implementing Network As A Service Structure PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Naas Architectural Framework Impact Of Implementing Network As A Service Structure PDF today and make your presentation stand out from the rest.
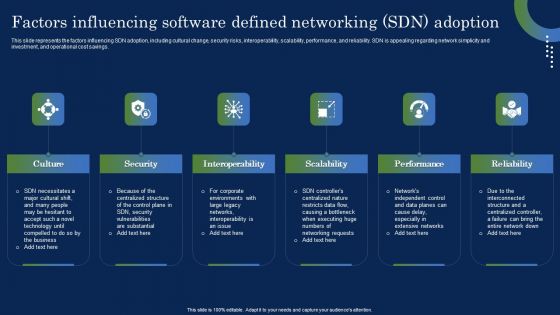
Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
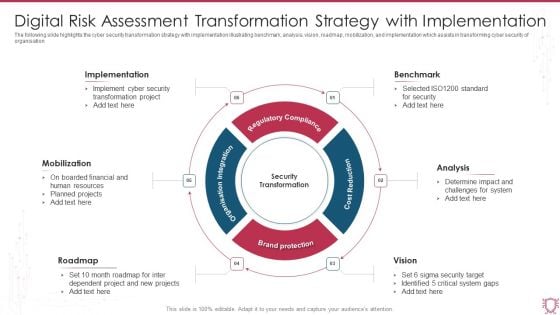
Digital Risk Assessment Transformation Strategy With Implementation Slides PDF
The following slide highlights the cyber security transformation strategy with implementation illustrating benchmark, analysis, vision, roadmap, mobilization, and implementation which assists in transforming cyber security of organisation. Presenting Digital Risk Assessment Transformation Strategy With Implementation Slides PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Implementation, Benchmark, Analysis, Vision. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
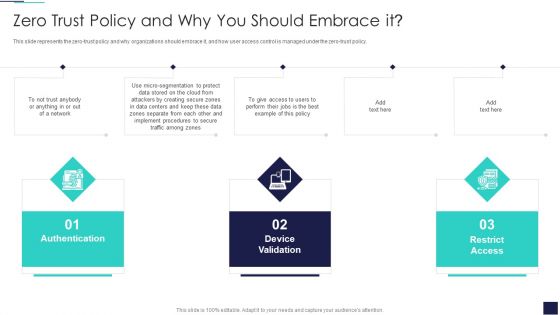
Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
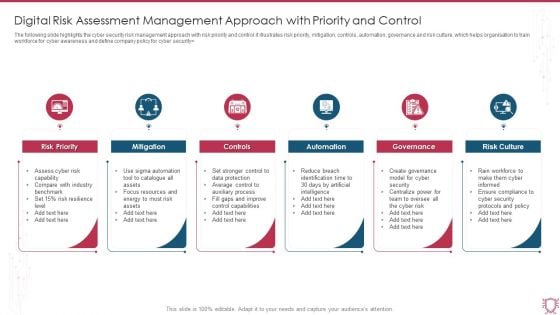
Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF
The following slide highlights the cyber security risk management approach with risk priority and control it illustrates risk priority, mitigation, controls, automation, governance and risk culture, which helps organisation to train workforce for cyber awareness and define company policy for cyber security. Persuade your audience using this Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Priority, Mitigation, Controls, Automation, Governance, Risk Culture. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
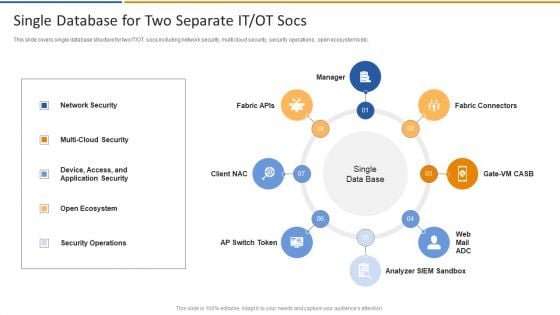
Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Network Security, Multi Cloud Security, Device Access, Application Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Transformation Of Consumer Emerging Technological Trends For Banking Company Topics PDF
This slide shows the latest technological trends which should be adopted by the ABC Bank which includes cyber security, upgraded ATMs, Chatbot, Artificial Intelligence etc. Presenting Digital Transformation Of Consumer Emerging Technological Trends For Banking Company Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Cyber Security, Upgraded ATMs, Cloud Computing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
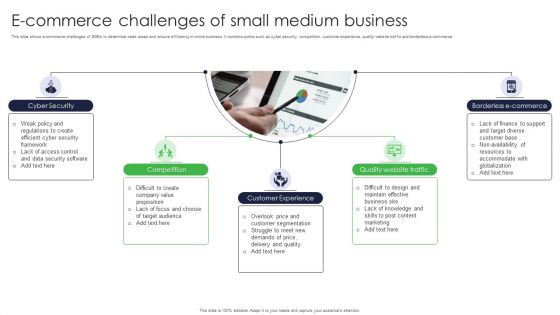
E Commerce Challenges Of Small Medium Business Ppt Infographic Template Inspiration PDF
This slide shows e-commerce challenges of SMEs to determine weak areas and ensure efficiency in online business. It contains points such as cyber security, competition, customer experience, quality website traffic and borderless e-commerce. Persuade your audience using this E Commerce Challenges Of Small Medium Business Ppt Infographic Template Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Customer Experience, Quality Website Traffic. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF
The following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Presenting Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Asset Inventory, Synchronization, Response, Security Gaps. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
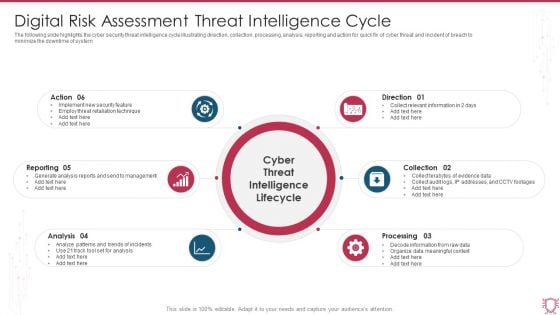
Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF
The following slide highlights the cyber security threat intelligence cycle illustrating direction, collection, processing, analysis, reporting and action for quick fix of cyber threat and incident of breach to minimize the downtime of system. Persuade your audience using this Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Reporting, Analysis, Processing, Direction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Application Software Development Business Profile SWOT Analysis Structure PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth This Digital Application Software Development Business Profile SWOT Analysis Structure PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF
The following slide highlights the five phase of risk based cyber security which includes business impact analysis, risk assessment, controls, report and monitor, it provides activity, value and outcome for each phase which helps company to develop a consistent incident response process. Presenting Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Business Impact Analysis, Risk Assessment, Controls, Report, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF
The following slide highlights the phase of cyber security incident response cycle depicting preparation phase, analysis phase, response phase, and post event phase. Persuade your audience using this Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Post Event Phase, Response Phase, Preparation Phase, Analysis Phase. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
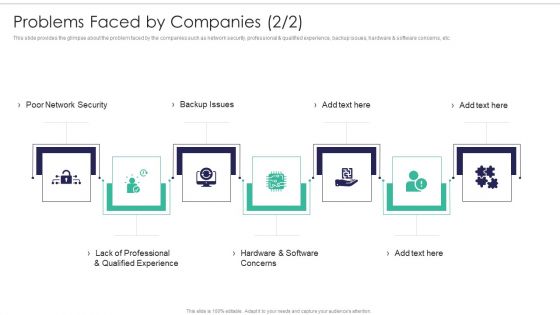
Software Firm Stakeholder Capital Raising Elevator Problems Faced By Companies Diagrams PDF
This slide provides the glimpse about the problem faced by the companies such as network security, professional and qualified experience, backup issues, hardware and software concerns, etc. Presenting software firm stakeholder capital raising elevator problems faced by companies diagrams pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like hardware and software concerns, poor network security, backup issues, lack of professional and qualified experience. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
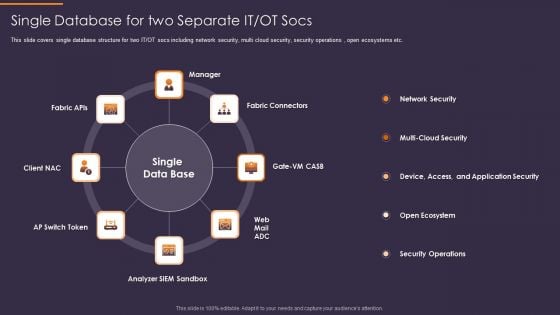
Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Fabric Connectors, Analyzer SIEM Sandbox, AP Switch Token, Client NAC, Fabric APIs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
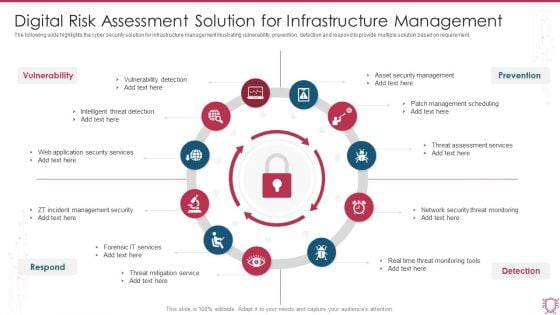
Digital Risk Assessment Solution For Infrastructure Management Pictures PDF
The following slide highlights the cyber security solution for infrastructure management illustrating vulnerability, prevention, detection and respond to provide multiple solution based on requirement. Persuade your audience using this Digital Risk Assessment Solution For Infrastructure Management Pictures PDF. This PPT design covers eleven stages, thus making it a great tool to use. It also caters to a variety of topics including Vulnerability Detection, Intelligent Threat Detection, Forensic IT Services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
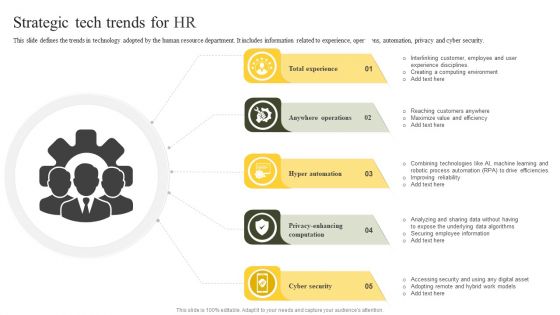
Strategic Tech Trends For HR Ppt PowerPoint Presentation File Professional PDF
This slide defines the trends in technology adopted by the human resource department. It includes information related to experience, operations, automation, privacy and cyber security. Persuade your audience using this Strategic Tech Trends For HR Ppt PowerPoint Presentation File Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Total Experience, Anywhere Operations, Hyper Automation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
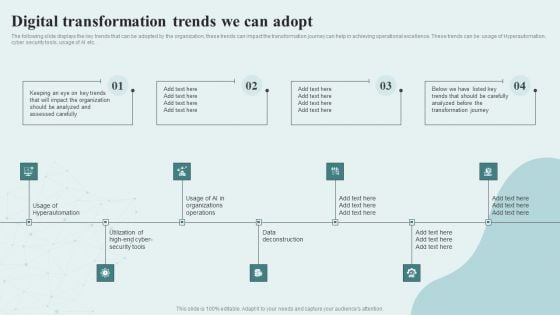
Digital Competency Evaluation And Modification Digital Transformation Trends We Can Adopt Themes PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyperautomation, cyber security tools, usage of AI etc. Want to ace your presentation in front of a live audience Our Digital Competency Evaluation And Modification Digital Transformation Trends We Can Adopt Themes PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
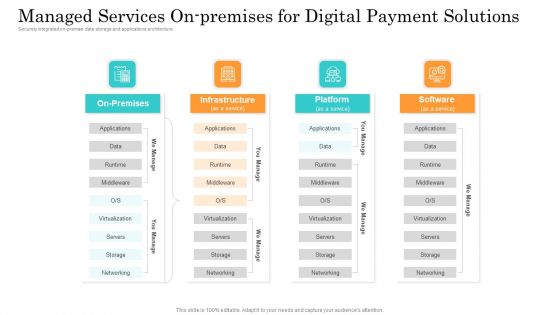
Online Payment Service Managed Services On Premises For Digital Payment Solutions Mockup PDF
Securely integrated on premise data storage and applications architecture. This is a online payment service managed services on premises for digital payment solutions mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, platform, servers, networking, storage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integrating Naas Service Model To Enhance What A Naas Model Should Look Like Topics PDF
This slide depicts how a network as a service model should contain, covering hardware or equipment, flexible consumption, predictable costs about usage, managing the naas model from the cloud and updates and security. Retrieve professionally designed Integrating Naas Service Model To Enhance What A Naas Model Should Look Like Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF from Slidegeeks today. This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
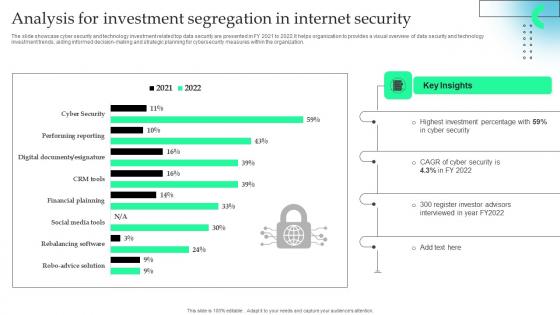
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.
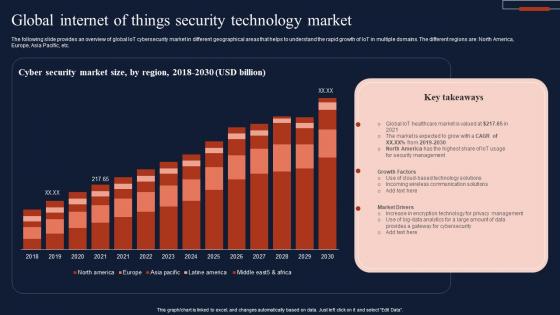
Global Internet Of Things Security Technology Market Infographics Pdf
The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc. Showcasing this set of slides titled Global Internet Of Things Security Technology Market Infographics Pdf The topics addressed in these templates are Cyber Security, Market Size, Technology Market All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc.
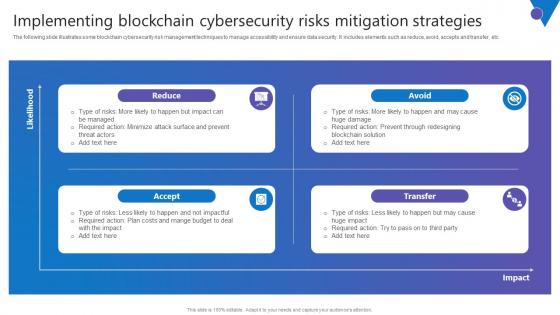
Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc.

Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf
Are you searching for a Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf from Slidegeeks today. Our Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Add More Services In The Organization Layered Pricing Strategy For Managed Services Themes Pdf
This slide covers the additional service which a company must introduce to grow in the industry such as cybersecurity services, network operation center monitoring, mobile device management solution, VoIP technology. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Add More Services In The Organization Layered Pricing Strategy For Managed Services Themes Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide covers the additional service which a company must introduce to grow in the industry such as cybersecurity services, network operation center monitoring, mobile device management solution, VoIP technology.

Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc.
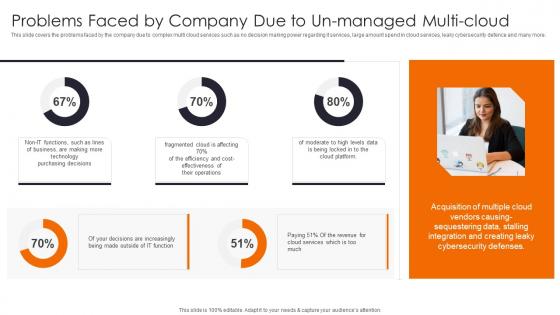
Problems Faced By Company Enhancing Workload Efficiency Through Cloud Architecture Topics Pdf
This slide covers the problems faced by the company due to complex multi cloud services such as no decision making power regarding it services, large amount spend in cloud services, leaky cybersecurity defence and many more. There are so many reasons you need a Problems Faced By Company Enhancing Workload Efficiency Through Cloud Architecture Topics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide covers the problems faced by the company due to complex multi cloud services such as no decision making power regarding it services, large amount spend in cloud services, leaky cybersecurity defence and many more.
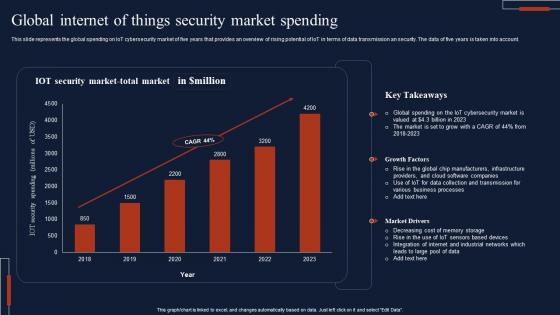
Global Internet Of Things Security Market Spending Download Pdf
This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account. Pitch your topic with ease and precision using this Global Internet Of Things Security Market Spending Download Pdf This layout presents information on IOT Security, Market Total, Key Takeaways It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account.


 Continue with Email
Continue with Email

 Home
Home


































